Study of Received Signal Strength Indication in
RFRSSISniffer

IntroductionThe ability to monitor the received signal strength in a radio receiver is a valuable development and diagnostic tool for the engineer. In an automotive application the ablility to monitor this received signal strength indicator (RSSI) value represents what a radio receiver will experience in service, including the effects related to antenna and mounting location. The article describes a simple method to re-configure the Atmel® ATA5830N device, utilizing its Flash program capability, to create an RSSI monitoring tool for labratory and in-vehicle use.The ATA5830N UHF transceiver chip incorporates a high-performance UHF transceiver and a low-power 8-bit AVR®microcontroller on a single die. Figure 1 shows a simplified block diagram of the ATA5830N device. Included in the device is 6KB of Flash memory available to the end user. This article describes an application that utilizes this Flash memory space to develop an application for an RSSI monitor that generates universal synchronous/asynchronous receiver transmitter- (USART-) formatted messages containing RSSI data. From an operational perspective this application lends itself well to several common RF engineering tasks such as: a) RF environment analysis, b) performance tuning of theFigure 1. ATA5830N Block Diagramreceiver section, c) RF component selection and d) antenna performance evaluation.Flash-based RSSI ApplicationR SSI data is a critical radio reception metric that reflects the level of RF signal energy at a given frequency channel and is useful in evaluating an RF environment. The Flash memory application uses the internal RSSI measuring function of the chip and communicates this value using a general-purpose I/O pin using standard USART communication protocol timing. This article describes how a Flash program application is implemented and demonstrates the flexibility of the internal AVR controller. The Flash application provides a small flexible RSSI measurement tool that can be easily and quickly configured to operate across a wide range of frequencies, providing a simple way to measure RSSI.The software for this demo was developed using the ATAK51002-V1 evaluation kit. The application operates with no external inputs required other than 5V DC power and the RF signal source. The desired radio parameters, such as frequency and intermediate frequency bandwidth (IFBW), are programmed into the part using the EEPROM configuration file. The user selects these values by using an Excel spreadsheet tool that automatically generates the EEPROM file. Once these values are programmed into the EEPROM, the application of power will automatically initiate the self-configuration and execution of the Flash application program. It begins measuring and outputting the 8-bit RSSI data values on pin 17 (PC3) of the device. USART communication parameters are 38400 Baud, 8 data bits,1 start bit and no parity bit (38400, 8-1-N). Each data byte output requires about 260μs to transmit and occurs about every 50ms. The output data is at logic value voltage levels (about 0V to 5V) and, while not compliant with RS-232 standards, most PCs have no problem in receiving and displaying this data stream using a terminal program.RSSI Measurement DetailsReceived signal strength indicator (RSSI) is a measurement of the power present in a received radio signal. In theATA5830N chip, this function is built into the receiver’s digital signal processing (Rx DSP) section and occurs completely in the digital signal domain, allowing for high relative and absolute RSSI accuracy.In this application, RSSI values are returned as 8-bit values and the signal power at the matched 50Ω antenna input can be calculated in dBm as:RF Power In (dBm) = RSSI/2 – 155 (154 in 868-928MHzband)The ATA5830N datasheet notes the following RSSI measurement specifications:• Absolute RSSI accuracy ± 5.5dBm • Relative RSSI accuracy ± 1dB •RSSI resolution 0.5dBThe typical RSSI range is a function of the IFBW selected:• IFBW = 25kHz >>> RSSI = -115dBm to -25dBm • IFBW = 80kHz >>> RSSI = -110dBm to -25dBm • IFBW = 165kHz >>> RSSI = -105dBm to -25dBm •IFBW = 366kHz >>> RSSI = -100dBm to -25dBmSoftware Operational FlowOn power-up and after the hardware-generated power-on reset is complete, the AVR controller will execute its main() function in ROM, where the EEPROM configuration settings are loaded and checked. This EEPROM configuration defines all operational parameters of the device, including that a Flash application program is present. When this EEPROM setting is encountered, the application flow jumps to the Flash main(), and the application flow begins. The Flash main() function can be very simple since the ROM software functions will perform most of the work. In this application, the Flash program function loops indefinitely, first requesting ROM-code-based RSSI measurements and then calling Flash code functions that format and output the data. The following is the Flash program loop that drives this application:Operation and UseHardware PlatformThe ATA5830N can be used in several frequency bands:310MHz to 318MHz, 418MHz to 477MHz and 836MHzto 928MHz, operating from a single crystal. The highly integrated radio architecture is optimized for minimal external part count. See Figure 2 for the schematic of a low-band Flash-based application such as the one described in this article.SetupThe only required external signals are a +5V power supply and the RF signal input. The reference design included inthe ATAK51002-V1 evaluation kit consumes about 9mA when running this application, which is sufficiently low to enable battery-powered use. Once the reference design is powered up, the ATA5830N device must be awakened by momentarily connecting any of the “npwron" pins (15, 16, 17, 18, 19 and 29) to ground or the “pwron” pin to +5V. After the part is awake and active, no other input is required and the RSSI data will be available at PC3 pin 17.RF ConsiderationsIn addition to the EEPROM configuration settings, the hardware in the RF path must be optimized or “matched” to the specific frequency being used. The default configuration frequency for the ATAK51002-V1 evaluation kit is 433.9MHz, so the application kit hardware is shipped with this hardware installed. If another frequency is selected, the matching component values in the RF signal path need to be changed. The ATA5830N device includes two separate LNA inputs, one for low-band (315MHz and 433MHz) and one for high-band (869MHz to 902MHz) operation. These LNA inputs are provided since the chip is capable of multi-band operation and these separate ports provide optimum performance matching for each frequency range. The hardware configuration as shipped utilizes the low-band input port. The hardware must be modified accordingly to measure a high-band frequency.A list of component values for several common radio frequency bands is available upon request and included in the evaluation kit. Installation of the corresponding hardware component values is required for optimal performance at the desired frequency.PC ConnectionData is output at pin 17 (PC3), which can be accessed at one of the I/O pins on the hardware evaluation board. This signal can be connected directly to pin 2 of a PC-connected RS-232 port. While the voltage level is not compliant with RS-232 standards, most PCs will successfully receive this data. The data can then be displayed using a terminal emulation program such as “Realterm”, available at no cost at /.for(;;){_WDR;ATA_makeGlobalSystemFlags(); // ROM code check and execution of mode changesRDCR |= (1 << RQSS); // Register bit set to request RSSI measurementrssi=RSSI; // Store the RSSI register value in SRAM variableif (rssicnt==100){ //Every 100th reading output data to FLASH program (~50mS) RSSI_flash(); // FLASH program to initialize required timersRSSI_TransmitValue(rssi); // FLASH program to format and output datawhile ((T4CR & (1<<T4ENA))); // Wait for data transmission to completePORTC &= ~(1<<PORTC3); // Set output port valueTMCR = (TMCR & 0xF8) | SSI_PC3_OUTPUT; // Set the modulator MUX to output at PORTCATA_timer4Close(); // Close the timer used by the FLASH functions}rssicnt++; // increment counter}Figure 2. ATA5830N Flash Application SchematicRF Power InputATA5830N RSSI Response-120-110-100-90-80-70-60-50-40-30-20-10R S S I V a l u e O u t p u t-20-30-40-50-60-70-80-90-100-110-120Figure 3. Sample Data Collected Using Flash ApplicationData CollectedFigure 3 shows sample RSSI data collected using the described Flash application with the ATA5830N chipconfigured to operate at a center frequency of 314.9MHz with an IFBW of 165kHz.Summary and ResultsThis article highlights the capability and flexibility of the ATA5830N radio transceiver. By generating a program that runs in the Flash memory space, and leveraging the availableROM-based functions, end users can customize the chip for their individual needs. The described application, for example, reports measured RSSI values every 50ms using standard USART timing. This tool would be useful in RF environment analysis such as choosing an operating band or frequency. While not quite as easy to program as a commercial spectrum analyzer, the tool does provide a means to test the RF energy content of a specific frequency and measurement bandwidth.Perhaps the most useful application for this tool is theoptimization of external components for an automotive car access system using the ATA5780N or ATA5830N device. Traditional fine-tuning of a receiver requires a method to extract received data or RSSI, and is typically done with an external microcontroller. Using this application, the external microcontroller and its programming can be eliminated—all that is needed is a PC.External ReferencesThe software and documentation, incl. an application note with even greater detail for this application, is available by contacting ********************.The Flash software program was generated using Atmel Studio 6, IAR Embedded Workbench for AVR and JTAGICE mkII.。
无线传感网络煤矿井下人员定位系统设计

1 系统架构
煤矿井下人员定位系统由 3 大部分组成: 井上 监控中心、井下定位基站、人员定位终端设备。井上
基金项目: 河南省科技攻关计划资助项目 ( 102300410410 ) ; 河南省 高等学校青年骨干教师资助计划( 2009GGJS - 122 ) ; 河南省教育厅 自然科学研究计划资助项目( 2010B510016)
3结语
基于无线传感网络的煤矿井下人员定位系统在 河南省新密市景岗煤矿进行了井下测试,该定位系 统能够及时、准确的将井下各个区域人员的动态情
况及矿井的环境参数反映到地面监控中心的计算机 系统,使管理人员能够随时掌握井下人员的分布情 况和每个矿工的运动轨迹,系统定位精度在 1 m 以 内。该系统还适用于矿难救援,救援人员也可根据 井下人员定位系统所提供的数据、图形,迅速了解有 关人员的位置情况,及时采取相应的救援措施,提高 应急救援工作的效率,大大提高煤矿企业的安全生 产和管理水平。
〔4〕 李文江,陈 宇,刘晓平,等. 基于 ZigBee 技术的煤矿 井下人员定位系统设计〔J〕. 成都大学学报,2008,27 ( 4) : 322 - 325.
TDOA中的修正牛顿及泰勒级数方法

