rfc6012.Datagram Transport Layer Security (DTLS) Transport Mapping for Syslog
rfc3312读书笔记
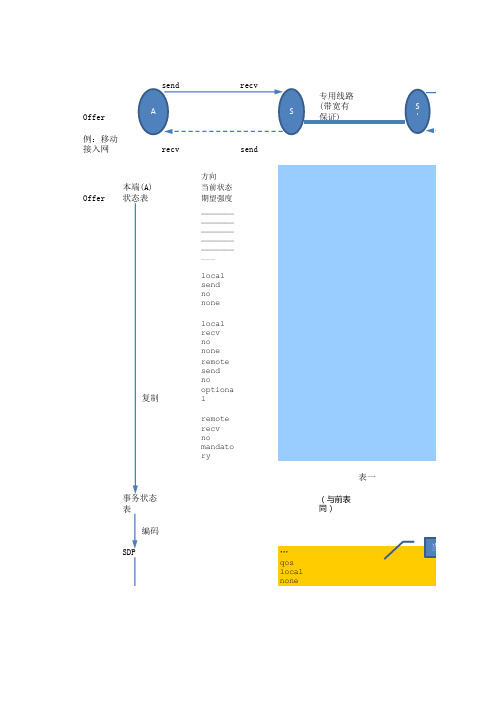
本端(B) 状态表
方向 当前状态 期望强度 _______ _______ _______ _______ _______ ___
local send no noneman datory
local recv no mandato ry
表三
更新
remote send no none
remote recv no none
local recv no optiona l
remote send no none
remote recv no none
a=curr: qos remote nao=ndees:q os none local sendrec va=des:q os optiona l remote sae=nddes:q os mandato ry remote recv …
Offer
例:移动 接入网
send A
recv
recv send
专用线路
S
(带宽有 保证)
Offer
本端(A) 状态表
复制
事务状态 表
编码 SDP
方向 当前状态 期望强度 _______ _______ _______ _______ _______ ___
local send no none
local recv no none remote send no optiona l
remote
recv
no 表一并更 mandato
对比 新它
ry
本端(A) 状态表
方向 当前状态 期望强度 _______ _______ _______ _______ _______ ___
local send no none
中移动家庭网关终端技术规范v3.0.0

中国移动通信企业标准家庭网关终端技术规范版本号:3.0.0中国移动通信集团公司发布╳╳╳╳-╳╳-╳╳发布 ╳╳╳╳-╳╳-╳╳实施QB-╳╳-╳╳╳-╳╳╳╳ T e c h n i c a l S p e c i f i c a t i o n f o r H o m e G a t e w a y目录3.术语、定义和缩略语 ....................................................................................... 错误!未指定书签。
USB扩展及管理(可选)................................................................................ 错误!未指定书签。
DLNA(可选)............................................................................................................... 错误!未指定书签。
5.6.硬件要求....................................................................................................... 错误!未指定书签。
设备面板标识要求........................................................................................... 错误!未指定书签。
操作管理 ...................................................................................................................... 错误!未指定书签。
srv6相关标准

SRv6(Segment Routing over IPv6)是一种基于IPv6网络的新型路由技术,它通过在IPv6数据包中添加一个24位的标签来标识不同的路径。
这种技术可以提高网络的可扩展性、灵活性和安全性。
以下是一些与SRv6相关的标准:1. RFC 8210:这是SRv6的基本规范,定义了SRv6的基本概念、操作和实现要求。
2. RFC 8365:这个文档描述了如何使用BGP-LS(Border Gateway Protocol - Link State)协议在IPv6网络中传播SRv6路由信息。
3. RFC 8402:这个文档描述了如何使用MP-BGP(Multiprotocol BGP)协议在IPv6网络中传播SRv6路由信息。
4. RFC 8415:这个文档描述了如何使用IS-IS(Intermediate System to Intermediate System)协议在IPv6网络中传播SRv6路由信息。
5. RFC 8475:这个文档描述了如何使用OSPF(Open Shortest Path First)协议在IPv6网络中传播SRv6路由信息。
6. RFC 8597:这个文档描述了如何使用BFD(Bidirectional Forwarding Detection)协议在IPv6网络中检测SRv6路径的状态。
7. RFC 8795:这个文档描述了如何使用LDP(Label Distribution Protocol)协议在IPv6网络中分发SRv6标签。
8. RFC 8879:这个文档描述了如何使用PCE(Path Computation Element)协议在IPv6网络中计算SRv6路径。
9. RFC 8915:这个文档描述了如何使用SDN(Software-Defined Networking)技术来实现SRv6网络。
10. RFC 9119:这个文档描述了如何使用SRv6技术来实现网络切片。
lsa的报文格式 -回复

lsa的报文格式-回复LSA(Link-State Advertisement)是在链路状态路由协议(如OSPF和IS-IS)中使用的一种报文格式。
它用于在网络中传播信息,包括路由器的链路状态和网络拓扑,以便在整个网络中建立可靠的路由。
LSA的报文格式包含了各种字段,用于描述路由器、链路和网络的属性。
下面将一步一步解释LSA报文格式的各个字段。
1. Type(类型):这个字段用于指示LSA的类型。
不同类型的LSA用于传输不同类型的信息,通常有以下几种类型:Router LSA,Network LSA,Summary LSA和AS-external LSA等。
每个类型的LSA都有不同的用途和内容。
2. LS Age(LSA的时效):这个字段表示LSA的年龄,即它生成后经过的时间。
这个字段的目的是为了帮助路由器判断LSA是否过时,如果一个LSA的时效过高,则可能代表该LSA已经失效,需要更新。
3. Link State ID(链路状态标识):这个字段用于唯一标识一个LSA。
在Router LSA中,它表示该LSA所属的路由器的接口IP地址;在Network LSA中,它表示该LSA所属的网络的网络地址。
通过Link State ID,路由器可以识别和区分不同的LSA。
4. Advertising Router(广告路由器):这个字段指示了生成并发送该LSA的路由器的ID。
通过Advertising Router字段,其他路由器可以知道该LSA是由哪个路由器生成的。
5. LS Sequence Number(LSA序列号):这个字段表示LSA的序列号。
每个LSA都有一个唯一的序列号,用于区分各个版本的同一个LSA。
如果两个LSA的序列号相同,则表示它们是同一个LSA的不同版本。
6. Checksum(校验和):这个字段用于校验LSA的完整性。
通过计算LSA 的各个字段,并进行校验和计算,接收方可以检查该LSA是否在传输过程中发生了错误。
计算机网络-5_Transport_Layer(传输层协议)解析

network layer: logical
Household analogy:
12 kids sending letters to 12 kids
processes = kids
app messages = letters
relies on, enhances, network layer services
Computer Networking: A Top Down Approach Featuring the Internet,
2nd edition. Jim Kurose, Keith Ross Addison-Wesley, July 2002.
Transport Layer
3-1
Chapter 3: Transport Layer
32 bits source port # dest port #
other header fields
application data (message)
TCP/UDP segment format
Transport Layer 3-9
Connectionless demultiplexing
How demultiplexing works
host receives IP datagrams
each datagram has source IP address, destination IP address each datagram carries 1 transport-layer segment each segment has source, destination port number (recall: well-known port numbers for specific applications) host uses IP addresses & port numbers to direct segment to appropriate socket
ssh server的算法 -回复

ssh server的算法-回复SSH(Secure Shell)是一种网络协议,用于在安全的通信通道上执行远程计算机之间的加密和身份验证。
SSH服务器的算法是为确保安全通信而实施的一系列加密算法和身份验证方法。
SSH服务器算法的主要目标是提供安全和可靠的远程访问,使用户能够通过加密的通信连接到远程计算机系统。
以下将逐步介绍SSH服务器算法的几个关键方面:1. 加密算法:SSH服务器使用加密算法来保护通信的机密性。
常见的加密算法包括对称加密算法(如AES、3DES)、非对称加密算法(如RSA、DSA)和散列算法(如SHA-256)。
对称加密算法用于加密和解密通信数据,而非对称加密算法用于实现密钥交换和数字签名。
散列算法用于生成和验证消息签名。
2. 身份验证方法:SSH服务器通过身份验证方法验证用户的身份,确保只有授权的用户才能访问远程系统。
最常用的身份验证方法是密码身份验证和公钥身份验证。
密码身份验证要求用户输入密码以验证其身份,而公钥身份验证通过在用户和服务器之间交换密钥对来进行身份验证。
3. 密钥交换协议:SSH服务器使用密钥交换协议来生成临时会话密钥,以确保通信过程中的机密性和完整性。
常见的密钥交换协议有Diffie-Hellman(DH)和基于椭圆曲线的密钥交换协议(ECDH)。
这些协议允许服务器和客户端在安全的通道上交换密钥,并在通信过程中生成会话密钥。
4. 会话管理:SSH服务器使用会话管理来维护客户端和服务器之间的连接。
会话管理包括在通信开始时建立连接、密钥交换和身份验证过程,以及在通信结束时终止连接。
会话管理还涉及到会话的状态维护和错误处理。
5. 基于证书的身份验证:一些高级的SSH服务器支持基于证书的身份验证。
此方法使用公钥加密技术和数字证书颁发机构(CA)来验证用户的身份。
服务器使用CA 签名的用户公钥证书来验证用户的身份,并与文件系统上保存的相应用户私钥进行比较。
6. 安全性和性能优化:SSH服务器算法还涉及一些安全性和性能优化的技术。
tls1.2原理 -回复

