Abstract Introducing Fixed-Point Iteration Early in a Compiler Course
一类不确定对象的扩张状态观测器

一类不确定对象的扩张状态观测器一、本文概述在当今复杂的工程和科学领域,对系统状态进行准确观测和估计是至关重要的。
当涉及到一类具有不确定性的对象时,传统的状态观测器设计方法可能无法满足性能要求。
针对这一问题,本文提出了一种新颖的扩张状态观测器(Extended State Observer, ESO)设计方法,专门用于处理一类具有不确定性的对象。
本文的核心思想是将对象的不确定性视为一个额外的状态,并将其纳入到观测器的设计中。
通过这种方式,观测器不仅能够估计对象的内部状态,还能够实时估计和补偿不确定性。
这一方法的关键在于设计一个适当的扩张状态观测器,使其能够在存在不确定性的情况下仍然保持良好的性能。
本文的结构安排如下:我们将介绍一类不确定对象的数学模型,并讨论其特性。
接着,我们将详细阐述所提出的扩张状态观测器的设计原理和步骤。
我们将通过仿真实验验证所提出方法的有效性和鲁棒性。
我们将总结全文并提出未来可能的研究方向。
本文的研究成果有望为处理不确定性对象的状态观测问题提供新的思路和方法,对于提高系统的性能和可靠性具有重要意义。
二、不确定对象建模与分析在现代控制理论中,不确定对象的建模与分析是确保系统稳定性和性能的关键步骤。
不确定对象通常指的是那些存在参数变化或外部扰动的系统,这些不确定性因素可能会对系统的行为产生显著影响。
为了有效地设计一个扩张状态观测器,首先需要对这些不确定因素进行准确的建模。
在建模过程中,我们通常采用数学方法来描述系统的动态特性和不确定性。
这包括使用状态空间表示法来定义系统的状态变量和方程,以及引入适当的不确定性模型,如摄动理论或概率模型,来描述系统参数的不确定性。
通过对这些不确定性进行量化,我们可以更好地理解和预测系统在不同操作条件下的行为。
分析不确定对象时,我们的目标是确定系统在各种不确定性条件下的稳定性和性能。
这通常涉及到对系统方程进行线性化处理,并应用如Lyapunov稳定性理论等方法来评估系统稳定性。
abstract方法

abstract方法Abstract方法。
在面向对象的编程中,抽象方法是一种非常重要的概念。
它是一种在抽象类或者接口中声明但不实现的方法,需要由子类去实现具体的逻辑。
本文将对抽象方法进行详细的介绍,包括其定义、特点、使用方法以及示例等内容。
首先,抽象方法是指在抽象类或者接口中声明但不实现的方法。
它只有方法的声明,没有方法体。
抽象方法的存在是为了让子类去实现具体的逻辑,从而达到代码的灵活性和可扩展性。
在Java中,使用关键字“abstract”来声明抽象方法,而在C#中,则使用关键字“abstract”来修饰方法。
其次,抽象方法的特点是必须在抽象类或者接口中声明,而且不能包含方法体。
另外,包含抽象方法的类必须被声明为抽象类,而包含抽象方法的接口则必须被实现。
在使用抽象方法时,需要注意的是子类必须实现父类中的所有抽象方法,否则子类也必须声明为抽象类。
使用抽象方法的好处在于可以定义一套规范,让子类去实现具体的逻辑。
这样一来,可以在不同的子类中实现不同的逻辑,从而提高代码的复用性和可维护性。
此外,抽象方法还可以降低代码的耦合度,使得程序更加灵活和易于扩展。
下面通过一个简单的示例来说明抽象方法的使用方法。
假设有一个图形类Shape,其中包含一个抽象方法calculateArea()用于计算图形的面积。
然后有两个子类Circle和Rectangle分别继承Shape类,并实现calculateArea()方法来计算圆形和矩形的面积。
这样一来,就可以通过多态的方式来调用不同子类的calculateArea()方法,而不需要关心具体是哪个子类。
总之,抽象方法是面向对象编程中非常重要的概念,它可以提高代码的灵活性和可扩展性,降低代码的耦合度,使得程序更加易于维护和扩展。
通过本文的介绍,相信读者对抽象方法有了更深入的理解,可以在实际的项目中更加灵活地运用抽象方法来设计和实现代码。
不确定环境下的最小权顶点覆盖问题的开题报告

不确定环境下的最小权顶点覆盖问题的开题报告一、问题描述顶点覆盖问题(Vertex Cover, VC)是指在给定无向图G(V,E)中,选出最小的顶点集合使它们的邻接点集合包含整个边集E的顶点集合。
其中,边的顶点集合为该边的两个端点。
此外,如果每个顶点有一个正整数的权值,那么问题被称为带权顶点覆盖问题(Weighted Vertex Cover, WVC)。
问题可以表示为:在无向图G(V,E)中,每个顶点有一个正整数的权值,选出具有最小权值的顶点集合V0,使得对于每个边(u,v)∈E,至少一个端点在V0内。
在实际应用中,许多问题都可以抽象为顶点覆盖问题,例如社交网络中的个人与个人之间的关系可以用图来表示,顶点代表个人,边代表关系,顶点覆盖问题可以用来帮助找到最小的个人集合,使得他们可以代表整个社交网络,方便对个人之间的关系进行分析;物流配送中的装车规划问题,顶点覆盖问题可以用来帮助找到最小的装车点确定配送方案。
二、问题分析无权顶点覆盖问题的求解方法比较简单,直接选取一个邻边、未选中的点覆盖边即可。
但带权顶点覆盖问题是NP完全问题,常见的求解方法有:1.贪心算法从权值最小的顶点开始,选取顶点和它的邻边,直到所有边都被覆盖。
2.整数规划算法将顶点集合的选择问题转化为0-1规划问题,利用整数规划求解器求解。
3.近似算法使用一些常见的近似算法,如禁忌搜索、模拟退火算法等,来求解带权顶点覆盖问题。
三、研究内容1.将带权顶点覆盖问题转化为整数规划问题,研究各种求解整数规划问题的算法,并比较它们的效率和精度。
2.设计一个基于禁忌搜索和模拟退火算法的近似算法,研究它的效率和精度,尝试对算法进行优化。
3.结合贪心算法,探究其在带权顶点覆盖问题中的适用性和局限性。
四、预期成果1.提出针对带权顶点覆盖问题的整数规划算法,研究其精度和效率性;2.设计模拟退火和禁忌搜索的近似算法;3.开发出实现以上算法的程序;4.在不同的数据集上测试程序,并评估算法的性能。
java abstractpointcutadvisor使用案例

java abstractpointcutadvisor使用案例在Spring框架中,切面(Aspect)是一种非常重要的概念,它允许开发者在特定的连接点(Joinpoint)上定义一系列的行为,比如方法拦截、事务管理等。
在切面中,Pointcut(切点)决定了哪些连接点会被拦截,而Advice(建议)则定义了在这些连接点上执行的具体逻辑。
AbstractPointcutAdvisor是一个抽象的切面通知器,它提供了一种便捷的方式来创建自定义的切面。
通过继承AbstractPointcutAdvisor,并实现相关的方法,我们可以快速定义一个自己的切面。
下面是一个使用AbstractPointcutAdvisor的示例代码:```javaimport org.springframework.aop.Pointcut;import org.springframework.aop.support.AbstractPointcutAdvisor;public class MyPointcutAdvisor extends AbstractPointcutAdvisor {private Pointcut pointcut;private MyAdvice advice;public MyPointcutAdvisor(Pointcut pointcut, MyAdvice advice) {this.pointcut = pointcut;this.advice = advice;}@Overridepublic Pointcut getPointcut() {return this.pointcut;}@Overridepublic Advice getAdvice() {return this.advice;}}```在上述代码中,我们首先导入了`org.springframework.aop.Pointcut`和`org.springframework.aop.support.AbstractPointcutAdvisor`类。
稀疏表示分类中遮挡字典构造方法的改进

稀疏表示分类中遮挡字典构造方法的改进第一章:引言介绍稀疏表示分类的背景和意义,以及现有研究中存在的遮挡字典构造问题。
简要介绍本文的主要研究内容和贡献。
第二章:相关工作综述综述稀疏表示分类及其在图像识别中的应用,以及已有方法解决的问题。
重点介绍现有方法中存在的局限性和不足,为本文提出的改进方法奠定理论基础。
第三章:改进的遮挡字典构造方法详细介绍本文提出的改进方法:基于非空子空间门限的遮挡字典构造方法。
阐述该方法的理论基础和具体实现方式,并与现有方法进行比较和分析。
第四章:实验结果和分析通过对真实数据集上的实验,比较改进方法和现有方法的分类准确度和效率,验证改进方法的有效性和优越性,并分析和讨论实验结果。
第五章:总结和展望总结全文的主要工作和研究成果,阐述改进方法的重要性和应用前景,并提出未来进一步改进的方向和展望。
随着计算机技术的发展和普及,图像识别已经被广泛应用于人类的各个领域。
在这个领域中,稀疏表示分类作为一种有效的分类方法,因其在识别准确度和效率方面的优势而备受关注。
稀疏表示分类是一种基于字典学习的图像识别方法,该方法可以将图像表示为由字典中的原子线性组合而成的向量,其中大部分原子系数为零。
在分类时,将待分类图像表示为稀疏向量,由此可以快速地进行图像分类和识别。
其因为拥有较高的识别准确度和较低的计算成本而在近年来受到越来越多的关注。
然而,稀疏表示分类在实际应用中也遇到了一些问题。
其中之一就是遮挡字典构造问题。
遮挡字典指的是由于图像中某些部分被遮挡或缺失,导致字典的某些原子部分无法区分不同类别的图像。
这种遮挡情况是普遍存在的,并且会严重影响图像识别的准确度和鲁棒性。
为了解决这个问题,现有的一些方法主要采用了增量字典学习、梯度迭代等策略,但这些方法存在训练时间长、字典过大和识别效率低等问题,需要进一步优化和改进。
基于此,本文提出了一种改进的遮挡字典构造方法,即基于非空子空间门限的遮挡字典构造方法。
Java abstract关键字详解

