Computing Igusa's local zeta functions of univariate polynomials, and linear feedback shift
【计算机应用与软件】_搜索技术_期刊发文热词逐年推荐_20140724
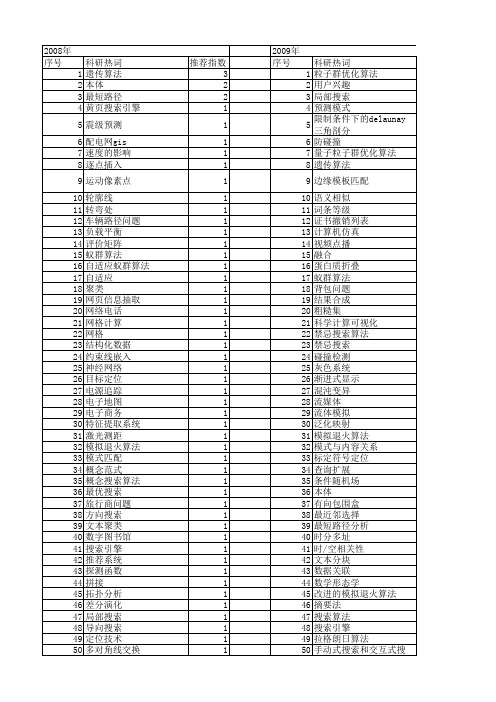
科研热词 搜索引擎 遗传算法 运动估计 自适应 垂直搜索 lucene 音乐数据库 遥测数据 迷宫搜索算法 运动拼接网格 路径规划 贝叶斯网络 调度 话题跟踪 话题检测 证书撤销 设计agent 认知无线电 蚂蚁算法 节点搜索 自动分流 聚类 网页清理 网络舆情 缺失数据 综合搜索 统计检验 统一数据接口 线性搜索 等高图 知识共享 直接解法 电脑鼠机器人 生长树 爬虫 熟收敛 灾变算子 混沌搜索 桌面搜索 标准遗传算法 栅格法 机器人 有解性 最优路径 时间步记忆搜索 无线传感器网络 族间交叉 旋律搜索 旅行商问题 数码问题 搜索算法 微粒群优化
推荐指数 2 2 2 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
2010年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52
2009年 序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
lovasz local lemma的证明 -回复

lovasz local lemma的证明-回复lovasz local lemma是一种概率方法,用于证明存在性问题。
它由鲁迅大学的匈牙利裔数学家Miklós Lovász于1975年发现并证明。
这个引人注目的定理最初是为组合问题提出的,但后来发展成为解决其他领域中的存在性问题的有力工具。
在本文中,我们将逐步探讨lovasz local lemma 的证明过程。
首先,让我们定义lovasz local lemma用到的一些基本概念。
假设有一个由n个事件组成的事件空间Ω={A_1,A_2,...,A_n},其中每个事件A_i都与其他k个事件有关。
这些事件出现或不出现被认为是随机的。
我们的目标是证明至少存在一个事件A_i,使其不受其他事件的影响,即事件A_i 的发生仅取决于自身。
根据lovasz local lemma的条件,如果我们可以证明每个事件A_i最多依赖于其他d个事件的发生,并且Pr(A_i) ≤p < 1/4d,那么至少存在一个事件A_i是独立的。
这将揭示出事件的某种自由性,即使在其他事件发生的情况下,它也可以独立地发生。
为了证明这个引人注目的定理,我们需要一个严格的算法。
接下来,我们将介绍一种被称为染色法的方法,这是证明lovasz local lemma的一种常见方法。
首先,我们为每个事件A_i分配一个颜色c_i,这些颜色取值范围为{1,2,...,n}。
然后,我们定义事件的邻接列表G={A_1,A_2,...,A_n},其中A_i与事件A_j相关联,如果A_i依赖于A_j的发生。
在染色时,我们假设颜色分配是随机的,即每个事件有相同的概率获得任何颜色。
现在,我们要构建一个函数Bad(A_i),用于判断事件A_i是否处于“坏”的状态。
我们定义坏事件为,事件A_i依赖于其他事件A_j的发生,并且A_j与A_i具有相同的颜色。
简而言之,如果存在一个相邻事件A_j具有相同的颜色,那么事件A_i被认为是坏的。
c++中scientific

计算库的应用一、引言C++作为一种广泛使用的编程语言,其在科学计算领域有着重要的应用价值。
在C++中,科学计算库是非常重要的组成部分,它提供了许多常用的科学计算功能和算法,可以帮助程序员简化复杂的科学计算任务。
本文将重点介绍C++中科学计算库的应用,并讨论其在实际工程和科学研究中的重要性。
二、C++中常用的科学计算库在C++中,有许多优秀的科学计算库可供选择,例如:1. Eigen():Eigen是一个开源的C++模板库,提供了线性代数和矩阵运算的功能,是C++中常用的科学计算库之一。
2. Armadillo():Armadillo是一个C++模板库,提供了高效的线性代数运算和矩阵计算的功能,具有简单易用的API和高性能的特点。
3. Boost C++库():Boost是一个经典的C++库,提供了丰富的科学计算功能,包括数值计算、随机数生成、多元函数优化等。
三、科学计算库在工程领域的应用在工程领域,科学计算库发挥着重要的作用,例如:1. 有限元分析:有限元分析是工程领域常用的数值计算方法,可以用于模拟和分析各种结构的力学行为。
利用C++中的科学计算库,可以高效地实现有限元分析算法,加快计算速度并提高计算精度。
2. 机器学习:机器学习算法是近年来备受关注的热门技术,它可以应用于工程领域的数据分析、预测和优化问题。
C++中的科学计算库提供了丰富的数值计算和统计学习功能,可以帮助工程师快速实现各种机器学习算法。
3. 优化问题:在工程设计和生产过程中,经常需要解决各种优化问题,例如工艺优化、产品设计优化等。
使用C++中的科学计算库,可以快速实现各种优化算法,对工程优化问题进行高效求解。
四、科学计算库在科学研究中的应用在科学研究中,科学计算库也发挥着重要的作用,例如:1. 数学模型求解:科学研究经常需要建立各种数学模型来描述自然现象,利用C++中的科学计算库,可以高效地对数学模型进行数值求解,研究模型的性质和行为。
实数编码遗传算法求二阶两点边值问题的数值解

实数编码遗传算法求二阶两点边值问题的数值解
实数编码遗传算法求二阶两点边值问题的数值解
应用实数编码遗传算法,对二阶两点边值问题提出了一种简单的数值解法.该解法适于线性和非线性问题的求解,理论分析和数值实验证明了该该方法的有效性.