tls1.2原理-回复TLs协议(Transport Layer Security,传输层安全协议)是一种加密协议,用于保护网络通信的数据安全。
在网络通信过程中,TLS协议通过建立安全通道,对数据进行加密和认证,以防止数据被窃听、篡改和伪装攻击。
TLS 1.2是TLS协议的一种版本,在这篇文章中,我们将逐步解释TLS 1.2的原理。
第一步:握手协议TLS 1.2的通信流程始于握手协议。
握手协议是TLS 1.2的核心,用于创建和协商加密通道。
握手协议由以下几个步骤组成:1. 客户端向服务器发送一个握手请求。
请求中包含支持的TLS版本、加密算法和其他相关参数。
2. 服务器回应客户端的握手请求,并返回自己的数字证书。
数字证书包含服务器的公钥和相关身份信息。
3. 客户端对服务器发送的证书进行验证。
验证过程包括检查证书的有效性和真实性,以及与信任的证书颁发机构进行核对。
4. 客户端生成一个随机数,作为对称加密算法的密钥。
5. 客户端使用服务器的公钥加密生成的密钥,以确保只有服务器能够解密该密钥。
6. 客户端向服务器发送加密的对称密钥,此时TLS 1.2握手协议的安全通道已经建立。
第二步:加密算法协商在握手协议的过程中,客户端和服务器协商选择使用的加密算法。
这些算法包括对称加密算法、散列算法和公钥加密算法。
对称加密算法用于加密和解密通信数据。
常用的对称加密算法有AES、DES 等。
TLS 1.2要求支持AES算法。
散列算法用于生成消息摘要,用于验证数据的完整性。
常用的散列算法有SHA-1、SHA-256等。
TLS 1.2要求支持SHA-256算法。
公钥加密算法用于加密对称密钥和进行数字签名。
常用的公钥加密算法有RSA、Diffie-Hellman等。
TLS 1.2要求支持RSA算法。
在握手协议的过程中,客户端和服务器协商选择使用的加密算法和协议版本。
双方必须选择支持的算法和协议版本以建立安全通道。
第三步:加密数据传输一旦握手协议完成,安全通道建立后,客户端和服务器之间的数据传输将通过加密方式进行。
rfc2661.Layer Two Tunneling Protocol L2TP

