Configuration of Protected Virtual Private Networks
VMWARE 试题

VMWARE 销售试题姓名: ____________一、判断题:1、必须更改虚拟机中的应用程序,因为虚拟机中使用的操作系统不同于物理计算机中使用的操作系统。
答案:2、虚拟机的兼容性特性表明,针对任何标准的开箱即用型操作系统 (如Windows 、Linux 、Netware 或 Solaris)开发的应用程序均可在虚拟机上运行。
答案:3、可以在同一服务器上同时运行多台虚拟机。
答案:4、VMware vsphere 允许您虚拟化计算资源,但网络和存储资源仍然只能作为物理资源进行管理。
答案:5、P2V 将正在运行的虚拟机从一台物理计算机迁移到另一台物理计算机上。
答案:6、VMware VCenter 仅可管理单个服务器主机上的虚拟机。
答案:7、我的客户有一个需要占用大量 I/O 资源的应用程序。
此应用程序会妨碍虚拟基础架构运行。
答案:8、运行刀片服务器的客户不适宜采用服务器整合和控制解决方案答案:9、确定客户意欲对哪些工作负载进行虚拟化极其重要,因为许多工作负载类型(如通信应用程序和数据库)都不适合使用 VMware vsphere 。
答案:10、VIEW 的主要好处是:个人数据可以从用于保护服务器应用程序的同一基础架构中受益(例如,获得强健的安全性和业务连续性) 。
答案:11、下列所有内容均属 VMware 业务连续性解决方案的好处:–更易于实施和管理–支持工作的复杂性降低–成本降低答案:12、因为在使用 VMware 产品时用户不需要寻找和安装与主服务器完全相同的硬件,所以缩短了恢复故障服务器所需的时间答案:13、在与潜在客户讨论这些解决方案时,应以我们的客户使用 VMware 解决方案的经历为基础,以便在潜在客户心目中形成这样的印象: VMware 解决方案可以解决与自己所面临问题类似的问题。
答案:14、客户必须使用 VMware Consolidated Backup 备份虚拟机。
答案:二、单选题:1、请阅读下面的定义,选择与它匹配的虚拟机特性:“当物理主机上的某台虚拟机停机时,并不会影响同一主机上的其余虚拟机。
P2V常见问题

Converter Standalone 5.0 版本中包含以下已知问题:•安装•常规•Windows 源•Linux 源•第三方格式•本地化•用户指南和帮助安装在重新安装 Converter Standalone 之前,必须重新启动运行 64 位 Windows Vista 或更高版本的计算机如果从 64 位 Windows Vista、Windows Server 2008 或 Windows 7 计算机上卸载Converter Standalone 后没有重新启动计算机,则后续的 Converter Standalone 安装可能会失败,并会显示以下错误消息:错误 29144。
无法安装服务 Vstor2 MntApi 1.0 Driver(共享)。
请重新引导并尝试再次安装 (Error 29144. Could not install service Vstor2 MntApi 1.0 Driver (shared). Please reboot and try to install again)。
解决办法:重新启动 Windows Vista、Windows Server 2008 或 Windows 7 计算机,然后尝试重新安装 Converter Standalone。
Converter Standalone 安装程序未发出任何通知即移除 Workstation 6.5.x 远程代理使用 Workstation 6.5.x 热克隆 Windows 源计算机时,Workstation 会在源上部署一个远程 Workstation 代理。
如果选择保留该源上的远程代理,然后将 Converter Standalone 安装在同一计算机上,则 Converter Standalone 安装程序将卸载该代理且不发送任何警告消息。
成功转换之后,运行 64 位 Windows Vista 或更高版本的远程源计算机的后续 P2V 转换可能会失败如果成功转换某一运行 64 位 Windows Vista、Windows Server 2008 或 Windows 7 操作系统的远程源计算机后尝试再次转换,则转换将失败,并且会显示错误消息:Converter Standalone Agent 在 x.x.x.x 上安装失败,错误代码: 1603 (Converter Standalone Agent installation failed on x.x.x.x Error code: 1603)1603,其中 x.x.x.x 是源计算机的 IP 地址。
Protected Port的功能与配置
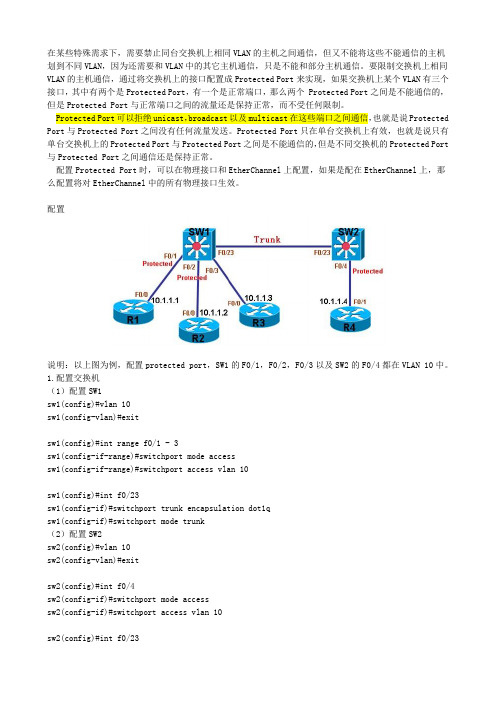
在某些特殊需求下,需要禁止同台交换机上相同VLAN的主机之间通信,但又不能将这些不能通信的主机划到不同VLAN,因为还需要和VLAN中的其它主机通信,只是不能和部分主机通信。
要限制交换机上相同VLAN的主机通信,通过将交换机上的接口配置成Protected Port来实现,如果交换机上某个VLAN有三个接口,其中有两个是Protected Port,有一个是正常端口,那么两个 Protected Port之间是不能通信的,但是Protected Port与正常端口之间的流量还是保持正常,而不受任何限制。
Protected Port可以拒绝unicast,broadcast以及multicast在这些端口之间通信,也就是说Protected Port与Protected Port之间没有任何流量发送。
Protected Port只在单台交换机上有效,也就是说只有单台交换机上的Protected Port与Protected Port之间是不能通信的,但是不同交换机的Protected Port 与Protected Port之间通信还是保持正常。
配置Protected Port时,可以在物理接口和EtherChannel上配置,如果是配在EtherChannel上,那么配置将对EtherChannel中的所有物理接口生效。
配置说明:以上图为例,配置protected port,SW1的F0/1,F0/2,F0/3以及SW2的F0/4都在VLAN 10中。
1.配置交换机(1)配置SW1sw1(config)#vlan 10sw1(config-vlan)#exitsw1(config)#int range f0/1 - 3sw1(config-if-range)#switchport mode accesssw1(config-if-range)#switchport access vlan 10sw1(config)#int f0/23sw1(config-if)#switchport trunk encapsulation dot1qsw1(config-if)#switchport mode trunk(2)配置SW2sw2(config)#vlan 10sw2(config-vlan)#exitsw2(config)#int f0/4sw2(config-if)#switchport mode accesssw2(config-if)#switchport access vlan 10sw2(config)#int f0/23sw2(config-if)#switchport trunk encapsulation dot1qsw2(config-if)#switchport mode trunk2.配置路由器(1)配置R1r1(config)#int f0/0r1(config-if)#ip add 10.1.1.1 255.255.255.0(2)配置R2r2(config)#int f0/0r2(config-if)#ip add 10.1.1.2 255.255.255.0(3)配置R3r3(config)#int f0/0r3(config-if)#ip add 10.1.1.3 255.255.255.0(4)配置R4r4(config)#int f0/1r4(config-if)#ip add 10.1.1.4 255.255.255.03.测试正常情况下的通信(1)测试R1到R2的连通性r1#ping 10.1.1.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms r1#说明:因为没有配置protected port,所以R1到R2通信正常。
PowerFlex 20-HIM-A6 20-HIM-C6S HIM 固件版本 2.006 发布说明

Release Notes20-HIM-A6 / -C6S HIM Firmware Revision 2.006Catalog Numbers 20-HIM-A6, 20-HIM-C6S HIMThis release note describes major revision 2, minor revision 6 of firmware for the PowerFlex® 20-HIM-A6 and 20-HIM-C6S HIM (Human Interface Module).The following information is included in this document: EnhancementsThis firmware revision includes support for the PowerFlex 755TM, 755TR, and 755TL drives.Corrected Anomalies This section describes the anomalies that are corrected in this revision offirmware.•This firmware revision fixes an anomaly where the Element names were repeated in a Group, and Group names were repeated in a File. The HIMdisplay no longer shows repeated Elements and Groups.•In previous firmware revisions, the "Security is Enabled" notification appeared if a clear fault command was initiated on a write-protected HIMport. This notification no longer appears, and the fault is cleared correctly.•In previous firmware revisions, cities such as Istanbul and Johannesburg were options in the "Americas" region during time zone setup for thePowerFlex 753 and 755 drives. This firmware revision fixes the anomalyand the cities no longer appear as options in the incorrect region.Topic Page Enhancements 1Corrected Anomalies 1Known Anomalies 2Determining Firmware Revision 3Updating the Firmware 5Restrictions 7Compatible Revisions 72Known Anomalies CopyCat and PowerFlex 755T ProductsCopyCat does not directly support the following parameters in port 0 ofPowerFlex 755T products:•33 [VoltageClass Cfg]•35 [Duty Rating Cfg]•46 [Velocity Units]•65 [Pri MtrCtrl Mode]•67 [Sec MtrCtrl Mode]•70 [Application Sel]Changes to these parameters in port 0 determine which parameters are in otherports. Changes to these parameters require a power cycle to take effect.Therefore, CopyCat cannot properly download to non-0 ports without a powercycle after downloading to port 0.The work around for this problem is a two-step CopyCat download. Perform aCopyCat download, then cycle power, then repeat the CopyCat download. Thefirst download configures port 0. The second download configures the otherports.Escape Key Causes HIM Crash on PowerFlex 755T ProductsPowerFlex 755T products do not support Process Display. The HIM does notproperly recognize this. Pushing the soft ESC button on the main screen causesthe HIM to attempt to move to the Process Display screen. On PowerFlex 755Tproducts, this cause the HIM to crash and reboot. T o reset the HIM, continue topress the ESC button until the HIM resets.HIM Loses Least Significant Bit (LSB) of Manual Reference PreloadWhen a switch from automatic reference to manual reference moves is triggeredby a digital input, the HIM loses the LSB of the preloaded reference. For examplewhen moving to manual control with an automatic reference of 2.00 Hz, theHIM preloads the manual reference as 1.79 Hz.3Determining Firmware Revision This section describes procedures to determine the firmware revision of your PowerFlex 20-HIM-A6 or 20-HIM-C6S HIM.Using the 20-HIM-A6 or 20-HIM-C6S HIMUsing Connected Components Workbench Software1.Go online with the HIM connected to the drive by using a 1203-USBconverter or an EtherNet/IP network connection.unch the Connected Components W orkbench™ software.3.In the Device T oolbox right pane, select Discover, and click BrowseConnections.The Connection Browser appears.4.Expand the tree view as needed and select the 20-HIM-A6 or20-HIM-C6S HIM that is connected to the drive.5.Click OK.Connected Components Workbench software connects to the HIM.46.Create any database files if needed (for later use when offline), add theHIM to the Project Organizer left pane, and open the Device Detailswindow for the HIM (see Figure 1).Figure 1 Connected Components Workbench Screen with Device DetailsThe HIM firmware revision (for example, 2.003) is shown below the HIMpicture (circled in red in the graphic).Using DriveExecutive Softwareunch the DriveExecutive™ software.2.Go online with the drive connected to the HIM by using a 1203-USBconverter or an EtherNet/IP network connection.3.In the DriveExecutive tree view, select the 20-HIM-A6 or 20-HIM-C6SHIM (see Figure 2).4.Click the information iconto display the adapter Properties screen.55.The ‘Revision’ field shows the present revision of the adapter firmware (forexample, 2.003).Figure 2 DriveExecutive Window with Information Icon and Device PropertiesUpdating the Firmware Note: The PowerFlex 755T products do not support the DPI option (the HIMis a DPI option) flashing.This section describes procedures to update the adapter firmware. Flash kits fordrives, communication adapters, and peripherals are provided on theAllen-Bradley W eb Updates site at/support/abdrives/webupdate. Updating can be performedby using a 1203-USB converter. For information about how to connect to yourdrive, see its respective user manual. It can be viewed and downloaded on theLiterature Library website at .ATTENTION: Risk of permanent equipment damage exists. Once an update has beenstarted, do not remove power from the drive until after the download has completedand the HIM has reinitialized with the connected drive. If power is removed before thisoccurs, the HIM may be permanently damaged. A HIM that has been damaged in thisway cannot be repaired.6Installing the Flash Kit1.Go to the Allen-Bradley Web Updates site at /support/abdrives/webupdate and install the flash kitfor the PowerFlex 20-HIM-A6 or 20-HIM-C6S HIM, which alsoautomatically installs the ControlFLASH software on your computer.Y ou are now ready to use ControlFLASH or DriveExecutive software toupdate the firmware.2.See the respective section and follow the instructions.Using ControlFLASH Software to Update Firmware1.With the Flash Kit installed, choose Start > (All) Programs > Flash Programming T ools > ControlFLASH to launch the ControlFLASHsoftware.2.On the ControlFLASH Welcome screen, click Next >.3.Choose the appropriate 20-HIM-x6 [connection type] update from the list of available updates.4.Click Next >.5.Expand the tree view for the communication path you are using, and select the drive icon that represents the drive that is connected to the HIM youare updating.6.Click OK.7.If the Multiple Assemblies Found window appears, select ‘Port X - 20-HIM-x6’ from the list and click OK.If this window does not appear, proceed with step 8.8.With the Firmware Revision window displayed, select ‘2.006.xx [language]’ from the list of available updates.9.Click Next >.IMPORTANT Connected Components Workbench software is not intended to be used as a firmware update tool, therefore it cannot be used. The recommended tool to use is ControlFLASH™ software, which is downloaded automatically when the respective firmware revision file isdownloaded from the Allen-Bradley updates website to your computer.IMPORTANT This update may cause the HIM parameters to revert to their default values. You maywant to save your configuration by using the HIM CopyCat feature or DriveExecutivesoftware before updating.710.Follow the remaining screen prompts until the update procedure completes and displays the new firmware revision ing DriveExecutive Software to Update Firmware 1.With the Flash Kit installed (see Installing the Flash Kit on page 6), launch DriveExecutive software.2.Go online with the drive connected to the HIM by using a 1203-USB converter or an EtherNet/IP network connection.3.In the DriveExecutive tree view, select the 20-HIM-x6.4.Click the information icon (see Figure 2) to display the HIM Properties screen.5.On the HIM Properties screen, click the Component Details tab.6.Click Flash Update to start the update.7.Select the 20-HIM-x6 from the list of available devices.8.Click Next >.9.Select ‘2.006.xx [language]’ from the list of available updates.10.Click Next >.11.Follow the remaining screen prompts until the update procedure completes and displays the new firmware revision 2.006.RestrictionsNo restrictions apply to this revision of patible Revisions T o use this revision of firmware, update your tools and devices as needed.IMPORTANT This update may cause the HIM parameters to revert to their default values. You may want to save your configuration using DriveExecutive software or the HIM CopyCat feature before updating.Tool/Device Version RequiredDriveExecutive software 5.01 or laterPowerFlex 7-Class drive all versions compatible20-HIM-A6 / -C6S HIM all versions compatibleRSLinx® Classic software 2.43 or laterConnected Components Workbench 1.02 or laterRockwell Otomasyon Ticaret A.Ş., Kar Plaza İş Merkezi E Blok Kat:6 34752 İçerenköy, İstanbul, T el: +90 (216) 5698400Publication 20HIM-RN013A-EN-P - May 2017Copyright © 2017 Rockwell Automation, Inc. All rights reserved. Printed in the U.S.A.Rockwell Automation SupportUse the following resources to access support information.Documentation FeedbackY our comments will help us serve your documentation needs better. If you have any suggestions on how to improve this document, complete the How Are W e Doing? form at /idc/groups/literature/documents/du/ra-du002_-en-e.pdf .Technical Support CenterKnowledgebase Articles, How-to Videos, FAQs, Chat, User Forums, and Product Notification Updates.https:/// Local Technical Support Phone NumbersLocate the phone number for your country./global/support/get-support-now.page Direct Dial CodesFind the Direct Dial Code for your product. Use the code to route your call directly to a technical support engineer./global/support/direct-dial.page Literature LibraryInstallation Instructions, Manuals, Brochures, and Technical Data./global/literature-library/overview.page Product Compatibility and DownloadCenter (PCDC)Get help determining how products interact, check features and capabilities, and find associated firmware./global/support/pcdc.page Allen-Bradley, Connected Components Workbench, ControlFLASH, DriveExecutive, PowerFlex, Rockwell Automation, Rockwell Software, and RSLinx are trademarks of Rockwell Automation, Inc.EtherNet/IP is a trademark of ODVA, Inc.Trademarks not belonging to Rockwell Automation are property of their respective companies.Rockwell Automation maintains current product environmental information on its website at/rockwellautomation/about-us/sustainability-ethics/product-environmental-compliance.page .。
ccie笔试
Which two options are two characteristics of the HSRPv6 protocol?哪两个选项属于热备份路由协议的特性?A. It uses virtual MAC addresses 0005.73a0.0000 through 0005.73a0.0fff.B. It uses UDP port number 2029QUESTION 2Like OSPFv2, OSPFv3 supports virtual links. Which two statements are true about the IPv6 address of a virtual neighbor? (Choose two)OSPFv2和OSPFv3都支持虚链路,关于IPv6地址的虚拟邻居,哪两个语句是正确的。
[ˈpri:fɪks]E. It is the global scope address, and it is discovered by examining theintra-area-prefix-LSAs received by the virtual neighbor.他是全球范围地址,通过检查接收到虚拟邻居的区域间、区域内、前缀、链路状态广播来发现对方。
F. Only prefixes with the LA-bit set can be used as a virtual neighbor address. 开头为LA-bit的才能用做虚拟邻居的地址。
QUESTION 3Witch two statements are true about an EVPL ?(Ethernet Virtual Private Line) rɪ'fɜ:rɪd vi: (to) 涉及,查阅C. The EVPL service is also referred to as E-line. (EVPL服务也被称为E-line)D. It is a point-to-point Ethernet connection between a pair of UNIs.他是在一对用户网路终端设备上的点到点以太网连接。
网络可靠性实现