作者:彭灵翔胡兵 PENG Ling-xiang HU Bing 作者单位:彭灵翔,PENG Ling-xiang(四川大学数学学院,成都,610064;西安卫星测控中心,西安,710043)
胡兵,HU Bing(四川大学数学学院,成都,610064)
刊名:四川大学学报(自然科学版)ISTIC PKU英文刊名:JOURNAL OF SICHUAN UNIVERSITY(NATURAL SCIENCE EDITION) 年,卷(期):2007 44(6) 分类号:O241.8 关键词:二阶两点边值问题实数编码遗传算法数值解常微分方程有限差分法。
非保守荷载超弹性大变形分析的复变量无单元Galerkin方法

摘要不同于其它数值计算方法在求解过程中需要划分网格,无网格法在求解力学问题时只需要定义节点,直接建立系统代数方程,在涉及网格畸变、网格移动等问题时具有灵活性、自适应性,是一种具有强大发展潜力的数值计算方法。
无单元Galerkin方法是目前应用最广的无网格计算方法,本文将复变量移动最小二乘近似引入无单元Galerkin方法中,可以改进无单元Galerkin方法中计算量大的问题。
相对于移动最小二乘近似,采用复变量移动最小二乘近似中基函数的维数降低,从而试函数中的系数项减少,问题域中需要的节点数也相应减少,计算效率提高。
在实际工程结构和材料的大变形过程中,外荷载往往会随着受力面的变形而发生变化,此时荷载是依赖于变形状态的非保守力,数值处理相对复杂。
相较于弹性材料的大变形分析,超弹性材料在受力作用下可以产生更大的变形,而且由于其近不可压性,在采用数值方法进行求解时易出现体积锁死和压力震荡现象,造成分析困难。
综上所述,有必要研究非保守荷载下超弹性材料的大变形问题。
使用有限元方法解决这类问题时易发生网格畸变,无网格法由于其自身的优越性,在处理这类问题上有很大的优势。
本文将复变量无单元Galerkin方法应用于求解非保守荷载下弹性和超弹性大变形问题,采用罚函数法引入本质边界条件,推导了非保守荷载大变形问题的增量形式的完全Lagrange格式的Galerkin积分弱形式。
采用混合变量法解决超弹性材料的不可压性带来的求解困难,采用复变量移动最小二乘法建立位移场的逼近函数,推导了相应的超弹性切线模量、应变位移转换矩阵和刚度矩阵,建立了无网格大变形分析的离散方程,采用Newton-Raphson法进行迭代求解。
本文建立了非保守荷载作用下超弹性大变形分析的算法流程,编制了MATLAB计算程序,对经典悬臂梁算例、蜂窝结构以及纯弯梁算例等进行了计算分析。
与无单元Galerkin方法得到的结果相比,采用复变量无单元Galerkin 方法计算效率更高;采用复变量无单元Galerkin方法分析大转动问题时能得到非常大的变形而不会因产生网格畸变导致很大的误差;对三维超弹性材料进行模拟与分析,分析了超弹性材料在基本荷载作用下的应力应变关系;分析了采用复变量无单元Galerkin方法求解负泊松比结构的可行性,为研究负泊松比结构的物理特性和力学性能奠定了基础。
武汉大学资环学院gis地图学与地理信息系统考研(真题+答案+笔记)

现在大家可能也在面临着选择,比如是否考研,考哪个学校,考哪个专业,跟哪个导师, 怎样平衡专业课与公共课的时间等等。作为过来人,当初的我们和大家一样,也在思考着类 似的问题;也正因为是过来人,我们才有了给大家提供建议的底气。借此机会,把我们一些 个人看法与大家交流,虽个人经历不同,经验不足以证明什么,但仅供参考之用足矣! 1、为什么要考研?
II
学长学姐们对大家网上购买资料的几点忠告
1、考研不易,资料的作用显而易见,只要经济允许,大家还是要找个信得过的 提供者。
2、买资料注意,首先,一定要和对方聊聊,看对方是什么出身,如果一个人连 地域分异规律、新仙女木事件、中心地理论、空间分析、遥感影像分辨率都不知 道是什么,那他是无法保证质量的。有时候,对方会狡辩说是找人编写的,那大 家扪心自问下,如果有人出钱让你编资料,但对方对这块也不懂,也就是说质量 上是没人把关的,你会十二分的用心吗?其次,要让对方截图,任意指定版块进 行截图,很多资料描述的都很美,但实际拿到后会大失所望。随机性的截图可以 避免这一点。
3、资料更新说明
新的年份,考研范围、考试重点和大纲都会有新的变化,针对这种变化,本中心每年都会进行一次较大内 容更新,所以本套资料仅适用于 2015 年,请大家多加关注我们!谢谢。
4、资料接受说明
收到资料后,在不拆开前提下,可自由浏览资料内容,如不满意,2 小时之内,联系我们,然后无偿退货。 但对于那些擅自拆开书钉,进行复印,而后再退货的资料贩子,我们也会坚决维护我们的权益,与之奉陪 到底!联系方式:咨询 QQ:2593665687,TEL:18012981114
克里金插值无法估算半变异函数

克里金插值无法估算半变异函数摘要:I.克里金插值简介- 克里金插值的定义- 克里金插值的应用场景II.半变异函数的重要性- 半变异函数的定义- 半变异函数在克里金插值中的作用III.克里金插值无法估算半变异函数的原因- 克里金插值算法的基本原理- 为什么克里金插值无法估算半变异函数IV.解决方案与建议- 使用其他插值方法进行半变异函数的估算- 改进克里金插值算法以适应半变异函数的估算正文:I.克里金插值简介克里金插值(Kriging Interpolation)是一种地统计学中的插值方法,主要用于空间数据的预测和插值。
它通过空间位置的权重来计算每个点的预测值,可以较好地处理数据的不确定性和空间相关性。
克里金插值在资源调查、环境监测、地理信息系统等领域有着广泛的应用。
II.半变异函数的重要性半变异函数(Half Variance Function)是地统计学中描述空间数据变异程度的一个重要概念,它反映了数据在空间位置上的变化情况。
半变异函数的估算对于分析空间数据的结构和规律具有重要意义。
在克里金插值中,半变异函数用于计算插值权重,对插值结果的精度具有重要影响。
III.克里金插值无法估算半变异函数的原因克里金插值算法基于最小二乘法,通过空间位置的权重来计算每个点的预测值。
在计算过程中,克里金插值方法需要对相邻点之间的距离进行平方处理,这使得克里金插值算法无法直接处理半变异函数。
因为半变异函数需要考虑空间位置和距离的平方,而克里金插值算法只考虑了空间位置。
IV.解决方案与建议由于克里金插值算法无法直接估算半变异函数,我们可以考虑使用其他插值方法来进行半变异函数的估算。
例如,普通克里金插值(Ordinary Kriging)和简单克里金插值(Simple Kriging)是两种常用的地统计学插值方法,可以用于半变异函数的估算。
此外,我们还可以尝试改进克里金插值算法,使之能够适应半变异函数的估算。
例如,可以考虑在克里金插值算法中引入距离的平方项,从而使克里金插值方法能够处理半变异函数。
基于多级全局信息传递模型的视觉显著性检测

2021⁃01⁃10计算机应用,Journal of Computer Applications 2021,41(1):208-214ISSN 1001⁃9081CODEN JYIIDU http ://基于多级全局信息传递模型的视觉显著性检测温静*,宋建伟(山西大学计算机与信息技术学院,太原030006)(∗通信作者电子邮箱wjing@ )摘要:对神经网络中的卷积特征采用分层处理的思想能明显提升显著目标检测的性能。
然而,在集成分层特征时,如何获得丰富的全局信息以及有效融合较高层特征空间的全局信息和底层细节信息仍是一个没有解决的问题。
为此,提出了一种基于多级全局信息传递模型的显著性检测算法。
为了提取丰富的多尺度全局信息,在较高层级引入了多尺度全局特征聚合模块(MGFAM ),并且将多层级提取出的全局信息进行特征融合操作;此外,为了同时获得高层特征空间的全局信息和丰富的底层细节信息,将提取到的有判别力的高级全局语义信息以特征传递的方式和较低层次特征进行融合。
这些操作可以最大限度提取到高级全局语义信息,同时避免了这些信息在逐步传递到较低层时产生的损失。
在ECSSD 、PASCAL -S 、SOD 、HKU -IS 等4个数据集上进行实验,实验结果表明,所提算法相较于较先进的NLDF 模型,其F -measure (F )值分别提高了0.028、0.05、0.035和0.013,平均绝对误差(MAE )分别降低了0.023、0.03、0.023和0.007。
同时,所提算法在准确率、召回率、F -measure 值及MAE 等指标上也优于几种经典的图像显著性检测方法。
关键词:显著性检测;全局信息;神经网络;信息传递;多尺度池化中图分类号:TP391.413文献标志码:AVisual saliency detection based on multi -level global information propagation modelWEN Jing *,SONG Jianwei(School of Computer and Information Technology ,Shanxi University ,Taiyuan Shanxi 030600,China )Abstract:The idea of hierarchical processing of convolution features in neural networks has a significant effect onsaliency object detection.However ,when integrating hierarchical features ,it is still an open problem how to obtain rich global information ,as well as effectively integrate the global information and of the higher -level feature space and low -leveldetail information.Therefore ,a saliency detection algorithm based on a multi -level global information propagation model was proposed.In order to extract rich multi -scale global information ,a Multi -scale Global Feature Aggregation Module(MGFAM )was introduced to the higher -level ,and feature fusion operation was performed to the global information extracted from multiple levels.In addition ,in order to obtain the global information of the high -level feature space and the rich low -level detail information at the same time ,the extracted discriminative high -level global semantic information was fused with the lower -level features by means of feature propagation.These operations were able to extract the high -level global semantic information to the greatest extent ,and avoid the loss of this information when it was gradually propagated to the lower -level.Experimental results on four datasets including ECSSD ,PASCAL -S ,SOD ,HKU -IS show that compared with the advanced NLDF (Non -Local Deep Features for salient object detection )model ,the proposed algorithm has the F -measure (F )valueincreased by 0.028、0.05、0.035and 0.013respectively ,the Mean Absolute Error (MAE )decreased by 0.023、0.03、0.023and 0.007respectively ,and the proposed algorithm was superior to several classical image saliency detection methods in terms of precision ,recall ,F -measure and MAE.Key words:saliency detection;global information;neural network;information propagation;multi -scale pooling引言视觉显著性源于认知学中的视觉注意模型,旨在模拟人类视觉系统自动检测出图片中最与众不同和吸引人眼球的目标区域。
数学建模-遗传算法(GA)

初始化种群
种群规模 基因链长度 进化代数
交叉概率 pc 变异概率 pm
适应度函数
Pc取值0.4~0.99 Pm取值0.01~0.1且Pm随 Pc取值增大而减小
选择操作
求解每个个体的适应度,从 父代与子代中选取出适应度 高的个体,再以这些选出的 个体作为父本继续进化,直 到达到迭代次数或满足算法 的收敛准则。
实战演练
我方有一个基地,经度和纬度为(70,40)。 假设我方飞机的速度为1000 公里/小时。 我方派一架飞机从基地出发,侦察完敌方所 有目标,再返回原来的基地。在敌方每一目 标点的侦察时间不计,求该架飞机所花费的 时间(假设我方飞机巡航时间可以充分长)。
交叉前
P1 (0.1 0.9 0.2 | 0.4 0.6 0.5 0.7 0.8 0.3) P2 (0.4 0.5 0.9 | 0.1 0.8 0.7 0.6 0.2 0.3)
交叉后
P1 (0.4 0.5 0.9 | 0.4 0.6 0.5 0.7 0.2 0.3) P2 (0.1 0.9 0.2 | 0.1 0.8 0.7 0.6 0.8 0.3)
有序交叉:
产生两个交叉点,让中间部分基因先复制到下 一代,从一个双亲路径的第二个划分点开始, 从另外一个双亲路径中来的城市按相同的顺序 复制。当字符串的结尾到达时,转从字符串的 开始处继续,最终得到两个子代
