Deadlock-Free Information Structure Distributed Mutual Exclusion Algorithms
Second_CH08_deadlock

8.2 Deadlock Characterization死锁的特性
8.2.1 Necessary Conditions产生死锁的必要条件 Deadlock can arise if four conditions hold simultaneously. 四个条件同时出现,死锁才可能发生 Mutual exclusion: only one process at a time can use a resource. 互斥:一次只有一个进程可以使用一个资源 Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes. 占有并等待:一个至少持有一个资源的进程等待获得额 外的由其他进程所持有的资源
死锁的预防
Operating System Concepts
8.14
Basic Facts 基本事实
If graph contains no cycles no deadlock.
如果图没有环,那么不会有死锁 If graph contains a cycle 如果图有环 if only one instance per resource type, then deadlock. 如果每一种资源类型只有一个实例,那么死锁发 生 if several instances per resource type, possibility of deadlock. 如果一种资源类型有多个实例,可能死锁
Operating System Concepts
chapter-6 操作系统

5.
6.
由这个给定节点出发,察看是否有未标记的引出弧 (unmarked outgoing arcs)。如果有,转到步骤5; 否则,转到步骤6。If so, go to step 5; if not, go to step 6. 选取一个未标记的引出弧并标记它。然后,将引出 弧所到的节点作为新的当前节点,转到步骤3. 如果这是最初节点并且图中没有任何环路,算法终 止。否则,回溯到前一个节点,把其定位当前节点 ,转到步骤3。
Request the resource.
请求资源:若请求不能立即满足,则等待; Use the resource. 使用资源:获得资源后,使用; Release the resource. 释放资源:使用完毕,将资源归还系统。
Assume: when a process is denied a resource request, it is put to sleep.
哪个实例存在死锁的可能?
Resource Acquisition
Consider
a situation with two processes, A and B, and two resources.
Figure 6-2. (a) Deadlock-free code.
Resource Acquisition
6.3 The Ostrich Algorithm (鸵鸟算法)
鸵鸟算法 视而不见 不同的人对待死锁有不同的态度
主要看应用场合 死锁发生概率
UNIX多死锁问题采取忽略的方法
6.4 Deadlock Detection and Recovery
死锁的检测detection
允许系统死锁,但要及时检测出死锁的发生,并精 确地确定与死锁有关的进程和资源,然后采取适当 措施解除死锁。
Chapter-03

conditions for deadlock
• 3.2.1 conditions for deadlock [※※※※※]
• Four conditions for deadlock:
– 1. mutual exclusion condition . Each resource is either currently signed to exactly one process or is available – 2. hold and wait condition. Processes currently holding resources granted earlier can request new resources. – 3. no preemption condition. Resources previously granted can not be forcibly taken away form a process. They be explicitly released by the process holding them. – 4. circular wait condition. There must be a circular chain of two or more processes, each of which is waiting for a resource held by the next member of the chain.
压力容器等面积法补强面积计算范围的探讨

nt 接管名义厚度;
C 腐蚀余量。
参考文献
1 GB 150 1998 钢制压力容器. 1998: 74~ 78 2 王志 文. 化 工容 器 及 设 备. 北 京: 化 学 工业 出 版 社,
1990: 103~ 105 3 刁玉玮, 王立业. 化工设备机械基础. 大连: 大连理 工
大学出版社, 1989: 190~ 195 ( 本文编辑 朱必兰)
主题词 压力容器 补强面积 计算
等面积补强法是压力容器常规设计中开孔补强 设计的主要方法之一, 由于该方法对开小孔计算安 全可靠而被广泛采用。目前大学化工机械专业也主 要介绍这种补强法, 但不同的资料介绍的补强面积 计算法 及补强范 围的确 定方法 不同[ 1~ 3] 。笔者 就 GB 150 1998 钢制压力容器!及现行大学教材中的 补强面积计算及补强范围试谈自己的看法。
Oracle死锁分析过程详解

Oracle死锁分析过程详解Oracle死锁分析过程详解Oracle死锁分析关于死锁一般3种处理方式1、事前预测2、资源分级3、事后检测释放我知道的ORACLEMYSQL都是采用第三种在行锁级别上的话。
这里分析一个ORACLE死锁,首先一个死锁肯定会生成一个TRACE文件,这里会记录很多信息如:Deadlockgraph:---------Blocker(s)-----------------Waiter(s)---------ResourceNameprocesssessionholdswaitsprocesssessionhold swaitsTX-0058000f-0000b4736491204X6511252XTX-0019001c-0004e0b06511252X6491204X这里给出了进程和会话idRowswaitedon:Session1204:obj-rowid=0003D942-AAA9lCAAEAADgaNAAI (dictionaryobjn-252226,file-4,block-919181,slot-8) Session1252:obj-rowid=0003D942-AAA9lCAAEAADgaNAAa (dictionaryobjn-252226,file-4,block-919181,slot-26)这里给出导致死锁的行同时给出了最后触发死锁会话1252的语句-----InformationfortheOTHERwaitingsessions----- Session1252:sid:1252ser:35883audsid:7170593user:235/FEECORESV flags:(0x100045)USR/-flags_idl:(0x1)BSY/-/-/-/-/-flags2:(0x40009)-/-/INCpid:651O/Sinfo:user:oracle,term:UNKNOWN,ospid:13035 image:oracle@oratest11clientdetails:O/Sinfo:user:sky,term:unknown,ospid:1234machine:autobotsprogram:JDBCThinClientapplicationname:JDBCThinClient,hashvalue=2546894660currentSQL:UPDATE-----EndofinformationfortheOTHERwaitingsessions-----InformationforTHISsession:-----CurrentSQLStatementforthissession(sql_id=3vh5sc7pgtrjy)-----UPDATE那么到这里我们大概能够分析出A:1204拿到AAA9lCAAEAADgaNAAa行锁B:1252拿到AAA9lCAAEAADgaNAAI行锁C:1204需要AAA9lCAAEAADgaNAAI则等待D:1252需要AAA9lCAAEAADgaNAAa则触发死锁1204回滚那么随后trace给出1204C这一步等待时间和事物信息SO:0xee1fcd10,type:4,owner:0xf031e750,flag:INIT/-/-/0x00if:0x3c:0x3proc=0xf031e750,name=session,file=ksu.hLINE:12624,pg=0(session)sid:1204ser:2443trans:0xe9221180,creator:0xf031e 750flags:(0x100045)USR/-flags_idl:()BSY/-/-/-/-/-flags2:(0x40009)-/-/INCDID:,short-termDID:txnbranch:(nil)oct:6,prv:0,sql:0xf25d2278,psql:0xc4346788,user:235/FEECO RESVksuxdsFALSEatlocation:0servicename:SYS$USERSCurrentWaitStack:0:waitingfor''enq:TX-rowlockcontention''name|mode=0x54580006,usn<<16|slot=0x19001c,sequence=0x4e0b0wait_id=33seq_num=34snap_id=1waittimes:snap=3.001739sec,exc=3.001739sec,total=3.0017 39secwaittimes:max=infinite,heur=3.001739secwaitcounts:calls=1os=1in_wait=1iflags=0x15a0随后给出了导致他等待会话的等待信息,这里不给出。
死锁

死锁的例子
P1 ......; Receive(P2, M); ......; Send(P2,M); ......; P2 ......; Receive(P1,M); ......; Send(P1,M); ......;
死锁的例子
P1 Request(D); ......; Request(T); ......; Release(T); ......; Release(D); P2 Reques(T); ......; Request(D); ......; Release(D); ......; Release(T);
银行家(banker)算法
为了检查一个状态是安全的,银行家 检验他是否有充分的资源满足某个 顾客。如果有,这些贷款被假定是 要还贷的,并且检查该顾客现在最 接近限额,等等。如果所有的贷款 最终都能够还贷,则状态是安全的 ,可以贷给其初始的请求。
图 多资源的银行家算法
多资源的银行家算法
银行家算法可以推广到处理多资源的 情况。在图中左边矩阵表示资源当 前的赋予情况,右边矩阵表示每个 进程为了完成仍然需要资源的情况 。向量E表示系统所具有的资源,向 量P表示当前进程所占有的资源,向 量A表示系统可供使用的资源。
定义 4.1 如果不存在T使得S→i→T,则称 进程Pi在状态S被阻塞(blocked)。 进程P1在状态T被阻塞。 定义 4.2 如果进程Pi在状态S被阻塞,并且 对于所有满足S→*→T的状态T,进程Pi 在状态T也被阻塞,则称进程Pi在状态S 死锁(deadlocked)。 进程P2在状态U和V死锁。进程P1在状态 T不死锁,因为T→2→S不阻塞进程P1。
银行家(banker)算法
检查一个状态是否安全的算法如下: ⑴寻找一行R它的未满足资源需求小 于或等于A。如果不存在这样的行R ,系统最终将死锁,因为没有一个 进程能够运行完成。 ⑵假设所选中的行R的进程请求它所 需的全部资源并结束,标志该进程 终止并且将它的全部资源加到向量A 上。
操作系统原理课件-第八讲死锁问题(DEADLOCK)

Finish[i] = false和Necdi≤Work,如找到则执行步骤C,如找不 到同时满足以上二条件的进程则执行步骤D。
C.当进程i获得资源后可顺利执行直到完成,并释放出分配给它的 资源,表示如下:
work = work+Allocationi ; Finish[i]=true ;转执行步骤B。 D.如果所有的Finish[i]=true,则表示系统处于安全状态,否则 系统处于不安全状态。
P4
743
431
002
P2
745
600
302
P0
10 4 7 7 4 3
010
532 743 745 10 4 7 10 5 7
True
True True T0时刻的另 True 一个安全序 True 列
2、 P1请求资源
P1发出请求向量Request(1,0,2),系统按银行家算法进行检查: (1)Request1(1,0,2)≤Need(1,2,2) (2)Request1(1,0,2) ≤Available(3,3,2) (3)系统假定可为P1分配资源,并修改Available,Allocation1和
Need向量。 (4)检查此时系统是否安全。
发现可以找到一个安全序列{P1,P3,P4,P0,P2},因此系 统是安全的,可以立即将P1所申请的资源分配给它。
3、P4请求资源
P4发出请求向量Request4(3,3,0),系统按银行 家算法进行检查: (1)Request4(3,3,0)≤Need4(4,3,1) (2)Request4(3,3,0)≮Available(2,3,0),让 P4等待。
假设用Requesti[ j]=k表示并发执行时进程i提出请求j类资 源k个。系统按下述步骤进行检查:
专业英文字汇
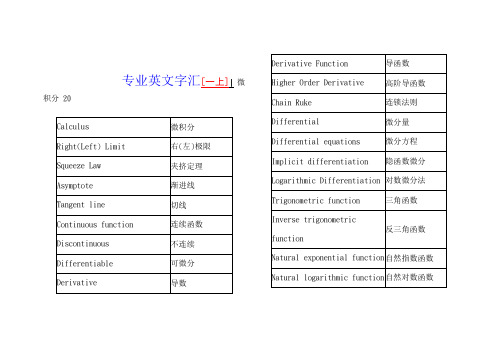
Trigonometric function
三角函数
Inverse trigonometric function
反三角函数
Naturalexponentialfunction
自然指数函数
Naturallogarithmicfunction
自然对数函数
物理实习30
dynaห้องสมุดไป่ตู้ics
动力学
kinematics
扇区
security
安全性
starvation
饥饿
statement
叙述
subalgorithm
子算法
subprogram
子程序
subroutine
子程序
syntax
语法
Unicode
万国码
variable
变数
whitespace
空白
frame
韧体
message
讯息
RAM
随机存取内存
ethernet
资料列
information
信息
router
路由器
network
网络
internet
因特网
recursive
递回
broadcast
广播
modem
调制解调器
register
缓存器
header
标头
compile
编译
compiler
编译器
tree
树
robot
机器人
monitor
屏幕
bandwidth
频宽
hacker
IBM Rational统一流程
专业英文字汇

byte
字节
carry
进位
client
客户端
cohesion
凝聚
collision
碰撞
compiler
编译器
compression
压缩
constant
常数
couping
耦合
database
数据库
datagram
资料框
deadlock
死结
declaration
宣告
decoding
解碼
decryption
Shift Operator
移位运算子
模数
most significant bit‚MSB
最大位
multiplexers
多任务器
one’s complement
l的补码
oscillate
振荡
output enable
输出致能
parity bit
同位
priority
优先权
product
积
quad
四个
reduction
简化
redundant
以太网络
subtree
子树
nonpreemptive
不可抢先排班
Method
方法
matching
比对
host
主机
server
主机服务器
Pascaline
加法器
encryption
加密
preemptive
可抢先排班
reliability
可靠性
portability
可移植性
readability
可读性
21世纪大学英语读写教程第四册UNIT3