高可用性技术(故障检测技术)在路由网络中的应用国网电科院信息通信技术服务中心蓝鹏引言:为了保证网络的不间断运行,特别是核心出口网络的高可用性,通常在部署较大规模网络时,会采取链路级备份、设备级备份等方式。
技术上通常使用多管理引擎备份、浮动静态路由、VRRP、HSRP等。
虽然这些技术给网络带来了一些备份作用,但是对于实时性要求较高的网络还会存在一些问题,本文结合在H3C路由器上的配置实例说明一些故障检测技术与传统技术的结合(联动)从而实现更为智能的高可用性解决方案。
关键字:可靠性故障检测技术 NQA BFD TRACK 路由协议网络收敛(一)、可靠性概述随着网络的快速普及和应用的日益深入,网络中断可能影响大量业务,因此,作为业务承载主体的基础网络,其可靠性日益成为倍受关注的焦点。
在实际网络中,总避免不了各种非技术因素造成的网络故障和服务中断。
因此,提高系统容错能力、提高故障恢复速度、降低故障对业务的影响,是提高系统可靠性的有效途径。
1.可靠性需求可靠性需求根据其目标和实现方法的不同可分为三个级别,各级别的目标和实现方法如表 1 所示。
级别目标实现方法1减少系统的软、硬件故障硬件:简化电路设计、提高生产工艺、进行可靠性试验软件:软件可靠性设计、软件可靠性测试等2即使发生故障,系统功能也不设备和链路的冗余设计、部署倒换策略、提高倒换成功率受影响提供故障检测、诊断、隔离和恢复技术3尽管发生故障导致功能受损,但系统能够快速恢复表 1在上述三个级别的可靠性需求中,第 1 级别需求的满足应在网络设备的设计和生产过程中予以考虑;第 2 级别需求的满足应在设计网络架构时予以考虑;第 3 级别需求则应在网络部署过程中,根据网络架构和业务特点采用相应的可靠性技术来予以满足。
2.可靠性度量通常我们使用 MTBF ( Mean Time Between Failures ,平均故障间隔时间)和 MTTR ( Mean Timeto Repair ,平均修复时间)这两个技术指标来评价系统的可靠性。
常用JAVA关键字英语大全 带音标
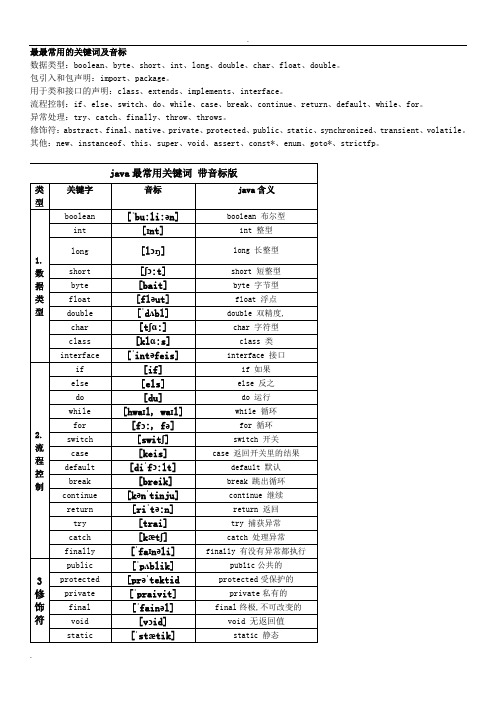
最最常用的关键词及音标数据类型:boolean、byte、short、int、long、double、char、float、double。
包引入和包声明:import、package。
用于类和接口的声明:class、extends、implements、interface。
流程控制:if、else、switch、do、while、case、break、continue、return、default、while、for。
异常处理:try、catch、finally、throw、throws。
修饰符:abstract、final、native、private、protected、public、static、synchronized、transient、volatile。
其他:new、instanceof、this、super、void、assert、const*、enum、goto*、strictfp。
Java基础常见英语词汇(共70个)['ɔbdʒekt] ['ɔ:rientid]导向的 ['prəʊɡræmɪŋ]编程OO: object-oriented ,面向对象OOP: object-oriented programming,面向对象编程[dɪ'veləpmənt][kɪt]工具箱 ['vɜːtjʊəl]虚拟的JDK:Java development kit, java开发工具包JVM:java virtual machine ,java虚拟机['dʒɑːvə] [mə'ʃiːn]机器[kəm'paɪl]Compile:编绎Run:运行['veərɪəb(ə)l] [ɒpə'reɪʃ(ə)n] [pə'ræmɪtə]variable:变量operation:操作,运算parameter:参数['fʌŋ(k)ʃ(ə)n]function:函数 member-variable:成员变量member-function:成员函数[dɪ'fɔːlt] ['ækses] ['pækɪdʒ] [ɪm'pɔːt] ['stætɪk]default:默认access:访问 package:包import:导入static:静态的[vɔid] ['peər(ə)nt] [beɪs] ['sjuːpə]void:无(返回类型) parent class:父类 base class:基类super class:超类[tʃaɪld] [di'raivd] [əʊvə'raɪd] [əʊvə'ləʊd] child class:子类derived class:派生类override:重写,覆盖overload:重载['faɪn(ə)l] ['ɪmplɪm(ə)nts]final:最终的,不能改变的implements:实现[rʌn'taim] [æriθ'metik] [ik'sepʃən]Runtime:运行时ArithmeticException:算术异常[ə'rei] ['indeks] [baundz] [ik'sepʃən] [nʌl] ['pɔintə]指针ArrayIndexOutOfBoundsException:数组下标越界异常 Null Pointer Exception:空引用异常ClassNotFoundException:类没有发现异常['nʌmbə]['fɔ:mæt]NumberFormatException:数字格式异常(字符串不能转化为数字)[θrəuz]Throws: (投掷)表示强制异常处理Throwable:(可抛出的)表示所有异常类的祖先类[læŋ] ['læŋɡwidʒ] [ju'til] [,dis'plei] [ə'rei] [list]Lang:language,语言Util:工具 Display:显示ArrayList:(数组列表)表示动态数组 [hæʃ] [mæp]HashMap: 散列表,哈希表[swiŋ] ['æbstrækt] ['windəu] ['tu:lkit]Swing:轻巧的Awt:abstract window toolkit:抽象窗口工具包[freim] ['pænl] ['leiaut] [skrəul] ['və:tikəl] Frame:窗体 Panel:面板Layout:布局Scroll:滚动Vertical:垂直['hɔri'zɔntəl] ['leibl] [tekst] ['fi:ld]Horizontal:水平Label:标签TextField:文本框['εəriə] ['bʌtən] [tʃek] [bɔks]TextArea:文本域Button:按钮Checkbox:复选框['reidiəu] ['kɔmbəu] ['lisənə]Radiobutton:单选按钮Combobox:复选框Listener:监听['bɔ:də] [fləu] [ɡrid] ['menju:] [bɑ:]Border:边界Flow:流Grid:网格MenuBar:菜单栏['menju:] ['aitəm] ['pɔpʌp]Menu:菜单MenuItem:菜单项PopupMenu:弹出菜单['daiəlɔɡ] ['mesidʒ] ['aikɔn] [nəud]Dialog:对话框 Message:消息Icon:图标Node:节点['dʒa:və] ['deitəbeis] [,kɔnek'tivəti]Jdbc:java database connectivity :java数据库连接[draivə] ['mænidʒə] [kə'nekʃən] ['steitmənt]DriverManager:驱动管理器Connection:连接 Statement:表示执行对象[pri'peəd] [ri'zʌlt]Preparedstatement:表示预执行对象Resultset:结果集['eksikju:t] ['kwiəri]executeQuery:执行查询334157810 这群每日java技术免费分享定期java资料更新Jbuilder中常用英文(共33个)[kləuz] [ik'sept] [peinz]Close all except…:除了..全部关闭 Panes:面板组[bi:n] ['prɔpətiz] [meik] [bild] [,ri:'bild]Bean:豆子Properties:属性 Make:编绎Build:编绎Rebuild:重编绎[ri'freʃ] ['prɔdʒekt] [di'fɔ:lt]Refresh:刷新 Project properties:项目属性 Default project properties:默认的项目属性[di:'bʌɡ] ['prefərənsiz] [kən'fiɡə] ['laibrəriz] Debug:调试Preferences:参数配置 Configure:配置Libraries:库JSP中常用英文[,ju:ni'və:səl] [ri'sɔ:s] [ləu'keiʃən]URL: Universal Resource Location:统一资源定位符['intənet] [ik'splɔ:rə] ['dʒa:və] ['sə:və] [peidʒ]IE: Internet Explorer 因特网浏览器 JSP: java server page: java服务器页面['mɔdəl] [kən'trəulə] ['tɔmkæt]Model:模型 C:controller:控制器 Tomcat:一种jsp的web服务器['mɔdju:l] ['sə:vlet] [i'niʃəlaiz] ['sta:tʌp] WebModule:web模块 Servlet:小服务程序 Init: initialize,初始化 Startup:启动['mæpiŋ] [pə'ræmitə] ['seʃən] [,æpli'keiʃən]Mapping:映射 Getparameter:获取参数 Session:会话 Application:应用程序['kɔntekst] [,ri:di'rekt] [dis'pætʃ] ['fɔ:wəd]Context:上下文 redirect:重定向 dispatch:分发 forward:转交[ 'ætribju:t] ['kɔntent] [taip]setattribute:设置属性 getattribute:获取属性 contentType:内容类型[tʃɑ:] [in'klu:d] [tæɡ] [lib]charset:字符集 include:包含 tag:标签 taglib:标签库[ik'spreʃən] ['læŋɡwidʒ] [skəup] ['empti]EL:expression language,表达式语言 Scope:作用域 Empty:空['stændəd] [tæɡ] ['laibrəri]JSTL:java standard tag library :java标准标签库[di'skripʃən] [kɔ:]TLD:taglib description,标签库描述符 Core:核心 Foreach:表示循环[va:(r)] ['vεəriəbl] ['steitəs] ['aitəm]Var:variable,变量 Status:状态 Items:项目集合['fɔ:mæt] [filtə]Fmt:format,格式化 Filter:过滤器334157810 这群每日java技术免费分享定期java资料更新(报错英文['strʌktʃəz]Data Structures 基本数据结构['dikʃənəriz]Dictionaries 字典[prai'ɔrəti] [kju:z]Priority Queues 堆[ɡrɑ:f] ['deɪtə] ['strʌktʃəz]Graph Data Structures 图[set] ['deɪtə]['strʌktʃəz]Set Data Structures 集合[tri:s]Kd-Trees 线段树[nju:'merikəl] ['prɔ:bləms]Numerical Problems 数值问题[sɔlviŋ] ['liniə] [i'kweiʃənz]Solving Linear Equations 线性方程组['bændwidθ] [ri'dʌkʃən]Bandwidth Reduction 带宽压缩['meitriks] [,mʌltipli'keiʃən]Matrix Multiplication 矩阵乘法[di'tə:minənt] ['pə:mənənt]Determinants and Permanents 行列式[kən'streind] [ʌnkən'streɪnd] [,ɔptimai'zeiʃən] Constrained and Unconstrained Optimization 最值问题['liniə] ['prəuɡræmiŋ]Linear Programming 线性规划['rændəm] ['nʌmbə] [,dʒenə'reiʃən]Random Number Generation 随机数生成['fæktərɪŋ] [prai'mæləti] ['testɪŋ]Factoring and Primality Testing 因子分解/质数判定['ɑːbɪtrərɪ][prɪ'sɪʒən][ə'rɪθmətɪk]Arbitrary Precision Arithmetic 高精度计算['næpsæk] ['prɒbləm]Knapsack Problem 背包问题[dɪ'skriːt] ['fʊriər] [træns'fɔːm]Discrete Fourier Transform 离散Fourier变换Combinatorial Problems 组合问题Median and Selection 中位数Generating Permutations 排列生成Generating Subsets 子集生成Generating Partitions 划分生成Generating Graphs 图的生成Calendrical Calculations 日期Job Scheduling 工程安排Satisfiability 可满足性Graph Problems -- polynomial 图论-多项式算法Connected Components 连通分支Topological Sorting 拓扑排序Minimum Spanning Tree 最小生成树Shortest Path 最短路径Transitive Closure and Reduction 传递闭包Matching 匹配Eulerian Cycle / Chinese Postman Euler回路/中国邮路Edge and Vertex Connectivity 割边/割点Network Flow 网络流Drawing Graphs Nicely 图的描绘Drawing Trees 树的描绘Planarity Detection and Embedding 平面性检测和嵌入Graph Problems -- hard 图论-NP问题Clique 最大团Independent Set 独立集Vertex Cover 点覆盖Traveling Salesman Problem 旅行商问题Hamiltonian Cycle Hamilton回路Graph Partition 图的划分Vertex Coloring 点染色Edge Coloring 边染色Graph Isomorphism 同构Steiner Tree Steiner树Feedback Edge/Vertex Set 最大无环子图Computational Geometry 计算几何Convex Hull 凸包Triangulation 三角剖分Voronoi Diagrams Voronoi图Nearest Neighbor Search 最近点对查询Range Search 范围查询Point Location 位置查询Intersection Detection 碰撞测试Bin Packing 装箱问题Medial-Axis Transformation 中轴变换Polygon Partitioning 多边形分割Simplifying Polygons 多边形化简Shape Similarity 相似多边形Motion Planning 运动规划Maintaining Line Arrangements 平面分割Minkowski Sum Minkowski和Set and String Problems 集合与串的问题Set Cover 集合覆盖Set Packing 集合配置String Matching 模式匹配Approximate String Matching 模糊匹配Text Compression 压缩Cryptography 密码Finite State Machine Minimization 有穷自动机简化Longest Common Substring 最长公共子串Shortest Common Superstring 最短公共父串DP——Dynamic Programming——动态规划recursion ——递归)报错英文第一章:JDK(Java Development Kit) java开发工具包JVM(Java Virtual Machine) java虚拟机Javac 编译命令java 解释命令Javadoc 生成java文档命令classpath 类路径Version 版本static 静态的String 字符串类334157810 这群每日java技术免费分享定期java资料更新JIT(just-in-time) 及时处理:第三章:OOP object oriented programming 面向对象编程Object 对象Class 类Class member 类成员Class method 类方法Class variable 类变量Constructor 构造方法Package 包Import package 导入包第四章:Base class 基类Super class 超类Overloaded method 重载方法Overridden method 重写方法Public 公有Private 私有Protected 保护Static 静态Abstract 抽象Interface 接口Implements interface 实现接口第五章:RuntimeExcepiton 运行时异常ArithmeticException 算术异常IllegalArgumentException 非法数据异常ArrayIndexOutOfBoundsException 数组索引越界异常NullPointerException 空指针异常ClassNotFoundException 类无法加载异常(类不能找到)NumberFormatException 字符串到float类型转换异常(数字格式异常)IOException 输入输出异常FileNotFoundException 找不到文件异常EOFException 文件结束异常InterruptedException (线程)中断异常throws 投、掷、抛print Stack Trace() 打印堆栈信息get Message()获得错误消息get Cause()获得异常原因method 方法able 能够instance 实例Byte (字节类)Character (字符类)Integer(整型类)Long (长整型类)Float(浮点型类)Double (双精度类)Boolean(布尔类)Short (短整型类)Digit (数字)Letter (字母)Lower (小写)Upper (大写)Space (空格)Identifier (标识符)Start (开始)String (字符串)length (值)equals (等于)Ignore (忽略)compare (比较)sub (提取)concat (连接)trim (整理)Buffer (缓冲器)reverse (颠倒)delete (删除)append (添加)Interrupted (中断的)第七章:toString 转换为字符串GetInstance 获得实例Util 工具,龙套Components 成分,组成 Next Int 下一个整数Gaussian 高斯ArrayList 对列LinkedList 链表Hash 无用信息,杂乱信号Map 地图Vector 向量,矢量Collection 收集Shuffle 混乱,洗牌RemoveFirst 移动至开头RemoveLast 移动至最后lastElement 最后的元素Capacity 容量,生产量Contains 包含,容纳InsertElementAt 插入元素在某一位置334157810 这群每日java技术免费分享定期java资料更新第八章:io->in out 输入/输出File 文件isFile 是文件isDirectory 是目录getPath 获取路径getAbsolutePath 获取绝对路径lastModified 最后修改日期Unicode 统一的字符编码标准, 采用双字节对字符进行编码FileInputStream 文件输入流FileOutputStream文件输出流IOException 输入输出异常fileobject 文件对象available 可获取的BufferedReader 缓冲区读取FileReader 文本文件读取BufferedWriter 缓冲区输出FileWriter 文本文件写出flush 清空close 关闭DataInputStream 二进制文件读取DataOutputStream二进制文件写出EOF 最后encoding 编码Remote 远程release 释放第九章:JBuider Java 集成开发环境(IDE)Enterprise 企业版Developer 开发版Foundation 基础版Messages 消息格Structure 结构窗格Project 工程Files 文件Source 源代码Design 设计History 历史Doc 文档File 文件Edit 编辑Search 查找Refactor 要素View 视图Run 运行Tools 工具Window 窗口Help 帮助Vector 矢量addElement 添加内容Project Winzard 工程向导Step 步骤Title 标题Description 描述Copyright 版权Company 公司Aptech Limited Aptech有限公司author 作者Back 后退Finish 完成version 版本Debug 调试New 新建ErrorInsight 调试第十章:JFrame 窗口框架JPanel 面板JScrollPane 滚动面板title 标题Dimension 尺寸Component 组件Swing JAVA轻量级组件getContentPane 得到内容面板LayoutManager 布局管理器setVerticalScrollBarPolicy 设置垂直滚动条策略AWT(Abstract Window Toolkit)抽象窗口工具包GUI (Graphical User Interface)图形用户界面VERTICAL_SCROLLEARAS_NEEDED 当内容大大面板出现滚动条VERTICAL_SOROLLEARAS_ALWAYS 显示滚动条VERTICAL_SOROLLEARAS_NEVER 不显示滚动条JLabel 标签Icon 图标image 图象LEFT 左对齐RIGHT 右对齐JTextField 单行文本getColumns 得到列数setLayout 设置布局BorderLayout 边框布局CENTER 居中对齐JTextArea 多行文本setFont 设置字体setHorizontalAlignment 设置文本水平对齐方式setDefaultCloseOperation 设置默认的关闭操作add 增加JButton 按钮JCheckBox 复选框JRadioButton单选按钮addItem 增加列表项getItemAt 得到位置的列表项getItemCount 得到列表项个数setRolloverIcon 当鼠标经过的图标setSelectedIcon 当选择按钮的图标getSelectedItem 得到选择的列表项getSelectedIndex 得到选择的索引ActionListener 按钮监听ActionEvent 按钮事件actionPerformed 按钮单击方法(编程词汇A2A integration A2A整合abstract 抽象的abstract base class (ABC)抽象基类abstract class 抽象类abstraction 抽象、抽象物、抽象性access 存取、访问access level访问级别access function 访问函数account 账户action 动作activate 激活active 活动的actual parameter 实参adapter 适配器add-in 插件address 地址address space 地址空间address-of operator 取地址操作符ADL (argument-dependent lookup)ADO(ActiveX Data Object)ActiveX数据对象advanced 高级的aggregation 聚合、聚集algorithm 算法alias 别名align 排列、对齐allocate 分配、配置allocator分配器、配置器angle bracket 尖括号annotation 注解、评注API (Application Programming Interface) 应用(程序)编程接口app domain (application domain)应用域application 应用、应用程序application framework 应用程序框架appearance 外观append 附加architecture 架构、体系结构archive file 归档文件、存档文件argument引数(传给函式的值)。
H3C交换机VRRP和堆叠