Java abstract关键字详解1. abstract关键字或抽象类与抽象方法1.1 由来举例1:随着继承层次中一个个新子类的定义,类变得越来越具体,而父类则更一般,更通用。
类的设计应该保证父类和子类能够共享特征。
有时将一个父类设计得非常抽象,以至于它没有具体的实例,这样的类叫做抽象类。
举例2:我们声明一些几何图形类:圆、矩形、三角形类等,发现这些类都有共同特征:求面积、求周长。
那么这些共同特征应该抽取到一个共同父类:几何图形类中。
但是这些方法在父类中又无法给出具体的实现,而是应该交给子类各自具体实现。
那么父类在声明这些方法时,就只有方法签名,没有方法体,我们把没有方法体的方法称为抽象方法。
Java语法规定,包含抽象方法的类必须是抽象类。
1.2 语法格式•抽象方法:被abstract修饰没有方法体的方法。
•抽象类:被abstract修饰的类。
抽象类的语法格式[权限修饰符]abstract class类名{}[权限修饰符]abstract class类名extends父类{}抽象方法的语法格式[其他修饰符]abstract返回值类型方法名([形参列表]);注意:抽象方法没有方法体代码举例:public abstract class Animal {public abstract void eat();}public class Cat extends Animal {public void eat(){System.out.println("小猫吃鱼和猫粮");}}public class CatTest {public static void main(String[] args){// 创建子类对象Cat c =new Cat();// 调用eat方法c.eat();}}此时的方法重写,是子类对父类抽象方法的完成实现,我们将这种方法重写的操作,也叫做实现方法。
1.3 使用说明1.抽象类不能创建对象,如果创建,编译无法通过而报错。
C#中abstract的用法详解

C#中abstract的⽤法详解参考:abstract可以⽤来修饰类,⽅法,属性,索引器和时间,这⾥不包括字段. 使⽤abstrac修饰的类,该类只能作为其他类的基类,不能实例化,⽽且abstract修饰的成员在派⽣类中必须全部实现,不允许部分实现,否则编译异常. 如:using System;namespace ConsoleApplication8{ class Program { static void Main(string[] args) { BClass b = new BClass(); b.m1(); } } abstract class AClass { public abstract void m1(); public abstract void m2(); } class BClass : AClass { public override void m1() { throw new NotImplementedException(); } //public override void m2() //{ // throw new NotImplementedException(); //} }}Abstract classes have the following features:抽象类拥有如下特征:1,抽象类不能被实例化, 但可以有实例构造函数, 类是否可以实例化取决于是否拥有实例化的权限 (对于抽象类的权限是abstract, 禁⽌实例化),即使不提供构造函数, 编译器也会提供默认构造函数;2,抽象类可以包含抽象⽅法和访问器;3,抽象类不能使⽤sealed修饰, sealed意为不能被继承;4,所有继承⾃抽象类的⾮抽象类必须实现所有的抽象成员,包括⽅法,属性,索引器,事件;abstract修饰的⽅法有如下特征:1,抽象⽅法即是虚拟⽅法(隐含);2,抽象⽅法只能在抽象类中声明;3,因为抽象⽅法只是声明, 不提供实现, 所以⽅法只以分号结束,没有⽅法体,即没有花括号部分;如public abstract void MyMethod();4,override修饰的覆盖⽅法提供实现,且只能作为⾮抽象类的成员;5,在抽象⽅法的声明上不能使⽤virtual或者是static修饰.即不能是静态的,⼜因为abstract已经是虚拟的,⽆需再⽤virtual强调.抽象属性尽管在⾏为上与抽象⽅法相似,但仍有有如下不同:1,不能在静态属性上应⽤abstract修饰符;2,抽象属性在⾮抽象的派⽣类中覆盖重写,使⽤override修饰符;抽象类与接⼝:1,抽象类必须提供所有接⼝成员的实现;2,继承接⼝的抽象类可以将接⼝的成员映射位抽象⽅法.interface I{void M();}abstract class C: I{public abstract void M();}抽象类实例:// abstract_keyword.cs// 抽象类using System;abstract class BaseClass // 抽象类{protected int _x = 100; //抽象类可以定义字段,但不可以是抽象字段,也没有这⼀说法.protected int _y = 150;public BaseClass(int i) //可以定义实例构造函数,仅供派⽣的⾮抽象类调⽤; 这⾥显式提供构造函数,编译器将不再提供默认构造函数. {fielda = i;}public BaseClass(){}private int fielda;public static int fieldsa = 0;public abstract void AbstractMethod(); // 抽象⽅法public abstract int X { get; } //抽象属性public abstract int Y { get; }public abstract string IdxString { get; set; } //抽象属性public abstract char this[int i] { get; } //抽象索引器}class DerivedClass : BaseClass{private string idxstring;private int fieldb;//如果基类中没有定义⽆参构造函数,但存在有参数的构造函数,//那么这⾥派⽣类得构造函数必须调⽤基类的有参数构造函数,否则编译出错public DerivedClass(int p): base(p) //这⾥的:base(p)可省略,因为基类定义了默认的⽆参构造函数{fieldb = p;}public override string IdxString //覆盖重新属性{get{return idxstring;}set{idxstring = value;}}public override char this[int i] //覆盖重写索引器{get { return IdxString[i]; }}public override void AbstractMethod(){_x++;_y++;}public override int X // 覆盖重写属性{get{return _x + 10;}}public override int Y // 覆盖重写属性{get{return _y + 10;}}static void Main(){DerivedClass o = new DerivedClass(1);o.AbstractMethod();Console.WriteLine("x = {0}, y = {1}", o.X, o.Y); }}。
abstract 的写法
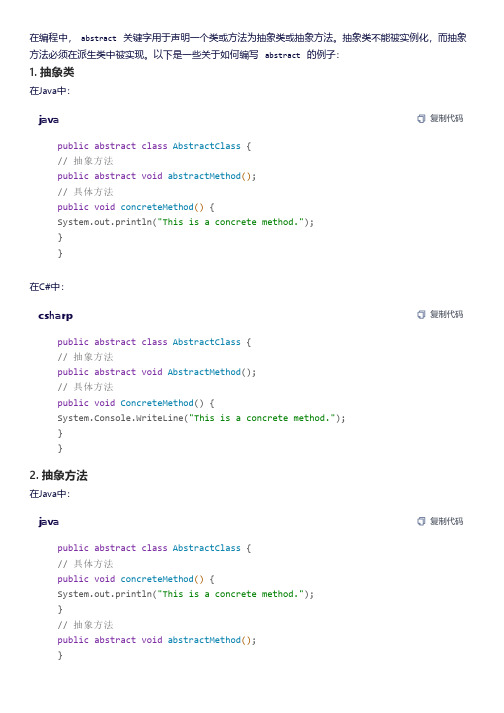
在编程中,abstract关键字用于声明一个类或方法为抽象类或抽象方法。
抽象类不能被实例化,而抽象方法必须在派生类中被实现。
以下是一些关于如何编写abstract的例子:1. 抽象类在Java中:java复制代码public abstract class AbstractClass {// 抽象方法public abstract void abstractMethod();// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}}在C#中:csharp复制代码public abstract class AbstractClass {// 抽象方法public abstract void AbstractMethod();// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}}2. 抽象方法在Java中:java复制代码public abstract class AbstractClass {// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}// 抽象方法public abstract void abstractMethod();}在C#中:csharp复制代码public abstract class AbstractClass {// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}// 抽象方法public abstract void AbstractMethod();}注意点:抽象类不能被实例化。
c++ abstract修饰类用法

C++中abstract修饰类的用法1. 概述在C++中,我们经常会听到关于abstract类的概念。
那么,abstract 类到底是什么?它又有什么作用呢?2. 什么是abstract类在C++中,我们可以使用关键字“abstract”来修饰一个类,使其成为一个“abstract类”。
一个abstract类是一种不能被实例化的类,即不能创建它的对象。
abstract类通常用于定义接口和抽象的行为,它的目的是为了让其他类继承并实现它的纯虚函数。
3. abstract类的定义要定义一个abstract类,我们可以在类中声明纯虚函数。
纯虚函数是指在类中声明但没有实现的虚函数。
通过在函数声明后面加上“= 0”来将一个虚函数声明为纯虚函数。
例如:```C++class AbstractClass {public:virtual void pureVirtualFunction() = 0;};```4. abstract类的作用abstract类的作用主要有以下几点:- 定义接口:abstract类定义了一组接口,表示了一种抽象的行为。
其他类可以继承并实现这些接口。
这样一来,我们就可以通过基类指针来调用派生类的函数。
- 特定行为的约束:abstract类可以约束其派生类必须实现某些特定的行为。
这样一来,我们就可以确保派生类都具有相同的接口,从而提高代码的一致性和可维护性。
- 防止实例化:abstract类的对象不能被创建,这可以防止程序员错误地使用该类,从而避免一些潜在的错误。
5. 如何使用abstract类在C++中,我们可以通过继承abstract类并实现其中定义的纯虚函数来使用abstract类。
例如:```C++class ConcreteClass : public AbstractClass {public:void pureVirtualFunction() override {// 实现纯虚函数的具体逻辑}};```在上面的例子中,ConcreteClass继承了AbstractClass,并实现了其中定义的纯虚函数pureVirtualFunction。
Abstract Point Location Algorithms of Minimum Size£