21世纪大学英语读写教程第四册UNIT3Unit 3Text APre-reading ActivitiesFirst Listening Before Listening to the tape, have a quick look at the following words.smallpox 天花stuck 被难住了cowpox 牛痘lateral thinking 横向思维vertical 纵向的;垂直的Second Listening Listen to the tape again and then choose tne best answer to each of the following questions.1. How did Dr. Jenner solve the problem of smallpox? A) By studying many, many sick people. B) By studying people who didn't get sick. C) By studying lateral thinking. D) With help from Dr. de Bono.2. The key to lateral thinking is _________. A) never giving up B) getting help from others C) moving sideways D) changing you point of view3. The saying, "When thegoing gets tough, the tough get going" expresses________. A) the aggressive attitude of vertical thinking B) traditionally western lateral thinking C) a way to change your point of view D) how Edward de Bono likes to solve problems 4. The main purpose of this passage is ________. A) to discuss a major medical breakthrough B) to introduce a new concept of problem solving C) to talk about the life of Edward de Bono D) to contrast Eastern and Western ways of thinkingHow to Change Your Point of ViewCaroline SeebohmDr. Edward Jenner was busy trying to solve the problem of smallpox. After studying case after case, he still found no possible cure. He had reached an impasse in his thinking. At this point, he changed his tactics. Instead of focusing on people who had smallpox, he switched his attention to people who did not have smallpox. It turned out that dairymaids apparently never got the disease. From the discovery that harmless cowpox gave protection against deadly smallpox came vaccination and the end of smallpox as a scourge in the western world. We often reach an impasse in our thinking. We are looking at a problem and trying to solve it and it seems there is a dead end. It is on these occasions that we bee tense, we feel pressured, overwhelmed, in a state of stress. We struggle vainly, fighting to solve the problem. Dr. Jenner, however, did something about this situation.He stopped fighting the problem and simply changed his point of view—from his patients to dairy maids. Picture the process going something like this: Suppose the brain is a puter. This puter has absorbed into its memory bank all your history, your experiences, your training, your information received through life; and it is programmed according to all this data. To change your point of view, you must reprogramme your puter, thus freeing yourself to take in new ideas and develop new ways of looking at things. Dr. Jenner, in effect, by reprogramming his puter, erased the old way of looking at his smallpox problem and was free toreceive new alternatives. That's all very well, you may say, but how do we actually do that? Doctor and philosopher Edward de Bono has e up with a techniquefor changing our point of view, and he calls itLateral Thinking. The normal Western approach to a problem is to fight it. The saying, "When the going gets tough, the tough get going," is typical of this aggressive attitude toward problem-solving. No matter what the problem is, or the techniques available for solving it, the framework produced by our Western way of thinking is fight. Dr. de Bono calls this vertical thinking; the traditional, sequential, Aristotelian thinking of logic, moving firmly from one step to the next, like toy blocks being built one on top of the other. The flaw is, of course, that if at any pointone of the steps is not reached, or one of the toy blocks is incorrectly placed, then the whole structure collapses. Impasse is reached, and frustration, tension, feelings of fight take over. Lateral thinking,Dr. de Bono says, is a new technique of thinking about things—a technique that avoids this fight altogether, and solves the problem in an entirely unexpected fashion. In one of Sherlock Holmes's cases, his assistant, Dr. Watson, pointed out that a certain dog was of no importance to the case because it did not appear to have done anything. Sherlock Holmes took the opposite point of view and maintained that the fact the dog had done nothing was of the utmost significance, for it should have been expected to do something, and on this basic he solved the case. Lateral thinking sounds simple. And it is. Once you have solved a problem laterally, you wonder how you could ever have been hung up on it. The key is making that vital shift in emphasis, that sidestepping of the problem, instead of attacking it head-on. Dr. A. A. Bridger, psychiatrist at Columbia University and in private practice in New York, explains how lateral thinking works with his patients. "Many people e to me wanting to stop smoking, for instance," he says. "Most people fail when they are trying to stop smoking because they wind up telling themselves, 'No, I will not smoke; no, 1 shall not smoke; no, I will not; no, I cannot...' It's a fight and what happens is you end up smoking more." "So instead of looking at the problem from the old ways of no, and fighting it, I show them a whole new point of view—that you are your body's keeper, and your body is something through which you experience life. If you stop to think about it, there's really something helpless about your body. It can do nothing for itself. It has no choice, it islike a baby's body. You begin then a whole new way of looking at it—‘I am now going to take care of myself, and give myself some respect and protection, by not smoking.' “There is a Japanese parable about a donkey tied to a pole by a rope. The rope rubs tight against his neck. The more the donkey fights and pulls on the rope, the tighter and tighter it gets around his throat—until he winds up dead. On the other hand, as soon as he stops fighting, he finds that the rope gets slack, he can walk around, maybe find some grass to eat...That's the same principle: The more you fight something the more anxious you bee—the more you're involved in a bad pattern, the more difficult it is to escape pain. "Lateral thinking," Dr. Bridger goes on, "is simply approaching a problem with what I wouldcall an Eastern flanking maneuver. You know, when azen archer wants to hit the target with a bow and arrow, he doesn't concentrate on the target, he concentrates rather on what he has in his hands, so when he lets the arrow go, his focus is on the arrow, rather than the target. This is what an Easternflanking maneuver implies—instead of approaching the target directly, you approach it from a sideways point of view—or laterally instead of vertically." "I think the answer lies in that direction," affirms Dr. Bridger. "Take the situation where someone is in a crisis. The Chinese word for crisis is divided intotwo characters, one meaning danger and the other meaning opportunity. We in the Western world focusonly upon the ‘d anger' aspect of crisis. Crisis in Western civilization has e to mean danger, period. Andyet the word can also mean opportunity. Let us now suggest to the person in crisis that he cease concentrating so upon the dangers involved and the difficulties, and concentrate instead upon the opportunity—for there is always opportunity in crisis. Looking at a crisis from an opportunity point of view is a lateral thought." (1 100 words)New Wordssmallpox n. a highly contagious disease causing spots which leave marks on the skin 天花impasse n. a position from which progress is impossible; deadlock 僵局;死胡同tactics n. a method or process of carrying out a scheme or achieving some end 战术;策略dairymaid n. a girl or woman who works in a dairy 牛奶场女工dairy n. 1. place where milk is kept and milk products are made 牛奶场;奶品场 2. shop where milk, butter, etc. are sold 乳品店cowpox n. a disease of cows, of which the virus was formerly used in vaccination against smallpox 牛痘vaccination n. 接种疫苗scourge n. thing or person that causes great troubleor misfortune 苦难的根源;灾难;祸害dead end n. a point beyond which progress or achievement is impossible; a street or passage closed at one end 僵局;死巷,死胡同vainly ad. uselessly; in vain 枉然地;徒劳地vain a. 1. having too high an opinion of one's looks, abilities, etc.; conceited 自视甚高的;自负的 2. useless or futile 无用的,无益的,无效的;徒劳的erase vt. rub out; remove all traces of 擦掉;抹去lateral a. of, at, towards, or from the side or sides 横向的;侧面的;向侧面的laterally ad. in a lateral direction, sideways 横向地;侧面地;旁边地lateral thinking 横向思维,水平思考going n. 1. the condition of the ground for walking, driving or riding 地面状况 2. condition of progress 进行情况;进展framework n. 1. set of principles or ideas used as a basis for one's judgement, decisions, etc. 参照标准;准则;观点 2. structure giving shape and support 框架,结构vertical a. straight up and down; at right angles to a horizontal plane 纵向的;垂直的vertically ad. in a vertical direction 垂直地sequential a. of, forming, or following in (a) sequence 相继的;连续的flaw n. a defect; fault; error 瑕疵;缺点structure n. sth. built; anything posed of parts arranged together; way in which sth. is put together, organized, built, etc. 结构;建筑物;构造物utmost a. greatest; highest 极度的;极高的significance n. importance; meaning 重要性;意义,含义sidestep v. step aside; avoid by stepping aside 横跨一步避开;回避head-on ad. in a direct manner; with the head or front first 正面地;迎头向前地parable n. a brief story used to teach some moral lesson or truth 寓言donkey n. 驴slack a。
lock-free 机制

lock-free 机制lock-free机制是一种在并发编程中无需使用锁来实现线程安全的机制。
传统的线程安全机制通常使用锁来保护共享资源,但锁在高并发场景下可能导致线程竞争、死锁和性能下降等问题。
为了避免这些问题,lock-free机制被广泛应用于并发编程中。
lock-free机制的核心思想是通过使用原子操作来实现对共享资源的同步访问,而不需要使用锁对资源进行保护。
原子操作是一个不可分割的操作,具有“一次性执行,不可被中断”的特点,因此可以保证在多线程环境下也能正确地进行。
lock-free机制的实现通常依赖于硬件的原子指令和一些算法。
为了保证原子操作的正确性,硬件提供了一系列的原子指令,比如读-改-写指令(比如CAS指令)和条件更新指令(比如CMPXCHG指令)。
这些指令可以保证对共享资源的操作在执行过程中不会被其他线程干扰,从而实现线程安全。
除了硬件原子指令外,lock-free机制还需要依赖于一些算法来解决并发访问共享资源时的冲突问题。
常见的算法包括:无锁队列、无锁链表、无锁哈希表等。
这些算法通常会使用原子操作来实现对数据结构的插入、删除和查询等操作,以确保多线程环境下的正确性和性能。
lock-free机制有以下几个优点:1. 提高并发性能:由于不需要使用锁进行同步,多个线程可以同时访问共享资源,而不会被阻塞,从而提高了并发性能。
2. 避免死锁和线程竞争:锁在高并发场景下可能引发死锁和线程竞争等问题,而lock-free机制避免了使用锁,因此也避免了这些问题的出现。
3. 减少资源占用:锁通常需要占用一定的系统资源,如内核资源和内存空间。
而lock-free机制不需要锁,因此可以减少资源的占用。
然而,lock-free机制也存在一些挑战和限制:1. 难以实现:相比传统的加锁机制,lock-free机制的实现难度较大。
需要设计合适的算法和应用硬件原子指令,保证在多线程环境下的正确性。
2. 可能引发ABA问题:由于没有使用锁进行同步,可能会出现ABA问题。
中外合资经营企业合同英文版