H3C交换机VRRP和堆叠1. 前⾔平时对系统和主机的维护⼯作⽐较多⼀些,对⽹络设备的配置就相对少了很多。
最近为了上⼀批设备,针对交换机的配置也学习了⼀番,本⽂记录⼏个在实操中⽤到的实例。
2. 概念在系统运维中,经常会⽤冗余的⽅式来保证业务、服务、系统的⾼可⽤性,⽽在⽹络中也存在冗余和⾼可⽤的⽅式。
对于交换机来说,VRRP 和堆叠。
2.1 MSTP这⾥不准备对 STP 进⾏展开了说,为了快速的学习交换机的配置,这部分原理知识后续在补充。
为了解决单点故障的问题,⽹络设备引⼊了冗余的机制,通过冗余链路来实现⽹络的冗余,但是冗余⼜会引发新的环路问题,如图:我们都知道交换机是根据 MAC 地址表来转发数据帧的,如果地址位置未知,则⼴播,如果交换机接收到⼴播帧也会像所有端⼝发送,实际上这种来回循环在⽹络中已经形成了环路,成为了物理环路,在交换机内部已经形成了⼴播风暴,这种风暴的形成最终的结果就是⽹络资源的耗尽,交换机的死机,影响正常⼯作。
要控制这样的⼴播风暴,就需要引⼊ STP ⽣成树协议。
逻辑上是断开环路,防⽌⼴播风暴的产⽣,当线路故障,阻塞接⼝就被会激活,恢复通信,起到备份线路的作⽤。
上⾯是对 STP 的讲述,现在很多交换机都默认采⽤ MSTP 这种⽅式。
MSTP 主要是将⼆层设备上端⼝绑定到不同的链路,从⽽实现不同链路的⽣成树计算相互独⽴,互不影响。
特点:mstp可以快速收敛,⼜提供了数据转发多个冗余路径,在数据转发过程中实现 vlan 数据负载均衡。
在这个图中,很明显SW1 - SW2 - SW3 形成了⼀个环路,这个时候就需要使⽤到 stp ⽣成树协议。
当 host-1 的⽹关为: SW1 ⽽达到 SW1 有两条链路:Host1 --> SW3 --> SW1Host1 --> SW3 --> SW2 --> SW1同理, host-2 到达 SW2 也是有两条链路的,通过⽇常⽣活也能够知道,⽬的地越近越好,能否按照下图这样的⽅式来⾛呢?这样,即选择了最优的链路,数据也能负载均衡到不同的链路上。
华为HCIA网络技术实验配置及拓扑图

SIMON///s/1RMKmPaOdQ2g_BY6t3dHhZQ 提取码: 74rv
目录
1、测试主机连通性........................................................................................................................................... 3 2、Telnet 配置认证 ........................................................................................................................................... 3 3、Stelnet 和 SFTP 配置 RSA 认证 ............................................................................................................... 4 4、配置通过 FTP 进行文件操作.................................................................................................................... 8 5、配置接口双工模式、速率 ...................................................................................................................... 10 6、Vlan 及 Access 接口配置......
CS单元测试题

单元测试(一)一、选择题(每小题2分,共50分)1、Java中定义类头时,不可能用到的关键字是( B )。
A)class B)private C)extends D)public2、下列类头定义中,错误的是( A )。
A)public x extends y {...}B)public class x extends y {...}C)class x extends y implements y1 {...}D)class x {...}3、设 A为已定义的类名,下列声明A类的对象a的语句中正确的是( D )。
A) float A a; B) public A a=A( );C) A a=new int( ); D) static A a=new A( );4、设i、j为类X中定义的int型成员变量名,下列X类的构造方法中不正确的是( D )。
A) void X(int k ){ i=k; } B) X(int k ){ i=k; }C) X(int m, int n ){ i=m; j=n; } D) X( ){i=0;j=0; }5、以下为类A中构造方法的声明,其中正确的是( B )。
A)void A(int x){...} B) public A(int x){...}C)public a(int x){...} D) static A(int x){...}6、下列方法定义中不正确的是( D )。
A) float x( int a,int b ) { return (a-b); }B) int x( int a,int b) { return a-b; }C) int x( int a,int b ) { return a*b; }D) int x(int a,int b) { return 1.2*(a+b); }7、Java语言中类间的继承关系是( B )。
A)多重的 B) 单重的 C) 线程的 D) 不能继承8、以下关于Java语言继承的说法正确的是( C )。
软件开发人员英语单词集

JA V A关键字Abstract['æbstrækt]adj. 抽象的n. 摘要;抽象;抽象的概念Boolean['bu:liən] adj. 布尔Break[breik]vt. 打破,弄破;中断;中止Byte[bait]n. [计]字节;8位元组case [keis] n.情形,情况,箱,案例cast [kɑ:st] n.投掷catch [kætʃ] v.抓住;赶上,了解,感染char[tʃɑ:]n.字符class[klɑ:s, klæs]n. 阶级;班级;种类continue [kən'tinju:]vi. 继续,延续;连续default [di'fɔ:lt]n. [计]系统默认值do[du:] vt. 做;进行;完成;解答double ['dʌbl] n. 两倍;[计]双精度型else [els] adv. 其他;否则;另外extends [ik'stends]v. 延伸;扩充;继承false [fɔ:ls]adj. 错误的;虚伪的;伪造的final ['fainəl] adj. 最终的;不可更改的future ['fju:tʃə] adj. 将来的finally ['fainəli]adv. 最后;决定性地float[fləut] n.漂流物;浮舟;浮萍for [fɔ:; fə]conj. 因为prep. 给,为循环if [if] conj. 如果n. 条件,设想implements['implimənt, 'impliment]vt. 实施,执行;实现,使生效import[im'pɔ:t] n. 进口vt. 输入,进口instanceof['instəns] n. 实例;运算符int[int] abbr. [计]整数,中断interface['intə(:),feis]n. [计] 界面,接口long[lɔŋ, lɔ:ŋ]长整型native['neitiv] adj. 本国的;本地的new[nju:]创建新的实例null[nʌl] n. 零,空package['pækidʒ] n. 包,包裹private['praivit] adj. 私人的;私有的protected[prə'tektid]受保护的public['pʌblik]a. 公共的,公众的return [ri'tə:n] v. 返回,归还,回来short [ʃɔ:t] adj. 短的static['stætik] adj. 静态的super['sju:pə]switch[switʃ] vi. 转换n. 开关synchronized['siŋkrənaiz]adj. 同步的this [ðis]pron. 这;这个throw [θrəu] vt. 投;抛throwstransient['trænziənt] adj. 短暂的true[tru:]adj. 真实的;正确的常用编程术语try[trai]vi. 尝试;努力;试验void[vɔid]无类型volatile['vɔlətail] 【计算机】易失的while[(h)wail]conj. 当...的时候const n. 常量,常数goto vi. 转到无条件转移Utility[ju:'tiliti] n. 公用程序Struts[strʌtz] n. [计算机]标记层;源代码Dynamic[dai'næmik]adj. 动态的features ['fi:tʃə] n. 特色,特征graphics ['græfiks] n.[计算机]图形学template ['templit]模板,样板enum(enumerate)[ɪˈnu:məˌreɪt]枚举allocation[,æləu'keiʃən] 分配、定位applications [,æpli'keiʃən]应用程序client ['klaiənt]客户,客户机directory [di'rektəri]目录domain [dəu'mein] name 域名filter ['filtə]过滤器IP(Internet Protocol ['prəutəkɔl])网际协议authorization [,ɔ:θərai'zeiʃən]授权Back up备份browser ['brauzə]浏览器channel ['tʃænəl]信道、通路CGI(Common ['kɔmən] Gateway Interface)公用网关接口crash [kræʃ](崩溃)Component[kəm'pəunənt]组件environment variable['vєəriəbl]环境变量fragments['fræɡmənt] 分段gateway ['geitwei]网关hyperlink ['haipəliŋk]超文本链接icon ['aikɔn]图标Java Virtual['və:tjuəl] Machine Java虚拟机message ['mesidʒ]消息Module['mɔdju:l]模块path [pɑ:θ]路径permission[pə(:)'miʃən]权限prority['prɔriti]优先权protocol ['prəutəkɔl]协议process [prə'ses]进程proxy ['prɔksi]代理route [ru:t]路由router ['ru:tə(r)]路由器thread[θred]线程Virtual directory虚目录Virtual Machine虚拟机workstation ['wə:ksteiʃ(ə)n]工作站application framework应用程式框架architecture ['ɑ:kitektʃə]系统架构、体系结构array [ə'rei]阵列数组assembly [ə'sembli] language 汇编语言binary['bainəri] operator二元操作符border['bɔ:də]边框、框线边框button ['bʌtən]按钮按钮communication [kə,mju:ni'keiʃn] 通讯command [kə'mɑ:nd] line 命令列命令行combo ['kɔmbəu] box 复合方块、复合框组合框compiler [kəm'pailə]编译器编译器component [kəm'pəunənt]组件组件composition[kɔmpə'ziʃən]复合、合成、组合组合concept['kɔnsept]概念概念concurrent [kən'kʌrənt]并行并发configuration [kən,figju'reiʃən]组态配置connection [kə'nekʃən]连接,连线constraint[kən'streint] 约束(条件)construct [kən'strʌkt] 构件构件container [kən'teinə] 容器容器containment[kən'teinmənt]内含包容context ['kɔntekst]背景关系、周遭环境control [kən'trəul]控制元件、控件控件console [kən'səul]主控台控制台cursor ['kə:sə]游标光标custom['kʌstəm]订制、自定定制database schema ['ski:mə]数据库结构纲目data structure ['strʌktʃə]数据结构debug [di:'bʌg] 除错调试debugger [di:'bʌgə]除错器调试器declaration [,deklə'reiʃən]宣告声明define [di'fain]定义预定义definition [,defi'niʃən]定义、定义式constant ['kɔnstənt]常数常量constructor[kən'strʌktə]建构式构造函数destroy [dis'trɔi]摧毁、撤消destructor [dis'trʌktə]解构式析构函数directive [di'rektiv]指令(编译)指示符dispatch [dis'pætʃ]分派分派distributed[dis'tribju:tid]computing分布式计算document ['dɔkjumənt]文件文档equal ['i:kwəl]相等event [i'vent]事件e vent driven ['drivn]事件驱动的exception [ik'sepʃən]异常情况异常procedure [prə'si:dʒə]程序过程profile ['prəufail]评测评测programmer ['prəugræmə]程序员project ['prɔdʒekt]专案项目、工程property ['prɔpəti]属性qualified ['kwɔlifaid]经过资格修饰qualifier ['kwɔlifaiə]资格修饰词queue [kju:]伫列队列random ['rændəm] number随机数、乱数record ['rekɔd,ri'kɔ:d] 记录reference ['refrəns]引用、叁考址叁器register ['redʒistə]暂存器寄存器reflection [ri'flekʃən]反射、映像relational[ri'leiʃənəl]database关系数据库represent [,ri:pri'zent] 表述,表现routine [ru:'ti:n]常式例程schedule ['skedʒjul]排程调度scroll [skrəul]bar/ 卷轴滚动条serial ['siəriəl]串行specification [,spesifi'keiʃən]规格、规范solution[sə'lju:ʃən]解法,解决方案方案stack [stæk]堆叠栈statement['steitmənt]述句语句、声明symbol ['simbəl]符号记号syntax ['sintæks]语法template ['templit]模板、范本模板transaction [træn'zækʃən]交易事务trigger ['trigə]触发UML unified['ju:nifaid]modeling['mɔdliŋ] language统一建模语言variable['vєəriəbl]变量vector ['vektə]向量viable ['vaiəbl]可实行的、可行的exception declaration异常声明exception handling['hændliŋ]异常处理exception specification [,spesifi'keiʃən]异常规格exit ['eksit]退离,退出expression [iks'preʃən]运算式、表达式facility [fə'siliti]设施、设备feature ['fi:tʃə]特性field [fi:ld]栏位,资料栏flush [flʌʃ]清理、扫清刷新formal ['fɔ:məl] parameter[pə'ræmitə]形式叁数function['fʌŋkʃən]函式、函数function object ['ɔbdʒikt]函数对象functionality [,fʌŋkəʃə'næliti]功能、机能generate['dʒenə,reit]生成,产生generic [dʒi'nerik] /泛型、通用的、泛化global object全域物件全局对象node[nəud]节点assignment [əˈsaɪnmənt] 指派、指定赋值、分配cache[kæʃ]快取高速缓存character[ˈkæriktə]字元字符dialog[ˈdaiəlɔɡ]对话窗、对话框expression[iksˈpreʃən]运算式、表达式identifie r[aiˈdentifaiə]标识符initialize[iˈniʃəlaiz] 初始化invoke [ɪnˈvəʊk] 唤起调用modifier[ˈmɔdifaiə]饰词修饰符operating system (OS)/ 作业系统操作系统operation[ˌɔpəˈreiʃən]操作、操作行为override[ˌəuvəˈraid]改写、覆写重载、overflow[ˌəuvəˈfləu]上限溢位overload[ˌəʊvəˈləʊd]多载化、重载Agent[ˈeidʒənt]代理Attachment [əˈtætʃmənt]附件Column[ˈkɔləm]列Search engines[ˈendʒins]搜索引擎virus[ˈvaiərəs]病毒web portals[ˈpɔ:təl] 门户网站DBMS database management[ˈmænidʒmənt] system数据库管理系统HTML Hypertext Markup Language超文本标示语言SQL structured query[ˈkwiəri] language结构化查询语言URL uniform resource locator[ləuˈkeitə] 统一资源定位器CPU central[ˈsentrəl] processing unit [ˈju:nit]中央处理器file transfer protocol[ˈprəʊtəˌkɔ:l] (FTP)文件传送协议hypertext[ˈhaipəˌtekst] markup language(HTML)超文本链接标识语言uniform[ˈju:nifɔ:m]resource locator(URL)统一资源定位器Wide area network(WAN)广域网Local area network(LAN)局域网align [əˈlaɪn] 排列、对齐asynchronous[eiˈsiŋkrənəs]异步的bitmap[ˈbɪtˌmæp]位图cascading [kæˈskeɪd] delete级联删除cascading update级联更新console[kənˈsəul]控制台data integrity[inˈteɡriti]数据完整性digest[daiˈdʒest]摘要formal[ˈfɔ:məl]parameter[pəˈræmitə]形参infinite[ˈinfinit] loop无限循环initialization[iˌniʃəlaiˈzeiʃən]list初始化列表integrity[inˈteɡriti]完整性、一致性object oriented[ˈɔ:rientid]面向对象的。
config加密与解密

section.SectionInformation.UnprotectSection();
config.Save();
}
}
总结:此方法很方便,并且很简单,但安全性没有密钥加密高。
方法二、
此时,只需运行:
aspnet_regiis -pdf "connectionStrings" "F:\zizhubm"
就可以对web.config文件进行解密。
(注意,如果还是有错误,那可能是您没有给生成的密匙文件足够的权限,去到 C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\RSA\MachineKeys 目录下,
需要添加引用
using System.Web.Configuration;
using System.IO;
//加密
protected void Button1_Click(object sender, EventArgs e)
{
Configuration config = WebConfigurationManager.OpenWebConfiguration(Request.ApplicationPath);
{
section.SectionInformation.ProtectSection("DataProtectionConfigurationProvider");
config.Save();
}
}
aspnet_regiis -pz "Key"
删除后再运行程序,会提示出错:
华为路由器配置手册---

