License protection with a tamper-resistant token
License无法启动解决方法

License⽆法启动解决⽅法Licenses⽆法启动解决⽅法如今,许多⽹络使⽤增强安全性的防⽕墙抵御外部侵袭。
由于许可管理器使⽤TCP/IP 协议,因此应⽤此类防⽕墙可导致许可管理器服务器和与其相连的客户端之间出现问题。
问题通常是由于防⽕墙关闭或阻⽌访问许可管理器通信所⽤端⼝导致的。
默认情况下,如果端⼝27000 可⽤,lmgrd后台程序将在该端⼝启动,否则将在27000–27009 范围内的下⼀开放端⼝启动。
⽂件中第⼆⾏的ARCGIS 后台程序不局限于特定端⼝范围。
该端⼝是动态的,这意味着它可以侦听任何可⽤端⼝。
要保护许可管理环境并允许应⽤防⽕墙,可将ARCGIS 后台程序锁定到特定端⼝。
此外,也可将lmgrd后台程序从默认的27000 更改为介于27000 和27009 之间的其他端⼝。
由于此范围的流量低,所以可以预先指定该范围供许可管理器使⽤。
步骤提供的步骤需要您短暂地停⽌许可管理器。
停⽌期间,与许可管理器的连接可能会丢失。
1. 单击―开始‖>―程序‖> ArcGIS >―许可管理器‖>―许可服务器管理器‖。
2. 在内容列表中选择―启动/停⽌许可服务器‖,然后单击―停⽌‖。
3. 打开Windows 资源管理器并导航到许可管理器安装位置(默认情况下为C:\Program Files (x86)\ArcGIS\License10.0\bin),在该位置您会看到service.txt ⽂件。
4. 该⽂件应与下图类似:SERVER this_host ANY VENDOR ARCGIS FEATURE ACT ARCGIS 1 permanent 1 7ED49106D630注:在第⼀⾏末尾,可以选择直接在ANY 后指定⼀个端⼝号。
在VENDOR ⾏,添加PORT=####,其中#### 是您指定的特定端⼝号,⽤于将供应商后台程序锁定到特定端⼝,如1234。
进⾏更改后,您的service.txt ⽂件应包含类似下列内容:SERVER this_host ANY 27000VENDOR ARCGIS PORT=1234 FEATURE ACT ARCGIS 1 permanent 1 7ED49106D6301. 保存 .txt ⽂件。
Klocwork培训手册K9.1

4.2 命令行分析 ........................................................................................................................... 11 4.3 KMC 分析步骤.......................................................................................................................12 4.4 TORNADO 程序分析 .................................................................................................................14
热源产品参考指南说明书

THERMAL PRODUCTSProduct Range Guidetechnical support.Table of ContentsTemperature Probes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3RTD Sensors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4-5Thermistors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6-7Precision Thermostats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8-9High Reliability Thermostats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10-11Commercial Thermostats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12-13Flexible Heaters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14-15Humidity Sensors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16-192 sensing .honeywell .com3SeriesLTPR300ES110Featuresprobes have durable, closed-tip designand accuracy; stainless steel constructiondesign, brass encapsulationSeriesES1205006655Temp. sensing type immersion air-gas/immersion-liquid level/air/surfaceFeaturesdesign, brass encapsulationresistance, and termination optionsinterchangeability, enhanced accuracy and response timeTemperature Sensors |Temperature ProbesSeriesHEL-700HEL-775Featuresrange, ceramic case material, multiple sizesceramic SIP, solderable leadsSeriesHEL-776/777700Featuresenhanced stability, thin film platinum, molded plastic SIP package, solderable leadsinterchangeability, SMD and chip package ver-sions, enhanced stability and time responseTemperature Sensors | RTD Sensorssensing .honeywell .com5SeriesHRTSTDFeaturesresistance interchangeable, accurate, fast, laser-trimmed, wide temperature rangeinterchangeable without recalibration, thin film, laser trimmed, air or liquid temperaturesensingTemperature Sensors | RTD SensorsSeries111112115120Description small, hermetically sealed glass bead large, hermetically sealed glass bead E-I tested and matched beads on mini glass probe Featuresand long-term stability, hermetically sealed in glass, micro size, welded platinum iridium leadstime, hermetically sealed in glass, small size, enhanced long-term stabilityinterchangeable pairs, extended life, compression-type glass hermetic seal,high pressure solder sealSeries140142143173Description small disc large disc large disc EIA 0805 surface Featuresrugged design, solder-able leadsrugged design, solder-able leadspc-board mountable, solderable leadsand reel, glass-coated ceramic, 0805 EIApackageTemperature Sensors | Thermistorssensing .honeywell .com7121126128129135standard glass probe matched large glass bead matched mini glass probe matched large glass probe glass encapsulated chip, DO-35 typeenhanced reliability and stability, weldable/solderable dumet leadsinterchangeability, enhanced sensitivity and reliability, small sizeinterchangeability, enhanced sensitivity and reliability, minia-ture sizeenhanced sensitivity, reliability, and stability; miniature sizeuniform dimensions, tape and reel175192194197ICLEIA 1206 surface mount,uni-curve with bare leads anduni-curve with insulated leads chip with bare leads and epoxy in-rush current limiter glass-coated ceramic, 1206 EIA packageinterchangeability, enhanced stability and life, epoxy coatedinterchangeability, enhanced stability and life, epoxy coated, teflon-coated leadscoatedtemp protective coating, rugged design, pc-board mountable1On a 2252 and 3000 Ohm part, diameter can be up to 3,05 mm [0.120 in] max.Series3000 Custom Packaged3100 Hermetic3100U REDI TEMPThermostats | Precision Thermostatssensing .honeywell .com3106 Low-level Hermetic 3150 LowSilhouette Hermetic3156 Low-levelSilhouette Hermetic3001/3004 SeriesNon-Hermetic9Series3200 Aerospace3153 LowSilhouette HermeticFeaturesNASA certified, space qualified, hermetically sealed, tight tolerances and differentials, pre-set and tamper proof, SPST contactshermetically sealed, tight tolerances and differen-tials, pre-set and tamper proof, SPST contacts* Based on 240 Vac and life-cycle dependent. Call for further details.Thermostats | High Reliability Thermostatssensing .honeywell .com113MS1 QPL35003800 Industrial-Grade3600/3601Custom-Packagedeach unit is 100% thermally and mechani-cally inspected, available to open or close on temperature rise, calibrations preset at factory, SPST contactstight tolerances and differentials,hermetically sealed, designed specifically for military and commercial aircraft, each unit is 100% thermally and mechanically inspectedeasily customized, used where high levels of vibration and mechanical shock are commongold contacts, available to open or close on temperature rise, specifically designed for PCBs, flexible circuitry, sophisticated time-based circuits, wave solderableSeries2450A2450CM2450CMGSeries2450RG2455R2455RAThermostats | Commercial Thermostatssensing .honeywell .com13 2450HR2450HRG2450R2450RC2450RCG2455RVB2455RC2455RG2455RMSeries78000Featuresno wires in clear view area, optical grade, thin film polyester, low power consumptionHeaters | Flexible Heaterssensing .honeywell .com15340031003200®®minimal thicknesswiresflat, molded-to-shape, spiral wrapSeriesHoneywell HumidIcon™ HIH6000Honeywell HumidIcon™ HIH6100Description digital output-type relative humidity (RH) and digital output-type relative humidity (RH) andHumidity Sensors | Honeywell Humidicon™sensing .honeywell .com17Honeywell HumidIcon™ HIH7000Honeywell HumidIcon™ HIH8000digital output-type relative humidity (RH) and digital output-type relative humidity (RH) andSeriesHIH-5030/5031HIH-4000Description covered, filtered or unfiltered integrated circuit integrated circuit Featuresnear linear voltage output vs. %RH, laser trimmed, molded thermoset plastic housing, chemically resis-tant, tape and reel near linear voltage output vs. %RH; laser trimmed, molded thermoset plastic housing, chemically resistantHumidity Sensors | Humiditysensing .honeywell .com19HIH-4010/4020/4021HIH-4030/4031HIH-4602-A, CHIH-4602-Lcovered or uncovered, filtered or unfiltered covered, filtered or unfiltered integrated monolithic IC with integral thermistor or integrated circuit near linear voltage output vs. %RH, laser trimmed, molded thermoset plastic housing, chemically resistant near linear voltage output vs. %RH, laser trimmed, molded thermoset plastic housing, chemically resistant, tape and reel humidity and temperature sensing in one package, near linear voltage output vs. %RH, laser trimmed, chemically resistant,built-in static protectionnear linear voltage output vs %RH, laser-trimmed, chemically resistant, enhancedaccuracy, fast responseHumidity Sensors Used in Wall Mount Transducers (Asia-Pacific Region Only)SCT Series009015-12-EN | 12 | 10/19© 2019 Honeywell International Inc . All rights reserved .Find out moreTo learn more about Honeywell’s sens-ing and switching products, call +1-815-235-6847, email inquiries to *********************, or visit Warranty/RemedyHoneywell warrants goods of its manufacture as being free of defective materials and faulty workmanship . Hon-eywell’s standard product warranty applies unless agreed to otherwise by Honeywell in writing; please refer to your order acknowledgement or consult your local sales office for specific warranty details . If warranted goods are returned to Honeywell during the period of coverage, Honeywell will repair or replace, at its option, without charge those items it finds defective . The foregoing is buyer’s sole remedy and is in lieu of all other warranties, expressed or implied, including those of merchantability and fitness for a par-ticular purpose. In no event shall Honeywell be liable for consequential, special, or indirect damages.While we provide application assistance personally, through our literature and the Honeywell web site, it is up to the customer to determine the suitability of the product in the application .Specifications may change without notice . The information we supply is believed to be accurate and reliable as of this printing . However, we assume no responsibility for its use .Honeywell Sensing and Internet of Things 9680 Old Bailes Road Fort Mill, SC 29707 。
服务许可证错误原因中英文对照表