Network Working Group W. Townsley Request for Comments: 2661 A. Valencia Category: Standards Track cisco Systems A. Rubens Ascend Communications G. Pall G. Zorn Microsoft Corporation B. Palter Redback Networks August 1999 Layer Two Tunneling Protocol "L2TP"Status of this MemoThis document specifies an Internet standards track protocol for the Internet community, and requests discussion and suggestions forimprovements. Please refer to the current edition of the "InternetOfficial Protocol Standards" (STD 1) for the standardization stateand status of this protocol. Distribution of this memo is unlimited.Copyright NoticeCopyright (C) The Internet Society (1999). All Rights Reserved.AbstractThis document describes the Layer Two Tunneling Protocol (L2TP). STD 51, RFC 1661 specifies multi-protocol access via PPP [RFC1661]. L2TP facilitates the tunneling of PPP packets across an interveningnetwork in a way that is as transparent as possible to both end-users and applications.Table of Contents1.0 Introduction (3)1.1 Specification of Requirements (4)1.2 Terminology (4)2.0 Topology (8)3.0 Protocol Overview (9)3.1 L2TP Header Format (9)3.2 Control Message Types (11)4.0 Control Message Attribute Value Pairs (12)4.1 AVP Format (13)4.2 Mandatory AVPs (14)4.3 Hiding of AVP Attribute Values (14)Townsley, et al. Standards Track [Page 1]4.4.1 AVPs Applicable To All Control Messages (17)4.4.2 Result and Error Codes (18)4.4.3 Control Connection Management AVPs (20)4.4.4 Call Management AVPs (27)4.4.5 Proxy LCP and Authentication AVPs (34)4.4.6 Call Status AVPs (39)5.0 Protocol Operation (41)5.1 Control Connection Establishment (41)5.1.1 Tunnel Authentication (42)5.2 Session Establishment (42)5.2.1 Incoming Call Establishment (42)5.2.2 Outgoing Call Establishment (43)5.3 Forwarding PPP Frames (43)5.4 Using Sequence Numbers on the Data Channel (44)5.5 Keepalive (Hello) (44)5.6 Session Teardown (45)5.7 Control Connection Teardown (45)5.8 Reliable Delivery of Control Messages (46)6.0 Control Connection Protocol Specification (48)6.1 Start-Control-Connection-Request (SCCRQ) (48)6.2 Start-Control-Connection-Reply (SCCRP) (48)6.3 Start-Control-Connection-Connected (SCCCN) (49)6.4 Stop-Control-Connection-Notification (StopCCN) (49)6.5 Hello (HELLO) (49)6.6 Incoming-Call-Request (ICRQ) (50)6.7 Incoming-Call-Reply (ICRP) (51)6.8 Incoming-Call-Connected (ICCN) (51)6.9 Outgoing-Call-Request (OCRQ) (52)6.10 Outgoing-Call-Reply (OCRP) (53)6.11 Outgoing-Call-Connected (OCCN) (53)6.12 Call-Disconnect-Notify (CDN) (53)6.13 WAN-Error-Notify (WEN) (54)6.14 Set-Link-Info (SLI) (54)7.0 Control Connection State Machines (54)7.1 Control Connection Protocol Operation (55)7.2 Control Connection States (56)7.2.1 Control Connection Establishment (56)7.3 Timing considerations (58)7.4 Incoming calls (58)7.4.1 LAC Incoming Call States (60)7.4.2 LNS Incoming Call States (62)7.5 Outgoing calls (63)7.5.1 LAC Outgoing Call States (64)7.5.2 LNS Outgoing Call States (66)7.6 Tunnel Disconnection (67)8.0 L2TP Over Specific Media (67)8.1 L2TP over UDP/IP (68)Townsley, et al. Standards Track [Page 2]9.0 Security Considerations (69)9.1 Tunnel Endpoint Security (70)9.2 Packet Level Security (70)9.3 End to End Security (70)9.4 L2TP and IPsec (71)9.5 Proxy PPP Authentication (71)10.0 IANA Considerations (71)10.1 AVP Attributes (71)10.2 Message Type AVP Values (72)10.3 Result Code AVP Values (72)10.3.1 Result Code Field Values (72)10.3.2 Error Code Field Values (72)10.4 Framing Capabilities & Bearer Capabilities (72)10.5 Proxy Authen Type AVP Values (72)10.6 AVP Header Bits (73)11.0 References (73)12.0 Acknowledgments (74)13.0 Authors’ Addresses (75)Appendix A: Control Channel Slow Start and CongestionAvoidance (76)Appendix B: Control Message Examples (77)Appendix C: Intellectual Property Notice (79)Full Copyright Statement (80)1.0 IntroductionPPP [RFC1661] defines an encapsulation mechanism for transportingmultiprotocol packets across layer 2 (L2) point-to-point links.Typically, a user obtains a L2 connection to a Network Access Server (NAS) using one of a number of techniques (e.g., dialup POTS, ISDN,ADSL, etc.) and then runs PPP over that connection. In such aconfiguration, the L2 termination point and PPP session endpointreside on the same physical device (i.e., the NAS).L2TP extends the PPP model by allowing the L2 and PPP endpoints toreside on different devices interconnected by a packet-switchednetwork. With L2TP, a user has an L2 connection to an accessconcentrator (e.g., modem bank, ADSL DSLAM, etc.), and theconcentrator then tunnels individual PPP frames to the NAS. Thisallows the actual processing of PPP packets to be divorced from thetermination of the L2 circuit.One obvious benefit of such a separation is that instead of requiring the L2 connection terminate at the NAS (which may require along-distance toll charge), the connection may terminate at a (local) circuit concentrator, which then extends the logical PPP session over Townsley, et al. Standards Track [Page 3]a shared infrastructure such as frame relay circuit or the Internet.From the user’s perspective, there is no functional difference between having the L2 circuit terminate in a NAS directly or using L2TP.L2TP may also solve the multilink hunt-group splitting problem.Multilink PPP [RFC1990] requires that all channels composing amultilink bundle be grouped at a single Network Access Server (NAS).Due to its ability to project a PPP session to a location other thanthe point at which it was physically received, L2TP can be used tomake all channels terminate at a single NAS. This allows multilinkoperation even when the calls are spread across distinct physicalNASs.This document defines the necessary control protocol for on-demandcreation of tunnels between two nodes and the accompanyingencapsulation for multiplexing multiple, tunneled PPP sessions.1.1 Specification of RequirementsThe key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT","SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in thisdocument are to be interpreted as described in [RFC2119].1.2 TerminologyAnalog ChannelA circuit-switched communication path which is intended to carry3.1 kHz audio in each direction.Attribute Value Pair (AVP)The variable length concatenation of a unique Attribute(represented by an integer) and a Value containing the actualvalue identified by the attribute. Multiple AVPs make up ControlMessages which are used in the establishment, maintenance, andteardown of tunnels.CallA connection (or attempted connection) between a Remote System and LAC. For example, a telephone call through the PSTN. A Call(Incoming or Outgoing) which is successfully established between a Remote System and LAC results in a corresponding L2TP Sessionwithin a previously established Tunnel between the LAC and LNS.(See also: Session, Incoming Call, Outgoing Call).Townsley, et al. Standards Track [Page 4]Called NumberAn indication to the receiver of a call as to what telephonenumber the caller used to reach it.Calling NumberAn indication to the receiver of a call as to the telephone number of the caller.CHAPChallenge Handshake Authentication Protocol [RFC1994], a PPPcryptographic challenge/response authentication protocol in which the cleartext password is not passed over the line.Control ConnectionA control connection operates in-band over a tunnel to control the establishment, release, and maintenance of sessions and of thetunnel itself.Control MessagesControl messages are exchanged between LAC and LNS pairs,operating in-band within the tunnel protocol. Control messagesgovern aspects of the tunnel and sessions within the tunnel.Digital ChannelA circuit-switched communication path which is intended to carrydigital information in each direction.DSLAMDigital Subscriber Line (DSL) Access Module. A network device used in the deployment of DSL service. This is typically a concentrator of individual DSL lines located in a central office (CO) or local exchange.Incoming CallA Call received at an LAC to be tunneled to an LNS (see Call,Outgoing Call).Townsley, et al. Standards Track [Page 5]L2TP Access Concentrator (LAC)A node that acts as one side of an L2TP tunnel endpoint and is apeer to the L2TP Network Server (LNS). The LAC sits between anLNS and a remote system and forwards packets to and from each.Packets sent from the LAC to the LNS requires tunneling with theL2TP protocol as defined in this document. The connection fromthe LAC to the remote system is either local (see: Client LAC) or a PPP link.L2TP Network Server (LNS)A node that acts as one side of an L2TP tunnel endpoint and is apeer to the L2TP Access Concentrator (LAC). The LNS is thelogical termination point of a PPP session that is being tunneled from the remote system by the LAC.Management Domain (MD)A network or networks under the control of a singleadministration, policy or system. For example, an LNS’s Management Domain might be the corporate network it serves. An LAC’sManagement Domain might be the Internet Service Provider that owns and manages it.Network Access Server (NAS)A device providing local network access to users across a remoteaccess network such as the PSTN. An NAS may also serve as an LAC, LNS or both.Outgoing CallA Call placed by an LAC on behalf of an LNS (see Call, IncomingCall).PeerWhen used in context with L2TP, peer refers to either the LAC orLNS. An LAC’s Peer is an LNS and vice versa. When used in context with PPP, a peer is either side of the PPP connection.POTSPlain Old Telephone Service.Townsley, et al. Standards Track [Page 6]Remote SystemAn end-system or router attached to a remote access network (i.e.a PSTN), which is either the initiator or recipient of a call.Also referred to as a dial-up or virtual dial-up client.SessionL2TP is connection-oriented. The LNS and LAC maintain state foreach Call that is initiated or answered by an LAC. An L2TP Session is created between the LAC and LNS when an end-to-end PPPconnection is established between a Remote System and the LNS.Datagrams related to the PPP connection are sent over the Tunnelbetween the LAC and LNS. There is a one to one relationshipbetween established L2TP Sessions and their associated Calls. (See also: Call).TunnelA Tunnel exists between a LAC-LNS pair. The Tunnel consists of aControl Connection and zero or more L2TP Sessions. The Tunnelcarries encapsulated PPP datagrams and Control Messages betweenthe LAC and the LNS.Zero-Length Body (ZLB) MessageA control packet with only an L2TP header. ZLB messages are usedfor explicitly acknowledging packets on the reliable controlchannel.Townsley, et al. Standards Track [Page 7]2.0 TopologyThe following diagram depicts a typical L2TP scenario. The goal is to tunnel PPP frames between the Remote System or LAC Client and an LNS located at a Home LAN.[Home LAN][LAC Client]----------+ |____|_____ +--[Host]| | |[LAC]---------| Internet |-----[LNS]-----+| |__________| |_____|_____ :| || PSTN |[Remote]--| Cloud |[System] | | [Home LAN]|___________| || ______________ +---[Host]| | | |[LAC]-------| Frame Relay |---[LNS]-----+| or ATM Cloud | ||______________| :The Remote System initiates a PPP connection across the PSTN Cloud to an LAC. The LAC then tunnels the PPP connection across the Internet, Frame Relay, or ATM Cloud to an LNS whereby access to a Home LAN isobtained. The Remote System is provided addresses from the HOME LANvia PPP NCP negotiation. Authentication, Authorization and Accounting may be provided by the Home LAN’s Management Domain as if the userwere connected to a Network Access Server directly.A LAC Client (a Host which runs L2TP natively) may also participatein tunneling to the Home LAN without use of a separate LAC. In thiscase, the Host containing the LAC Client software already has aconnection to the public Internet. A "virtual" PPP connection is then created and the local L2TP LAC Client software creates a tunnel tothe LNS. As in the above case, Addressing, Authentication,Authorization and Accounting will be provided by the Home LAN’sManagement Domain.Townsley, et al. Standards Track [Page 8]3.0 Protocol OverviewL2TP utilizes two types of messages, control messages and datamessages. Control messages are used in the establishment, maintenance and clearing of tunnels and calls. Data messages are used toencapsulate PPP frames being carried over the tunnel. Controlmessages utilize a reliable Control Channel within L2TP to guarantee delivery (see section 5.1 for details). Data messages are notretransmitted when packet loss occurs.