TDOA中的修正牛顿及泰勒级数方法房嘉奇;冯大政;李进【摘要】在多站无源时差定位系统模型下,泰勒级数算法和牛顿算法在较差初始值条件下容易出现迭代发散问题.针对这一问题,提出了基于修正泰勒级数法和牛顿法的时差定位算法.该方法对于较差初始值引起的病态海森矩阵,运用正则化理论中的吉洪诺夫法或衰减奇异值分解法进行修正,其中控制海森矩阵修正量的重要的正则化参数由著名的L曲线理论确定.实验结果证明:相对于原泰勒级数及牛顿算法,经过改进后的算法对于较差的初始值,具有较高的概率使迭代算法的解稳健地收敛到目标的真实位置,并拥有较强的能力移除局部最小值;相对于时差定位模型下的一些广泛应用的线性解法,也成为闭式解法,在低信噪比环境下具有更高的定位精度.【期刊名称】《西安电子科技大学学报(自然科学版)》【年(卷),期】2016(043)006【总页数】7页(P27-33)【关键词】无源定位;时差定位;修正泰勒级数算法;修正牛顿算法;正则化算法【作者】房嘉奇;冯大政;李进【作者单位】西安电子科技大学雷达信号处理国家重点实验室,陕西西安 710071;西安电子科技大学雷达信号处理国家重点实验室,陕西西安 710071;西安电子科技大学雷达信号处理国家重点实验室,陕西西安 710071【正文语种】中文【中图分类】TN97多站无源定位技术是电子侦查、电子对抗的一个重要组成部分,被广泛应用于雷达、导航、监督、无线通信、无线传感器网络等领域.无源定位技术在测量参数方面可以分成接收信号强度(Received Signal Strength,RSS)、到达时间(Time Of Arrival,TOA)、到达角度(Angle Of Arrival,AOA)、到达时间差(Time Difference Of Arrival,TDOA)、到达频差(Frequency Difference Of Arrival,FDOA)等方法.笔者主要研究的是到达时间差方法,也称为时差定位技术.在三维空间中,该技术利用目标辐射源到两个接收基站的到达时间差信息确定一个以两基站为焦点的双曲面,通过多个基站的时差测量值确定多个双曲面,其交点即为目标位置.到达时间差目标位置估计方法有以下优点: 接收机上通常只需安装单个天线;接收机与接收机之间不需要进行时间同步;定位精度较高.由于基于到达时间差的定位问题高度非线性非凸特征,并不是一个能够简单求解的问题.到达时间差定位方法按照类型可以分为线性化方法和非线性化方法.目前大多数研究主要侧重于线性化方法(闭式解方法)[1-4],这些方法通过线性化到达时间差的非线性方程组来求解目标位置,它们可被归类为线性最小二乘(Least Squares,LS)、两次加权最小二乘(Two-Stage Weighted Least Squares, TSWLS) 和多维尺度分析(MultiDimensional Scaling analysis,MDS) 等.线性化方法的特点是计算量小,在信噪比较高时定位精度能够达到克拉美罗界(Cramer-Rao Lower Bound, CRLB),但线性化非线性方程组必然会带来性能的损失.因此,所有的线性化算法都会受到门槛效应的影响,即在噪声功率大到一定界限后定位精度误差逐渐偏离克拉美罗界.针对这一缺点,线性化算法所求得的解可以被作为非线性迭代算法的初值,从而去获取一个更精确的位置解.当前主要的迭代算法有泰勒级数法(Taylor-Series, TS)[5]以及牛顿法(NewTon, NT)[6]两种,但是迭代算法的一个重要弊端在于,当迭代初始值较差时(由线性化算法的解在大噪声环境下产生的较大偏差引起),迭代算法很容易发散.笔者将研究的重点放在解决迭代算法中最关键的收敛性问题上,利用最大似然估计(Maximum Likelihood, ML)确定目标函数,然后采用牛顿法进行求解.牛顿法是泰勒展开式的二阶近似,它忽略了泰勒展开式中的高阶项,然而在高度非线性的时差定位问题中,较差的初始值会导致高阶项对解的贡献变得比较重要,因而忽略高阶项很容易致使迭代发散.笔者提出了修正牛顿算法(Modified NewTon,MNT)用于克服该问题,对于由较差初值引起的病态海森矩阵,运用正则化理论中常用的吉洪诺夫(TIkhonov,TI)法或衰减奇异值分解法(Damped Singular Value Decomposition, DSVD)[7]将该病态矩阵转化为良态矩阵,其中控制海森矩阵修正量的重要的正则化参数由著名的L曲线理论[8]确定,并将其同另一种确定正则化参数的方法——广义交叉检验法(Generalized Cross Validation, GCV)进行对比.需要注意的是,泰勒级数算法相比较于牛顿算法只用到了一阶泰勒展开,因此正则化理论也可以应用到泰勒级数算法中.笔者同时提出了修正泰勒级数法(Modified Taylor-Series, MTS)对原泰勒级数算法进行改进.经过改进的修正泰勒级数法、修正牛顿算法同改进前的算法相比,在收敛性上具有稳定性,具有较好的移除局部最小值的能力,能够稳健地收敛到全局最优点; 同改进前算法和线性化算法相比,在低信噪比环境下具有更高的定位精度.在多站无源时差定位系统下,假设待测目标辐射源位置x=[x,y,z]T,第i个已知接收基站的位置 si= [xi,yi,zi]T,i=1,…,M,M为参与定位的基站数目,在三维空间内至少需要4个不在同一平面之内的基站来确定目标的位置.目标和第i个基站之间的距离为其中,·表示2范数.选定中心基站为第1个基站,则基站1和基站i之间的时差信息测量值为其中,c为电磁波传播速度,ti1为基站1与基站i之间的到达时间差测量值,di1为与测量时差信息对应的测量距离差(Range Difference Of Arrival, RDOA),ni1 c为到达时间差测量误差.用测量距离差来代替到达时间差.将到达时间差测量等式方程组采用向量形式表达,即其中,d=[d21,d31,…,dM1]T,r=[r1,r2,…,rM]T,n=[n21,n31,…,nM1]T.G为第1列均为 -1 的 (M- 1)×1 的列向量与维数为 (M-1) 的单位矩阵所合并的 (M-1)× M的矩阵,G= [-1M-1,IM-1].噪声n为零均值、协方差矩阵E(n nT)= Qt的向量.根据最大似然估计,目标函数可写为牛顿法和泰勒级数法的本质相同,泰勒级数法只比牛顿法少用到了泰勒展开式中的二阶展开项.因此,首先研究牛顿法,去除二阶项即可得到泰勒级数法.牛顿法是一种经典的迭代算法,在每次迭代中通过二阶泰勒近似来改进估计值.令迭代次数k=1,2,…,n,每次迭代后新的更新的估计值xk+1可表示为其中,梯度向量和海森矩阵f(xk)和2f(xk)可写成其中,式(10)中的⊗表示Kronecker积,vec(·)表示将矩阵沿列向量化.文献[9-10]中分析了海森矩阵病态的原因并提出了正则化理论解决办法,在此基础上,笔者不仅仅对牛顿法,也对泰勒级数法进行了改进,并同时对正则化的方法以及正则化参数的选择进行了更深入的研究.令 A= 2f(x),b= -f(x),矩阵A奇异值分解为其中,U和V为单位正交矩阵,UTU=VTV=In,Σ=diag(σ1,σ2,…,σn),σi 和向量ui,vi为特征值和特征向量.由式(5)得到每次迭代的改变量式(7)中的第2项即式(10)为二阶项.若忽略二阶项,牛顿法退化为泰勒级数法,因此只需将式(7)中第2项忽略,其他计算步骤不变,可在原泰勒级数法的基础上得到修正的泰勒级数法.其表达式可与牛顿法写成相同的形式,即式(5)~(7),只需将式(7)中的第2项删去即可.3.1 正则化方法正则化理论是一种解决不适定问题的有效方法,它用一种与原不适定问题相邻近的适定问题的解去逼近原问题的解.常用的正则化方法有吉洪诺夫正则化法、截断奇异值分解法(Truncated Singular Value Decomposition,TSVD)和衰减奇异值分解法等.吉洪诺夫法正则化等价于求解式(13)在二次约束下的惟一最小二乘解,即将该问题转化为求解下述二次优化问题:经过修正后的修正量为经过修正后的改变量ΔxTI,其实质相当于在原参量前加入了滤波器fi.特征值越小,滤波器fi也越小,其小特征值对应项的贡献也越小.其中λ为正则化参数,用来控制式(14)中前项(数据能量)与后项(稳定能量)之间的比例.截断奇异值分解方法仅采用矩阵A的大特征值对应的特征空间来构造方程组的解,舍弃了小特征值对应的特征向量.假设A有m个大特征值,则选取m作为截断参数.满足条件σ1,σ2,…,σm≥ λ的特征值保留,舍弃σ1,σ2,…,σm< λ的特征值.因此,采用截断奇异值分解法得到的修正量可以写为衰减奇异值法就是常用的对角加载法,它是一种常用的稳健技术,可以有效地解决病态矩阵求逆问题.对式(13)直接应用对角加载,得到这3种算法中截断奇异值分解法主要应用于区分信号和噪声空间的多特征值矩阵,而对于到达时间差目标定位问题,要求的海森矩阵在不考虑速度及基站误差的情况下维数很小,因此截断奇异值分解法这种直接滤除小特征值的方法对于本问题不适用.对于吉洪诺夫法和衰减奇异值分解法两种方法来说,吉洪诺夫方法适用于秩亏情况,而衰减奇异值分解法更适用于病态矩阵情况.3.2 正则化参数上节提到的3种方法的性能都十分依赖正则化参数λ的选择.正则化参数的选择方法有L曲线法和广义交叉检验法.L曲线理论将残差范数A Δx-b和正则化范数Δx的和作为变量取对数画图,通过对比结果确定正则化参数.该方法所绘制的尺度图形中会出现一条明显的L曲线.将曲线中的最大曲率作为其拐点,通过寻找该拐点求得与之相对应的λ.令ρ= lg A Δx-b,θ= lg Δx,该曲率定义为广义交叉检验法也是一种常用的确定正则化参数λ的方法,它的原理是假定将任意的观测值bi从原观测序列b中去除,在此时通过剩余观测值求得的正则化解能够较好地预测b中被去掉的这个观测值bi.它等效为求解下面函数的最小值问题: 矩阵Al满足关系式Δx=Alb.广义交叉检验法在理论上能够选择最优的参数λ,但某些时候广义交叉检验法函数的变化趋势非常平缓,这时很难找到它的最小值.而相比较而言,L曲线法能够快速准确地找到最佳正则化参数.因此,笔者采用L曲线法作为确定正则化参数的方法.对一些值得注意的问题进行如下解释说明:(1) 同泰勒级数算法相比,牛顿算法因为存在式(7)中的第2项,能够提供一个较为精确的海森矩阵,因此具有较高的定位精度.然而当初值较差时,牛顿算法中的海森矩阵可能负定导致迭代发散.对于泰勒级数算法,因为式(7)中的第1项一直为对称正定矩阵,因此具有较高的收敛概率,但因海森矩阵表达的不完全,其定位结果可能陷入局部最小值中.笔者提出的修正牛顿算法和修正泰勒级数算法继承了原算法的特点,相比于修正泰勒级数算法,修正牛顿算法具有较高的定位精度和较差的收敛性.(2) 众所周知,迭代算法需要一个初值,它完全随机选取是不合适的.在实际应用中,闭合式算法的解通常被作为初值带入迭代算法.笔者采用著名的两次加权最小二乘算法来求得初值.在噪声较大时,两次加权最小二乘算法的解可能存在较大误差,此时多维尺度分析算法被用来取代两次加权最小二乘算法以获得一个误差相对较小的初值.(3) 当目标函数值f(xk+1)>f(xk)时,认为迭代的过程中出现了发散的现象;反之,则认为迭代收敛,继续观察,并设定迭代的终止条件为梯度f(xk)< ε.由于时差定位问题的高度非线性特征,因此有时候尽管迭代收敛,但其结果可能陷入局部最小值中.当使用闭合式算法的解作为迭代算法的初值时,若迭代的最终结果为全局最优解,则迭代只需要非常少的次数就可以收敛; 若最终结果为局部最小值,则需要多次迭代才能收敛.在这里需要设定一个迭代次数的门限用来移除局部最小值.如果该门限设置较为宽松,则少量的局部最小解仍然存在于全局最优解中,致使平均值变差; 反之,如果该门限设置较严,则许多全局最优解将被遗弃,算法实用性降低.笔者提出的正则化算法通过对海森矩阵的修正,在实际上会减慢目标函数的收敛速度,对于全局最优解影响很小.而对于局部最小解来说,由于其本身收敛速度就较慢,再经过文中算法的减缓,收敛速度进一步降低,很容易就能够超出所设置的迭代门限.相对于文献[6]中所设置的较严格的两次迭代门限(超过两次迭代的结果都当做局部最小值被移除,会导致很多全局最优解的遗失),笔者所设置的门限为较为宽松的5次.由于笔者提出的算法具有较强的辨识局部最小值的能力,因此在保证算法实用性的同时,又能够获得较好的性能.实验中假设5个基站的位置分别为 (300 m,100 m,150 m),(400 m,150 m,100 m),(300 m,500 m,200 m),(350 m,200 m,100 m),(-100 m,-100 m,-100 m),设置基站1为中心基站,近距离目标和远距离目标位置分别为(280 m,325 m,275 m) 或 (2 800 m,3 250 m,2 750 m).目标的定位精度以均方误差(Root Mean Square Error, RMSE)形式表示.实验中的测量距离差为零均值,协方差矩阵σ2 R 的高斯噪声,σ2 为时差测量中噪声的功率,R为对角线元素为1而其余元素为0.5的矩阵,设置迭代次数门限为5.实验为 5 000次蒙特卡罗实验的平均数据.图1和图2描述了近距离和远距离目标情况下泰勒级数法、牛顿法、修正泰勒级数法和修正牛顿法的收敛概率值.从图中可以看到,根据说明(1)中的解释,泰勒级数法、修正泰勒级数算法在收敛性上相比于牛顿法,修正牛顿算法的更好.在图1中,泰勒级数法和牛顿算法随着噪声的变大,很容易导致迭代发散,而笔者所提出的修正泰勒级数法和修正牛顿算法具有较强的性能来保证迭代的收敛.在噪声较大时,收敛概率可以提高大概10%.在图2中,泰勒级数法、修正泰勒级数法和修正牛顿算法都具有较好的收敛概率,只有牛顿法的收敛性较差.图3和图4分别展现了近距离和远距离目标情况下泰勒级数法、牛顿法、修正泰勒级数法和修正牛顿算法的定位精度估计,同时和两种经典的闭合式算法两次加权最小二乘和多维尺度分析进行比较.从图3可以看到,所有的算法在高信噪比时都能够达到克拉美罗界.随着噪声的提升,闭合式算法两次加权最小二乘、多维尺度分析受门槛效应的作用,所求的位置解误差逐渐变大; 泰勒级数法和牛顿算法的定位精度也严重地偏离了克拉美罗界,这是因为结果中存在的局部最小值大大提升了平均均方误差估计值.笔者提出的修正泰勒级数法、修正牛顿算法相比于其他算法在大噪声环境下具有较高的定位精度,从图中可以注意到,修正泰勒级数算法的定位精度相比于多维尺度分析算法的略差,这是因为在实验中设置的迭代次数门限较为宽松,致使结果中依然存在少量的局部最小值从而拉高了平均估计精度.门限选取越严格,修正泰勒级数法的估计精度越趋近于修正牛顿算法.在图4中可以看到,修正泰勒级数法和修正牛顿算法的定位精度优于其他算法的,由于式(7)中的第2项的值在远距离目标情况下会变得很小,因此笔者提出的两种算法结果趋于一致.定位精度在噪声非常大时略低于克拉美罗界,这是因为噪声过大时的估计不再是无偏估计的.图5给出了修正牛顿算法中的两种正则化算法——吉洪诺夫法、衰减奇异值分解法的比较结果,实验从均方误差和收敛概率两方面分别验证了算法的性能.由于初值由闭合式算法给出,相比于随机给出的初值更为准确.从图中可以看出,在定位精度方面,两种方法几乎相同;在收敛概率方面,吉洪诺夫算法的收敛性要略好于衰减奇异值分解算法的.图6给出了正则化参数选择的两种方法——L曲线和广义交叉检验法,再结合文中的两种正则化方法(吉洪诺夫法、衰减奇异值分解法),产生4种算法组合.该实验固定到达时间差测量噪声为零均值、方差 25/c2 的高斯噪声.因为实验中选取的噪声功率较小,因此采用闭合式算法的定位精度本身就很高,再经过迭代算法其性能改善不大.在迭代算法搜索λ的过程中,情况较好时广义交叉检验法和L曲线法所需时间步骤相同; 情况较差时广义交叉检验算法寻找参数λ的过程依然过于缓慢,需要很多次迭代才能寻找出参数λ,有时候甚至需要几十次迭代,而L曲线法相比则显得更加高效稳定.因此,笔者将L曲线法作为参数λ的选择方法.对到达时间差定位问题,笔者在原迭代算法基础上提出了修正泰勒级数法以及修正牛顿法,运用正则化理论中的吉洪诺夫技术修正病态海森矩阵,解决了迭代方法中关键的收敛性问题.同原方法相比,经过改进的修正泰勒级数法、修正牛顿算法能够更加稳健地收敛到全局最优解; 与两次加权最小二乘、多维尺度分析等线性算法相比,尽管由于迭代算法的特性使其计算量相对较大,但在低信噪比环境中定位误差更接近于克拉美罗界.文中算法的核心思想在于对病态海森矩阵的正则化处理,此算法可用于多种观测模型,如到达时间、到达角度等.当目标运动时,此算法也能够结合到达频差方程组求解目标的位置及速度,具有良好的实用价值和广泛的适用范围.【相关文献】[1] WANG Y, HO K C. TDOA Source Localization in the Presence of Synchronization Clock Bias and Sensor Poition Erors[J]. IEEE Transactions on Signal Processing, 2013,61(18): 4532-4544.[2]WEI H W, PENG R, WAN Q, et al. Multidimensional Scaling Analysis for Passive Moving Target Localization with TDOA and FDOA Measurements[J]. IEEE Transactions on Signal Processing, 2010, 58(3): 1677-1688.[3]LIN L, SO H C, CHAN F K W, et al. A New Constrained Weighted Least Squares Algorithm for TDOA-based Localization[J]. Signal Processing, 2013, 93(11): 2872-2878.[4]朱国辉, 冯大政, 周延. 一种利用多运动接收站的时差定位算法[J]. 西安电子科技大学学报, 2015, 42(2): 35-39.ZHU Guohui, FENG Dazheng, ZHOU Yan. New TDOA Localization Algorithm Using Multiple Moving Receivers[J]. Journal of Xidian University, 2015, 42(2): 35-39.[5]KOVAVISARUCH L, HO K C. Modified Taylor-series Method for Source and Receiver Localization Using TDOA Measurements with Erroneous ReceiverPositions[C]//Proceedings of the IEEE International Symposium on Circuits and Systems: 3. Piscataway: IEEE, 2005: 2295-2298.[6]YU H, HUANG G, GAO J, et al. An Efficient Constrained Weighted Least Squares Algorithm for Moving Source Location Using TDOA and FDOA Measurements[J]. IEEE Transactions on Wireless Communications, 2012, 11(1): 44-47.[7]HANSEN P C. Regularization Tools: a Matlab Package for Analysis and Solution of Discrete Ill-posed Problems[J]. Numerical Algorithms, 1994, 6(1): 1-35.[8]HANSEN P C, JENSEN T K, RODRIGUEZ G. An Adaptive Pruning Algorithm for the Discrete L-curve Criterion[J]. Journal of Computational and Applied Mathematics, 2007, 198(2): 483-492.[9]房嘉奇, 冯大政, 李进. 稳健收敛的时差频差定位技术[J]. 电子与信息学报, 2015, 37(4):798-803. FANG Jiaqi, FENG Dazheng, LI Jin. A Robustly Convergent Algorithm for Source Localization Using TDOA and FDOA[J]. Journal of Electronics & Information Technology, 2015, 37(4): 798-803.[10]房嘉奇, 冯大政, 李进. 存在基站误差的稳健时差定位算法[J]. 系统工程与电子技术, 2015,37(5):998-1003.FANG Jiaqi, FENG Dazheng, LI Jin. Robust Source Location Algorithm Using TDOA in the Presence of Sensor Position Errors[J]. Systems Engineering and Electronics, 2015, 37(5): 998-1003.。
基于到达时间差法的震源定位研究与实现