Point Location Algorithms of Minimum SizeValentina Damerow vio@uni-paderborn.deLukas Finschifinschi@ifor.math.ethz.chMartin Zieglerziegler@uni-paderborn.deAbstractConsider the classical point location problem:for afixed ar-rangement of hyperplanes and its induced partition of-space report,upon input of some point,which face it lies in.With sufficient memory,this is easy to solve in logarithmictime.But how fast can algorithms(formalized asLinear Decision Trees)of minimum size be?The presentwork gives lower and upper bounds for the time complexityof point location under this constraint.They show that,inaddition to,the maximum number of walls of a cellturns out to be a crucial parameter.We also consider a re-laxation of the strict minimum-size condition allowing forconstant factor overhead.1MotivationPoint Location is among the very basic problems in Com-putational ually,a partition of-space intoregions isfixed and available for preprocess-ing;the goal is to determine which a given query pointlies in.We consider the case where those regionsare the faces induced by hyperplanes;see,e.g.,Figure1.Definition1Fix a non-degenerate1arrangementof oriented hyperplanes in-space.For each,let and denote its negative andpositive halfspace,respectively.The position vector indicates,for each,whether lies above,on,or below:A face of is a non-empty collection of pointssharing the same position vector:for some.Its dimension equalsminus the number of zeros in.Figure1illustrates that not each possible sign vectorcorresponds to a face:here,no point satisfies.Therefore the number of faces does not attain.2Lower dimensional faces are identified in a similar way,cf.Lemma12.The algorithmic semantics:Let denote ’s root.For input ,proceed to the left,middle,or right subtreedepending on whether lies on,or ,respec-tively;continue until reaching a leaf .solves (the point location problem induced by)if,for each ,the above process ends up in aleaf labelled with ’s position vector:.The size of an LDT is the number of its leaves.H 1H 3−++ − −+ 0 −+ + −+ − 0+ − +H 2−+0−+− − +− 0 +− + +H 20−+− − 0− 0 0− + 0H 20−+− − −− 0 −− + −H 20−+H 3−+0H 20 0 −0 + −0−+H 30 − −0 − 00 − +0−+Figure 3:S AMPLE R LDT FORTHE ARRANGEMENT IN Figure 1.Obviously ,the total number of faces of an arrange-ment,constitutes a lower bound to the size of any LDT solv-ing the corresponding point location problem:each face has a different position vector and thus requires at least one leaf of its own.An LDT attaining this bound (i.e.,having exactly leaves)is said to be of minimum size .The one depicted in Figure 3for instance has this property 3.Dobkin and Lipton’s algorithm however is not of mini-mum size:the introduction of additional vertical linesincreases the number of cells fromto ,cf.Figure 2.In fact,since their algorithmperforms point location within this refined arrangement ithas,as an LDT,(at least)many leaves.The natural question arising for LDTs of minimum size is of course:What depth (i.e.,running time)can be achieved under this constraint?For answers we refer to Section 2of the present work.Some further comments on the above model of computa-tion and its notion of ‘size’:Any reasonable LDT has,for all its internal nodes ,out-degree either two or three.There-fore the total number of nodes will not differ from its size (in the sense of Definition 2)by more than a factor of two.This in contrast to B RANCHING P ROGRAM models (based on di-rected acyclic graphs rather than trees)where different log-ical paths of execution are allowed to rejoin;cf.Figure 6.6in [3].Actually most algorithms considered ‘small’in this model (like [1])are,as LDTs,not of minimum size.The same holds for Fredman’s A RITHMETIC M ODEL ,mostly used to prove lower bounds as in [4].In this model point location (i.e.,halfspace range queries over a trivial semi-group)can be performed in constant timeusingstorage space which,of course,is not very realistic.More precisely,the maximum number of walls of any cell of the arrangement constitutes an important param-eter:Any rLDT for will need(2)This has already been observed by Ukkonen[9]and ex-ploited to prove,in this model,exponential lower time bounds for several-complete problems.Our second re-sult complements(2)with an upper bound,that is,a fast minimum-size algorithm:Theorem5To any non-degenerate arrangement of hyperplanes in-space,there exists an rLDT of(3)solving the associated point location problem.Notice that in(3),the‘’from(2)is replaced by‘’thus leaving a gap between lower and upper bound.Next result nearly closes this gap:Infixed dimension,rLDTs cannot in general be faster than(3)by more than a factor: Theorem6To any pair of integers with,there exists a non-degenerate2D line arrangementwith such that any rLDT for hassolving the associated point location problem.It is not clear whether sublinear time remains feasible in higher dimensions by LDTs of size nor whether the 2D case can be improved to logarithmic depth.3ProofsDue to space limitations,we present only rough ideas on which our proofs to Theorems4to7are based.Omitted proofs can be found in the appendix.Definition8Let denote the family of-dimensional faces of non-degenerate hyperplane ar-rangement;let.Every is a relatively open convex polytope.will be called a sub-arrangement.As refines ,a cell may in general consist of several faces from:it is a super-cell.Let denote the collection of those faces from contained in and itscardinality.Figure5:S UPER-CELL CONTAINING5ORDINARY CELLS. 3.1Proof of Theorem4For each leaf of some LDT for arrangement,letdenote the set of inputs arriving in.Those partition into relatively open convex polytopes.Furthermore,as solves,by Definition2:this has already been used in Section1to argue that possesses at least as many leaves as has faces.By virtue of the following lemma,the converse inclusion holds as well,provided every leaf of is reachable:Lemma9Let be an rLDT for and suppose that for each of its leaves.Then. In particular,possesses exactly as many leaves as has faces.It can easily be achieved that each leaf of T is reach-able:Any’dead’branch may be pruned without affecting an LDT’s operation.According to Lemma9,a thus stripped rLDT is of minimum size.This time let be an LDT of minimum size.itself needs not to be an rLDT:Consider,e.g.,a variant of the LDT from Figure3with the top query for replaced by any other line passing through vertex;as this affects only,is still a valid LDT forwith19leaves although. However it turns out that only this kind of non-restricted queries can occur in minimum size LDTs.Lemma10Let be an LDT of minimum size for.Then any non-restricted query of can be replaced by some without affecting its operation.Repeated application of this tool obviously converts anLDT of minimum size into an equivalent rLDT of same depth.3.2Proof of Theorem5The proof consists of two steps.We willfirst construct an rLDT that only decides the arrangement,i.e.,it tells fora given point whether it lies on any of the hyperplanesor not:”?”This rLDT can then be extended to one actually solving the point location problem,i.e.,reporting the face lies in.Step number one proceeds by performing divide-and-conquer among the putative cells that might lie in.Recall that for an rLDT we may only query hyperplanes from .Intuitively,in order to obtain small depth,should have about as many cells on its left as on its right.The existence of such a hyperplane is guaranteed by the very centralLemma11Fix some non-degenerate arrangementof hyperplanes in and a supercell.Letdenote the maximum number of walls of any cell.There exists such that(4)for an appropriate orientation of.Indeed,this result allows for the strategy indicated in Fig-ure6which is easily seen to yield an rLDT.Notice that the property””is maintained throughout the algorithm.a)Initialize to be the‘supercell’.b)Choose according to Lemma11;query’s position with respect to:c)if,accept and exit;if,set;similarly for.d)Continue with b)until contains onlya constant number of hyperplanes from.e)Check these sequentially:if lies on any of them,accept;otherwise reject.Figure6:R LDT FOR DECIDING BASED ON L EMMA11.Moreover because of(4),each iteration of the loop body b)-c)reduces the number of cells that might lie in by a factor of nearlyand,this proves a depth of for this rLDT deciding. We will now turn it into an rLDT solving the associated point location problem.The underlying construction has al-ready been used by Meyer auf der Heide in a slightly differ-ent context to prove C LAIM3in[8].Lemma12Let be an LDT of size deciding the hy-perplane arrangement in.Then there exists an LDT of same depth and that solves the associated point location problem.If is an rLDT,so is.The possible factor of is not significant since restricted LDTs have minimum size anyway,c.f.Theorem4.3.3Proof of Theorem6As was shown in the proof to Theorem4,leaf of an LDT of minimum size corresponds to a face of the arrangement and vice versa.Let denote some cell having walls and its associated leaf of.being the intersection of all(half)planes queried on the path between and’s root,must be among these queries.There-fore is preceded by at least these query nodes and thus:this is essentially the argument that led Ukkonen to his lower bound(2).CC’xFigure7:F IRST STEP OF THE ITERATIVE CONSTRUCTION;ITSELF AND ALL S WILL HAVE WALLS.A cell with walls can be induced by an arrangementof hyperplanes.Figure7indicates how to extend this2D arrangement by new lines: Through each of the triangles adjacent to place additional lines in such a way that now is surrounded by cells also having walls each.Notice that each of the added lines also produces a new triangle.By careful placement it is possible that these lines neither intersect nor any of the adjacent.Thus no cell of has more than walls:.Furthermore, consists of lines in general position.Andfinally,any LDT of minimum size for has depth at least:Consider the leaf of with.As already pointed out,on the path from’s root to at least the walls of must be queried(otherwise it is not possi-ble to distinguish between points lying inside of or close to).For a point let denote the last tested wall of.Now consider some lying in the cell that is sep-arated from by.According to our construction has walls,too.Thus on its way through,an input queries nec-essarily and the additional walls of, hence the depth is at least.Notice that we did not (and could not)make any presumption on the order in which would test the walls of.Continuing the above construction times leads to a non-degenerate arrangement oflines where each of the cells has exactly walls whereas any other cell does not have more than walls.Therefore it is.Ukkonen’s above argument then reveals that an LDT of minimum size for must have depth at least. Now choose.3.4Proof of Theorem7Consider a non-degenerate2D arrangement of lines.If no cell has more thanwalls each.Lemma13Let denote a non-degenerate arrangement of lines in the plane.There exist additional lines such that each cell has at mostis the best(smallest number of walls,maximum taken over all cells)that additional lines can achieve.In any case it is sufficient to prove Theorem7:apply Theorem5to the arrangement with its at mostfaces to obtain the claimed LDT for.3.5Proof of Lemma11W.l.o.g.orient each hyperplane such that it has no more cells (from)on its negative than on its positive side,that is,We will prove by contradiction that then some satis-fies(4).So suppose that(5)Consider all possible subsets of hyperplanes;for each such,consider the collection of those cells from which are,for each,on the positive side: (6)Among those subsets of hyperplanes for which this collection is non-empty(contains at least one cell) choose some that is maximal w.r.t.set inclusion.Claim14Such a sub-arrangement has exactly one cell from on the respective positive sides of all: This thus is a cell not only of but also of;in other words:each wall of belongs to,i.e.,it has on its positive side.According to the lemma’s prerequisite,these are at most walls:,.And by presump-tion(5),each of them has strictly less than cells on its negative side,.Therefore a total of cells from can have the property of lying on the negative side of any of these walls from.And by virtue of Claim14,is the only cell that fails this property.The total number of cells from thus must be:contradiction.Proof(Claim14):is a super-cell con-sisting of at least one ordinary cell from:we chose such that(6)is non-empty.Now suppose that this(convex!) super-cell consists of several cells from.Choose an adja-cent pair and some hyperplane separating them;w.l.o.g.and.Then lies on the positive sides not only of all but also of this new which thus can be added to in contradiction to its maxi-mality.References[1]A DAMY,U.,R.S EIDEL:”On the Exact Worst CaseQuery Complexity of Planar Point Location”,pp.609-618in Proc.9th ACM-SIAM SODA(1998).[2]B EN-O R,M.:”Lower Bounds for Algebraic Computa-tion Trees”,pp.80-86in Proc.15th ACM STOC(1983).[3]DE B ERG,M,M.VAN K REVELD,M.O VERMARS,O.S CHWARZKOPF:”Computational Geometry:Algo-rithms and Applications”,Springer(1997).[4]B R¨ONNIMANN,H.,B.C HAZELLE,J.P ACH:”HowHard is Halfspace Range Searching?”,pp.143-155in put.Geom.10(1993).[5]C LARKSON,K.E.,H.E DELSBRUNNER,L.J.G UIBAS,M.S HARIR, E.W ELZL:”CombinatorialComplexity Bounds for Arrangements of Curves and Spheres”,pp.99-160in put.Geom.5(1990).[6]D OBKIN,D.,R.J.L IPTON:”Multidimensional Search-ing Problems”,pp.181-186in SIAM put.5(2) (1976).[7]G R¨UNBAUM,B.:”Convex Polytopes”,Wiley(1967).[8]M EYER AUF DER H EIDE,F.:”Fast Algorithms for-Dimensional Restrictions of Hard Problems”,pp.740-747in J.ACM35(3)(1988).[9]U KKONEN,E.:”Exponential Lower Bounds for some-complete Problems in Restricted Linear Decision Tree Model”,pp.181-192in BIT23(2)(1983).A More ProofsA.1Proof of Lemma9Suppose on the contrary that some is a proper subset of,i.e.,for some.By virtue of the lemma’s prerequisite,there exists.Since and end up in different leaves of,it must query some hyperplane to distinguish between them.On the other hand no can separate from because they both lie in the same face of.Hence ,and must have been an un restricted LDT–con-tradiction.A.2Proof of Lemma10Just as in the proof to Lemma9,it is for each leaf of.Furthermore,as the LDT is of minimum size, it has exactly as many leaves as has faces;thus we have .Consider some internal node of querying hyperplane .Similar to Subsection3.1let denote the set of all inputs passing through.The following properties are straightforward to verify:Observation15a)is a super-face4of contain-ing for each leaf in’s subtree.b)may be replaced,without affecting’s operation,byany hyperplane(oriented appropriately)satisfyingc)Let be convex subsets of,,and some hyperplane containing.Then contains as well.Let.The cases andbeing trivial we focus on. By virtue of a),is a face of some.As is relatively open,the intersection is -dimensional.Let denote the middle descendant of.is a super-face of because of a). Therefore,is the disjoint union of faces from; let denote such a face of maximum possible dimension: (7)being a-dimensional face of contained in the-dimensional face of,there must exist some such that.We claim that this satisfies the prerequisite of b)and hence may replace query in.Indeed as and both have dimension,c)implies.Similarly from(7)and c)follows that.Altogether we thus obtain..Consider some cell of having more than walls,i.e.,a‘large’one.Take its vertices ordered w.r.t.increasing-coordinates;draw a vertical line through every-th of them.These lines cut the large cells into smaller pieces,each having at most vertices.Being in2D this also means that each has at most walls.Cells that used to be‘small’(i.e.,having at most walls) might be intersected by these new lines;but here,too,the number of walls of any piece will not grow beyond. We apply the above procedure not only to one but simul-taneously to all cells that initially used to be‘large’.This yields,where denotes the collec-tion of newly introduced lines.Figure9:T HREE‘LARGE’CELLS,INDEPENDENTLY CUT INTOSMALLER PIECES BY VERTICAL LINES THROUGH ANY4TH OF THEIR RESPECTIVE VERTICES:SUB-CELLS NOW HAVE ATMOST6WALLS EACH.The resulting arrangement is a degenerate one:we have parallel(i.e.,non-intersecting)lines which furthermore pass through vertices(i.e.,an intersection of lines). An infinitesimal shift of the cures the latter without increasing by more than1.And by small rotation of them,one can achieve that any two(yet no three)do intersect.Let it be so very small that all inter-sections are far away from any bounded cell of. Thus the maximum number of walls of each cellstays unaffected by this operation.This yields a non-degenerate arrangement with at most。
Java中的abstract方法和abstract类的问题