交叉前
P1 (1 9 2 | 4 6 5 7 | 8 3) P2 (4 5 9 | 1 8 7 6 | 2 3)
交叉操作
定义:从种群中所选择的每一对母体, 以一定的交叉概率 Pc 交换它们之间的 部分基因。
注意:交叉概率太大,适应度高的个 体很快被破坏;若太小,又影响算法 效率
人工智能之遗传算法(GA),搜索最优解的方法

人工智能之遗传算法(GA),搜索最优解的方法导读:人们一提到遗传算法(GA),就会联想到达尔文的生物进化论。
遗传算法(GA)是一类借鉴生物界的进化规律演化而来的随机化搜索方法。
今天我们重点探讨一下遗传算法(GA)。
^_^人们一提到遗传算法(GA),就会联想到达尔文的生物进化论。
遗传算法(GA)是一类借鉴生物界的进化规律演化而来的随机化搜索方法。
它是由美国的J.Holland教授1975年首先提出。
目前,遗传算法(GA)已成为进化计算研究的一个重要分支。
概念和定义:遗传算法(GeneTIcAlgorithm)是模拟达尔文生物进化论的自然选择和遗传学机理的生物进化过程的计算模型,是一种通过模拟自然进化过程搜索最优解的方法。
遗传算法(GA)是从代表问题可能潜在的解集的一个种群(populaTIon)开始,而一个种群则由经过基因(gene)编码的一定数目的个体(individual)组成。
每个个体实际上是染色体(chromosome)带有特征的实体。
染色体作为遗传物质的主要载体,即多个基因的集合,其内部表现(即基因型)是某种基因组合,它决定了个体的形状的外部表现。
因此,在一开始需要实现从表现型到基因型的映射即编码工作。
由于仿照基因编码的工作很复杂,往往进行简化,初代种群产生之后,按照适者生存和优胜劣汰的原理,逐代(generaTIon)演化产生出越来越好的近似解,在每一代,根据问题域中个体的适应度(fitness)大小选择(selecTIon)个体,并借助于自然遗传学的遗传算子(geneticoperators)进行组合交叉(crossover)和变异(mutation),产生出代表新的解集的种群。
这个过程将导致种群像自然进化一样的后生代种群比前代更加适应于环境,末代种群中的最优个体经过解码(decoding),可以作为问题近似最优解。
遗传操作是模拟生物基因遗传的做法。
在遗传算法中,通过编码组成初始群体后,遗传操作的任务就是对群体的个体按照它们对环境适应度(适应度评估)施加一定的操作,从而。
数据挖掘算法之遗传算法

数据挖掘算法之遗传算法遗传算法(GA,Genertic Algorithm)是一种基于生物进化过程中自然选择与遗传机制的模拟算法,它广泛应用于机器学习、模式识别、控制系统优化及数据挖掘等领域中,在数据挖掘中它不公可以用于聚类分析,也可用于分类分析。
遗传算法的基本流程如下图:遗传编码由问题空间向GA编码空间的映射称为编码,反之则称为解码。
遗传编码是遗传算法的基础,一般要体现两个原则:✓编码方案应与问题本身相关性大,而与其它编码方案相关性小✓编码方案应采用最小字符集,以使问题得到自然、简单的表示和描述二进制编码是最基础的编码方式,应用范围非常广泛,其它编码方式有大字符集编码、序列编码、实数编码、树编码、自适应编码、乱序编码等。
适应值函数(评价函数)是评估染色体的主要工具,其设置分为三个步骤:1.确定目标函数:遗传算法中有一个求解问题的目标,而这个目标可以用一个函数来表示,这个函数就叫目标函数。
目标函数应预先设定。
2.从目标函数到适应值函数的转换:由于目标函数的值范围不定,而适应值函数的值一般是非负数为主,以表示染色体的适应程度,因此需要建立一个由目标函数到适应值函数间的转换。
3.适应值调整:适应值函数计算出来的适应值需作适当调整,使其控制在一定数值区间内,以避免不同染色体间的适应值差距过大而引起的不一致性。
遗传算子遗传算法利用遗传算子产生新一代群体来实现群体进化,算子的设计是遗传策略的主要组成部分,也是调整和控制进化过程的基本工具。
1.选择:按照某种策略从父代种群中选择一些染色体(不作任何改动)进入下一代种群,常用的选择算法有适应值比例选择、Boltzmann选择、排序选择、联赛选择、精英选择、稳态选择等。
2.交叉:随机从种群中抽取两个染色体,根据染色体位串长度L,随机选取[1, L-1]中的一个或多个的整数k作为交叉位置,然后根据交叉概率p c,实施交叉操作,即两个染色体在交叉位置处,相互交换各自的部分内容,从而形成新的一对染色体。
Eigenvalues of a real supersymmetric tensor
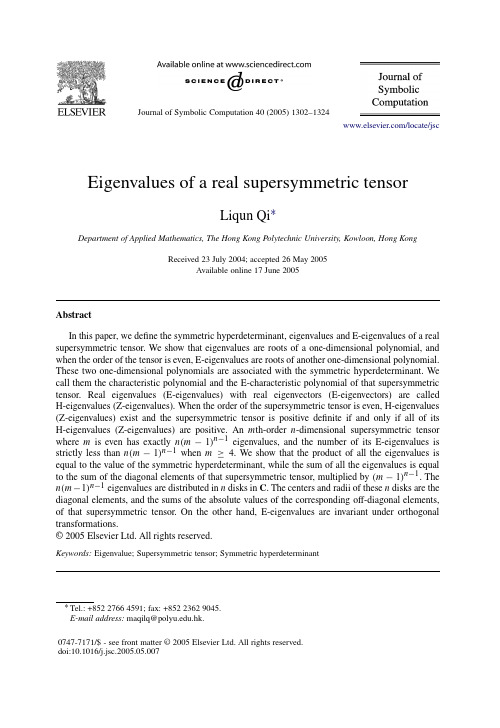
Abstract In this paper, we define the symmetric hyperdeterminant, eigenvalues and E-eigenvalues of a real supersymmetric tensor. We show that eigenvalues are roots of a one-dimensional polynomial, and when the order of the tensor is even, E-eigenvalues are roots of another one-dimensional polynomial. These two one-dimensional polynomials are associated with the symmetric hyperdeterminant. We call them the characteristic polynomial and the E-characteristic polynomial of that supersymmetric tensor. Real eigenvalues (E-eigenvalues) with real eigenvectors (E-eigenvectors) are called H-eigenvalues (Z-eigenvalues). When the order of the supersymmetric tensor is even, H-eigenvalues (Z-eigenvalues) exist and the supersymmetric tensor is positive definite if and only if all of its H-eigenvalues (Z-eigenvalues) are positive. An m th-order n -dimensional supersymmetric tensor where m is even has exactly n (m − 1)n −1 eigenvalues, and the number of its E-eigenvalues is strictly less than n (m − 1)n −1 when m ≥ 4. We show that the product of all the eigenvalues is equal to the value of the symmetric hyperdeterminant, while the sum of all the eigenvalues is equal to the sum of the diagonal elements of that supersymmetric tensor, multiplied by (m − 1)n −1 . The n (m − 1)n −1 eigenvalues are distributed in n disks in C. The centers and radii of these n disks are the diagonal elements, and the sums of the absolute values of the corresponding off-diagonal elements, of that supersymmetric tensor. On the other hand, E-eigenvalues are invariant under orthogonal transformations. © 2005 Elsevier Ltd. All rights reserved.
遗传算法选取最优参数MATLAB程序

遗传算法选取最优参数MATLAB程序复制代码在这里使用启发式算法GA(遗传算法)来进行参数寻优,用网格划分(grid search)来寻找最佳的参数c和g,虽然采用网格搜索能够找到在CV意义下的最高的分类准确率,即全局最优解,但有时候如果想在更大的范围内寻找最佳的参数c和g会很费时,采用启发式算法就可以不必遍历网格内的所有的参数点,也能找到全局最优解。
关于遗传算法这里不打算过多介绍,想要学习的朋友可以自己查看相关资料。
使用GA来进行参数寻优在在libsvm-mat-2.89-3[FarutoUltimate3.0]工具箱中已经实现gaSVMcgForClass.m(分类问题参数寻优)、gaSVMcgForRegress.m(回归问题参数寻优)。
1.2. 3. 4. 5. 6. 7.利用GA参数寻优函数(分类问题):gaSVMcgForClass[bestCVaccuracy,bestc,bestg,ga_option]=gaSVMcgForClass(train_label,train,ga_option) 输入:train_label:训练集的标签,格式要求与svmtrain相同。
train:训练集,格式要求与svmtrain相同。
ga_option:GA中的一些参数设置,可不输入,有默认值,详细请看代码的帮助说明。
8. 输出:9. bestCVaccuracy:最终CV意义下的最佳分类准确率。
10. bestc:最佳的参数c。
11. bestg:最佳的参数g。
12. ga_option:记录GA中的一些参数。
13. ========================================================== 14. 利用GA 参数寻优函数(回归问题):gaSVMcgForRegress 15.[bestCVmse,bestc,bestg,ga_option]=16. gaSVMcgForRegress(train_label,train,ga_option) 17. 其输入输出与gaSVMcgForClass类似,这里不再赘述。
高斯分布moment generation function

高斯分布Moment Generating Function高斯分布(Gaussian distribution)是统计学中常见的一种概率分布,也被称为正态分布(normal distribution)。
它在自然界和社会现象中广泛出现,并且在实际生活中有着重要的应用。
高斯分布的研究对于理解数据集的分布、参数估计以及推断假设非常重要。
在统计学中,矩(moment)是描述概率分布的基本工具之一。
矩生成函数(moment generating function)是一种用来描述随机变量的矩的函数,在应用中经常被用来推导随机变量的矩,特别是求解方差和协方差等重要统计量。
在高斯分布的场景下,矩生成函数被称为高斯分布的矩生成函数。
高斯分布高斯分布是一种连续的概率分布,其特点是形成一个钟形曲线。
高斯分布的概率密度函数(probability density function,PDF)可以通过以下公式表示:[ f(x) = e^{-} ]其中,μ是均值,σ是标准差。
高斯分布的均值决定了曲线的位置,而标准差则决定了曲线的形状。
均值为μ的高斯分布将其峰值定位在μ处,标准差越大,曲线越平缓。
高斯分布在自然界和社会现象中的广泛存在具有重要的实际应用价值。
例如,在金融领域,股票价格的变化通常被假设为高斯分布,基于高斯分布的统计方法可以帮助投资者进行风险评估和投资决策。
矩生成函数矩生成函数是随机变量的矩的生成函数,对于随机变量X,其矩生成函数被定义为:[ M_X(t) = E(e^{tx}) = _{-}{}e{tx}f(x)dx ]其中,E(⋅)表示期望值运算符,f(x)是随机变量X的概率密度函数。
通过矩生成函数,我们可以推导出随机变量的矩,特别是可以求解高斯分布的方差和协方差等重要统计量。
对于高斯分布,其矩生成函数可以通过以下公式计算:[ M_X(t) = e^{t+ t^2 ^2} ]注意到,高斯分布的矩生成函数具有非常简洁的形式,这使得求解高斯分布的矩成为相对简单的任务。
机器人自主导航与定位技术测试考核试卷

3.请详细说明视觉SLAM中的特征提取、特征匹配和运动估计三个关键步骤的作用及其相互关系。()
4.在机器人路径规划中,解释A*算法和RRT(Rapidly-exploring Random Trees)算法的基本思想,并比较它们的优缺点。()
三、填空题(本题共10小题,每小题2分,共20分,请将正确答案填到题目空白处)
1.在机器人自主导航中,______是一种通过传感器数据来同时完成地图构建和定位的技术。()
2.机器人导航中的______算法是一种基于启发式的搜索算法,用于寻找从起点到目标点的最优路径。()
3.在视觉SLAM中,______是一种常用的前端处理技术,用于提取图像中的特征点。()
8. AB
9. ABC
10. ABCD
11. AB
12. ABCD
13. ABC
14. ABC
15. ABCD
16. ABC
17. ABC
18. ABCD
19. ABC
20. ABC
三、填空题
1. SLAM
2. A*算法
3.特征提取
4.避障算法
5.粒子滤波器
6.信标定位
7. IMU(惯性测量单元)
8.路径跟踪控制
A.速度控制
B.方向控制
C.轨迹跟踪
D.动态避障
19.以下哪些方法可以用于机器人的地形感知?()
A.激光雷达
B.摄像头
C.触觉传感器
D.红外传感器
20.以下哪些技术可以用于提高机器人定位的实时性?()
A.并行计算
B.硬件加速
C.算法优化
ACM-GIS%202006-A%20Peer-to-Peer%20Spatial%20Cloaking%20Algorithm%20for%20Anonymous%20Location-based%