摘要摘要基于到达时间差法的震源定位研究与实现当前,震源定位的应用十分广泛,涉及到微震监测、岩体破裂、爆破位置确定、管道裂纹定位以及煤矿安全等领域,若能预先掌握震源位置信息,则可以避免这些突发情况带来的灾害,进而减少损失。
到达时间差法是一种基于时延估计的定位模型,常用来确定目标的位置。
该模型具有定位准确等特点,在一些工程领域中大量应用。
本文以地震动信号为研究对象,探讨震源定位的问题。
从地震动信号特征分析、信号的预处理和时延估计、震源定位及位置修正等几方面进行研究,具体内容如下:由于大地介质成分复杂,我们首先通过经验模态分解和Hilbert变换对振动信号进行处理,得出不同的Hilbert谱,并基于Hilbert谱对地震动信号的时、频域以及能量特性进行分析,对比不同情况下信号的波形及频谱,进而讨论地震动信号的衰减规律。
比较几种常见的小波基函数和阈值估计方法,然后利用小波阈值方法对振动信号的背景噪声进行消噪处理。
对于信噪比较低时,互相关方法很难提取到准确的时延估计问题,采用一种最大似然估计窗函数的广义互相关方法进行时延估计,并实验验证该方法的有效性。
针对经典Chan定位算法得到较差定位结果的情况下,牛顿优化方法容易发散导致算法失效这一问题,提出一种修正特征值的方法将病态矩阵正定化,通过引入步长因子来提高迭代速度,使每次迭代沿下降方向的同时尽快收敛。
通过实测数据验证,改进后的方法可避免初始值偏差大导致迭代发散的问题,并利用均方差对Chan算法和本文的方法进行定位性能比较。
完成了多传感器数据采集系统的设计,包括硬件采集和上位机软件的编写两部分。
计算了试验场地的波速,设计了不同情况下的多组震源定位实验,对定位结果进行讨论,最后分析可能引起定位偏差的原因。
关键词:时延估计,时频分析,牛顿迭代,数据采集,震源定位I吉林大学硕士学位论文II AbstractResearch and Implementation of Vibration Source Localization Based on TDOAMeasurementAt present, the application of vibration source localization is very extensive, involving the microseismic monitoring, rock rupture, blasting position determination, pipeline crack localization and coal mine safety and other fields, if you can get the location information in advance, you may avoid these unexpected disasters, and reducing losses. Time difference of arrival method is a localization model based on time delay estimation, which is often used to determine the position of the target. The model has the characteristics of accurate positioning, and have a large number of applications in any engineering fields.In this paper, seismic signal as the object of study, to explore the problem of vibration source. This paper studies the characteristics of seismic signal, the preprocessing of signal and the estimation of time delay, the vibration source localization and its correction. The details are as follows:Due to the complex composition of the earth medium, we first process the seismic signals by empirical modal decomposition and Hilbert transform, and obtain different Hilbert spectra. Based on the Hilbert spectrum, the time-frequency and energy characteristics of the seismic signals are analyzed. The waveform and the spectrum of the signal, and then discuss the attenuation of the seismic signal. Some common wavelet basis functions and threshold estimation methods are compared, and then the background noise of the vibration signal is denoised by the wavelet threshold method. For the low SNR, the cross correlation method is difficult to extract the exact time delay estimation problem. The generalized cross correlation method of the maximum likelihood estimation window function is used to estimate the delay and verify the effectiveness of the method.For the classical Chan localization algorithm has poor results orientation, Newton optimization method of divergence leading to this algorithm failure, the paper presents a method of modifying the characteristic values of the ill conditioned matrixAbstractis positive definite, to improve the speed of iteration by introducing the step factor, so that each iteration along the descent direction and convergence as soon as possible. The experimental results show that the improved method can avoid the problem of the divergence of the initial value, and the performance of the algorithm is compared with the Chan algorithm and the method in this paper by RMSE.Completed the design of multi-sensor data acquisition system, including hardware acquisition and PC software design in two parts. The wave velocity of the test site is calculated, and several sets of source localization experiments are designed. The results of the positioning are discussed. Finally, the reason of the positioning deviation may be analyzed.Keywords:Time delay estimation, time-frequency analysis, Newton iteration, data acquisition, vibration source localizationIII吉林大学硕士学位论文IV 目录第1章绪论 (1)1.1 课题研究的背景及意义 (1)1.2 课题的国内外研究概况 (2)1.2.1 地震动信号分析及定位理论研究现状 (2)1.2.2 源定位技术的国内外现状 (5)1.3 本论文的主要工作 (7)第2章地震动波理论基础及特性分析 (9)2.1 地震动波类型及特性 (9)2.2 振动传感器及装置的选择 (10)2.3 地震动信号特性分析及相关理论 (12)2.3.1 地震动波的衰减 (12)2.3.2 基于希尔伯特-黄变换的时频分析 (12)2.3.3 远近距离波形的对比研究 (17)2.4 本章小结 (19)第3章地震动信号的预处理与时延估计 (20)3.1 小波去噪 (20)3.1.1 小波阈值去噪原理 (20)3.1.2 小波去噪性能分析 (23)3.2 广义互相关时延估计 (25)3.2.1 基于最大似然窗函数的广义互相关方法 (25)目录3.2.2 时延估计方法验证 (27)3.3 本章小结 (28)第4章基于Chan和牛顿迭代混合的震源定位优化方法 (30)4.1 基于Chan算法的初始定位 (30)4.1.1 Chan定位算法 (30)4.1.2 定位算法的仿真 (32)4.2 基于牛顿迭代的优化修正方法 (34)4.2.1 基于TDOA模型的牛顿迭代法 (34)4.2.2 改进的牛顿迭代方法 (35)4.2.3 定位算法的仿真 (37)4.3 定位的结果评价标准 (39)4.4 本章小结 (41)第5章多传感器数据采集系统与定位实验 (42)5.1 基于C ORTEX-M3内核处理器的数据采集 (42)5.1.1 硬件模块介绍 (42)5.1.2 数据采集系统硬件部分 (43)5.1.3 数据采集系统软件设计 (45)5.2 振动数据采集软件设计 (47)5.2.1 LabVIEW (47)5.2.2 数据采集上位机软件设计 (47)5.3 实验过程及结果 (50)V吉林大学硕士学位论文VI 5.3.1 实验的设计安排 (50)5.3.2 实验场地振动信号特性分析 (51)5.3.3 实验场地速度的计算 (53)5.3.4 多情况下的震源模拟实验讨论 (54)5.4 定位结果误差的原因分析 (60)5.5 本章小结 (61)第6章总结与展望 (62)6.1 全文工作总结 (62)6.2 展望 (63)参考文献 (64)作者简介及科研成果 (69)致谢 (70)第1章绪论第1章 绪论1.1 课题研究的背景及意义“定位”一词,最早出自古语“审名以定位,明分以辩类”,最初是指确定事物的名位,而现在多指对物体所在的位置进行测量,确定方位。
高精度室内定位算法与技术综述

0 引言在日常生活中,以位置为基础的服务(Location-based services,LBS)已经和人类的生活息息相关。
可靠的LBS 服务离不开准确的位置信息。
当前,依赖全球卫星导航系统(global navigation satellite system, GNSS)的室外定位技术[1]已经趋于成熟,甚至在于特定需求下可以达到亚米级的精度。
但是看似相似的室内定位技术实际却是截然不同,室内定位技术受环境影响较大,室外环境下障碍物较少,一般情况下二维定位即可满足需求。
而室内环境复杂,各种家具、楼房等等都会对定位产生影响,并且室内定位的精度需求远远高于室外,往往需要“厘米级”精度[2]才能满足用户需求,因此利用GNSS 提供位置服务的方案不太合适。
根据数据统计,在实际生活中,人类在室内度过的时间平均可以达到70% - 90%,对于LBS 的需求更迫切,GNSS 服务无法满足用户需求的情况下,需求精准室内位置信息已经成为室内LBS 服务发展的红线。
同时,随着几种主流室内定位技术,包括有Wi-Fi、蓝牙、超宽带、蜂窝移动网络的发展,已经能更为精确地实现信号的传递与检测。
1 应用前景随着定位技术的发展,基于位置的服务越来越受到人们的关注。
目前,LBS 已经渗透到人们日常生活的方方面面,关于室内定位的需求价值早已远远超出早期学者的预期,精确、实时的位置信息打破了虚拟空间的数据信息与真实世界物理对象的壁垒,掀起零售、制造、物流、急救、大型公共场所导航等行业的革命,真正意义上推动万物互联的进程。
[3]在商场、停车场、机场、火车站、医院等大型公共场所中,LBS 是不可或缺的。
比如,在人们外出旅游时,LBS 可以给人们带来方便,便于人们查询景点、餐厅、酒店宾馆等信息;当发生事故时,LBS 可以更加准确地提供具体信息。
同时,在信息时代的背景下,随着人工智能、机器人技术的发展,一些新型行业的兴起,比如无人医疗护理、智能制造、智能物流等行业也更加需要LBS 提供技术支撑。
RSSI

基于RSSI的无线传感器网络三角形质心定位算法引言无线传感器网络是面向事件的监测网络,对于大多数应用,不知道传感器位置而感知的数据是没有意义的。
实时地确定事件发生的位置或获取消息的节点位置是传感器网络最基本的功能之一,也是提供监测事件位置信息的前提,所以定位技术对传感器网络应用的有效性起着关键的作用。
在无线传感器网络中,按节点位置估测机制,根据定位过程中是否测量节点间的实际距离或角度,可分为基于距离(Range—based)的定位算法和距离无关(Range—free)的定位算法。
前者需要测量节点间的实际距离;后者是利用节点间的估计距离来计算末知节点的位置。
在基于距离的定位算法中,测量节点间距离或方位时采用的方法有TOA(Time of Arrival),TDOA(Time Difference of Arrival),RSSI(ReceivedSignal Strength Indication)和AOA(Angle of Arri—val)。
距离无关的算法主要有质心算法、DV—hop算法等。
相比之下,基于距离的定位算法测量精度较高,距离无关的定位算法对硬件要求较低。
比较各种基于距离的测距算法,TOA需要精确的时钟同步,TDOA需要节点配备超声波收发装置,AOA需要有天线阵列或麦克风阵列,这三种算法对硬件要求较高。
RSSI技术主要是用RF信号,而节点本身就具有无线通信能力,故其是一种低功耗、廉价的测距技术。
接收信号强度指示RSSI的定位方法,是在已知发射节点的发射信号强度,根据接收节点收到的信号强度,计算出信号的传播损耗,再利用理论和经验模型将传输损耗转化为距离,最后计算节点的位置。
因为理论和经验模型的估测性质,故而RSSI具有较大定位误差。
基于RSSI技术,提出一种将RSSI测量方法与三角形质心算法相结合的新型定位算法,该算法用三角形质心算法减小RSSI的测量误差。
仿真表明,该算法基于RSSI的三边测量法定位算法相比,极大提高了定位精度。
一种利用历史数据构造虚拟标签的定位算法

计算机应用研究
Application Research of Computers
Vol.29 பைடு நூலகம்o.1 Jan. 2011
一种利用历史数据构造虚拟标签的定位算法
赵劲 1,高强 1,杨凯文 2,刘述 3
(1. 北京航空航天大学电子信息工程学院,北京,100191; 2. 华北计算机系统工程研究所,北京,100096; 3. 工业和信息化部电信研究院,北京,100045) 摘 要:在 RFID 定位算法中, 利用接收信号强度统计模型进行直接定位的精确度不高, 而利用实际参考标签定位存在信号易 碰撞、外出部署不便等问题,因此本文提出一种基于虚拟标签的 RFID 定位算法 VIREH 以克服以上缺点。该算法利用历史数 据构建虚拟参考标签,然后利用虚拟参考标签代替实际参考标签进行定位。依据 VIREH 算法,开发基于 Android 移动设备的 RFID 定位系统,在系统中使用 VIREH 算法进行定位,对定位误差进行了统计以测试算法性能。测试结果表明 VIREH 算法的 定位精度较直接定位有显著提高,较使用实际参考标签没有明显降低,有助于提高 RFID 定位精度。 关键词: 射频识别;虚拟参考标签;安卓定位系统 文献标识码: A 中图分类号: TN925.93 文章编号:
是平均值为 0 的高斯分布随机变数,即信号穿过障碍物产生 的随机衰减,其标准差范围为 4~10。利用该模型,通过带入 依据经验值得到的一组 Pr (d0 ) 与 d 0 ,直接计算得出目标标 签的位置信息,但这种定位方法由于使用单纯的理论模型, 受到的局限很大, 对于穿墙、 无线信号环境复杂等实际情况, 定位精度不高。 在使用实际参考标签进行定位的 LANDMARC 定位算法中 [2] ,利用离目标标签最近的一组实际参考标签进行定位。通 过比较读写器测得的目标标签场强值与实际参考标签场强 值的相对大小来对实际参考标签进行选取,这样的方法可以 有效的抵消环境因素的影响,特别是非视距的定位中,能够 有效地克服障碍物造成信号衰减不规律的问题。但是该方法 存在无法有效处理的、严重的多径效应,若想提高精度,则 需要增加参考标签部署的密度,这样容易带来标签之间发射 信号碰撞、干扰等问题。同时,在定位环境中部署参考标签, 会增加定位设备的成本,在定位环境改变后(如监狱人员外 出劳动等) ,重新部署参考标签会带来不便。 为了克服使用实际参考标签遇到的困难, Zhao Yiyang 等学者提出了通过建立虚拟标签来提高定位精度的定位算 [4][5] 法 。算法通过线性插值法等方法在相邻的两个实际的参 考标签之间来构造若干个虚拟参考标签,然后不同位置部署 的读写器可以利用虚拟参考标签求解出待定位标签的位置。
无线传感器网络RSSI测距方法与精度分析

无线传感器网络RSSI测距方法与精度分析詹杰;吴伶锡;唐志军【摘要】基于RSSI的测距技术是一项低成本的距离测量技术.分析了接收信号强度指示器(RSSI)多种测距模型,结合采用IEEE802.15.4协议的CC2430芯片,设计了测距实验,获取了多组数据,通过对实验数据的分析,提出结合信标节点确定参数、高斯拟合确定测量值的RSSI测距处理方法.实验证明,该方法能提高RSSI测距的抗干扰能力,20 m内节点间的测距精度能达到1.5 m以下.【期刊名称】《电讯技术》【年(卷),期】2010(050)004【总页数】5页(P83-87)【关键词】无线传感器网络;接收信号强度指示器;测距精度;高斯拟合【作者】詹杰;吴伶锡;唐志军【作者单位】湖南科技大学,物理学院,湖南,湘潭,411201;湖南科技大学,物理学院,湖南,湘潭,411201;湖南科技大学,物理学院,湖南,湘潭,411201【正文语种】中文【中图分类】TN9291 引言在无线传感器网络应用中,位置信息对传感器网络的监测活动至关重要, 在目标监测与跟踪、基于位置信息的路由、网络的负载均衡以及网络拓扑结构[1]等许多应用中都要求网络节点预先知道自身的位置,以便在通信和协作过程中利用位置信息完成应用要求。
常用的定位方法必须测量节点间间距,一般测距方式有GPS[2]、红外线[3]、超声波[4]和接收信号强度指示器(RSSI)[5]等。
GPS定位成本高、误差大;红外测距精度高、成本低,但适用范围太窄;超声测距需要额外的硬件,增加了节点的硬件成本和尺寸并且能耗高,受气温、湿度等的影响较大;RSSI测距误差大,这些方式都不适合无基础设施的矿山地质灾害监控系统使用。
在矿山地质灾害监测项目中,我们利用商用无线收发芯片所具备的RSSI功能对监控系统收发的数据进行处理,提高RSSI测距的精度,实现了低成本的测距。
2 RSSI测距原理无线信号传输的一个重要特点就是信号强度随着距离的增大而衰减。
反射与噪声对室内可见光定位系统精度影响及其克拉美罗界