Java中的abstract方法和abstract类的问题当知道一个类的子类将不同的实现某个方法时,把该类声明为抽象类很有用,可以共用相同的父类方法,不必再定义。
抽象类和抽象方法的关系:含有抽象方法的类一定是抽象类,抽象类里不一定含有抽象方法。
抽象类存在的意义是用来被继承的。
一个类继承了一个抽象类,必须实现抽象类里面所有的抽象方法,否则,此类也是抽象类。
abstract修饰符用来修饰类和成员方法1:用abstract修饰的类表示抽象类,抽象类位于继承树的抽象层,抽象类不能被实例化。
2:用abstract修饰的方法表示抽象方法,抽象方法没有方法体。
抽象方法用来描述系统具有什么功能,但不提供具体的实现。
abstract 规则:1:抽象类可以没有抽象方法,但是有抽象方法的类必须定义为抽象类,如果一个子类继承一个抽象类,子类没有实现父类的所有抽象方法,那么子类也要定义为抽象类,否则的话编译会出错的。
2:抽象类没有构造方法,也没有抽象静态方法。
但是可以有非抽象的构造方法3:抽象类不能被实例化,但是可以创建一个弓I用变量,类型是一个抽象类,并让它弓I用非抽象类的子类的一个实例4:不能用final修饰符修饰Qjava里面有抽象类么?和接口的区别是什么?A:java中有抽象类,用关键字abstract修饰。
以下是我对这个问题的看法。
首先,从语法上讲,抽象类是一个类,根据java的单继承体系。
如果它有子类,那么它的子类只能继承它。
java允许实现多个接口。
所以一个类可以实现多个接口抽象类里面可以定义各种类型和访问权限的变量(就像普通类一样),也可以定义各种访问权限的方法(就像普通类一样)。
但是接口不可以。
在接口里面定义的方法默认就是public absti-act的,变量默认就是public staticfinal的。
(不管你有没有加权限控制符,不加,默认就是这些权限;加错了,权限缩小7,那么就会报错)其次,从意义上讲,如果继承一个抽象类,那么抽象类和它的子类就有父子关系,即有类的层次关系(这关系到类的设计问题)。
python abstractmethod 方法

Python中的abstractmethod方法是面向对象编程中非常重要的概念之一。
它允许开发者定义抽象基类(Abstract Base Classes),并在其中声明抽象方法,这些方法需要在子类中进行实现。
通过abstractmethod方法,Python提供了一种强大的方式来约束和规范子类的行为,从而提高代码的可维护性和可扩展性。
在Python中,我们可以使用abc模块来定义抽象基类,并通过abstractmethod装饰器来声明抽象方法。
这使得在使用和维护大型代码库时更加方便和安全。
通过对abstractmethod方法的深入理解,开发者可以更好地利用Python强大的面向对象编程特性,提高代码的质量和可读性。
在本文中,我将从基本概念、使用方法、实际应用和个人观点等方面,对abstractmethod方法进行全面评估和探讨。
通过以从简到繁的方式展开讲解,希望能够帮助您更加深入地理解abstractmethod方法的重要性和灵活运用。
1. 基础概念在面向对象编程中,抽象类和抽象方法是非常重要的概念。
抽象类是指不能被实例化的类,其中的抽象方法需要在子类中进行实现。
而abstractmethod方法的作用就是用来声明抽象方法,从而使得子类必须实现这些方法才能正常运行。
这种强制实现的机制可以帮助开发者规范代码结构,提高代码的可维护性和可读性。
2. 使用方法通过在抽象基类中使用abstractmethod装饰器来声明抽象方法,可以很容易地定义出清晰的接口和规范。
子类必须实现这些抽象方法,否则在实例化时会抛出TypeError异常。
这种方式可以有效地减少代码中的错误和不一致性,提高代码的健壮性和可靠性。
3. 实际应用在实际项目开发中,abstractmethod方法可以被广泛应用。
在设计框架和库时,可以使用abstractmethod方法定义接口和规范,从而规范用户的使用行为;在团队协作时,可以使用abstractmethod方法约束团队成员的代码实现,提高代码的统一性和规范性;在单元测试时,可以使用abstractmethod方法确保代码的覆盖率和正确性。
科技论文abstract写法说明