中外合资经营企业合同英文版Joint ventures between Chinese and foreign companies have become increasingly common in recent decades as China has opened up its economy to greater international investment and cooperation. These partnerships offer numerous benefits to both the Chinese and foreign entities involved, allowing them to leverage each other's strengths, share risks and resources, and expand their reach into new markets. However, drafting an effective and comprehensive joint venture contract is critical to the success of such arrangements.The joint venture contract serves as the legal foundation upon which the partnership is built, outlining the rights, responsibilities, and obligations of each party. It is essential that this document is carefully crafted to anticipate and address potential issues that may arise during the course of the venture. Key considerations in the joint venture contract include the purpose and scope of the partnership, the ownership structure and management responsibilities, the financial arrangements and profit-sharing mechanisms, the duration and termination conditions of the agreement, and the dispute resolution procedures.Defining the Purpose and ScopeThe joint venture contract should begin by clearly articulating the purpose and scope of the partnership. This includes specifying the business activities that will be undertaken, the target markets and customers, and the products or services that will be offered. It is important to ensure that the objectives of the joint venture are aligned with the strategic goals and core competencies of both the Chinese and foreign partners. Any limitations or restrictions on the activities of the joint venture should also be explicitly stated.Ownership Structure and ManagementThe ownership structure of the joint venture is a critical component of the contract, determining the degree of control and influence that each party will have. This may involve an equal 50-50 split, or a majority-minority arrangement where one partner holds a larger equity stake. The contract should detail the capital contributions of each party, as well as the process for making future capital injections or adjustments to the ownership percentages.The management structure of the joint venture is closely tied to the ownership model. The contract should outline the composition of the board of directors, the decision-making authority of the board, and the process for appointing and removing directors. It should also specify the roles and responsibilities of any executive managementpositions, such as the general manager, finance director, or operations manager. Provisions for deadlock resolution in the event of disagreements between the partners should also be included.Financial Arrangements and Profit-SharingThe joint venture contract must carefully delineate the financial arrangements between the Chinese and foreign partners. This includes detailing the initial capital investment, the procedures for funding ongoing operations and expansion, and the mechanisms for distributing profits. The contract should specify the accounting standards and reporting requirements that will be followed, as well as the rights of each party to access financial information and conduct audits.The profit-sharing model is a critical component of the financial provisions. This may involve a simple split of net profits based on the equity ownership percentages, or a more complex formula that takes into account factors such as capital contributions, technology transfers, or management expertise. The contract should also address the handling of losses, including the responsibilities of each party to cover deficits and the conditions under which the venture may be terminated due to financial underperformance.Duration and TerminationThe joint venture contract should specify the intended duration ofthe partnership, whether it is a fixed term or an open-ended arrangement. It should also outline the conditions under which the joint venture may be terminated, such as the expiration of the agreed term, a material breach of the contract by one party, or the inability of the partners to resolve a deadlock. The contract should detail the procedures for winding up the joint venture, including the distribution of assets, the settlement of liabilities, and the protection of intellectual property and confidential information.Dispute ResolutionGiven the inherent complexities and potential for conflicts in a joint venture, the contract must include robust provisions for dispute resolution. This may involve a tiered approach, starting with direct negotiation between the partners, progressing to mediation by a third-party neutral, and ultimately culminating in binding arbitration or litigation. The contract should specify the applicable laws and jurisdictions that will govern the dispute resolution process, as well as any requirements for the parties to attempt to resolve disputes in good faith before pursuing formal legal action.ConclusionDrafting a comprehensive and well-structured joint venture contract is essential to the success of partnerships between Chinese and foreign companies. By carefully addressing key issues such as the purpose and scope of the venture, the ownership and managementstructure, the financial arrangements, the duration and termination conditions, and the dispute resolution procedures, the contract can help to mitigate risks, align the interests of the partners, and establish a strong foundation for a mutually beneficial collaboration. As China continues to open its doors to international investment, the importance of these joint venture contracts will only continue to grow.。
操作系统名词解释整理

==================================名词解释======================================Operating system: operating system is a program that manages the computer hardware. The operating system is the one program running at all times on the computer (usually called the kernel), with all else being systems programs and application programs.操作系统:操作系统一个管理计算机硬件的程序,他一直运行着,管理着各种系统资源Multiprogramming: Multiprogramming is one of the most important aspects of operating systems. Multiprogramming increases CPU utilization by organizing jobs (code and data) so that the CPU always has one to execute.多程序设计:是操作系统中最重要的部分之一,通过组织工作提高CPU利用率,保证了CPU始终在运行中。
batch system: A batch system is one in which jobs are bundled together with the instructions necessary to allow them to be processed without intervention.批处理系统:将许多工作和指令捆绑在一起运行,使得它们不必等待插入,以此提高系统效率。
SSD6名词解释
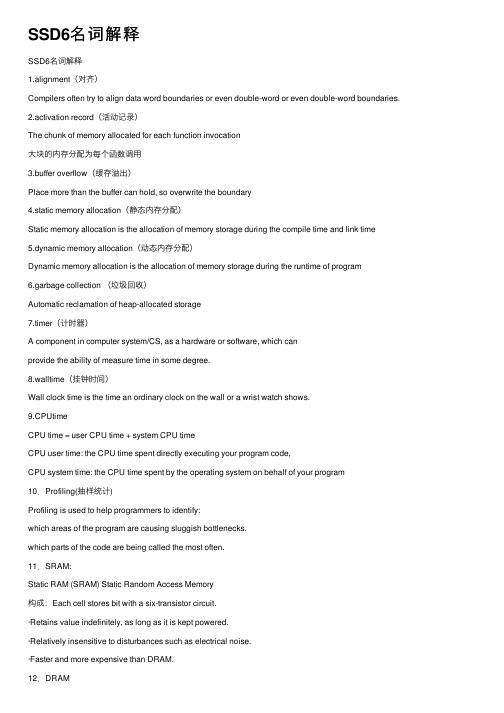
SSD6名词解释SSD6名词解释1.alignment(对齐)Compilers often try to align data word boundaries or even double-word or even double-word boundaries.2.activation record(活动记录)The chunk of memory allocated for each function invocation⼤块的内存分配为每个函数调⽤3.buffer overflow(缓存溢出)Place more than the buffer can hold, so overwrite the boundary4.static memory allocation(静态内存分配)Static memory allocation is the allocation of memory storage during the compile time and link time5.dynamic memory allocation(动态内存分配)Dynamic memory allocation is the allocation of memory storage during the runtime of program6.garbage collection (垃圾回收)Automatic reclamation of heap-allocated storage7.timer(计时器)A component in computer system/CS, as a hardware or software, which canprovide the ability of measure time in some degree.8.walltime(挂钟时间)Wall clock time is the time an ordinary clock on the wall or a wrist watch shows.9.CPUtimeCPU time = user CPU time + system CPU timeCPU user time: the CPU time spent directly executing your program code,CPU system time: the CPU time spent by the operating system on behalf of your program 10.Profiling(抽样统计)Profiling is used to help programmers to identify:which areas of the program are causing sluggish bottlenecks.which parts of the code are being called the most often.11.SRAM:Static RAM (SRAM) Static Random Access Memory构成:Each cell stores bit with a six-transistor circuit.·Retains value indefinitely, as long as it is kept powered.·Relatively insensitive to disturbances such as electrical noise.·Faster and more expensive than DRAM.12.DRAMDynamic RAM (DRAM) Dynamic Random Access Memory·构成:Each cell stores bit with a capacitor and transistor.·Value must be refreshed every 10-100 ms.·Sensitive to disturbances.·Slower and cheaper than SRAM.13.memory hierarchy(存储器的层次结构)The computer system is not to rely on a single memory component or technology but to employ a memory hierarchy. Thus, smaller, more expensive, faster memories are supplemented by larger, cheaper, slower memories. The key to the success of this organization is the last item: decreasing frequency of access.计算机系统不是依赖于单⼀的存储组件或技术,⽽是使⽤存储器的层次结构。
操作系统课件第06章 死锁

