7506E与CISCO交换机MSTP协议对接配置
MSTP协议配置

步骤3 exit 退出VLAN配置模式
使能MSTP
使能MSTP的配置步骤
步骤1 config spanning-tree 进入spanning-tree配置模式
步骤2 Spanning-tree mode mst 配置mst工作模式
1.1.9 设置MSTP使能
接口配置
MSTP在只二层接口上起作用,包括普通以太网和Trunk端口,以太网和Trunk缺省都为二层接口。当用户希望使能某以太网或trunk的二层转发功能,以使其参与生成树计算时,可以进行以下配置:
MSTP在二层接口上的配置步骤
步骤1 interface ethernet 进入以太网接口
1.1.7 设置端口non-stp特性
MSTP可以将某些端口设置为不参与协议计算的端口,其方法是设置non-stp属性。
non-stp属性配置步骤
步骤1 config spanning-tree 进入spanning-tree配置模式并配置生成树模式
步骤2 spanning-tree port [none-stp] [yes|no] {}*1 配置端口是否参加STP运算,端口不参加STP运算后,处于Forward状态。
Maximum-age:报文最大的生存周期;
Max-hops:MST域内报文的最大生存周期。
下面说明MST模式接口的时间参数配置:
设置时间参数配置步骤
步骤1 config spanning-tree 进入spanning-tree配置模式
步骤2 Spanning-tree mode mst 配置mst工作模式
H3C_S7506E维护操作管理守则

精心整理H3C_S7506E维护操作手册配置举例:1、配置设备主机名如:sysnameH3C_S7506E2、3如:4如:5如:6如:7如:authorization-attributelevel38、配置将用户名admin及密码abc应用于telnet登录验证如:service-typetelnet9、开启telnet如:telnetserverenable10、配置E0/0接口描述如:descriptionto_G1/0/1_1.1.1.111、配置E0/0接口IP地址(广域网口IP地址)如:ipaddress2.2.2.212、配置E0/0接口为全双工状态如:13如:14如:15如:16如:17如:18如:19、配置环回地址如:ipaddress3.3.3.25520、配置VLAN端口如:interfaceVlan-interface121、配置VLAN接口的描述如:descriptionServer22、配置VLAN端口IP地址如:ipaddress3.3.3.1.023创建备份组并配置虚拟IP地址如:vrrpvrid1virtual-ip3.3.3.3 24、配置交换机在备份组中的优先级如:25如:26如:27如:2829如:30如:area 0.0.0.1network0.0.0.3network1.1.1.00.0.0.25531、设置OSPF链路开销参考值10000 bandwidth-reference1000032、将该OSPF区域设置为完全末梢区如:stubno-summary33、OSPF的开销如:ospfcost2034、开启SNMP代理如:35如:36如:37如:38如:39如:40如:snmp-agenttrapqueue-size500 41、配置SNMP陷阱报文生存时间如:snmp-agenttraplife60042、配置远程登录接口如:user-interfacevty0443、配置远程登录使用用户名及密码验证。
S7506E三层交换机配置

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991supervlansubvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator andif-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan#dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0 gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0 gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0 gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0#interface Vlan-interface30#interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227mirroring-group 2 monitor-port #interface GigabitEthernet3/0/5 port access vlan 3901qos apply policy kefang inbound #interface GigabitEthernet3/0/6 port access vlan 8#interface GigabitEthernet3/0/7 port access vlan 3999description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enable#interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound##interface GigabitEthernet3/0/32 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/33 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound ##interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkinterface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkinterface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2 #snmp-agent。
MSTP以太业务不同厂家设备互通配置参考

结合中央级传输骨干网业务开通模式及电路开通中出现的问题,为提高中央级传输骨干网业务开通效率,减少各地方不同设备厂家MSTP传输设备与中央级传输骨干网阿尔卡特MSTP传输设备间的互通配置问题,结合?国家电子政务网络中央级传输骨干网业务开通配置技术标准?及几次全国电路组网开通测试中获取的珍贵经历,再次明确中央级传输骨干网不同厂家间MSTP设备互通的配置要求,愿能为电路开通及设备选择提供帮助。
一、一样厂家或不同厂家间设备互通必须配置及调整的内容〔一〕开销字节1.J0、J1、J2字节J0、J1、J2字节应配置为15个连续的“0”〔ASCII值〕。
2.C2字节假设采用VC3、VC4虚级联,C2字节要设置为“0x1B〞。
3.V5字节假设采用VC12虚级联,V5字节的b5、b6、b7应配置为“101〞,K4复帧的b12-b19应设为“0000 1101〞(0D)。
或理解为V5字节的应发和应收都应为“0x0D〞。
〔二〕内部端口LCAS状态中央级传输骨干网电路要求LCAS设置在“使能〞状态,地方用户端MSTP设备需检查LCAS的状态,并设置在“使能〞〔或开启〕状态。
〔三〕外部端口工作模式以太端口工作模式需依据地方用户端网络设备的端口进展调整,一般要配置为100M全双工模式二、一样厂家或不同厂家间设备互通需核对、检查内部端口封装映射的设置内容1.映射协议选择:GFP2.扰码选择:X43+13.检验字段长途:无4.扩展头选项:无三、各厂家设备互通应注意的内容中央级传输骨干网用户中心节点一般采用阿尔卡特1660SM设备,因此各地方设备应分别满足与该设备的互通要求,结合?国家电子政务网络中央级传输骨干网业务开通配置技术标准?,汇总电路全程测试中发现的问题,分别说明如下。
(一)阿尔卡特1642与阿尔卡特1660互通需注意的内容1.阿尔卡特1642工作模式应配置为:ETS方式〔透传〕。
2.阿尔卡特1642 J2字节1642默认J2字节为alcatel, 必须调整为15个连续的“0”〔ASCII值〕。
S7506E设备参数
支持流量整形和流量监管
MPLS特性
支持L3VPN:支持跨域MPLS VPN(Option1/2/3)、嵌套MPLS VPN、支持分层PE(HoPE)、CE双归属、MCE、多角色主机、GRE隧道等;支持L2VPN:Martini、Kompella、CCC和SVC方式;支持MPLS TE、RSVP TE
安全特性
支持IP+MAC+PORT任意组合的绑定,支持非法帧报文过滤,用户分级管理和口令保护,支持端口隔离,支持SSH,支持SNMPv3网管
★可靠性
支持VRRP,RRPP,Ethernet OAM(802.3ah),支持Graceful Restart for OSPF/BGP/IS-IS
设备管理
SNMP V1/V2/V3;RMON1/2/3/9;支持sFlow流量统计,Syslog;支持WEB网管,支持MIB-II;中文图形化管理
QOS
优先级队列调度:每端口支持8个优先级队列,3个丢弃优先级,支持SP、WRR、CBWFQ队列调度算法,支持WRED拥塞避免算法,支持流量整形,支持802.1P,DSCP/TOS优先级和重新标记能力,支持基于时间段的流分类和QoS控制能力;支持标准和扩展ACL,基于VLAN的ACL;支持VLAN ACL和IPv6 ACL;每板ACL条目数>=4000条
★虚拟化特性
支持H3C IRF2技术或Cisco VSS技术,将多台物理设备虚拟化为一台逻辑设备,虚拟组内可以实现一致的转发表项,统一的管理,跨物理设备的链路聚合
支持4台设备的虚拟化
支持至少三种以上分裂检测功能
支持远距离虚拟化,距离可达70km
S7506E设备参数