Abstract1 StructureThe structure and content of the Abstract have changed in recent decades. Before on-line publication databases such as the Science Citation Index, the Abstract was printed at the top of a research article and its function was mainly to encourage the reader to continue reading the article and to facilitate that reading by providing a brief preview. The reader and the writer didn’t consider the Abstract of a research article as an independent unit because it was not normally read without reference to the article itself.The Internet has influenced the way that science research is communicated and the way that scientists access published research. Abstract databases allow scientists to search and scan the scientific literature and then decide which research articles they want to read in detail. Some readers simply want to know what is going on in their research area and may not be interested in the details; others may want to know details but are only interested in research articles which are directly relevant to their own research. However, if readers are going to actually read your research article, the Abstract now needs to persuade them to obtain a copy of it, not just encourage them to keep reading a paper theyhave already accessed.Abstracts compete for attention in on-line databases. Many more people will read the title than the Abstract, and many more will read the Abstract than the whole paper. This means that however ‘good’ and wellwritten the Abstract is, it needs to have independent validity. It should make sense as a standalone, self-contained description of the research article, and readers should be able to understand the key points and results of the research even if they never see the whole article. The Abstract, in this sense, is a representation of the research article.Why does the unit on Abstracts come at the end of this book rather than at the beginning?In the first place, the style and the length of the Abstract depend on where you plan to submit it and that decision may be taken late in — or even after —the writing process. However, the most important reason for putting this unit on Abstracts at the end of the book is that you are in a better position to create an Abstract after you have finished writing the other sections of your paper. The content of the Abstract is derived from the rest of the article, not the other way around. Although you should not simply cut and paste whole sentences from the body of the article, the Abstract does not contain material which is not already in the paper. Thismeans that you don’t need to create completely new sentences; once you have decided what should go in the Abstract you can select material, including parts of sentences and phrases, from the relevant sections of the paper and adapt or modify them to meet the demands of an Abstract. This also means that the Abstract is easier to write than the rest of the paper!Does every Abstract follow the same model?No, and the title of the Abstract reflects this. Some are called Summary, some are called Background, some are called Abstract and others have no title at all. Most Abstracts are results-focused and there are basic similarities in all Abstracts, but there are two quite distinct models. The first model is similar to a summary, and is very structured. It deals with all the main subsections of the research article and can even have subtitles such as Background/Method/Results/Conclusions. The second model is more common, and focuses primarily on one or two aspect of the study, usually — but not always — the method and the results. Both models will be discussed here. Note that the models for an Abstract described here are appropriate for articles, papers, theses etc. Abstracts for conferences may not follow either of these models.How do I know which model to choose?This decision is based on the type of research you have done and theGuide for Authors of the journal where you want to publish your research. The decision is normally determined by the journal rather than the author. If the choice is yours, then generally speaking, the more narrow and specified your research topic, the less likely you are to use the summary format. This is because in a narrow research field, most readers already know the background. The word limit set by each journal also has a significant effect on the structure and therefore also on the content of the Abstract.So as you can see, when we come to ask our three questions:How do I start the Abstract? What type of sentence should I begin with? What type of information should be in the Abstract, and in what order? How do I end this section?You already know a lot about what the Abstract should include and in what order.Here are examples of both models.Remember that Model 2 Abstracts are more common than Model 1. Start by reading the Abstract below, which is an example of a structured Abstract using the summary format (Model 1). The title of the paper is: Physical properties of petroleum reservoir fluids derived from acoustic measurements. Don’t worry if you have diffi culty understanding terms such as bubble point. Just try to get a general understanding at this stage and familiarise yourself with the structure.MODEL 1Abstract: The speed of sound in a fluid is determined by, and therefore an indicator of, the thermodynamic properties of that fluid. The aim of this study was to investigate the use of an ultrasonic超声波cell to determine crude oil properties, in particular oil density. An ultrasonic cell was constructed to measure the speed of sound and tested in a crude oil sample. The speed of sound was measured at temperatures between 260 and 411 K at pressures up to 75 MPs.The measurements were shown to lead to an accurate determination of the bubble point沸点of the oil. This indicates that there is a possibility of obtaining fluid density from sound speed measurements and suggests that it is possible to measure sound absorption with an ultrasonic cell to determine oil viscosity黏度.Now look at an example of the second, more common, type of Abstract. The title of this paper is: Effect of polymer coatings on drug release.MODEL 2Abstract: This study investigated the use of a novel water-soluble polymer blend as a coating to control drug release. It was found that using a blend of methylcellulose甲基纤维素and a water-soluble copolymer 共聚物significantly slowed the release rate of ibuprofen布洛芬compounds in vitro and allowed for a more consistent release rate of 10–20% per hour.2 Grammar and Writing SkillsBecause the Abstract is derived from the rest of the article, most of the grammar and writing skills have already been covered in previous units. The use of VERB TENSE, however, is very important in the Abstract. This section also deals with the LENGTH and LANGUAGE of the Abstract.2.1 Verb tenseVerb tense is especially important in the Abstract because the strict word limit means that you may need to omit phrases that tell the reader whose work you are referring to, or what you think about your results. In this case, these can be achieved by careful and accurate use of verb tense.Remember that the tense you use in a sentence may be grammatically correct —and therefore no editor or proofreader will notice it or draw your attention to it — but if you have not chosen the appropriate tense the sentence will not mean what you wanted it to mean and it will not have the effect you hoped it would have.The gap/problem is normally in the Present Simple tense,for example: The main problem, however, is…We examine why these models have diffi culty with…However, this assumption is not valid when…This is complicated复杂的,难懂的by…However, this assessment cannot be based so lely on…Although it is known theoretically that…When you are referring to what the paper itself does or what is actually in the paper itself, use the Present Simple tense, for example:论文中实际有什么,研究得到了什么结果This paper presents a new methodology for…In th is paper we apply…This study reports an improved design for…In this paper we extend an existing approach to…We consider a novel system of…The implications for learning algorithms are discussed…New numerical results are presented here for…When you are referring to your methodology, or what you did during the research period, it is common to use the Past Simple tense,也有可能是一般现在时for example:Two catalysts催化剂were examined in order to…Samples were prepared for electron microscopy using…A crystalliser was constructed using…The effect of pH was investigated by means of…The data obtained were evaluated using…A pe rmeameter was used to investigate…It is also possible to use the Present Simple tense to talk about your methodology, especially when you are referring to calculations计算or equations方程式which can be found in the paper itself:Numerical examples are ana lysed in detail…The calculated wavelengths are compared to…Several models are created using…The accuracy is evaluated by…A detailed comparison is made between…The method is illustrated on blends of homopolymers…Results can be expressed in either the Present Simple tense, for example: We find that oxygen reduction may occur up to 20 microns from the interface…No dilation was observed…This was consistent with…Organised fibers were found after 6 weeks…These profiles were affected by…This f inding correlated with…But be aware that the sentence may use two different tenses. Even if the first part of the sentence is in the Past Simple tense (We found/It was found etc.) you can decide to put the finding/result itself or the implication of the result in the Present Simple tense if you believe it is strong enough to be considered as a fact or truth:The experiments demonstrated there are two matrices…It was found that proteins are produced from…The results demonstrated that the morphology i s different…This image suggested that there is a direct relationship between…Some of the reasons behind that choice are discussed in the unit on Introductions (Section 1.2.1) and the unit on Results (Section 3.4.2). In addition to the reasons given there, it is worth noting that the Abstract tends to present the contents of the paper in fairly direct way, not only because of the word limits imposed by editors, but also to engage the attention of the reader. This influences the decision to use the Present Simple for the results or the implications, even though those implications may have been stated in the Past Simple in the article itself.Achievements can be expressed in the Present Perfect tense, as in theDiscussion/Conclusion:We have obtained ac curate quantitative LIF measurements…This investigation has revealed that…We have devised a strategy which allows…We have demonstrated the feasibility of this approach by…A novel material has been produced which…Three-dimensional FE predictions h ave confirmed that… Considerable insight has been gained concerning…The model consistently underpredicts…The ratio shifts towards…We show that this theory also applies to…The most accurate readings are obtained from…We find that this does not vary…These examples illustrate that overpotential is better described in terms of…Or, more commonly, in the Past Simple tense, for example: The Y-type was found to produce…The hydrocarbons showed a marked increase in…and also in the Present Simple tense:This process can successfully be combined with…The framework described here is both simple and universal…The value of our approach lies in…This provides a powerful tool for…This novel film is mechanically robust and is able to…The algorithm p resented here ensures that…Applications are normally stated in the Present Simple tense:This process is suitable for the production of…This framework can be used to evaluate…This approach can be applied to…This demonstrates potential for general applicability to…These profiles may serve as a predictor for…This framework can be used to evaluate…2.2 LengthThe Abstract usually has a strict word limit. Most are between 80– 150 words and are written as a single paragraph. Even longer Abstracts (150–250 words) are usually written as a single paragraph. Don’t submit an Abstract that is over the word limit or it may be cut by an editor in a way that does not represent your work appropriately. For your first draft, don’t worry too much about the word limit. Once you have decided which of the two Abstract models you will use, start by including whatever you think is important, and then gradually remove words, phrases and evensentences that are not essential.2.3 Language不用太专业,尽量少用缩略词,需要Think of the search phrases and keywords that people looking for your work might use. Make sure that those exact words or phrases appear in your Abstract, so that they will turn up at the top of a search result listing. The Abstract is sometimes written in a slightly less technical way than the article itself in order to attract a wider audience. This may mean that some of your readers do not know a particular technical term or acronym 首字母缩写that you want to include. To solve this problem, you can use the acronym, abbreviation缩写词or technical term in the Abstract but you should first say what it means or stands for. For example: Granules颗粒of hydroxyapatite (HA)羟磷灰石were implanted.3 Build a Model3.1 sample analysisYou are now ready to build a model of the Abstract by writing a short description of what the writer is doing in each sentence in the space provided below. This should be very easy, because all the components of the Abstract have occurred in previous subsections. As before, the Key is on the next page.GUIDELINESThis time you will need to build two models, to cover the two types of Abstracts. You should only need to spend 10–20 minutes on this task, because the sentenc e types are familiar to you from previous units. Don’t forget that your models are only useful if they can be transferred to other Abstracts, so don’t include content words or you won’t be able to use the models to generate your own Abstract.Remember that one way to find out what the writer is doing in a sentence, rather than what s/he is saying, is to imagine that your computer has accidentally deleted it. What changes for you, as a reader, when it disappears? If you press another key on the computer and the sentence comes back, how does that affect the way you respond to the information?As mentioned in previous sections, another way to figure out what the writer is doing is to look at the grammar and vocabulary clues. What is the tense of the main verb? What is that tense normally used for? Is it the same tense as in the previous sentence? If not, why has the writer changed the tense? What words has the writer chosen to use?Model Analysis—AbstractMODEL 1KeyIn Sentence 1 ‘Th e speed of sound in a fluid is determined by, and therefore an indicator of, the thermodynamic properties of that fluid.’the writer provides background factual information.In Sentence 2 ‘Th e aim of this study was to investigate the use of an ultrasonic cell to determine crude oil properties, in particular oil density.’ the writer combines the method, the general aim and the specific aim ofthe study in one sentence.In Sentences 3 and 4 ‘An ultrasonic cell was constructed to meas ure the speed of sound and tested in a crude oil sample. 4 The speed of sound was measured at temperatures between 260 and 411 K at pressures up to 75 MPs.’ the writer summarises the methodology and provides details.In Sentence 5 ‘Th e measurements were shown to lead to an accurate determination of the bubble point of the oil.’ the writer indicates the achievement of the study.In Sentence 6 ‘Th is indicates that there is a possibility of obtaining fluid density from sound speed measurements and suggests that it is possible to measure sound absorption with an ultrasonic cell to determine oil viscosity.’ the writer presents the implications of the study.Model 2KeyIn Sentence 1 ‘Th is paper reports the use of a novel water-soluble polymer blend as a coatin g to control drug release.’ the writer combines what the paper does (This paper reports), the method or materials used (water-soluble polymer blend), the contribution (novel) and the aim of thestudy (to control drug release).In Sentence 2 ‘It was found that using a blend of methylcellulose and a water-soluble copolymer significantly slowed the release rate of ibuprofen compounds in vitro and allowed for a more consistent release rate of 10–20% per hour.’ the writer refers to the method in more detail and provides numerical details of the results.3.2 The modelHere are the sentence descriptions we have collected:MODEL1MODEL 2Rather than construct two different models, the model description given in the box below will include both types of Abstracts. We can streamline the sentence types we have collected so that the model has five basic components.The more structured type, Model 1, typically includes the first four components in the box below in approximately the order presented; in this type of Abstract, each component tends to occur separately. These structured Abstracts occasionally include the fifth component, LIMITATIONS and/or FUTURE WORK.Model 2 selects just two or three of the components and tends to combine components in a single sentence where possible. The components generally include RESULTS and/or ACHIEVEMENTS and frequently METHODOLOGY, but this depends on the research area and the level of specificity. A wider research focus may require BACKGROUND or AIM in the Abstract. In Model 2, the order of components is very flexible indeed — the only pattern that is generally METHODOLOGY tends to come before RESULTS.Model5.4.2 Vocabulary for the Abstract 1. BACKGROUNDAIMPROBLEMWHAT THE PAPER DOESNote: It is also possible to use many of these verbs with it or, i.e. In this paper it is shown/argued that… or in the passive, i.e. A framework is presented…2. METHODOLOGY/MATERIALS3. RESULTSACHIEVEMENT/CONTRIBUTIONIMPLICATIONSYou can find more in Unit 3, Section 3.4.2, as well as examples of how these are used, but remember not to use the weaker forms such as seem to suggest or tend to be related to in the Abstract.4. APPLICATIONS5. LIMITATIONS and FUTURE WORKLimitations and future work are rarely mentioned in an Abstract and then only briefly.。
航空发动机控制软件质量量化控制的应用