华为路由器配置手册华为路由器配置手册第一章系统基本命令本章主要介绍命令行接口相关命令、配置文件管理命令、基本的系统管理命令、网络测试工具命令、系统调试命令、SNMP配置命令、日志配置命令和终端服务命令。
第二章接口配置命令本章主要介绍以太网口配置命令、串口配置命令、CE1/PRI接口配置命令和接口管理命令。
第三章广域网协议配置命令本章主要介绍PPP、SLIP、MP、LAPB、X.25、X.25交换、帧中继和ISDN协议配置命令。
第四章网络协议配置命令本章主要介绍IP地址配置命令、静态地址解析配置命令、静态域名解析配置命令、地址转换配置命令、IP性能配置命令、静态路由配置命令、OSPF路由协议配置命令、RIP路由协议配置命令、IGRP路由协议配置命令、BGP路由协议配置命令和IPX协议配置命令。
第五章安全配置命令本章主要介绍AAA配置命令、Radius协议配置命令、终端访问安全配置命令、防火墙配置命令和包过滤配置命令。
第六章拨号配置命令本章主要介绍DDR配置命令和Modem管理配置命令。
第七章备份中心配置命令本章主要介绍备份中心配置命令。
第八章VPN配置命令本章主要介绍L2TP协议配置命令。
第九章桥配置命令本章主要介绍透明桥协议配置命令。
第十章Quidway(R)系列路由器调试命令本章主要介绍调试命令的使用方法及各协议或功能的调试命令。
第一章系统基本命令1.1命令行接口相关命令与命令行接口相关的命令包括:configurecontroller e1disableenableexithelpinterfacelanguagelogic-channelroutershow historyvpdn-group1.1.1 configure用户使用configure命令从特权用户模式进入全局配置模式。
configure【命令模式】特权用户模式【举例】Quidway#configureEnter configuration commands, one per line. End with command exit! Quidway(config)#【相关命令】exit1.1.2. controller e1用户使用controller e1命令从全局配置模式进入CE1/PRI接口配置模式。
EM530 EM540三相和两相系统能量分析仪用户手册说明书

EM530/EM540Energy analyzer for three-phase and two-phase systemsUSER MANUALSummaryEM530 and EM540 5 Introduction 5 Description 5 Available versions 6 UCS (Universal Configuration Software) 7Use 8 Interface 8 Introduction 8 SETTINGS menu display 8 INFO menu display 8 RESET menu display 8 Measurement page display 8 Information and warnings 9Working with EM530/EM540 10 Working with the measurement pages 10 Working with the SETTINGS menu 10 Working with the INFO menu 10 Working with the RESET menu 10Commissioning 11 Preliminary settings 11 MID SETTINGS menu 11 QUICK SETUP menu 12 Menu description 13 Measurement pages 13 SETTINGS menu 14 INFO menu 15 RESET menu 16Input, output and communication 17 Digital input 17 Digital output (version O1) 17 Modbus RTU port (version S1) 17 M-Bus port (version M1) 17Essential information 18 Alarms 18 Introduction 18 Variables 18 Alarm types 18 DMD values 19 Average value calculation (dmd) 19 Integration interval 192EM530/EM540 - User manual | CARLO GAV AZZI Controls SpAExample 19 LCD display 19 Home page 19 Backlight 19 Screensaver 19 Page filter 19 Restoring the factory settings 20 Restoring the settings using the RESET menu 20 Restoring the MID menu using the RESET menu 21 WIRING CHECK function 22 Introduction 22 Display check 22 Check from UCS software 22 Virtual correction from UCS software or UCS Mobile 22 Tariff management 22 Tariff management via digital input 22 Tariff management Modbus RTU 22Maintenance and disposal 23 Troubleshooting 23 Alarms 23 Communication problems 23 Display problem 23EM530/EM540 - User manual | CARLO GAV AZZI Controls SpA3Information propertyCopyright © 2019, CARLO GAVAZZI Controls SpAAll rights reserved in all countries.CARLO GAVAZZI Controls SpA reserves the right to apply modifications or make improvements to the relative documentation without the obligation of advance notice.Safety messagesThe following section describes the warnings related to user and device safety included in this document: NOTICE: indicates obligations that if not observed may lead to damage to the device.CAUTION! Indicates a risky situation which, if not avoided, may cause data loss.IMPORTANT: provides essential information on completing the task that should not be neglected.General warningsThis manual is an integral part of the product and accompanies it for its entire working life. It should be consulted for all situations tied to configuration, use and maintenance. For this reason, it should always be accessible to operators.NOTICE: no one is authorized to open the analyzer. This operation is reserved exclusively for CARLO GAVAZZI technical service personnel.Protection may be impaired if the instrument is used in a manner not specified by the manufacturer.Service and warrantyIn the event of malfunction, fault, requests for information or to purchase accessory modules, contact the CARLO GAVAZZI branch or distributor in your country.Installation and use of analyzers other than those indicated in the provided instructions void the warranty.Download4EM530/EM540 - User manual | CARLO GAV AZZI Controls SpA5EM530/EM540 - User manual | CARLO GAV AZZI Controls SpA EM530 and EM540EM530 is an energy analyzer connected through 5 A current transformers, for two- and three-phase systems up to 415 V L-L.EM540 is an energy analyzer for direct connection up to 65 A, for two- and three-phase systems up to 415 V L-L.In addition to a digital input, the unit can be equipped, according to the model, with a static output (pulse or alarm), a Modbus RTU communication port or an M-Bus communication port.EM530 - FrontEM540 - FrontEM530 and EM540 – BackPFA modelsEasy connection function: irrespective of the current direction, the power always has a plus sign and contributes to increase the positive energy meter. The negative energy meter is not available.PFB modelsFor each measuring time interval, the individual phase energies with a plus sign are summed to increase the positive energy meter (kWh+), while the others increase the negative one (kWh-).Example:P L1= +2 kW, P L2= +2 kW, P L3= -3 kWIntegration time = 1 hourkWh+ = (2+2) x1h = 4 kWhkWh- = 3 x 1h= 3kWh6EM530/EM540 - User manual | CARLO GAV AZZI Controls SpAPFC modelsFor every measuring interval time, the energies of the single phases are summed; according to the sign of the result, the positive (kWh+) or negative totalizer (kWh-) is increased.Example:P L1= +2 kW, P L2= +2 kW, P L3= -3 kWIntegration time = 1 hour+kWh=(+2+2-3)x1h=(+1)x1h=1 kWh-kWh=0 kWhUCS is available in desktop and mobile versions.It may connect to EM530 or EM540 via RS485 (RTU protocol, desktop version only).UCS allows to:• set up the unit (online or offline);• display the system state for diagnostic and setup verification purposesOverview of the UCS functions:• Setting up the system with energy meter connected (online setup)• Defining the setup with energy non connected, then applying it later (offline setup)• Displaying the main measurements• Displaying the state of inputs and outputs• Displaying the state of the alarms• Recording the measurements of selected variables• Check connection and correct wiring errorsEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA7UseInterfaceEM530 and EM540 are organized into two menus:• Measurement pages: pages allowing to display the energy meters and the other electrical variables• Main menu, divided into three sub-menus:»SETTINGS: pages allowing to set the parameters»INFO: pages displaying general information and the set parameters»RESET: pages allowing to reset the partial counters and the dmd calculation, or to restore the factory settings8EM530/EM540 - User manual | CARLO GAV AZZI Controls SpAEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA910EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpAWorking with EM530/EM540Working with the SETTINGS menuWorking with the INFO menuWorking with the RESET menu11EM530/EM540 - User manual | CARLO GAV AZZI Controls SpA CommissioningCommissioningAt switch-on, the device displays two preliminary setting menus:• MID SETTINGS, for EM530, MID models only • QUICK SETUPThis procedure, only available in MID models, allows to program the current transformer ratio (CT ratio).12EM530/EM540 - User manual | CARLO GAV AZZI Controls SpACommissioningThis procedure is available when the instrument is switched on for the first time.Note: the available parameters depend on the model.In the “QUICK SETUP?” starting pageS1 modelsM1 modelsO1 models13EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA Menu descriptionThe displayed pages depend on the selected system.14EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA17Thd LL THD of phase 1-phase2 voltage THD of phase2-phase3 voltage THD of phase3-phase1 voltage 18Thd A THD of phase 1 current THD of phase 2 current THD of phase 3 current 19nEutrAL CurrEnt Neutral current20L1 kVA L2 kVA L3 kVA Phase 1 apparent power Phase 2 apparent power Phase 3 apparent power 21L1 kvar L2 kvar L3 kvar Phase 1 reactive power Phase 2 reactive power Phase 3 reactive power 22L1 PF L2 PF L3 PF Phase 1 power factor Phase 2 power factor Phase 3 power factor 23L1-N V L2-N V L3-N V Phase 1 voltage Phase 2 voltage Phase 3 voltage 24L1-2 V L2-3 V L3-1 V Phase 1-phase 2 voltage Phase 2-phase 3 voltage Phase 3-phase 1 voltage 25L1 A L2 A L3 A Phase 1 current Phase 2 current Phase 3 current 26L1 kW L2 kW L3 kW Phase 1 active power Phase 2 active power Phase 3 active power 27L1 kWh TOT L2 kWh TOT L3 kWh TOTActive energy phase 1Active energy phase 2Active energy phase 315EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpARS485AddrESS Address 1 to 2471S1 models onlyPArity Parity NO/EVEN no bAudrAtEBaudrate9.6 kbps 19.2 kbps 38.4 kbps 57.6 kbps 115.2 kbps 9.6 kbpsStoP bitStop bit 1 or 21M busPri Add Primary address 1 to 250 0M1 models onlybAudrAtEBaudrate0.3 kbps 2.4 kbps 9.6 kbps2.4 kbpsOutput Function Function OffPuLSE (kWh+): pulse output linked to kWh+PuLSE (kWh-): pulse output linked to kWh-ALArM: linked to alarm status PuLSE (kWh+)O1 models onlydurAtion Pulse duration30 ms 100 m30 ms PuLSES Pulse weight (pulses/kWh)0.1/1/10/100/500/10001000StAtuSOutput status No (normally open)Nc (normally closed)ALARMEnAbLE EnableYES/no no VAriAbLEMonitored variablekW A V L-N V L-L PF Kvar kVAkWSEt 1Activation threshold -15000 to 150000.00Set 2Deactivation threshold -15000 to 150000.00dELAYActivation delay0 to 3600 s 0dISPLAYLiGHtTimer for backlight switch-offOn: always on 1 min 2 min 5 min 10 min 15 min 30 min 60 minoFF: always off OnSC SAVErScreensaver enabling, see “Screensaver” on page 19oFFSLidE: slideshow home: homepage home Non-MID models onlyHOME homepage1 to 271Non-MID models onlyPAGESMeasurement page filterenabling, see “Page filter” on page 19ALL FiLtEr OFFWirinGWiring check enabling on/OFFonPASS Password enabling for the SETTINGS and RESET menu0 (not protected) to 99990 (NOTPROTECTED)End-Exit--16EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA9Input Function Digital input function 10rS 485AddrESS Address S1 versions only 11rS485bAudrAtE Baudrate (kbps)S1 versions only 12rS485PArity Parity S1 versions only 13rS485StoP bit Stop bitS1 versions only 14M buS PriM Add M-Bus primary address M1 versions only 15M bus bAudrAte M-Bus baudrate M1 versions only 16M bus SEC Add M-Bus secondary address M1 versions only 17output Function Digital output function O1 versions only 18Output StAtuS Current output status O1 versions only 19output duration Pulse output duration O1 versions only 20Output PuLSE Output pulse weight O1 versions only21ALArM EnAbLe Alarm enabling 22ALArM VAriAbLE Linked variable 23ALArM SEt 1Alarm activation set point 24ALArM SEt 2Alarm deactivation set point 25ALArM dELAY Alarm activation delay 26display LIGHt Backlight timer 27display SC SAVEr Screensaver type 28display home Home page 29display PAGES Page filter enabling 30display WirinG Wiring check enabling 31tAriFF Tariff management 32CHECKSuM Firmware checksum33WiRinG Wiring check code to correct errors34terminal Screw terminal phase assignment (press enter to see)35On time Total working time 36EndExitThis menu allows to reset the following settings:17EM530/EM540 useEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA Input, output and communicationDigital inputThe digital input can perform four functions:Digital output (version O1)The digital output can perform two functions:Modbus RTU port (version S1)Modbus RTU communication port is used to transmit data to a Modbus master (Carlo Gavazzi UWP3.0 or any SCADA, PLC, BMS, etc).For further information about Modbus RTU communication refer to the communication protocol.M-Bus port (version M1)M-Bus communication port is used to transmit data to a M-Bus master (Carlo Gavazzi SIU-MBM or any third party M-Bus mas-ter).For further information about M-Bus communication refer to the communication protocol.18Essential informationEM530/EM540 - User manual | CARLO GAV AZZI Controls SpAEssential informationAlarmsEM500 manages a measured variable alarm. To set the alarm, define:• the variable to be monitored (VARIABLE )• alarm activation threshold value (SET POINT 1)• alarm deactivation threshold value (SET POINT 2)• alarm activation delay (ACTIVATION DELAY )The unit can monitor one of the following variables:• system active power • system apparent power • system reactive power • system power factor• phase-neutral voltage (OR logic)• phase-phase voltage (OR logic)• current (OR logic)Note: if you select a current or a voltage, the analyzer simultaneously monitors all the phases available in the set measurement system and triggers the alarm when at least one of the phases is in alarm (OR logic)Up alarm (Set point 1 ≥ Set point 2)The alarm activates when the monitored variable exceeds the Set 1 value for a time equal to the activation delay (Delay) and deactivates when the values drops below Set 2.(s)Set 1Set 2DelayDown alarm (Set point 1 < Set point 2)The alarm activates when the monitored variable drops below the Set 1 value for a time equal to the activation delay (Delay) and deactivates when it exceeds Set 2.(s)Set 2Set 1Delay19Essential informationEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA DMD valuesEM530 and EM540 calculate the average values of the electrical variables within a set integration interval (15 min by default).The integration interval starts at switch-on or when the reset command is issued. The first value is displayed at the end of the first integration interval.The following is a sample integration:• reset at 10:13:07• set integration time: 15 min.The first value displayed at 10:28:07 refers to the interval from 10:13:07 to 10:28:07.LCD displayThe unit may display the default measurement pages after no operation has been performed for five minutes, if the screensaver is enabled and the screensaver type is as “Home page” (default value).Notes: if you select a page that is not available in the set system, the unit displays as its home page the first available page. In MID models the home page cannot be changed and displays the active energy meter.EM530 and EM540 are equipped with a backlight system. You can set whether the backlight shall always be ON or whether it should automatically switch off after a given interval has elapsed since a button was pressed (1 to 60 minutes).If the SCREENSAVER function is enabled (default setting), after 5 minutes have elapsed since a button was pressed the unit will display the home page if the screensaver type is “Home page” (default setting), or it shall activate the slideshow function, which displays the selected pages on a rotating basis.Notes: In MID models the screensaver setting is “Homepage” and cannot be changed.The page filter makes it easier to use and browse the measurement pages. When you use the buttons, the unit shall only display the pages you are most interested in, which can be selected through the UCS software (S1 version) or is pre-defined (O1 and M1 version)Note: to display all the pages without using the UCS software, you can disable the page filter from the SETTINGS MENU (DISPLAY → PAGES→ ALL). By default, the pages included in the filter are: 1 (kWh+ TOT, kW), 2 (kWh- TOT, kW), 5 (VLN, VLL, Hz), 7 (kvarh+ TOT, kvar), 8 (kvarh- TOT, kvar), 25 (L1 A, L2 A, L3 A), see “Measurement pages” on page 13.20Essential informationEM530/EM540 - User manual | CARLO GAV AZZI Controls SpARestoring the factory settingsFrom the RESET menu you can restore all the factory settings. At start-up the QUICK SET-UP menu shall be available again.Notes:meters are not reset. In MID models you cannot reset the CT current transformer ratio (CT RATIO).21Essential informationEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA To change the set CT ratio and restore the MID settings menu shown at first power on EM530 MID models, enter the reset menuand confirm “MID res”.Note: in MID models the reset can only be performed if the energy meter has not exceeded 1 kWh. In case of wrong settings, you can then correct any CT current transformer setting errors (CT ratio), reactivating the MID programming menu.Notes: if active energy has exceeded 1 kWh, the CT ratio cannot be changed.22Essential informationEM530/EM540 - User manual | CARLO GAV AZZI Controls SpAWIRING CHECK functionThe WIRING CHECK function allows to check and correct the connections.For it to work properly, the following three conditions must be met:1. the set system must be “3P+N”,2. all voltages must be connected,3. All currents must be greater than zero, with an offset ranging between a 45° lag and a 15° lead (power factor > 0.7 inductiveor > 0.96 capacitive)During operation, if a wiring error is detected the alarm icon will light up.If the three conditions fail to be met, the following indications shall be displayed in the WIRING info page:• V MISSING: at least one voltage is missing• I MISSING: at least one current is missing• PF OUT OF RANGE: the current-voltage offset is out of range.By connecting to the analyzer through the UCS software or UCS Mobile, you can verify the connections and perform the steps required to correct the wiring error.The virtual correction function allows to calculate the wiring error solution and to modify the association of the physical connections with the measurement references.Example if the connections of terminals 5 and 6 are inverted (voltage 2 and voltage 3), by accepting the proposed solution, voltage 2 shall be the one measured with reference to terminal 6, while voltage 3 shall be the one referring to terminal 5.The unit shall display theicon, signalling that the association was modified via software and referring to the info pages to check the phase-terminal associations set by UCS.Note: the function is not available in MID modelsTariff managementTo manage tariffs using the digital input set the function of the digital input as tariff (via keypad or UCS software).The current tariff depends on the status of the inputTariff management Modbus RTUTo manage tariffs using the Modbus RTU command enable tariff management via Modbus command from UCSMaintenance and disposalTroubleshootingNote: in case of other malfunctions or of any failure, please contact the CARLO GAVAZZI branch or the distributor for your countryAlarmsCommunication problemsDisplay problemDownloadEM530/EM540 - User manual | CARLO GAV AZZI Controls SpA23CleaningTo keep the display clean, use a slightly wet cloth. Never use abrasives or solvents.Responsibility for disposalDispose of the unit by separately collecting its materials and bringing them to the facilities specified by government authorities or by local public bodies. Proper disposal and recycling will help preventing potentially harmful consequences for the environment and for people.24EM530/EM540 - User manual | CARLO GAV AZZI Controls SpACARLO GAVAZZI Controls SpAvia Safforze, 832100 Belluno (BL) Italy***************************info: +39 0437 355811fax: +39 0437 355880EM530_EM540 - User Manual2021-09 | Copyright © 2020。
TE相关排障命令