Chapter 6: Deadlocks死锁⏹What is Deadlock死锁的定义⏹System Model关于资源的系统模型⏹Deadlock Characterization 死锁的特征⏹Methods for Handling Deadlocks 死锁的处理方法☞Deadlock Prevention 死锁的预防☞Deadlock Avoidance 死锁的避免☞Deadlock Detection 死锁的检测☞Recovery from Deadlock 死锁的恢复⏹Combined Approach合成方法to DeadlockHandlingWhat is Deadlock死锁的定义Traffic Deadlock交通死锁The Deadlock Problem死锁问题的定义⏹A set of blocked processes被阻塞的进程eachholding a resource资源and waiting to acquire a resource held by another process in the set.一个集合中的所有进程各持有部分资源,且在等待集合中另一个进程所持有的资源⏹Example☞System has 2 tape drives.☞P1and P2each hold one tape drive and each needs another one.⏹Example☞semaphores A and B, initialized to 1P 0P 1wait (A);wait(B) wait (B);wait(A)Bridge Crossing过桥Example⏹Traffic only in one direction.⏹Each section of a bridge can be viewed as a resource.⏹If a deadlock occurs, it can be resolved if one car backsup (preempt resources and rollback回退).⏹Several cars may have to be backed up if a deadlockoccurs.如果死锁,有些汽车必须倒车⏹Starvation饿死is possible.Deadlock Characterization死锁的特征Deadlock Characterization死锁的特征Deadlock can arise发生if four conditions hold simultaneously同时.⏹Mutual exclusion互斥:only one process at a time canuse a resource独占资源.⏹Hold and wait保持且等待: a process holding at least oneresource is waiting to acquire additional resources held byother processes.⏹No preemption不可剥夺: a resource can be releasedonly voluntarily by the process holding it, after that processhas completed its task.⏹Circular wait循环等待:there exists a set {P0, P1, …, P0}of waiting processes such that P0 is waiting for a resourcethat is held by P1, P1is waiting for a resource that is heldbyP2, …, P n–1is waiting for a resource that is held byP n, and P0is waiting for a resource that is held by P0.四者缺一不可System Model关于资源的系统模型System Model关于资源的系统模型⏹Resource types R1, R2, . . ., R mCPU cycles, memory space, I/O devices⏹Each resource type R i has W i instances实例.☞同类资源中的各实例在满足需求方面均相同⏹Each process utilizes a resource as follows:☞request 申请☞use 使用☞release 释放⏹If in deadlock, none of the processes in the set can …死锁中的进程,不能:☞run运行☞release resources释放资源☞be awakened被唤醒Resource-Allocation Graph资源分配图A set of vertices节点V and a set of edges边线E.⏹V is partitioned into two types:☞P= {P1, P2, …, P n}, the set consisting of all the processes进程in the system.☞R= {R1, R2, …, R m}, the set consisting of all resource资源types in the system.⏹request edge申请边线–directed edge P1 →R j⏹assignment edge分配边线–directed edge R j→P iResource-Allocation Graph (Cont.)⏹Process⏹Resource Type with 4 instances⏹P i requests an instance of R j ⏹P i is holding an instance of R j P iP iR jR jExample of a Resource Allocation GraphResource Allocation Graph With A DeadlockResource Allocation Graph With A Cycle But No DeadlockBasic Facts⏹If graph contains no cycles ⇒no deadlock.资源分配图中没有循环⇒没有死锁⏹If graph contains a cycle ⇒资源分配图中有循环:☞if only one instance per resource type, then deadlock.如果每种资源仅有一个实例,则形成死锁☞if several instances per resource type, possibility of deadlock.如果有些资源有多个实例,则不一定死锁Methods for Handling Deadlocks死锁的处理方法Methods for Handling Deadlocks死锁的处理方法⏹Ensure that the system will never enter a deadlock state.确保系统从不发生死锁☞Deadlock Prevention死锁的预防☞Deadlock Avoidance死锁的避免⏹Allow the system to enter a deadlock state and thenrecover.允许系统发生死锁,而后恢复☞Deadlock Detection死锁的检测⏹Ignore the problem and pretend假装that deadlocks neveroccur in the system; used by most operating systems,including UNIX.假设系统从不发生死锁,忽略此类问题The Ostrich鸵鸟Algorithm⏹Pretend there is no problem假装没有问题⏹Reasonable if 在以下情况下可行☞deadlocks occur very rarely 死锁极少发生☞cost of prevention is high防止成本很高⏹UNIX and Windows takes this approach⏹It is a trade off折衷between☞convenience 方便性☞correctness 正确性Deadlock Prevention死锁的预防Restrain the ways request can be made.限制申请方式⏹Mutual Exclusion–not required for sharable resources;must hold for nonsharable resources.互斥——只对独占资源需要预防(独占→共享)⏹Hold and Wait–must guarantee that whenever aprocess requests a resource, it does not hold any otherresources.在申请资源时,不允许占有其他资源☞Require process to request and be allocated all itsresources所有资源before it begins execution, or allowprocess to request resources only when the process hasnone.☞Low resource utilization低资源利用率; starvation饿死possible.Deadlock Prevention (Cont.)⏹No Preemption不可剥夺–☞If a process that is holding some resources requests another resource that cannot be immediately allocated to it,then all resources currently being held are released.在申请新资源不能满足时,已持有资源全部释放☞Preempted resources are added to the list of resources for which the process is waiting.被剥夺的资源分配给等待进程☞Process will be restarted only when it can regain its old resources, as well as the new ones that it is requesting.进程只有当新旧资源都能同时满足时,才重新开始运行⏹Circular Wait–impose强加a total ordering排序of allresource types, and require that each process requests resources in an increasing order of enumeration.强制按特定顺序申请资源Summary of approaches to deadlock prevention死锁的预防方法总结Deadlock Avoidance死锁的避免Requires that the system has some additional a priori推理的information available.⏹Simplest and most useful model requires that eachprocess declare the maximum number of resources ofeach type that it may need.要求各进程声明每种资源的最大需求数量⏹The deadlock-avoidance algorithm dynamically examinesthe resource-allocation state to ensure that there cannever be a circular-wait condition.死锁避免算法动态检测资源分配状态,确保不循环等待⏹Resource-allocation state is defined by the number ofavailable and allocated resources, and the maximumdemands of the processes.资源分配状态由已分配资源数、可利用资源数和各进程的最大资源需求数确定Safe State安全状态⏹When a process requests an available resource, systemmust decide if immediate allocation leaves the system ina safe state.当进程申请资源时,系统须决定立即分配是否安全⏹System is in safe state if there exists a safe sequence ofall processes.如果存在一个所有进程的安全顺序,则系统处于安全状态⏹Sequence <P1, P2, …, P n> is safe if for each P i, theresources that P i can still request can be satisfied bycurrently available resources + resources held by all the P j, with j<I.☞If P i resource needs are not immediately available, then P ihave finished.can wait until all Pj☞When P j is finished, P i can obtain needed resources, execute, return allocated resources, and terminate.☞When P i terminates, P i+1can obtain its needed resources, and so on.Basic Facts⏹If a system is in safe state ⇒no deadlocks.如果系统处于安全状态⇒没有死锁⏹If a system is in unsafe state ⇒possibility ofdeadlock.如果系统处于不安全状态⇒不一定死锁因为各进程的运行存在不确定性,如个别进程的退出等⏹Avoidance ⇒ensure that a system will neverenter an unsafe state.死锁的避免⇒确保系统从不进入不安全状态Safe, Unsafe , Deadlock StateAlgorithms for Deadlock Avoidance避免死锁的算法⏹Resource-Allocation Graph Algorithm资源分配图算法⏹Banker’s Algorithm银行家算法Resource-Allocation Graph Algorithm资源分配图算法⏹Claim需要edge P i R j indicated that process P j mayrequest resource R j; represented by a dashed line.需要边表示进程可能会申请资源,用虚线表示⏹Claim需要edge converts to request edge when a processrequests a resource.当进程申请一个资源时,需要边转化为申请边⏹When a resource is released by a process, assignmentedge reconverts to a claim edge.当进程释放一个资源时,分配边转化为需要边⏹Resources must be claimed a priori推理的in the system.对资源的需求数需事先声明Resource-Allocation Graph For Deadlock AvoidanceUnsafe State In Resource-Allocation GraphBanker’s Algorithm银行家算法⏹Multiple instances.资源分配图不适用于多实例系统⏹Each process must a priori claim maximum use.每一进程必须能推算出最大资源的需求量⏹When a process requests a resource it mayhave to wait.当一个进程申请资源时,它可能需要等待⏹When a process gets all its resources it mustreturn them in a finite amount of time.当一个进程得到其所有申请资源后,须在有限时间内归还The Banker's Algorithmfor a Single Resource(a) (b) (c)⏹Three resource allocation states☞safe☞safe☞unsafeBanker's Algorithmfor Multiple Resources Example of banker's algorithm with multiple resources E:总的资源P:已分配资源A:剩余资源Data Structures for the Banker’s AlgorithmLet n= number of processes, and m = number of resources types.⏹Available:Vector of length m. If available [j] = k, there arek instances of resource type R j available.⏹Max: n x m matrix. If Max [i,j] = k, then process P i mayrequest at most k instances of resource type R j.⏹Allocation: n x m matrix. If Allocation[i,j] = k then P i iscurrently allocated k instances of R j.⏹Need: n x m matrix. If Need[i,j] =k, then P i may need kmore instances of R j to complete its task.Need[i,j]= Max[i,j] –Allocation[i,j].Safety Algorithm1.Let Work and Finish be vectors向量of length m and n,respectively. Initialize:Work = AvailableFinish [i] =false for i= 1,2, …, n.2.Find an i such that both:(a) Finish[i] = falseWork(b) NeediIf no such i exists, go to step 4.3.Work= Work + Allocation iFinish[i] =truego to step 2.4.If Finish[i] == true for all i, then the system is in a safestate, else unsafe.Resource-Request Algorithm for Process P i Request i = request vector for process P i . If Request i [j ] = k then process P i wants k instances of resource type R j .1.If Request i ≤Need i go to step2. Otherwise, raise error condition, since process has exceeded its maximum claim.2.If Request i ≤Available , go to step3. Otherwise P i must wait, since resources are not available.3.Pretend to allocate requested resources to P i by modifying the state as follows:Available = Available -Request i ;Allocation i = Allocation i + Request i ;Need i =Need i –Request i;;•If safe ⇒the resources are allocated to P i .•If unsafe ⇒P i must wait, and the old resource-allocation state is restoredExample of Banker’s Algorithm⏹ 5 processes P0 through P4; 3 resource types A(10 instances),B(5instances, and C(7 instances).⏹Snapshot at time T0:Allocation Max AvailableA B C A B C A B CP00 1 07 5 3 3 3 2P1 2 0 0 3 2 2P2 3 0 2 9 0 2P3 2 1 1 2 2 2P40 0 2 4 3 3Example (Cont.)⏹The content of the matrix. Need is defined to be Max –Allocation.NeedA B CP07 4 3P1 1 2 2P2 6 0 0P30 1 1P4 4 3 1⏹The system is in a safe state since the sequence < P1, P3, P4,P2, P0> satisfies safety criteria.Example P1Request (1,0,2) (Cont.)⏹Check that Request ≤Available (that is, (1,0,2) ≤(3,3,2) ⇒true.Allocation Need AvailableA B C A B C A B CP00 1 0 7 4 3 2 3 0P1 3 0 20 2 0P2 3 0 1 6 0 0P3 2 1 1 0 1 1P40 0 2 4 3 1⏹Executing safety algorithm shows that sequence <P1, P3, P4,P0, P2> satisfies safety requirement.⏹Can request for (3,3,0) by P4be granted?⏹Can request for (0,2,0) by P0 be granted?Deadlock Detection死锁的检测⏹Allow system to enter deadlock state允许系统进入死锁状态⏹Detection algorithm检测算法⏹Recovery scheme恢复方案Single Instance of Each Resource Type单实例资源类型⏹Maintain wait-for graph☞Nodes are processes.☞P i P j if P i is waiting for P j.i进程在等待j进程释放某资源⏹Periodically定期地invoke激活an algorithm thatsearches for a cycle in the graph.⏹An algorithm to detect a cycle in a graphrequires an order of n2operations, where n isthe number of vertices in the graph.算法复杂度n2Resource-Allocation Graph and Wait-for Graph Resource-Allocation Graph Corresponding wait-for graphSeveral Instances of a Resource Type多实例资源类型⏹Available: A vector of length m indicates the number ofavailable resources of each type.向量m表示每种类型资源可利用的实例数⏹Allocation:An n x m matrix defines the number ofresources of each type currently allocated to eachprocess.矩阵n x m表示各种资源分配给每个进程的实例数⏹Request:An n x m matrix indicates the current requestof each process. If Request [i j] = k, then process P i isrequesting k more instances of resource type. R j.矩阵n x m表示各进程当前请求的资源实例数Detection Algorithm检测算法1.Let Work and Finish be vectors of length m and n,respectively Initialize:(a) Work= Available(b)For i= 1,2, …,n, if Allocationi ≠0, thenFinish[i] = false;otherwise, Finish[i] = true.2.Find an index i such that both:(a)Finish[i] == false(b)Request i≤WorkIf no such i exists, go to step 4.Detection Algorithm (Cont.)3.Work= Work+ AllocationiFinish[i] = truego to step 2.4.If Finish[i] == false, for some i, 1 ≤i≤n, then the system is indeadlock state. Moreover, if Finish[i] == false, then Pi isdeadlocked.Algorithm requires an order of O(m x n2)operations to detect whether the system is in deadlocked state.Example of Detection Algorithm⏹Five processes P0through P4;three resource typesA (7 instances),B (2 instances), and C(6 instances).⏹Snapshot at time T0:Allocation Request AvailableA B C A B C A B CP00 1 0 0 0 0 0 0 0P1 2 0 0 2 0 2P2 3 0 30 0 0P3 2 1 1 1 0 0P40 0 2 0 0 2⏹Sequence <P0, P2, P3, P1, P4> will result in Finish[i] = truefor all i.Example (Cont.)⏹P2requests an additional instance of type C.RequestA B CP00 0 0P1 2 0 1P20 0 1P3 1 0 0P40 0 2⏹State of system?☞Can reclaim resources held by process P0, but insufficient resources to fulfill other processes‘ requests.☞Deadlock exists, consisting of processes P1, P2, P3, and P4.Detection-Algorithm Usage检测算法的使用⏹When, and how often, to invoke depends on:何时,如何激活依赖于:☞How often a deadlock is likely to occur?死锁发生的频率☞How many processes will need to be rolled back?需要回退的进程数量one for each disjoint cycle每个循环一个⏹If detection algorithm is invoked arbitrarily任意地, theremay be many cycles in the resource graph and so we would not be able to tell which of the many deadlocked processes “caused” the deadlock如果检测算法可随意激活,可能会在资源分配图中找到很多循环,从而很难发现是哪个进程“引起”了死锁。
os03b