要求设备采用业务承载母板与接口子卡分离的设计,提高设备可扩展性
★总插槽数
≥4
★业务插槽数
配置主控引擎冗余后,业务插槽数(大槽)>=2,业务子卡槽位数最大支持8
★交换容量
≥240G
★整机包转发率
≥48Mpps
系统可靠性
支持双主控,主备切换“零丢包”
关键部件冗余
支持主控引Байду номын сангаас、电源等关键部件冗余备份
关键部件冗余支持主控板电源模块冗余可支持业务板卡类型防火墙业务板入侵防御系统板无线控制器业务板负载均衡业务板应用控制网关业务板网络流量分析业务板sslvpn业务业务板异常流量检测业务板异常流量清洗业务板虚拟化特性支持h3cirf2技术或ciscovss技术将多台物理设备虚拟化为一台逻辑设备虚拟组内可以实现一致的转发表项统一的管理跨物理设备的链路聚合支持4台设备的虚拟化支持至少三种以上分裂检测功能支持远距离虚拟化距离可达70km提供相关专利证明文件需提供重庆本地相关应用案例不少于3个
支持基于端口、MAC地址、IP地址、IP优先级、DSCP优先级、TCP/UDP端口号、协议类型等方式的流分类;
支持流量整形和流量监管
MPLS特性
支持L3VPN:支持跨域MPLS VPN(Option1/2/3)、嵌套MPLS VPN、支持分层PE(HoPE)、CE双归属、MCE、多角色主机、GRE隧道等;支持L2VPN:Martini、Kompella、CCC和SVC方式;支持MPLS TE、RSVP TE
★资质认证
提供工信部(原信产部)IPv4、IPv6入网证书,提供IPv4、IPv6检验报告,为了保证设备软件的合法性,必须提供中华人民共和国国家版权局颁发的计算机软件著作权登记证书
H3C_S7506E维护操作手册

H3C_S7506E维护操作手册配置举例:1、配置设备主机名如:sysnameH3C_S7506E2、配置Routerid如:routerid1.1.1.13、配置vlan1的描述如:vlan1descriptiongateway4、删除默认用户admin如:undolocal-useradmin5、创建本地用户admin如:local-useradmin6、配置ds用户的密码为密文加密的abc如:passwordcipherabc7、配置使用用户名admin及密码abc登录之后的用户级别为最高的3级如:authorization-attributelevel38、配置将用户名admin及密码abc应用于telnet登录验证如:service-typetelnet9、开启telnet如:telnetserverenable10、配置E0/0接口描述如:descriptionto_G1/0/1_1.1.1.111、配置E0/0接口IP地址(广域网口IP地址)如:ipaddress2.2.2.212、配置E0/0接口为全双工状态如:duplexfull13、配置E0/0接口速率为1000M如:speed100014、配置E0/0接口的OSPF为点对点模式如:ospfnetwork-typep2p15、开启interfaceVlan-interface143接口的OSPF的bfd如:ospfbfdenable16、配置VLAN1接口的描述如:descriptiongateway17、配置interfaceVlan-interface1接口的IP地址(局域网网关IP地址)如:ipaddress3.3.3.25218、配置环回接口0如:interfaceLoopBack019、配置环回地址如:ipaddress3.3.3.252.25520、配置VLAN端口如:interfaceVlan-interface121、配置VLAN接口的描述如:descriptionServer22、配置VLAN端口IP地址如:ipaddress3.3.3.1.023创建备份组并配置虚拟IP地址如:vrrpvrid1virtual-ip3.3.3.324、配置交换机在备份组中的优先级如:vrrpvrid1priority12025、配置备份组中交换机的抢占延迟时间如:vrrpvrid1preempt-modetimerdelay6026、配置链路聚合创建interfaceBridge-Aggregation1如:interfaceBridge-Aggregation127、配置interfaceBridge-Aggregation1端口类型如:portlink-typetrunk28、配置MSTPstpregion-configuration//进入MST域视图region-nameabc//配置MST域的域名instance1vlan1to23//配置多生成树实例和VLAN的映射关系instance2vlan4activeregion-configuration//激活MST域的配置stpinstance1rootsecondary//配置MST1的根桥29、启用进程号为1的OSPF协议如:ospf130、在相应area中发布广域网及局域网地址如:area 0.0.0.1network0.0.0.3network1.1.1.00.0.0.25531、设置OSPF链路开销参考值10000bandwidth-reference1000032、将该OSPF区域设置为完全末梢区如:stubno-summary33、OSPF的开销如:ospfcost2034、开启SNMP代理如:snmp-agent35、配置SNMP的只读属性为abc如:snmp-agentcommunityreadabc36、配置SNMP的读写属性为abc如:snmp-agentcommunitywriteabc37、配置SNMP代理发送的信息的版本为适应所有版本如:snmp-agentsys-infoversionall38、开启SNMP陷阱报文如:snmp-agenttrapenable39、配置SNMP陷阱报文发往5.5.5.5,且其安全名称为abc如:snmp-agenttarget-hosttrapaddressudp-domain5.5.5.5paramssecuritynameabc 40、配置SNMP队列长度如:snmp-agenttrapqueue-size50041、配置SNMP陷阱报文生存时间如:snmp-agenttraplife60042、配置远程登录接口如:user-interfacevty0443、配置远程登录使用用户名及密码验证。
MSTP配置

MSTP配置MSTP配置mstp配置包括:配置交换机的mst域指定交换机为根桥或备份根桥配置mstp的工作模式配置交换机的bridge优先级置mst域的最大跳数配置交换网络的网络直径配置交换机的时间参数配置特定交换机的超时时间因子配置端口的最大发送速率配置端口为边缘端口或者非边缘端口配置端口的path cost配置端口的优先级配置端口是否与点对点链路相连配置端口的mcheck变量配置交换机的保护功能开启/关闭设备mstp特性开启/关闭端口mstp特性配置vlan列表与生成树实例的映射关系开启单端口环路检测特性配置设备支持标准mstp或私有mstp报文格式特性只有开启设备mstp特性后其他配置才能生效。
在启动mstp之前,可以配置设备或以太网端口的相关参数;启动mstp后,这些参数将生效;mstp关闭后,这些配置参数仍被保留;当mstp重新启动后,这些参数仍将生效。
未生效的域参数可以使用check region-configuration命令显示;在mstp未启动前配置的其他参数可以使用display current-configuration命令来显示;启动后的mstp参数可以使用相关的display命令显示,可以参考本章的“mstp显示和调试”章节。
当gvrp和mstp同时在交换机上启动时,gvrp报文将沿着生成树实例cist进行传播。
因此在gvrp和mstp同时在交换机上启动的情况下,如果用户希望通过gvrp在网络中发布某个vlan,则用户在配置mstp的vlan映射表时要保证把这个vlan映射到cist上。
cist即生成树实例0。
1.2.1 配置交换机的mst域交换机属于哪个mst域由域名、vlan映射表、mstp修订级别配置决定。
用户可以通过下面的配置过程将当前交换机划分在一个特定的mst域内。
1. 进入mst域视图请在系统视图下进行下列配置。
2. 配置mst域的参数请在mst域视图下进行下列配置。
S7506E三层交换机配置上课讲义