+-------------------+| PPP Frames |+-------------------+ +-----------------------+| L2TP Data Messages| | L2TP Control Messages |+-------------------+ +-----------------------+| L2TP Data Channel | | L2TP Control Channel || (unreliable) | | (reliable) |+------------------------------------------------+| Packet Transport (UDP, FR, ATM, etc.) |+------------------------------------------------+Figure 3.0 L2TP Protocol StructureFigure 3.0 depicts the relationship of PPP frames and ControlMessages over the L2TP Control and Data Channels. PPP Frames arepassed over an unreliable Data Channel encapsulated first by an L2TP header and then a Packet Transport such as UDP, Frame Relay, ATM,etc. Control messages are sent over a reliable L2TP Control Channelwhich transmits packets in-band over the same Packet Transport.Sequence numbers are required to be present in all control messagesand are used to provide reliable delivery on the Control Channel.Data Messages may use sequence numbers to reorder packets and detect lost packets.All values are placed into their respective fields and sent innetwork order (high order octets first).3.1 L2TP Header FormatL2TP packets for the control channel and data channel share a common header format. In each case where a field is optional, its space does not exist in the message if the field is marked not present. Notethat while optional on data messages, the Length, Ns, and Nr fieldsmarked as optional below, are required to be present on all controlmessages.Townsley, et al. Standards Track [Page 9]This header is formatted:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+|T|L|x|x|S|x|O|P|x|x|x|x| Ver | Length (opt) |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Tunnel ID | Session ID |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Ns (opt) | Nr (opt) |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Offset Size (opt) | Offset pad... (opt)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+Figure 3.1 L2TP Message HeaderThe Type (T) bit indicates the type of message. It is set to 0 for a data message and 1 for a control message.If the Length (L) bit is 1, the Length field is present. This bitMUST be set to 1 for control messages.The x bits are reserved for future extensions. All reserved bits MUST be set to 0 on outgoing messages and ignored on incoming messages.If the Sequence (S) bit is set to 1 the Ns and Nr fields are present. The S bit MUST be set to 1 for control messages.If the Offset (O) bit is 1, the Offset Size field is present. The Obit MUST be set to 0 (zero) for control messages.If the Priority (P) bit is 1, this data message should receivepreferential treatment in its local queuing and transmission. LCPecho requests used as a keepalive for the link, for instance, should generally be sent with this bit set to 1. Without it, a temporaryinterval of local congestion could result in interference withkeepalive messages and unnecessary loss of the link. This feature is only for use with data messages. The P bit MUST be set to 0 for allcontrol messages.Ver MUST be 2, indicating the version of the L2TP data message header described in this document. The value 1 is reserved to permitdetection of L2F [RFC2341] packets should they arrive intermixed with L2TP packets. Packets received with an unknown Ver field MUST bediscarded.The Length field indicates the total length of the message in octets. Townsley, et al. Standards Track [Page 10]Tunnel ID indicates the identifier for the control connection. L2TPtunnels are named by identifiers that have local significance only.That is, the same tunnel will be given different Tunnel IDs by eachend of the tunnel. Tunnel ID in each message is that of the intended recipient, not the sender. Tunnel IDs are selected and exchanged asAssigned Tunnel ID AVPs during the creation of a tunnel.Session ID indicates the identifier for a session within a tunnel.L2TP sessions are named by identifiers that have local significanceonly. That is, the same session will be given different Session IDsby each end of the session. Session ID in each message is that of the intended recipient, not the sender. Session IDs are selected andexchanged as Assigned Session ID AVPs during the creation of asession.Ns indicates the sequence number for this data or control message,beginning at zero and incrementing by one (modulo 2**16) for eachmessage sent. See Section 5.8 and 5.4 for more information on usingthis field.Nr indicates the sequence number expected in the next control message to be received. Thus, Nr is set to the Ns of the last in-ordermessage received plus one (modulo 2**16). In data messages, Nr isreserved and, if present (as indicated by the S-bit), MUST be ignored upon receipt. See section 5.8 for more information on using thisfield in control messages.The Offset Size field, if present, specifies the number of octetspast the L2TP header at which the payload data is expected to start. Actual data within the offset padding is undefined. If the offsetfield is present, the L2TP header ends after the last octet of theoffset padding.3.2 Control Message TypesThe Message Type AVP (see section 4.4.1) defines the specific type of control message being sent. Recall from section 3.1 that this is only for control messages, that is, messages with the T-bit set to 1. Townsley, et al. Standards Track [Page 11]This document defines the following control message types (seeSection 6.1 through 6.14 for details on the construction and use ofeach message):Control Connection Management0 (reserved)1 (SCCRQ) Start-Control-Connection-Request2 (SCCRP) Start-Control-Connection-Reply3 (SCCCN) Start-Control-Connection-Connected4 (StopCCN) Stop-Control-Connection-Notification5 (reserved)6 (HELLO) HelloCall Management7 (OCRQ) Outgoing-Call-Request8 (OCRP) Outgoing-Call-Reply9 (OCCN) Outgoing-Call-Connected10 (ICRQ) Incoming-Call-Request11 (ICRP) Incoming-Call-Reply12 (ICCN) Incoming-Call-Connected13 (reserved)14 (CDN) Call-Disconnect-NotifyError Reporting15 (WEN) WAN-Error-NotifyPPP Session Control16 (SLI) Set-Link-Info4.0 Control Message Attribute Value PairsTo maximize extensibility while still permitting interoperability, a uniform method for encoding message types and bodies is usedthroughout L2TP. This encoding will be termed AVP (Attribute-ValuePair) in the remainder of this document.Townsley, et al. Standards Track [Page 12]4.1 AVP FormatEach AVP is encoded as:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+|M|H| rsvd | Length | Vendor ID |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Attribute Type | Attribute Value...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+[until Length is reached]... |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+The first six bits are a bit mask, describing the general attributes of the AVP.Two bits are defined in this document, the remaining are reserved for future extensions. Reserved bits MUST be set to 0. An AVP receivedwith a reserved bit set to 1 MUST be treated as an unrecognized AVP. Mandatory (M) bit: Controls the behavior required of animplementation which receives an AVP which it does not recognize. If the M bit is set on an unrecognized AVP within a message associatedwith a particular session, the session associated with this messageMUST be terminated. If the M bit is set on an unrecognized AVP within a message associated with the overall tunnel, the entire tunnel (and all sessions within) MUST be terminated. If the M bit is not set, an unrecognized AVP MUST be ignored. The control message must thencontinue to be processed as if the AVP had not been present.Hidden (H) bit: Identifies the hiding of data in the Attribute Value field of an AVP. This capability can be used to avoid the passing of sensitive data, such as user passwords, as cleartext in an AVP.Section 4.3 describes the procedure for performing AVP hiding.Length: Encodes the number of octets (including the Overall Lengthand bitmask fields) contained in this AVP. The Length may becalculated as 6 + the length of the Attribute Value field in octets. The field itself is 10 bits, permitting a maximum of 1023 octets ofdata in a single AVP. The minimum Length of an AVP is 6. If thelength is 6, then the Attribute Value field is absent.Vendor ID: The IANA assigned "SMI Network Management PrivateEnterprise Codes" [RFC1700] value. The value 0, corresponding toIETF adopted attribute values, is used for all AVPs defined withinthis document. Any vendor wishing to implement their own L2TPextensions can use their own Vendor ID along with private Attribute Townsley, et al. Standards Track [Page 13]values, guaranteeing that they will not collide with any othervendor’s extensions, nor with future IETF extensions. Note that there are 16 bits allocated for the Vendor ID, thus limiting this featureto the first 65,535 enterprises.Attribute Type: A 2 octet value with a unique interpretation acrossall AVPs defined under a given Vendor ID.Attribute Value: This is the actual value as indicated by the Vendor ID and Attribute Type. It follows immediately after the AttributeType field, and runs for the remaining octets indicated in the Length (i.e., Length minus 6 octets of header). This field is absent if the Length is 6.4.2 Mandatory AVPsReceipt of an unknown AVP that has the M-bit set is catastrophic tothe session or tunnel it is associated with. Thus, the M bit shouldonly be defined for AVPs which are absolutely crucial to properoperation of the session or tunnel. Further, in the case where theLAC or LNS receives an unknown AVP with the M-bit set and shuts down the session or tunnel accordingly, it is the full responsibility ofthe peer sending the Mandatory AVP to accept fault for causing annon-interoperable situation. Before defining an AVP with the M-bitset, particularly a vendor-specific AVP, be sure that this is theintended consequence.When an adequate alternative exists to use of the M-bit, it should be utilized. For example, rather than simply sending an AVP with the M- bit set to determine if a specific extension exists, availability may be identified by sending an AVP in a request message and expecting a corresponding AVP in a reply message.Use of the M-bit with new AVPs (those not defined in this document)MUST provide the ability to configure the associated feature off,such that the AVP is either not sent, or sent with the M-bit not set.4.3 Hiding of AVP Attribute ValuesThe H bit in the header of each AVP provides a mechanism to indicate to the receiving peer whether the contents of the AVP are hidden orpresent in cleartext. This feature can be used to hide sensitivecontrol message data such as user passwords or user IDs.The H bit MUST only be set if a shared secret exists between the LAC and LNS. The shared secret is the same secret that is used for tunnel authentication (see Section 5.1.1). If the H bit is set in any Townsley, et al. Standards Track [Page 14]AVP(s) in a given control message, a Random Vector AVP must also bepresent in the message and MUST precede the first AVP having an H bit of 1.Hiding an AVP value is done in several steps. The first step is totake the length and value fields of the original (cleartext) AVP and encode them into a Hidden AVP Subformat as follows:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length of Original Value | Original Attribute Value ...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+... | Padding ...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+Length of Original Attribute Value: This is length of the OriginalAttribute Value to be obscured in octets. This is necessary todetermine the original length of the Attribute Value which is lostwhen the additional Padding is added.Original Attribute Value: Attribute Value that is to be obscured.Padding: Random additional octets used to obscure length of theAttribute Value that is being hidden.To mask the size of the data being hidden, the resulting subformatMAY be padded as shown above. Padding does NOT alter the value placed in the Length of Original Attribute Value field, but does alter thelength of the resultant AVP that is being created. For example, If an Attribute Value to be hidden is 4 octets in length, the unhidden AVP length would be 10 octets (6 + Attribute Value length). After hiding, the length of the AVP will become 6 + Attribute Value length + sizeof the Length of Original Attribute Value field + Padding. Thus, ifPadding is 12 octets, the AVP length will be 6 + 4 + 2 + 12 = 24octets.Next, An MD5 hash is performed on the concatenation of:+ the 2 octet Attribute number of the AVP+ the shared secret+ an arbitrary length random vectorThe value of the random vector used in this hash is passed in thevalue field of a Random Vector AVP. This Random Vector AVP must beplaced in the message by the sender before any hidden AVPs. The same random vector may be used for more than one hidden AVP in the same Townsley, et al. Standards Track [Page 15]message. If a different random vector is used for the hiding ofsubsequent AVPs then a new Random Vector AVP must be placed in thecommand message before the first AVP to which it applies.The MD5 hash value is then XORed with the first 16 octet (or less)segment of the Hidden AVP Subformat and placed in the Attribute Value field of the Hidden AVP. If the Hidden AVP Subformat is less than 16 octets, the Subformat is transformed as if the Attribute Value field had been padded to 16 octets before the XOR, but only the actualoctets present in the Subformat are modified, and the length of theAVP is not altered.If the Subformat is longer than 16 octets, a second one-way MD5 hash is calculated over a stream of octets consisting of the shared secret followed by the result of the first XOR. That hash is XORed with the second 16 octet (or less) segment of the Subformat and placed in the corresponding octets of the Value field of the Hidden AVP.If necessary, this operation is repeated, with the shared secret used along with each XOR result to generate the next hash to XOR the next segment of the value with.The hiding method was adapted from RFC 2138 [RFC2138] which was taken from the "Mixing in the Plaintext" section in the book "NetworkSecurity" by Kaufman, Perlman and Speciner [KPS]. A detailedexplanation of the method follows:Call the shared secret S, the Random Vector RV, and the AttributeValue AV. Break the value field into 16-octet chunks p1, p2, etc.with the last one padded at the end with random data to a 16-octetboundary. Call the ciphertext blocks c(1), c(2), etc. We will also define intermediate values b1, b2, etc.b1 = MD5(AV + S + RV) c(1) = p1 xor b1b2 = MD5(S + c(1)) c(2) = p2 xor b2. .. .. .bi = MD5(S + c(i-1)) c(i) = pi xor biThe String will contain c(1)+c(2)+...+c(i) where + denotesconcatenation.On receipt, the random vector is taken from the last Random VectorAVP encountered in the message prior to the AVP to be unhidden. The above process is then reversed to yield the original value.Townsley, et al. Standards Track [Page 16]。
TLS协议中的会话恢复机制