Operating Systems
5.14
R1
request edge
R3
assignment edge
环(cycles)意义
如果图中没有环,则系统中没有 进程死锁。
P1
P2
P3
如果有环,在死锁可能存在(a deadlock may exist)。
如果每个资源类型只有一个 实例(exactly one instance),则一个环意味着 死锁已经发生。
操作系统
Operating Systems
第3章 CPU调度 & 死锁
Chapter 3: CPU Scheduling & Deadlocks
Deadlock 死锁
A process requests resources; and if the resources are not available at that time, the process enters a waiting state. Sometimes, a waiting process is never again able to change state, because the resources it has requested are held by other waiting processes. ----This situation is called a deadlock.
Operating Systems
5.22
尽管这种方对死锁问题法看起来不是一种可行的办法,不过某些操作 系统使用这种方法。
在许多系统中,死锁很少发生。因此,这种方法相对必须经常 使用的昂贵的死锁预防、避免检测及恢复方法要廉价。而且在某 些情况下,系统是处在一种冻结状态(frozen state)而不是死锁 状态(deadlock state).
Deadlock Checking Using Net Unfoldings

1 Introduction
In the eld of static analysis of concurrent systems deadlock freeness is almost always a desirable property. Many research has been carried out to propose methods that check this property 3]. One of these was presented by McMillan in 8]. It is based on net unfoldings of Petri net systems. A net unfolding is class of partial order semantics of Petri nets, also known as branching process 4]. The heuristic used in McMillan's algorithm is particularly good where the unfolding grows more deeply than widely and thereby only few end points of the unfolding (i.e., cut-o points) have to be considered. These kinds of unfoldings correspond to systems with a more deterministic behaviour. In contrast, highly non-deterministic systems tend to yield wide unfoldings that slow McMillan's algorithm down. We introduce an approach that exploits the characteristic of wide unfoldings (i.e., the number of cut-o points is high). Moreover, we present an implementation of McMillan's algorithm and compare both approaches by means of several examples. We use Corbett's benchmark examples 3] as well as McMillan's examples 8] which allows a direct comparison between his LISP implementation and our carried out in C 12]. The paper is organized as follows: In section 2 we give a brief introduction of the basic concepts of Petri nets and net unfoldings. In this section we fall back on the introduction given in 5]. Section 3 presents the deadlock detection method using a linear algebraic approach. In section 4 we give an implementation of McMillan's deadlock algorithm 8]. In section 5 we show some results and compare both approaches. Section 6 serves as a conclusion and gives an outlook on further work. All proofs are presented in appendix A.
解决Oracle数据库死锁

解决Oracle数据库死锁解决Oracle数据库死锁2011年01月12日星期三08:35 P.M.解决Oracle数据库死锁介绍本文我们尝试总结在多个用户并发情况下,如何识别和解决删除操作期间发生的死锁问题,在开始之前,我们先简单描述一下什么是死锁以及什么东西会导致死锁。
死锁在任何数据库中发生死锁都是不愉快的,即使是在一个特殊的情况下发生也是如此,它们会减小应用程序的接受程度(ACCEPTANCE),因此避免并正确解释死锁是非常重要的。
当两个或更多用户相互等待锁定的数据时就会发生死锁,发生死锁时,这些用户被卡住不能继续处理业务,Oracle自动检测死锁并解决它们(通过回滚一个包含在死锁中的语句实现),释放掉该语句锁住的数据,回滚的会话将会遇到Oracle错误"ORA-00060:等待资源时检测到死锁"。
是什么导致了死锁?明确地锁定表是为了保证读/写一致性,未建立索引的外键约束,在相同顺序下表不会锁住,没有为数据段分配足够的存储参数(主要是指INITTRANS,MAXTRANS和PCTFREE参数)很容易引发突发锁和死锁,原因是多种多样的,需要重新逐步审查。
识别死锁当Oracle数据库检测到死锁时(Oracle错误消息:ORA-00060),相应的消息就写入到警告日志文件中(alert.log),另外还会在USER_DUMP_DEST目录下创建一个跟踪文件,分析警告日志文件和跟踪文件是非常耗时的。
下面是一个警告日志文件示例:Mon Aug 07 09:14:42 2007 ORA-000060:Deadlock detected.Moreinfo in file e:\oracle\admin\GEDEON\udump\ORA01784.TRC.下面是从跟踪文件中节选出来的片段,从其中我们可以看出是哪个语句创造了死锁,相关的语句和被锁定的资源已经标记为粗体。
/users/ora00/log/odn_ora_ 1097872.trc Oracle9i Enterprise Edition Release 9.2.0.8.0-64bit Production With the Partitioning,OLAP and Oracle Data Mining options JServer Release 9.2.0.8.0-Production ORACLE_HOME=/soft/ora920 System name:AIX Node name:beaid8 Release:2 Version:5 Machine:00C95B0E4C00 Instance name:ODN Redo thread mounted by this instance:1 Oracle process number:17 Unix process pid:1097872,image:oracle@beaid8(TNS V1-V3)*2007-06-04 14:41:04.080*SESSION ID:(10.6351)2007-06-04 14:41:04.079 DEADLOCK DETECTED(ORA-00060)The following deadlock is not an ORACLE error.It is adeadlock due to user error in the design of an application orfrom issuing incorrect ad-hoc SQL.The following information may aidin determining the deadlock:Deadlock graph:---Blocker(s)-----Waiter(s)---Resource Name process session holds waits process session holds waits TM-00001720-00000000 17 10 SX 16 18 SX SSX TM-0000173a-00000000 16 18 SX 17 10 SX SSX session 10:DID 0001-0011-00000002session 18:DID 0001-0010-00000022 session 18:DID 0001-0010-00000022session 10:DID 0001-0011-00000002 Rows waited on:Session 18:obj-rowid=00001727-AAABcnAAJAAAAAAAAA(dictionary objn-5927,file-9,block-0,slot-0)Session 10:obj-rowid=00001727-AAABcnAAJAAAAAAAAA(dictionary objn-5927,file-9,block-0,slot-0)Information on the OTHER waiting sessions:Session 18:pid=16 serial=2370 audsid=18387 user:21/ODN O/S info:user:mwpodn00,term:unknown,ospid:,machine:beaida program:JDBC Thin Client application name:JDBC Thin Client,hash value=0 Current SQL Statement:DELETE FROM ODNQTEX WHERE EX_ID=:B1 End of information on OTHER waiting sessions.Current SQL statement for this session:DELETE FROM ODNQTFN WHERE FN_ID_EXIGENCE_EX=:B1---PL/SQL Call Stack---object line object handle number name 7000000135 f7fd8 34 procedure ODN.ODNQPDR 700000013 5f89f0 16 procedure ODN.ODNQPZB我们可以使用企业管理器来决定保留所有的锁还是释放掉它们,为了便于说明,我们打开2个sqlplus实例会话(在此期间同时发生了死锁)来一起调式,当每个语句执行完毕后,我们看到锁仍然保留下来了,它可以帮助我们识别出是哪个资源引起的死锁。
黑马程序员英语单词册