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991subvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0 gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0 gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1##interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7port access vlan 3999description to UTM-200_G 0/0qos apply policy kefang inbound#interface GigabitEthernet3/0/8port access vlan 8qos apply policy kefang inbound#interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/33port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/34port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound#interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47 port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound #interface GigabitEthernet3/0/48 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/13port link-type trunkqos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunk#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunk#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253 ip route-static 10.12.41.0 255.255.255.0 192.168.30.253 ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2。
思科交换机vrrpmstp配置实例

思科交换机vrrpmstp配置实例一、组网需求1、witcha、witchb选用两台锐捷的5750;witchc、hwichd选用锐捷的3750和37602、全网共有两个业务vlan,为vlan10、vlan203、Switcha、witchb都分别对两vlan起用两vrrp组,实现两组的业务的负载分担和备份。
4、Switcha、witchb、witchc、witchd都起用mtp多生成数协议,并且所有设备都属于同一个mt域,且实例映射一致(vlan10映射实例1、vlan20映射实例2其他vlan映射默认实例0)。
5、Vlan10业务以witcha为根桥;vlan20业务以witchb为根桥;实现阻断网络环路,并能实现不同vlan数据流负载分担功能。
二、组网图三、配置步骤Switcha配置:1#howrunBuildingconfiguration...Currentconfiguration:1651byte!verionRGNOS10.2.00(2),Releae(29287)(TueDec2520:39:14CST2007-ngcf49)hotname1co-operateenable!!!vlan1!vlan10!vlan20!!noervicepaword-encryption!panning-tree开启生成树(默认为mtp)panning-treemtconfiguration进入mt配置模式reviion1指定MSTreviionnumber为1nameregion1指定mt配置名称intance0vlan1-9,11-19,21-4094缺省情况下vlan都属于实例0intance1vlan10手工指定vlan10属于实例1intance2vlan20手工指定vlan20属于实例2panning-treemt1priority0指定实例1的优先级为0(为根桥)panning-treemt2priority4096指定实例2的优先级为4096interfaceGigabitEthernet0/1witchportaccevlan10配置g0/1属于vlan10! interfaceGigabitEthernet0/2witchportaccevlan20配置g0/2属于vlan20!interfaceGigabitEthernet0/3!..interfaceGigabitEthernet0/24设置g0/24为trunk接口且允许vlan10/20通过witchportmodetrunk!interfaceVLAN10创建vlan10vi接口ipaddre192.168.10.1255.255.255.0配置ip地址vrrp1priority120配置vrrp组1优先级为120vrrp1ip192.168.10.254配置vrrp组1虚拟ip地址为192.168.10.254!interfaceVLAN20创建vlan20vi接口ipaddre192.168.20.1255.255.255.0配置ip地址vrrp2ip192.168.20.254配置vrrp组2虚拟ip地址为192.168.20.254默认vrrp组的优先级为100默认不显示!linecon0linevty04login1#howvlanVLANNameStatuPort-------------------------------------------------------------------------------1VLAN0001STATICGi0/3,Gi0/4,Gi0/5,Gi0/6Gi0/7,Gi0/8,Gi0/9,Gi0/10Gi0/11,Gi0/12,Gi0/13,Gi0/14Gi0/15,Gi0/16,Gi0/17,Gi0/18Gi0/19,Gi0/20,Gi0/21,Gi0/22Gi0/23,Gi0/2410VLAN0010STATICGi0/1,Gi0/2420VLAN0020STATICGi0/2,Gi0/24Switchb配置:2#howrunBuildingconfiguration...Currentconfiguration:1607byte!verionRGNOS10.2.00(2),Releae(27932)(ThuDec1310:32:09CST2007-ngcf31)hotname2!!!vlan1!vlan10!vlan20!!noervicepaword-encryption!panning-treepanning-treemtconfigurationreviion1nameregion1intance0vlan1-9,11-19,21-4094intance1vlan10intance2vlan20panning-treemt1priority4096panning-treemt2priority0interfaceGigabitEthernet0/1witchportaccevlan10!interfaceGigabitEthernet0/2witchportaccevlan20!..interfaceGigabitEthernet0/24witchportmodetrunk! interfaceVLAN10ipaddre192.168.10.2255.255.255.0vrrp1ip192.168.10.254!interfaceVLAN20ipaddre192.168.20.2255.255.255.0vrrp2priority120vrrp2ip192.168.20.254!linecon0linevty04login!!end2#howvlanVLANNameStatuPort--------------------------------------------------------------------------------1VLAN0001STATICGi0/3,Gi0/4,Gi0/5,Gi0/6Gi0/7,Gi0/8,Gi0/9,Gi0/10Gi0/11,Gi0/12,Gi0/13,Gi0/14Gi0/15,Gi0/16,Gi0/17,Gi0/18Gi0/19,Gi0/20,Gi0/21,Gi0/22Gi0/23,Gi0/2410VLAN0010STATICGi0/1,Gi0/2420VLAN0020STATICGi0/2,Gi0/24Switchc配置:3#howrunBuildingconfiguration...Currentconfiguration:1540byte!verionRGNOS10.2.00(2),Releae(28794)(FriDec2109:27:15CST2007-ngcf32)hotname3!vlan10!!ervicepaword-encryption!panning-treepanning-treemtconfigurationreviion1nameregion1intance0vlan1-9,11-19,21-4094intance1vlan10intance2vlan20 panning-treemt1priority0panning-treemt2priority4096interfaceFatEthernet0/1witchportaccevlan10!interfaceFatEthernet0/2witchportaccevlan10!..interfaceGigabitEthernet0/25!interfaceGigabitEthernet0/26!interfaceGigabitEthernet0/27!interfaceGigabitEthernet0/28!interfaceVLAN10ipaddre192.168.10.3255.255.255.0!iproute0.0.0.00.0.0.0192.168.10.254!!linecon0linevty04loginSwitchd配置:Buildingconfiguration...Currentconfiguration:1066byte!verionRGNOS10.2.00(2),Releae(27932)(ThuDec1310:31:41CST2007-ngcf32)hotname4!vlan1!vlan20!!noervicepaword-encryption!panning-treepanning-treemtconfigurationreviion1nameregion1intance0vlan1-9,11-19,21-4094intance1vlan10intance2vlan20panning-treemt1priority4096panning-treemt2priority0interfaceGigabitEthernet0/1witchportaccevlan20!interfaceGigabitEthernet0/2witchportaccevlan20!..interfaceGigabitEthernet0/12!interfaceVLAN20ipaddre192.168.20.3255.255.255.0!!!!iproute0.0.0.00.0.0.0192.168.20.254!!linecon0linevty04login!四、查看vrrp、mtp信息Switcha信息:1#howvrrp查看vrrp信息VLAN10-Group1StateiMaterVirtualIPaddrei192.168.10.254configuredVirtualMACaddrei0000. 5e00.0101Advertiementintervali1ecPreemptionienabledmindelayi0ecP riorityi120MaterRouteri192.168.10.1(local),priorityi120MaterAdvertiemen tintervali1ecMaterDownintervali3ecVLAN20-Group2StateiBackup VirtualIPaddrei192.168.20.254configuredVirtualMACaddrei0000. 5e00.0102Advertiementintervali1ecPreemptionienabledmindelayi0ecP riorityi100MaterRouteri192.168.20.2,priorityi120MaterAdvertiementinterv ali1ecMaterDownintervali3ec1#1#1#1#howpanning-treeinterfacegigabitEthernet0/1查看g0/1接口tp 状态信息PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.00d0.f836.ed70PortDeignatedPort:800 1PortForwardTranition:6PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:deignatedPort######MST1vlanmapped:10PortState:forwardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:0001.00d0.f823.ef82PortDeignatedPort:800 1PortForwardTranition:5PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:rootPort######MST2vlanmapped:20PortState:forwardingPortPriority:128 PortDeignatedRoot:0002.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:1002.00d0.f836.ed70PortDeignatedPort:800 1PortForwardTranition:4PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:deignatedPort1#1#1#howpanning-treeinterfacegigabitEthernet0/2查看g0/2接口tp 状态信息PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.00d0.f836.ed70PortDeignatedPort:800 2PortForwardTranition:5PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST1vlanmapped:10PortState:forwardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:0001.00d0.f836.ed70PortDeignatedPort:800 2PortForwardTranition:4PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST2vlanmapped:20PortState:dicardingPortPriority:128 PortDeignatedRoot:0002.001a.a909.8fe0PortDeignatedCot:0 PortDeignatedBridge:0002.00d0.f8d7.ae12PortDeignatedPort:8002 PortForwardTranition:3PortAdminPathCot:20000PortOperPathCot: 20000PortRole:alternatePort1#1#1#howpanning-treeinterfacegigabitEthernet0/24g0/24接口tp状态信息PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.001a.a909.8fe0PortDeignatedPort:801 8PortForwardTranition:5PortAdminPathCot:20000PortOperPathCot:200 00PortRole:rootPort######MST1vlanmapped:10PortState:forwardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:0001.00d0.f836.ed70PortDeignatedPort:801 8PortForwardTranition:5PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST2vlanmapped:20PortState:forwardingPortPriority:128 PortDeignatedRoot:0002.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:0002.001a.a909.8fe0PortDeignatedPort:801 8PortForwardTranition:4PortAdminPathCot:20000PortOperPathCot:200 00PortRole:rootPort1#Switchb信息:2#howvrrpVLAN10-Group1StateiBackupVirtualIPaddrei192.168.10.254configuredVirtualMACaddrei0000. 5e00.0101Advertiementintervali1ecPreemptionienabledmindelayi0ecP riorityi100MaterRouteri192.168.10.1,priorityi120MaterAdvertiementinterv ali1ecMaterDownintervali3ecVLAN20-Group2StateiMaterVirtualIPaddrei192.168.20.254configuredVirtualMACaddrei0000. 5e00.0102Advertiementintervali1ecPreemptionienabledmindelayi0ecP riorityi120MaterRouteri192.168.20.2(local),priorityi120MaterAdvertiemen tintervali1ecMaterDownintervali3ec2#2#2#2#2#2#2#howpanning-treeinterfacegigabitEthernet0/1PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.001a.a909.8fe0PortDeignatedPort:800 1PortForwardTranition:1PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:deignatedPort######MST1vlanmapped:10PortState:forwardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:0001.00d0.f823.ef82PortDeignatedPort:800 2PortForwardTranition:2PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:rootPort######MST2vlanmapped:20PortState:forwardingPortPriority:128PortDeignatedBridge:0002.001a.a909.8fe0PortDeignatedPort:800 1PortForwardTranition:1PortAdminPathCot:200000PortOperPathCot:20 0000PortRole:deignatedPort2#2#2#2#howpanning-treeinterfacegigabitEthernet0/2PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.001a.a909.8fe0PortDeignatedPort:800 2PortForwardTranition:1PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST1vlanmapped:10PortState:forwardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:1001.001a.a909.8fe0PortDeignatedPort:800 2PortForwardTranition:2PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST2vlanmapped:20PortState:forwardingPortPriority:128PortDeignatedBridge:0002.001a.a909.8fe0PortDeignatedPort:800 2PortForwardTranition:1PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort2#2#2#2#2#howpanning-treeinterfacegigabitEthernet0/24PortAdminPortFat:DiabledPortOperPortFat:DiabledPortAdminAuto Edge:EnabledPortOperAutoEdge:DiabledPortAdminLinkType:auto PortOperLinkType:point-to-pointPortBPDUGuard:DiabledPortBPDUFilter:Diabled######MST0vlanmapped:1-9,11-19,21-4094PortState:forwardingPortPriority:128PortDeignatedRoot:8000.001a.a909.8fe0PortDeignatedCot:0PortDeignatedBridge:8000.001a.a909.8fe0PortDeignatedPort:801 8PortForwardTranition:1PortAdminPathCot:20000PortOperPathCot:200 00PortRole:deignatedPort######MST1vlanmapped:10PortState:dicardingPortPriority:128 PortDeignatedRoot:0001.00d0.f823.ef82PortDeignatedCot:0PortDeignatedBridge:0001.00d0.f836.ed70PortDeignatedPort:801 8PortForwardTranition:1PortAdminPathCot:20000PortOperPathCot:200 00PortRole:alternatePort。
S7506E 系列交换机IRF2 功能配置案例