许可证错误原因对照表FLEXnet Licensing Error Codes Error Code Descriptions-1 Cannot find license file.-2 Invalid license file syntax.-3 No license server system for this feature.-4 Licensed number of users already reached.-5 No such feature exists.-6 No TCP/IP port number in license file and FLEXnet Licensing service does not exist. (pre-v6 only-7 No socket connection to license server manager service.-8 Invalid (inconsistent license key or signature.The license key/signature and data for the feature do not match. Thisusually happens when a license file has been altered.-9 Invalid host.The hostid of this system does not match the hostid specified in thelicense file.-10 Feature has expired.-11 Invalid date format in license file.-12 Invalid returned data from license server system.-13 No SERVER lines in license file.-14 Cannot find SERVER host name in network database.The lookup for the host name on the SERVER line in the license filefailed. This often happens when NIS or DNS or the hosts file isincorrect. Workaround: Use IP address (e.g., 123.456.789.123 insteadof host name.-15 Cannot connect to license server system.The server (lmgrd has not been started yet, or the wrong[email=port@host]port@host[/email]or license file is being used, or the TCP/IP port or host name in thelicense file has been changed.-16 Cannot read data from license server system.-17 Cannot write data to license server system.-18 License server system does not support this feature.-19 Error in select system call.-21 License file does not support this version.-22 Feature checkin failure detected at license server system.-23 License server system temporarily busy (new server connecting .-24 Users are queued for this feature.-25 License server system does not support this version of this feature.-26 Request for more licenses than this feature supports.-29 Cannot find ethernet device.-30 Cannot read license file.-31 Feature start date is in the future.-32 No such attribute.-33 Bad encryption handshake with vendor daemon.-34 Clock difference too large between client and license server system. -35 In the queue for this feature.-36 Feature database corrupted in vendor daemon.-37 Duplicate selection mismatch for this feature. Obsolete with v8.0+ vendor daemon.-38 User/host on EXCLUDE list for feature.-39 User/host not on INCLUDE list for feature.-40 Cannot allocate dynamic memory.-41 Feature was never checked out.-42 Invalid parameter.-47 Clock setting check not available in vendor daemon.-52 Vendor daemon did not respond within timeout interval.-53 Checkout request rejected by vendor-defined checkout filter.-54 No FEATURESET line in license file.-55 Incorrect FEATURESET line in license file.-56 Cannot compute FEATURESET data from license file.-571 socket( call failed.-59 Message checksum failure.-60 License server system message checksum failure.-61 Cannot read license file data from license server system.-62 Network software (TCP/IP not available.-63 You are not a license administrator.-64 lmremove request before the minimum lmremove interval.-67 No licenses available to borrow.-68 License BORROW support not enabled.-69 FLOAT_OK can’t run standalone on license server system.-71 Invalid TZ environment variable.-73 Local checkout filter rejected request.-74 Attempt to read beyond end of license file path.-751 SYS$SETIMR call failed (VMS .-76 Internal FLEXnet Licensing error—please report to Macrovision Corporation.-77 Bad version number must be floating-point number with no letters.-82 Invalid PACKAGE line in license file.-83 FLEXnet Licensing version of client newer than server.-84 USER_BASED license has no specified users - see license server system log.-85 License server system d oesn’t support this request.-87 Checkout exceeds MAX specified in options file.-88 System clock has been set back.-89 This platform not authorized by license.-90 Future license file format or misspelling in license file.The file was issued for a later version of FLEXnet Licensing than thisprogram understands.-91 Encryption seeds are non-unique.-92 Feature removed during lmreread, or wrong SERVER line hostid.-93 This feature is available in a different license pool.This is a warning condition. The server has pooled one or moreINCREMENT lines into a single pool, and the request was made on an INCREMENT line that has been pooled.-94 Attempt to generate license with incompatible attributes.-95 Network connect to THIS_HOST failed.Change this_host on the SERVER line in the license file to theactual host name.-96 License server machine is down or not responding.See the system administrator about starting the server, or make sure thatyou’re referring to the right host (see LM_LICENSE_FILE environmen tvariable .-97 The desired vendor daemon is down.1 Check the lmgrd log file, or2 Try lmreread.-98 This FEATURE line can’t be converted to decimal format.-99 The decimal format license is typed incorrectly.-100 Cannot remove a linger license.-101 All licenses are reserved for others.The system administrator has reserved all the licenses for others. Reservations are made in the options file. The server must be restartedfor options file changes to take effect.-102 A FLEXid borrow error occurred.-103 Terminal Server remote client not allowed.-104 Cannot borrow that long.-106 License server system out of network connections.The vendor daemon can't handle any more users. See the debug log forfurther information.-110 Cannot read dongle: check dongle or driver.Either the dongle is unattached, or the necessary software driver for this dongle type is not installed.-112 Missing dongle driver.In order to read the FLEXid hostid, the correct driver must be installed. These drivers are available from your software vendor.-114 SIGN= keyword required, but missing from license certificate. You need to obtain a SIGN= version of this license from your vendor.-115 Error in Public Key package.-116 TRL not supported for this platform.-117 BORROW failed.-118 BORROW period expired.-119 lmdown and lmreread must be run on license server machine.-120 Cannot lmdown the server when licenses are borrowed.-121 FLOAT_OK requires exactly one FLEXid hostid.-122 Unable to delete local borrow info.-123 Returning a borrowed license early is not supported. Contact the vendor for further details.-124 Error returning borrowed license.-125 A PACKAGE component must be specified.-126 Composite hostid not initialized.-127 A item needed for the composite hostid is missing or invalid.-128 Error, borrowed license doesn't match any known server license.-135 Error enabling the event log.-136 Event logging is disabled.-137 Error writing to the event log.-139 Communications timeout.-140 Bad message command.-141 Error writing to socket. Peer has closed socket.-142 Error, cannot generate version specific license tied to a single hostid, which is composite.-143 Version-specific signatures are not supported for uncounted licenses.-144 License template contains redundant signature specifiers.-145 Bad V71_LK signature.-146 Bad V71_SIGN signature.-147 Bad V80_LK signature.-148 Bad V80_SIGN signature.-149 Bad V81_LK signature.-150 Bad V81_SIGN signature.-151 Bad V81_SIGN2 signature.-152 Bad V84_LK signature.-153 Bad V84_SIGN signature.-154 Bad V84_SIGN2 signature.-155 License key required but missing from the license certificate. The application requires a license key in the license certificate. You need toobtain a license key version of this certificate from your vendor.-156 Invalid signature specified with the AUTH= keyword.-500 Invalid server port number.-501 Invalid value in license where an integer was expected.-502 Invalid value supplied for count.-503 Invalid hostid supplied in license.-504 Invalid hostid type supplied.-505 Bad feature line syntax.-506 Internal FLEXnet Licensing error.-507 Bad date format in license file.-508 Bad SERVER line.-509 Bad license string.-510 Server's feature doesn't authenticate on client side.-511 No license checked out.-512 License already checked out.-513 Error list returned.-514 No certicom module available.-515 Wrong or incomplete certicom module.-516 SIGN or SIGN2 required in license certificate.-517 Feature object has no license sources.-518 An Identical license is already checked out on this license source.-519 This license has an asynchronously-queued checkout pending.-521 Library for native hostid couldn't be loaded-522 Already connected to another vendor daemon.-523 No such user, host, or display.-524 Shutdown of license server system failed.-525 Shutdown failed — already connected to license server system.-526 Invalid license source string.-527 Log file switch error.------------------------------------------------------------------------------------------------------译成中文(简体)FLEXnet许可错误代码错误代码说明-1找不到许可证文件。
Win7系统中安装ArcGIS时许可管理器无法启动的解决步骤

Win7系统中安装ArcGIS时许可管理器无法
启动的解决步骤
ArcGIS是一款GSI专业电子地图信息编辑和开发软件,有很多win7用户在电脑中使用的时候,却遇到这样一个问题,就是许可管理器无法启动,点击启动没有任何反应。
那么应该怎么办呢?不要着急,我现在就来跟大家讲讲win7系统中安装ArcGIS时许可管理器无法启动的解决步骤。
解决方法1:
1、安装许可管理器(License)之后,点击License Server Administrator,打开许可管理器;
2、点击Start,启动License,没有任何反应。
如果安装和破解过程没有错误的话,可以尝试以下步骤;
3、问题之一就是Windows防火墙把License给挡住了。
此时,打开控制面板;
4、点击系统与安全,进入系统与安全界面;
5、点击Windows防火墙,进入Windows防火墙界面;
6、我们可以看到,屏幕左侧有打开或关闭Windows防火墙一栏,点击该栏;
7、选择关闭Windows防火墙,并确定;
8、重新启动License。
如果还是没有反应的话,重新安装ArcGIS 后再次尝试。
如果还是不行的话,可以看下面的原因二。
解决方法2:
1、如果你尝试了以上方法,但是License仍然无法启动。
那么请检查ArcGIS的安装和破解过程是否有误,并且有没有出现软件冲突(例如:ERDAS),如果都没有的话,那么就有可能是系统问题了,建议重装系统吧。
上述便是win7系统中安装ArcGIS时许可管理器无法启动的解决步骤,遇到类似情况的小伙伴们可以参考上面的图文步骤来解决。
TAKEX PASSIVE INFRARED SENSOR Wide angle protectio