A Peer-to-Peer Spatial Cloaking Algorithm for AnonymousLocation-based Services∗Chi-Yin Chow Department of Computer Science and Engineering University of Minnesota Minneapolis,MN cchow@ Mohamed F.MokbelDepartment of ComputerScience and EngineeringUniversity of MinnesotaMinneapolis,MNmokbel@Xuan LiuIBM Thomas J.WatsonResearch CenterHawthorne,NYxuanliu@ABSTRACTThis paper tackles a major privacy threat in current location-based services where users have to report their ex-act locations to the database server in order to obtain their desired services.For example,a mobile user asking about her nearest restaurant has to report her exact location.With untrusted service providers,reporting private location in-formation may lead to several privacy threats.In this pa-per,we present a peer-to-peer(P2P)spatial cloaking algo-rithm in which mobile and stationary users can entertain location-based services without revealing their exact loca-tion information.The main idea is that before requesting any location-based service,the mobile user will form a group from her peers via single-hop communication and/or multi-hop routing.Then,the spatial cloaked area is computed as the region that covers the entire group of peers.Two modes of operations are supported within the proposed P2P spa-tial cloaking algorithm,namely,the on-demand mode and the proactive mode.Experimental results show that the P2P spatial cloaking algorithm operated in the on-demand mode has lower communication cost and better quality of services than the proactive mode,but the on-demand incurs longer response time.Categories and Subject Descriptors:H.2.8[Database Applications]:Spatial databases and GISGeneral Terms:Algorithms and Experimentation. Keywords:Mobile computing,location-based services,lo-cation privacy and spatial cloaking.1.INTRODUCTIONThe emergence of state-of-the-art location-detection de-vices,e.g.,cellular phones,global positioning system(GPS) devices,and radio-frequency identification(RFID)chips re-sults in a location-dependent information access paradigm,∗This work is supported in part by the Grants-in-Aid of Re-search,Artistry,and Scholarship,University of Minnesota. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.ACM-GIS’06,November10-11,2006,Arlington,Virginia,USA. Copyright2006ACM1-59593-529-0/06/0011...$5.00.known as location-based services(LBS)[30].In LBS,mobile users have the ability to issue location-based queries to the location-based database server.Examples of such queries include“where is my nearest gas station”,“what are the restaurants within one mile of my location”,and“what is the traffic condition within ten minutes of my route”.To get the precise answer of these queries,the user has to pro-vide her exact location information to the database server. With untrustworthy servers,adversaries may access sensi-tive information about specific individuals based on their location information and issued queries.For example,an adversary may check a user’s habit and interest by knowing the places she visits and the time of each visit,or someone can track the locations of his ex-friends.In fact,in many cases,GPS devices have been used in stalking personal lo-cations[12,39].To tackle this major privacy concern,three centralized privacy-preserving frameworks are proposed for LBS[13,14,31],in which a trusted third party is used as a middleware to blur user locations into spatial regions to achieve k-anonymity,i.e.,a user is indistinguishable among other k−1users.The centralized privacy-preserving frame-work possesses the following shortcomings:1)The central-ized trusted third party could be the system bottleneck or single point of failure.2)Since the centralized third party has the complete knowledge of the location information and queries of all users,it may pose a serious privacy threat when the third party is attacked by adversaries.In this paper,we propose a peer-to-peer(P2P)spatial cloaking algorithm.Mobile users adopting the P2P spatial cloaking algorithm can protect their privacy without seeking help from any centralized third party.Other than the short-comings of the centralized approach,our work is also moti-vated by the following facts:1)The computation power and storage capacity of most mobile devices have been improv-ing at a fast pace.2)P2P communication technologies,such as IEEE802.11and Bluetooth,have been widely deployed.3)Many new applications based on P2P information shar-ing have rapidly taken shape,e.g.,cooperative information access[9,32]and P2P spatio-temporal query processing[20, 24].Figure1gives an illustrative example of P2P spatial cloak-ing.The mobile user A wants tofind her nearest gas station while beingfive anonymous,i.e.,the user is indistinguish-able amongfive users.Thus,the mobile user A has to look around andfind other four peers to collaborate as a group. In this example,the four peers are B,C,D,and E.Then, the mobile user A cloaks her exact location into a spatialA B CDEBase Stationregion that covers the entire group of mobile users A ,B ,C ,D ,and E .The mobile user A randomly selects one of the mobile users within the group as an agent .In the ex-ample given in Figure 1,the mobile user D is selected as an agent.Then,the mobile user A sends her query (i.e.,what is the nearest gas station)along with her cloaked spa-tial region to the agent.The agent forwards the query to the location-based database server through a base station.Since the location-based database server processes the query based on the cloaked spatial region,it can only give a list of candidate answers that includes the actual answers and some false positives.After the agent receives the candidate answers,it forwards the candidate answers to the mobile user A .Finally,the mobile user A gets the actual answer by filtering out all the false positives.The proposed P2P spatial cloaking algorithm can operate in two modes:on-demand and proactive .In the on-demand mode,mobile clients execute the cloaking algorithm when they need to access information from the location-based database server.On the other side,in the proactive mode,mobile clients periodically look around to find the desired number of peers.Thus,they can cloak their exact locations into spatial regions whenever they want to retrieve informa-tion from the location-based database server.In general,the contributions of this paper can be summarized as follows:1.We introduce a distributed system architecture for pro-viding anonymous location-based services (LBS)for mobile users.2.We propose the first P2P spatial cloaking algorithm for mobile users to entertain