在本次项目中,两台7506E核心交换机之间是用IRF技术,使用这种虚拟化技术可以集合多台设备的硬件资源和软件处理能力,实现多台设备的协同工作、统一管理和不间断维护。
以下为配置模板:# 设置RG-SP-HX-S7506E的成员编号为1,成员优先级为20,创建IRF端口2,并将它与物理端口Ten-GigabitEthernet2/0/7 Ten-GigabitEthernet2/0/8绑定。
(形成聚合IRF链路)独立运行模式配置:< RG-SP-HX-S7506E> system-view[RG-SP-HX-S7506E] irf member 1[RG-SP-HX-S7506E] irf priority 20[RG-SP-HX-S7506E] irf-port 2[RG-SP-HX-S7506E-irf-port 2] port group interface Ten-Gigabitethernet 2/0/7[RG-SP-HX-S7506E-irf-port 2] port group interface Ten-Gigabitethernet 2/0/8[RG-SP-HX-S7506E-irf-port 2] quit将当前配置保存到下次启动配置文件。
[RG-SP-HX-S7506E] quit< RG-SP-HX-S7506E> save将设备的运行模式切换到IRF模式。
< RG-SP-HX-S7506E> system-view[RG-SP-HX-S7506E] chassis convert mode irfThe device will switch to IRF mode and reboot. You are recommended to save the current running configuration and specify the configuration file for the next startup. Continue? [Y/N]:yDo you want to convert the content of the next startup configuration file flash:/startup.cfg to make it available in IRF mode? [Y/N]:yPlease wait...Saving the converted configuration file to the main board succeeded.Slot 1:Saving the converted configuration file succeeded.Now rebooting, please wait...设备重启后7506E-01组成了只有一台成员设备的IRF。
S7506E三层交换机配置