一、考试故障诊断命令1.Ping:Comware ping:ping -a x.x.x.x y.y.y.y 用源地址x.x.x.x去ping目的地址y.y.y.y2. Tracert:Tracert是为了探测源节点到目的节点之间数据报文所经过的路径。
别忘了开启ip unreachable enable和ip ttl enable!3. debugging使用debugging命令前,先输入以下命令:<h3c>terminal debugging <H3C>terminal monitor,使用完debuggin命令后,通过undo debug all命令关闭调试。
二、调整串行接口波特率V.24 可以工作在同步或异步,同步最高64Kbps,异步最高115200bps。
V.35 只能工作在同步,最高2Mbps。
TE考试一般使用V.35线缆,使用display interface serial xxx,观察接口是DTE还是DCE V.35串口线接口的实际速率是由接口的波特率决定(默认64K),在DCE接口下使用baudrate xxx命令修改波特率,在DTE接口下使用virtual-baudrate xxx命令修改波特率。
三、PPP协议故障排除1. PPP协议故障排除的一般步骤●验证问题分析→使用display interface命令查看接口信息,如显示LCP协议进入OPENED状态,而IPCP依然为Initial状态;或者LCP变为OPENED状态后又很快重新开始协商,可考虑为验证的问题。
→通过debugging ppp all查看提示信息。
如果成功协商了验证,PPP会打印出PAP或CHAP验证的报文,如果验证失败,会打印出“PPP authentication failed”信息,可以根据报文的具体内容分析验证失败的原因。
2.PPP验证的考点●检查题目所要求的认证方式(单向和双向)●检查验证端设备local-user配置账号的信息(sevice-type不指定该账户是不生效的)display local-user●检查验证端设备是否启动验证功能:display current-configuration int s2/0●检查被验证端设备配置发送的用户名:display current-configuration int s2/0●检查验证是否通过:debugging ppp all3.PPP捆绑的考点●检查物理接口是否启用ppp mp 功能,并绑定相应虚接口:display ppp mp四、VLAN协议故障排除●display vlan→用来显示VLAN的相关信息。
Cisco 880系列集成服务路由器数据册说明书

Data SheetCisco 880 Series Integrated Services RoutersThe Cisco® 880 Series Integrated Services Routers (ISRs) combine Internet access, security, voice, and wireless services onto a single, secure device that is simple to use and manage for small businesses and enterprise small branch offices and teleworkers. The Cisco 880 Series delivers features including firewall, content filtering, VPNs, and wireless LANs (WLANs) at broadband speeds to small offices. Easy deployment and centralized management features enable enterprises or service providers to deploy the Cisco 880 Series in small branch offices or small businesses. Product OverviewCisco 880 Series Integrated Services Routers are fixed-configuration routers that provide collaborative business solutions for secure voice and data communication to small businesses and enterprise teleworkers. They offer concurrent broadband services over third-generation (3G), Metro Ethernet, and multiple DSL technologies to provide business continuity. Wireless 802.11n and 3G offer LAN and WAN mobility. The routers provide the performance required for concurrent services, including firewall, intrusion prevention, content filtering, and encryption for VPNs; optional 802.11g/n for mobility; and quality-of-service (QoS) features for optimizing voice and video applications. In addition, the web-based Cisco Configuration Professional configuration tool simplifies setup and deployment. Centralized management capabilities give network managers visibility and control of the network configurations at the remote site.Cisco 880 Series Integrated Services Routers offer:●High performance for broadband access in small offices and small branch-office and teleworker sites●Collaborative services with secure analog, digital voice, and data communication●Business continuity and WAN diversity with redundant WAN links: Fast Ethernet, Multimode G.SHDSL(Ethernet in the First Mile [EFM] and ATM), Multimode DSL (very-high-data-rate DSL 2 [VDSL2] andasymmetric DSL 2 and 2+ [ADSL2 and ADSL2+, respectively]), 3G, and ISDN●Voice-enabling features:◦Cisco Unified Communications Manager Express (5 user), which offers innovative key system and small private-branch-exchange (PBX) capabilities for small and medium-sized business customers◦Survivable Remote Site Telephony (SRST) voice continuity for enterprise small branch-office and teleworker sites◦Cisco Unified Border Element (Cisco UBE) IP-IP voice gateway functions for connecting to Session Initiation Protocol (SIP) trunking services as a replacement for Primary Rate Interface (PRI) or foreign-exchange-office (FXO) voice connectivity to the service provider. Note: Cisco Unified Border Elementsupport for the Cisco 880 Series has feature limitations as compared to the Cisco Integrated ServicesRouters Generation 2 (ISR G2) Routers. Go to /go/cube for the full set of CiscoUnified Border Element features. Cisco Unified Border Element limitations on Cisco 880 Routers arelisted later in this document.●Enhanced security, including:◦Firewall with advance application and control for email, Instant Messaging (IM), and HTTP traffic◦Site-to-site remote-access and dynamic VPN services: IP Security (IPsec) VPNs (Triple Data Encryption Standard [3DES] or Advanced Encryption Standard [AES]), Dynamic Multipoint VPN (DMVPN), GroupEncrypted Transport VPN with onboard acceleration, and Secure Sockets Layer (SSL) VPN◦Intrusion prevention system (IPS): An inline, deep-packet inspection feature that effectively mitigates a wide range of network attacks◦Content filtering: A subscription-based integrated security solution that offers category-based reputation rating; keyword blocking; and protection against adware, malware, spyware, and Uniform ResourceLocator (URL) blocking●Four-port 10/100 Fast Ethernet managed switch with VLAN support; two ports support Power over Ethernet(PoE) for powering IP phones or external access points●Secure 802.11g/n access-point option based on draft 802.11n standard with support for autonomous orCisco Unified WLAN architectures●Newer Cisco 880 Series (part numbers C881-K9, C886VA-K9, C886VAJ-K9, C887VA-K9, C887VAM-K9and C888-K9), which are fanless, providing a quiet, comfortable working environment in small offices●CON/AUX port for console or external modem●One USB 1.1 port for security eToken credentials, booting from USB, and loading configuration●Easy setup, deployment, and remote-management capabilities through web-based tools and Cisco IOS®SoftwareFigure 1 shows a Cisco 881 Integrated Services Router.Figure 1. Cisco 881 Integrated Services Router with Integrated 802.11n Access PointTables 1 and 2 list the routers that currently make up the Cisco 880 data, voice, and SRST series, respectively. Table 1. Cisco 880 Series Data ModelsTable 2. Cisco 880 Series Voice ModelsThe Cisco 880 Series is ideal for small branch offices and teleworkers who need to be connected to larger enterprise networks as well as small businesses for either voice or data applications. These routers help extend corporate networks to secure remote sites while giving users access to the same applications found in a corporate office. When users require WLAN access, visibility and control of network security are even more critical at the remote site. The Cisco 880 Series meets this need with a single device that combines integrated 802.11g/n capabilities with security features such as Wi-Fi Protected Access (WPA), including authentication with IEEE 802.1x with Cisco Extensible Authentication Protocol (LEAP) and Protected EAP (PEAP) and encryption with WPA Temporal Key Integrity Protocol (TKIP). (Refer to the wireless solution overview and security data sheet for more information.) The Cisco 880 Series models that include the integrated access point can use either autonomous or Cisco Unified WLAN modes. In Cisco Unified WLAN mode, as part of an enterprise WLAN architecture, all WLAN functions are centrally managed through Cisco Wireless LAN Controllers and the Cisco Wireless Control System (WCS).Service providers and value-added resellers can take advantage of the Cisco 880 Series to provide a true business-class broadband service. Business customers are using broadband access to connect to the Internet or to connect offices together, and they require a platform that incorporates voice and security without sacrificing performance. The Cisco 881V and Cisco 887VA-V voice routers offer industry-leading voice gateway capability with the ability enable Cisco Unified Communications Manager Express or SRST as required. Many of these customers are connecting computers in offices through WLANs; having a single device for both WAN and WLAN access provides a new option for managed services. These customers also require a higher level of support to keep their networks operational. Services with these customers should be simple to set up, while allowing a level of remote management and troubleshooting to address support inquiries quickly. The Cisco 880 Series meets the requirements of small offices and managed services providers.Figure 2 shows deployment scenarios.Figure 2. Deployment ScenariosApplicationsThe Cisco 880 Series is ideally suited for deployment in a small office or in a small office that is part of a large network, most often with a secure VPN connection. These types of offices can include the following:●Small remote office: The Cisco 880 Series can connect users in a small remote office, such as aninsurance, lawyer, or sales office. When connecting to the main office, VPN encryption and integratedsecurity such as firewall and intrusion prevention protect the network at the perimeter. The Cisco 880 with the Cisco Unified Border Element Series can also support connection to SIP trunking voice-over-IP (VoIP) services the service provider offers. Additionally, IT managers can centrally manage the remote site toquickly troubleshoot any network problems. For added reliability, customers can also use the integrated 3G or ISDN backup or connect through an external modem if the primary broadband link fails. Integratedsecure unified WLAN connectivity simplifies the deployment and management devices at the remote site.Redundant WAN links offer business continuity, enabling nondisruptive business operation.●Virtual office: The Cisco 880 Series is ideal for corporate teleworkers who have a mix of broadbandconnection types such as DSL, 3G, and Metro Ethernet. The Cisco 880 Voice Gateway and SRST Series provides a secure virtual office with all the collaborative services such as data, voice, and fax services.SRST helps ensure voice services are operational in case of WAN link failure, and redundant WAN links help ensure business continuity. QoS features in the Cisco 880 Series allow for connection of an IP oranalog phone to the router, giving voice traffic precedence over data applications. Integrated WLAN support in the Cisco 880 Series helps ensure that if wireless connectivity is used it is secure. (Refer to the Cisco Virtual Office Solution, /go/cvo, for more information.)●Remote call-center agent: Similar to teleworking applications, this solution extends the Cisco IP ContactCenter solution for telephone call-center agents to remote sites. With a high-quality, secure connectionthrough the Cisco 880 Series, call-center agents can be dispersed away from costly call-center facilitieswhile maintaining secure and productive voice and data access in their homes. SRST and business-continuity solutions in the Cisco 880 Series provide reliability and continuous business operation.Alternatively, the remote call-center agent can be provided with SIP trunking service with servicedemarcation provided by Cisco Unified Border Element features, and the central call center can forwardcalls to the remote call-center agent through the remote-office SIP trunk.●Retail VPN: Retail stores migrating from dialup connections for point-of-sale transactions can use the Cisco880 Series to take advantage of low-cost broadband access with the required security to comply withpayment-card-industry (PCI) and other data security requirements. They can then add multiple devices and applications to the store network to take advantage of the increased bandwidth and also incorporateoptional WLAN support to enable secure mobility and enhance productivity.●Managed services: Service providers and value-added resellers can use the Cisco 880 Series as a platformto offer differentiated business-class security, voice, and WLAN services for small business customers. With built-in analog and digital voice ports and the ability to upgrade to a five-user Cisco Unified Communications Manager Express IP PBX, service providers can now offer all the Cisco Unified Communications benefits to small and medium-sized businesses. The SIP trunking connectivity features of the Cisco 880 with the Cisco Unified Border Element Series Router can provide the high-quality VoIP service needed through the service provider cloud.Features and BenefitsTable 3 lists the features and benefits of the Cisco 880 Series Integrated Services Routers.Table 3. Features and Benefits of Cisco 880 Series RoutersSummaryCisco 880 Series Integrated Services Routers combine increased network performance with advanced security to allow small-office customers to get the most from their broadband connections for both data and voice applications. With models supporting different broadband technologies such as DSL, 3G, and Metro Ethernet, the Cisco 880 Series can be deployed at any small-office location. Optional integrated 802.11g/n wireless capabilities provide true business-class WAN and WLAN access in a single solution. With the Cisco 880 Series, enterprise IT managers and service providers can take advantage of a solution that can be easily set up at the remote site and can be centrally managed to reduce ongoing operational costs.Product SpecificationsCisco IOS Software SupportTable 4 lists the minimum Cisco IOS Software releases and the default Cisco IOS Software feature sets.Table 4. Cisco IOS Software Releases and Default Cisco IOS Software Feature Sets* Cisco 881V, 887VA-V, 881 SRST, and 888 SRST run the Cisco 880 voice universal image, which shares the same data and security features as the Advanced IP feature sets of Cisco 880 data models.Tables 5 and 6 list Cisco IOS Software features of the Cisco 880 Series.Table 5. Cisco IOS Software Features on Cisco 880 Series: Advanced Security Feature Set (Default)Table 6. Cisco IOS Software Features on Cisco 880 Series: WLAN Features (Available with Wireless Option)16Cisco IOS Software Advanced IP Services Feature Set (Optional Software Upgrade)The Advanced IP Services software image has all the features of the Advanced Security software image with the addition of the features listed in Tables 7 through 10.Table 7. Cisco IOS Software Features on Cisco 880 Series: Advanced IP Services Feature Set (Optional Software Upgrade)Table 8. Cisco IOS Software Features on Cisco 880V Series: Advanced IP Services Feature SetTable 9. Cisco IOS Software Features on Cisco 880 SRST Series: Advanced IP Services Feature SetTable 10. Cisco IOS Software Features on Cisco 880 Series with Cisco Unified Border Element: Advanced IP Services Feature SetSystem SpecificationsTables 11 and 12 list the system specifications for the Cisco 880 Series Routers. Table 11. System Specifications●Nonoperating temperature: -4 to 149°F (-20 to 65°C)●Nonoperating humidity: 5 to 95% relative humidity (noncondensing)Table 12. Wireless LAN and 3G SpecificationsDSL SpecificationsTables 13 through 21 list the DSL features specifications and DSL access multiplexer (DSLAM) interoperability support for the Cisco 880 Series Routers. For more information and details about DSLAM and line-card interoperability, please refer to the following document: What Is Cisco ISR and ISR G2 xDSL Interoperability?Table 13. DSL Features SpecificationsMultimode DSL (VDSL2 and ADSL2/2+)(886VA and 887VA models)●Broadcom Chipset●Dying gasp●IEEE 802.1q VLAN tagging●Independent DSL firmware loadingVDSL2●ITU G.993.2 (VDSL2)●997 and 998 band plans●VDSL2 profiles: 8a, 8b, 8c, 8d, 12a, 12b, and 17a●U0 band support (25-276 kHz)●Ethernet PTM mode only based on IEEE 802.3ah 64/65 octet encapsulation●DELT Diagnostics ModeADSL2/2+●ADSL over basic telephone service with Annex A and Annex B ITU G. 992.1 (ADSL), G.992.3 (ADSL2), andG.992.5 (ADSL2+)●ADSL over basic telephone service with Annex M (extended upstream bandwidth) G.992.3 (ADSL2) andG.992.5 (ADSL2+)◦Cisco 887VA-M is optimized for PSD Mask EU-64 M9.◦Cisco 887VA-M supports UK Annex M.●G.994.1 ITU Ghs●Reach-extended ADSL2 (G.922.3) Annex L for increased performance on loop lengths greater than 16,000feet from central office●T1.413 ANSI ADSL DMT issue 2 compliance●DSL Forum TR-067 conformity●Inpulse Noise Protection (INP) and extended INP●Downstream Power Back-Off (DPBO)●ATM mode onlyADSL specifications (886 and 887 models) ●ST-Microelectronics 20190 Chipset●ADSL over basic telephone service with Annex A and Annex B ITU G. 992.1 (ADSL), G.992.3 (ADSL2), andG.992.5 (ADSL2+)●ADSL over basic telephone service with Annex M (extended upstream bandwidth) G.992.3 (ADSL2) andG.992.5 (ADSL2+)◦Cisco 887-M is optimized for PSD Mask EU-64 M9.◦Cisco 887M supports UK Annex M only with Huawei 5300 DSLAM and its EADB line card with customer-premises-equipment (CPE) firmware Version 4.0.17.●G.994.1 ITU G.hs●Reach-extended ADSL2 (G.922.3) Annex L for increased performance on loop lengths greater than 16,000 feet from central office●T1.413 ANSI ADSL DMT issue 2 compliance●DSL Forum TR-067 conformity●Does not provide interoperability with carrierless amplitude modulation/phase modulation (CAP)-based ADSL lines●Dying gasp●IEEE 802.1q VLAN tagging with Cisco IOS Software Release 15.1(1)T or laterVDSL2 specifications (887V models) ●Broadcom Chipset●ITU G.993.2 (VDSL2) over basic telephone service only●997 and 998 band plans, over basic telephone service only●VDSL2 profiles supported: 8a, 8b, 8c, 8d, 12a, 12b, and 17a●U0 band support (25276 kHz)●Ethernet PTM mode only based on IEEE 802.3ah 64/65 octet encapsulation ●DELT Diagnostics Mode●IEEE 802.1q VLAN taggingG.SHDSL (ATM mode) specifications (Cisco 888) ●Conexant/Ikanos Chipset●2- and 4-wire modes●Symmetrical WAN speeds up to 2.304 Mbps over a single copper pair and up to 4.608 Mbps over two copper pairs using ITU-T G.991.2 Annex A and Annex B●Wetting current (Section A.5.3.3 of G.991.2)●Dying gasp; uses power status bit (Section 7.1.2.5.3 of G.991.2) for signalingG.SHDSL (EFM mode) specifications (Cisco 888E) ●Conexant/Ikanos Chipset●2-wire mode●Symmetrical WAN speeds up to 2.304 Mbps over a single copper pair using ITU-T G.991.2 Annex A and Annex B●Symmetrical WAN speeds from 768 kbps to 5.696 Mbps over a single copper pair using ITU-T G.991.2 AnnexF and Annex G●Symmetrical WAN speeds up to 22.784 Mbps over four copper pairs using IEEE 802.3ah EFM bonding●Wetting current (Section A.5.3.3 of G.991.2)●Dying gasp; uses power status bit (Section 7.1.2.5.3 of G.991.2) for signaling●Rate adaptionMultimode G.SHDSL (EFM/ATM) specifications (Cisco 888EA) ●Lantiq Chipset●4-pair support●Compliance with standard based on ITU Recommendation G.991.2●Support for G.SHDSL Annexes A (U.S. signaling) and B (European signaling)●Support for Annexes F and G●Symmetrical WAN speeds up to 1 x 2304 kbps over single copper pair, up to 2 x 2304 kbps over two copper pairs, up to 3 x 2304 kbps over three copper pairs, and up to 4 x 2304 kbps over four copper pairs using ITU-TG.991.2 Annexes A and B●Symmetrical WAN speeds up to 1 x 5696 kbps over single copper pair, up to 2 x 5696 kbps over two copper pairs, up to 3 x 5696 kbps over three copper pairs, and up to 4 x 56964 kbps over four copper pairs using ITU-T G.991.2 Annexes F and G●Support for EFM bonding; supports up to four SHDSL pairs bonding●In ATM mode, support for maximum of 8 permanent virtual circuits (PVCs)●Support for dying gasp and wetting current●Support for point-to-point configuration●Support for 802.1Q, QinQ, trunk, and VLAN tagging●Support for ATM CoS and IP QoS features, 802.1P, and DSCP●Support for EFM (IEEE 802.3ah) OA&M●Ability to configure multiple G.SHDSL EFM EHWICs per Cisco 1921, 1941, 2900, and 3900 Series Routers●Compliance with single RJ-45 connector system requirementsTable 14. Multimode DSL DSLAM Interoperability for Cisco 887VATable 15. Multimode DSL DSLAM Interoperability for Cisco 886VATable 16. ADSL-over-ISDN DSLAM Interoperability for Cisco 886Table 17. ADSL over Basic Telephone Service DSLAM Interoperability for Cisco 887 and 887MTable 18. VDSL2 DSLAM Interoperability for Cisco 887VTable 19. G.SHDSL DSLAM Interoperability for Cisco 888Table 20. G.SHDSL DSLAM Interoperability for Cisco 888ETable 21. Multimode G.SHDSL DSLAM Interoperability for Cisco 888EA-K9Ordering InformationTable 22 lists ordering information for the Cisco 880 Series. To place an order, visit the Cisco ordering homepage. Table 22. Ordering Information* Each software part number has the Cisco IOS Software release number at the end of the string. For example, the part number of IOS 12.4(20)T data universal image for Cisco 880 series is S880DUK9-12420T.** This Memory license is only valid for C881-K9, C886VA-K9, C886VAJ-K9, C887VA-K9, C887VAM-K9 and C888-K9Cisco License Manager is a secure client- and server-based application used to manage Cisco IOS Software activation and licenses. For more information about Cisco License Manager, visit /go/clm. Cisco Services for the Branch OfficeServices from Cisco and our certified partners can help you reduce the cost and complexity of branch-office deployments. We have the depth and breadth of experience across technologies to architect a blueprint for a branch-office solution to meet your company's needs. Planning and design services align technology with business goals and can increase the accuracy, speed, and efficiency of deployment. Technical services help maintain operational health, strengthen software application functions, solve performance problems, and lower expenses. Optimization services are designed to continually improve performance and help your team succeed with newtechnologies. For more information, please visit /go/services.。
Synway AST Series TEJ400P TEJ401P TEJ400E TEJ401E