high quality location-based services without compromising their privacy.3.We provide experimental evidence that our proposed algorithm is efficient in terms of the response time,is scalable to large numbers of mobile clients,and is effective as it provides high-quality services for mobile clients without the need of exact location information.The rest of this paper is organized as follows.Section 2highlights the related work.The system model of the P2P spatial cloaking algorithm is presented in Section 3.The P2P spatial cloaking algorithm is described in Section 4.Section 5discusses the integration of the P2P spatial cloak-ing algorithm with privacy-aware location-based database servers.Section 6depicts the experimental evaluation of the P2P spatial cloaking algorithm.Finally,Section 7con-cludes this paper.2.RELATED WORKThe k -anonymity model [37,38]has been widely used in maintaining privacy in databases [5,26,27,28].The main idea is to have each tuple in the table as k -anonymous,i.e.,indistinguishable among other k −1tuples.Although we aim for the similar k -anonymity model for the P2P spatial cloaking algorithm,none of these techniques can be applied to protect user privacy for LBS,mainly for the following four reasons:1)These techniques preserve the privacy of the stored data.In our model,we aim not to store the data at all.Instead,we store perturbed versions of the data.Thus,data privacy is managed before storing the data.2)These approaches protect the data not the queries.In anonymous LBS,we aim to protect the user who issues the query to the location-based database server.For example,a mobile user who wants to ask about her nearest gas station needs to pro-tect her location while the location information of the gas station is not protected.3)These approaches guarantee the k -anonymity for a snapshot of the database.In LBS,the user location is continuously changing.Such dynamic be-havior calls for continuous maintenance of the k -anonymity model.(4)These approaches assume a unified k -anonymity requirement for all the stored records.In our P2P spatial cloaking algorithm,k -anonymity is a user-specified privacy requirement which may have a different value for each user.Motivated by the privacy threats of location-detection de-vices [1,4,6,40],several research efforts are dedicated to protect the locations of mobile users (e.g.,false dummies [23],landmark objects [18],and location perturbation [10,13,14]).The most closed approaches to ours are two centralized spatial cloaking algorithms,namely,the spatio-temporal cloaking [14]and the CliqueCloak algorithm [13],and one decentralized privacy-preserving algorithm [23].The spatio-temporal cloaking algorithm [14]assumes that all users have the same k -anonymity requirements.Furthermore,it lacks the scalability because it deals with each single request of each user individually.The CliqueCloak algorithm [13]as-sumes a different k -anonymity requirement for each user.However,since it has large computation overhead,it is lim-ited to a small k -anonymity requirement,i.e.,k is from 5to 10.A decentralized privacy-preserving algorithm is proposed for LBS [23].The main idea is that the mobile client sends a set of false locations,called dummies ,along with its true location to the location-based database server.However,the disadvantages of using dummies are threefold.First,the user has to generate realistic dummies to pre-vent the adversary from guessing its true location.Second,the location-based database server wastes a lot of resources to process the dummies.Finally,the adversary may esti-mate the user location by using cellular positioning tech-niques [34],e.g.,the time-of-arrival (TOA),the time differ-ence of arrival (TDOA)and the direction of arrival (DOA).Although several existing distributed group formation al-gorithms can be used to find peers in a mobile environment,they are not designed for privacy preserving in LBS.Some algorithms are limited to only finding the neighboring peers,e.g.,lowest-ID [11],largest-connectivity (degree)[33]and mobility-based clustering algorithms [2,25].When a mo-bile user with a strict privacy requirement,i.e.,the value of k −1is larger than the number of neighboring peers,it has to enlist other peers for help via multi-hop routing.Other algorithms do not have this limitation,but they are designed for grouping stable mobile clients together to facil-Location-based Database ServerDatabase ServerDatabase ServerFigure 2:The system architectureitate efficient data replica allocation,e.g.,dynamic connec-tivity based group algorithm [16]and mobility-based clus-tering algorithm,called DRAM [19].Our work is different from these approaches in that we propose a P2P spatial cloaking algorithm that is dedicated for mobile users to dis-cover other k −1peers via single-hop communication and/or via multi-hop routing,in order to preserve user privacy in LBS.3.SYSTEM MODELFigure 2depicts the system architecture for the pro-posed P2P spatial cloaking algorithm which contains two main components:mobile clients and location-based data-base server .Each mobile client has its own privacy profile that specifies its desired level of privacy.A privacy profile includes two parameters,k and A min ,k indicates that the user wants to be k -anonymous,i.e.,indistinguishable among k users,while A min specifies the minimum resolution of the cloaked spatial region.The larger the value of k and A min ,the more strict privacy requirements a user needs.Mobile users have the ability to change their privacy profile at any time.Our employed privacy profile matches the privacy re-quirements of mobiles users as depicted by several social science studies (e.g.,see [4,15,17,22,29]).In this architecture,each mobile user is equipped with two wireless network interface cards;one of them is dedicated to communicate with the location-based database server through the base station,while the other one is devoted to the communication with other peers.A similar multi-interface technique has been used to implement IP multi-homing for stream control transmission protocol (SCTP),in which a machine is installed with multiple network in-terface cards,and each assigned a different IP address [36].Similarly,in mobile P2P cooperation environment,mobile users have a network connection to access information from the server,e.g.,through a