****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. * * Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ******************************************************************************* Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33vlan 3988description wireless supervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250 #vlan 3991supervlansubvlan 1200 to 1225 #vlan 3992supervlansubvlan 100 to 111 #vlan 3993supervlansubvlan 1032 to 1150vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0 gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168..0 mask 255.255.254.0gateway-list 192.168..1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! -type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3990ip address 192.168..1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0 local-proxy-arp enableinterface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128 local-proxy-arp enable#description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2#interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2#interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2#interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/46port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunk#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunk#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2#snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
cisco思科交换机配置篇

cisco思科交换机配置篇cisco思科交换机配置篇要进行思科交换机的配置,首先就得进入交换机的全局配置模式,在成功连接交换机并且登陆成功进入特权模式下,下面跟yjbys店铺一起来学习一下思科交换机的配置命令吧!1、输入进入全局配置模式:switch#configure terminalEnter configuration commands, one per line. End with CNTL/Z.switch(config)#switch(config)#switch(config)#这么简单的一条命令,俺们就进入到全局配置模式了,还记得上一篇中查看端口所查询到的信息中name字段下的值吗?这字段其实代表的是交换机端口的描述信息2、修改端口描述switch#switch#switch#conf terEnter configuration commands, one per line. End with CNTL/Z.switch(config)#switch(config)#int fa0/3switch(config-if)#switch(config-if)#descswitch(config-if)#description updateDescswitch(config-if)#switch(config-if)#exitswitch(config)#exitswitch#switch#show interswitch#show interfaces statuswitch#show interfaces statusPort Name Status Vlan Duplex Speed TypeFa0/1 connected 1 a-full a-100 10/100BaseTXFa0/2 h3c2.250 connected trunk a-full a-100 10/100BaseTX Fa0/3 updateDesc notconnect 1 auto auto 10/100BaseTXFa0/4 connected 1 a-full a-100 10/100BaseTXFa0/5 h3c-2.200 connected 1 a-full a-100 10/100BaseTXFa0/6 notconnect 1 auto auto 10/100BaseTX修改描述的关键命令在于,在配置模式下,进入到要修改的端口下,然后使用description + “内容”!效果应该很直观了吧,接下来就是修改端口的所在Vlan了3、修改端口Vlanswitch#switch#switch#conf tEnter configuration commands, one per line. End with CNTL/Z.switch(config)#switch(config)#int fa0/3switch(config-if)#switch(config-if)#sw acc vl 2switch(config-if)#switch(config-if)#exitswitch(config)#switch(config)#exitswitch#switch#show inter statuPort Name Status Vlan Duplex Speed TypeFa0/1 connected 1 a-full a-100 10/100BaseTXFa0/2 h3c2.250 connected trunk a-full a-100 10/100BaseTX Fa0/3 updateDesc notconnect 2 auto auto 10/100BaseTXFa0/4 connected 1 a-full a-100 10/100BaseTXFa0/5 h3c-2.200 connected 1 a-full a-100 10/100BaseTXFa0/6 notconnect 1 auto auto 10/100BaseTX逻辑和修改端口描述是一样的,对于配置来说,肯定是到了能有配置权限的地方和要配置的对象,这里修改端口Vlan的关键命令为:sw acc vl + vlantag,命令很明显被简写了,但是不影响执行,命令的全写为:switchport access vlan + vlantag还有一些对端口的简单操作,譬如修改端口的模式,4、修改端口模式switch(config-if)#switchport trunk encap dot1q ----------------设置vlan 中继的'封装协议注:dot1q就是 IEEE 802.1Q协议,是vlan的一种封装方式,是公有协议。
mstp协议配置(MSTPprotocolconfiguration)

mstp协议配置(MSTP protocol configuration)Cisco MSTP configuration (multi spanning tree)First, what is the current MSTP and STP related protocols: IEEE 802.1D (STP), 802.1W (RSTP), 802.1 (MSTP). Among them, 802.1D was the earliest standard about STP. RSTP (Rapid Spanning Tree Protocol) is the extension of STP, its main feature is to increase the port state fast switching mechanism, can realize the fast conversion of network topology.First, what is MSTP?The current protocols related to STP are: IEEE 802.1D (STP), 802.1W (RSTP), 802.1 (MSTP). Among them, 802.1D was the earliest standard about STP. RSTP (Rapid Spanning Tree Protocol) is the extension of STP, its main feature is to increase the port state fast switching mechanism, can realize the fast conversion of network topology. MSTP (Multiple Spanning Tree Protocol) proposes the concept of multiple spanning trees, which can map different VLAN to different spanning trees, so as to achieve the goal of network load balancing.1.1 configure MSTP1.1.1 setup modeSTP is divided into two modes: CST and MST. Users can choose reasonable patterns according to their needs:CST modeCST (Common Spanning Tree) generates a spanning tree over the whole network, and STP is based on port settings. If STP sets port blocking, all VLAN is blocked on the port. The feature of this mode is configuration, simple implementation, suitable for small network. The disadvantage is that without the concept of VLAN, when the user's VLAN topology configuration is not the same, it may cause some VLAN can not communicate properly.MST modeMST (Multiple Spanning Tree) is an extension of CST, which has the following characteristics:Multiple switches can be virtualized into a MST domain, which is similar to a bridge of CST and interworking with CST bridge MST.In the MST domain, multiple VLAN with the same topology can be mapped to a spanning tree instance, that is, MSTI (Multiple Spanning Tree Instance). Each MSTI can have different topologies in the domain to achieve the purpose of traffic balancing.The steps of configuring the spanning tree pattern are as follows:Step 1 enters the spanning-tree configuration pattern and configures the spanning tree patternStep 2 spanning-tree mode [cst | mst] select spanning tree schemaStep 3 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter config spanning-treeQuick setting of 12.1.2RSTP introduces the mechanism of fast state transition, and reasonably configure port attributes, which can achieve fast network conversion.Edge attributeSwitches on the edge of the network are generally connected to the terminal devices, such as PC, workstations. To become a Edge port and connected to the terminal port configuration, can realize the rapid conversion of the port state, without the need for Discarding, Learning conversion, Forwarding process.Edge attribute configuration stepsStep 1 config spanning-tree enters thespanning-treespanning-tree configuration modeStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree port [edge] [yes | whether the specified port of the no] {}*1 configuration switch participates in the calculation of the STP protocol of the specified domain, and defaults to participate in the calculationStep 4 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameterP2P attributeThe switch port is directly connected with the switch port, and the port is the P2P interface. RSTP uses a negotiation mechanism for the P2P interface, can realize the rapid conversion of the state of the ports (Discarding, Forwarding).P2P attribute configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration modeStep 2 spanning-tree port [none-stp] [yes |Does the designated port of the no] {}*1 configuration switch participate in the calculation of the STP protocol in the specified domain, and the default is to participate in the calculationStep 3 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameterIf the port is not shared and / * medium connected to port settings for the P2P property. * /1.1.3 setting time parametersMST has four configurable time parameters:Hello-time:STP message interval;Forward-delay: Learning, Discarding port is from Learning Forwarding, a state of timeMaximum-age: maximum lifetime of message;Maximum lifetime of message in Max-hops:MST domain.The time parameter configuration of the MST mode interface is illustrated below:Set time parameter configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration modeStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree [hello-time] {}*1 configuration, when the switch is selected as root bridge, send the time interval of BPDU, unit is second, default is 2. Hello-time must be less than or equal to forward-delay – 2Step 4 spanning-tree [forward-delay] {}*1 sets the time interval of port state switching when the switch is selected as root bridge. The unit is seconds, and the default is 15. The time of forward-delay must be greater than or equal tohello-time + 2Step 5 spanning-tree [maximum-age] {}*1 configure switch on the designated domain BPDU message aging longest interval, the unit is seconds, default is 20, received more than this time BPDU message, directly discarded.The time of maximum-age must be greater than or equal to 2 * (hello-time + 1), less than or equal to 2 * (forward-delay –1)Step 6 spanning-tree max-hops MST configure bridge Forward delay parametersStep 7 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.4 sets bridge instance priorityThe user can configure the bridge priority manually to plan the network reasonably. The bridge with the highest priority (the smaller the value) is the root bridge of the network. When the distance between the two links to the root bridge is the same, select the path that specifies the high priority of the bridge. Configure the MSTI bridge priority on the specified MSTID, default is 32768, the MSTI bridge priority must be a multiple of 4096.Priority configuration steps for bridge instancesStep 1 config spanning-tree enters the spanning-tree configuration pattern and configures the spanning tree patternStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree priority MST configure bridge instance priorityStep 4 exit exit spanning-tree configuration modeStep 5 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.5 set port priorityWhen the distance between the two links to the root bridge is the same, the specified bridge priority is the same, and the topology is determined according to the port priority.Port priority configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration pattern and configures the spanning tree patternStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree port priority MST configure port priorityStep 4 exit exit spanning-tree configuration modeStep 5 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.6 set port pathAfter the root bridge is selected, the port path is of great significance to the network topology. The smaller the distance to the root, the more likely it is to become the pathway. After selecting the root bridge, according to the port speed and so on,Reasonable configuration of port path can form ideal topology.Port pathcost configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration pattern and configures the spanning tree patternStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree port path-cost [auto |] MST configuration port pathcostStep 4 exit exit spanning-tree configuration modeStep 5 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.7 setting port non-stp characteristicsMSTP can set some ports as ports that do not participate in protocol calculations. The method is to set the non-stp property.Non-stp attribute configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration pattern and configures the spanning tree patternStep 2 spanning-tree port [none-stp] [yes| no] {}*1 configuration port whether to participate in the STP operation, the port does not participate in the STP operation, in the Forward state.Step 3 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.8 sets the MSTP domainThe same domain that belongs to MSTP must satisfy: the mapping relation of name, revision, Vlan and MSTI is exactly the same when there is physical connection between devices.MSTP domain configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration modeStep 2 Spanning-tree mode MST configuration MST modeStep 3 spanning-tree MST name configuration MSTP domain identifier nameStep 4 spanning-tree MST revision configuration MSTP domain identifier versionStep 5 spanning-tree map VLAN MST configuration mapping between MSTP domain and VLANsStep 6 exit exit spanning-tree configuration modeStep 7 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameter1.1.9 set MSTP enableInterface configurationMSTP works on only two layers of interfaces, including common Ethernet and Trunk ports, and Ethernet and Trunk default are two layers of interfaces. When users want to enable a two layer forwarding function of an Ethernet or trunk to enable them to participate in the spanning tree calculation, the following configuration can be performed:The configuration steps of MSTP on the two layer interfaceStep 1 interface Ethernet into Ethernet interfaceStep 2 forward L2 enable prohibits the two layer forwarding function of the interfaceStep 3 exit exit Ethernet configuration modeVLAN configurationThe MST model involves VLAN. MSTP cares about the two attributes of VLAN; and SuperVlan, protocol based Vlan, etc. are not MSTP considerations.The configuration steps of MST on VLANStep 1 interface VLAN enters the VLAN configuration modeStep 2 add port untagged adds ports to the VLAN in untagged modeStep 3 exit exit VLAN configuration modeEnabling MSTPEnabling MSTP configuration stepsStep 1 config spanning-tree enters the spanning-tree configuration modeStep 2 Spanning-tree mode MST configuration MST modeStep 3 Spanning-tree enable enable MSTPStep 4 exit exit spanning-tree configuration modeStep 5 show spanning-tree MST displays the MSTP configuration, mst-instance displays the IST information at 0, and the other is the MSTI parameterConfiguration column:Case descriptionThe main example is the switch configuration of the MSTP domain. Create a single MST Region on three switches, and create 3 Instance in them. By configuring the instance priority, bridge1 (MAC: 0005:3b80:03cf) is the root bridge in Instance1,实例2中2(Mac:0005.3b81.1278)为根桥,在instance3中bridge3(Mac:2222:2222:2222)为根桥。
Cisco交换机之间的连接方法