反射与噪声对室内可见光定位系统精度影响及其克拉美罗界张秀楠;邵建华;柯炜;袁亚男;聂帅【摘要】基于到达信号强度(RSS)测距的方法,可见光室内定位系统中因为墙面反射和外界噪声等存在干扰,从而产生误差.将计算机图形学中的Phong模型应用到可见光定位的墙面反射模型中,通过计算仿真反射和噪声信号到达接收端的强度,与发射端直射到接收端的信号强度进行对比,发现干扰信号中反射信号的强度与直射强度处于同一个数量级上,因此干扰对于可见光定位系统误差的影响不容忽略.仿真得到这些干扰对于最终定位系统造成的误差,并且与表示定位性能的克拉美罗下界进行对比,发现最大误差达到1.82 m,平均误差为0.12 m,干扰现象在墙角区域明显.%The visible light indoor positioning system based on received signal strength(RSS)has positioning error due to the disturbance of the wall reflection and the external noise. This system applies Phong in computer graphics to the wall reflection of visible light positioning. Comparing signal strength from LEDs directly with the reflection and noise simula-tion at the receiving,it is found that signal strength of the wall reflection and direct strength are in the same order of magnitude. Thus the disturbance of the wall reflection and the external noise cannot be ignored. This article compares the simulation error caused by the disturbance to the positioning system with Cramer-Rao bound which represents the lower limit of the positioning error. It is found that maximum error is 1.8 m and the average error is 0.12 m. The disturbance phenomenon is obvious in the corner of the wall.【期刊名称】《南京师大学报(自然科学版)》【年(卷),期】2017(040)003【总页数】8页(P102-109)【关键词】可见光;定位;反射;噪声;克拉美罗界【作者】张秀楠;邵建华;柯炜;袁亚男;聂帅【作者单位】南京师范大学物理科学与技术学院,江苏南京210023;南京师范大学物理科学与技术学院,江苏南京210023;南京师范大学物理科学与技术学院,江苏南京210023;南京师范大学物理科学与技术学院,江苏南京210023;南京师范大学物理科学与技术学院,江苏南京210023【正文语种】中文【中图分类】TN929.1随着社会的加速发展,数据和多媒体等业务的迅速增加,人们对于室内导航与定位越来越依赖,特别是在较复杂的环境下,如在室内高保密会议和军、工、政保密工作场地,在公共区域、商业场所室内等. 因此,人们探索出很多种方法,如ZigBee定位技术、WLAN定位技术、红外线技术、超声波技术、蓝牙技术、超宽带定位技术、射频识别定位技术等[1]. 但是上述方法都需要通过安装发送与接收设备等繁杂的工序,并且这些技术对于安装环境的要求也较为苛刻,这些因素极大地增加了定位的成本,从而限制了这些技术的推广与使用[2].LED被称为第四代光源,它的发明为照明技术带来了新的革命,它集合了各种传统光源的优势,并且具有电压低、功耗低、寿命长、易于小型化等各项优点. 因此基于白光LED的通信技术应运而生,并以其能效高、绿色环保、不受电磁干扰等影响的优势,兼具照明与通信两种功能成为近几年来的一个研究热点. 从2000年,日本研究人员提出并仿真基于LED灯作为基站的可见光室内通信系统后,可见光的通信迅速得到各国的关注.基于白光LED的可见光室内定位技术也随之被提出. 目前已有的室内定位技术大多是在发射端通过各路LED灯不断发送一定的光信号,位于室内的移动目标接收到LED灯发来的信号,通过接收到的光信号来判断移动目标所在的位置. 每路LED灯通过发送不同频率的数据信号(FDM),或者在不同的时间发送数据信号(TDM),给每个LED灯一个自己的专用标识ID,来标记接收到的光信号来自哪一路[3]. 接收端在识别信号来源的同时,利用TOA、TDOA、AOA、RSS等方法进行测距. 但是大多文献没有考虑到外界干扰对距离测量的影响,进一步对定位精度造成的影响.在移动通讯中,关键的一个环节就是定位服务的精度要求,本文针对这一要求,研究定位过程中墙面反射光及外界自然光对定位精度的影响,对比不同定位方法中外界因素影响下的误差大小,并与克拉美罗界进行比对.1.1 系统模型本文所采用的系统模型如图1所示[4-5],该模型中室内定位场所为5 m×5 m×3 m 的空间,4个LED灯安装在天花板上,利用LED灯的照明与通信双重功能,对LED灯进行合理的布置,尽可能使接收平面上所有位置都能被光照覆盖. 4个LED灯光照强度完全相同,且发射信号自带信标(ID),使接收端(PD)能够分辨来自每个LED灯的信号强度.1.2 理想信道模型及定位方法1.2.1 信道模型室内定位系统主要由天花板上的LED灯作为发射源发出带有ID的光信号,光信号由接收端的PD接收. 图2给出了可见光室内定位系统的典型直射模型.本文中辐射模型采用最经典的朗伯辐射模型[6-7],其中发射端发出的光信号直接到达接收端的直射路径信道增益Hd可由式(1)表示.式中,AR是光检测器接收面积,θ是辐射角,ψ是接收角,TS(ψ)是光滤波器增益,g(ψ)是光聚器增益,FOV 为光接收机视角(Field Of View),n为朗伯系数,即式(2):,式中,θ1/2为LED光源的半功率角.直射路径中,接收端接受强度Pr与发射端辐射强度Pt之间的关系可由式(3)表示: 发送端辐射强度Pt为光功率,因此上式中接收信号强度Pr也是光功率,以下记作Pr_Opt,在光电探测器中首先将接收到的光功率以γ转换系数转变为电流[8],如式(4)所示:,则接收到的电功率表示为式(5):1.2.2 Phong模型和一次反射光信号从发射端传播到接收端途中,除了上面所述的直射情况,传播路径还包括反射部分,并且在信号传播过程中不可避免会有外界光被接收端所接收,这些都是可见光定位系统中的“噪声”. 本文中将这“噪声”简单分割为信号传播途中经过周围四面墙的反射光和外界包括自然光的一些干扰因素.为了简化模型,本节将讨论墙面一次反射光的信道模型. 本文中的反射面模型采用光照模型中的Phong反射模型[9],这个模型不同于理想的镜面反射和漫反射模型. 完全漫反射光可以被认为是光源发出的光被墙面接收,然后重新反射出来,即从一个方向射进墙面,又以各个方向均匀地向外射出,因此无论在什么位置都可以看到漫反射光. 而理想的镜面反射模型是光源发射出的光线以一个入射角射进一个光滑的平面,反射角一定是与入射角相同的,因此只有在反射方向才能看到反射光. 本文采用的Phong不同于上面两者,而是将完全漫反射光与镜面反射按一定的比例相结合,构成了一个与现实中的墙面反射比较为真实的模型.图3给出了可见光室内定位系统的墙面一次反射模型.如图3所示,光信号由光源辐射出去,墙面的反射可以看作是先把墙面作为接收端接收光信号,然后又作为发射端发射出去,因此这一反射过程可以看成把两次直射相结合. 在反射过程中,首先将墙面分割成许多的小平面,本文中称之为微元面,每个微元面的面积为1 dm×1 dm. 当光信号从光源处发射出去以后,房间四周墙面的某个微元面作为接收端接收光信号,此时光照经过第一段距离的衰减后,接收信号强度为: 式中,Hd为直流信道增益,是LED光源的强度,是墙面在直射路径下的接收强度.墙面上的微元面接收到光信号后又可以看作为一个朗伯光源,而每个微元面的辐射强度为:式中,ρsurface表示墙面的反射系数.在这种模型中,入射光根据反射系数有部分被吸收,以ρ·α的概率进行镜面反射,以ρ·(1-α)的概率进行漫反射.经过墙面一次反射后接收平面上的PD接收到的信号强度为:1.2.3 噪声模型本节所述噪声为接收端PD接收到的除去墙面反射光部分其它因素造成的干扰,主要包括热噪声和散粒噪声两个部分,具体参数如表1所示[10].热噪声的功率为:散粒噪声的功率为:1.3 定位方法本节中采用定位中比较经典的三边定位法进行定位. 根据三边定位法的原理[11-12],给出PD未知位置与4个LED已知位置之间距离构成的方程组,如式(12)所示.式中,(x,y)表示最终定位的PD的位置,(xi,yi)表示第i个LED灯在天花板上的位置,di表示PD到第i个LED之间的距离,该距离可由上述式(1)中的信道增益得到. 上面所说的三边定位法是针对理想情况下准确无误地测出发送端与接收端之间距离的,但是在现实条件下,由于反射和噪声等不可避免的干扰存在,测算出的收发端之间的距离往往会小于理想情况下测算出的距离,那么利用三边定位法就无法定位到接收端的一点,所以我们使用下列方法进行定位.将上式(12)变形得到式(13).将上式转换为矩阵的形式进行求解,即转换为AX=B,则方程组的解即为X=[x y z]′=A-1B.在本设计中因为A没有逆矩阵,则无法求解该方程组,因此我们这边引入了广义逆这个概念. 根据最小二乘法的准则,将目标函数定位为XLS=argmin‖AX-B‖2,解出该方程组的最小二乘解为X=A†B.1.4 定位误差与克拉美罗下界的对比克拉美罗下界(CRB)为任何无偏估计确定了一个下界,也就是不可能有方差小于这个下限的无偏估计量. 本文中,利用克拉美罗下界来表示可见光室内定位系统的性能好坏. 因此我们给出空间内各点处的克拉美罗下界,通过推导接收平面内各点的克拉美罗下界,可以得到在反射和噪声作为干扰条件下的定位理论最佳性能[13-14].由上面式(1)和(3)得到,式中,i=1,2,3,4表示第i个发射端LED灯的参数,因此Pni=(Pn1,Pn2,Pn3,Pn4)T表示第i个LED灯接收到的噪声功率,而且则有且,那么,因此克拉美罗下界的倒数可以表示为:2.1 定位系统的仿真可见光室内定位系统采用MATLAB软件进行仿真实验. 仿真中4个LED灯的位置分别在A(1,1,3),B(4,1,3),C(1,4,3),D(4,4,3). 利用RSS到达信号强度的方法进行测距,图4给出了4个LED光源照明强度的分布.2.2 反射及噪声的影响考虑干扰中一次反射及噪声对于定位精度的影响. 为了简化模型,本文中仅考虑四周墙面的反射,且墙面以常用的反射系数和镜面反射指数作为仿真模型,选取反射系数为0.66,以0.66×0.4的概率进行镜面反射,0.66×0.6的概率进行漫反射,不考虑天花板和地面的反射.图5和6分别给出了经过四周墙面反射后的反射光的强度分布图和空间内外界噪声的分布情况.由图5和6可示,一次反射光和外界噪声相对于直射光的强度还是比较大的,特别是反射光的强度,因此肯定会对定位精度造成较大的影响. 下面我们对反射光及噪声对于定位误差的影响进行仿真. 本文中采用误差公式[15](20)表达定位误差.式中,(xm,ym)表示仿真中利用最小二乘法定位出的坐标.图7和图8分别给出了仿真空间内各处由于一次反射光和噪声对定位误差造成的影响. 并且图9给出了把反射光和噪声作为一个干扰整体,其对于定位误差造成的影响.2.3 克拉美罗下界及其与算法误差的对比分析图10和图11分别给出在反射与噪声两外界干扰下的克拉美罗下界. 上面已经给出了定位性能的下界,我们将最小二乘法定位精度与这个下界进行对比. 图12和图13分别给出了反射和噪声在最小二乘法下的定位误差与反射和噪声作为观测误差下的克拉美罗下界对比图. 克拉美罗下界给出反射及噪声的平均误差为0.015 8 m,利用最小二乘算法下的平均误差为0.124 2 m,两者相差一个数量级,对比表明,最小二乘法运用下的定位精度相对较高.2.4 定位误差与反射系数的关系以上仿真是考虑了市面上较为常见的白粉墙面作为仿真对象进行一次反射,本小节中将研究墙面反射系数和光滑程度对定位误差造成的影响. 图14给出了不同镜面反射指数(α)下,定位精度与墙面反射系数之间的关系. 由图分析可得,墙面反射系数在0.3处,定位误差较小;定位误差会随着镜面反射指数的增加而增加,定位精度随之减小,即墙面越粗糙,在接近完全漫反射的情况下,定位误差最小,定位精度最高.本文对可见光室内定位系统进行了简要介绍,将在墙面上反射的复杂过程进行了简化,并采用光照模型里面比较经典的Phong模型进行仿真. 在朗伯模型的基础上,深入讨论了含有反射光和高斯噪声等干扰的影响下接收到的信号强度. 结果表明,相对于直射光的强度,墙面的反射干扰的强度还是很大并且不能忽略,因此对于干扰的研究十分必要.文章采用接收信号强度(RSS)的方法进行测距,然后使用最小二乘法实现定位. 整个系统采用使用广泛的LED灯进行照明,并且能实现室内定位,无需接收信号同步,因此设备简单,数据处理计算难度都不大. 最后将定位精度与克拉美罗下界进行了对比,仿真结果表明精度相对较高.然而,仿真结果可以看出最小二乘法下的定位精度与克拉美罗下界之间还是有一定的差距,定位误差的大小一直是衡量定位方法好坏的一项比较重要的标准,因此如何去减小定位误差提高定位精度的问题将成为接下来的研究重点.【相关文献】[1] 汪苑,林锦国. 几种常用室内定位技术的探讨[J]. 中国仪器仪表,2011(2):54-57.[2] 赵嘉琦,迟楠. 室内LED可见光定位若干关键技术的比较研究[J]. 灯与照明,2015,39(1):34-41.[3] NADEEM U,HASSAN N U,PASHA M A. Indoor positioning system designs using visible LED lights:performance comparison of TDM and FDM protocols[J]. Electronicsletters,2015,51(1):72-74.[4] 沈芮,张剑. 基于可见光通信的室内定位方法[J]. 信息工程大学学报,2014,15(1):41-45.[5] ZHANG W,KAVEHRAD M. A 2-D indoor localization system based on visible light LED[C]//Photonics Society Summer Topical Meeting Series,Seattle,2012:80-81.[6] SOO Y J,SWOOK H,CHANG S P. TDOA-based optical wireless indoor localization using LED ceiling lamps[J]. IEEE transactions on consumer electronics,2011,57(4):1 592-1 597. [7] KAHN J,BARRY J. Wireless infrared communications[J]. Springerinternational,1994,85(2):265-298.[8] HYUN S K,DEOK R K,SE H Y,et al. An indoor visible light communication positioning system using a RF carrier allocation technique[J]. Journal of lightwavetechnology,2013,31(1):134-144.[9] 吴凤和,王金芬,尹清静,等. 基于锥角计算的Phong混合反射模型反射参数估算[J]. 燕山大学学报(自然科学版),2014,38(2):144-151.[10] ZHANG X L,DUAN J Y,FU Y G,et al. Theoretical accuracy analysis of indoor visible light communication positioning system based on received signal strength indicator[J]. Journal of lightwave technology,2014,32(21):4 180-4 186.[11] 吴楠,王旭东,胡晴晴,等. 基于多LED的高精度室内可见光定位方法[J]. 电子与信息学报,2015,37(3):727-732.[12] 孙佩刚,赵海,韩光洁,等. 混沌三角形定位参考点选择算法[J]. 计算机研究与发展,2007,44(12):1 987-1 995.[13] 沈芮,张剑,王鼎. 基于可见光通信的室内定位算法及相应参数估计克拉美罗界[J]. 激光与光电子学进展,2014,51:1-8.[14] WANG T Q,SEKERCIOGLU Y A,NEILD A,et al. Position accuracy of time-of-arrival based ranging using visible light with application in indoor localization systems[J]. Journal of lightwave technology,2013,31(20):3 302-3 308.[15] ZHOU Z,MOHSEN K,PENG D. Indoor positioning algorithm using light-emitting diode visible light communications[J]. Optical engineering,2012,51(8):1-6.。
2012年移动代维考试(D) 考试

当前位置:员工考试 »试卷查看试卷查看2012年移动代维考试(D)考试考生:饶湘明成绩:68.0一、单选题共50道题,总分50分。
1、以下哪个现象不存在模拟网,而只存在于数字无线网中?()瑞利衰落拥塞快衰落码间干扰考生答案:D参考答案:A得分:0.0?2、GPRS使用CS2的编码方式的时候1个TS的最大速率是__ __kbps。
()1211.41622.8考生答案:C参考答案:A得分:0.0?3、以下关于天馈线安装的描述,哪项是错误的?()为了防止天线进水,在正向安装全向杆状天线时,天线底部的排水(气)孔应打开,天线顶部的排水(气)孔应密封。
定向天线不能倒立安装。
在反向(倒立)安装全向杆状天线时,天线底部和顶部的排水(气)孔都应打开。
为了防止馈线进水,在拧接好的跳线与天线的连接处、跳线与馈线的连接处应先用防水自黏胶带密封,再用绝缘胶带包扎、密封好。
考生答案:C参考答案:C得分:1.0?4、直放站告警处理机制中,对于已屏蔽的告警项目如何处理?()不上报该告警,监控中心查询该告警状态为正常;不上报该告警,监控中心查询该告警状态为非正常;上报该告警,监控中心查询该告警状态为正常;上报该告警,监控中心查询该告警状态为非正常。
考生答案:A参考答案:A得分:1.0?5、分别在直放站的输入端和输出端测试其至施主天线和覆盖天线的驻波比,其驻波比要求小于() 1.31.41.5考生答案:C参考答案:C得分:1.0?6、在GSM900系统中,施主基站CDU端的最大输出功率是()45dbm33dbm47dbm33w考生答案:C参考答案:C得分:1.0?7、器件RD-5NK/NK/NK-06F1是()5dB耦合器6dB耦合器二功分三功分考生答案:B参考答案:B得分:1.0?8、一部手机最多可以从___个PSET中分配信道()1234考生答案:A参考答案:A得分:1.0?9、当以下()设备的施主基站载波扩容时,应相应对其直放站进行扩容。
单选(英文题)