TAKEXPASSIVE INFRARED SENSORWide angle protection : PI R -T45WP (40 lbs PET IMMUNE)We appreciate your purchase of a TAKEX passive infrared sensor. This sensor will provide long and dependable service when properly installed. Please read this Instruction Manual carefully for correct and effective use.Please Note: This sensor is designed to detect intrusion and to initiate an alarm ; it is not a burglary-preventing device.TAKEX is not responsible for damage, injury or losses caused by accident, theft, Acts of God ( including inductive surge by lightning ), abuse, misuse, abnormal usage, faulty installation or improper maintenance.1.PARTS DESCRIPTIONCover BaseTerminalsWiring hole(Knockout)Tamper switchirCornerLensLock s crew "lMounting c«>HoleE� Alarm LED:, a,Index(Red) � :!,,---Mounting hole(Knockout)Mode selectorCover lock s crew /Recessed �Wiring hole2.DO'S AND DON'T'S•Install the sensor in a location such that intruders are more likely to cross the protection zones, rather than approach head on.•Do not install in a site which is subject to electrical noise or intense vibration.•The passive infrared sensor is designed to detect infrared energy variations caused by the presence of a human body. Therefore, note that similar variations in conditions in protection area, due to other reasons, may cause the sensor to create an alarm as it is unable to distinguish between sources. [MAINTENANCE]•Avoid direct sunlight, spot light or intense reflections on the sensor or the protection zone.•Do not install the sensor outdoors (indoor use only).•Do not install the sensor directly on the ceiling. (When installed on ceiling, use optional attachment BCW-401.)•When the unit is soiled, clean the cover with a soft cloth moistened with a small amount of cleansing -solution. Do not use chemicals such as thinners or alcohol.•Check operation once a week. Do not fail to check operation whenever furniture in coverage area is moved.3.COVERAGE RANGE AND PET IMMUNITY4.WIRING■Wide Angle PIR-T45WPPROTECTION AREA ADJUSTMENTThe area of protection can be adjusted to allow for different mounting heights as below side view. Loosen Lock Screw, and by moving the inner PCB upwards, the coverage of the sensor can be shortened.There are three field coverage index marks that are printed onto th � P <?B located Matched to the on the left hand side 1ust below ;t ege the left PCB guide rail. They are to be matched to the bottom ofthe guide rail. If the PCB is raised past the bottom index the tamper �\ \ plunger will not activate, leaving �the circuit open; in alarm.� Indexes PET IMMUNITYeThe sensor is designed to not detect animalsunder 40lbs. (20kg).eTo maintain maximum pet immunity, the sensor is required to be installed 8.2ft (2.5m) from the floor vertically without changing the set up as it comes.eThe sensor may detect multiple animals in the protection area even that are smaller than 401bs.eArea adjustment by PCB will decrease the pet immunity.e11 is therefore recommended � to use optional BCW-401 multi purpose mounting bracket ifarea adjustment is required, which will minimize the performance deterioration of the pet immunity.POWER ALARM10-18VDC 24V/0.25A25mA (AC/DC) non -polarity N.C./N.O.k k1k k1TAMPER30VDC/0.1AN.C.IAllowable wiring distance between sensor ]and power sourceSize of wire used Distance at 12VDC AWG 22 (Dia. 0.65mm) 830 ft. (250m) AWG 20 (Dia. 0.80mm) 1470 ft. (450m) AWG 18 (Dia. 1.00mm) 2300 ft. (700m)•The maximum wire length, when two or more units are connected, is the above distance divided by the number of units.•The protection circuit can be wired to a distance of 3,300 ft (1,000m) with AWG 22 (0.65mm dia.) wire. •All wiring should be in accordance with the national electric code NFPA-70.•The power supply used with this unit must have a minimum 4 hours standby power capability.5.INSTALLATION6.OPERATION1. Loosen cover lock screw and detach the cover.2. Open knockout hole.1. Turn the power ON, and wait for 1 minute until the alarm LED stops blinking.3. Install the base on the wall.* Tw o mounting pitches are available.2. Walk test in the protection area to check if an alarm is activated. Check on both of the alarm LED and control panel.*When installed on wall corner, make use of knockouts on sides. 4. Connect wires to terminals (Refer to 4. WIRING) It is important to check operation whenever the area of protection is changed. * P lug up an opening of wiring hole .5. Attach the cover, and tighten cover lock screw.3. After correct operation has been confirmed, turn the alarm LED OFF with mode selector on PWB unit. (When set at OFF, the alarm LED does not light even if an alarm is activated.)7.MODE SETTINGSensor operation can be changed by mode selector on PWB unit.•Pulse count : 1•Selection of alarm contact : 3 N.O.: Cl s larm 4 : L st s si v , p v s fals alarms c us d by mp r ure fluctu . 2 : N rmally s t this posi i . N.C.: Op larm eAUTD RESET MEMORY : 4•Alarm LED : 2�;� � !:�;::::i ;�Factory set ON : Lights alarm OFF: LED dis bl dOperation : M m ry is lw ys s d wh s s is rm d.* M m ry fu c i lw ys ctiv .8.SPECIF/CATIONSModelD c i svs mCov r geS si v z eSupply volt 2eCurre c sumn i Alarm outputT mn r u pu Alarm LED (Red)PIR-T45WPassiv infrar d Wide Angl 36' (llm) M ax.29 Pairs 10 to 18V DC (n-p l ri y) 25mAMax. Dry c act (S mi-C nduc r) (N.O. / N.C. sel c ble)Rese : Appr x. 2sec., R iting: 24V, 0.25A M ax (p o c iv resis c 3.3 n) 30V N.C.: Bli ki g t warmi g upLigh i g alarm (LED dis bl d): Bli king m mory ac ivat d (3 min.) Ligh i g m m ry i dicati (47 mi .)C ve ge adjus m Vertic lly 3 st ps Puls cou zt4 se1ect b1e Alarm m m ry Aut eset: 3 minu s bl nki g, 47 m nut s l ghting nd ut m tically r s Low v l aiz:iceDry contact alarm Ambienttemnerature ran11:e -15 C +55 C (+5 F +131 F ) w th u c ndensa i M un i g p si i I d r use nly (c li g mou with opti l chm BCW-401)W igh 120g (4.2oz) Ann ara c B dy : ABS resi Le s : PE resi The specifica ions are subject to change without notice.Limited Warranty :Wh l m h s b ctiva d, th al m LED blinking for 3 m . and th n r mai s lit for 47 mi . It ut m tically s t d m m ry is ls c c l d. I c s h t th s s trigg s whil i s LED is li , LED ligh s for furth r 4 7 mi . after h .9.EXTERNAL DIMENSIONSunit : inch(mm)PIR-T45W■BCW-401 (Optional)TAKEX pr ducts are warr d b fr e fr m d fects i m erial d workm ship fo 12 months from origin l dat f shipm nt. Our warra y do s o cov r dam g failu c us d by Ac s of G d, bus misus , b rmal us g , faul y i s ll i , improp m i anc o y epairs h r ha thos provid d by TAKEX. All impli d warra ti s wi h r sp ct o TAKEX, i cludi g impli d warra i s for merchant bility nd impli d warr i s for fi n ss, re limi d i dur i to 12 m hs from riginal d f shipm . Duri g th Warra y P ri d, TAKEX will pair r pl c , i s s le p i ,fr of charg , any d fec v parts r tur ed p p id. Pl s provid h mod l nwnb r of the produc s, rigin l da of shipm n and tu of difficul y b i g xp ri c d. Th r will b charges d r d for pr duc repairs m d ft r u Warran y P ri d h s xpi d.。
04-SR-安全防护装置

RS 章节
目录
安全带…………………………………………2
注意事项…………………………………………2 辅助安全防护系统(SRS)“气囊”和 “安全带”………………………………………2
安全带维修注意事项…………………………3 维修……………………………………………3 前座安全带……………………………………4 拆卸与安装……………………………………6 后座安全带……………………………………7 拆卸与安装……………………………………7
RS-8
辅助安全防护系统(SRS)
准备
准备
特殊维修工具
工具型号 工具名称
说明
KV99106400 膨胀工具
处置气囊模块
KV99105300 气囊模组支架
HT61961000 和 HT62152000 结合 *特殊 TORX 套筒
KV99108300 用于前乘客气囊的膨胀工具
市售维修工具
工具名称
Tamper Resistant Torx 插座
注意: · 维修 SRS 之前,将点火开关转至“OFF”,拆开两条电瓶线并等
待至少 3 分钟。 · 特殊螺栓上涂有黏剂,而其它螺栓则为搭铁用。这些螺栓被拆
卸后即不可再使用:须使用新的螺栓来更换。 · 检查诊断感知器元件是否安装适当。 · 检查诊断感知器元件是否无变形、凹陷、裂痕或生锈。如果有
明显损伤记号,则使用新品更换。 · 检查诊断感知器元件是否无变形或生锈。 · 如果诊断感知器已掉过或遭遇撞击,则使用新品更换。 · 诊断感知器更换后,实施 SRS 自我诊断。详情请参考“SRS来自说明固定气囊模块
用于特殊螺栓 [TAMPER RESIS-TANT TORX (尺寸 T50)] a:3.5(0.138)直径 b:8.5-8.6(0.335-0.339)直径 c:大约 10(0.39)平方 单位:mm(in)
IEDScout使用方法说明