Cisco交换机之间的连接方法你还在为不知道Cisco交换机之间的连接方法而烦恼么?接下来是小编为大家收集的Cisco交换机之间的连接方法教程,希望能帮到大家。
Cisco交换机之间的连接方法的方法对于交换机之间的连接,比较熟悉的应该有两种:一、是堆叠,二、是级联。
对于级联的方式比较容易造成交换机之间的瓶颈,而虽然堆叠技术可以增加背板速率,能够消除交换机之间连接的瓶颈问题,但是,受到距离等的限制很大,而且对交换机数量的限制也比较严格。
Cisco公司推出的交换机集群技术,可以看成是堆叠和级连技术的综合。
这种技术可以将分布在不同地理范围内的交换机逻辑地组合到一起,可以进行统一的管理。
具体的实现方式就是在集群之中选出一个Commander,而其他的交换机处于从属地位,由Commander统一管理。
对于新的Catalyst 3500 XL系列中的Catalyst 3512XL、Catalyst 3524XL和Catalyst 3508G XL三个型号均可以成为Commander,而对于被管理者2900和1900系列均可以加入交换机集群,使用Cisco最新的交换集群技术将传统的堆叠技术提高到新的水平。
据说对于2900XL系列也可以成为Commander。
该系列产品面向中型企事业单位,在提供高性能和低成本的同时,降低了复杂度,并易于集成到已有的网络上。
它允许网络管理员使用标准的Web 测览器。
通过单一的IP地址从网络上的任何地方管理地理上分散的交换机。
具体举例如下:假设网络中心采用Cisco 的Catalyst 6506交换机,而集群的Commander 采用Catalyst 3508 GXL 在集群的Commander与中心交换机之间,可以通过千兆连接或者通过GEC实现4千兆的连接,而在集群内部采用3500、2900、1900的组合,之间通过FEC等方式相连接。
然后为集群分配独立的Ip地址就可以对整个集群进行管理了。
H3C 7506交换机主主模式_配置
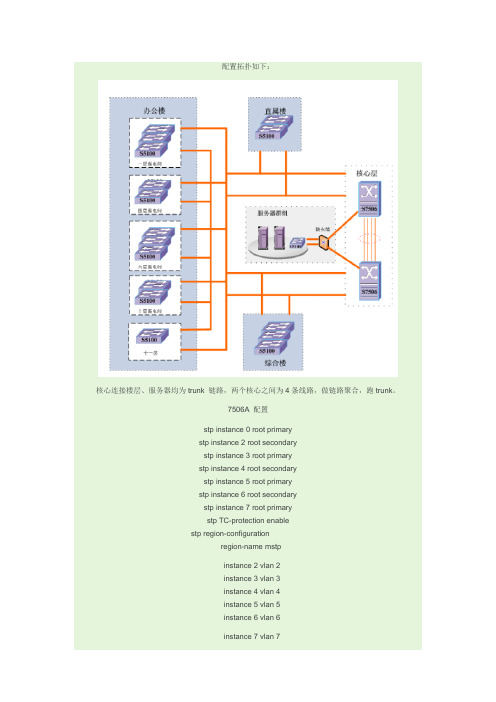
配置拓扑如下:核心连接楼层、服务器均为trunk 链路,两个核心之间为4条线路,做链路聚合,跑trunk。
7506A 配置stp instance 0 root primarystp instance 2 root secondarystp instance 3 root primarystp instance 4 root secondarystp instance 5 root primarystp instance 6 root secondarystp instance 7 root primarystp TC-protection enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.251 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254interface Vlan-interface3ip address 192.168.3.251 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254vrrp vrid 3 priority 110interface Vlan-interface4ip address 192.168.4.251 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254interface Vlan-interface5ip address 192.168.5.251 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254vrrp vrid 5 priority 110interface Vlan-interface6ip address 192.168.6.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254interface Vlan-interface7ip address 192.168.7.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254vrrp vrid 6 priority 110link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 17506B 配置stp instance 0 root primarystp instance 2 root primarystp instance 3 root secondarystp instance 4 root primarystp instance 5 root secondarystp instance 6 root primarystp instance 7 root secondary stp TC-protection enablestp region-configuration region-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.252 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254vrrp vrid 2 priority 110interface Vlan-interface3ip address 192.168.3.252 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254interface Vlan-interface4ip address 192.168.4.252 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254vrrp vrid 4 priority 110interface Vlan-interface5ip address 192.168.5.252 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254interface Vlan-interface6ip address 192.168.6.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254vrrp vrid 6 priority 110interface Vlan-interface7ip address 192.168.7.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 1楼层交换机配置(S5100)vlan 2 to 7stp bpdu-protectionstp enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configuration所有连接PC机的端口,全部配置边缘端口(stp edged-port enable)楼层连接核心的两条上行链路配置为trunk,这两个端口不能配置边缘端口注:双机做完后,可以用dis stp brief 查看状态1、两个核心上所有连接楼层接入的端口都应该为fordowing状态2、楼层接入交换机主核心线路端口应该为fordowing,从核心线路端口应该为discard核心间的链路聚合,随后有相关日志描述。
cisco各种协议配置设备互连