编号题干A1Below ,which function is notbelong to SGSNCiphering,authentication2About CAN using ,which one iswrong?The ConsistencyCheck is a set ofrules checking theconsistency of thenetworkconfiguration in theplanned or validarea.3Why can BTS power control beused to increase the capacity(that is, tightening thefrequency reuse in thenetwork)?It increases thesensitivity of themobile4Why are base stations sometimescascade connects?To save antennas5When mounting D.F. th minimumdistanc from floor to lowr ofD.F. mounting is1200mm6Which unit enables connectionof multiple transmitters to thsame antenna?Combining andDistribution Unit(CDU)7Which protocol performs the addressing for circuit related signaling?MTP8Which of these parameters canaffect the SS drop rate?BSTXPWR9which of these different"dropped call rates" gives a"subscriber perceived" droprate?Dropped TCHconnections of thetotal number of TCHconnections10Which of the following units manages the A-bis linkresources in th RBS2000?TRU11Which of the followingstatements about the urbanmodel is not true?Permanent screens,used in the half-screen part of theurban model,are usedto define theenvironment alongthe calculationprofile in a generalway and, therefore,the locations of thescreens do not needto coincide with theactual placementsof, for ex12Which of the followingSignaling System No. 7Protocols are used for routingof signaling messages?MAP, TCAP13Which of the following is theright setting of the BasicRecording Period (BRP) for STS?20 or 25minutes.14Which of the following is not avalid SDCCH configuration?SDCCH/4 combinedwith CCCH ontimeslot one15Which of the followingfunctions is designed to reduce congestion in cells?Handover16Which of the following faultswill affect the function of awhole TRU immediately?TX Internal FaultMap Class 2A, faultcod 1217Which of the followingalgorithms is made up of thethree stages: Mcriterion, K-criterion and L-Creterion?Ericsson-algorithm18Which of the criteria below isnot influenced by the value ofCHAP?Prioritizing ofdifferent users ornot.19Which of Ericsson@s NetworkImprovement PerformanceServices includes optimizationactivities?Network Design andPerformanceConsulting (NDPC)20Which is the most importantfactor for determining thepaging capacity in the BTS?MFRMS (controls thenumber of paginggroups)21Which drop counter is steppedwhen a call is disconnectedbecause MAXTA is exceeded?SS drop counter22When mounting D.F. the minimum distance from floor to lower ofD.F. mounting is1200mm23When may the merry-go-roundeffect occur?If the hysteresis istoo small24When install the ?" cable, the minimum banding radii without rebinding is300mm25What should be done beforemoving out a TRU magazines?Power off all TRUs26What part was added to the MTPin the SS7 signaling system to enable it to support connctionorintated and connectionless signaling?ISUP27What parameter is used for theoutput power at the locatingreference point on non-BCCHcarriers?BSPWR28What is TRHYST used for?It modifies the sufficient level condition for neighboring cells.29What is the result from fieldmeasurements of coveragecompared with:The required signalstrength30What is the purpose of settingBSRXSUFF to -150 dBm andMSRXSUFF to 0 dBm in all cells?To enable path lossranking.31What is the parameter TINITused for?To set the initialvalue of the timerthat inhibitshandover after achange of channel.32What is the normal event thatleads to an abnormaldisconnection and stepping ofthe drop counter?Failed decoding ofspeech frames33What is the most common valueof the hysteresis used when estimating margins for log-normal fading? 3 dB34What is the ERP (EffectiveRadiated Power), if the outputpower from the radio is 43 dBm,the cable losses 3 dB, and theantenna gain 14 dBd?43 dBm35What is the difference betweenBSTXPWR at the "preferredreference point" and thereported signal strength in themobile?Path loss36What is the basic ranking inthe Ericsson1 locatingalgorithm based on?Relative signalstrength37What is TET used for?To perform measurements of the percentage of interfered traffic.38What is one of the differencesbetween the phase 1 and phase 2establishment causes?Phase 2establishment causesdistinguish betweenanswer to paging andcall re-establishment.39What is not taken into accountwhen deriving SQI?FER40What is ICDM?Intra-Cell Downlink Measurements41What is CRH used for?It is used in combination with ACCMIN to cater for a layered cell structure in a dual band network.42What is BQOFFSET used for?It is used as a signal strength offset to penalize cells after a bad quality urgency handover.43What is added to the MSsensitivity level to obtain therequired signal strength,SSreq?Rayleigh fadingmargin44What expression is usually usedfor the paging success rate?Successful repeatedpage attempts (inlocation area) oftotal number offirst and repeatedpage attempts (inlocation area).45What cell property is limitedby timing advance?Number ofsimultaneous calls46What are event and levelcounters?It is the name ofthe softwarecounters that arestepped in functionblocks outside theSTS (in RPs andCPs).47In WCDMA,which one is notbelong to the UE IDLE mode?MN selection andreselection48Use the enclosed Erlang Tableto work out which is theoptimum SDCCH configurationusing four TRXs, if theSDCCH/TCH traffic ratio is 30%and the required GoS on the TCHis 2%. (Assume no cellbroadcast and no immediateassignment on the TCH.)SDCCH/849The wave propagation predictionalgorithm 9999 takes a lot intoaccount, but not:Terrain profile50The SS7 signaling is mad up ofa Message Part(MTP)and a numberof User/Application Parts(UP).What User or Application Partis used for signaling betweenthe BSC and the MSC in the GSM network?MAP51The RBS2000 is mad up of anumber of "Units" known as?Hardware Units52The purpose of ramping is toavoid handover decisions to anew neighbor based on only afew samples. What is a commonparameter setting for macrocells?SSRAMPSI=20 andSSRAMPSD=1053The idle mobile derives anentity called C2. How is C2used?C2 for a particularcell must be largerthan zero for amobile to be allowedto camp on thatcell.54The idle mobile derives anentity called C1. How is C1used?C1 for a particularcell must be largerthan zero for amobile to be allowedto camp on thatcell.55The GPRS functionality isactivated in a cell by which command?RRNSI56The device type for the 64 kbpsTim Slots on the Abis interfaceis :RALT57The counter values are copiedand transferred to a databaseon the hard disk in the IOGaccording to theNRP (Number ofrecording period)58The Cabinet Assembly andextension Manual defines:Mounting of RU@S inthe cabinet59The base station use FCOMB,this order to the leastfrequency interval400kHz60Th SS7 signaling is mad up of a Massage Part(MTP)and a numberof User/Application Parts(UP).What User or Application Partis used for signaling betweenthe BSC and the MSC in the GSM network?MAP61Th RBS2000 is mad up of anumber of "Units" known as?Hardware Units62TEMS speech quality index, SQI,is capable of producing speechquality estimates,What is nottaken into account?Bit errordistribution63Reusing frequencies in acellular pattern (compared to"one big cell")Increases channelutilization, cost,and interference.64Maximum how many RBS2302 can be connected in a linear cascaded chain?365Is it possible to have RBS 200and RBS 2000 in the same Cellin ericsson R8?Yes, but the RBS 200must b configured asslave, and RBS 2000as master.66is CRH used for?It is used in combination with ACCMIN to cater for a layered cell structure in a dual band network.67In GPRS:The MS performs an autonomous cell selection in both packet idle and packet transfer mode.68If there is alarm Fan Capacity Reduced, what@s the possibleunit to b checked?FAN69If the path loss compensation parameter, LCOMPDL, is set toten, the down regulation in theBTS output power, due to pathloss compensation, is limitedto: 6 dB70If a call is dropped duringexcessive TA, bad quality andpoor signal strength, whichcause counter will step?SS drop counter71How many TRXs can the ericssonBSC support?12872How many transmitters (TXs) can be configured to an omniantenna using a CDU-D?473How many paging requests can,at the most, fit into onepaging block?274How many different paging areas are supported for GPRS?175How many ARFCNs can an operatoruse if allocated 15 MHz uplinkand15 MHz downlink (minus onefor guard band)?14 ARFCNs76What is GPRS?General Standard Radio System77For the different object types,there are a number ofindependent individuals,regarded as Objects78For RBS 2202 +24VDC, what@s thvoltag rang us19 to 29 VDC79Flexible alarm classificationin ericsson R8 allows:Changing specific CPand SP alarmslogans.80CHA (Command HandlingApplication) can handle whichthree types of command files?command file, OPScommand file, systemcommand file81Cells in the basic ranking list are divided into categories.How many categories are there,if the serving cell isconsidered as a category of its own?282Calculate the processorcapacity in terms of calls/swhen the traffic load is 72%and the load per call is 25ms28,8 calls/s83below ,which parameter isassociated with" disconnection Criteria"KHYST84Assume that there are 12frequencies (f1-f12) in thehopping frequency set. Whatdefault MAIO values areallocated to the first sevenTRXs in the cell"?0, 1, 2, 3, 4, 5,and 685Are the UL signal strengthmeasurements used in thelocating algorithm?No, not at all.86Any faults that may occur atthE BTS, which permanentlyeffect the normal operation ofthe equipment, will be recordedin what two different eventregisters?Faulty Unit List anderror Log87An idle mode mobile must readthe BCCH data and decode BSICfor the neighboring cells, atleast, once during certain timeintervals. What are theintervals?Five seconds (BSICand BCCH data)88AGBLK must be set to a non-zerovalue (that is = 1 inEricsson@s GSM system), if:Cell broadcast isused in a cell witha non-combinedconfiguration.89A transmitted signal isreceived at -50 dBm and thereis -150 dBm interference at thesame frequency. What is C/I? 3 dB90A repeater can be used to:Increase the capacity locally (in a traffic hot spot).91A cell has three TRUs with an SDCCH/8 configuration. What isthe maximum number of telephone calls it can support simultaneously with a half-rate vocoder?2292An idle mode mobile must readthe BCCH data and decode BSICfor the neighboring cells, atleast, once during certain timeintervals. What are theintervals?Five seconds (BSICand BCCH data)93What are event and levelcounters?It is the name ofthe softwarecounters that arestepped in functionblocks outside theSTS (in RPs andCPs).94For the different object types,there are a number ofindependent individuals,regarded as.Objects95A cell has three TRUs with an SDCCH/8 configuration. What isthe maximum number of telephone calls it can support simultaneously with a half-rate vocoder?2296Why do we introduce GPRS inmobile telecommunicationsystem?To improve voicequality.97Which one is NOT correct amongthe following statements?GPRS stands forGeneral Packet RadioService.98Which GPRS MS can have both CSand PS connection at the sametime?Class A99List the basic GPRS networkelements that support PSservice.SGSN and GGSN100What@s the protocol standard onGb interface?IP101What@s the platform forEricsson GSN node?Cello102What can a GPRS user do afterhe has done GPRS Attach (buthave not finished PDP ContextActivation)?Sending data103Which one is responsible forPDCH allocation?PCU104Charging principles will bemore flexible in GPRS network.Which one is difficult intraditional GSM network?time-based charging105In Ericsson GPRS solution,which one or ones have to do hardware upgrade in thefollowing GSM network elements?RBS106Which IP address should be usedwhen you try to access oneEricsson GSN node with PXM inthe O&M center?GSN O&M VIP107What Is the destination IPaddress in the IP header of thepacket sent from DNS toEricsson SGSN?GSN O&M VIP108Which IP address is used toencapsulate GTP packets?GSN O&M VIP109For RBS 2202 extension cabinetwhich TRU back plane dip switchsetting is true?1up 2up 3down 4up5up 6down110Which logical channel must be dimensioned for each cell when considering the frequency ofcall setups?SACCH111What is the difference between1 milliwatt and 1 watt?20 dB112Which of the following problemsexists in digital radiosystems, but not in analogradio systems?Rayleigh fading113What is system balance?Each cell can handle the same amount of subscribers114Which of these is not aprediction model for radiocoverage?Algorithm 9999115A subscriber makes a two minutecall and a four minute callduring the busy hour. How muchtraffic does he generate forthat hour?10 millierlangs116Which of the following is notnecessary to consider whensurveying a potential site?Frequency allocation117What is the advantage of usingDTX for an MS?Increases batterylife118What does locating mean?Paging of a mobile in more than one cell119Which of the following isEricsson@s scheme to graduallytighten the reuse distance in anetwork?Multiple Re-usePattern (MRP)120Antenna gain is obtained by?A power amplifier in the antenna system121What is the name of the type offading which is due toshadowing?Multipath122What is used to prevent @ping-ponging@ , that is, rapid,successive handovers?DiscontinuousTransmission123When the BSC verifies the datastored in the BTS and finds adiscrepancy, what action istaken?The MO will beloaded and testedand the BTSparameters will beupdated124What MOs can be tested withcommand ordered equipmenttests?TG, TRXC, TX, RX &TS125Where is paging initiated?BSC126Where are measurement reports,which determine handover of acall,carried out?BSC and MS127How often is a completemeasurement report transmittedfrom the MS tothe BSC?Every 60 s128Blocking supervisionmeasurements take place every100 sec129Which of the following Burstshas the longest Guard Period?SynchronizationBurst130is it possible to change theBCCH frequency without haltingthe Cell in Ericsson R8?No, only possiblefor the TCH131Which of the following is trueregarding Location Areas?One Location Areacan belong toseveral BSCs132The common radio network (key)performance indicators can besorted into three groups,which?Accessibility,retainability, andservice integrity133Which of Ericsson@s NetworkImprovement PerformanceServices includes optimizationactivities?Network Design andPerformanceConsulting (NDPC)134How does the two nodes in IOG20 communicate?ICB135Name the subsystem in IOG20that handles the hardware ofthe IO terminals DCS136How many RPs can be scanned bythe CP each time for the Serial RP-bus type?8137The files in ( ) volume areused to store the CP backupsoftware.RELVOLUME138( ) is used to collectstatistical data for various measurements and the softwareis loaded in IOG20.RMS139Manual dumps are usually madeafter ( ) is performed.Function Change140What is the first action takenwhen a software error isdetected?Forlopp reset141After an Automatic Reload ofthe CP, data from which Logmust be manually loaded?Transaction Log142In command EXRUI, we define the( ) and ( ) software.Operating andMaintenance143PDSPL2 hardware is the commonplatform for ( ) devices.tone sending andreceiving144( ) handles signalling betweenCP and RPs.SPU145In HLR the MSISDN is link tothe ( ).Location Area146Location Updating is requiredwhen an MS enters a new ( ).LA or MSC147Echo Canceller is normally usedfor traffic from ( )routes.Other MSC148During a hand-over to anotherMSC, the ( ) s requested fromthe target MSC.Hand-over number149DTI is used during a data callfor()number seriesconversion150SCCP is used to make MTP more Connection Less151The information contained inone timeslot on the TDMA frameis called a ( )traffic channel152Transceiver Handler (TRH) isused for ( )in PD signalling153Stoppage situation in the AXEexchange means that:the clocks are notproperlysynchronized154In APZ 212, the SPU ( ) all jobsignals from RPH and IPU.handles155A software fault in the systemwill effect which CP?CP-A156In Network Synchronization, ifthe value of the WDL exceedsthe set limits for the DIP thatis EX, what happens?Nothing happens, DIPis still working asEX157In CCS, OPC tells theOriginating SP, DPC theDestination SP and CIC is the information about the ( )channel.Speech158An MSU is the packet containing( ) about the rmation159STP in the signaling networkcan be either Stand-alone or ().Integrated160A few parallel Signaling Linkstowards the same destination iscalled a ( ).Signalling Channel161A semi-permanent connection inCCS is required to preventdisconnection during a ( ).Small System Restart162In CAS, TS16 is used to convey( ) signals.Register signals163What is a data file in our DSin CP? A file full of data164What RP types are used in theSerial RP-bus?RP1, RP2 and RPA165The ( ) ensures that the APZ isrunning all the time, even whenone side is faulty.MaintenanceSubsystem166If the RP pair handles 16 EMs together, how many can one RP handle if the other is faulty?16167What is the switching principlein GSS?Time-Space-Space-Time168Which block in the GSS handles administration ofconnection/disconnection ofspeech paths?GS169CALL CONFIRMED is a signal sentfrom the MS to the MSC for thepurpose of?Responding to SETUPsignal from the MSC170Which of the following is usedby the BTS and MS in providing security for the speech anddata over the air interface?Ki171Which command orders alarmsetting of device alarms?REALR172The subsystem that id concernedwith the PCM links is?RCS173The BSC consists of which ofthe following groups ofsubsystems?LHS, MTS, RCS, RTS,TAS, GSS, CCS andSTS174OSS is the Ericsson product for centralized control of the GSM Network. OSS is based on what Ericsson family of management product?SMAS175Which command is used to definea combined report?SDRSI176Which command is used toinitiate the Call Path Tracing function(in bsc)?RACPI177When troubleshooting a class 1Afault, which commands are inthe proper order of executionwithout having to go anotherOPI?RXMFP, RXBLI, RXTEI,RXBLE178What is the input and outputinformation is GTT?input: GT, output:DPC179In System Level 2, the AXEexchange is divided into parts,what are they?Switching Part & AXEpart180Defining a new route isconsidered what activity in AXEexchange?Operational activity181In the ( ), a call attempted isimmediately rejected when thereis no idle device in theroute.Delayed System182How do you find a PrintedCircuit Board (PCB) in the exchange? By using command: EXDEP183If you find a command and donot understand how to expressthe parameters, which part ofALEX documents do you look for?OperationalInstruction184There are two SupportProcessors (SP) in IOG20, whatare they called?CP-A & CP-BB C D答案Mobility management Logical linkmanagementtowards the MSSubscriber addressespublish DThe CNA Table function is only used to display all or a subset of the parameters for a number of objects.The status of aconsistencycheck jobs canbe monitoredthrough the CNAJobs function.The RBSes (TGs) are movedby the BSM application.CIt increases the number of mobiles with high C/I.The powerconsumption inthe radio basestation isreduced.It reduces the number ofmobiles with low C/I.DTo b able to reuse frequencies To share RBSequipments To share PCM links D1300mm1400mm1500mm DPower Supply Unit (PSU)Transceiver Unit(TRU)Distribution Switch Unit(DXU)ASCCP ISUP TUP ABSRXMIN BSRXSUFF None of these A Dropped calls ofthe total number of calls terminated in the cell Erlang minutesper dropped TCHconnectionAverage call dropsexperienced during one hourtalk time BCDU DXU ABU CTemporary screens, used in the half-screen part of the urban model,are used to describe details with the actual placements of, for example, trees in this environment.The recursivemicro cell partof the urbanmodel usessomething calledthe illusorydistance, whichis always longerthan or equal tothe line-of-sight distance.The resulting path lossfrom the urban model isobtained by taking themaximum value of the twocontributions, calculatedby the half-screen andrecursive microcellalgorithms.DTCAP, SCCP MTP, SCP B10 or 20minutes 5 or 15minutes.C SDCCH/4 includingCBCH combined with CCCH on timeslot zero SDCCH/8 non-combined ontimeslot zeroSDCCH/8 including CBCH non-combined on timeslot one ADynamic Power Control DiscontinuousTransmission Cell Load Sharing DRX external FaultMap Class 2A, Faultcod 14TX VSWR alarm Mains Power failure alarm AGSM-algorithm Ciphering-algorithm ATCH or SDCCH first.Overlaid subcellas a last resortor not.Phase 1 or phase 2 mobiles.ABrief System Audit (BSA)SystemPerformanceReview (SPR)Radio Network Improvement(RNI)DAGBLK (reserves a paging block for access grant)Paging strategy(for example,second page inthe MSC servicearea or in theLA)Combined or non-combinedmapping DQ drop counter TA drop counter None of these D1300mm1400mm 1500mm D If the offset is non-zero If PSSTEMP is set to a low value If PTIMTEMP is set to a low value B120mm 70mm 360mmC Move away two local buses Move away all TRU power cables All of the aboveCTCAP SCCP TCAP CBSPWRBBSTXPWR BSPWRT CIt modifies the sufficient level condition for neighboring cells and the serving cell.It is used to move the L-L border.It is used to move the K-K border.B The required signal strength, plus the log-normal fading marginThe design criterion, minus the body loss The design criterionmultiplied by a"probability of coverage"factor A To ensure that the signal strength on the uplink isalways sufficient.To obtain an absolute signal strength ranking.To disable path loss ranking.C To set the initial value of the timer that controls the measurement events of the mobile.To set theinitial value of the timer that controls if handover during signaling is allowed or not.To set the initial value of the timer that controls if handover to another BSC is allowed or not.AFailed decoding ofSAACH frames Poor signal strengthExcessive timing advanceB5dB C.6dB8dB A 26 dBm60 dBm54 dBm DPath loss, minus antenna gain Path loss, minusantenna gain,plus feeder lossPath loss, minus antennagain plus feeder andcombiner losses CAbsolute signal strength Minimum signalstrength Sufficient signal strength ATo predict thetrafficdistribution in the future.To find therightfrequencies.To find the right hot-spotlocation.DPhase 2 establishment causes distinguish between MS originated call and answer to paging.Phase 2establishmentcausesdistinguishbetween locationupdating andanswer topaging.Phase 2 establishmentcauses distinguish betweenMS originated calls andSMS.DHO events Speech coder Timing advance DInter Cell Dependency Matrix InterferenceCombined withDownlinkMeasurementsInternal Cell DisturbanceMeasurements BIt is used as atemporary offset to make a cell appear better during cell re-selection.It is used as ahysteresisbetween locationarea borders.It is used in a limitedservice state to enableemergency calls.CIt is used tooffset the trigger conditions for a bad quality urgency handover.It is used toprevent a newhandover attemptin a cell afterhandoverfailure.It is used to restrict thedistance to a candidatecell, if a bad qualityurgency condition istriggered.DRayleigh fading margin and interference margin Rayleigh fadingmargin,interferencemargin, and bodylossRayleigh fading margin andbody loss CSuccessful repeated page attempts (in location area) of total number of repeated page attempts (in location area).Successful firstand repeatedpage attempts(in locationarea) of totalnumber of firstpage attempts(in locationarea).Successful first andrepeated page attempts (inlocation area) of totalnumber of first and secondpage attempts (in locationarea).CFrequency of callsetups Radius Antenna length CIt is the name of the counters of alternative A when they arestored/used in the STS later.It is the nameof the countersof alternative Bwhen they arestored/used inOSS later.ACell selection and reselection Read systeminformation Open loop power control DSDCCH/8 + SDCCH/42*SDCCH/82*SDCCH/8 + SDCCH/4CCurvature of the earth Diffraction lossdue toobstructingbuildingsTransmitter and receiverantenna effective heights DBSSAP OMAP SCCP B Replicable Units Logical Units BSSRAMPSI=10 and SSRAMPSD=10SSRAMPSI=5 andSSRAMPSD=2SSRAMPSI=2 and SSRAMPSD=5DC2 is a quality check and if not fulfilled, the idle mobile must try another cell to camp on.C2 and BSIC arereported to theserving cell, atleast, onceevery fiveseconds toenable networkcontrolled cellre-selection.At cell re-selection, thecell with the largestderived C2 is chosen tocamp on.DC1 is a quality check and if not fulfilled, the idle mobile must try another cell to camp on.C1 and BSIC arereported to theserving cell, atleast, onceevery fiveseconds toenable networkcontrolled cellre-selection.At cell re-selection, thecell with the largestderived C1 is chosen tocamp on.ARLGRP RLGSI C MALT RBLT TC CSI (Scanning Interval)BRP (BasicRecordingPeriod)CTesting of the RU@S in the cabinet Preventivemaintenance ofthe cabinet All of the above A600kHz200kHz25kHz BBSSAP OMAP SCCP B Replaceable Units Logical Units B。
几种典型无线传感器网络定位算法研究