ExamplesManual Version: IEDScout.AE.7 - Year 2011© OMICRON electronics. All rights reserved.This manual is a publication of OMICRON electronics GmbH.All rights including translation reserved. Reproduction of any kind, e.g., photocopying, microfilming, optical character recognition and/or storage in electronic data processing systems, requires the explicit consent of OMICRON electronics.Reprinting, wholly or in part, is not permitted. The product information, specifications, and technical data embodied in this manual represent the technical status at the time of writing and are subject to change without prior notice.We have done our best to ensure that the information given in this manual is useful, accurate, up-to-date and reliable. However, OMICRON electronics does not assume responsibility for any inaccuracies which may be present.The user is responsible for every application that makes use of an OMICRON product.IEDScout ExamplesContents1 Requirements and Setup (4)1.1 System Requirements (4)1.2 Installation (4)1.3 Prerequisites (4)Network Settings (4)IEDScout (4)Multiple Network Adapters (4)2 Examples (5)2.1 Discovering and Browsing an IED (5)Defining the IED (5)Discovering the IED (6)Browsing the IED (7)2.2 Working with SCL Files (8)Saving an SCL File (8)Connecting Using an SCL File (9)2.3 Polling Data (9)2.4 Working with Reports (10)Enabling a Report (10)General Interrogation (10)2.5 Subscribing and Recording GOOSE (11)Subscribing using GOOSE Control Blocks (11)Accessing VLAN Information (12)GOOSE Sniffing (13)Transferring GOOSE Information to Configure a CMC Test Set (13)Subscribing Manually (13)GOOSE Recording (14)2.6 Simulating GOOSE (15)Creating a GOOSE (15)Creating a GOOSE Sequence (15)Running a GOOSE Sequence (16)2.7 Analyzing Client/Server Communication (17)General (17)Accessing Client/Server Traffic (17)ACSI Sniffer (17)Views and Functions (18)Search and Filter (19)Details of C/S Traffic (19)Drilling Down (20)Exporting Data and Analysis with External Protocol Software (21)This document provides a quick introduction to some common applications performed with IEDScout and some tips to optimize the work with IEDScout.1 Requirements and Setup1.1 System Requirements• A physical computer with x86 or x64 architecture (no virtual machine)•Windows XP SP2 and above (32 bit only),Windows Vista any SP level (32 bit only) orWindows 7 any SP level (32 bit and 64 bit) operating system•Administrator or Power User rights for the installation• A free USB port for the USB license key•An Ethernet adapter with TCP/IP protocol bound to itNote: Wireless adapters typically do not work with GOOSE/GSSE•If a firewall is present, port 102 must be opened1.2 InstallationOn executing the setup program of IEDScout, the installer will start up:Follow the instructions provided during the installation procedure.1.3 PrerequisitesNetwork SettingsBefore starting work with IEDScout, the network settings on the PC have to be configured properly. It is assumed that the user has administrator or power user rights for changing the network settings. The network adapter must be enabled and must have a valid IP address.IEDScoutTo use the full featured IEDScout, the USB license key has to be plugged into a USB port; otherwise IEDScout will run in evaluation mode.In the G O O S E Tab of the IEDScout configuration, the network adapter for GOOSE must be selected in the field A d a p t e r; the same steps are needed for GSSE. IEDScout only displays adapters that are able to send and receive GOOSE/GSSE messages.Multiple Network AdaptersTo avoid problems due to other programs that also use port 102 (e.g. Microsoft Outlook with Exchange server), IEDScout must be set to use a specific adapter (a specific IP address):In the RFC1006 tab of the IEDScout Configuration window, the L o c a l I P must be set to the IP address of the interface to be used for connecting to the IEDs. When the PC running IEDScout has only one network interface, the L o c a l I P may be left at the default value "0.0.0.0".2 Examples2.1 Discovering and Browsing an IEDDefining the IEDA new IED is added with the N e w Button in the S e r v e r s tab of the C o n f i g u r a t i o n window.A name for the new device must be specified (e.g. "Q0_S"), along with the IP address. In this example the IED's IP address is 192.168.0.77.If a similar device is already present, the option U s e e x i s t i n g s e r v e r d e f i n i t i o n is useful. In this case only the parameters that differ between the two server definitions have to be changed.Figure 1 Defining the IED (Create new Server)The parameters needed to connect to a device should be specified in the documentation for the IED. Usually the IP address is sufficient to connect to an IED.If special parameters need to be set, the A d v a n c e d Button will reveal all available options.The D i s c o v e r button offers a list of servers to connect to. Pick the new server and the S e r v e r Q u e r yP r o g r e s s window will open.IEDScout now reads the self-description of the IED. It discovers the data model of the IED and then reads the actual values contained in the data. Depending on the size of the data model, the speed of the connection, and the server, this may take more than a minute.IEDScout creates a new server section for the discovered IED on the main screen. Double click on the subsections of the IED provides access to all the services that the IED supports.E. g. double clicking on D a t a opens the D a t a V i e w, which will be explained later.Additionally, Datasets and all Control Blocks (GOOSE, Reports, Logs, Sampled Values) can be accessed from here.Right click on the light blue colored root of the IED allows the user to D i s c o n n e c t or D e l e t e the server.Figure 2 Connected to "Q0_S"The status of the connection to the IED is indicated with the following icons:– Shows whether the loaded IED is connected (green) or disconnected (gray) – The IED has been discovered– The IED definition has been loaded from an SCL file (will be explained below)When one of the logical devices in the Main screen is double-clicked, the D a t a V i e w will open. It is divided into two panes.The nesting depth in the left pane is limited to the LD level and gives an overview of the IEDs and their top level structure. This pane is especially useful for quickly navigating between IEDs when multiple devices are loaded.The right pane is for inspecting the IEDs' data models in detail, down to the attribute level.Figure 3 Data View with "Q0_S" loadedThe data tree shows the different types of objects with different icons:• – The server (IED), the root of the data tree• – Logical Device• – Logical Node• – Functional Constraint• – Data Object• – Data Attributes, the leafs of the treeThe D a t a V i e w uses colors to signalize the status and the information source of the data.• – Initial value, the value has not yet been updated• – The value has been retrieved by a read command• – Data has changed within a report• – Data has been updated by a report General Interrogation (GI)• – Value comes from periodic reporting• – This value has just been writtenA context menu opens when a selected data item is right-clicked with the mouse. The context menu offers various functions to be performed with the item, such as R e a d, W r i t e, P o l l i n g, etc. Depending on the selected item (context), some functions which do not apply to that item will be disabled (grayed out).2.2 Working with SCL FilesIEDScout provides useful features with SCL. An SCL file can be created from a discovered IED. If an SCL file with definitions of an IED is provided, the connection and browsing process can be facilitated. Saving an SCL FileThis function is typically used to produce an ICD file for a discovered IED. There are several usages of this SCL file: support further re-connection to the device, import of GOOSE definitions by the GOOSE Configuration module of the OMICRON Test Universe, Simulating of the IED, etc.The S a v e S C L function is accessible from the main screen via the toolbar or the Filemenu.The S a v e S C L window opens. First, the server is selected in the "Server" list.Specifying the I E D N a m e is mandatory and essential to get a correct SCL file. The IED discovery process delivers the IED Name and the LD names concatenated together without delimiters. In the SCL file, these two names need to be stored separately. To split IED Name and LD names correctly, the IED Name has to be known.IEDScout tries to guess the IED Name, which succeeds when sufficiently different LD names are contained in the server. If there is only one LD in the server or if the LD names do not differ at the first character, IEDScout cannot make a correct guess. In this case, the user must provide the correct IED Name. In any case, the IED Name is not arbitrary and must at least match the leading characters of the(IED Name + LD name) string delivered by the IED.Figure 4 Save SCL window Other information as I E D T y p e,M a n u f a c t u r e r and C o n f i g V e r s i o n are optional.As far as possible, IEDScout will correct deviations from the standard in the discovered data model to create a conformant SCL file. Corrections are listed in the "Results:" list.When storing the SCL file, information about the meanings of attributes of type "Enum" is added. The default source for this information is the file "enums.dat". While D i s c o v e r delivers only the ordinal integer values for enumerators, the meanings are displayed in text form when connecting to the device using an SCL file (see the next example).Connecting Using an SCL FileWhen connecting using an SCL file, no parameters have to be specified and the connection operation is much faster because the data model will not be requested from the server.Opening the SCL FileAn SCL file (.icd, .scd, .cid) is opened by selecting the O p e n S C L function from the toolbar or the F i l e menu in the main screen.It is also possible to drag-and-drop an SCL file onto the Main screen of IEDScout.A tree view with all servers in the SCL file is displayed. The tree can be expanded to a certain level to examine the devices offered. A selection specifies which server's data are actually loaded into IEDScout. IEDScout creates new server sections for the selected servers on the main screen, just as if they were found through a D i s c o v e r process.ConnectingIf the addressing (for example the IP address) of the server has changed since the SCL file was created, according modifications can be made by double-clicking on A d d r e s s.A connection is then established by simply clicking C o n n e c t in the right click popup menu of the light blue IED root node.Connecting to a server by using its SCL file speeds up the process considerably, since the discovery of the data model structure is not necessary. This information is already delivered by the SCL file.The actual data can then be read with the R e a d D a t a function in the context menu of the IED or by using the R e a d function (from the context menu of a data item) in the D a t a V i e w.Additionally, the SCL file contains information about the meanings of attributes of type "Enum". This information is then displayed in text form along with the ordinal values for enumerators.2.3 Polling DataData to be polled are collected in the P o l l i n g window. All polled data can be viewed together in one place. This is especially convenient when data from different IEDs are to be observed together, which would not be simultaneously visible in the data view.The Polling Window opens as soon as a data object or attribute is added for polling. Adding data items is done in the D a t a V i e w by focusing an item (DO or DA) and selecting P o l l from the context menu or by dragging & dropping items from the D a t a V i e w to the P o l l i n g window.Items can be individually removed by using the context menu in the P o l l i n g window.Figure 5 Polling Window with dataAll data are polled with the same rate. The polling interval can be selected from preset values.The green dot on the toolbar flashes when the data are polled.If polling is paused, the data can be refreshed manually.2.4 Working with ReportsEnabling a ReportTo enable a report from the device, a report control block (RCB) must be selected. This is done by browsing the object model in the Data View and setting the focus on a RCB. The context menu then offers the function E n a b l e. The values in the RCB that are changed by IEDScout by this action are then marked in purple.Figure 6 Data tree with enabled report (purple)Depending on the trigger options, the server will then send the reports to IEDScout. The updated data will be marked red in the data tree.General InterrogationWhen the report control block is enabled (as mentioned before) and the trigger option allows a general interrogation, the G I function triggers a report that is sent regardless of the other trigger conditions.2.5 Subscribing and Recording GOOSEIEDScout provides four different methods to subscribe to a GOOSE.Subscribing using GOOSE Control BlocksSubscribing by the Control Blocks displayed in the Main ScreenThe Main screen lists all available GOOSE Control Blocks (GCBs) of the IED. When one is double-clicked, the GCB detail window opens. The menu bar has a S u b s c r i b e button.Figure 7 Subscribing from the GOOSE Control Block detail viewOn pressing the S u b s c r i b e button, the GOOSE Subscription Window opens and the GOOSE is displayed in detail.Figure 8 Subscribed GOOSEAll subscription actions lead to the GOOSE Subscription Window or can be initiated from there (see further examples).Subscribing by the Control Blocks displayed in the Data ViewWith the focus on a GOOSE Control Block (GCB), the context menu (accessible via right-click) offers the function S u b s c r i b e G C B. Selecting this function will automatically set up a GOOSE subscription.Figure 9 Subscription using a GOOSE Control BlockAccessing VLAN InformationThe GOOSE subscription also shows the VLAN information in the"Network" branch, but IEDScout can only do so if the Ethernetpackets received actually contain such a VLAN tag.Until a few years ago, network components were not aware ofVLANs and just passed on the entire Ethernet packetsunmodified.Today, modern network equipment is becoming more and more"VLAN aware" and behaves accordingly. VLANs are primarily anissue of network management, so VLANs are primarily handled inEthernet switches and the VLAN tags are not intended to beprocessed by the end devices. Consequently, networkcomponents (switches, adapters, drivers) may strip the VLANtags from the Ethernet packets. It depends on several factors ifand where VLAN tags are stripped, but with the development ofthe networking components, it becomes less likely that applications such as IEDScout will even get the VLAN tags delivered for display and further analysis. Only in specific cases it is possible to get the VLAN tags actually delivered. There are few helpful materials on this, the few ones can be found by submitting an internet search for "capture vlan" or similar.Given the situation as described above, the VLAN information is more likely to be shown as "No VLAN tag".GOOSE SniffingThe GOOSE Sniffer can be started from the G O O S E S u b s c r i p t i o n window or the A c t i o n menu of the Main window. It finds all GOOSE messages arriving at the GOOSE adapter (as specified in the Configuration dialog).These GOOSEs can then be subscribed with the S u b s c r i b e button. Various other functions are accessible from the context menu of a GOOSE entry.Transferring GOOSE Information to Configure a CMC Test SetThe GOOSE Sniffer also supports Drag & Drop or Copy & Paste to the OMICRON Test Universe GOOSE Configuration Module to subscribe/simulate GOOSEs with the CMC test set.Drag & Drop or Copy & PasteFigure 10 Transferring a data from the GOOSE Sniffer to the GOOSE Configuration Module Subscribing ManuallyAdditionally, a GOOSE can be subscribed "from scratch" without using the IED's data model and access to the control blocks. All relevant GOOSE parameters must be known and specified manually. This can be done in G O O S E S u b s c r i p t i o n s with the S u b s c r i b e button. The GOOSE parameters have to be entered in the opening subscription dialog.Figure 11 Subscribing manually by specifying parametersGOOSE RecordingIEDScout has a powerful function for recording GOOSE traffic. Complex relations between data in multiple GOOSEs can be analyzed this way.The data are recorded into COMTRADE files which can be analyzed in several viewer applications. OMICRON TransView may be available for this purpose if the OMICRON Test Universe software (with EnerLyzer) is installed.The name template defines the location where the COMTRADE records are stored and the base file name. Incrementing numbers are appended to the filenames for further recordings.Figure 12 GOOSE Recording WindowThe O p e n function will launch the application associated with the COMTARDE configuration files (CFG file extension) to view the COMTRADE files.When using OMICRON TransView, the maximum recording time is limited to approximately 35 minutes with a µs resolution.Data attributes to be included in the recording need the checkmark next to them checked. Normally, only state changes are recorded. When the sequence number (SqNum) is included, all retransmits will be recorded as well.Trigger conditions can be set up with attributes selected for recording.2.6 Simulating GOOSEThe GOOSE message to be created for the example shall have the following properties:GOOSE ParametersGOOSE Control Reference: IEDScout/LLN0$GO$EvalDataset Reference: IEDScout/LLN0$Eval_DataSetGOOSE ID: GOOSEIDApplication ID: 0x3FFFMulticast MAC Address: 01:0C:CD:01:01:FFRetransmission: First Interval: 1000ms, Multiplier: 2, Max Interval: 8000ms,default strategyData: Boolean; Integer; BitString[4]Creating a GOOSEOpen the G O O S E O u t p u t view by selecting G O O S E S i m u l a t i o n s from the toolbar.Create a new GOOSE with A d d G O O S E.In the Destination MAC address field specify the last two bytes of 01 0C CD 01 01 FF.The initial data must be entered in the D a t a field.For this example, "{False, 0, [1000]}" is the initial data. The data can also be edited with the … button next to the Data field.The other fields are filled out according to the parameters given above:G o I D: "GOOSEID"G c R e f: "IEDScout/LLN0$GO$Eval"D a t S e t: "IEDScout/LLN0$Eval_DataSet".Set the AppID and the VLAN parameters with the Advanced button at the Advanced Addressing Window. The strategy can be changed through the S t r a t e g y button. For this example, the defaults are used. Creating a GOOSE SequenceThe data shall change every second between four different states:Step 1: {False, 0, [1000]}Step 2: {True, 1, [0100]}Step 3: {False, 2, [0010]}Step 4: {True, 3, [0001]}With the I n s e r t S t e p button, four steps are inserted. The D e l a y field is set to 1000ms on all steps.The corresponding data are specified in the data fields.The GOOSE will be published as soon the setup is confirmed with O K on the E d i t G O O S E/G S S E window.Figure 13 The example GOOSE with all parameters filled inThe GOOSE and the sequence shown in Figure 13 is the one used in the evaluation version of IEDScout. Running a GOOSE SequenceBy clicking on R u n in the G O O S E O u t view, the data changes every second according to the setting in the steps.2.7 Analyzing Client/Server CommunicationGeneralThe client/server (C/S) communication is a generic term for the "Two Party Application Association" (TPAA), which is one of the abstract communication services (ACSI) defined in IEC 61850-7-2.In a substation, the client is typically the station controller and the server is typically an IED such as a protection relay and the C/S communication is mainly used for the classical SCADA data exchange.In the context of IEC 61850, the term "MMS" is often used when C/S is actually meant. But in fact MMS (Manufacturing Message Specification, ISO 9506) is just the specific transport protocol used to perform the C/S communication. The specific communication service mapping (SCSM) of the abstract communication services to the MMS protocol is described in IEC 61850-8-1, which also contains the mapping of the GOOSE service to Ethernet. C/S communication could also be performed over alternate transport protocols, e.g. Web-Services, which are actually considered for certain applications like wind power generation.Accessing Client/Server TrafficThere is a significant difference between GOOSE and C/S communication. GOOSE is an Ethernet (network layer) multicast traffic (MCAA: Multicast Application Association). Unless dedicated filters are set up, the Ethernet switches will replicate a received GOOSE and forward it to all connected links. So any device can receive a GOOSE without further efforts.With C/S communication, this is different. The C/S communication is performed over explicitly established connections between the client and the server. The data packets are forwarded as unicast traffic, and that means that the corresponding Ethernet packets are only forwarded on those links that actually establish the path between the involved end points (the client and the server). Without special precautions, an analysis tool like the IEDScout, connected to an arbitrary port on an Ethernet switch, will not receive the packets to be analyzed.There are two means of accessing unicast traffic: taps and mirror ports. A tap is a device that is inserted into a network link and that replicates the traffic going over the link to additional ports, from where it can be received for further processing. A mirror port can be typically found on managed Ethernet switches and this port can be configured to replicate the traffic from specified other ports on the switch, similar as if a tap was used.So for receiving C/S communication with IEDScout, the access to the traffic of interest must be first established as indicated above.For capturing the C/S traffic that is caused by IEDScout itself in its role as a client, there are no special precautions necessary as this traffic is anyway accessible for IEDScout.IEDScout obtains the C/S traffic from the same network adapter that is selected for GOOSE.ACSI SnifferThe A C S I S n i f f e r is accessed via the toolbar from the main screen.The function captures not only the messages related to the C/Straffic, but also the GOOSE messages, so these two ACSI servicesare covered together.To get a better overview and for easier understanding, dedicatedviews for specific kinds of traffic/messages are provided on theACSI level. To investigate the traffic in more detail, drilling down tolower protocol layers (MMS and Ethernet) is also possible.The figure on the right shows how the top level ACSI services(defined in IEC 61850-7-2) relate with the layers below.The mapping of the C/S services to MMS (which itself usesTCP/IP) and the mapping of GOOSE directly to Ethernet is definedin IEC 61850-8-1.Views and FunctionsThe C l i e n t/S e r v e r+G O O S E view shows the C/S messages and the GOOSE messages together. This view gives insight in the course of actions where C/S requests and responses and GOOSEs depend on each other. In this regard, this is more than just an event list.The top half of the list of events below was captured from the execution of a switch command (with SBO) on an XCBR. When the switching happens, the course of the CB status is published via GOOSE and when the CB has entered its new state, reports are generated.At about half down the list, the CB is tripped via a GOOSE (e.g. published by a protection relay), the change of the CB status is again published via GOOSE and reports are sent to the client.By default, only GOOSE status changes are displayed. If desired, the display of GOOSE retransmissions can be enabled by checking R e t r a n s m i s s i o n s in the toolbar. This is a simple (and thus very fast) display filter that suppresses any GOOSEs with a sequence number other than zero. Be aware that if the first GOOSE with a new status (the one with sequence number zero) is missing for some reason, the status change will not be visible at all when repetitions are not shown. There is no further detection of the status changes from analyzing the status numbers.The two kinds of communication can be separately viewed in the C l i e n t/S e r v e r and G O O S E views.The R e p o r t view is provided for convenience. This frequently used filtered view can be accessed in the dedicated tab without the need to use the filter function.Search and FilterIn any view, search and filter functions are available. A toolbar with input fields for search and filter strings are displayed at the bottom of the list.The S e a r c h function does not alter the amount of the displayed entries, but allows finding and stepping through all occurrences of the search string.The F i l t e r function limits the amount of the displayed messages to those containing the filter string.The string matching is case insensitive and works on all text strings (path names, time stamps, ...) that are displayed in the different columns, even if the string is in a collapsed sub-tree that is not currently visible. For example, filtering for "report" in the C/S view would result in a similar (not exactly the same!) display as the R e p o r t view provides.Details of C/S TrafficC/S communication is mostly confirmed (only unsolicited reports are unconfirmed), so the traffic mainly consists of request/response sequences. IEDScout detects requests and responses that belong to each other and groups them together.When expanding an entry in a C/S view, this grouping of the request and the associated response becomes visible. In the figure below this is shown for the operate command.Drilling DownIn any view, a drill down to the underlying protocol layer is possible to obtain more details.When drilling down from a C/S view to investigate the transactions on the MMS layer, all messages belonging to the selected C/S transaction are highlighted in the M M S view with a light yellow color. This will reveal for instance, that a single request/response pair of the C/S layer can consist of multiple MMS messages.The scope of messages belonging to an ACSI transaction cannot always be determined with absolute precision, so the highlighted range may contain some excess messages.More details on the MMS transactions can be seen when further expanding the entries. The E x p a n ds u b t r e e and C o l l a p s e s u b t r e e functions are most useful with MMS, because the nesting can be rather deep with this protocol.The E t h e r n e t view shows the individual Ethernet packets with only few details. To provide a focused view, only packets belonging to IEC 61850 C/S and GOOSE communication are listed.。
PROE错误代码大全