TLS协议中的会话恢复机制Transport Layer Security(TLS)协议中的会话恢复机制传输层安全(TLS)协议是用于保护网络通信的重要安全协议,它在互联网上广泛使用。
会话恢复机制是TLS协议中的一个重要功能,它允许通信双方在已建立的会话中恢复数据传输,提高通信效率。
本文将详细介绍TLS协议中的会话恢复机制及其在实际应用中的重要性。
一、TLS协议概述TLS协议是在传输层对网络通信进行加密和认证的协议,它基于传输控制协议(TCP)或用户数据报协议(UDP)实现。
TLS协议使用公开密钥加密算法,确保通信的安全性和完整性。
在建立TLS连接时,通信双方将协商加密算法、密钥长度和认证方式等参数,并通过公钥加密机制对会话密钥进行交换,确保通信过程中的数据传输的机密性和完整性。
二、会话恢复机制的作用会话恢复机制是TLS协议中的一个重要功能,它通过利用已建立的TLS会话信息,避免在每次通信时重新建立连接和进行密钥交换,从而提高通信效率。
会话恢复机制的主要作用包括:1. 降低握手延迟:在TLS协议中,握手过程是建立连接和进行密钥协商的重要环节。
在会话恢复机制的支持下,通信双方可以重复使用已建立的TLS会话信息,避免重新进行握手过程,从而降低握手延迟。
2. 减少计算和网络资源消耗:TLS协议在密钥交换和加密解密等过程中需要消耗计算和网络资源。
利用会话恢复机制,在已建立的TLS 会话中重复使用密钥等信息,可以节省计算和网络资源,提高系统性能。
3. 提高用户体验:通过使用会话恢复机制,TLS连接的恢复过程可以更加快速和无缝地进行。
这意味着用户可以更快地访问已经建立的连接,从而提高用户体验和满意度。
三、TLS会话恢复机制的实现TLS协议中的会话恢复机制主要通过会话标识符(Session ID)和会话票据(Session Ticket)两种方式实现。
1. 会话标识符(Session ID)会话标识符是TLS协议中用于唯一标识会话的标识。
AWAF知识点学习