黑马程序员英语单词册经过几天的整理黑马程序员将必备的600词汇,和有关计算机需要掌握的词汇整理出来,分享给大家学习,希望对你有所帮助。
- 1 -程序员必备的 600 个英语词汇(1)对于时刻需要和国际接轨的码农们,英语的重要性是毋庸置疑的。
尤其是那些胸怀大志的潜在大牛们,想在码农行业闯出一片天地,秒杀身边的小弟们,熟练掌握英语更是实现其目标最关键的因素之一。
否则,试想在你捧着某出版社刚刚翻译出来的《JSP高效编程》苦苦学习JSP模板的时候,你旁边的小弟却是拿着原版的《AngularJS in Action》学习开发单页面应用,虽然你们都同样认真地学习了一个月,可做出来东西的效果能一样吗?所以,英语好才能学到最新最炫的技术,否则只能拿着国内出的翻译版学习两三年前的老古董还把它当个宝。
首先要有词汇:下面开始我们的英语词汇的学习生涯!application 应用程式应用、应用程序application framework 应用程式框架、应用框架应用程序框架architecture 架构、系统架构体系结构argument 引数(传给函式的值)。
叁见 parameter 叁数、实质叁数、实叁、自变量array 阵列数组arrow operator arrow(箭头)运算子箭头操作符assembly 装配件assembly language 组合语言汇编语言assert(ion) 断言assign 指派、指定、设值、赋值赋值assignment 指派、指定赋值、分配assignment operator 指派(赋值)运算子 = 赋值操作符associated 相应的、相关的相关的、关联、相应的associative container 关联式容器(对应 sequential container)关联式容器atomic 不可分割的原子的attribute 属性属性、特性audio 音讯音频A.I. 人工智慧人工智能background 背景背景(用於图形着色)- 2 -后台(用於行程)backward compatible 回溯相容向下兼容bandwidth 频宽带宽base class 基础类别基类base type 基础型别 (等同於 base class)batch 批次(意思是整批作业) 批处理benefit 利益收益best viable function 最佳可行函式最佳可行函式(从 viable functions 中挑出的最佳吻合者)binary search 二分搜寻法二分查找binary tree 二元树二叉树binary function 二元函式双叁函数binary operator 二元运算子二元操作符binding 系结绑定bit 位元位bit field 位元栏位域bitmap 位元图位图bitwise 以 bit 为单元逐一┅bitwise copy 以bit 为单元进行复制;位元逐一复制位拷贝block 区块,区段块、区块、语句块boolean 布林值(真假值,true 或 false)布尔值border 边框、框线边框brace(curly brace) 大括弧、大括号花括弧、花括号bracket(square brakcet) 中括弧、中括号方括弧、方括号breakpoint 中断点断点build 建造、构筑、建置(MS 用语)- 3 -build-in 内建内置bus 汇流排总线business 商务,业务业务buttons 按钮按钮byte 位元组(由 8 bits 组成) 字节cache 快取高速缓存call 呼叫、叫用调用callback 回呼回调call operator call(函式呼叫)运算子调用操作符(同 function call operator)candidate function 候选函式候选函数(在函式多载决议程序中出现的候选函式)chain 串链(例 chain of function calls) 链character 字元字符check box 核取方块 (i.e. check button) 复选框checked exception 可控式异常(Java)check button 方钮 (i.e. check box) 复选按钮child class 子类别(或称为 derived class, subtype) 子类class 类别类class body 类别本体类体class declaration 类别宣告、类别宣告式类声明class definition 类别定义、类别定义式类定义class derivation list 类别衍化列类继承列表class head 类别表头类头class hierarchy 类别继承体系, 类别阶层类层次体系class library 类别程式库、类别库类库- 4 -class template 类别模板、类别范本类模板class template partial specializations类别模板偏特化类模板部分特化class template specializations类别模板特化类模板特化cleanup 清理、善后清理、清除client 客端、客户端、客户客户client-server 主从架构客户/服务器clipboard 剪贴簿剪贴板clone 复制克隆collection 群集集合combo box 复合方块、复合框组合框command line 命令列命令行(系统文字模式下的整行执行命令)communication 通讯通讯compatible 相容兼容compile time 编译期编译期、编译时compiler 编译器编译器component 组件组件composition 复合、合成、组合组合computer 电脑、计算机计算机、电脑concept 概念概念concrete 具象的实在的concurrent 并行并发configuration 组态配置connection 连接,连线(网络,资料库) 连接- 5 -constraint 约束(条件)construct 构件构件container 容器容器(存放资料的某种结构如 list, vector...) containment 内含包容context 背景关系、周遭环境、上下脉络环境、上下文control 控制元件、控件控件console 主控台控制台const 常数(constant 的缩写,C++ 关键字) constant 常数(相对於 variable) 常量constructor(ctor) 建构式构造函数(与 class 同名的一种 member functions)copy (v) 复制、拷贝拷贝copy (n) 复件, 副本cover 涵盖覆盖create 创建、建立、产生、生成创建creation 产生、生成创建cursor 游标光标custom订制、自定定制data 资料数据database 资料库数据库database schema 数据库结构纲目data member 资料成员、成员变数数据成员、成员变量data structure 资料结构数据结构datagram 资料元数据报文dead lock 死结死锁- 6 -debug 除错调试debugger 除错器调试器declaration 宣告、宣告式声明deduction 推导(例:template argument deduction) 推导、推断default 预设缺省、默认defer 延缓推迟define 定义预定义definition 定义、定义区、定义式定义delegate 委派、委托、委任委托delegation (同上)demarshal 反编列散集dereference 提领(取出指标所指物体的内容) 解叁考dereference operator dereference(提领)运算子 * 解叁考操作符derived class 衍生类别派生类design by contract 契约式设计design pattern 设计范式、设计样式设计模式※ 最近我比较喜欢「设计范式」一词destroy 摧毁、销毁destructor 解构式析构函数device 装置、设备设备dialog对话窗、对话盒对话框directive 指令(例:using directive) (编译)指示符directory 目录目录disk 碟盘dispatch分派分派distributed computing 分布式计算 (分布式电算) 分布式计算- 7 -分散式计算 (分散式电算)document 文件文档dot operator dot(句点)运算子 . (圆)点操作符driver 驱动程式驱动(程序)dynamic binding 动态系结动态绑定今天的英语学习就到这了!!!!- 8 -程序员必备的 600 个英语词汇(2)哥是来吐槽的,虽说英语很重要,对于每一位程序员,非常重要,每一行代码,都是密密麻麻的英文字母重要,有时还要去苦思深虑的去为变量、方法、类取其一个名字,思前想后,一个又长又难懂的名字诞生了!当时一阵欣慰,日后,再见,一阵伤感,这到底是个毛意思?efficiency 效率效率efficient 高效高效end user 终端用户entity 物体实体、物体encapsulation 封装封装enclosing class 外围类别(与巢状类别 nested class 有关)外围类enum (enumeration) 列举(一种 C++ 资料型别) 枚举enumerators 列举元(enemy 型别中的成员) 枚举成员、枚举器equal 相等相等equality 相等性相等性equality operator equality(等号)运算子 == 等号操作符equivalence 等价性、等同性、对等性等价性equivalent等价、等同、对等等价escape code 转义码转义码evaluate 评估、求值、核定评估event 事件事件event driven 事件驱动的事件驱动的exception 异常情况异常exception declaration 异常宣告(ref. C++ Primer 3/e, 11.3)异常声明exception handling 异常处理、异常处理机制异常处理、异常处理机制exception specification 异常规格(ref. C++ Primer 3/e, 11.4)异常规范exit 退离(指离开函式时的那一个执行点) 退出- 9 -explicit 明白的、明显的、显式显式export 汇出引出、导出expression 运算式、算式表达式facility 设施、设备设施、设备feature 特性field 栏位,资料栏(Java) 字段, 值域(Java)file 档案文件firmware 韧体固件flag 旗标标记flash memory 快闪记忆体闪存flexibility 弹性灵活性flush 清理、扫清刷新font 字型字体form 表单(programming 用语) 窗体formal parameter 形式叁数形式叁数forward declaration 前置宣告前置声明forwarding 转呼叫,转发转发forwarding function 转呼叫函式,转发函式转发函数fractal 碎形分形framework 框架框架full specialization 全特化(ref. partial specialization) function 函式、函数函数function call operator 同 call operatorfunction object 函式物件(ref. C++ Primer 3/e, 12.3) 函数对象function overloaded resolution函式多载决议程序函数重载解决(方案)- 10 -functionality 功能、机能功能function template 函式模板、函式范本函数模板factor 仿函式仿函式、函子game 游戏游戏generate 生成generic 泛型、一般化的一般化的、通用的、泛化generic algorithm 泛型演算法通用算法getter (相对於 setter) 取值函式global 全域的(对应於 local) 全局的global object 全域物件全局对象global scope resolution operator全域生存空间(范围决议)运算子 :: 全局范围解析操作符group 群组group box 群组方块分组框guard clause 卫述句 (Refactoring, p250) 卫语句GUI 图形介面图形界面hand shaking 握手协商handle 识别码、识别号、号码牌、权柄句柄handler 处理常式处理函数hard-coded 编死的硬编码的hard-copy 硬拷图屏幕截图hard disk 硬碟硬盘hardware 硬体硬件hash table 杂凑表哈希表、散列表header file 表头档、标头档头文件heap 堆积堆- 11 -hierarchy 阶层体系层次结构(体系)hook 挂钩钩子hyperlink 超链结超链接icon 图示、图标图标IDE 整合开发环境集成开发环境identifier 识别字、识别符号标识符if and only if 若且唯若当且仅当Illinois 伊利诺伊利诺斯image 影像图象immediate base 直接的(紧临的)上层 base class。
死锁(ora-00060)以及死锁相关的知识点