航空发动机控制软件质量量化控制的应用佘红英,徐凯健(中国航发控制系统研究所,江苏无锡214063)航空发动机Aeroengine收稿日期:2018-05-23基金项目:航空动力基础研究项目资助作者简介:佘红英(1964),女,高级工程师,从事质量管理工作;E-mail:843924824@。
摘要:为实现安全关键软件的零缺陷泄漏的目标,依据航空发动机控制软件的特点,采用能力成熟度模型集成(CMMI)4级量化管理的方法,设立量化控制模型,定义过程性能指标。
在项目中利用蒙特卡洛模拟来预测和控制质量目标实现情况的应用,进行航空发动机控制软件的质量量化控制,能够在项目研制过程中,基于过程质量的符合性,预测缺陷泄漏的概率并实施有效控制,为研制高质量的控制软件提供了可靠保障。
关键词:缺陷泄漏;控制软件;安全关键软件;能力成熟度模型集成;量化控制;蒙特卡洛模拟;航空发动机中图分类号:V233.7+3文献标识码:Adoi:10.13477/ki.aeroengine.2018.05.015Application of Quality Quantitative Control in Aeroengine Control SoftwareSHE Hong-ying ,XU Kai-jian(AECC Aero Engine Control System Institute ,Wuxi 214063,China)Abstract:In order to achieve the goal of zero defect leakage of safety key software ,the method of 4-level quantization management of the Capability Maturity Model Integration(CMMI )was adopted to establish the quantitative control model and define the processperformance index based on the characteristics of aeroengine control software.Monte Carlo simulation was used to predict and control the application of quality objectives realized condition in the project ,so as to achieve quality quantitative control of aeroengine control software.In the process of project development ,the probability of defect leakage was predicted and effective control was carried out based on the conformity of process quality ,which provided a reliable guarantee for the development of high quality control software.Key words:defect leakage ;control software ;safety key software ;CMMI ;quantitative control ;Monte Carlo simulation ;aeroengine第44卷第5期Vol.44No.50引言发动机控制软件是航空发动机控制系统中的核心关键部件,属于机载安全关键软件,其运行结果直接影响人身和设施的安全,为此采取有效的方法来保证安全关键软件的“零缺陷”泄漏,将得到越来越多的关注。
基于格的用户匿名三方口令认证密钥协商协议

2018年2月Journal on Communications February 2018 第39卷第2期通信学报V ol.39No.2基于格的用户匿名三方口令认证密钥协商协议王彩芬,陈丽(西北师范大学计算机科学与工程学院,甘肃兰州 730070)摘 要:随着量子理论的快速发展,离散对数问题和大整数分解问题在量子计算下存在多项式求解算法,其安全性受到严重威胁,因此,提出2个基于环上带误差学习问题的用户匿名三方口令认证密钥协商方案,包括基于格的隐式认证密钥协商方案和基于格的显式认证密钥协商方案,并证明了其安全性。
其中,隐式认证密钥协商协议通信量少、认证速度快,显式认证密钥协商协议安全性更高,同时实现用户和服务器的双向认证、可抗不可测在线字典攻击。
与其他口令认证密钥协商协议相比,所提协议有更高的效率和更短的密钥长度,能够抵抗量子攻击,因此,该协议既高效又安全,适用于大规模网络下的通信。
关键词:格密码;可证明安全;口令认证;密钥交换;环上带误差中图分类号:TP309.7文献标识码:Adoi: 10.11959/j.issn.1000-436x.2018021Three-party password authenticated key agreementprotocol with user anonymity based on latticeWANG Caifen, CHEN LiCollege of Computer Science and Engineering, Northwest Normal University, Lanzhou 730070, China Abstract: With the rapid development of quantum theory and the existence of polynomial algorithm in quantum computation based on discrete logarithm problem and large integer decomposition problem, the security of the algorithm was seriously threatened. Therefore, two authentication key agreement protocols were proposed rely on ring-learning-with-error (RLWE) assumption including lattice-based implicit authentication key agreement scheme and lattice-based explicit authentication key agreement scheme and proved its security. The implicit authentication key agreement protocol is less to communicate and faster to authentication, the explicit authentication key agreement protocol is more to secure. At the same time, bidirectional authentication of users and servers can resist unpredictable online dictionary attacks. The new protocol has higher efficiency and shorter key length than other password authentication key agreement protocols. It can resist quantum attacks. Therefore, the protocol is efficient, secure, and suitable for large-scale network communication.Key words: lattice-based cryptology, provably secure, password authentication, key exchange, ring-learning-with-error1 引言随着大数据时代的到来以及量子计算机的快速发展,人们对数据的安全有了更高的要求,格密码依靠其独特的困难问题和归约结果成为密码学研究的热点,基于离散对数问题和大整数分解问题在量子计算下存在多项式求解算法,其安全性受到严重威胁,因此,格理论被应用于抗量子攻击的密收稿日期:2017-09-18;修回日期:2018-01-17基金项目:国家自然科学基金资助项目(No.61662069, No.61562077, No.61662071);西北师范大学青年教师科研能力提升计划基金资助项目(No.NWNU-LKQN-14-7)Foundation Items: The National Natural Science Foundation of China (No.61662069, No.61562077, No.61662071), The Founda-·22·通信学报第39卷码体制中。
基于预处理的位平面复杂度分割隐写改进算法

基于预处理的位平面复杂度分割隐写改进算法作者:刘虎袁海东来源:《计算机应用》2012年第01期文章编号:1001-9081(2012)01-0089-03 doi:10.3724/SP.J.1087.2012.00089摘要:位平面复杂度分割(BPCS)隐写易受复杂度直方图攻击,为了弥补这一缺陷,提出了一种基于预处理的改进隐写算法。
算法针对载密图像进行统计特征的量化分析,求导出逆向预处理的补偿规则,进而对嵌入信息引起的复杂度变化进行逆向的预处理补偿。
实验结果表明,改进的算法在保证隐蔽性的同时具有很好的抗复杂度直方图攻击的能力,由于补偿过程是在隐藏秘密信息之前发生的,算法也较好地保持了BPCS大容量隐写的优点。
关键词:信息隐藏;隐写;位平面复杂度分割;预处理;直方图中图分类号: TP391.413; TP309.2 文献标志码:Aography is vulnerable to complex histogram attack, this paper proposed an improved algorithm based on preprocessing. The steganography derived compensatory rule from distribution of the cover image. Then it used reversed preprocessing in compensation to the change of complexity caused by embedded information. The experimental results show that the proposed algorithm can properly hide information and counteract the attack of complex histogram. The compensation happens before information hiding, so it can maintain the big capacity characteristic of the original algorithm.preprocessing; histogram0 引言随着计算机、网络和数字化等信息技术的发展,作为信息安全重要研究方向的信息隐藏技术也被赋予了新的生命。
面向主题的无监督文本摘要生成方法