cisco 各种协议配置设备互连《网络设备互连》实训报告书《网络设备互连》一. 课程的地位、作用和目的《网络设备互连》课程是计算机专业一门重要课程,在计算机教学中占有十分重要的地位。
掌握好本课程的内容,是学习和完成计算机应用的必备条件,也是今后走上社会工作时必须具有的一种技能。
本课程主要研究计算机网络基础和网络管理及计算机网络操作系统,主要内容包括计算机网络技术基础,数据通信基础,网络互联的概念与互联技术,计算机局域网和广域网方面的有关基本概念,实用组网技术,Internet和远程网络的接入技术,Internet 基础知识与应用以及使用Windows NT 对网络进行初步管理等。
根据高职高专教学的特点,在教学中应贯彻理论教学和实际应用相结合的原则,使学生能够很好地理解组网技术中优化的设计和管理思想以及具体的实现技术。
因此特增开了《网络设备互连》课程。
《网络设备互连实训》是学生学完《网络设备互连-学习指南》课程后进行的一次综合实练。
旨在加深对课程所学知识的理解,掌握设备配置的方法和步骤,培养学生解决实际问题的能力。
二. 实训方法1、讲解知识点2、自行通过网络或图书馆查阅资料3、通过Cisco Packet Tracer虚拟实训室练习4、通过网络实训室机房的真实设备进行练习。
三、实训目的:1、熟悉路由器几种模式,熟练应用快捷键。
2、熟悉基本的配置命令,会查看命令参数。
3、了解交换机路由器的基本配置第1页《网络设备互连》实验一交换机的基本配置实训设备:CISCO 路由器一台,PC 一台,超级终端软件,配置连线。
网络拓扑图:基本配置及步骤:第2页《网络设备互连》用计算机去telnet交换机第3页《网络设备互连》实验二 VLAN 隔离及VLAN 间通信1(VLAN/802.1Q,本交换机隔离网络拓扑实验项目VLAN/802.1Q,本交换机隔离测试实验环境PC1 连接在交换机的0/5 口;PC2 连接在交换机的0/15 口实验配置交换机上面的配置第4页《网络设备互连》PC1PC2PC2去pingPC1 第5页《网络设备互连》2(VLAN/802.1Q,跨交换机VLAN 网络拓扑图三层交换机上面的配置第6页《网络设备互连》二层交换机配置三台PC的配置PC1 PC2PC3互相pingPC3pingPC1第7页《网络设备互连》PC3pingPC2实验三快速生成树协议802.1W第8页《网络设备互连》网络拓扑图实验项目快速生成树 802.1W 测试实验环境用一台支持 802.1w 的交换机与STAR-S2126G 交换机用两条双绞线互联(这里分别连接在0/2、0/4 口)实验配置用show spanning-tree int f0/2去查看实验四路由器的基本配置第9页《网络设备互连》网络拓扑routerA的配置RouterA的效果A上面的配置第10页《网络设备互连》时钟频率RouterB上面的远程配置B的配置第11页《网络设备互连》配置成功路由器端口全部为绿色PCAPCBPC远程登录路由器路由器A配置第12页《网络设备互连》PCB去pingPCA实验五 PPP CHAP 认证实验拓扑第13页《网络设备互连》RouterA的配置RB实验六 PPP PAP 认证实验拓扑第14页《网络设备互连》RouterA的配置RouterB的配置SHOW intS1/0 第15页《网络设备互连》Debug ppp authentication 实验七静态路由网络拓扑第16页《网络设备互连》路由器A的配置PCARouterB 第17页《网络设备互连》PCApingPCB实验八动态路由(RIP)第18页《网络设备互连》网络拓扑实验内容通过动态路由 RIP,使路由器A,B 具有非直连子网的路由信息。
思科交换机与PC机物理连接和操作

408网络异构实训室思科交换机与PC机物理连接和操作刘祥荣目录一、前言 ................................. - 1 -二、工作准备 ............................. - 2 -三、操作步骤 ............................. - 3 -四、注意事项 ............................ - 11 -五、延伸 ................................ - 12 -一、前言在网络如此发达的时代,交换机起着重要的作用:学习、转发数据包、清除第二层环路。
傻瓜式交换机只能满足小型公司、家庭用户的需求。
傻瓜式的交换机功能少,不能进行手工的配置,满足不了大型公司流量需求。
本文主要介绍思科交换机和PC机之间的物理连接方法以及操作。
二、工作准备1、Console线(反转线rollover):用于连接思科交换机和PC机。
2、超级终端(Hyper Terminal)或者Secure CRT:这些软件用来进行配置交换机。
(本文用Secure CRT操作)3、网线(直通线)三、操作步骤第一步:将console线的RJ-45端口插入思科交换机的Console端口;第二步:将console线的另一端插入PC的COM 口;第三步:插入思科交换机的电源线,并通电。
第四步:双击打开Secure CRT软件,按【文件】-【快速连接】第五步:在协议一栏,点击黑色下三角▼,选择【Serial】设置相关参数:端口选择【COM1】(至于是COM1还是COM2,要视具体情况而定,这里选择COM1);波特率选择【9600】(因为这是串口的最高通信速率);数据位为【8】;奇偶校验【None】;停止位【1】。
最后按【确定】如下图所示,则表示连接成功。
第六步:把网线的一端插入交换机的下行接口,另一端插入桌面的B端口;其他主机的网线都要插进桌面的B端口。
Cisco交换机配置教程