Synway AST SeriesTEJ400P/TEJ401PTEJ400E/TEJ401ETEJ800P/TEJ801PTEJ800E/TEJ801EDigital Trunk Interface BoardVersion 1.1Synway Information Engineering Co., LtdContentsContents (i)Copyright Declaration (ii)Revision History (iii)Chapter 1Overview (1)1.1 Features (2)1.2 Operation Principle (3)Chapter 2Installation (4)2.1 Hardware Structure (4)2.2 Interface Identification (6)2.3 Slot Compatibility (7)2.4 System Requirements (8)2.5 Hardware Installation (8)Appendix A Technical Specifications (11)Appendix B Technical/Sales Support (12)Copyright DeclarationThis manual is provided by Synway Information Engineering Co., Ltd (hereinafter referred to as ‘Synway’) as the support file for ‘Synway TEJ Series board driver software’. Both the software and this manual are copyrighted and protected by the laws of the People's Republic of China.All rights reserved; no part of this manual may be extracted, modified, copied, reproduced or transmitted in any form or by any means, electronic or mechanical, without prior written permission from Synway. By using this manual, you agree to the following Software License Agreement. Synway reserves the right to revise this manual without prior note. Please contact Synway for the latest version of this manual before placing an order.Synway has made every effort to ensure the accuracy of this manual but does not guarantee the absence of errors. Moreover, Synway assumes no responsibility in obtaining permission and authorization of any third party patent, copyright or product involved in relation to the use of this manual.Note: Asterisk and Digium mentioned in this book are registered trademarks of Digium Inc.Revision HistoryVersion Date Comments Version 1.0 2010-5 Initial publication.Version 1.1 2011-3 Add relative content about the new board models TEJ400P, TEJ401P, TEJ800P, TEJ801P.Note: Only major revisions to this manual itself recorded herein.Chapter 1 OverviewThe Synway TEJ400P, TEJ400E, TEJ800P, TEJ800E, TEJ401P, TEJ401E, TEJ801P and TEJ801E are digital trunk interface boards which support E1, T1 and J1 in Asterisk. As the second generation of the Synway TEJ series, they are in 2U size, 120mm in length, compact in structure and high in integration. Among them, TEJ400P, TEJ401P, TEJ800P and TEJ801P include 3.3V PCI bus, while TEJ400E, TEJ401E, TEJ800E and TEJ801E include PCIex1 bus, designed especially for various application systems that require high performance.They all perform echo cancellation by on-board DSPs. The enhanced capability of TEJ401P, TEJ401E, TEJ801P, TEJ801E in echo cancellation reaches 128ms for time delay estimation, which ensures high-quality voice talk without extra modules or devices to support echo cancellation. They are absolutely cost-effective. The design of on-board EMC and lightning-proof circuits further guarantees the security in use.These boards are completely compatible with Asterisk in hardware and support smooth connection to Asterisk platform. Therefore they have a lot of advanced call features.Supported Data Modes: Cisco HDLC, HDLC, PPP, Multi-link PPP, Frame Relay.Supported Voice Modes:PRI CPE and PRI NET— NI1— NI2— EuroISDN— 4ESS(AT&T)— 5ESS(Lucent)— DMS100E&M— Wink—Feature Group B—Feature Group DFXO and FXS— Ground Start— Loop Start—Loop Start with Disconnect DetectThese boards connect the Asterisk server with PSTN, Channel Bank or PBX via T1, E1 or J1 interface to build a specialized telephony network environment. Figure 1-1 and Figure 1-2 below are typical application models with these boards.Legacy PhonesLegacyTEJXXXRemote officesAsterisk ServerFigure 1-1 Application Model I: Traditional Telephony SystemTEJXXXSwitchAsterisk ServerIP PhonesNote: TEJXXX in Figure 1-1 and Figure 1-2 represent available TEJ series boardsFigure 1-2 Application Model II: VoIP Telephony System1.1 Featuresz PCI/PCIe Bus SupportTEJ400P/TEJ401P/TEJ800P/TEJ801P includes PCI bus, PCI r2.2 compliant; in the universal PCI design, it supports 3.3V/5V PCI slot and PCI-X slot.TEJ400E/TEJ401E/TEJ800E/TEJ801E includes PCIe bus, PCI Express r1.0a compliant;supports PCI Express X1, X4, X8, X16 slots and the PNP (plug and play) feature.z DMA Read and WriteThe use of DMA technique for data reading and writing helps minimize the cost of the host CPU.z Compatible with AsteriskEntirely compatible with Asterisk in hardware, with all source codes open.z RJ48C JackThe TEJ400P, TEJ400E, TEJ800P, TEJ800E, TEJ401P, TEJ401E, TEJ801P, TEJ801E boards all have four RJ48C jacks. Among them, TEJ400P, TEJ400E, TEJ401P and TEJ401E have common RJ48C jacks which can either connect directly with digital trunks or convert to BNC connectors via a proper adapter, while TEJ800P, TEJ800E, TEJ801P and TEJ801E have special RJ48C jacks (RJ48C/M) each of which can convert to two commonRJ48C jacks via a two-way hub, making connection easy and malfunctions rare.z Echo CancellationThe echo cancellers that Synway developed for these boards use on-board DSPs to work.TEJ401P, TEJ401E, TEJ801P and TEJ801E support up to 128ms for time delay estimation per channel, while TEJ400P, TEJ400E, TEJ800P and TEJ800E support 32ms, really cost-effective. It not only cancels out the effect of voice playback on DTMF and busy tones detection, but also avoids self-excited oscillation and howling, and minimizes the possibility of registering wrong DTMF and busy tones in a conference call, designed especially for VoIP application environments.z Voice CODEC SupportSupports A-law, μ-law codecs.z Clock Sync SupportSupports input and output of CT clock, allowing clock synchronization with multiple boards.z EMC & Lightning-proof Circuits Available1.2 Operation PrincipleMother BoardPCM InterfaceEchoRecording PlaybackHost Computer Interface (PCI/PCIe)Figure 1-3 Operation PrincipleChapter 2 2.1 zInstallationHardware StructureTEJ800P/TEJ801P BoardFigure 2-1 Left and Front ViewsPCM1 PCM5PCM2 PCM6PCM3 PCM7RJ48C/MLED2LED6 LED3LED7 LED4LED8PCI InterfaceFigure 2-2 Rear ViewzTEJ800E/TEJ801E BoardFigure 2-3 Left and Front ViewsClock Sync InterfaceLED2LED6 LED3LED7 LED4LED8PCIe InterfacePCM1 PCM5PCM2 PCM6PCM3 PCM7RJ48C/MFigure 2-4 Rear ViewNotes:1) PCM0~PCM7 in Figure 2-3 above are 8 transmit/receive interfaces to trunks. 2) LED1~ LED8 are indicators for PCM0~PCM7. They have three states as listed below.○1On: PCM synchronous; ○2Flashing: PCM not synchronous; ○3Off: Port unused 3) INm and OUTm respectively indicate the grounding jumpers at the receive and transmit endsof PCM(m-1), m =1~8. With regard to the configuration of grounding jumpers, refer to Step 1 in Section 2.5 Hardware Installation. 4) JP12 is an interface to the clock sync line.5) Except for the number of transmit/receive interfaces to trunks, the TEJ400P/401P board isalmost the same as TEJ800P/801P in appearance and the TEJ400E/401E board is almost the same as TEJ800E/801E in appearance. The picture is only for reference, please make the object as the standard.2.2 Interface IdentificationTEJ400P , TEJ401P , TEJ400E and TEJ401E adopt common RJ48C jacks. See Table 2-1 below for the pin layout of a standard RJ48C.Table 2-1 Common RJ48CTEJ800P , TEJ801P , TEJ800E and TEJ801E adopt special RJ48C jacks which we call RJ48C/M.See Table 2-2 below for the pin layout of an RJ48C/M.Table 2-2 RJ48C/M2.3 Slot CompatibilityMake sure them compatible with PCI or PCIe slots when using these boards. Users may choose whichever suitable according to the slot patterns illustrated in Figure 2-5 below.S lo ts 32104567Figure 2-5 PC SlotsSlot Number:0: AGP Pro slot1: 64-bit 5.0V PCI slot2: 64-bit 3.3V PCI slot3: 32-bit 5.0V PCI slot4: PCI-Express x1slot5: PCI-Express x8 slot6: PCI-Express x4 slot7: PCI-Express x16 slotTEJXXP boards support the slots numbered 1, 2, 3 (i.e. PCI slots) in Figure 2-5; TEJXXE boards support the slots numbered 4, 5, 6, 7 (i.e. PCIe slots) in Figure 2-5 and the PNP (plug and play) feature.2.4 System RequirementsHost System RequirementsCPU: 800MHz Intel® Pentium®III or aboveMemory: 64M or moreHD: Depends on individual requirementsSupported Operating SystemsLinux: Debian, Fedora, Rad Hat2.5 Hardware InstallationNote: Always turn off the power before installation!Step 1: Configure the grounding jumper.To use 100ΩT1, 110ΩJ1 or 120ΩE1 balanced twisted-pair cable, disconnect all grounding jumpers.In consideration of various line conditions, this series boards are equipped with two groups of grounding jumpers on each channel which respectively control the groundings of the transmitting and receiving ends. In case the 75ΩE1 unbalanced coaxial cable is used, the grounding jumpers at the receiving end should be disconnected while those at the transmitting end should be short-circuited, provided that the PC is properly grounded. This configuration is the factory default setting and applicable to most situations so that there is usually no need to change it. If it is difficult to ground the local PC, you may short-circuit the on-board grounding jumper at the receiving end and use the transmitting end at the opposite terminal for grounding. If the receiving end at the opposite terminal is grounded (improper operation), the on-board grounding jumper at the transmitting end must be disconnected. Refer to Table 2-3 for details.Generally speaking, even in the case of proper grounding at both terminals, only the external layer of the E1 coaxial cable at the transmitting end is allowed to be grounded. The grounding of both transmitting and receiving ends may result in a current loop with ground wires, bringing instability to signals. Therefore, such grounding must be strictly avoided.Table 2-3 Configuration of Grounding Jumpers for Use of 75ΩE1 Unbalanced Coaxial CableStep 2: Properly fit the board onto the PC chassis.It is suggested to fix the L-brackets on the board with screws before going to the next step.Step 3: Connect to digital trunks.A TEJ800P, TEJ801P, TEJ800E or TEJ801E board provides 4 RJ48C/M jacks, each of which in use should be converted to 2 common RJ48C jacks via a two-way hub as shown in Figure 2-6 below. Each common RJ48C can either connect directly with digital trunks or convert to 2 BNC connectors via an RJ48C-to-BNC adapter. See Figure 2-7.Figure 2-6 Two-way Hub for RJ48C/MFigure 2-7 RJ48C-to-BNC AdapterA TEJ400P, TEJ401P, TEJ400E or TEJ401E board provides 4 common RJ48C jacks, each of which can either connect directly with digital trunks or convert to 2 BNC connectors via an RJ48C-to-BNC adapter. See Figure 2-7 above.Step 4: Set up an application environment.Connect digital trunks with the on-board RJ48C jack to establish an application environment.Step 5: Connect the clock sync line.Note: Skip this step if there is no need of clock synchronization with multiple boards.The on-board clock sync line is used to connect with other boards, such as digital trunk boards, analog boards from Synway or even boards from other companies, to offer a same clock to all boards connected together. This can reduce the error in faxing and guarantee the accuracy in data transmission between boards.See Figure 2-8 below for the clock sync line provided by Synway.Figure 2-8 Clock Sync LineStep 6: Boot your computer and install the driver.Regarding driver installation, refer to the file ‘SynAST UserManual.doc’ for details.Appendix A Technical SpecificationsDimensions120×64mm2 (excluding L-bracket)Weight≤120gEnvironmentOperating temperature: 0℃—50℃Storage temperature: -20℃—75℃Humidity: 10%—90% non-condensingStorage humidity: 10%—90%non-condensingInput/output InterfaceDigital trunk interface:TEJ400P/TEJ401P/TEJ400E/TEJ401E:4 RJ48C jacksTEJ800P/TEJ801P/TEJ800E/TEJ801E:4 RJ48C/M jacksE1 interface:Compliant with G.703, including 75Ωunbalanced interface and 120Ω balanced interfaceT1/J1 interface:DSX-1 and CSU line build-outs available for different extents of signal losses,including 100Ω and 110Ω balancedinterfacesAudio SpecificationsCODEC: CCITT A/µ-Law 64kbpsDistortion: ≤3%Frequency response: 300-3400Hz (±3dB) Signal-to-noise ratio: ≥38dBEcho suppression: ≥40dBMaximum System CapacityDepends on the system consumption ofAsterisk and the processing capability ofcomputer.Power Requirements+3.3V DC:≈1800mAMaximum power consumption: ≤6.5W Audio Encoding & DecodingA-Law 64kbpsμ-Law 64kbpsSampling Rate8kHzSafetyLightning resistance: Level 4Appendix B Technical/Sales SupportThank you for choosing Synway. Please contact us should you have any inquiry regarding our products. We shall do our best to help you. However, our technicians and salesmen are mainly responsible for maintaining our boards and providing relative technical support. If there are problems about Asterisk, please keep touch with Digium Inc. for help.HeadquartersSynway Information Engineering Co., Ltd/9F, Synway D&R Center, No.3756, Nanhuan Road, Binjiang District,Hangzhou, P.R.China, 310053Tel: +86-571-88860561Fax: +86-571-88850923Technical SupportTel: +86-571-88864579Mobile: +86-189********Email:***********************Email:**********************MSN:**************************Sales DepartmentTel: +86-571-88860561Tel: +86-571-88864579Fax: +86-571-88850923Email:****************。
[vrrp配置实例]packettracer5.0配置实例
![[vrrp配置实例]packettracer5.0配置实例](https://img.taocdn.com/s3/m/d1027234182e453610661ed9ad51f01dc281576a.png)
[vrrp配置实例]packettracer5.0配置实例#配置BFD echo报文方式的Source IP,IP地址可以任意指定,不要与实际接口地址相同。
system-view[SwitchB] bfd echo-source-ip 10.10.10.10#配置VLAN101和VLAN102。
[SwitchB] vlan 101[SwitchB-vlan101] port Gigabitethernet 3/0/1[SwitchB-vlan101] port Gigabitethernet 3/0/24[SwitchB-vlan101] quit[SwitchB] vlan 102[SwitchB-vlan102] port Gigabitethernet 3/0/2[SwitchB-vlan102] quit[SwitchB] interface GigabitEthernet 3/0/1[SwitchB-GigabitEthernet3/0/1] undo shutdown[SwitchB-GigabitEthernet3/0/1] quit[SwitchB] interface GigabitEthernet 3/0/24[SwitchB-GigabitEthernet3/0/24] undo shutdown[SwitchB-GigabitEthernet3/0/24] quit[SwitchB] interface GigabitEthernet 3/0/2[SwitchB-GigabitEthernet3/0/2] undo shutdown[SwitchB-GigabitEthernet3/0/2] quit#配置上行接口。
[SwitchB] interface vlan-interface 102[SwitchB-Vlan-interface102] undo shutdown[SwitchB-Vlan-interface102] ip address 100.0.0.3 24[SwitchB-Vlan-interface102] quit#创建VRRP备份组1。
H3C VRRP+MSTP+链路聚合实战
H3C VRRP+MSTP+链路聚合实践拓扑配置步骤设备A的配置#配置端口g 1/0/22属于VLAN 300、g 1/0/2属于VLAN 200、g 1/0/1属于VLAN 100。
<SwitchA> system-view[SwitchA] vlan30[SwitchA-vlan 30] port GigabitEthernet 1/0/22[SwitchA-vlan30] quit[SwitchA] vlan 100[SwitchA-vlan100] port GigabitEthernet 1/0/1[SwitchA-vlan100] quit[SwitchA] vlan 200[SwitchA-vlan200] port GigabitEthernet 1/0/2[SwitchA-vlan200] quit#创建二层聚合接口1。
[SwitchA] interface bridge-aggregation 1[SwitchA-Bridge-Aggregation1] quit#分别将端口GigabitEthernet 1/0/23和GigabitEthernet 1/0/24加入到聚合组1中。
[SwitchA] interface GigabitEthernet 1/0/23[SwitchA- GigabitEthernet 1/0/23] port link-aggregation group 1 [SwitchA-GigabitEthernet 1/0/23] quit[SwitchA] interface GigabitEthernet 1/0/24[SwitchA-GigabitEthernet 1/0/24] port link-aggregation group 1 [SwitchA-GigabitEthernet 1/0/24] quit#配置二层聚合接口1为Trunk端口,并允许VLAN 101和102的报文通过。
施耐德电气 Integra 1221 单相三相电力系统仪表安装使用说明书