面向主题的无监督文本摘要生成方法作者:***来源:《电脑知识与技术》2021年第28期摘要:随着人工智能的迅速发展,传统的文本摘要技术也从抽取式摘要向生成式摘要发展。
当源文档中存在着多个主题的内容时,现有的大多数生成式文本摘要方法会尽全面地对多主题内容进行概括和总结,而对其中包含某个主题的内容可能无法进行细致描述。
针对这一问题,本文提出了一个面向主题信息的无监督文本摘要生成方法。
在给定目标主题信息的情况下,在解码器中利用注意力机制将目标主题信息与文本本身的主题信息进行信息融合,从而使得包含了目标主题的文本得到较大的注意力权重,以此生成与目标主题相关的文本摘要。
在大规模英文文本数据集Yelp上的实验结果验证了所提方法的有效性和先进性。
关键词:自然语言处理;序列到序列模型;无监督学习;生成式摘要;主题信息;注意力机制中图分类号:TP18 文献标识码:A文章编号:1009-3044(2021)28-0127-04开放科学(资源服务)标识码(OSID):Topic-oriented Unsupervised Text Summarization Generation MethodJIANG Jie(Guangdong University of Technology, Guangzhou 510006, China)Abstract: With the rapid development of artificial intelligence, traditional text summarization techniques have also evolved from extractive summaries to generative summaries. When there are multiple topics in the source document, most of the existing generative text summaries will summarize and summarize the content of multiple topics in a comprehensive manner, and the content of a certain topic may not be able to be described in detail. In response to this problem, this paper proposes a topic-oriented unsupervised text summary generation method. Given the target topic information, in the decoder, the attention machanism is used to fuse the target topic information with the topic information of the text itself, so that the text which contains the target topic information gets a larger attention weight, so as to generate a text summary related to the target topic. The experimental results on the large-scale English text data set Yelp verify the effectiveness and advancement of the proposed method.Key words: natural language processing( NLP );sequence-to-sequence( seq2seq )model;unsupervised learning;abstractive summarization;topic information;attention mechanism1 引言随着互联网产生的文本数据越来越多,文本信息过载问题日益严重,对各类文本进行一个“降维”处理显得非常必要,文本摘要便是其中一个重要的手段。
迂回相位编码技术制作匹配滤波器的宏像素选取

迂回相位编码技术制作匹配滤波器的宏像素选取第36卷第4期2006年4月激光与红外IASER&INFRAREDV o1.36,No.4April,2006文章编号:1001-5078(2006)04-0292-03迂回相位编码技术制作匹配滤波器的宏像素选取张勇,闫鹏程,王永仲,侯章亚(1.军械工程学院军械技术研究所,河北石家庄050000;2.军械工程学院光学与电子工程系,河北石家庄050003)摘要:实验中选择了不同的宏像素取法制作光学相关器的匹配滤波器,可保留更多的复振幅信息,从而大大改善了光学相关器的识别能力,实验结果验证了该方法的正确性. 关键词:光学相关器;匹配滤波器;迂回相位编码;宏像素中图分类号:TN713.6文献标识码:A'TheStudyofMacro-pixelSelectinginMakingMatchingFilter ByDetourPhaseEncodingTechnologyZHANGY ong,Y ANPeng.cheng,WANGY ong.zhong,HOUZhaJ1g—ya(1.OrdnanceTechnologyInstituteOrdnanceEngineeringCollege,Shijiazhuang050000;2.DepartmentofOptical—electricalOrdnanceEngineeringCollege,Shijiazhuang050003,China)Abstract:Inexperiment,thematchingfiltermadebydifferentmacro—pixelselectingcanreservemorecomplexampli- tudeinformationandimprovetherecognitioncapabilityofopticalcorrelator.Theexperimentalresultshowsthefeasi—bilityofthismethod.Keywords:opticalcorrelator;matchingfilter;detourphaseencoding;macro—pixel 1引言光学相关信息处理系统以光子传递信息,利用光学或光电子器件进行操作运算,通过光的折射,干涉和衍射等特性,实现对输入信息的各种变换与处理.这种处理的结果大多体现在输出光信号出现较高的峰值,据此可以从众多的噪声信号中识别出感兴趣的目标.与计算机图像处理相比,光学信息处理系统采用并行处理模式,运算速度快,同时具有巨大的数据传输速率和信息通道….为了保证光学相关器在实时模式下工作,一般都采用两片空间光调制器(SLM)用于场景输入和匹配滤波J.和以往的利用全息片进行光学相关处理不同的是,由于SLM本身的像素结构,采用迂回相位编码技术制作的匹配滤波器可以采用不同的宏像素选取方法.较常用的是4×4的宏像素取法j.实际上,选择不同的宏像素取法可以获得不同的匹配相关结果.采用4×1,l×4的宏像素取法可保留更多的复振幅信息,从而大大改善V anderLugt光学相关器的识别能力.2V anderLugt相关器光学相关信息处理系统一般可分为两大类,即联合变换相关器(JTc)和V anderLugt相关器(VLC).JTC结构灵活,不存在制作复滤波器及其严格的复位问题,易于实现相关运算.但该器件存在较强的零级衍射,导致相关输出的衍射效率较低;同时,联合变换相关输出平面中零级衍射峰的宽度较大,限制了输入面目标图像和参考图像的大小及相对位置J.相比之下,VLC工作原理简单,有很高的信噪比,图1为它的工作原理框图.实验中采用2mW,波长为632.8nm的He-Ne激光器作为相干光源,傅立叶变换透镜焦距为4oomm,场景和滤波均采用液晶型SLM,分辨率为1024×768,SLM1载入待识别的场景,SLM2载入匹配滤波器.假设SLM1上的输入图像为f(),经傅里叶变换透镜后,可得:作者简介:张勇(1974一),男,工程师,主要研究方向为光电仪器检测,智能诊断系统研制等.E-mail:******************收稿日期:2005-08—12激光与红外No.42006张勇闫鹏程王永仲等迂回相位编码技术制作匹配滤波器的宏像素选取293planeLl,L2实现扩柬准直,L3,L4为傅立叶透镜,SLM1为输入面,SLM2为滤波面,f=400ram图1V anderLugt相关器原理框图Fig.1functionaldla~'amofV anderLugtcorrelatorF(M,t))=IF(M,t))Iexp[ie(M,t))](1)制作的匹配滤波器应为:H(Ⅱ,)=F(",)=lF(M,)Iexp[一(M,t))](2)其中,F(u,)是F(u,)的复数共轭;日(,)为复相位角.可得VLC的相关输出为:F(F(M,t))H(M,t)))=F(M,t))F(M,t))=,(,Y)~fix,Y)(3)其中,算子"0"为相关运算,即相关器输出为被识别图像的自相关,表现在相关输出平面上出现尖锐的相关峰分布.3匹配滤波器制作传统的匹配滤波器制作方法是:当由计算机完成幅值和相位编码后,使用绘图仪,阴极射线管,或者计算机控制的微密度计制作原图,经光学缩版后变成实际使用的计算全息片J.这种方法制作工艺繁琐,光学相关系统不能在实时模式下工作.随着SLM制作工艺的不断提高,目前的光学相关器系统大都采用了两片SLM,来解决系统工作的实时性问题.SLM是由许多基本的独立单元组成的一维或二维阵列,这些独立的小单元称为SLM像素,它决定了SLM的分辨率.图2为VLC相关器系统中使用的SLM表面结构示意图.26.023.016.026.0图2空间光调制器表面结构不恿幽Fig.2pictureofsurfacestructureofSLM在制作匹配滤波器时,滤波平面的抽样点为SLM像素,SLM像素是SLM的最小可分辨单元,它不能被再次分割,因此不能直接利用抽样点进行编码,这时需要对绘制的匹配滤波器数据进行二次抽样,每个抽样单元称为一个宏像素(Macro—pixe1),它是绘制匹配滤波器的最小基本单元.图3为四级迂回相位编码方法的示意图.传统的4×4的宏像素取法是选取16个SLM像素作为一个宏像素,沿着方向分为四个部分,Y方向保持不变,方向各部分的相位分别是0,~r/2,仃,3~r/2,与复数平面上的实轴和虚轴所表示的四个方向相对应.匹配滤波器图上待纪录的一个样点的复振幅可以沿着图中四个相位方向分解成四个正交的分量.JF一一P一rl4宏像素suI像素(a)四分量合成矢量图(b)4×4宏像素选取方式图3四级迂回相位编码方法Fig.3four—stagedetourphaseencodingmethodm,n)=(m,n)r+(m,n)+(m,n)r一+(m,n)一(4)式(4)中,r√,r一,一是复平面上的四个基矢量,即:T=j=2,r一=j一=25,)是非负数.对于一个样点,这四个分量中只有两个分量为非零值.因此要描述一个样点的复振幅,只要在两个子单元中使用开孔的大小或灰度等级表示即可,如图3(b)所示.利用李威汉延迟抽样编码技术,把任意给定的函数分解为四个实的非负分量,每个分量的抽样都相对于原来的抽样单元中心有不同的延时量∑,这将会给每个分量带来不同的相位信息,经过公式推导J,可得匹配滤波器的透过率函数为:h(,Y)=∑∑[F1(rndx,nJy)占(一mdx,Y—ndy)+F3(mdx+2d/4,ndy)占(一mdx一2dx/4,Y—ndy)+F2(mdx+/4,ndy)6(一mdx—d/4,Y—ndy)+(mdx+3dx/4,ndy)6(if,一mdx一3dx/4,Y一呐)](6)由于SLM本身的像素结构,其每个像素填充的灰度等级和相对位置能直接反映了匹配滤波器的透过率函数.SLM的像素已经是最小不可分单元,因此制作完成的匹配滤波器不能像以往利用全息片的方法进行缩放,利用4×4的宏像素取法制作的匹配滤波器,只能在16个SLM像素中使用一个傅立叶变换数据作为整个宏像素的有效填充数据,因此数据利用效率仅为6.25%.实验中采用了一种新的宏像素选取方法,分别为4×1和1×4的宏像素取法,利用4个SLM像素组成一个宏像素,这样傅立叶变换后的数据利用效率可提高到25%,由于该方法比传统方法保留了更多的复振幅数据,因此相关信号也更加尖锐,更加利于判读.4×1和1×4宏像素取法的示意图为图4,采用4×4,4×1,1×4宏●毫rI.士294第36卷像素取法制作的匹配滤波器如图5.采用4×1宏像素取法的匹配滤波器的透过率函数和4×4的透过率函数相同,但前者却保留了更多的复振幅信息; 采用1×4宏像素取法的匹配滤波器的透过率函数改写为:h(,Y)=∑∑[F.(mdx,nay)(Y—ndy,—mdx)+(mdx,ndy+2dy/4)6(Y—ndy一2dy/4,一,)+F2(mdx,nay+dy/4)6(Y—ndy—dy/4,—mdx)+F4(mdx,ndy+3dy/4)6(y—nay一3dy/4,—mdx)](7)Il.IIl.SLM像素…(a)4×1宏像素取法(b)1x4宏像索取法图4不同的宏像素选取方式Fig.4selectingme~odofdifferentMacro?pixel关识别时各级衍射像的问距越小,相关峰的离轴距离越近,从而有可能出现混叠现象,影响相关峰的判读.相比之下,采用4×1或1×4的宏像素取法制作的匹配滤波器数据利用率较高,同时也能真实地反映抽样点的复振幅信息,因此相关峰信号在相关峰峰值强度和信噪比方面均有较大改善,从而有利于后续的相关信号判读.2(j02∞笾!og200l80藿120100noiseDistributionnoiseDistribution图7相关信号主要指标随噪声变化曲线Fig.7cuwediagramofmainp~ameterofcorrelation signalunderthedifferentnoisedegree4结论由于选用了空间光调制器来满足光学相关信息处理系统在实时模式下工作,因此可选择不同的宏一■■■(a)待识别目标(b)4x4宏像素(c)4×1宏像素(d)1x4宏像素图5采用不同宏像素制作的匹配滤波器Fig.5matchingfiltermadebydifferentMacro—pixel(a)4×4宏像素(b)4×l宏像素(c)1×4宏像素图6不同宏像素制作的匹配滤波器相关结果Fig.6correlationresultbymatchingfilterllladebydifferentMarco—pixel 将3种不同的匹配滤波器输送至VLC滤波平面的空间光调制器上,获得的相关结果如图6(由于CCD采集窗口的限制,部分再构像未能全部进入视场).由图6可以看出,相关峰的离轴距离与编码过程中的宏像素选取有关J.为了定量比较上述3种不同宏像素取法制作的匹配滤波器的实际匹配相关效果,分别计算了信噪比SNR(相关峰强度与相关峰旁瓣外的噪声均方差之比),相关峰峰值(PV).输入高斯白噪声,以噪声方差作为噪声等级,采用的噪声分布范围为0.01—0.20,获得的曲线列示于图7,可以看出,除了4×4宏像素取法制作的匹配滤波器抗噪能力较差外,其他2种匹配滤波器均表现较好.分析其原因主要是编码时对数据利用率越少,制成的匹配滤波器所产生的光栅栅距越大,导致相像素取法制作匹配滤波器.和传统的4×4宏像素取法相比,采用4×1或1×4的更为精细的宏像素划分方法保留了更多的振幅信息和相位信息,因此可获得更为理想的相关信号输出,改善VLC相关器的识别能力.致谢;本课题为军械技术研究所基金项目,在此表示感谢.参考文献:[1]王永仲.现代军用光学技术[M].北京:科学出版社, 2003,467—470.[2]李育林,傅晓理.空间光调制器[M].北京:国防工业出版社,1996,55—68.[3]苏显渝,李继陶.信息光学[M].北京:科学出版社, 1999,159.[4]王永仲,张勇,薛蕊,等.功率谱微分法在实时联合变换相关器中的应用[J].激光与红外.2004.34(5):399—340.[5]吕银环,王国田,等.几种相关匹配算法性能的研究与分析[J].红外与激光工程,2003,32(4):372—376.[6]俞世钢.提高计算机制全息图再现像质的有效方法[J].应用激光,2003,23(4):225—228.[7]浦东林,王策,吴建宏,等.光刻胶傅里叶全息图的纪录条件对重构图像信噪比的影响[J].激光杂志,25 (1):58—59.[8]虞祖良,全国藩.计算机制全息图[M].北京:清华大学出版社,1984.[9]BraceDHansche,JJeffMason,FredMDickey.Quad- phase—onlyfilterimplementation[J].AppliedOptics, 1989,28(22):4840—4844.。
abstract 类命名