PROE错误代码大全作者:wangqian 日期:2009-05-26字体大小: 小中大前面全部都是: License request failed for feature PROE_DDiTy:开始,然后数字代码不同-1 "cannot find license file"“无法找到许可证文件”中英文解答(由"lhwm"翻译):The unlock software was unable to locate a license file.锁定软件无法找到许可证文件。
Check the settings of these two environment variables:检查设置这两个环境变量:DIVISIONROOT should specify the release directory or be unset. divisionroot应指定释放目录或给予取消。
DIVISION_LICENSE_FILE should specify the license file or be unset. division_license_file应指定许可文件或给予取消。
If neither variables are set the license file is assumed to be/home/division/etc/license/license.dat.如果没有变数设定许可文件,假设为/home/division/etc/license/license.dat 。
Check that the license file is valid.检查许可证文件是有效的。
-2 "invalid license file syntax"“无效的许可证文件语法”中英文解答(由"lhwm"翻译):The license file is corrupt.许可文件已损坏。
win7下kb3061518补丁引起catiaV5 R21找不到许可问题
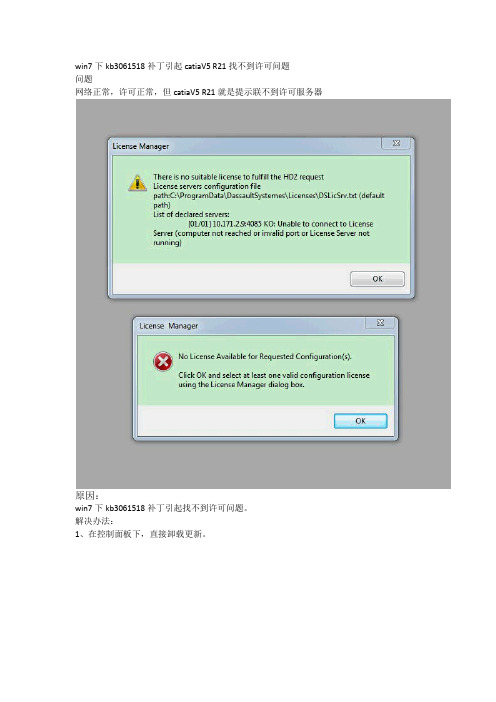
win7下kb3061518补丁引起catiaV5 R21找不到许可问题
问题
网络正常,许可正常,但catiaV5 R21就是提示联不到许可服务器
原因:
win7下kb3061518补丁引起找不到许可问题。
解决办法:
1、在控制面板下,直接卸载更新。
2、修改注册表,操作步骤如下:
1单击“开始”,单击“运行”,在“打开”框中键入regedit,再单击“确定”。
2找到并单击注册表中的以下子项:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyEx changeAlgorithms\Diffie-Hellman
3在“编辑”菜单上,指向“新建”,然后单击“DWORD 值”。
4键入ClientMinKeyBitLength 作为DWORD 的名称,然后按Enter 键。
5右键单击“ClientMinKeyBitLength”,然后单击“修改”。
6
在“值数据”框中,键入00000200,然后单击“确定”。
注:按默认16进制,十进制是512。
7退出注册表编辑器,然后重新启动计算机。
利用license机制来保护Java软件产品的安全