死锁(ora-00060)以及死锁相关的知识点最近碰到一个死锁的问题:ora-00060 deadlock detected while waiting for resource (ora-00060 等待资源时检测到死锁)查看udump(SQL> show parameter USER_DUMP_DEST; 查看该目录)下面的trace,发现如下日志:*** 2009-08-13 10:53:11.656*** SERVICE NAME:(his3) 2009-08-13 10:53:11.593*** SESSION ID:(130.3437) 2009-08-13 10:53:11.593DEADLOCK DETECTED[Transaction Deadlock]Current SQL statement for this session:UPDATE MY_KUCUN1 SET KUCUNSL = KUCUNSL - :B3 WHERE YINGYONGID = :B2 AND JIAGEID = :B1----- PL/SQL Call Stack -----object line objecthandle number name33DF6A44 6002 package body HIS3KS.PKG_MY_JINXIAOCUN2FD11B48 1 anonymous blockThe following deadlock is not an ORACLE error. It is adeadlock due to user error in the design of an applicationor from issuing incorrect ad-hoc SQL. The followinginformation may aid in determining the deadlock:Deadlock graph:---------Blocker(s)-------- ---------Waiter(s)---------Resource Name process session holds waits process session holds waitsTX-000b001c-00005019 38 130 X 19 106 XTX-00010025-000100ee 19 106 X 38 130 Xsession 130: DID 0001-0026-00008297 session 106: DID 0001-0013-00004EB8 session 106: DID 0001-0013-00004EB8 session 130: DID 0001-0026-00008297 Rows waited on:Session 106: obj - rowid = 0000E1AB - AAAOGrAAXAAAJHQAAT(dictionary objn - 57771, file - 23, block - 37328, slot - 19)Session 130: obj - rowid = 0000E1AB - AAAOGrAAXAAAJHQAAZ(dictionary objn - 57771, file - 23, block - 37328, slot - 25)Information on the OTHER waiting sessions:Session 106:pid=19 serial=671 audsid=309881 user: 64/HIS3KSO/S info: user: NT AUTHORITY\ANONYMOUS LOGON, term: MEDIINFO-QA2, ospid: 6708:6612, machine: WORKGROUP\MEDIINFO-QA2program: cicsas.exeapplication name: cicsas.exe, hash value=0Current SQL Statement:UPDATE MY_KUCUN1 SET KUCUNSL = KUCUNSL - :B3 WHERE YINGYONGID = :B2 AND JIAGEID = :B1End of information on OTHER waiting sessions.================================================== =几个重要的信息就是锁的类型是X,说明是DML语句导致的行级排他锁,涉及到两个Session:130和106。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Proceedings of the 19th ACSC Conference,Melbourne, Australia, January 31 - February 21996.Deadlock-Free Information Structure DistributedMutual Exclusion AlgorithmsUmberto Bonollo Elizabeth A. SonenbergDepartment of Computer Science The University of MelbourneParkville 3052Australia umberto@cs.mu.oz.au eas@cs.mu.oz.au AbstractIn the distributed mutual exclusion problem, a set of processes must coordinate their actions so that at any time at most one process may be within its critical section. Information structure distributed mutual exclusion algorithms (ISDME) are instances of a general algorithm which can represent several non-token-based algorithms. This paper introduces a new deadlock-free ISDME algorithm (DF-ISDME)which operates on a restricted class of information structures. DF-ISDME allows deadlock-free solutions for a wider class of information structure topologies than a previously identified class of deadlock-free Maekawa algorithms (DF-Maekawa),but retains the same throughput as DF-Maekawa.The paper provides a detailed description of the DF-ISDME algorithm, and correctness proofs.Message performance of the new algorithm is discussed, as are potential application scenarios.Keywords Distributed systems, distributed algorithms, distributed mutual exclusion, operating systems.1IntroductionIn the distributed mutual exclusion problem [2, 6,10], a set of distributed processes must coordinate their actions such that at any time at most one process has access to a shared resource: for example,a network printer, or a tuple in a distributed database.A process may only be within its critical section (CS)whenever it has gained exclusive access to the shared resource. Processes can only communicate with each other by message passing - there is no shared memory.There are several well known distributed mutual exclusion algorithms which have been published in the literature. Generally, these distributed mutual exclusion algorithms can be classed as either token-based or information structure (ISDME)algorithms. In token-based algorithms, a unique token is passed among the processes. Possession of the token guarantees mutual exclusion. The token-based algorithm of Suzuki and Kasami [11] is a well known example. Information structure algorithms are instances of a general algorithm (GEN-ISDME)proposed by Sanders [7] as a means of classifying several non-token-based algorithms [2, 6, 3]. Among the advantages of information structure algorithms is their potential for local handling of process failure and process recovery while, by comparison, token-based algorithms require global cooperation for handling process failure which can be quite complex [7]. A taxonomy of distributed mutual exclusion algorithms appears in the survey by Singhal [9].A distributed system is a set of distributed processes, i n ∈{,,...,}12, which are connected by a communications network. Most descriptions of distributed mutual exclusion algorithms assume a specific communications and processing environment with the following properties: Processes may be asynchronous meaning that there are time intervals within which no instructions need be executed; Each process is associated with a communication channel from which it can receive messages and each process can send messages to the communication channels of any of the other processes; Communication between the processes is assumed to be reliable meaning that all messages sent are eventually delivered, and that messages can't be corrupted or duplicated; Message transit times are finite but arbitrary; Messages between any two processes are assumed to arrive in the order they were sent, called first-in-first-out(FIFO) order; Message arrivals at a process are handled serially; and finally processes can't fail. The performance of a mutual exclusion algorithm can be measured by the average number of messages (M )exchanged per execution of a CS and the synchronisation delay (D ) between successive executions of the CS in response to concurrent requests for CS access.In an ISDME algorithm, each process has a pair of sets called the request set and the inform set which form the local information structure . The collection of these pairs defines the global information structure. For the GEN-ISDME algorithm, each process requests permission to enter its CS by sending Request messages to the processes which are members of its request set 1 followed by waiting for Grant messages to be received from them. Upon exiting its CS, the process will then send Release messages to the processes which are members of its inform set. Mutual exclusion is only guaranteed when the request sets and the inform sets satisfy a certain condition on the global information structure.It turns out that the request sets and inform sets can describe the topology of several well known and practical mutual exclusion algorithms [7] including the following which are listed here along with their message performance M : The Centralised Algorithm [4] with a single centralised coordinator, M =3; The fully-distributed Ricart-Agrawala [6] Algorithm,M n =−21(); Lamport [2] Fully Distributed Algorithm, M n =−31(); and Maekawa [3]Algorithm, O (n ). While there are algorithms which can enter the CS by sending very few messages (e.g., O (log n ) [5]), this is also accompanied by longer delays D to enter the CS (e.g.also O (log n ) [5]). On the other hand, most ISDME algorithms have delays of D =1 [6] or of D =2 [3]which means they perform well under heavy demand for the CS.Unfortunately, due to arbitrary communication delays, the GEN-ISDME algorithm can deadlock under certain information structures [7] and so is impractical. Sanders proposed a deadlock-detecting algorithm (DDGEN-ISDME) which detects and avoids potential deadlock situations: it uses a deadlock recovery scheme requiring the exchange of Inquire , Yield , and Fail messages. The deadlock recovery scheme is quite complex. As Sanders [7] has pointed out, the original version of the Maekawa algorithm used such a scheme but didn't send Fail messages under certain circumstances hence still leaving a scenario for deadlock. The potential for deadlock means that ISDME algorithms may perform1 It's crucial that the Request messages are sent without waiting for replies and in no particular order;Request messages could be implemented using some broadcast primitive.worse than their lower bound whenever the potential for deadlock arises. The probability of the lower bound not being achieved increases under conditions of heavy demand for the CS.The objective of this paper is to identify a class of deadlock-free ISDME algorithms which do not require any deadlock recovery scheme. As we will show, this will be achieved by introducing a new deadlock-free ISDME algorithm (DF-ISDME) which operates on a more restricted class of information structures than the class introduced by Sanders for GEN-ISDME. Our DF-ISDME algorithm only has a synchronisation delay of D =1 which is twice as fast as the delay of the Maekawa algorithm D =2 [3].Research related to this work has been carried out by Singhal [8]. Singhal proposed an algorithm for a class of deadlock-free Maekawa algorithms (DF-Maekawa) whose class of information structures is a restriction on the class admitted by the standard Maekawa algorithms. The message performance for DF-Maekawa is 312()n − compared with O (n )for Maekawa as the deadlock freedom is achieved at the expense of increased communication costs, but the delay is D =1. The DF-ISDME algorithm introduced here can handle a more general class of information structures than DF-Maekawa can yet it still retains the D =1 delay. The class of information structures handled by DF-ISDME may be viewed along a continuum from DF-Maekawa on the one hand to Ricart-Agrawala [6] on the other. However,our focus is based on the information structure approach of Sanders [7] whereas Singhal's focus in [8] was solely on the classes admitted by Maekawas's algorithm [3].In the following sections, we describe the DF-ISDME algorithm. We then present formal proofs of its correctness. The performance of the algorithm under optimal conditions is shown We show an example of its application. We then conclude with our discussion.2 A Deadlock-Free ISDME AlgorithmIn this section, we define the concept of information structures for ISDME algorithms and describe a new deadlock-free ISDME algorithm (DF-ISDME).2.1Information StructuresThe following definitions apply to information structures in an ISDME algorithm: The local i nformation structure for a process i is defined by a pair of sets called, the request set , R i , and the inform set , I i . The global information structure for a set of processes is the collection of local information structures for each process, i n ∈{,,...,}12. A process i must send a Request message before entering the CS to all the processes which are members of its requestset, R i and it must only send Release messages on exiting the CS to the processes which are members of its inform set, I i. For convenience, we define for each process i the status set, St i. The status set St i is derived from the inform sets of the processes using the following rule,∀ij:i I j∈↔j St i∈. A process i keeps track of any processes j St i∈since j must inform i before j enters the CS and after j exits the CS.Figures 1 and 2 show two ISDME algorithms whose topology is described in terms of their global information structures. The local information structure of each process together with its corresponding status set is also shown. As in [7], for processes i and j, a solid arc from i to j indicates that j I i∈ and j R i∈. A dashed arc from i to j indicates that j R i∈but j I i∉. Figure 1 corresponds to the symmetric fully-distributed Ricart-Agrawala algorithm [6] in which each process requests permission from every other process before entering the CS. Figure 2 corresponds to an algorithm in which each process requests permission from a predetermined subset of processes. In Figure 2, either process 2 or process 3 will request entry by asking processes 1, 2, and 3; process 1 only asks itself, but receives requests from the other two processes; when process 2 or process 3 exits the CS it must inform process 1 by sending it a Release message; processes 2 and 3 never send Release messages to each other.Beverly Sanders introduced a general algorithm called DDGEN-ISDME in [7] which guarantees mutual exclusion if a global information structure satisfies the following information structure conditions.ISDME Mutual Exclusion Theorem (Sanders [7]). The information structure conditions ∀∈i i I i:,∀⊆i I Ri i:, and ∀≠ij i j:()I Ii j∩≠∅∨()i R j Rj i∈∧∈are necessary and sufficient conditions for the DDGEN-ISDME algorithm to guarantee mutual exclusion.For mutual exclusion, the DF-ISDME algorithm requires that the following information structure conditions hold: ∀∈i i I i:, ∀⊆i I Ri i:, and ∀≠ij i j: ()i I j Ij i∈∨∈∨()i R j Rj i∈∧∈(For a proof see Section 3.2). The class of information structures allowed by the DF-ISDME information structure conditions is a subset of the class of information structures allowed by Sanders' ISDME theorem [7]. The DDGEN-ISDME algorithm requires a complex deadlock-recovery scheme for deadlock-freedom [7, 8]. The DF-ISDME algorithm is deadlock-free but does not require deadlock-recovery. Both of the algorithms shown in Figures 1 and 2 are deadlock-free with respect to the DF-ISDME algorithm.2.2DF-ISDME Algorithm Description In this section we present the DF-ISDME algorithm code. The following variables are used by a process i: The request set R i and the inform set I i which form the local information structure together with the status set St i derived from I i. A logical clock clk [2] which is used to tag each Request message sent by i with a logical time t such that the next value of t will be one greater than the highest time value that i has received thus far. A priority request queue Q i which maintains an ascending order sorted list of the timestamps associated with Request messages received by process i. A timestamp is a tuple consisting of the time value of a Request together with the process identifier of the process making the request. A timestamp (,)i t i is less than (has higher priority)than a timestamp (,)j t j, written (,)(,)i t j ti j<, when ()()t t t t i ji j i j<∨=∧<holds. The function priority_insr(Q i,(,)j t j) returns a new priority queue inserting the timestamp (,)j t j into the priority request queue described by the current valueof Q i. Send statements are of the form send j msgi(,) which sends the message represented by the tuple msg to the channel associated with process j.Send statements are always enabled when control reaches them and they never block. Receive statements are ofR2 = {1,2,3,4} I1 = {1}I2 = {2}St1 = {1}St2 = {2}R3 = {1,2,3,4} I4 = {4}I3 = {3}St4 = {4}St3 = {3} Figure 1: Ricart-Agrawala ISDME InformationStructure.R1 = {1}R2 = {1,2,3} I1 = {1}I2 = {1,2}St2 = {2}I3 = {1,3}St3 = {3}Figure 2: Example ISDME Information Structure.the form recv msgi() which receives the next message from the channel associated with process i into the tuple described by msg.Receive statements are enabled for a process i when control reaches them and the channel associated with i is not empty, otherwise the receive statement will block until a message for i arrives in the channel.The DF-ISDME algorithm for a process i is defined by the following program code:loop// process i waiting (requesting) to enter the CSw1:clk := clk + 1w2:t := clkw3:∀s ∈ R i : send i( s, (Req, i, t, clk) )w4:grants_left := | R i |w5:while grants_left > 0 ∨ (i, t) ≠ head(Q i) doh1:recv i( (msg, r, u, c) )h2:clk := max(clk, c)h3:if msg = Req then // Request msg, u=crq1:Q i := priority_insr(Q i, (r, u))rq2:if¬( (,)(,)i t r u< ) thenrq3:send i( r, (Gr, i, u, clk) )rq4:if r ∉ St i thenrq5:Q i := Q i - {(r, u)}endifendifelseh4:if msg = Rel then // Rel msg: only if i ∈ I j rl1:Q i := Q i - {(r, u)}e lseh5:if msg = Gr then // Grant messagegr1:grants_left := grants_left - 1endif // Grendif // Relendif // Reqendwhile// process i can now enter the CScs:doCS// process i exiting the CSex1:∀s ∈ I i : send i( s, (Rel, i, t, clk) )ex2:Remain i := Q iex3:while Remain i≠φdorm1:(r, v) := head(Remain i)rm2:send i( r, (Gr, i, v, clk) )rm3:if r ∉ St i thenrm4:Q i := Q i - {(r, v)}endifrm5:Remain i := tail(Remain i)endwhileendloopFrom the program code, a process i enters the waiting region, w1..w5,chooses a time value t, and tries to gain permission to enter the CS by sending Request (Req) messages to all the members of its request set, R i. Process i's current request to enter is noted in t to be compared against any other