abstract 类命名Abstract类是面向对象编程中的一个重要概念,它是一种特殊的类,旨在被其他类继承而不是被直接实例化。
本文将介绍Abstract类的定义、特点以及在实际开发中的应用。
Abstract类是一种抽象的概念,它提供了一种定义类的模板或蓝图的方式。
在Abstract类中可以定义一些抽象方法,这些方法只有方法的签名而没有具体的实现。
具体的实现需要在继承这个Abstract 类的子类中完成。
因此,Abstract类可以被看作是一种规范或契约,它规定了子类必须实现的方法,但并不关心方法的具体实现细节。
Abstract类的定义通常使用关键字"abstract"来修饰类名。
在Java 语言中,一个类只能继承一个Abstract类,而不能同时继承多个Abstract类。
这是由于Java语言的单继承特性所决定的。
因此,在设计Abstract类时,需要考虑类的继承关系,确保它能够被其他类继承并实现其中的抽象方法。
Abstract类的特点有以下几个方面:1. 抽象方法:Abstract类中可以包含抽象方法,这些方法只有方法的签名而没有具体的实现。
抽象方法的定义使用关键字"abstract"修饰,且没有方法体。
子类继承Abstract类时,必须实现这些抽象方法。
2. 非抽象方法:Abstract类中也可以包含非抽象方法,这些方法有具体的实现。
子类可以直接继承并使用这些非抽象方法。
3. 实例化限制:由于Abstract类本身是抽象的,所以不能直接实例化。
只能通过继承这个Abstract类的子类来创建对象。
Abstract类在实际开发中有着广泛的应用。
它可以用来定义一些通用的行为或属性,以供多个子类共享。
通过继承Abstract类,子类可以获得Abstract类中定义的抽象方法和非抽象方法。
子类可以根据自身的需求来实现这些抽象方法,从而实现自己的特定功能。
Abstract类还可以用来实现一些设计模式,如模板方法模式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Abstract
When teaching a course in compiler design, it is conventional to introduce the iterative calculation of least fixed points quite late in the course, in the guise of iterative dataflow analysis. In this paper I point out that the same mathematical and algorithmic ideas can be introduced much earlier, in the parsing portion of the course, as an explanation of the standard algorithm for computing the F IRST sets of a context-free grammar. Doing so not only renders these techniques more familiar when they re-appear in data-flow analysis, it also provides a more sound foundation for the F IRST algorithm than is typically offered. Moreover, these techniques deserve increased curricular prominence because they naturally lead to proofs of correctness for general nondeterministic algorithms that subsume multiple deterministic algorithms.
tions, each of which has a non-terminal as its left-hand side and a (possibly empty) finite string of grammar symbols as its right-hand side. A (possibly empty) finite string of grammar symbols is said to be derivable from an initial grammar symbol if one can start with the initial symbol and by successive replacements of the left-hand side of a production by the right-hand side arrive at the string. We can now define the F IRST problem in this context. We will consider F IRST to be a function from N ∪ T to T ∪ { }, where is a special symbol not in N ∪ T . (We will ignore the conventional, but easy, extension of F IRST’s domain to longer strings of grammar symbols.) The fundamental definition of F IRST is F IRST(x) = {y ∈ T | a string starting with y is derivable from x} ∪ (if the empty string is derivable from x, { }, else {}) This function plays an important role in both LL and LR parser construction. Thus, any standard compiler construction text, such as [1] or [2], will contain some algorithm for computing the F IRST function of a CFG, or, as it is commonly termed, computing the F IRST sets. However, it is not immediately obvious from the above fundamental definition of F IRST what form such an algorithm could take, because it is a completely non-effective definition: it suggests computing F IRST(x) by looking through the set of all strings derivable from x and seeing what terminals they start with. Yet in general infinitely many strings may be derivable from a non-terminal, rendering this approach impossible. This is why we redefine F IRST in the next section as the least fixed-point of a set of equations, which leads to an effective algorithm for its computation.
flow analysis portion of a compiler design course. Moreover this non-determinism is of great practical importance, because it allows one proof of correctness for a general nondeterministic algorithm to serve for many different deterministic algorithms that concretely instantiate it. As such, there is a desirable decoupling between correctness and efficiency: the correctness can be proven first, and then a deterministic instantiation chosen based on its efficiency. The problem is that this approach is too fundamental to be addressed for the first time in the context of iterative dataflow analysis, late in the typical compiler design course. It would be preferable if the concepts could be introduced earlier in some other context, and then re-used for data-flow analysis. Much to my surprise, there is a natural opportunity early in the compiler design course, in the material on parsing. The standard compiler design texts, e.g. [1, 2], show a technique for computing the so-called F IRST sets of a grammar that amounts to an iterative computation of a least fixedpoint. Yet none of the texts I am familiar with takes the opportunity to show how the correctness of such an algorithm can be verified. Therefore, this paper will remedy this omission by showing how the computation of F IRST sets can be used as an early introduction to non-deterministic least fixedpoint iterations. In the remaining sections, I will state the problem of computing F IRST sets for a context free grammar, re-express it as the quest for a least fixed point, then make the notion of a non-deterministic least fixed-point iteration precise and show how the F IRST problem can be solved through such an iteration, and finally sketch how this specific iteration can be proved correct. Although the focus is on this one problem, I’ll point out the features that are relied upon for the proof, and hence govern the scope of its generalizability. This mirrors how I have taught this material and is an approach I advocate.