AWAF知识点学习AWAF知识点Data GuardData Guard是在HTTP响应中防⽌铭感数据泄露的,⽐如在HTTP响应中包含了信⽤卡信息、U.S.Social Security number等,或者是⾃定义的信息。
有两种防护⽅式当Policy是Blocking的时候,如果响应中包含了敏感信息,AWAF会拦截这个响应AWAF也可以对敏感信息进⾏加密,只有在Policy是Transparent或者是Bolcking但是Data Guard是Alarm/Learn的时候才会加密,加密的形式是*,并且需要勾选Mask Data可以使⽤⾃定义的Patterns来本地化定义⾝份证信息或电话号4[0-9]{3}-[0-9]{4}-[0-9]{4}-#表⽰以4开头的前⼗⼆位数为敏感数据,AWAF将对其进⾏隐藏#[]表⽰0-9的数字;{}表⽰数的位数Exception Patterns该选项表⽰指定系统认为那些不是铭感数据File Content Detection指定系统是否检查⽂件内容的响应,如果是,哪些类型的⽂件内容被视为敏感数据。
这可以防⽌服务器将您不希望返回给⽤户的⽂件内容传递给⽤户。
Enforcement Mode⽤于指定Data Guard对那些URL进⾏防护Ignore URLs---Data Guard会防护所有的URL,除了列表中的Enforce URLs---Data Guard会防护列表中的URL,即使该URL并不在Security Policy中AWAF将Cookie分为两种,分别是Allowed和EnforcedAllowed类型的Cookie⼀般是Persistent Cookie、Single Sign On Cookie、或者是其他的合法的Cookie。
当这类Cookie背设置为Allow,AWAF会忽略并不会触发告警;Allowed Cookie可以设置Explicit和Wildcard两种Enforced类型的Cookie是在客户端侧不应该被修改的。
一类lsa报文格式 -回复

一类lsa报文格式-回复什么是LSA报文格式?LSA(Link State Advertisement)报文格式是一种用于OSPF(Open Shortest Path First)协议中的报文格式。
OSPF是一种用于路由选择的链路状态协议,它通过交换链路状态信息来构建网络拓扑图,并计算出最短路径。
LSA报文格式是OSPF用于交换链路状态信息的一种规范格式,它包含了路由器或者交换机对周围邻居设备发送的信息。
下面将会逐步介绍LSA报文格式的各个字段以及字段中的信息。
1. 报文头部信息:Reported Link State ID:报告的链路状态标识符,用于唯一地标识链路状态。
Advertising Router:广告路由器,指的是产生该LSA报文的路由器的ID。
Link State Sequence Number:链路状态序列号,用于唯一地标识不同的链路状态。
LSA Age:LSA的年龄,表示该链路状态信息的更新时间。
Options:选项字段,用于指示该LSA报文的特性和功能。
Checksum:校验和,用于验证整个LSA报文的完整性。
Length:报文长度,指的是整个LSA报文的字节长度。
2. 链路描述部分:Link ID:链路ID,用于标识该链路连接的目标设备。
Link Data:链路数据,用于提供与该链路相关的详细信息。
Type:链路类型,用于指示链路的类型,例如点对点连接、网络连接等等。
Metric:链路度量,用于表示链路的开销,即通过该链路达到目标设备所需的代价。
3. 发送者的附加信息:Adjacent Router:邻接路由器,指的是产生该LSA报文的路由器所连接的邻居路由器。
Neighbor ID:邻居ID,用于标识邻居路由器的唯一性。
Interface ID:接口ID,用于标识产生该LSA报文的路由器与邻居路由器之间的接口。
通过以上的介绍,我们可以看出LSA报文格式用于传递OSPF协议中的链路状态信息。
lsa的报文格式 -回复

lsa的报文格式-回复报文是计算机网络中用于传输数据的一种通信格式。
不同的通信协议使用不同的报文格式,其中包括了头部和数据两部分。
本文将以“LSA的报文格式”为主题,详细介绍LSA(链路状态广告)协议中使用的报文格式。
链路状态广告(Link State Advertisement,LSA)是OSPF(开放最短路径优先)协议中用于交换网络拓扑信息的报文格式。
LSA报文通过在网络中的路由器之间传递,用于构建并维护一个网络中的链路状态数据库(Link State Database,LSDB)。
LSDB包含了所有路由器对网络拓扑的理解,以及路由算法用于计算最短路径的基础数据。
LSA报文分为几种不同的类型,每种类型都有自己特定的报文格式。
下面将逐一介绍每种类型的报文格式。
1. 路由器链路状态广告(Router LSA)报文格式路由器LSA用于描述一个路由器的连接情况以及其所连网络的拓扑信息。
该类型的LSA报文格式如下:[ LS Age Options LS Type Link State ID Advertising Router LS Sequence Number LS Checksum Length Link count Link ID Link Data Type TOS Metric ...]报文格式包括以下字段:- LS Age:该LSA报文的年龄,以计时单位表示。
- Options:LSA报文所携带的选项信息,如是否支持多点链接等。
- LS Type:表示该LSA报文的类型,此处为路由器LSA,值为1。
- Link State ID:该LSA的唯一标识符,对于路由器LSA,通常为该路由器的ID。
- Advertising Router:生成并发送该LSA报文的路由器的ID。
- LS Sequence Number:用于确保LSA报文的有序交付,以最新的序列号为准。
- LS Checksum:校验和字段,用于检查报文的完整性。
sftp 消息认证算法

sftp 消息认证算法SFTP(Secure File Transfer Protocol)是一种通过加密保护数据传输安全的文件传输协议。
而消息认证算法(Message Authentication Algorithm)则是在SFTP中用于对传输的消息进行认证,以确保传输的完整性和真实性。
SFTP中常用的消息认证算法包括HMAC(Hash-based Message Authentication Code)算法和MAC(Message Authentication Code)算法。
这些算法通过在消息中添加认证码来保证消息的完整性,并使用预共享密钥进行消息的验证。
HMAC算法是一种基于散列函数的消息认证算法,并且广泛应用于各种网络通信协议中。
它的安全性来源于散列函数的不可逆性和预共享密钥的机密性。
HMAC算法的基本过程如下:1. 预共享密钥生成:通信双方在建立连接之前,需要协商生成一个相同的预共享密钥。
2. 消息分割:待传输的消息被分割成固定长度的数据块。
3. 数据块散列:将每个数据块与预共享密钥一起送入散列函数中进行散列计算。
4. 认证码生成:将所有散列计算得到的结果进行逻辑运算,并生成最终的认证码。
5. 消息传输:将原始消息和认证码一起传输给接收方。
6. 认证码验证:接收方使用相同的预共享密钥对接收到的消息进行计算,并与接收到的认证码进行比较,以验证消息的完整性和真实性。
MAC算法也是一种消息认证算法,但它使用的是对称密钥加密算法,如DES(Data Encryption Standard)或AES(Advanced Encryption Standard)。
MAC算法的基本过程如下:1. 预共享密钥生成:通信双方在建立连接之前,需要协商生成一个相同的预共享密钥。
2. 消息分割:待传输的消息被分割成固定长度的数据块。
3. 数据块加密:将每个数据块与预共享密钥一起送入加密算法中进行加密计算。
4. 认证码生成:将所有加密计算得到的结果进行逻辑运算,并生成最终的认证码。
encrypted clienthello 原理 -回复