利⽤license机制来保护Java软件产品的安全通常可以通过license机制来保护软件产品的安全,我们可以限定只有购买了license的⽤户在特定的机器上使⽤我们的软件。
我设想的license机制有以下的主要功能点:Ø 应⽤程序可以创建以及验证绑定给⽤户、系统等实体的license。
Ø 防⽌⽤户随意拷贝软件和license。
Ø licenses可以是永久性的或者临时性的(在某个特定时期内有效)Ø licenses的验证由JAVA Security API提供的数字签名机制来实现。
Ø license安装模块需要⽤特殊机制对其进⾏保护,以防被反编译轻易破解。
1、 定义license的⽂件格式License⽂件采⽤普通java properties⽂件的定义格式。
⽂件中定义了产品、版本、Mac地址、license类型、license有效期等信息。
如下所⽰:=cpuProduct.version=3.2License.type=CommercialLicense.expiry=2010-05-12Server.macaddress=00-1B-77-2C-9D-8Fsignature=302d0215008b4ef2390e11d28f5ea7b86f71ba5168bfeaa6b402146c77706b985be68cc515c6079b31ad50e3f17552其中最下⾯⼀串数据为根据上⾯⼏项基本信息签名产⽣的注册号。
2、 创建以及验证license以下是部分实现代码(篇幅问题,只好只粘⽅法说明):/** ⽣成公钥、私钥对。
公钥公开,注意保管好私钥(如果泄露,则有可能被hacker随意创建license) */public static void generateKey() throws Exception;/** ⽤私钥对license进⾏数据签名*/public static synchronized void sign(License license) throws Exception ;/*** 验证license是否合法。
Win7系统安装使用PSASP常见问题
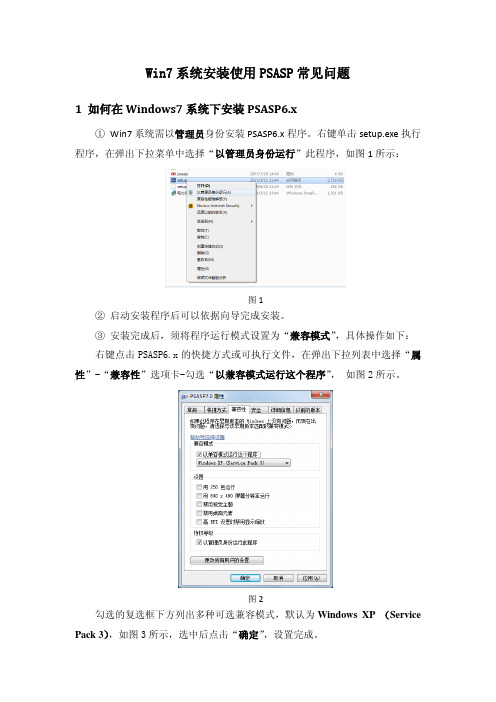
Win7系统安装使用PSASP常见问题1 如何在Windows7系统下安装PSASP6.x①Win7系统需以管理员身份安装PSASP6.x程序。
右键单击setup.exe执行程序,在弹出下拉菜单中选择“以管理员身份运行”此程序,如图1所示:图1②启动安装程序后可以依据向导完成安装。
③安装完成后,须将程序运行模式设置为“兼容模式”,具体操作如下:右键点击PSASP6.x的快捷方式或可执行文件,在弹出下拉列表中选择“属性”-“兼容性”选项卡-勾选“以兼容模式运行这个程序”,如图2所示。
图2勾选的复选框下方列出多种可选兼容模式,默认为Windows XP (Service Pack 3),如图3所示,选中后点击“确定”,设置完成。
图32 如何在Windows7系统下安装PSASP7① Win7系统下选择以管理员身份运行安装程序,具体操作请参看问题1。
②启动安装程序后,安装过程可依据向导提示完成。
3 安装过程提示“不能正确安装软件狗驱动”安装PSASP7或PSASP6.x程序,直接双击setup.exe可执行文件,未以管理员身份运行,程序会弹出对话框提示:“不能正确安装软件狗驱动”,如图4所示。
图4解决方法为右键单击setup.exe可执行文件,在弹出的下拉菜单中选择“以管理员身份运行”这个程序。
4 安装过程提示“安装程序没有访问安装目录的权限”安装PSASP7或PSASP6.x程序,直接双击setup.exe可执行文件,未以管理员身份运行,程序会弹出对话框提示:“安装程序没有访问安装目录的权限”,解决办法同问题3。
5 启动计算软件后,提示“software key not respond…”①请先检查加密狗是否接入计算机;②若加密狗已接入计算机,可从安装光盘\program files\PSASP文件夹下查找MicroDogInstdrv.exe加密狗驱动程序,安装加密狗驱动;③若已安装加密狗驱动问题依然存在,请登陆,下载最新加密狗驱动程序进行安装。
lmtools 临时借用license 操作步骤