requesting processes. Whenever a process i receives a Request message (see h1..h3) from a process j, it inserts j's request timestamp into Q i. Now if i's pending request t is of lower priority (higher time value) than j's then i will immediately send a Grant (Gr) message to j.At this point ( see rq4..rq5), j's timestamp can be deleted from Q i but only if it is not a member of i's status set St i. If i's pending request t is not of lower priority than j's then i will retain j's timestamp in Q i and the Grant message to j will be delayed. Process i will only reach the CS after it has received Grant messages from all the processes in its request set R i(grants_left=0) and its own request timestamp is at the head of Q i. On leaving the CS, a process i enters the exit region, ex1..ex3,and sends Release (Rel) messages to all the processes in its inform set, I i (For a process j I i∈, this will have the effect of removing i's timestamp, see rl1,from Q j). Now, process i has had its turn and can immediately send Grant messages to the processes in Q i(whose requests were delayed). Again, at this point ( see rm3..rm4), j's timestamp can be deleted from Q i but only if it is not a member of i's status set St i.One of the intuitions behind the algorithm is that process i must retain in Q i any timestamp (,)j t j whenever j St i∈since i is being informed that j is wishing to enter the CS, and it need not be the case, from the DF-ISDME information structure conditions above, that i will necessarily make a request on j.3Proof of CorrectnessIn this section, we present proofs for mutual exclusion, deadlock freedom and no individual starvation for DF-ISDME. The form of the latter two proofs is similar to Singhal [8].3.1Preliminary DefinitionsIn this section, we present several definitions to be used in the accompanying proofs of the DF-ISDME algorithm.As discussed previously, For a process i, the status set St i is derived from the inform sets of the processes using the following rule,∀ij:i I j∈↔j St i∈ (1).Propositions which are state predicates of the form at_l where l is a label like cs or ex1hold at a state whenever control is at a location which is infront of the program statement labelled by l.Propositions of the form in_li..j are used to denote that control is at or within a range of locations labelled l l i i ,+1, ..., l j .A timestamp (,)i t i is less than (has higher priority) than a timestamp (,)j t j , written (,)(,)i t j t i j <, when ()()t t t t i j i j i j <∨=∧< holds.The proposition, granted ij means that "process i has been granted permission to enter the CS with respect to process j ." More formally, the meaning of granted ij depends on whether j is a member of i 's inform set, define granted ij as j ∈ I i : (¬sent_rl ij since sent_gr ji ) ∨ j ∈ R i - I i : (¬in_ex1..3i since sent_gr ji ) (2) which says that if j is a member of i 's inform set then i has been granted permission by j whenever i has not yet sent a Release message to j since the last time that j sent i a Grant message, or if j is not a member of i 's inform set (but still in i's request set) then i has been granted permission by j whenever i has not yet entered its exit section (labelled by ex1 to ex3 in the DF-ISDME algorithm)since the last time that j sent i a Grant message.The proposition granted i means that "process i has been granted [full] permission to enter the CS."More formally, granted i ≡ ∀k ∈ R i : granted ik ∧(i, t i ) = head (Q i ) (3), which says that a process i has been granted permission to enter the CS if and only if all processes k which are members of i 's request set have granted their permission and the timestamp (i, t i ) is at the head of i 's priority queue Q i .3.2Mutual ExclusionDF-ISDME Mutual Exclusion Theorem.The information structure conditions ∀∈i i I i : (4),∀⊆i I R i i : (5), and ∀≠ij i j : ()i I j I j i ∈∨∈ ∨i R j R j i ∈∧∈ (6) are sufficient conditions for the DF-ISDME algorithm to guarantee mutual exclusion.Proof.The safety proof will be by induction on the execution sequences of the distributed processes.With respect to the DF-ISDME algorithm, we claim the following formulas are invariant:at cs i _→granted i (7), at cs j _→ granted j (8),granted i j ij ,≠→(,)(,)i t j t i j <(9),and¬∧(__)at cs at cs i j (10). Invariant (7) states that if control for i reaches the location in the algorithm labelled by cs i then i must have been granted permission to enter the CS. Similarly, (8) for j.Invariant (9) states that the only situation in which i can be granted permission by j is when i 's request timestamp has higher priority than j 's request timestamp. Invariant (10) is the mutual exclusionrequirement stating that no two processes i and j can both be in the CS at the same time.Invariance of (7) and (8).For i, the only transition that could affect the truth of (7) is w5⇒cs . Here at cs i _ will be true but from the while-loop transition grants left i _=0 ∧(,)()i t head Q i i = must hold which implies granted i so the invariant still holds. Thus (7) is invariant and so too is (8) for j. oInvariance of (9).For i and j, we will focus on when the antecedent granted ij ,i ≠j becomes true and argue that the consequent is also true. When i 's request is received by j , i 's timestamp will be compared at rq2. The only way a Grant message will be sent to i after rq3 is if the if-statement condition holds which means (,)(,)i t j t i j < holds where u = t j . Thus (9) is invariant.oInvariance of (10) (Mutual Exclusion Requirement).Without loss of generality, the only way (10) can be violated is if i is in the CS (at_cs i holds) and j enters via the transition w cs j j 5⇒.1. Hence, assume that both i and j have entered the CS (at_cs i ∧ at_cs j ) and show that a contradiction will arise.2. From 1. and the invariance of (7) and (8), it follows that granted i ∧ granted j is true; recall from (3) that granted i ≡ ∀k ∈ R i : granted ik ∧(i, t i ) = head (Q i ), and similarly for j.3. Assume that the information structure conditions, (4), (5), and (6), hold, then it follows that i R j ∈∨j R i ∈ which means that at least one of the processes must send a Request message to the other process.4. Say, (without loss of generality) that i asks j then by (7) j must have granted that request,granted ij .5. From 4. the premise of (9) must hold and hence (,)(,)i t j t i j <.6. From 3. and 4. there are two cases: (i) j ∈ I i or (ii) j R I i i ∈−.7. Case 6. (i): here j ∈ I i and then from (1)i St j ∈, and so (,)i t i must be a member of the priority queue, Q j .8. From 7. and from 5. it follows that (,)i t i will be ahead of (,)j t j in the priority queue, Q j which is a contradiction with 2. granted j which states that (,)j t j will be at the head of Q j .9. Case 6. (ii): here j R I i i ∈− (and then from (1)i St j ∉), and to maintain the assumption in 3. itfollows that i I j∈∨()i R j Rj i∈∧∈. So j must ask (send a Request message to) i here in addition to the assumption from 4. that i asks j.10. From 4. and 5. it is still the case that (,)(,)i t j ti j<since granted ij, and in 9. we have argued that in addition j must ask i, but in this case i will not grant j's request since the if-statement transition condition labelled by rq i2is false, so ¬<((,)(,))j t i tj i→¬granted ji, contrapositive of (9). This is in contradiction to 2. granted j and hence granted ji. n3.3Deadlock FreedomDeadlock could occur for a set of processes if they were each involved in a circular wait. A circular wait could occur if each of the processes i in the cycle is blocked at the location labelled by h i1 and is yet to receive a Grant message from the successor process in the cycle and no there are no Grant messages in transit which are destined for any of these processes. Assume, by way of contradiction, that this is the case. Then each process in the circular wait has delayed sending a Grant message to its predecessor process in the cycle. A process i will only defer sending a Grant to a process j if it is in the region w1..w5and (,)(,)i t j ti j<. Thus, to achieve a deadlock, each process in the circular wait must be blocked by a process with a higher priority request which is impossible. Therefore, the algorithm is deadlock-free.3.4No Individual StarvationStarvation occurs when a few processes repeatedly execute their CSs while other processes wait indefinitely in the region w1..w5. Assume, by way of contradiction, that process j has been repeatedly executing its CS while process i has been waiting in the region w1..w5.Given that the information structure conditions, (4), (5), and (6) of the DF-ISDME mutual exclusion theorem hold, then it follows that i R j∈∨j R i∈ which means that at least one of the processes must send a Request message to the other process. Thus, we have the following two cases:Case 1. i R j∈.Process j asks i for permission to enter the CS which if j has priority will result in i sending a Grant message to j.At h2,after j has processed i's Grant message, its next request to execute the CS will get a timestamp lower in priority than the pending request of i. So the next request of j cannot have priority over the pending request of i and therefore i will not send a Grant message to j unless it has executed its CS.Case 2. j R i∈.Process j can repeatedly execute the CS as long as i's request hasn't reached it yet. However, at h2, after j has received i's Request message, j's next request to execute the CS will get a timestamp lower in priority than the pending request of i. Therefore, j will send a Grant message to i before its next execution of the CS.Therefore, contrary to our assumption a process cannot repeatedly execute its CS while other processes are waiting for their turn to execute the CS. Hence there is no individual starvation.4PerformanceIn this section, we consider the optimal conditions for message performance and the synchronisation delay for the DF-ISDME algorithm.4.1Message PerformanceThe mean message performance M is the average number of messages required by a single process per execution of the CS. From Figure 2, if there is a solid arc from a process i to a process j then three messages will be required along the arc per CS execution, that is a Request message will be sent to j, a Grant message will be received from j,and a Release message will be sent from i to j, since j I i∈which satisfies the inform-set part of the information structure condition (6). From Figure 2, if there is a dashed arc from a process i to a process j then two messages will be required along the arc per CS execution, that is a Request message will be sent to j, and a Grant message will be received from j,since j R i∈which satisfies the request-set part of the information structure condition (6). Let a represent the number of dashed arcs between any pair of distinct processes i and j. Let b represent the number of solid arcs between any pair of distinct processes i and j;self-loop solid arcs are not counted2. Therefore, the mean message performance M for a DF-ISDME algorithm is given by M a b n=+()23 (11).To find the optimal mean message performance, we need to build the minimum request and inform sets that will satisfy the DF-ISDME mutual exclusion theorem. We note that to satisfy the theorem, it is only necessary to have a single solid arc either from i to j or from j to i. Thus, in abstract, we can view any optimal information structure as an undirected graph consisting of either one single solid arc (in some direction) or consisting of a dashed arc (which2Since any messages that a process sends to itself need not incur a transmission cost in a practical implementation.represents the pair of directed dashed arcs from i to j and from j to i ). Hence if a and b have their meaning as before with b restricted to only count one occurrence of a solid arc between processes i and j,then the following relationship holds:n n a b ()()−=+122 (12). We note that n n ()−12is the number of edges in a graph where each node has one edge to every other node in the graph. Now using (12) and substituting for a in the expression for message performance (11) above, we obtain M n b n =−−21() with 0≤≤b n n ()−12 (13).Now, M is smallest when b =n n ()−1, and therefore M n =−321() which is equivalent to the DF-Maekawa algorithm [8]. Conversely, M is largest when b =0, and therefore M n =−21() which is equivalent to the Ricart-Agrawala algorithm [6].Thus the optimal message performance of DF-ISDME lies along a continuum from DF-Maekawa on the one hand to Ricart-Agrawala on the other depending on b the number of edges which are single solid arcs in the information structure.4.2Synchronisation DelayThe synchronisation delay D is the maximum number of sequential message propagations from one process to another between successive executions of the CS. It is assumed that the next process to enter the critical section is blocked and only waiting for the process in the CS to exit. For the DF-ISDME algorithm the delay is D =1 since the next process j to enter is either waiting to receive a Release message to remove the timestamp ahead of its own request in Q j or (,)j t j is at the head of Q j and it is waiting to receive a Grant message to proceed. The DF-ISDME algorithm has twice the throughput of the Maekawa [3] algorithm which has a delay of D =2. The DF-ISDME algorithm retains the D =1 delay of the DF-Maekawa algorithm [8].5ApplicationIn this section, we show the potential application of the DF-ISDME algorithm. As an application example, consider that telecommunication network topologies may sometimes span administrative management domains such as for international calls between countries. Further suppose that half of the processes are colocated in one domain and half in the other domain. Since these management domains are managed by separate organisations, it may be the case that strictly optimal topologies may not be cost-effective or achievable. For example, although an M n =−321/() topology is the lower bound for DF-ISDME and equivalent to DF-Maekawa [8], it achieves this average performance for a pair of processes by asking one of them to send threemessages and the other none, yielding an average of 32 messages per process - it also assumes that costs can be amortised across management domains. Now,if one of the processes must originate a connection to a process in the other management domain then the originating process might need to hold the call open for the duration of the execution of its CS because it needs to send a Release message on exiting the CS. It may be much more cost-effective to allow processes that communicate between management domains to send 2 messages each per process prior to CS entry with no further communication required on CS exit.6DiscussionThe class of information structures which satisfies the DF-ISDME mutual exclusion theorem is a subset of the class of information structures which satisfies the ISDME mutual exclusion theorem of Sanders [7].However, the class of DF-ISDME information structures is a superset of the class of information structures admitted by DF-Maekawa [8]. The DF-ISDME algorithm has a synchronisation delay of D =1 which is twice as fast as the Maekawa algorithm [3] which has a delay of D =2. The DF-ISDME algorithm still retains the D =1 delay of the DF-Maekawa algorithm [8]. The DF-ISDME algorithm may be viewed as representing a continuum from DF-Maekawa on the one hand to Ricart-Agrawala [6] on the other. As Singhal [8] has shown for the DF-Maekawa algorithm (and hence for the lower bound of DF-ISDME), the message performance of M n =−321() is better than the worst case 5n of the Maekawa algorithm for n ≤17 under situations of heavy demand for the CS.The DF-ISDME algorithm allows deadlock-free solutions to apply to a wider class of information structure topologies than the DF-Maekawa algorithm.The move from deadlock-prone Maekawa [3] to deadlock-free DF-ISDME means that the message performance has gone from O (n ) to O (n ). The deadlock-freedom has been achieved at the expense of increased communication costs. The information structure approach used here is interesting because it provides an abstract view of an entire class of algorithms. We observe that a deadlock-free solution not requiring deadlock-recovery is impossible for certain information structures which satisfy the ISDME mutual exclusion theorem of Sanders [7](like Maekawa [3]) but do not satisfy the DF-ISDME theorem presented here.One of the motivations behind the work in this paper is to better understand the impact of global system requirements such as deadlock-freedom on the knowledge (and hence communication) required by the processes in a distributed system. Our current research work is using a knowledge-theoretic。