几种典型无线传感器网络定位算法研究朱慧勇【摘要】无线传感器网络中的定位算法根据是否用到测距分为基于测距的定位算法与基于非测距的定位算法.文章根据这两种分类论述了TOA,AOA,TDOA,质心算法、APIT算法、Bounding-Box算法、凸规划算法等几种典型的无线传感器网络定位算法.【期刊名称】《江苏科技信息》【年(卷),期】2017(000)008【总页数】4页(P38-41)【关键词】基于测距的定位算法;基于非测距的定位算法;无线传感器网络【作者】朱慧勇【作者单位】西安铁路职业技术学院,陕西西安710014【正文语种】中文无线传感器网络中常用的测距技术有到达的时间[1](Time of Arrival,TOA),到达的角度[2](Angel of Arrival,AOA),到达的时间差[3](Time Different Of Ar⁃rival,TDOA),接收的信号强度指示[4](Received Sig⁃nal Strength Indicator,RSSI)。
凡是用到以上测距技术的定位算法都可以归于基于测距的定位算法。
反之为基于非测距的定位算法。
一般来说,基于非测距的算法不需要额外的硬件去获得距离信息,定位精确度不高,在成本和能耗上优于基于测距的算法。
基于非测距的定位算法主要有质心算法[5]、APIT算法[6]、Bounding-Box算法[7]、凸规划算法[8]等等。
下面按基于测距的定位算法与基于非测距的定位算法的分类来阐述几种典型的无线传感器网络定位算法。
1.1基于TOA的定位算法TOA测距技术的主要原理是发射信号的速度乘以时间,可以分为单程测距和双程测距。
单程测距:发射节点在时间t1发射信号,接收节点在时间t2收到信号。
假设信号的传播速度为v,于是发射节点到接收节点的距离d:d=v×(t2-t1) (1)单程测距对发射节点和接收节点要求严格的时间同步。
双程测距:发射节点在时间t1发射信号,接收节点在时间t2收到信号,接收节点然后在时间t3也发射信号给发射节点,发射节点在时间t4收到信号。
如何在Digi手机路由器上实现最大信号强度说明书

How to Achieve Maximum Signal Strengthwith Digi Cellular RoutersWhat tools do I have for determining signal strength?The best throughput comes from placing the device in an area with the greatest Received Signal Strength Indicator (RSSI). RSSI is a measurement of the Radio Frequency (RF) signal strength between the base station and the mobile device, expressed in dBm. The better the signal strength, the less data retransmission and, therefore, better throughput.•How do I read RSSI on the Digi cellular router?RSSI information is available from several sources:1. The LEDs on the device give a general indication (1-4 “bars”).2. Via the Digi device’s local user interface:http (Digi web interface > Information > System Info > Mobile)CLI command “display mobile” via telnet, SSH or local serial port connection (via HyperTerminal, TeraTerm or other emulation package) to the Digicellular router.3. Digi Connectware® Manager (Server Platform) can also display the value in dBmvia System Information screen.•What do the numbers mean?-101 dbm or less (0-1 LED) -> Unacceptable coverage-100 dbm to –91 dbm (1-2 LEDs) -> Weak Coverage-90 dbm to –81 dbm (2-3 LEDs) -> Moderate coverage-80 dbm or greater (4 LEDs) -> Good CoveragePre-install surveys can also be done using a data device such as Blackberry, Treo andeven cell phone. Check out this guide from WPS Antennas on how to use a cell phone fora basic site survey: /pdf/testmode/FieldTestModes.pdf.These data devices cannot provide a 100% reliable comparison to how a Digi cellularrouter will behave due to antenna differences, etc. Generally, if the other device worksokay, the Digi device should as well. As noted below, special antennas can usually helpin areas with marginal signal.What about placement?Placement can drastically increase the signal strength of a cellular connection. Often times, just moving the router closer to an exterior window or to another location within the facility can result in optimum reception.•Another way of increasing throughput is by physically placing the device on the roof of the building (in an environmentally safe enclosure with proper moisture and lightningprotection).o Simply install the device outside the building and run an RJ-45 Ethernetcable to your switch located in the building.o Keep antenna cable away from interferers (AC wiring).Antenna OptionsOnce optimum placement is achieved, if signal strength is still not desirable, you can experiment with different antenna options. Assuming you have tried a standard antenna, next consider: •Check your antenna connection to ensure it is properly attached. If you have the ConnectPort™ WAN VPN product, ensure the internal antenna connectors are alsoproperly connected.•Cabled antenna (Digi part # - DC-ANT-DBDT) has no dBm gain, but has 8-foot cable and magnetic base for attachment to metal ground plane.•High gain antenna (Digi part # - DC-ANT-DBHG), which has higher dBm gain and longer antenna.•Antenna boosters and directional antennas:o Companies such as sell signal enhancingtechnologies ranging from $100-$1000.Directional antennas are larger and take some time to set up but aretypically in the $150 price range. Also verify if the antenna is single- ordual-band. Single-band antennas require matching the signal from thecarrier. If you aren’t sure which frequency you carrier is using in aparticular location, you may contact WPS Antennas for assistance.Powered antenna boosters can be much more expensive, but are ofteneasier to set up.o Many cabled antennas require a metal ground plane for maximumperformance. The ground plane typically should have a diameter roughlytwice the length of the antenna.Does it help overall throughput to stack the devices at one location?No, do not stack multiple routers per location. Adding additional routers at the remote location will not increase throughput because the bottleneck becomes the limited EGPRS capable data timeslots allocated at the cell site. All data customers share the same timeslots. If you stack routers, you will simply be competing with yourself for data channels.NOTE:Another way of optimizing throughput is by sending non-encrypted data through the device. Application layer encryption or VPN put a heavy toll on bandwidth utilization. For example, IPsec ESP headers and trailers can add 20-30% or more overhead.Digi International ▪ 11001 Bren Road East ▪ Minnetonka, MN 55343 ▪ 952-912-3444 ▪*************©2006 Digi International Inc.。
Secure Spaces Location-based Secure Wireless
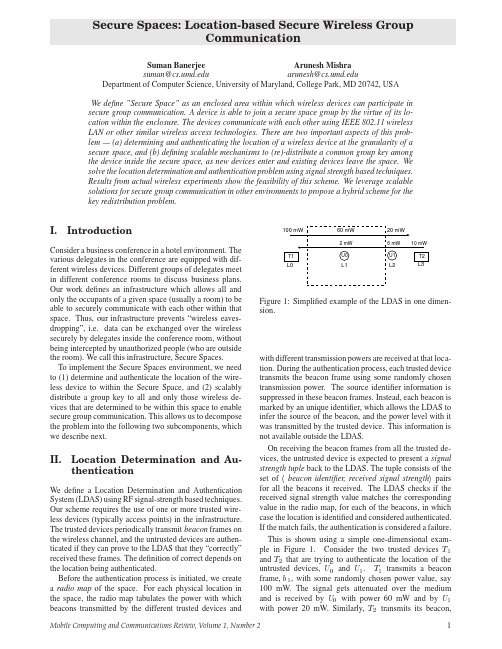
Zone MappingBit Map for each ZoneZone II Zone III Zone IV00011011signal strength range :Figure2:Mapping a zone to a bit-string for a trusted de-vice.,with another randomly chosen power value,say10 mW,which is received by with power2mW and by with power6mW.If and returns the signal-strength tuples as62and 26respectively,then their loca-tions are correctly determined and authenticated with re-spect to the radio map available at LDAS.For to mislead the LDAS to believe that its location as,it needs to return the signal strength tuple to be: 62,i.e.the tuple which is cor-rect for the location of.However,is not aware as to which trusted device transmitted which beacon(this bea-con source information is suppressed).Also,the trusted de-vice transmits each beacon with a randomly chosen power value.This prevents from using any location-based inference scheme to evaluate the correct received signal strengths at any other position for the different beacons.The security of the random power LDAS is based upon the anonymity of the beacon source and the random choice of power value with which the beacon is transmitted.In realistic scenarios,however,the signal strength mea-surements are never accurate due to channel fading,other sources of noise,and multipath effects.To mitigate the ef-fect of such measurement inaccuracies,we partition the received signal strength values into a set of equivalence classes,or zones.Typically received signal strength at dif-ferent rooms,in the business conference example,will fall in different zones for the same access points.Zones are separated by guard ranges.Such a coarse granularity of dif-ferentiation is sufficient in the Secure Spaces environment, since we are concerned in determining and authenticating location to the granularity of rooms.An untrusted device infers a location-specific authenti-cation key from the signal strength tuple as follows:The received signal strength of beacons from each access point corresponds to a zone,which in turn is mapped to a bit-string.This mapping is shown in Figure2.By concate-nating the bit-strings of different trusted devices in a deter-ministic sequence,the location-specific key is generated.For example,in Figure1,the signal strength tuple at lo-cation maps to zones3and1respectively for the two access points.Therefore the generated key,using the map-ping shown in Figure2,is the string.Clearly differ-ent rooms will have different location-specific authentica-tion keys.The untrusted device authenticates its location to the LDAS by encrypting a well-known text(together with some randomly chosen value to prevent re-play attacks)us-ing the location-specific authentication key and sending it to the LDAS server for verification.Our experimental data suggests that even by using a small set of trusted devices it is possible to distinguish between locations inside and outside such enclosed areas.III.Secure Group Communication Typical group communication systems rely on a single group key known to all and only the group members.Once this group key is securely distributed to all group members, secure messages can be exchanged by encrypting them with this key.The location-specific authentication key is used for location authentication and is not used for secure group communication.Instead,there is a single key server in the system that is responsible for generating location-specific communication keys for the secure spaces.Each device authenticated to be in a secure space needs the corresponding location-specific communication key for group communication within that space.Each time a new device moves into or an existing device departs from a secure space,a new communication key needs to be dis-tributed.All subsequent group communication in that se-cure space must use this new key.This is the process of group re-keying.We leverage the existing of three different schemes for group re-keying;the exact choice of the correct scheme de-pends on the number of devices that are located within the secure space.Thefirst scheme is called Pair-wise key ex-change.In this simple solution,the key server maintains a pair-wise key with each of the devices in the secure space (established using protocols like Diffie-Hellman[2]).On each change to the membership in the secure space,the key server chooses a new communication key and distributes it to each existing member encrypted by the correspond-ing pair-wise key.This scheme incurs overheads at the key server for storage,cryptographic operations,and communication.When the number of members at a se-cure space increases,we use other scalable mechanisms. The Key Graphs scheme[3]creates a hierarchy of keys to achieve scalability and incurs overheads at the key server.The Hierarchical clustering scheme[1]creates a hierarchy of members and asymptotically incurs overheads at the key server.Therefore,there exists a clear tradeoff between the sim-plicity of the key distribution scheme and its scalability. References[1]S.Banerjee and B.Bhattacharjee.Scalable SecureGroup Communication over IP Mulitcast.JSAC Spe-cial Issue on Networked Group Communication,20(8), October2002.[2]W.Diffie and M.Hellman.New directions in cryp-tography.IEEE Transactions on Information Theory, 22(6),November1976.[3]C.K.Wong,M.Gouda,and m.Secure groupcommunications using key graphs.Proceedings of Sig-comm,September1998.2Mobile Computing and Communications Review,Volume1,Number2。
面向狭小封闭战场环境的群智感知定位算法研究