encrypted clienthello 原理-回复【encrypted clienthello 原理】一词意味着客户端在与服务器进行通信时,使用了加密的ClientHello消息。
ClientHello消息是TLS/SSL握手过程中的第一个步骤,该过程被用于建立安全连接,以确保通信的机密性和完整性。
在这篇文章中,我们将详细介绍encrypted clienthello的原理,并逐步回答与之相关的问题。
第一部分:TLS/SSL握手过程简介为了更好地理解encrypted clienthello的原理,我们首先需要了解TLS/SSL的握手过程。
TLS(Transport Layer Security)是一种加密协议,用于在互联网上建立安全连接。
SSL(Secure Sockets Layer)是TLS的前身,目前已经过时。
TLS/SSL握手过程包括以下步骤:1. 客户端向服务器发送ClientHello消息,其中包含一些加密套件的列表,客户端支持的TLS/SSL版本号,以及一个随机数。
2. 服务器向客户端发送ServerHello消息,其中包含服务器选择的加密套件、TLS/SSL版本号,以及另一个随机数。
3. 服务器使用其私钥对随机数和其他参数进行加密,并用客户端提供的公钥进行加密,向客户端发送Certificate消息。
4. 客户端使用服务器的公钥解密Certificate消息,并验证服务器的身份和证书。
5. 客户端生成一个“Pre-Master Secret”,用服务器的公钥加密,并发送给服务器。
6. 服务器使用自己的私钥解密“Pre-Master Secret”。
7. 客户端和服务器使用两个随机数和“Pre-Master Secret”来生成“Master Secret”,并从中派生会话密钥、MAC密钥和初始化向量。
8. 握手结束后,客户端和服务器使用这些密钥来加密和验证通信流量。
第二部分:encrypted clienthello的发展背景在TLS/SSL握手过程中,ClientHello消息和Certificate消息通常是明文传输的。
ssh server的算法 -回复

ssh server的算法-回复SSH(Secure Shell)是一种用于安全远程访问和数据传输的协议。
它通过使用加密算法来保护传输过程中的数据安全性。
这篇文章将专注于SSH 服务器的算法,介绍一些常用的算法以及它们在SSH上的应用。
1. 对称加密算法(Symmetric Encryption Algorithm)对称加密算法使用相同的密钥用于加密和解密数据。
最常用的对称加密算法之一是AES(Advanced Encryption Standard),它使用不同的密钥长度(如128位、192位和256位),并且在SSH协议中被广泛采用。
AES 提供了高度的安全性和效率,使得数据在传输过程中难以被破解。
2. 非对称加密算法(Asymmetric Encryption Algorithm)非对称加密算法使用一对密钥(公钥和私钥)用于加密和解密数据。
公钥是公开的,任何人都可以使用它来加密数据。
私钥则被保密,并且只有拥有私钥的人才能解密数据。
在SSH服务器中,最常用的非对称加密算法是RSA(Rivest-Shamir-Adleman)。
当客户端发起SSH连接时,服务器将生成RSA密钥对。
服务器将其公钥发送给客户端,并将私钥存储在服务器上。
之后,客户端会使用服务器的公钥加密随机生成的对称密钥,并发送给服务器。
服务器使用自己的私钥解密对称密钥,然后使用该对称密钥进行后续通信的加密和解密操作。
这种方式既保证了安全性,又提高了效率。
另外,还有一种非对称加密算法是DSA(Digital Signature Algorithm),它主要用于数字签名和验证。
DSA也可以用于SSH连接的身份验证过程。
3. 哈希算法(Hash Algorithm)哈希算法将任意长度的数据转换为固定长度的数据,通常为一串固定长度的数字和字母。
在SSH中,哈希算法常用于生成消息认证码(MAC)和数字签名。
常见的哈希算法包括MD5(Message Digest 5)和SHA-1(Secure Hash Algorithm 1)。
sftp 消息认证算法

sftp 消息认证算法SFTP(Secure File Transfer Protocol)是一种安全的文件传输协议,它在SSH(Secure Shell)上构建。
SFTP使用SSH协议进行身份验证和加密,因此支持多种消息认证算法以确保通信的安全性。
以下是一些常见的SFTP消息认证算法:1. HMAC-SHA-2(HMAC with SHA-2):- SFTP可以使用基于SHA-2系列的HMAC算法,如HMAC-SHA-256和HMAC-SHA-512,来进行消息认证。
这些算法提供了强大的安全性。
2. HMAC-SHA-1:-尽管SHA-1已经被认为是不安全的,但在某些情况下,仍然可能会使用HMAC-SHA-1进行消息认证。
然而,强烈建议使用更安全的算法,如SHA-256或SHA-512。
3. HMAC-MD5:-类似于HMAC-SHA-1,HMAC-MD5也是一种较旧的消息认证算法,不再被推荐用于安全性要求较高的环境。
4. UMAC-64和UMAC-128:- UMAC是一种基于Poly1305的消息认证码算法。
UMAC-64使用64位密钥,而UMAC-128使用128位密钥。
它们提供了高性能和良好的安全性。
5. AES-GCM:- Advanced Encryption Standard Galois/Counter Mode(AES-GCM)是一种组合加密和消息认证码的模式。
它结合了AES加密和GCM认证,提供了高度的安全性和效率。
6. AES-CCM:- Advanced Encryption Standard Counter with Cipher Block Chaining-Message Authentication Code(AES-CCM)也是一种组合加密和消息认证码的模式,类似于AES-GCM。
这些消息认证算法用于验证SFTP通信中传输的数据的完整性,防止数据被篡改。
在配置SFTP 服务器和客户端时,通常可以指定首选的消息认证算法和加密算法。
lsa的报文格式 -回复

lsa的报文格式-回复"LSA的报文格式":介绍与解析链路状态广告报文链路状态广告(Link State Advertisement,LSA)是在链路状态路由协议中用于传输路由信息的关键报文。
它通过交换网络中的路由信息,并最终构建出网络拓扑图,以指导数据包在网络中的传送路径选择。
本文将分步详细介绍LSA的报文格式和其结构,以及解析LSA报文的过程。
一、导引1.1 概述LSA是链路状态路由协议中的一种重要报文,它通过交换路由信息,实现网络拓扑图的建立和路由算法的执行。
其中,OSPF(开放最短路径优先)协议是一种流行的链路状态路由协议,本文以OSPF协议为例,讲解LSA 的报文格式和解析过程。
1.2 目标本文旨在介绍LSA报文的格式和结构,以及如何解析LSA报文获取其中的关键信息。
二、LSA报文格式2.1 头部字段LSA报文通常由两个部分组成——头部字段和主体字段。
头部字段包含以下几个重要的信息:(1)LSA类型:用于标识报文的类型,不同类型的报文具有不同的结构和含义。
(2)广告者ID:表示发送该LSA报文的路由器的ID。
(3)广告版本号:表示当前LSA的版本号,用于区分不同的LSA报文。
(4)LSA报文长度:指示整个LSA报文的长度。
2.2 主体字段主体字段通常包含以下几个重要的信息:(1)连接状态:表示该路由器与其他路由器之间的连接状态,如是否可达、是否故障等。
(2)链路成本:表示该链路的成本,用于计算最优路径。
(3)链路ID:表示与该路由器直接相连的链路的唯一标识符。
(4)链路数据:包含了与链路相关的信息,如链路的带宽、延迟等。
三、LSA报文的解析过程3.1 接收LSA报文路由器在接收到LSA报文后,需要首先解析该报文以获取其中的关键信息。
解析过程如下:(1)解析报文头部字段,获取LSA类型、广告者ID、广告版本号和报文长度等信息。
(2)解析报文主体字段,获取连接状态、链路成本、链路ID和链路数据等信息。
ssl2.0概念 -回复