Cisco交换机配置教程The latest revision on November 22, 2020Cisco交换机配置教程Cisco交换机在网络届处于绝对领先地位,高端冗余设备(如:冗余超级引擎,冗余负载均衡电源,冗余风扇,冗余系统时钟,冗余上连,冗余的交换背板),高背板带宽,高多层交换速率等都为企业网络系统的高速稳定运行提供良好解决方案。
这就是为什么大型企业都选择Cisco交换机做核心层和分布层等主要网络设备。
被过滤广告Cisco分为高中低端交换机,分别面向不同层次。
但是多数Cisco 交换机都基于Cisco H家的I0S( Internet Operating System )系统。
所以设置都是大同小异。
让我们从零开始,一步一步教大家学会用Cisco交换机。
第一步:利用电脑超级终端与交换机建立连接可进行网络管理的交换机上有一个“Console”端口,它是专门用于对交换机进行配置和管理的。
可以通过Console端口连接和配置交换机。
用Cisco自带的Console线,RJ-45端接入Cisco交换机Console 口,Com 口端接入电脑Coml或Coin2 口,必须注意的是要记清楚接入的是那个Com 口。
按照步骤开启超级终端:开始一程序一附件一通讯一超级终端(图2)(图2)点击文件一新建连接(图3)(图3)输入超级终端名称,选择数据线所连端口(注意选择Com 口时候要对应Console线接入电脑的Com 口):图4(图4)确定一点击还原为默认值(图5)(图5)确定后开启交换机此时交换机开始载入IOS,可以从载入IOS界面上看到诸如IOS版本号,交换机型号,内存大小等数据当屏幕显示Press RETURN to get started的时候按回车就能直接进入交换机第二步:学习交换机的一些初级命令杵先我们要知道Cisco配置界面分两种,一种是基于CLI (Command-line Interface 命令行界面),一种是基于IOS (Internetwork Operting System 互联网操作系统)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
7506E与CISCO交换机MSTP协议对接配置一、组网需求:安徽某客户要求我司75E交换机与CISCO交换机MSTP协议对接,并具备防环和链路备份功能。
二、组网图:客户网络架构如下图,两台75E各配置一块安全插卡,所有PC网关设置在FW插卡上,安全插卡划分子接口方式。
两台75E作为网络核心交换机,通过vlan-interface Vlan100三层接口与3750互联。
通过trunk方式与接入层2960交换机互联。
目前2台75E和FW插卡没有开启STP协议,3台CISCO交换机运行PVST协议。
三、配置步骤:75E-1设备://开启STP协议,并将STP配置为mstp模式stp enablestp mode mstp//配置MSTP实例,在这台交换机上将instance 0 设置为主stp region-configurationregion-name h3crevision-level 1instance 0 vlan 1 to 4094active region-configuration#stp instance 0 root primary//配置与CISCO设备对接时需要修改的参数stp bpdu-protectionstp pathcost-standard dot1tstp timer-factor 1stp no-agreement-check#stp config-digest-snooping#//接口基本配置,并开启摘要侦听功能interface GigabitEthernet5/0/1port link-mode bridgeport access vlan 100stp config-digest-snooping#interface GigabitEthernet5/0/4port link-mode bridgeport link-type trunkport trunk permit vlan allstp config-digest-snooping#interface GigabitEthernet5/0/5port link-mode bridgeport link-type trunkport trunk permit vlan allspeed 1000duplex fullstp config-digest-snooping75E-2设备://开启STP协议,并将STP配置为mstp模式stp enablestp mode mstp//配置MSTP实例,在这台交换机上将instance 0 设置为备stp region-configurationregion-name h3crevision-level 1instance 0 vlan 1 to 4094active region-configuration#stp instance 0 root secondary//配置与CISCO设备对接时需要修改的参数stp bpdu-protectionstp pathcost-standard dot1tstp timer-factor 1stp no-agreement-check#stp config-digest-snooping#//接口基本配置,并开启摘要侦听功能interface GigabitEthernet5/0/1port link-mode bridgeport access vlan 100stp config-digest-snooping#interface GigabitEthernet5/0/4port link-mode bridgeport link-type trunkport trunk permit vlan allstp config-digest-snooping#interface GigabitEthernet5/0/5port link-mode bridgeport link-type trunkport trunk permit vlan allspeed 1000duplex fullstp config-digest-snooping安全插卡:因为安全插卡运行在三层模式,所以不需要开启STP协议。
3750配置://将STP配置mst模式,并将pathcost配置longspanning-tree mode mstspanning-treee pathcost method long//配置mst实例spanning-tree mst configurationname h3crevision 1instance 0 vlan 1-4094//接口基本配置,并配置MST开销值为20000 interface g1/0/27switchport access vlan 100switchport mode accessspanning-tree mst 0 cost 20000#interface g1/0/28switchport access vlan 100switchport mode accessspanning-tree mst 0 cost 200002960-1配置://将STP配置mst模式,并将pathcost配置long spanning-tree mode mstspanning-treee pathcost method long//配置mst实例spanning-tree mst configurationname h3crevision 1instance 0 vlan 1-4094//接口基本配置,并配置MST开销值为20000 interface g1/0/49switchport trunk allowed vlan 2,10 switchport mode trunkspanning-tree mst 0 cost 20000#interface g1/0/51switchport access vlan 100switchport mode accessspanning-tree mst 0 cost 200002960-2配置://将STP配置mst模式,并将pathcost配置long spanning-tree mode mstspanning-treee pathcost method long//配置mst实例spanning-tree mst configurationname h3crevision 1instance 0 vlan 1-4094//接口基本配置,并配置MST开销值为20000 interface g1/0/49switchport trunk allowed vlan 2,10switchport mode trunkspanning-tree mst 0 cost 20000#interface g1/0/51switchport access vlan 100switchport mode accessspanning-tree mst 0 cost 20000四、配置关键点:配置3750交换机为MST模式后,G1/0/27端口转发数据,G1/0/28端口处于阻塞状态,MSTP协议运行正常。
当配置2960-1交换机为MST模式后,2960-1交换机上联到75E的两个端口都会处于阻塞状态。
拔掉其中一根网线后,剩余一个端口还是处于阻塞状态。
将2960-2交换机配置为mst模式或者关闭stp协议,2960-1两端口状态就正常了,一个转发数据,一个处于阻塞状态。
当网络中有多台cisco 交换机,并且都是通过trunk方式说核心互联时,要先将运行PVST的cisco设备隔离或者关闭STP协议,然后逐一配置为mst模式。
因为CISCO交找机运行mst模式时收到pvst BPDU报文时会将收到此报文的端口置于阻塞状态。
此案例中3750与75E是三层互联,3750收不到PVST BPDU报文,所以3750不会被2960交换机PVST报文影响。
S8500交换机和Cisco交换机的MSTP对接注意事项一、各自支持的STP协议种类我司S8500交换机支持的STP协议:S8500交换机支持标准的STP、RSTP和MSTP,其中MSTP在不启用多实例时基本等同与RSTP。
Cisco支持的STP协议:Cisco支持PVST、PVST+、MISTP和MSTP。
二、MSTP互连对接测试S8500交换机可以与Cisco的PVST+和MSTP进行对接,其它几个协议不能对接。
但是由于Cisco的MSTP实现不规范,S8500上需要特别的配置,说明如下:按照协议规定,stp region-configuration的配置通过MD5摘要算法得到一个值,交换机之间通过比较这个值来确定是否属于同一个域。
如果stp region-configuration的配置完全一致,则结果必然一致,属于同一个域。
由于cisco的MD5算法与协议规定的不一致,导致相同的stpregion-configuration配置与H3C设备的结果不一致。
可以通过配置下面2条命令分别在全局和与cisco相连接的端口下来达到mstp 的互通。
[S1]stp config-digest-snooping[S1]int e8/1/1[S1-Ethernet8/1/1]stp config-digest-snoopin。