wireless modem or a base station,and the mobile users also have the ability to communicate with other peers via a wireless LAN,e.g.,IEEE 802.11or Bluetooth [9,24,32].Furthermore,each mobile client is equipped with a positioning device, e.g.,GPS or sensor-based local positioning systems,to determine its current lo-cation information.4.P2P SPATIAL CLOAKINGIn this section,we present the data structure and the P2P spatial cloaking algorithm.Then,we describe two operation modes of the algorithm:on-demand and proactive .4.1Data StructureThe entire system area is divided into grid.The mobile client communicates with each other to discover other k −1peers,in order to achieve the k -anonymity requirement.TheAlgorithm 1P2P Spatial Cloaking:Request Originator m 1:Function P2PCloaking-Originator (h ,k )2://Phase 1:Peer searching phase 3:The hop distance h is set to h4:The set of discovered peers T is set to {∅},and the number ofdiscovered peers k =|T |=05:while k <k −1do6:Broadcast a FORM GROUP request with the parameter h (Al-gorithm 2gives the response of each peer p that receives this request)7:T is the set of peers that respond back to m by executingAlgorithm 28:k =|T |;9:if k <k −1then 10:if T =T then 11:Suspend the request 12:end if 13:h ←h +1;14:T ←T ;15:end if 16:end while17://Phase 2:Location adjustment phase 18:for all T i ∈T do19:|mT i .p |←the greatest possible distance between m and T i .pby considering the timestamp of T i .p ’s reply and maximum speed20:end for21://Phase 3:Spatial cloaking phase22:Form a group with k −1peers having the smallest |mp |23:h ←the largest hop distance h p of the selected k −1peers 24:Determine a grid area A that covers the entire group 25:if A <A min then26:Extend the area of A till it covers A min 27:end if28:Randomly select a mobile client of the group as an agent 29:Forward the query and A to the agentmobile client can thus blur its exact location into a cloaked spatial region that is the minimum grid area covering the k −1peers and itself,and satisfies A min as well.The grid area is represented by the ID of the left-bottom and right-top cells,i.e.,(l,b )and (r,t ).In addition,each mobile client maintains a parameter h that is the required hop distance of the last peer searching.The initial value of h is equal to one.4.2AlgorithmFigure 3gives a running example for the P2P spatial cloaking algorithm.There are 15mobile clients,m 1to m 15,represented as solid circles.m 8is the request originator,other black circles represent the mobile clients received the request from m 8.The dotted circles represent the commu-nication range of the mobile client,and the arrow represents the movement direction.Algorithms 1and 2give the pseudo code for the request originator (denoted as m )and the re-quest receivers (denoted as p ),respectively.In general,the algorithm consists of the following three phases:Phase 1:Peer searching phase .The request origina-tor m wants to retrieve information from the location-based database server.m first sets h to h ,a set of discovered peers T to {∅}and the number of discovered peers k to zero,i.e.,|T |.(Lines 3to 4in Algorithm 1).Then,m broadcasts a FORM GROUP request along with a message sequence ID and the hop distance h to its neighboring peers (Line 6in Algorithm 1).m listens to the network and waits for the reply from its neighboring peers.Algorithm 2describes how a peer p responds to the FORM GROUP request along with a hop distance h and aFigure3:P2P spatial cloaking algorithm.Algorithm2P2P Spatial Cloaking:Request Receiver p1:Function P2PCloaking-Receiver(h)2://Let r be the request forwarder3:if the request is duplicate then4:Reply r with an ACK message5:return;6:end if7:h p←1;8:if h=1then9:Send the tuple T=<p,(x p,y p),v maxp ,t p,h p>to r10:else11:h←h−1;12:Broadcast a FORM GROUP request with the parameter h 13:T p is the set of peers that respond back to p14:for all T i∈T p do15:T i.h p←T i.h p+1;16:end for17:T p←T p∪{<p,(x p,y p),v maxp ,t p,h p>};18:Send T p back to r19:end ifmessage sequence ID from another peer(denoted as r)that is either the request originator or the forwarder of the re-quest.First,p checks if it is a duplicate request based on the message sequence ID.If it is a duplicate request,it sim-ply replies r with an ACK message without processing the request.Otherwise,p processes the request based on the value of h:Case1:h= 1.p turns in a tuple that contains its ID,current location,maximum movement speed,a timestamp and a hop distance(it is set to one),i.e.,< p,(x p,y p),v max p,t p,h p>,to r(Line9in Algorithm2). Case2:h> 1.p decrements h and broadcasts the FORM GROUP request with the updated h and the origi-nal message sequence ID to its neighboring peers.p keeps listening to the network,until it collects the replies from all its neighboring peers.After that,p increments the h p of each collected tuple,and then it appends its own tuple to the collected tuples T p.Finally,it sends T p back to r (Lines11to18in Algorithm2).After m collects the tuples T from its neighboring peers, if m cannotfind other k−1peers with a hop distance of h,it increments h and re-broadcasts the FORM GROUP request along with a new message sequence ID and h.m repeatedly increments h till itfinds other k−1peers(Lines6to14in Algorithm1).However,if mfinds the same set of peers in two consecutive broadcasts,i.e.,with hop distances h and h+1,there are not enough connected peers for m.Thus, m has to relax its privacy profile,i.e.,use a smaller value of k,or to be suspended for a period of time(Line11in Algorithm1).Figures3(a)and3(b)depict single-hop and multi-hop peer searching in our running example,respectively.In Fig-ure3(a),the request originator,m8,(e.g.,k=5)canfind k−1peers via single-hop communication,so m8sets h=1. Since h=1,its neighboring peers,m5,m6,m7,m9,m10, and m11,will not further broadcast the FORM GROUP re-quest.On the other hand,in Figure3(b),m8does not connect to k−1peers directly,so it has to set h>1.Thus, its neighboring peers,m7,m10,and m11,will broadcast the FORM GROUP request along with a decremented hop dis-tance,i.e.,h=h−1,and the original message sequence ID to their neighboring peers.Phase2:Location adjustment phase.Since the peer keeps moving,we have to capture the movement between the time when the peer sends its tuple and the current time. For each received tuple from a peer p,the request