ssl2.0概念-回复SSL(Secure Sockets Layer)是一种用来保护通信过程中传输的敏感数据安全的加密协议。
SSL 2.0 是SSL 协议的一个早期版本,但由于安全漏洞的存在,已经被现代的安全协议所取代。
在本文中,我们将深入讨论SSL 2.0 的概念、功能和存在的安全问题。
首先,我们来了解一下SSL 协议。
SSL 协议的主要目标是通过使用加密技术来确保在客户端和服务器之间传输的数据的安全性。
它通过在通信开始之前对双方进行身份验证,并使用公钥加密算法对数据进行加密和解密。
SSL 2.0 是SSL 协议的第二个版本,於1995年发布。
与SSL 1.0 相比,SSL 2.0 添加了会话复用和动态密钥分配等功能,提高了性能和安全性。
然而,SSL 2.0 存在许多安全问题。
首先,SSL 2.0 使用了弱的加密算法。
它主要使用了对称密钥加密算法,如RC2 和DES。
这些算法存在较弱的密钥长度和易受到暴力破解的风险。
此外,SSL 2.0 还使用了弱的密钥交换机制,如RSA 密钥交换。
这使得存在中间人攻击(Man-in-the-Middle Attacks)的风险,攻击者可以截获通信内容,甚至篡改数据。
除此之外,SSL 2.0 的握手过程也存在安全问题。
在SSL 2.0 中,客户端和服务器之间的握手不是完全独立的,而是依赖于与先前会话的连接关联。
这种连接复用机制存在安全风险,可能导致一个攻击者能够利用一个已获得的会话来伪装成真正的服务器,从而欺骗客户端。
另外,SSL 2.0 也没有有效的对服务器证书进行验证。
证书验证是SSL 协议的一个重要部分,用于保证连接的双方的身份。
然而,在SSL 2.0 中,证书验证的过程较为薄弱,容易受到中间人攻击的影响。
为了解决这些安全问题,SSL 2.0 逐渐被SSL 3.0 和TLS 1.0 所取代。
SSL 3.0 在设计上克服了SSL 2.0 的一些弱点,并引入了更安全的加密算法和密钥交换机制。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Internet Engineering Task Force (IETF) J. Salowey Request for Comments: 6012 Cisco Systems, Inc. Category: Standards Track T. Petch ISSN: 2070-1721 Engineering Networks Ltd R. Gerhards Adiscon GmbH H. Feng Huaweisymantec Technologies October 2010 Datagram Transport Layer Security (DTLS) Transport Mapping for SyslogAbstractThis document describes the transport of syslog messages over theDatagram Transport Layer Security (DTLS) protocol. It provides asecure transport for syslog messages in cases where a connectionless transport is desired.Status of This MemoThis is an Internet Standards Track document.This document is a product of the Internet Engineering Task Force(IETF). It represents the consensus of the IETF community. It hasreceived public review and has been approved for publication by theInternet Engineering Steering Group (IESG). Further information onInternet Standards is available in Section 2 of RFC 5741.Information about the current status of this document, any errata,and how to provide feedback on it may be obtained at/info/rfc6012.Copyright NoticeCopyright (c) 2010 IETF Trust and the persons identified as thedocument authors. All rights reserved.This document is subject to BCP 78 and the IETF Trust’s LegalProvisions Relating to IETF Documents(/license-info) in effect on the date ofpublication of this document. Please review these documentscarefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e ofthe Trust Legal Provisions and are provided without warranty asdescribed in the Simplified BSD License.Salowey, et al. Standards Track [Page 1]This document may contain material from IETF Documents or IETFContributions published or made publicly available before November10, 2008. The person(s) controlling the copyright in some of thismaterial may not have granted the IETF Trust the right to allowmodifications of such material outside the IETF Standards Process.Without obtaining an adequate license from the person(s) controlling the copyright in such materials, this document may not be modifiedoutside the IETF Standards Process, and derivative works of it maynot be created outside the IETF Standards Process, except to formatit for publication as an RFC or to translate it into languages other than English.Table of Contents1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . 32. Terminology . . . . . . . . . . . . . . . . . . . . . . . . . 33. Security Requirements for Syslog . . . . . . . . . . . . . . . 44. Using DTLS to Secure Syslog . . . . . . . . . . . . . . . . . 45. Protocol Elements . . . . . . . . . . . . . . . . . . . . . . 5 5.1. Transport . . . . . . . . . . . . . . . . . . . . . . . . 5 5.2. Port and Service Code Assignment . . . . . . . . . . . . . 5 5.3. Initiation . . . . . . . . . . . . . . . . . . . . . . . . 5 5.3.1. Certificate-Based Authentication . . . . . . . . . . . 6 5.4. Sending Data . . . . . . . . . . . . . . . . . . . . . . . 6 5.4.1. Message Size . . . . . . . . . . . . . . . . . . . . . 75.5. Closure . . . . . . . . . . . . . . . . . . . . . . . . . 76. Congestion Control . . . . . . . . . . . . . . . . . . . . . . 87. Security Policies . . . . . . . . . . . . . . . . . . . . . . 88. IANA Considerations . . . . . . . . . . . . . . . . . . . . . 89. Security Considerations . . . . . . . . . . . . . . . . . . . 9 9.1. DTLS Renegotiation . . . . . . . . . . . . . . . . . . . . 9 9.2. Message Loss . . . . . . . . . . . . . . . . . . . . . . . 9 9.3. Private Key Generation . . . . . . . . . . . . . . . . . . 99.4. Trust Anchor Installation and Storage . . . . . . . . . . 910. Acknowledgements . . . . . . . . . . . . . . . . . . . . . . . 1011. References . . . . . . . . . . . . . . . . . . . . . . . . . . 10 11.1. Normative References . . . . . . . . . . . . . . . . . . . 10 11.2. Informative References . . . . . . . . . . . . . . . . . . 11 Salowey, et al. Standards Track [Page 2]1. IntroductionThe syslog protocol [RFC5424] is designed to run over differenttransports for different environments. This document defines thetransport of syslog messages over the Datagram Transport LayerSecurity (DTLS) protocol [RFC4347].The Datagram Transport Layer Security (DTLS) protocol [RFC4347] isdesigned to meet the requirements of applications that need securedatagram transport. DTLS has been mapped onto different transports, including UDP [RFC0768] and the Datagram Congestion Control Protocol (DCCP) [RFC4340]. This memo defines both options, namely syslog over DTLS over UDP, and syslog over DTLS over DCCP.2. TerminologyThe following definitions from [RFC5424] are used in this document:o An "originator" generates syslog content to be carried in amessage.o A "collector" gathers syslog content for further analysis.o A "relay" forwards messages, accepting messages from originatorsor other relays, and sending them to collectors or other relays.o A "transport sender" passes syslog messages to a specifictransport protocol.o A "transport receiver" takes syslog messages from a specifictransport protocol.This document adds the following definitions:o A "DTLS client" is an application that can initiate a DTLS Client Hello to a server.o A "DTLS server" is an application that can receive a DTLS ClientHello from a client and reply with a Server Hello.The key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT","SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this document are to be interpreted as described in [RFC2119].Salowey, et al. Standards Track [Page 3]3. Security Requirements for SyslogThe security requirements for the transport of syslog messages arediscussed in Section 2 of [RFC5425]. These also apply to thisspecification.The following secondary threat is also considered in this document:o Denial of service is discussed in [RFC5424], which states that an attacker may send more messages to a transport receiver than thetransport receiver could handle. When using a secure transportprotocol handshake, an attacker may use a spoofed IP source toengage the server in a cryptographic handshake to deliberatelyconsume the server’s resources.4. Using DTLS to Secure SyslogDTLS can be used as a secure transport to counter all the primarythreats to syslog described in [RFC5425]:o Confidentiality to counter disclosure of the message contents.o Integrity checking to counter modifications to a message on a hop- by-hop basis.o Server or mutual authentication to counter masquerade.In addition, DTLS also provides:o A cookie exchange mechanism during handshake to counter Denial of Service attacks.o A sequence number in the header to counter replay attacks.Note: This secure transport (i.e., DTLS) only secures syslogtransport in a hop-by-hop manner, and is not concerned with thecontents of syslog messages. In particular, the authenticatedidentity of the transport sender (e.g., subject name in thecertificate) is not necessarily related to the HOSTNAME field of the syslog message. When authentication of syslog message origin isrequired, [RFC5848] can be used.Salowey, et al. Standards Track [Page 4]5. Protocol Elements5.1. TransportDTLS can run over multiple transports. Implementations of thisspecification MUST support DTLS over UDP and SHOULD support DTLS over DCCP [RFC5238]. Transports such as UDP or DCCP do not providesession multiplexing and session demultiplexing. In such cases, the application implementer provides this functionality by mapping aunique combination of the remote address, remote port number, localaddress, and local port number to a session.Each syslog message is delivered by the DTLS record protocol, whichassigns a sequence number to each DTLS record. Although the DTLSimplementer may adopt a queue mechanism to resolve reordering, it may not assure that all the messages are delivered in order when mapping on the UDP transport.When DTLS runs over an unreliable transport, such as UDP, reliability is not provided. With DTLS, an originator or relay may not realizethat a collector has gone down or lost its DTLS connection state, so messages may be lost.Syslog over DTLS over TCP MUST NOT be used. If a secure transport is required with TCP, then the appropriate security mechanism is syslog over Transport Layer Security (TLS) as described in [RFC5425].5.2. Port and Service Code AssignmentA syslog transport sender is always a DTLS client, and a transportreceiver is always a DTLS server.The UDP and DCCP port 6514 has been allocated as the default port for syslog over DTLS as defined in this document. The service code SYLG (1398361159) has been assigned to syslog.5.3. InitiationThe transport sender initiates a DTLS connection by sending a DTLSClient Hello to the transport receiver. Implementations MUST support the denial of service countermeasures defined by DTLS. When thesecountermeasures are used, the transport receiver responds with a DTLS Hello Verify Request containing a cookie. The transport senderresponds with a DTLS Client Hello containing the received cookie,which initiates the DTLS handshake. The transport sender MUST NOTsend any syslog messages before the DTLS handshake has successfullycompleted.Salowey, et al. Standards Track [Page 5]Implementations MUST support DTLS 1.0 [RFC4347] and MUST support the mandatory to implement cipher suite, which isTLS_RSA_WITH_AES_128_CBC_SHA as specified in [RFC5246]. Ifadditional cipher suites are supported, then implementations MUST NOT negotiate a cipher suite that employs NULL integrity orauthentication algorithms.Where privacy is REQUIRED, then implementations must either negotiate a cipher suite that employs a non-NULL encryption algorithm or elseachieve privacy by other means, such as a physically secured network. However, as [RFC5424], Section 8, points out, "In most cases, passing clear-text messages is a benefit to the operations staff if they are sniffing the packets from the wire", and so where privacy is not arequirement, then it is advantageous to use a NULL encryptionalgorithm.5.3.1. Certificate-Based AuthenticationThe mandatory to implement cipher suites for DTLS use certificates[RFC5280] to authenticate peers. Both the syslog transport sender(DTLS client) and the syslog transport receiver (DTLS server) MUSTimplement certificate-based authentication. This consists ofvalidating the certificate and verifying that the peer has thecorresponding private key. The latter part is performed by DTLS. To ensure interoperability between clients and servers, the methods for certificate validation defined in Sections 4.2.1 and 4.2.2 of[RFC5425] SHALL be implemented.Both transport receiver and transport sender implementations MUSTprovide means to generate a key pair and self-signed certificate incase a key pair and certificate are not available through anothermechanism.The transport receiver and transport sender SHOULD provide mechanisms to record the certificate or certificate fingerprint used by theremote endpoint for the purpose of correlating an identity with thesent or received data.5.4. Sending DataAll syslog messages MUST be sent as DTLS "application data". It ispossible that multiple syslog messages be contained in one DTLSrecord, or that a syslog message be transferred in multiple DTLSrecords. The application data is defined with the following ABNF[RFC5234] expression:Salowey, et al. Standards Track [Page 6]APPLICATION-DATA = 1*SYSLOG-FRAMESYSLOG-FRAME = MSG-LEN SP SYSLOG-MSGMSG-LEN = NONZERO-DIGIT *DIGITSP = %d32NONZERO-DIGIT = %d49-57DIGIT = %d48 / NONZERO-DIGITSYSLOG-MSG is defined in the syslog [RFC5424] protocol.5.4.1. Message SizeThe message length is the octet count of the SYSLOG-MSG in theSYSLOG-FRAME. A transport receiver MUST use the message length todelimit a syslog message. There is no upper limit for a messagelength per se. As stated in [RFC4347], a DTLS record MUST NOT spanmultiple datagrams. When mapping onto different transports, DTLS has different record size limitations. For UDP, see Section 3.2 of[RFC5426]. For DCCP, the application implementer SHOULD determinethe maximum record size allowed by the DTLS protocol running overDCCP, as specified in [RFC4340]. The message size SHOULD NOT exceed the DTLS maximum record size limitation of 2^14 bytes. To beconsistent with [RFC5425], in establishing a baseline forinteroperability, this specification requires that a transportreceiver MUST be able to process messages with a length up to andincluding 2048 octets. Transport receivers SHOULD be able to process messages with lengths up to and including 8192 octets.See Appendix A.2 of [RFC5424] for implementation guidance on message length, including fragmentation.5.5. ClosureA transport sender MUST close the associated DTLS connection if theconnection is not expected to deliver any syslog messages later. It MUST send a DTLS close_notify alert before closing the connection. A transport sender (DTLS client) MAY choose to not wait for thetransport receiver’s close_notify alert and simply close the DTLSconnection. Once the transport receiver gets a close_notify from the transport sender, it MUST reply with a close_notify.When no data is received from a DTLS connection for a long time(where the application decides what "long" means), a transportreceiver MAY close the connection. The transport receiver (DTLS Salowey, et al. Standards Track [Page 7]server) MUST attempt to initiate an exchange of close_notify alertswith the transport sender before closing the connection. Transportreceivers that are unprepared to receive any more data MAY close the connection after sending the close_notify alert.Although closure alerts are a component of TLS and so of DTLS, they, like all alerts, are not retransmitted by DTLS and so may be lostover an unreliable network.6. Congestion ControlBecause syslog can generate unlimited amounts of data, transferringthis data over UDP is generally problematic, because UDP lackscongestion control mechanisms. Congestion control mechanisms thatrespond to congestion by reducing traffic rates and establishing adegree of fairness between flows that share the same path are vitalto the stable operation of the Internet (see [RFC2914] and[RFC5405]).DCCP has congestion control. If DCCP is available, syslog over DTLS over DCCP is RECOMMENDED in preference to syslog over DTLS over UDP. Implementations of syslog over DTLS over DCCP MUST support Congestion Control Identifier (CCID) 3 and SHOULD support CCID 2 to ensureinteroperability.The congestion control considerations from Section 4.3 of [RFC5426]also apply to syslog over DTLS over UDP.7. Security PoliciesSyslog transport over DTLS has been designed to minimize the security and operational differences for environments where both syslog overTLS [RFC5425] and syslog over DTLS are supported. The securitypolicies for syslog over DTLS are the same as those described in[RFC5425], and all the normative requirements of Section 5 of[RFC5425] apply.8. IANA ConsiderationsIANA has assigned a registered UDP and DCCP port number for syslogover DTLS. The values are the same as for syslog over TLS. That is, the registry has been updated as follows:syslog-tls 6514/udp syslog over DTLS [RFC6012]syslog-tls 6514/dccp syslog over DTLS [RFC6012]Salowey, et al. Standards Track [Page 8]IANA has assigned the service code SYLG to syslog for use with DCCP. The allocation in the Service Code subregistry of the DatagramCongestion Control Protocol (DCCP) Parameters registry is as follows: 1398361159 SYLG Syslog Protocol [RFC6012]9. Security ConsiderationsThe security considerations in [RFC4347], [RFC5246], [RFC5425], and[RFC5280] apply to this document.9.1. DTLS RenegotiationTLS and DTLS renegotiation may be vulnerable to attacks described in [RFC5746]. Although RFC 5746 provides a fix for some of the issues, renegotiation can still cause problems for applications sinceconnection security parameters can change without the applicationknowing it. Therefore it is RECOMMENDED that renegotiation bedisabled for syslog over DTLS. If renegotiation is allowed, then the specification in RFC 5746 MUST be followed, and the implementationMUST make sure that the connection still has adequate security andthat any identities extracted from client and server certificates do not change during renegotiation.9.2. Message LossThe transports described in this document are unreliable. It ispossible for messages to be lost or removed by an attacker withoutthe knowledge of the receiver. [RFC5424] notes that implementers who wish a lossless stream should be using tls/tcp as their transport.In addition, the use of signed syslog messages [RFC5848] can alsoprovide an indication of message loss.9.3. Private Key GenerationTransport receiver and transport sender implementations oftengenerate their own key pairs. An inadequate random number generator (RNG) or an inadequate pseudo-random number generator (PRNG) togenerate these keys can result in little or no security. See[RFC4086] for random number generation guidance.9.4. Trust Anchor Installation and StorageTrust anchor installation and storage is critical. Transmission of a trust anchor, especially self-signed certificates used as trustanchors, from transport receiver to transport sender for installation requires one or more out-of-band steps. Care must be taken to ensure the installed trust anchor is in fact the correct trust anchor. The Salowey, et al. Standards Track [Page 9]fingerprint mechanism mentioned in Section 5.3.1 can be used by thetransport sender to ensure the transport receiver’s self-signedcertificate is properly installed. Trust anchor information must be securely stored. Changes to trust anchor information can causeacceptance of certificates that should be rejected.10. AcknowledgementsThe authors would like to thank Wes Hardaker for his review of thisproposal and for contributing his valuable suggestions on the use of DTLS. Thanks also to Pasi Eronen, David Harrington, Chris Lonvick,Eliot Lear, Anton Okmyanskiy, Juergen Schoenwaelder, RichardGraveman, the members of the syslog working group, and the members of the IESG for their review, comments, and suggestions.11. References11.1. Normative References[RFC0768] Postel, J., "User Datagram Protocol", STD 6, RFC 768,August 1980.[RFC2119] Bradner, S., "Key words for use in RFCs to IndicateRequirement Levels", BCP 14, RFC 2119, March 1997.[RFC4340] Kohler, E., Handley, M., and S. Floyd, "DatagramCongestion Control Protocol (DCCP)", RFC 4340, March 2006. [RFC4347] Rescorla, E. and N. Modadugu, "Datagram Transport LayerSecurity", RFC 4347, April 2006.[RFC5234] Crocker, D. and P. Overell, "Augmented BNF for SyntaxSpecifications: ABNF", STD 68, RFC 5234, January 2008.[RFC5238] Phelan, T., "Datagram Transport Layer Security (DTLS) over the Datagram Congestion Control Protocol (DCCP)",RFC 5238, May 2008.[RFC5246] Dierks, T. and E. Rescorla, "The Transport Layer Security (TLS) Protocol Version 1.2", RFC 5246, August 2008.[RFC5280] Cooper, D., Santesson, S., Farrell, S., Boeyen, S.,Housley, R., and W. Polk, "Internet X.509 Public KeyInfrastructure Certificate and Certificate Revocation List (CRL) Profile", RFC 5280, May 2008.[RFC5424] Gerhards, R., "The Syslog Protocol", RFC 5424, March 2009. Salowey, et al. Standards Track [Page 10][RFC5425] Miao, F., Ma, Y., and J. Salowey, "Transport LayerSecurity (TLS) Transport Mapping for Syslog", RFC 5425,March 2009.[RFC5426] Okmianski, A., "Transmission of Syslog Messages over UDP", RFC 5426, March 2009.[RFC5746] Rescorla, E., Ray, M., Dispensa, S., and N. Oskov,<"Transport Layer Security (TLS) Renegotiation Indication Extension", RFC 5746, February 2010.11.2. Informative References[RFC2914] Floyd, S., "Congestion Control Principles", BCP 41,RFC 2914, September 2000.[RFC4086] Eastlake, D., Schiller, J., and S. Crocker, "RandomnessRequirements for Security", BCP 106, RFC 4086, June 2005. [RFC5405] Eggert, L. and G. Fairhurst, "Unicast UDP Usage Guidelines for Application Designers", BCP 145, RFC 5405,November 2008.[RFC5848] Kelsey, J., Callas, J., and A. Clemm, "Signed SyslogMessages", RFC 5848, May 2010.Salowey, et al. Standards Track [Page 11]Authors’ AddressesJoseph SaloweyCisco Systems, Inc.2901 3rd Ave.Seattle, WA 98121USAEMail: jsalowey@Tom PetchEngineering Networks Ltd18 Parkwood CloseLymm, Cheshire WA13 0NQUKEMail: tomSecurity@Rainer GerhardsAdiscon GmbHMozartstrasse 21Grossrinderfeld, BW 97950GermanyEMail: rgerhards@Hongyan FengHuaweisymantec Technologies20245 Stevens Creek Blvd.Cupertino, CA 95014EMail: fhyfeng@Salowey, et al. Standards Track [Page 12]。