lmtools 临时借用license 操作步骤lmtools 是一款软件许可管理工具,能够帮助用户管理他们所拥有的软件许可证。
在某些情况下,我们可能需要临时借用别人的许可证来使用特定的软件。
本文将详细介绍如何使用lmtools 进行临时借用许可证的操作步骤。
步骤1:安装lmtools首先,确保您已经下载并安装了最新版本的lmtools 工具。
您可以从官方网站或其他可靠来源获得该工具的安装包。
一旦安装完成,您就可以开始使用lmtools 进行许可证管理。
步骤2:打开lmtools在您的计算机上找到并打开lmtools 工具。
通常,您可以在开始菜单、应用程序文件夹或桌面的快捷方式中找到该工具的图标。
双击该图标以启动lmtools。
步骤3:选择许可证管理选项在lmtools 的界面中,您将看到多个选项标签,如"系统设置"、"许可证管理"、"服务器活动" 等。
点击"许可证管理" 标签,以进入许可证管理界面。
步骤4:选择"临时借用许可证" 选项在许可证管理界面中,您将看到"临时借用许可证" 的选项。
点击该选项,以进入临时借用许可证的操作界面。
步骤5:选择许可证服务器在临时借用许可证的操作界面中,您需要选择从哪个许可证服务器借用许可证。
在"服务器" 下拉菜单中,选择目标服务器,然后点击"重新获取" 按钮以获取最新的许可证列表。
步骤6:选择要借用的许可证在"许可证列表" 中,您将看到可用的许可证。
选择您想要借用的许可证,然后点击"借用/归还" 按钮。
请注意,某些许可证可能有借用时间限制,您需要在规定的时间内归还许可证,否则将会有额外的费用或法律责任。
步骤7:确认许可证借用信息在确认界面中,您将看到您借用许可证的详细信息,包括许可证类型、借用时间和到期时间等。
enigma protector 注册控制 -回复

enigma protector 注册控制-回复什么是Enigma Protector ?Enigma Protector是一种强大的软件保护工具,它旨在保护软件免受盗版和破解的威胁。
它采用了先进的加密和保护技术,可防止未经授权的访问和篡改,并提供授权管理功能,允许软件开发者对其产品进行严格的许可证控制和使用限制。
为什么要注册Enigma Protector?在未注册Enigma Protector的情况下,你可能只能使用其基本功能,并且在保护软件方面会有一些限制。
注册Enigma Protector意味着你将获得完全的访问权限和功能,这将允许你最大程度地保护你的软件免受盗版和破解的威胁。
如何注册Enigma Protector?注册Enigma Protector是一个相对简单的过程,其中包含一些关键步骤。
步骤1:购买许可证首先,你需要购买Enigma Protector的许可证。
你可以通过访问EnigmaProtector官方网站或与其授权经销商联系来购买许可证。
根据你的需求,Enigma Protector提供了不同类型的许可证选择,例如个人许可证、商业许可证等。
步骤2:下载安装程序在购买许可证后,你将获得一个链接或向导,可用于下载Enigma Protector的安装程序。
请确保下载适用于你的操作系统的正确版本。
步骤3:安装Enigma Protector下载安装程序后,双击运行它并按照提示完成安装过程。
这通常涉及接受许可协议、选择安装路径等。
步骤4:打开Enigma Protector安装完成后,你可以在系统中找到Enigma Protector的图标。
双击该图标以打开Enigma Protector。
步骤5:输入许可证信息在Enigma Protector打开后,你将看到一个注册选项。
在这个选项中,你需要输入你购买的许可证的相关信息,例如许可证密钥等。
确保仔细输入所有信息,并确保没有拼写错误。
accelrys license administrator write permission

accelrys license administrator
write permission
"Accelrys License Administrator write permission" 是指 Accelrys 许可证管理员具有写入权限。
Accelrys 是一家提供科学计算和化学信息学软件的公司,其许可证管理系统用于控制和管理软件的使用权限。
当涉及到许可证管理员的写入权限时,通常意味着该管理员可以对许可证服务器或相关的配置文件进行写入操作,例如:
1. 配置许可证服务器:许可证管理员可能需要具有写入权限来修改许可证服务器的配置参数,例如更改许可证文件的路径、设置最大并发用户数等。
2. 更新许可证:管理员可能需要具有写入权限来安装、更新或激活软件的许可证。
3. 管理用户权限:管理员可能需要能够修改用户的许可证权限,例如分配或限制特定用户对软件的访问权限。
4. 监控和日志记录:管理员可能需要具有写入权限来记录许可证的使用情况、审计日志或生成报告。
总之,"Accelrys License Administrator write permission" 授予了管理员对许可证管理相关的写入操作权限,以便他们有效地管理和控制软件的许可证使用。
具体的权限和操作可能会根据 Accelrys 软件的配置和组织的需求而有所不同。
如果你需要更详细的信息,建议参考 Accelrys 软件的官方文档或联系 Accelrys 技术支持团队。
inconsistent encryption code in license file -回复

inconsistent encryption code in license file -回复在所提供的信息下,我们将一步一步探讨问题并提供可能的解决方案。
首先,我们需要了解什么是“不一致的加密代码”以及“许可文件”。
然后,我们将详细讨论如何解决这个问题。
加密代码是指将信息转化为密码形式的过程,目的是保护信息的安全性。
它使用算法和密钥对信息进行加密和解密。
许可文件是用于授权合法使用软件或许可权的文件。
这些文件通常包含有关授权用户和有效期限的详细信息。
不一致的加密代码可能会导致许可文件无法正确验证或解密。
这可能导致许可文件无法在预期的软件上运行,或者被黑客攻击窃取软件源代码和敏感信息。
解决这个问题的第一步是确定哪些部分的加密代码在许可文件中是不一致的。
可能的原因包括:使用了不同版本的加密算法、使用了不同的密钥或加密参数、或者许可文件本身被篡改。
通过仔细检查许可文件和相关的加密代码,我们可以确定加密代码的哪些部分是不一致的,并制定相应的解决方案。
解决不一致的加密算法版本可能需要升级软件或加密库。
这将确保许可文件和相关的加密代码使用相同的加密算法。
升级过程可能涉及到修改加密代码和进行系统测试,确保加密和解密过程正常运行。
如果问题是由于不同的密钥或加密参数引起的,我们需要找到许可文件和加密代码之间的不一致之处。
可能的解决方案包括:重新生成许可文件,以确保使用相同的密钥和加密参数;更新加密代码,以支持不同的密钥和加密参数;或者将许可文件和加密代码之间的不一致数据进行转换或映射。
如果许可文件本身被篡改,我们需要找到许可文件中的更改和不一致之处。
一种可能的解决方案是使用许可文件的备份或原始副本,以确保许可文件的完整性和一致性。
如果许可文件备份不可用或受损,我们可能需要联系软件供应商或授权机构以获取新的许可文件。
此外,为了避免不一致的加密代码,可以采取以下预防措施:1. 使用可靠和安全的加密算法和技术来加密代码和许可文件。
sublime text4 unlimited user license -回复

sublime text4 unlimited user license -回复什么是Sublime Text 4?Sublime Text 4是一款功能强大的跨平台文本编辑器,它被广泛用于编写程序代码和各种文本文件。
Sublime Text凭借其出色的性能、灵活的功能和友好的用户界面而闻名,而Sublime Text 4版本的发布进一步提高了其性能和功能。
Sublime Text 4无限用户许可是什么意思?无限用户许可意味着一次购买后,您可以将Sublime Text 4安装并使用在不同计算机上的无限个用户中。
这是对企业或组织来说特别有用,因为他们可以仅购买一次许可证,并在内部分享给所有员工使用。
这种许可方式还带来了许多其他好处,比如无需频繁激活和管理许可证,让软件的使用更加便捷。
如何获得Sublime Text 4无限用户许可?要获得Sublime Text 4无限用户许可,您需要访问Sublime Text官方网站,选择购买页面,然后选择无限用户许可选项进行购买。
您将需要提供一些必要的信息,如姓名、邮箱和发票信息等。
一旦付款完成,您将收到一封包含许可证密钥的电子邮件,您只需将该密钥输入Sublime Text 4中即可激活无限用户许可。
无限用户许可有哪些好处?Sublime Text 4无限用户许可带来了一系列实际好处。
首先,它提供了出色的灵活性,您可以将Sublime Text 4安装在多个计算机上,并与同事或团队共享使用。
这意味着您可以随时随地使用Sublime Text 4,而无需担心许可证限制或设备限制。
其次,无限用户许可使得软件的部署和管理更加便捷。
您只需购买一次许可证,就能够将Sublime Text 4提供给所有员工,并确保他们始终使用最新版本。
这消除了频繁的激活和更新许可证的烦恼,节省了时间和精力,提高了生产效率。
此外,无限用户许可还使得组织在财务上更加高效。
通过一次购买无限用户许可,组织可以避免为每个用户都单独购买许可证的费用,从而节省资金。
.net reactor license用法