originator, m,determines the greatest possible distance between them by an equation,|mp |=|mp|+(t c−t p)×v max p,where |mp|is the Euclidean distance between m and p at time t p,i.e.,|mp|=(x m−x p)2+(y m−y p)2,t c is the currenttime,t p is the timestamp of the tuple and v maxpis the maximum speed of p(Lines18to20in Algorithm1).In this paper,a conservative approach is used to determine the distance,because we assume that the peer will move with the maximum speed in any direction.If p gives its movement direction,m has the ability to determine a more precise distance between them.Figure3(c)illustrates that,for each discovered peer,the circle represents the largest region where the peer can lo-cate at time t c.The greatest possible distance between the request originator m8and its discovered peer,m5,m6,m7, m9,m10,or m11is represented by a dotted line.For exam-ple,the distance of the line m8m 11is the greatest possible distance between m8and m11at time t c,i.e.,|m8m 11|. Phase3:Spatial cloaking phase.In this phase,the request originator,m,forms a virtual group with the k−1 nearest peers,based on the greatest possible distance be-tween them(Line22in Algorithm1).To adapt to the dynamic network topology and k-anonymity requirement, m sets h to the largest value of h p of the selected k−1 peers(Line15in Algorithm1).Then,m determines the minimum grid area A covering the entire group(Line24in Algorithm1).If the area of A is less than A min,m extends A,until it satisfies A min(Lines25to27in Algorithm1). Figure3(c)gives the k−1nearest peers,m6,m7,m10,and m11to the request originator,m8.For example,the privacy profile of m8is(k=5,A min=20cells),and the required cloaked spatial region of m8is represented by a bold rectan-gle,as depicted in Figure3(d).To issue the query to the location-based database server anonymously,m randomly selects a mobile client in the group as an agent(Line28in Algorithm1).Then,m sendsthe query along with the cloaked spatial region,i.e.,A,to the agent(Line29in Algorithm1).The agent forwards thequery to the location-based database server.After the serverprocesses the query with respect to the cloaked spatial re-gion,it sends a list of candidate answers back to the agent.The agent forwards the candidate answer to m,and then mfilters out the false positives from the candidate answers. 4.3Modes of OperationsThe P2P spatial cloaking algorithm can operate in twomodes,on-demand and proactive.The on-demand mode:The mobile client only executesthe algorithm when it needs to retrieve information from the location-based database server.The algorithm operatedin the on-demand mode generally incurs less communica-tion overhead than the proactive mode,because the mobileclient only executes the algorithm when necessary.However,it suffers from a longer response time than the algorithm op-erated in the proactive mode.The proactive mode:The mobile client adopting theproactive mode periodically executes the algorithm in back-ground.The mobile client can cloak its location into a spa-tial region immediately,once it wants to communicate withthe location-based database server.The proactive mode pro-vides a better response time than the on-demand mode,but it generally incurs higher communication overhead and giveslower quality of service than the on-demand mode.5.ANONYMOUS LOCATION-BASEDSERVICESHaving the spatial cloaked region as an output form Algo-rithm1,the mobile user m sends her request to the location-based server through an agent p that is randomly selected.Existing location-based database servers can support onlyexact point locations rather than cloaked regions.In or-der to be able to work with a spatial region,location-basedservers need to be equipped with a privacy-aware queryprocessor(e.g.,see[29,31]).The main idea of the privacy-aware query processor is to return a list of candidate answerrather than the exact query answer.Then,the mobile user m willfilter the candidate list to eliminate its false positives andfind its exact answer.The tighter the spatial cloaked re-gion,the lower is the size of the candidate answer,and hencethe better is the performance of the privacy-aware query processor.However,tight cloaked regions may represent re-laxed privacy constrained.Thus,a trade-offbetween the user privacy and the quality of service can be achieved[31]. Figure4(a)depicts such scenario by showing the data stored at the server side.There are32target objects,i.e., gas stations,T1to T32represented as black circles,the shaded area represents the spatial cloaked area of the mo-bile client who issued the query.For clarification,the actual mobile client location is plotted in Figure4(a)as a black square inside the cloaked area.However,such information is neither stored at the server side nor revealed to the server. The privacy-aware query processor determines a range that includes all target objects that are possibly contributing to the answer given that the actual location of the mobile client could be anywhere within the shaded area.The range is rep-resented as a bold rectangle,as depicted in Figure4(b).The server sends a list of candidate answers,i.e.,T8,T12,T13, T16,T17,T21,and T22,back to the agent.The agent next for-(a)Server Side(b)Client SideFigure4:Anonymous location-based services wards the candidate answers to the requesting mobile client either through single-hop communication or through multi-hop routing.Finally,the mobile client can get the actualanswer,i.e.,T13,byfiltering out the false positives from thecandidate answers.The algorithmic details of the privacy-aware query proces-sor is beyond the scope of this paper.Interested readers are referred to[31]for more details.6.EXPERIMENTAL RESULTSIn this section,we evaluate and compare the scalabilityand efficiency of the P2P spatial cloaking algorithm in boththe on-demand and proactive modes with respect to the av-erage response time per query,the average number of mes-sages per query,and the size of the returned candidate an-swers from the location-based database server.The queryresponse time in the on-demand mode is defined as the timeelapsed between a mobile client starting to search k−1peersand receiving the candidate answers from the agent.On theother hand,the query response time in the proactive mode is defined as the time elapsed between a mobile client startingto forward its query along with the cloaked spatial