Setup and Operation GuideIntegra 1221Panel Mounted Energy Meterfor Single and Three PhaseElectrical Systems1 IntroductionThis document provides operating, maintenance and installation instructions. This unit measures and displays the characteristics of Single Phase Two Wire (1P2W), Three Phase Three Wire (3P3W) (Auxiliary model) and Three Phase Four Wire (3P4W) networks. The measuring parameters include voltage (V), current (A), frequency (Hz), power (kW/KVA/KVAr), power factor (PF), imported, exported and total energy (kWh/kVArh). The unit also measures maximum demand current and power, this is measured over pre-set periods of up to 60 minutes. This particular model accommodates 100mA RJ12 connected CT and can be configured to work with a wide range of CTs. It also comes with a complete communications capability with built in RS485 Modbus RTU outputs, configuration is password protected. This product is available in an auxiliary version (powered from a separate auxiliary) or a self-powered version (self-powered from any phase of the supply).1.1 Unit CharacteristicsThe Integra 1221 can measure and display:• Phase to neutral voltage and THD% (Total Harmonic Distortion) of all phases • Line frequency• Current, maximum demand current and current THD% of all phases• Power, maximum power demand and power factor• Imported, exported & total active energy• Imported, exported & total reactive energyThe unit has a password-protected setup menu for:• Changing the password• System configuration - 1P2W, 3P3W (Auxiliary model), 3P4W.• Demand s integration time (DIT)• Reset for max demand measurements 1.2 Current Transformer Primary CurrentThis unit requires configuring to operate with the appropriate current transformer(s), (100mA secondary). It is programmed by inputting the CT Primary value. It can be used on primary currents up to 9999A. e.g.for a 250/0.1A Pri (A) = 02501.3 RS485 Serial – Modbus RTUThis unit is compatible with remote monitoring through RS485 Modbus RTU. Setup screens are provided for configuring the RS485 port.1.4 Pulsed Outputs (Self-Powered version only)The Integra 1221 has two pulsed outputs. One pulsed output is configurable to active (Wh) or reactive (VArh) energy. The second pulsed output is fixed to 3200 pulses per displayed energy unit e.g. when the energy display is indicating kWh the pulsed output will produce 3200 pulses/kWh.2 Start Up ScreensThe first screen lights up all display segments andcan be used as a display check.The second screen indicates the product number,firmware and its build number.Please note: The numbers on the product mayvary from those shown here.The interfaceperformsa self-test and indicatesthe result if the test passes.If the test fails, the display will show ‘ERR= XXXXXXXX’ where the X’s will identify the fault. Theproduct will remain on this screen until the userenters the setup mode (the setup mode willoperate as normal). No Input registers will beavailable whilst the ‘ERR= XXXX XXXX’ isdisplayed.If the error cannot be rectified from the setupmenu, it is advised to power cycle the product. Ifthe issue remains, return the product to the factoryfor inspection.*After a short delay, the meter will display the power, volts and amps screen.3 MeasurementsThe buttons operate as follows:Selects the power, voltage, current and energy display screens.In setup m ode, this is “e scape” (hold 3 sec) button.Selects the voltage, current and THD display screens.In setup mo de, this is the “l eft” (press) button.Selects the frequency, power factor and max demand display screens.In setup m ode, this is the “u p” (press) button.Selects the power (active, reactive, apparent and system) displayscreens.In setup m ode, this is the “d own” (press) button.Selects the energy (active, reactive and total) display screens.In s etup mode, this is the “r ight” / “e nter” (press) button.4 SetupTo enter setup mode, hold the and buttons for 3 seconds, untilthe password screen appears.The setup is password-protected and must beentered before proceeding (d efault ‘0000’).If an incorrect password is entered, the product willexit the setup menu and return to the measurementscreens.To exit the setup menu, hold the button for 3 seconds, the measurementscreen will display.4.1 Setup Entry MethodsSome menu items, such as password and CT, require a four-digit number entrywhile others, such as supply system, require selection from a range of options.4.1.1 Menu Option Selection1. To edit the current option, press . The current option will begin to flash.e the and buttons to scroll through the available options.3. Press the button to confirm your selection. The word ‘SET’ willappear.4. On completion of setting-up, press the button to go back to the setupmenu or hold the button for 3 seconds to exit the setup menu completely.4.1.2 Number Entry ProcedureWhen setting up the unit, some screens require the entering of a number. Inparticular, on entry to the setup menu, a password must be entered. Digits areset individually from left to right. The procedure is as follows:1.The current digit to be set flashes and then can be adjusted using theand buttons.2.Press the button to move right to the next digit.3. After setting the last digit, press the button to save your selection.The word ‘SET’ will appear underneath as confirmation.5 Setup Menu StructureChange Password (CHnG PASS)Set a new four-digit password for the meterSystem Type (SyS 3P4)Use this section to set the type of electrical system (default setting is3 Phase4 Wire - 3P4). Available options: 3P4 /1P23P3 (Auxiliary model only).Voltage Transformer Primary Voltage, (Pri 277.0 V)The ‘Pri(V)’ menu enables the user to set the primary voltage (10V– 999 kV) of the voltage transformer (PT) that may be connected tothe meter.In 3 wire mode voltages are entered L-L and in 4 wire mode voltagesare entered L-N.Voltage Transformer Secondary Voltage, (SEC 277.0 V)The ‘SEC (V)’ option enables the user to set the secondary voltagebetween 100 – 277V AC.In 3 wire mode voltages are entered L-L and in 4 wire mode voltagesare entered L-N.Note: The unit can measure from 57.7V AC L-N (Auxiliary model)and from 100-277V AC (Self-powered model).Current Transformer Primary Current, (Pri 0005 A)Set maximum primary current that can be monitored according to CTin use (1A to 9999A).Current Transformer Secondary Current, (SEC 0.1 A)This is set to 0.1A.Incomer Entry (Ct Entr BOT)The meter is capable of two operating modes. Top Entry when theincoming cable is from the top. Bottom Entry when the incomingcable is from the bottom. BOT for bottom entry - TOP for top entry.Select either BOT or TOP on each meter according to the orientationof the line phases. Selections BOT or TOP will automatically switchL1 to L3 (Top) or L3 to L1 (BOT) - See diagram for exampleDemands Integration Time (dIt 30)This sets the period (in minutes) in which the current and powerreadings are integrated for maximum demand measurement.Available options: 8/15/20/30/60Energy Units Selection (EnrG 10E3 Unit kWh kVArh)Set the energy units used by the meter.Available options: kilo / MegaEnergy Low Power Limit (EnrG FLor On)To prevent creep caused by electrical noise being accumulated asenergy, the product will employ a low power limit, below which energywill not be accumulated. Available options: On/OffReset (rSEt ----)The meter provides a function to reset the maximum demand valueof current and power. Available options: dEd (max demand) / ALL /EnergyComms (COnS)Set Baud Rate: 4800/9600/19200/384000Set Parity: none/E (even)/oddSet Stop Bits: 1/2Set Address: 001-247Relay (rLy ----) (Self Powered version only)Relay 1 – Available options: Off/37 (Imp Wh)/38 (Exp Wh)/39 (ImpVArh)/40 (Exp VArh)/41 (Exp VAh)Pulse Duration – Available options: 200, 100 or 60mS.Pulse Rate – Available options: 1 Pulse per: 1W (0.001) / 10W (0.01)/ 100W (0.1) /1000W/1kWh (1) / 10kWh (10) / 100kWh (100)/1000kWh (1k)Note:There are limitations that need to be factored in whensetting the pulsed output. This is based upon the relay outputonly being able to pulse 2 times per second.Warnings∙During normal operation, voltages hazardous to lifemay be present at some of the terminals of this unit.∙At voltages below that specified in the Range of Usethe meter may shut down. However, voltageshazardous to life may still be present at some of theterminals of this unit.∙Installation and servicing should be performed only byqualified, properly trained personnel abiding by localregulations.∙Ensure all supplies are de-energised before attemptingconnection or other procedures.∙Terminals should not be user accessible afterinstallation and external installation provisions mustbe sufficient to prevent hazards under fault conditions.∙This unit is not intended to function as part of a systemproviding the sole means of fault protection - goodengineering practice dictates that any critical functionbe protected by at least two independent and diversemeans.∙The unit does not have internal fuses therefore externalfuses must be used for protection and safety underfault conditions.∙Never open-circuit the secondary winding of anenergized current transformer.∙If this equipment is used in a manner not specified bythe manufacturer, protection provided by theequipment may be impaired.Caution: Risk of Electric ShockBacklight Timeout (bAc 10)Programmable time that the backlight will remain on for before it isextinguished. Available options: Off/10/30/60/120Test (tESt)Test to check the display segments. Available options: Disp On (allsegments will light up simultaneously)/Disp Togl (half of thesegments will light up in one screen and the rest in another. Themeter will continuously switch between the two for visual checks). Product softwareDetails product code and firmware version.Default Frequency (dFlt 50)Available options 50 or 60.6 Specifications6.1 Measured ParametersThe unit can monitor and display the following parameters of a Single Phase Two Wire (1P2W), Three Phase Three Wire (3P3W) (Auxiliary model only) or Three Phase Four Wire (3P4W) system.6.1.1 Voltage and Current• Phase to neutral voltages 57.7-277V AC (L-N) (Auxiliary Powered only)• Phase to neutral voltages 100-277V AC (L-N) (Self-Powered only)• Phase to phase voltages 100-480V AC (L-L) (Auxiliary Powered only)• Phase to phase voltages 173-480V AC (L-L) (Self-Powered only)• Percentage total voltage harmonic distortion (V %THD) for each phase to neutral (not for 3P3W supplies).•Percentage total voltage harmonic distortion (V% THD) for L1-2, L2-3, L3-1 (3P3W supplies).• Current %THD for each Phase.• Burden <6VA• Auxiliary version: Auxiliary powered 100 to 250 VAC ±20%, at 45 to 66Hz or 100 to 250 VDC ±20%.•Self-powered version: Self powered from any phase and neutral (in 3P4W mode only)6.1.2 Power factor and Frequency and Max. Demand• Frequency in Hz• Instantaneous power:• Power 0-3600 MW• Reactive power 0-3600 MVAr• Volt-amps 0-3600 MVA• Maximum Demand Power since last reset• Power factor• Maximum Neutral Demand Current, since the last reset (for 3P4W supplies only)6.1.3 Energy Measurements• Imported/Exported active energy 0 to 9999999.9 kWh• Imported/Exported reactive energy 0 to 9999999.9 kVArh• Total active energy 0 to 9999999.9 kWh• Total reactive energy 0 to 9999999.9 kVArh6.2 Measured InputsVoltage inputs through 4-way fixed connector with 2.5mm² stranded wire capacity. Single Phase Two Wire (1P2W), Three Phase Three Wire (3P3W) or Three Phase Four Wire (3P4W) unbalanced. Line frequency measured from L1 Voltage or L3 Voltage. Three current inputs via RJ12 connector.6.3 Accuracy• Voltage ±(0.4% of Reading + 0·1% of Range Maximum)• Current ±(0.4% of Reading + 0·1% of nominal)• Frequency ±0·2% of mid-frequency• Power factor ±1% of unity (0·01)• Active power (W) ±(0.4% of Reading + 0.1% of Range Maximum)• Reactive power (VAr) ±(0.4% of Reading + 0.1% of Range Maximum)• Apparent power (VA) ±(0.4% of Reading + 0.1% of Range Maximum)• Active energy (Wh) Class 0.5S IEC 62053-22• Reactive energy (VARh) Class 0.5S IEC 62053-24• Total harmonic distortion 2%, up to 63rd harmonic6.4 Auxiliary Supply (Auxiliary version only)Auxiliary version: Three-way plug and socket connector with 2.5mm² stranded wire capacity. 100 to 250 VAC ±20%, at 45 to 66Hz or 100 to 250 VDC ±20%. Consumption <6VAThe auxiliary may be powered from the signal source, providing the source remains within tolerance of the auxiliary range.Self-powered version: This product is self-powered from any of the three phases and neutral.6.5 Interfaces for External MonitoringSelf-powered version: The following interfaces are provided:• Pulse output 1 indicating real-time measured energy (configurable) • Pulse output 2 3200 pulses/energy unit (not configurable). Only valid for 1:1 or5:5 CT ratios only.Self-powered and Auxiliary versions: The Modbus configuration (baud rate etc.)assignments are configured through the setup screens.6.5.1 Pulse Output (Self-Powered version only)Opto-coupler with potential free SPST-NO Contact•Pulse Output-1: Contact rating 250V AC, 50mA max•Pulse Output-2: Contact rating 70V DC, 27mA maxThe two pulsed outputs use a common (-) negative terminal.The pulse output can be set to generate pulses to represent kWh or kVArh.Rate can be set to generate 1 pulse per:0.001 = 1 Wh/VArh0.01 = 10 Wh/VArh0.1 = 100 Wh/VArh1 = 1 kWh/kVArh10 = 10 kWh/kVArh100 = 100 kWh/kVArh1000 = 1000 kWh/kVArhPulse width 200/100/60 milliseconds.6.5.2 RS485 Output for Modbus RTUFor Modbus RTU, the following RS485 communication parameters can beconfigured from the setup menu:Baud rate: 4800/9600/19200/384000Parity: none (default)/even/oddStop bits: 1 or 2RS485 Network Address: 3 digit number - 001-247Modbus™ Word order Hi/Lo byte order is set automatically to normal andcannot be configured from the setup menu.6.6 Reference Conditions of Influence QuantitiesInfluence Quantities are variables that affect measurement errors to a minordegree. Accuracy is verified under nominal value (within the specified tolerance)of these conditions.• Ambient te mperature 23°C ±1°C• Input waveform 50 or 60Hz ±2%• Input waveform Sinusoidal (distortion factor < 0·005)• Magnetic field of external origin Terrestrial fluxAuxiliary product (additional reference conditions):• Auxiliary supply voltage Nominal ±1%• Auxiliary supply frequency Nominal ±1%• Auxiliary supply waveform (if AC) Sinusoidal (distortion factor < 0·05)6.7 Environment• Operating temper ature -25°C to +70°C*• Storage temperature -40°C to +70°C*• Relative humidity 0 to 90%, non-condensing• Altitude Up to 2000m• Warm up time 1 minute• Vibration 10Hz to 50Hz, IEC 60068-2-6, 2g• Shock 30g in 3 planes*Maximum operating and storage temperatures are in the context of typical dailyand seasonal variation.6.8 Mechanics• Enclosure Style DIN 96 panel mount• Dimensions 96x96x (52 mm rear of panel)• Panel cut-out 92x92mm• Panel thickness 1-5 mm• Protection rating Front IP54, Rear IP30, IP64 with additional kit• Material UL 94-VO• Weight 340 g7 Installation and Maintenance7.1 Installation notesUnits should be installed in a dry position, where the ambient temperature isreasonably stable and will not be outside the range -25 to +70⁰C.Vibration should be kept to a minimum.Preferably, mount the Integra so that the display contrast is not reduced by directsunlight or other high intensity lighting.7.2 Input Wiring and Fusing (Auxiliary version only)Voltage lines must be fused with a fast blow AC fuse 1A maximum. Choosefuses of a type and with a breaking capacity appropriate to the supply and inaccordance with local regulations.A switch or circuit breaker allowing isolation of supplies to the unit must beprovided.7.3 Wire SizeVoltage terminal blocks will accept 0.5mm² to 2.5mm² stranded cable.7.4 MaintenanceThe front of the case should be wiped with a dry cloth only, using minimalpressure. If necessary wipe the rear case with a dry cloth.No user serviceable parts.8 Dimensions9 Installation9.1 RS485 Serial – Modbus RTUScreened twisted pair cable should be used. For longer cable runs or noisierenvironments, use of a cable specifically designed for RS485 may be necessaryto achieve optimum performance. All “A” terminals should be connectedtogether using one conductor of the twisted pair cable, a ll “B” terminals shouldbe connected together using the other conductor in the pair. The cable screenshould be connected to the “Gnd” terminals.A Belden 9841 (Single pair) or 9842 (Two pair) or similar cable with acharacteristic impedance of 120 ohms is recommended. The cable should beterminated at each end with a 120 ohm, quarter watt (or greater) resistor.For further information please refer to CI-3L12002 communications guide.9.2 Self-powered/Auxiliary Connection Diagrams9.2.1 Single phase two wires9.2.2 Three phase three wiresPlease note for 3P3W configuration L2 is connected through the neutraland not V2.9.2.3 Three phase four wiresThe maximum number of products that can be connect is a single chainis 20 products.While TE has made every reasonable effort to ensure the accuracy of the information inthis catalogue, TE does not guarantee that it is error-free, nor does TE make any otherrepresentation, warranty or guarantee that the information is accurate, correct, reliableor current. TE reserves the right to make any adjustments to the information containedherein at any time without notice. TE expressly disclaims all implied warranties regardingthe information contained herein, including, but not limited to, any implied warranties ofmerchantability or fitness for a particular purpose. The dimensions in this catalogue arefor reference purposes only and are subject to change without notice. Specifications aresubject to change without notice. Consult TE for the latest dimensions and designspecifications. TE connectivity (logo), TE (logo) and TE Connectivity are trademarks of theTE Connectivity Ltd. family of companies. Crompton is a trademark of CromptonParkinson and is used by TE Connectivity under a licence. Other logos, product andcompany names mentioned herein may be trademarks of their respective ownersTE Energy – innovative and economical solutions for the electrical powerindustry: cable accessories, connectors & fittings, insulators & insulation,surge arresters, switching equipment, street lighting, power measurementand control.Tyco Electronics UK LtdTE EnergyFreebournes RoadWitham, Essex CM8 3AHPhone: +44 (0)870 870 7500Fax: +44 (0)870 240 5289Email:********************Project 2277. Drawing No. CI-3L37801Rev.01 22/08/2019。