.net reactor license用法.net reactor是一款安全框架,可以为开发人员和软件供应商提供强大的保护措施,以确保他们的代码和知识产权得到最大的保护。
.net reactor可以加密、混淆和重组代码,以保护它们不被盗用或跟踪。
接下来让我们来了解一下.net reactor license的用法。
.net reactor提供了两种不同的许可证,分别为企业许可证和开发者许可证。
企业许可证适用于企业、组织和机构,而开发者许可证则适用于个人开发者。
企业许可证可以在多个计算机上使用,而开发者许可证只能在单个计算机上使用。
您可以从SMPROTECT的官方网站上购买的任何许可证都将在12个月内过期。
在过期之前,您需要续订许可证。
过期后,您将无法使用.net reactor。
为了使用.net reactor,您需要完成以下步骤:1.在计算机上安装.net reactor,安装期间您需要设置许可证。
要输入许可证,您需要打开.net reactor控制台并单击“许可证”选项卡。
2.在许可证选项卡中,您需要选择“添加许可证”选项,并在对话框中输入许可证信息。
许可证信息包括许可证密钥和许可证代码。
3.完成上述步骤后,您可以开始使用.net reactor。
在.net reactor控制台中,您可以选择要保护的应用程序,并选择要使用的保护级别。
根据您的要求,在代码中插入混淆器和重组器。
4.最后,运行混淆和重组操作,以生成经过保护的代码和程序。
这将创建一个新的程序文件,其中包含.net reactor的加密和混淆代码。
总之,.net reactor是一款功能强大的安全框架。
通过使用不同级别的保护,可以帮助开发人员和供应商保护其知识产权和信息。
希望这篇文章对于了解.net reactor的许可证用法有所帮助。
MSC所有软件安装MSC.License冲突终极解决方案

安装MSC软件License冲突终极解决方案由于专业的原因,在学习过程中,陆续使用到MSC几个不同的软件,个人电脑中安装有MSC.Patran.2005R2、MD.Patran.2008、MSC.Nastran.2005、MSC.Adams.2005R2、MD.Adams.2007R3、MD.Adams.2010、MSC.Easy5.2005R1.4和Easy5.v2010等不同的软件,在安装MSC不同软件的过程中,大家一定遇到过MSC.Licensing安装冲突的问题。
在实践中探索,在实践中提高。
通过不断的尝试,终于找到一个及其简单的方法,共享给大家:【一】:MSC&MD软件,2005年份的MSC.license版本是9.2,2007年份的MSC.license 的版本是10.8,最新的2010年的版本是最高版本的11.6。
【二】:MSC&MD软件的MSC.Licensing高版本能够兼容低版本,也就是说MSC.Licensing.11.6可以兼容10.8和9.2。
【三】:如果要安装不同的MSC软件,个人推荐的安装方式——只需要安装软件中最高版本的MSC.Licensing就行,用最高版本的MSC.Licensing就可以打开所有的MSC&MD 软件(个人电脑中只有一个MSC.Licensing.11.6的版本,就能打开所有的MSC&MD的软件)。
【四】:MSC.Licensing高版本能打开所有的低版本或则是同级版本的软件的前提条件是,所有软件的License.dat必须用最高版本的License.dat。
其言外之意便是所有软件的License.dat的位置必须指向最高版本的License.dat的位置。
【五】:如果还没有开始安装MSC软件,个人推荐的安装方式——在安装软件的过程中会出现一个提示你输入许可License.dat的提示,这个时候界面上会提示你有3个输入的方式,其一是输入个人计算机的名字,再次就是要你输入许可证License.dat的位置。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
License Protection with a Tamper-Resistant Token Cheun Ngen Chong,Bin Ren,Jeroen Doumen,Sandro Etalle,Pieter H Hartel,and Ricardo CorinEEMCS Faculty,University of Twente,Postbus217,7500AE Enschede The Netherlands chong,ren,doumen,etalle,pieter,corin@cs.utwente.nlCenter for Mathematics and Computer Science(CWI),P.O.Box94079,1090GBAmsterdam,The NetherlandsSandro.Etalle@cwi.nlAbstract.Content protection mechanisms are intended to enforce the usage rightson the content.These usage rights are carried by a license.Sometimes,a licenseeven carries the key that is used to unlock the protected content.Unfortunately,license protection is difficult,yet it is important for digital rights management(DRM).Not many license protection schemes are available,and most if not allare proprietary.In this paper,we present a license protection scheme,which ex-ploits tamper-resistant cryptographic hardware.The confidentiality and integrityof the license or parts thereof can be assured with our protection scheme.In ad-dition,the keys to unlock the protected content are always protected and storedsecurely as part of the license.We verifiy secrecy and authentication aspects ofone of our protocols.We implement the scheme in a prototype to assess the per-formance.1IntroductionIn a digital rights management(DRM)system,we use a license to specify the rights of a user on digital content[8].For example,a commercial software license restricts the execution of the licensed software to a particular number of times.A license often carries the key to unlock the protected content.Additionally,the license also carries metadata of the content,which may be as valuable as the content itself.Therefore,the license,just as the content,requires adequate protection.Unfortunately,license protection does not attract as much attention as content pro-tection.There are only a few license protection schemes available,and most if not all are proprietary.Our main security objectives are to ensure confidentiality and integrity of a license or parts thereof,so that keys and metadata can be protected.Additionally,we would like to enforce different usage rights on different parts of the content.For instance,a patient record contains sensitive information about a patient.We want to protect and share this information by using different keys.The doctor is issued all keys to access the entire patient record,but the insurance agent is only issued some keys to access some necessary information.To protect the patient record from being misused,we need to protect these keys.2.SECURITY REQUIREMENTS3.LICENSESCRIPT LICENSE1 up to Bodyprice is the link to the stock price;getvalue(V,X,Y,Z)sets the value of the binding X from the binding list V with the value Y and stores the binding into the binding list Z;iscurrprice is updated;subjects is the access control list of subjects that can view stock4.LICENSE PROTECTION SCHEME4.LICENSE PROTECTION SCHEME4.LICENSE PROTECTION SCHEMEprice;and clause canupdate,which updates the content of stockprice.The license only allows an authorized user(with the correct key)to access these protected parts.In Figure2,broker,who is a paid subscriber,can access the stockprice.As another example of theflexibility of the scheme,imagine a doctor issuing the right storage key to an insurance agent.The agent can access the necessary information in a patient record,which is encrypted under this storage key,while other sensitive information remains hidden from the agent.4.3ProtocolsIn this section,we describe the protocols of our protection scheme:Protocol A(for transmitting the license)and Protocol B(for using the license).For the reader’s conve-nience,we list the notation we use to describe the protocols in Table1.Protocol A This protocol(Figure5)requires interaction between the hardware token, the application,and the license provider.Its two main objectives are:(1)to send the protected license to the application;and(2)to send the public key of the application to the token.The application’s public key will certify the trustworthiness of the application when the license is used.A1Application()asks Token()to get the desired license(identified by) from Provider().must recognize.A2generates a fresh nonce,encrypts with the shared secret key with,, concatenates,and identity to the message received from,en-crypts the result with Provider’s public key,and send this to.The fresh nonce is necessary to prevent a replay attack.The secrecy of the nonce can be assured by encrypting it with.The authenticity of the nonce(i.e.,that it was produced by)is guaranteed by the presence of.Therefore,a malicious application cannot fabricate the message of step A2without the token.A3sends its identity and the message received from to.64.LICENSE PROTECTION SCHEME Meaning4.LICENSE PROTECTION SCHEMEtimes is incremented.In any case,we log the binding values so that when and re-connect to(Protocol A)say,for a new license or content,sends the stored binding values,so that can check if the user has cheated[8].If is used for thefirst time,will store it(can trust the integrity of at thefirst time because is always encrypted with a storage key).B4.2If is a license clause or a content part,no checking is done due to the limited resources of the token.Then,sends and its signature encrypted with a new session key to the reference monitor.The new session key is encrypted with the public key of,i.e.,.B5verifies before interpreting the data.Then,sends to,en-crypted with the session key.The encryption with is to ensure the au-thenticity of the session.B6After has used and updated(i.e.,is generated),sends to for re-encryption.B7replies with the encrypted,i.e..encrypts it with the session key to ensure the authenticity of the session.B8A new license is re-constructed by.asks to regenerate a new MAC value for the updated license.B9sends the new MAC to tofinish thefinal re-construction of.Steps B3to B6may be repeated in a session for different types of data(i.e.,license clause,binding or content part)during the use of the license and content.This completes the description of the protocols.84.LICENSE PROTECTION SCHEME5.PROTOTYPE6.PERFORMANCE EV ALUATION6.PERFORMANCE EV ALUATION6.PERFORMANCE EV ALUATION7.RELATED WORK8.CONCLUSIONS AND FUTURE WORK8.CONCLUSIONS AND FUTURE WORK。