第45卷第6期2023年12月指挥控制与仿真CommandControl&SimulationVol 45㊀No 6Dec 2023文章编号:1673⁃3819(2023)06⁃0036⁃05面向狭小封闭战场环境的群智感知定位算法研究李耀宇1,陈㊀杰1,魏㊀勇2(1.国防科学技术大学信息系统工程重点实验室,长沙㊀410073;2.中国人民解放军31015部队,北京㊀100091)摘㊀要:为解决在狭小封闭的战场环境,如敌方指挥中心㊁船舱㊁地下建筑物中,如何快速准确地获取自组织网络或目标对象的位置信息的问题,基于单兵智能终端设备提供的通信模块,利用可见光传感器等硬件设备的支持,通过研究群智感知式的通信信号指纹,结合图像匹配算法,提出了一种定位算法㊂该算法利用通信指纹数据实现了初步定位,结合融合图像和姿态传感器的加权平均算法,并采用群智感知方式补充与更新定位数据,通过调整图像匹配策略,在保持准确率的前提下,相比单一图像匹配定位算法,降低了算力的需求,在通信条件复杂的战场环境中提高了实时性能㊂对比标准的WKNN(WeightedK⁃NearestNeighbors)算法,提高了在复杂环境下定位的稳定性,且定位误差平均值低于1 72m,误差降低约50%㊂关键词:狭小战场;群智感知;定位算法中图分类号:E917㊀㊀㊀㊀文献标志码:A㊀㊀㊀㊀DOI:10.3969/j.issn.1673⁃3819.2023.06.006Researchoncrowd⁃sourcedlocalizationalgorithmfornarrowandclosedbattlefieldenvironmentLIYaoyu1,CHENJie1,WEIYong2(1.ScienceandTechnologyonInformationSystemsEngineeringLaboratory,NationalUniversityofDefenseTechnology,Changsha410073,China;2.Unit31015ofPLA,Beijing100091,China)Abstract:Inordertosolvetheproblemofhowtoquicklyandaccuratelyobtainthelocationinformationofself⁃organizingnet⁃worksortargetobjectsinthenarrowandclosedbattlefieldenvironment,suchastheenemycommandcenter,cabins,andun⁃dergroundbuildings,thispaperproposesapositioningalgorithmbasedonthecommunicationmoduleprovidedbyindividualin⁃telligentterminalequipment,weusethesupportofhardwaredevicessuchasvisiblelightsensors,andstudythecommunicationsignalfingerprintofswarmintelligenceperception,combinedwithimagematchingalgorithm.Thisalgorithmmainlycommuni⁃cateswithfingerprintdatatoachievepreliminarypositioning,combinesaweightedaveragealgorithmoffusedimagesandatti⁃tudesensors,andusesswarmintelligenceperceptiontosupplementandupdatepositioningdata.Byadjustingtheimagematc⁃hingstrategy,whilemaintainingaccuracy,comparedtoasingleimagematchingpositioningalgorithm,itreducescomputationalpowerrequirementsandimprovesreal⁃timeperformanceinbattlefieldenvironmentswithcomplexcommunicationconditions.ComparedwiththestandardWKNN(WeightedK⁃NearestNeighbors)algorithm,itimprovesthestabilityoflocalizationincomplexenvironments,andtheaveragelocalizationerrorislessthan1 72m,reducingtheerrorbyabout50%.Keywords:narrowbattlefieldenvironment;crowd⁃sourced;localizationalgorithm收稿日期:2023⁃03⁃17修回日期:2023⁃04⁃11作者简介:李耀宇(1984 ),男,副教授,研究方向为军事运筹㊁任务规划㊁建模与仿真㊂陈㊀杰(1985 ),男,副教授㊂㊀㊀现代战争中,位置信息的重要性不言而喻㊂准确的位置信息是指挥和决策的基础㊂室外环境中,定位可以采用卫星定位等多项技术,但是在狭小封闭的战场环境,例如特种作战所面对的地方指挥所㊁地下大型掩体设施㊁舰船内部等区域,位置信息的获得极为困难㊂首先,无法预先获得准确的先验信息,因为室内的情况不稳定,变化大,也没有公开的地理环境信息供参考;其次,电磁通信信号衰减,通风采光条件差,遮蔽物遮蔽等,导致一般室外的定位技术无法获得良好的效果,必须采用合适的室内定位技术㊂随着光学传感和图像识别技术的发展以及单兵智能终端设备算力的提高,基于单兵智能终端设备的图像匹配定位开始受到青睐㊂单兵智能终端设备通常包括通信模块㊁图像采集模块㊁姿势和加速度等传感器,为室内定位算法提供了必要的硬件支持㊂单纯基于图像匹配的定位方案需要构建庞大的图像数据库,图像匹配过程对算力需求高,难以保证实时性㊂单纯基于通信信号指纹的定位技术,实时性能有保障,但通讯信号可能受到环境干扰影响,仅利用算法难以克服精度下降问题㊂要想提高室内定位的综合性能,通常需要综合以上方案的特点,同时结合单兵智能终端设备提供的各类传感器支持㊂1㊀研究现状目前有很多方法可用来实现辅助室内定位,LEE[1]提出了一种基于射频(RF,RadioFrequency)指纹识别第6期指挥控制与仿真37㊀的最大似然估计(MLE,MaximumLikelihoodEstimation)初始化,制定了结合RF指纹识别的目标定位的最大似然问题㊂在开放空间㊁城市和室内三种测试环境中,与使用SDP(Semi⁃DefiniteProgramming)初始化的MLE算法相比,所提出的射频指纹辅助目标定位方法表现出高达63 31%和平均39 13%的性能提升㊂WiFi指纹也是一种常用的方法,乐燕芬[2]提出了一种指纹子空间匹配结合密度峰值聚类的定位算法,有效避免了大误差点㊂首先通过在线阶段目标接收信号强度(RSS,ReceivedSignalStrength)的接入点覆盖向量,确定有效的参考位置点;然后划分多个指纹子空间,利用改进的WKNN(WeightedK⁃NearestNeighbors)算法估计目标在每个子空间内的位置;最后选取决策值最大的选定个数估计位置确定目标㊂聂大惟[3]提出了一种基于信号强度指示器RSSI(ReceivedSignalStrengthIndi⁃cator)概率分布与贝叶斯估计的加权定位方法㊂该方法在研究RSSI的平稳性㊁分布特性的基础上,通过贝叶斯估计将先验的RSSI概率分布引入权重的计算,给异常值赋予较低的权重,降低了环境噪声和外界不确定因素对定位精度造成的影响㊂KNN(K⁃NearestNeighbors)依然是常用的一种方法[4],Razavi提出了一种室内定位场景,该场景应用度量学习和流形对齐,使用具有单个RSS样本的低分辨率无线电地图实现直接映射定位(DML,directmappinglocalization),将指纹识别工作量减少了87%㊂对比之前的定位方法,DML和基于重建射电图的K最近邻(reKNN,K⁃NearestNeighborsBasedonReconstructedRa⁃dioMap)在面积约为170m2的典型办公环境中分别实现了小于4 3m和3 7m的平均定位误差㊂不同智能手机设备硬件性能有差异,RSSI信号特征的变化率也会有差异㊂在实际操作中,传统的室内定位解决方案可能无法应对硬件差异引起的信号差异[5]㊂Tiku提出了一种基于多头注意神经网络的室内定位框架,该框架对设备异质性具有弹性㊂对各种室内环境中提出的框架的深入分析表明,与当时最先进的室内定位技术相比,准确度提高了35%㊂Hoang[6]针对轨迹定位,考虑轨迹中接收RSSI测量值之间的关系,对输入RSSI数据和顺序输出位置提出了加权平均滤波器,提高了RSSI时间波动之间的准确性㊂2㊀算法总体设计2 1㊀算法总体方案算法目标是用户使用单兵智能终端设备的通信芯片与摄像头实现高精度室内定位,无需其他硬件辅助,坐标系采用二维坐标系,不考虑高程㊂算法主要包括两个阶段:离线阶段与在线阶段㊂离线阶段构建数据库时,在不同参考点依次记录RP(ReferencePoint)的坐标值㊁AP(AccessPoint)数量与对应的MAC地址(MediaAccessControlAddress)㊁RSSI值㊁该RP正前方图像,同时采集该时刻单兵智能终端设备所处姿态(即单兵智能终端设备方向传感器的倾斜角㊁旋转角和方位角),将上述信息上传至服务器后进行预处理,将特征向量编码为F={f0,f1,f2, ,fN}存储,其中,f0 fN代表特征分量㊂在线阶段,根据设备采集的特征进行定位,用户单兵智能终端设备实时扫描可接收到MAC地址作为指纹标识的AP和对应RSSI值,首先使用WKNN算法初步定位㊂本算法支持用户获取更高精度,即采用SIFT(Scale⁃InvariantFeatureTransform)图像和单兵智能终端设备姿态匹配算法提高定位精度㊂用户可将定位结果以及对应信号指纹和图像特征上传,即采用群智感知的方式补充和更新定位数据库[7],以辅助他人定位㊂在线阶段,算法总体方案如图1所示㊂2 2㊀加权K邻近无线通讯网络通信指纹定位算法加权K邻近算法在指纹定位中通过引入距离权重因子对AP点选择进行约束,离实测RSSI值距离越近的点权重越大㊂距离定义[8]如下:Lp(d,i)=ðn(RSSI(i,n)MN-RSSI(i,n)RP)p()1p(1)式中,i表示实测扫描到的RP点序号,n表示移动节点和RP之间的AP点数量,最后选择K个 距离 最小值作为最近邻居,并根据这K个 距离 值归一化得各自权重,归一化公式[9]为ωi=1/Lp(d,i)ðKi=1(1/Lp(d,i))(2)取p=2,根据数据库中RP点的已存坐标和归一化 距离 权重因子,得到移动节点的初始位置:Pi(xy)KWNN=ðKi=1{i㊃ωi,ðKi=1yi㊃ωi}(3)K值对定位结果有直接影响,图2通过仿真实验对比不同K值下的定位效果,从图中看出,K=3时定位平均误差最小,因此本文选择最近邻居数K为3㊂在线定位阶段利用用户获取的图像和方向传感器输出值,计算与K个参考点对应的数据库特征数据,得到图像匹配因子和方向因子,对已有参考点权重进行校正,提高定位精度㊂2 3㊀图像匹配定位算法2 3 1㊀图像匹配策略目前存在多种图像定位算法,例如Niu[10]用SURF38㊀李耀宇,等:面向狭小封闭战场环境的群智感知定位算法研究第45卷图1㊀算法总体流程Fig 1㊀Totalityalgorithmprocess图2㊀K值对定位的影响Fig 2㊀TheinfluenceofK⁃valueonpositioning(SpeededUpRobustFeature)进行图像匹配定位,SURF处理速度较快,但处理尺度缩放和旋转变化不是最优㊂本文选择SIFT算法[11],该算法对于图像平移㊁旋转㊁尺度缩放㊁亮度变化等具有很好的不变性,能够更好适应用户拍摄图像时发生的平移㊁旋转㊁缩放变化[12]㊂SIFT算法处理图像在服务器中进行,生成图像描述子,表示为Nˑ128维特征向量,并存储在数据库中,其中N为一张图像的特征点总数,用户实时拍摄的图像在单兵智能终端设备上经过SIFT算法得到同样维数的特征向量后,计算两组特征向量间的欧氏距离作为图像关键特征点的相似性度量[13]㊂据文献[14],在大量存在尺度缩放㊁旋转和亮度变化的两幅图像之间进行匹配时,度量阈值ratio取值在0 4 0 6之间最佳,经过仿真试验,ratio取值为0 55时,定位平均误差最小,如图3所示㊂图3㊀图像匹配度量阈值对定位精度的影响Fig 3㊀Theimpactofimagematchingmetricthresholdonpositioningaccuracy经WiFi初步定位,假设得到的3张图片表示为I(DB,i)(i=1,2,3),各自提取特征总数F(DB,i),用户实际拍摄图像表示Is,提取特征总数为Fs,分别计算拍摄图像和数据库图像之间的共同特征数Fc:Fc=(FDB,iɘFs)ɪ[0,min(F(DB,i),Fs)](4)求得Fc后再求解匹配因子,同时用图像匹配因子第6期指挥控制与仿真39㊀校正WiFi定位得归一化 距离 权重因子,图像匹配因子定义为ηi⇒argmax(F(DB,i)ɘFsF(DB,i)+F(DB,i)ɘFsFs)(5)由定义可知,η的取值范围为[0 0,2 0],值越大,表示两张图像越相似㊂本文对根据WKNN算法选择的3张图像进行求解图像匹配因子后,选择最大的图像作为配对图像㊂用户所拍摄的图像压缩后的大小为1034ˑ731,特征提取Fs=714,对表1中样本a c分别提取特征,并求得图像匹配因子㊂表1㊀特征数量与图像匹配因子Tab 1㊀Numberoffeaturesandimagematchingfactor名称F(DB,i)Fcηi样本a6596471 888样本b6435631 664样本c6284891 6641 464㊀2 3 2㊀传感器限制图像方向随机性用户在同一位置拍照方向存在随机性,故经过无线通信网络通信指纹初步定位,不能确定数据库中所存图像所表示的方向和用户当前拍照方向的一致性,因此,本算法采用单兵智能终端设备方向传感器输出三维方向参数匹配单兵智能终端设备姿态来解决这一约束㊂假设用户拍照时刻记录单兵智能终端设备传感器输出的倾斜角㊁旋转角和方位角三维向量可表示为{θx,θy,θz},经初步定位找到的3个RP对应方向向量值表示{θxi,θyi,θzi},则方向向量值之间角度差为Δθi=(θx-θxi)2+(θy-θyi)2+(θz-θzi)2(6)方向因子ζ是每一组值所占的归一化权重,根据角度差的倒数来计算:ζi=1/ΔθiðKi=1(1/Δθi)(7)式中,K表示最近邻居数㊂2 3 3㊀基于图像和姿态匹配定位算法在上述过程中,通过SIFT算法,已经求得每张图像的匹配因子和方向匹配因子,为了校正初步定位,采用加权平均法来融合上述的3个因子,如图1所示,得到校正因子,定义校正因子ξ为ξi=ωi+ηi+ζiðKi=1(ωi+ηi+ζi)(8)最后校正定位用户的位置计算式为Pi(x,y)ImageMatch={ðKi=1xi㊃ξi,ðKi=1yi㊃ξi}(9)上两式中,K=3表示最近邻居数,i=1,2,3表示匹配得到的图像序号㊂2 4㊀群智感知方式更新数据库随着室内布局以及环境变化,室内信号指纹分布会发生改变,本文支持用户将实时测量到的信号指纹与图像上传至数据库,增加可用的参考点数量㊂采用群智感知更新数据库可以降低构建数据库的复杂性,维持数据库数据的实时性;在某些没有离线采集数据的区域,用户上传数据后,可辅助他人下次定位使用㊂在群智感知中,感知设备的多样性会造成无线通信网络通信指纹和方向向量的差异,本文采用同一款单兵智能终端设备,简化了设备多样性的影响,同时,对于错误感知数据的筛选,本文提出使用位置估计值P和RSSI两个值之间的相关系数因子作为数据剔除的依据,该因子的计算式为ρ=ði=1(Pi- P)(RSSIi-RSSI)ði=1(Pi- P)2ˑðKi=1(RSSIi-RSSI)2(10)式中,i=1,2, ,K,Pi为第i个RP坐标, P为定位估计坐标和K个RP坐标的平均值,RSSIi为第i个RP点的RSSI均值,RSSI为用户扫描RSSI值和K个RP的RSSI值㊂其中,ρ值与位置估计值和值呈正相关关系,据此可以控制数据质量㊂3㊀实验与数据分析3 1㊀实验设置为方便计算,本文用手机替代单兵智能终端设备进行测试,同时用WiFi替代专用通信网络,在覆盖面积1250m2的室内环境中开展实验,验证本文的算法㊂利用室内环境已有的WiFi热点进行定位模拟专有通信网络的定位㊂实验离线阶段,采集WiFi信号指纹构建数据库,采集的相应图像和三维方向向量作为特征向量在数据库中存储㊂离线阶段共随机采集150个RP点指纹和图像数据㊂3 2㊀数据分析图4为实测阶段WKNN算法定位和图像定位的累计分布函数CDF对比图,每组实验定位50次㊂从图中可以看出,新算法能够有效地提高定位精度,WKNN算法定位误差在2m以内的概率约为31 9%,但经过图像匹配定位校正的概率约为69 1%;当CDF为80%时,新算法为3m,WKNN算法定位约为4m,提高了25%㊂实测结果证明,算法能够提高定位精度㊂图5和图6是随着用户上传数据的增加,不同算法定位误差和方差对比曲线㊂从图5可以看出,随着用户参与,参考点数目从10增加到400,WKNN算法定40㊀李耀宇,等:面向狭小封闭战场环境的群智感知定位算法研究第45卷位误差从561m降低到3 50m,降低了376%㊂图4㊀定位累计分布函数图Fig 4㊀Locationcumulativedistributionfunctiondiagram图5㊀群智感知定位误差均值Fig 5㊀Meanvalueofgroupintelligenceperceptionpositioningerror与此同时,新算法定位误差从5 67m降低到1 71m,降低了69 8%㊂两算法纵向对比,当参考点为10时,两算法定位误差接近㊂随着参考点数量的增加,新算法逐渐好于原算法,当参考点数量为400时,新算法比原算法定位误差降低了50%㊂从图6可以看出,随着参考点数量增加,两种算法定位误差方差呈下降趋势,但新算法定位方差低于原算法,表明新算法定位稳定性较好㊂群智感知方式用于定位时,整个图像数据库数据量随时间推进而增加,而检索整个数据库寻找目标图像所需时间与图像数量呈正比,因此,本文采用WKNN算法邻居数K值限制图像检索范围,有效控制图像检索消耗的时间,在图像处理完成后,本文采用的结合WKNN和图像匹配的定位算法耗时如图7所示㊂实验设定位置更新频率为1Hz,图7中,ImageMatch表示算法的定位耗时,由于两张图像在匹配时存在多个共同点,每个特征点为1ˑ128维向量,计算耗时较大,但是均在1s以内,能够保证软件在自动图6㊀群智感知定位误差方差Fig 6㊀Varianceofgroupintelligenceperceptionpositioningerror图7㊀算法定位耗时Fig 7㊀Algorithmlocalizationtimeconsumption刷新时的定位实时解算要求㊂3 3㊀实验局限性分析实验数据表明,本文所提算法集成单兵智能终端设备后,大部分条件下,既改进了定位解算精度,又提高了实时性和稳定性,且降低了算力需求㊂本实验也存在两点局限性㊂一是采用单一设备进行实验,忽略了设备差异性带来的特征数据偏差问题,例如不同设备在相同位置,RSSI值如果差异过大,可能会影响定位精度㊂同时,设备之间的相互影响以及相互影响可能导致的不良后果,还需要进一步的研究和实验来证明㊂二是环境干扰对算法的影响考虑不足,特别是群智感知的控制策略方面,信号干扰容易造成数据明显错误,下一步研究会考虑引入过滤机制,防止错误的数据污染整个数据库㊂4㊀结束语本文针对无线通信网络通信指纹和图像匹配定位存在的问题,采用通信信号指纹辅助图像匹配定位思第6期指挥控制与仿真41㊀路,通过算法研究和实验融入了群智感知机制并进行了改进,对于解决狭小封闭的战场环境中的定位问题,具备积极的参考价值㊂当前,机器学习技术已经广泛地应用于很多领域,相关的研究也越来越多㊂未来可以考虑结合深度学习网络,特别是循环神经网络,引入状态转移控制机制,进一步提高定位的准确性和实时性㊂参考文献:[1]㊀LEEH,KANGT,JEONGS,etal.EvaluationofRFfin⁃gerprinting⁃aidedRSS⁃basedtargetlocalizationforemer⁃gencyresponse[C].2022IEEE95thVehicularTechnologyConference:(VTC2022⁃Spring),Helsinki,2022:1⁃7.[2]㊀乐燕芬,许远航,施伟斌.基于DPC指纹子空间匹配的室内WiFi定位方法[J].仪器仪表学报,2021,42(11):106⁃114.LEYF,XUYH,SHIWB.WiFifingerprintbasedindoorpositioningwithsubspacematchingandDPC[J].ChineseJournalofScientificInstrument,2021,42(1):106⁃114.[3]㊀聂大惟,朱海,吴飞,等.基于RSSI概率分布与贝叶斯估计的加权定位方法[J].全球定位系统,2022,47(2):52⁃59.NIEDW,ZHUH,WUF,etal.WeightedpositioningmethodbasedonRSSIprobabilitydistributionandBayesianestimation[J].GNSSWorldofChina,2022,47(2):52⁃59.[4]㊀RAZAVIA,VALKAMAM,LOHANES.K⁃meansfin⁃gerprintclusteringforlow⁃complexityfloorestimationinindoormobilelocalization[C].2015IEEEGlobecomWorkshops(GCWkshps),SanDiego,2016:1⁃7.[5]㊀TIKUS,GUFRAND,PASRICHAS.Multi⁃headattentionneuralnetworkforsmartphoneinvariantindoorlocalization[C].2022IEEE12thInternationalConferenceonIndoorPositioningandIndoorNavigation(IPIN),Bei⁃jing,2022:1⁃8.[6]㊀HOANGMT,YUENB,DONGXD,etal.RecurrentneuralnetworksforaccurateRSSIindoorlocalization[J].IEEEInternetofThingsJournal,2019,6(6):10639⁃10651.[7]㊀刘春燕,王坚.基于几何聚类指纹库的约束KNN室内定位模型[J].武汉大学学报(信息科学版),2014,39(11):1287⁃1292.LIUCY,WANGJ.ConstrainedKNNindoorpositioningmodelbasedonagrometricclusteringfingerprintingtech⁃nique[J].GeomaticsandInformationScienceofWuhanUniversity,2014,39(11):1287⁃1292.[8]㊀SAHAA,SADHUKHANP.Anovelclusteringstrategyforfingerprinting⁃basedlocalizationsystemtoreducethesearchingtime[C].2015IEEE2ndInternationalConferenceonRecentTrendsinInformationSystems(Re⁃TIS),Kolkata,2015:538⁃543.[9]㊀LEECW,LINTN,FANGSH,etal.Anovelcluste⁃ring⁃basedapproachofindoorlocationfingerprinting[C].2013IEEE24thAnnualInternationalSymposiumonPer⁃sonal,Indoor,andMobileRadioCommunications(PIM⁃RC),London,2013:3191⁃3196.[10]NIUJW,RAMANAKV,WANGBW,etal.Arobustmethodforindoorlocalizationusingwi⁃FiandSURFbasedimagefingerprintregistration[C].GUOS,LLORETJ,MANZONIP,etal.InternationalConferenceonAd⁃HocNetworksandWireless,Cham:Springer,2014:346⁃359.[11]KAWAJIH,HATADAK,YAMASAKIT,etal.Image⁃basedindoorpositioningsystem:fastimagematchingusingomnidirectionalpanoramicimages[C].Proceedingsofthe1stACMInternationalWorkshoponMultimodalPervasiveVideoAnalysis,Firenze,2010:1⁃4.[12]常强,SamuelVande,王维平,等.行人航迹推测辅助的Wi⁃Fi信号指纹定位算法[C].第六届中国卫星导航学术年会,西安,2015:729⁃739.CHANGQ,SAMUELVD,WANGWP,etal.Wi⁃Fifingerprintpositioningupdatedbypedestriandeadreckoningformobilephoneindoorlocalization[C].The6thChinaSatelliteNavigationConference,Xi an,2015:729⁃739.[13]LOWEDG.Distinctiveimagefeaturesfromscale⁃invariantkeypoints[J].InternationalJournalofComputerVision,2004,60(2):91⁃110.[14]WANGLY,ZHANGDQ,WANGYS,etal.Sparsemobilecrowdsensing:challengesandopportunities[J].IEEECommunicationsMagazine,2016,54(7):161⁃167.(责任编辑:张培培)。
WiFi中多AP间快速切换的研究与实现