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Configuration of Protected Virtual Private NetworksMarkosz Maliosz, Tibor Cinkler{Maliosz, Cinkler}@ttt-atm.bme.huDepartment of Telecommunications and TelematicsBudapest University of Technology and EconomicsPázmány Péter sétány 1/D, Budapest 1117, HungaryAbstractThe route configuration of Virtual Private Networks (VPNs) over a given physical network isaddressed considering the protection. We analyze protection at two different layers, first whenthe operator protects the virtual links of the VPN and second when the protection is done withinthe VPN. The problem is formulated as a general model without specializing to any particularnetwork type, however the proposed methods can be used for various SDH, ATM, IP, MPLS andWR-DWDM Networks. The service demands of VPNs are characterized by the bandwidthrequirements of node-pairs. Given the capacity matrix of the physical network and the trafficdemand matrices of the VPNs, the protected VPN configuration is sought which minimizes thenumber of links used by the VPNs, and results in global optimum. Numerical results fromcalculations on sample networks show the properties of the protection at different layers.IntroductionVirtual Private Networks have been increasingly wide-spread and used recently. More and more users require privacy and QoS guarantees over the public network infrastructure. Virtual Private Networks support the communication requirements of a closed group of users with special handling of privacy and security. The typical application of VPNs is remote access for joint project workers, or for a home user to access the company intranet. Privacy and security is handled by the upper communication layers, however the planning of the Virtual Private Networks over a physical network is a key question considering the operating costs. To ensure reliability the design must be prepared for failures. Therefore, the VPNs will have redundancy,a working and a protection path will be spanned between the node pairs. The route determination of the VPNs obeying link capacity constraints must be optimized considering the requirements for the protection.VPNs share the link bandwidth and the node resources among each other but the idea has several advantages. We do not have to build our own physical private network, only configure VPNs that reduces costs. When a VPN is inactive other VPNs can use its physical resources, and even in contrast to physical links, the VPNs can be simply reconfigured. The secure data transfer among the VPNs is provided by encryption of the communication. VPNs can be applied to different network architectures, e.g. to ATM or IP or to Multi-Service Networks. A VPN-Diffserv solution is proposed in [1].Our model deals with static bandwidth demands and analyzes the protection methods. In [2] there are also static demands considered, the paper plans to embed a VPN into a larger network while we place multiple VPNs at the same time into the network. In [3] dynamic relations are in scope with capacity resizing and stochastic fair sharing, but without protection. The resource allocation in conjunction with the routing design has been analyzed in [4,5,6] over multi-service networks with QoS constraints. Various tools are used like asymptotic approximations to reduce the complexity of the numerical calculations, multiplexing inside a VPN and introducing priorities between the traffic classes. Network dimensioning is addressed in [7] and the methodology is presented for determining the sizes of VPNs.In our framework multiple VPNs exist over the same physical network. The data paths can be protected at link layer and at VPN layer. The link layer protection means that each traffic demand between node pairs belonging to a VPN will have two paths reserved, both of them within that VPN. These two paths should bea protection VPN skeleton. (see Fig. 1) The skeletons are formed form the virtual links. In this case, only the link independence can be interpreted, because we deal with the VPNs only, we do not know the actual paths of the traffic demands. There will be always common points for the working and protection VPNs, thus ensuring that in case of failure the traffic can be switched to the protection path. For clarifying the two different protection approaches: when a link goes down at the link layer protection each path in each VPN concerning that link will be rerouted. However, at the VPN layer each path in each VPN concerning that link will be rerouted, i.e. whole VPNs will be rerouted from the working skeleton to the protection skeleton.The goal is to find optimal VPN configuration by minimizing the number of virtual links. By VPN configuration, we mean route selection and dimensioning for all VPNs simultaneously. The traffic and capacity matrices are given , these inputs are static values, like a snapshot from the actual network state. This method can be used in practice e.g. by a service provider to plan the VPNs with protection according to a weekly or monthly orders of companies.The service layer properties of a VPN are determined by the bandwidth requirement between each pair of nodes. For constant bitrate flows the bandwidth requirement is the exact value, however, if the traffic is bursty the effective bandwidth approximation can be used here.The calculated routes can be applied in practice using constraint-based routing instead of destination-based, for example in an MPLS VPN architecture [8,9].The modelsMinVL at Link LayerLink Disjoint CaseThis method minimizes the VPN cost, i.e. it minimizes the number of virtual links. MinVL is the abbreviation of Minimal Virtual Links. Let us assume the network is an undirected graph U(N,L,C). N is the set of nodes, L is the set of links between the nodes, and C is the capacity matrix, which contains the capacities of the physical links. The traffic matrices are given for each VPN, they contain the bandwidth demand for each node pair in the VPN. The variables in the optimization are:d l X 1and dl X 2are binary variables, where l is a physical link and d is a demand between two nodes}1,0{1∈d l X }1,0{2∈d l X p l Y is binary variable, where l is a physical link and p is the ordinal number of a VPN}1,0{∈d l Y d l X 1and d l X 2 represent, whether link l carries traffic, which belongs to demand d . d l X 1 is for theworking andd l X 2is for the protection path. pl Y represents, whether link l is used by VPN p or not. When thevariables are “0” then there is no traffic on link l , value of “1” indicates that there is traffic on that link. l is (i,j)pair of numbers, where i and j are the ordinal numbers of nodes, namely link l is between nodes i and j . d is an (i,j,b,v) tuple, i,j is a pair of numbers, where i and j are the ordinal numbers of nodes, b is the bandwidth requirement of the demand, v is the ordinal number of the VPN, and it means that there is a demand between nodes i and j with bandwidth b in VPN v .Node disjoint paths Link disjoint paths Working and protection between a node pair between a node pair VPN skeletons in VPN layer in link layer protectionin link layer protectionprotectionFigure 1Different Protection MethodsIn case of l only those (i,j) pairs of numbers are valid where (i,j) element is non-zero in the capacity matrix, these (i,j) pairs form the set L (L l ∈). In case of d , when the bandwidth requirement (b ) between (i,j)is not zero, then it is a valid demand. These form the set D (D d ∈).d l X 1,d l X 2 and pl Y variables cover the same quantity, but in different ways, namely the used links indifferent approaches. Whiled l X 1and dl X 2 show the link usage according to the demands between node pairs,p l Y shows whether a link is used by a particular VPN or not.The cost of the VPNs is defined as follows:The objective functions is:The constraints:Flow conservation constraints:These equations ensure that only sources originate and destinations sink the traffic flow. At theintermediate nodes the incoming and outgoing traffic is equal. This is expressed for both working and protection paths. The first sum stands for the traffic coming in into node j and the second sum is the outgoing traffic.Capacity constraintB stands for the physical capacity of link l, d b is the bandwidth requiremnt of demand d. d X 1,dX 2)min(VPN C =−∑∑∈∀∈∀Lk j d k j Lj i d j i X X ),(),(),(),(11otherwised of n destinatio is j if d of source is j if ,0,1,1−)2(,D d N j ∈∀∈∀)4()21(L l B b X X l Dd dd l d l ∈∀≤+∑∈∀},),(|),{(2N L L j i j i l ⊂∈=)1(∑∑∀∈=p Ll pl VPN Y C =−∑∑∈∀∈∀Lk j d k j Lj i d j i X X ),(),(),(),(22otherwised of n destinatio is j if d of source is j if ,0,1,1−)3(,D d N j ∈∀∈∀Diversity constraintp D is the set for those demands, that belong to VPN p. }1,0{∈p l Y therefore at most onlyone,d l X 1or dl X 2 can be “1” providing link independence.Node Disjoint CaseThis model adds only one more constraint to the previous case. Namely, the two paths must not have common nodes.Diversity constraint IIThis constraint expresses that there cannot be two paths going through node i , unless i is the source o rdestination of the demand.MinVL at VPN LayerAs mentioned in the Introduction at VPN layer only the link disjoint case can be interpreted. This method minimizes the VPN cost, i.e. it minimizes the number of virtual links while considering that the whole VPN must be protected.The variables in the optimization are:d l X 1and dl X 2are binary variables, where l is a physical link and d is a demand between two nodes}1,0{1∈d l X }1,0{2∈d l X p l Y 1and p l Y 2are binary variables, where l is a physical link and p is the ordinal number of a VPN}1,0{1∈d l Y }1,0{2∈d l Y d l X 1and d l X 2 represent whether link l carries traffic which belongs to demand d . d l X 1 is for the working andd l X 2is for the protection path. p l Y 1and p l Y 2represent whether link l is used by the working or protectionVPN p . When the variables are “0” then there is no traffic on link l, while value “1” indicates that there is traffic on that link. l and d are the same demands as above.d l X 1, d l X 2, p l Y 1, pl Y 2 variables cover also the same as at the Link Disjoint Case, namely the used linksin different approaches. Whiled l X 1and dl X 2 show the link usage according to the end-to-end demands,p l Y 1and p l Y 2shows whether a link is used by the working or protection VPN.The cost of the VPNs is defined as follows:The objective functions is:The constraints are partly from the Link Layer Model, therefore equations (2), (3) and (4) are applied here)5(,,21p pld l d l D d p L l Y X X ∈∀∀∈∀≤+)6(1)21(,,),(∑∈∈∀≤+dof n destinatio not is j d of source not is i L j i l d ld l D d X X )7()21(∑∑∀∈+=p Ll p l p l VPN Y Y C )min(VPN CAdditional capacity constraints:p D is the set for those demands, that belong to VPN p. If d l X 1, dl X 2 is “1” (showing link l is used forcarrying the traffic for demand d ), it involves that pl Y 1 , pl Y 2 should be “1” indicating that link l is used by VPN p .The diversity constraint in this model is:To ensure the link disjoint property, the following constraint must be added too, otherwise it could happen that the protection path were use the same link in the opposite direction.Optimization ProcessNetwork topologiesWe tested the models on sample network topologies with traffic demands for different scenarios. Four different topologies were investigated a 6-node network with 7 links, a 9-node network with 12 links, a 15-node network with 25 links and a 25-node network with 50 links (Fig. 2). Different traffic demands were selected for the VPNs in each case.ResultsILOG CPLEX optimizer [10] was used to solve the MIP problems. The route configuration results are compared to the results of a model without protection [11]. The results without protection are the trivial solutions in this case, since the link capacities are large enough to accommodate the protection paths as well. The charts in Fig. 3 show the number of hops, Fig. 4 shows the total capacity used in each case. Out of thed l X 1, dl X 2 results the smaller values are assignedto the working paths and the others to the protection paths. The number of hops and the capacity usage are summarizedseparately by working and protection paths. Bar 1 is the configuration without protection , bar 2 is the link disjoint link layer protection , bar 3 is the node disjoint link layer protection , and bar 4 is the VPN layer protection . As you can see,from the 15-node network there is no bar 4, because the MIP solver tool calculated hours long without results, which are not really in the acceptable time limit. Table 1 shows the number of virtual links, i.e. the result of the objective function, and the time consumption of the solver processes. The time consumption of not protected networks is only several hundredths of seconds, except the 25-node network, which has many links, causing higher paring the node disjoint and link disjoint cases, the node disjoint method can be solved quicker, although it has more constraints. The VPN layer protection lasts obviously longer than the others, since it is a more complicated )8(,,11p pld l D d p L l Y X ∈∀∀∈∀≤)9(,,22pp ld l D d p L l Y X ∈∀∀∈∀≤)10(,121p L l Y Y p l p l ∀∈∀≤+)11(,),(21),(),(p L j i Y Y p i j p j i ∀∈∀=6 nodes 15 nodes9 nodesThe number of virtual links (which is the objective function of the optimization) are increasing, at least doubled, when we use protection at the link layer, and even four or five times more in case of VPN layer protection. However, the number of virtual links in case of small network nodes is the same when we compare the link disjoint and node disjoint link layer protections. They have fewer links, therefore the two solutions could not really differ from each other.Fig. 3 shows that the VPN layer protection requires more hops, i.e. longer paths. The link disjoint and node disjoint link layer protection are almost at the same level in this aspect. In large networks with large number of VPNs the node disjoint solution requires slightly more hops. In Fig. 4 the results are similar to Fig. 3, namely longer paths result in higher capacity usage. The same tendency can be observed as in Fig 3, the link layer protection requires approximately doubled capacity, and VPN protection requires the doubled capacity of the link layer protection.uses less capacity than the unprotected network. The reason is that the optimization minimizes the number of virtual links, which are the same in these cases (see Table 1), and not the number of hops. The average of the working and protection values in number of hops or capacity usage are still greater than in the unprotected case. The node disjoint cases have the largest differences between the working and protection values.To show the differences between our approach – to minimize the number of Virtual Links – and the usual one, where the total cost (in this case the capacity usage) is minimized we present an example in Table 2. Three different objectives were aimed in the 9-node network 6 VPNs configuration. The first case, where only the capacity usage is minimized equals to the case when the VPNs are not considered, i.e. each demand is independently routed in the network. The second deals only with minimizing the number of Virtual Links, and the third one is a combination of the formers. The results show that minimizing only the capacity usage yields larger numbers in Virtual Links. Minimizing only the number of Virtual Links obviously yields higher capacity usage and utilizes more hops. The combined solution is near to the second solution regarding the number of Virtual Links. It provides smaller capacity usage than the second, but it is still higher than the first solution.Fig. 5 illustrates the path length distribution in two configurations. The link layer protection methods attempt to concentrate the traffic on shorter paths, while the VPN layer protection has another preferences. It does not deal with each path one-by-one, but with the VPN as a whole, therefore the path length distribution shows that this solution has more longer paths.ConclusionsJoint route selection and resource allocation of VPNs with different protection methods is discussed. Different methods were described to get the optimal VPN working and protection configuration over the physical network. The goal is to use minimal number of links, but with protected paths. The solutions were compared to each other, and to the unprotected case. The methods try to concentrate the traffic on fewer links, which results higher capacity usage, but this way the VPNs will have smaller expansion, i.e. they use less virtual links. Large networks require larger computational capacity, therefore the solution process should be enhanced with heuristics. The VPN layer protection is more complicated problem, than the link layer protection, however ensures the protection of whole VPNs’ virtual links. It requires about twice as much capacity than the link layer protection, which requires about twice as much than the unprotected configuration. The link or node disjoint link layer protection gives the opportunity to have different levels of protections in the system. Based on such results service providers can choose among the protection methods according to their preferences.References[1]Ibrahim Khalil, Torsten Braun, Edge Provisioning and Fairness in VPN-Diffserv Networks,The 9th International Conference on Computer Communication and Network (ICCCN 2000), October 16-18, 2000, Las Vegas, USA.[2]Martin Oellrich, Minimum-Cost Disjoint Virtual Private Networks under Edge Dependences, Boca 2000 – FifthINFORMS Telecommunications Conference, March 5-8, 2000, Boca Raton, Florida[3]Rahul Garg, Huzur Saran, Fair Bandwidth Sharing Among Virtual Networks: A Capacity Resizing Approach,INFOCOM 2000, Tel-Aviv[4] D. Mitra and K. G. Ramakrishnan, A Case Study of Multiservice, Multipriority Traffic Engineering Design forData Networks, Proc. IEEE GLOBECOM 99, pp.1077-1083, Dec.1999[5] D. Mitra, J. A. Morrison and K. G. Ramakrishnan, Optimization and Design of Network Routing using RefinedAsymptotic Approximations, Performance Evaluation, vol. 36-37, pp.267-288, 1999[6] D. Mitra, J.A. Morrison and K. G. Ramakrishnan, Virtual Private Networks: Joint Resource Allocation andRouting Design, Proc. IEEE INFOCOM 99[7]N. Anerousis, "Dynamic Virtual Private Network Dimensioning in Cost-Sensitive Environments", IEEEGlobecom, Rio de Janeiro, Brazil, December 1999.[8] B. Davie, Y. Rekhter, MPLS – Technology and Applications, Academic Press, 2000[9]I. Pepelnjak, J. Guichard, MPLS and VPN Architectures, Cisco Press[10]ILOG CPLEX 6.5 Documentation[11]M. Maliosz, T. Cinkler, Optimizing Configuration of Virtual Private Networks, Polish-Czech-Hungarian。