regionto the agent and receiving the candidate answers from theagent.The simulation model is implemented in C++usingCSIM[35].In all the experiments in this section,we consider an in-dividual random walk model that is based on“random way-point”model[7,8].At the beginning,the mobile clientsare randomly distributed in a spatial space of1,000×1,000square meters,in which a uniform grid structure of100×100cells is constructed.Each mobile client randomly chooses itsown destination in the space with a randomly determined speed s from a uniform distribution U(v min,v max).When the mobile client reaches the destination,it comes to a stand-still for one second to determine its next destination.Afterthat,the mobile client moves towards its new destinationwith another speed.All the mobile clients repeat this move-ment behavior during the simulation.The time interval be-tween two consecutive queries generated by a mobile client follows an exponential distribution with a mean of ten sec-onds.All the experiments consider one half-duplex wirelesschannel for a mobile client to communicate with its peers with a total bandwidth of2Mbps and a transmission range of250meters.When a mobile client wants to communicate with other peers or the location-based database server,it has to wait if the requested channel is busy.In the simulated mobile environment,there is a centralized location-based database server,and one wireless communication channel between the location-based database server and the mobile。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
|f (x)|s p | dx |,
s ∈ C,
where Re(s) > 0, and | dx | denotes the Haar measure on Qn p so normalized that Zn has measure 1. The following relation between Z ( s, f ) and H (t, f ) holds (seALINDO
[14], theorem 8.2.2): H (t, f ) = 1 − tZ (s, f ) , t = p −s . 1−t
Thus, the rationality of Z (s, f ) implies the rationality of the Poincar´ e series H (t, f ), and the computation of H (t, f ) is equivalent to the computation of Z (s, f ). Igusa [14, theorem 8.2.1] showed that the local zeta function Z (s, f ) admits a meromorphic continuation to the complex plane as a rational function of p−s . The first result of this paper is a polynomial time algorithm for computing the local zeta function Z (s, f ) attached to a polynomial f (x) ∈ Z[x], in one variable, with splitting field Q, and a prime number p. We also give an explicit estimate for its complexity (see algorithm Compute Z (s, f ) in section 2, and theorem 7.1). Many authors have found explicit formulas for Z (s, f ), or H (f, t), for several classes of polynomials, among them [6], [7], [10], [11], [[16] and the references therein], [19], [24], [25]. In all these works the computation of Z (s, f ), or H (f, t), is reduced to the computation of other problems, as the computation of the number of solutions of polynomial equations with coefficients in a finite field. Currently, there is no polynomial time algorithm solving this problem [23], [22]. Moreover, none of the above mentioned works include complexity estimates for the computation of Igusa’s local zeta functions. Of particular importance is Denef’s explicit formula for Z (s, f ), when f satisfies some generic conditions [6]. This formula involves the numerical data associated to a resolution of singularities of the divisor f = 0, and the number of rational points of certain non-singular varieties over finite fields. Thus the computation of Z (s, f ), for a generic polynomial f , is reduced to the computation of the numerical data associated to a resolution of singularities of the divisor f = 0, and the number of solutions of non-singular polynomials over finite fields. Currently, it is unknown if these problems can be solved in polynomial time on a Turing machine. However, during the last few years important achievements have been obtained in the computation of resolution of singularities of polynomials [2], [3], [4], [21]. The computation of the Igusa local zeta function for an arbitrary polynomial seems to be an intractable problem on a Turing machine. For example, for p = 2, the computation of the number of solutions of a polynomial equation with coefficients in Z/2Z is an NP−complete problem on a Turing Machine [9, page 251, problem AN9]. Then in the case of 2−adic numbers, the computation of the Igusa local zeta function is an NP−complete problem. Recently, Anshel and Goldfeld have shown the existence of a strong connection between the computation of zeta functions and cryptography [1]. Indeed, they proposed a new class of candidates for one-way functions based on global zeta functions. A one-way function is a function F such that for each x in the domain of F , it is easy to compute F (x); but for essentially all y in the range of F , it is an intractable problem to find an x such that y = F (x). These functions play a central role, from a practical and theoretical point of view, in modern cryptography. Currently, there is no guarantee that one-way functions exist even if P = NP. Most of the present candidates for one-way functions are constructed on the intractability of problems like integer factorization and discrete logarithms [12]. Recently, P. Shor has introduced a new approach to attack these problems [20]. Indeed, Shor have shown that on a quantum computer the integer factorization and discrete logarithm problems can be computed in polynomial time.
∞
H (t, f ) =
m=0
Nm (f )(p−n t)m ,
with t ∈ C, | t |< 1, and N0 (f ) = 1. This paper is dedicated to the computation of the sequence {Nm (f )}m≧0 when f is an univariate polynomial with splitting field Q. Igusa showed that the Poincar´ e series H (t, f ) admits a meromorphic continuation to the complex plane as a rational function of t [14], [15]. In this paper we make a first step towards the solution of the following problem: given a polynomial f (x) as above, how difficult is to compute the meromorphic continuation of the Poincar´ e series H (t, f )? The computation of the Poincar´ e series H (t, f ) is equivalent to the computation of Igusa’s local zeta function Z (s, f ), attached to f and p, defined as follows. We denote by Qp the field of p−adic numbers, and by Zp the ring of p−adic integers. For x ∈ Qp , vp (x) denotes the p−adic order of x, and |x|p = p−vp (x) its absolute value. The Igusa local zeta function associated to f and p is defined as follows: Z (s, f ) =