1212009年第11期,第42卷 通 信 技 术 Vol.42,No.11,2009 总第215期 Communications Technology No.215,Totally·网 络·WiFi 中多AP 间快速切换的研究与实现滕 劲, 徐昌庆(上海交通大学 无线通信研究所,上海 200240)【摘 要】目前,WiFi 已经成为了高速无线局域网的主要标准并且得到了广泛的应用。
鉴于WiFi 网络接入点(AP )覆盖范围小、移动用户需要频繁切换的特点,文中提出了多AP 连接和嗅探扫描两种技术来实现多AP 间的快速切换。
多AP 连接通过同时和多个AP 保持通信切实保障了通信连续性,而嗅探扫描为更有效地获取周围AP 信息提供了指导性方法。
实验表明这些技术有效地加快了切换的速度,有效保障了用户的QoS 。
【关键词】WiFi ;切换;多AP 连接;嗅探【中图分类号】TP393.17 【文献标识码】A 【文章编号】1002-0802(2009)11-0121-03Study and Implementation of Fast Inter-AP Handoffs in WiFi WLANTENG Jin, XU Chang-qing(Institute of Wireless Communication, Shanghai Jiaotong University, Shanghai 200240, China)【Abstract 】WiFi has become one of the major high-speed WLAN protocols and has been widely applied recently. Due to the fact that WiFi Access Points (AP) could cover only a small area and mobile users have to make frequent handoffs among them, this paper proposes two techniques to enable fast handoffs, namely multiple AP connections and Sniff Scan. Multiple AP connections ensure the communication continuity by simulatneously keeping communication with several APs, while Sniff Scan provides guiding methodology for efficient acquisition of nearby AP information. Experiments on real test-beds show that the these two techniques could accelerate the handoff processes and ensure the user ’s QoS.【Key words 】WiFi; handoff; Multiple-AP-Connection; sniffing0 引言无线网络介入技术使得人们从繁琐的物理连线中解放出来,给予了人们更大的自由度和灵活性。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Study of Received Signal Strength Indication in ZigBee Location Cluster for Indoor Localization Kamol Kaemarungsi#, Rachasak Ranron*, Prasit Pongsoon##National Electronics and Computer Technology Center (NECTEC)Pathumthani, Thailand1kamol.kaemarungsi@nectec.or.th3prasit.pongsoon@nectec.or.th*King Mongkut’s University of Technology North Bangkok (KMUTNB)Bangkok, Thailand2ratchasak.ranron@Abstract— This work focuses on the properties of received signal strength indication (RSSI) of ZigBee wireless sensor network, which can be used to implement indoor location system. The study collects a set of measurement samples in a closed room from an implementation of indoor localization application based on ZigBee Cluster Library (ZCL) framework. The measurement data are analyzed for their statistical parameters. The results are compared with the known properties of RSSI of wireless local area network reported in the literature. The insight of RSSI’s properties obtained in this work could be used to improve the localization application using ZigBee wireless sensor network. Keywords— Indoor localization, location fingerprint, received signal strength indication, wireless sensor network, ZigBeeI.I NTRODUCTIONWireless sensor network (WSN) such as ZigBee WSN can be deployed with localization capability, which can be applied for localization and tracking of object or people in health care applications [1]. That is the wireless sensor network can be used to relay location information and radio frequency (RF) channel parameters in order to estimate a location of mobile wireless sensor node [2]. The underlying framework for localization mechanism is outlined by the ZigBee Alliance in ZigBee Cluster Library Specification [2]. The crucial RF channel parameter used for locating a mobile node is the received signal strength indication (RSSI) reported in decibel milliwatt (dBm), which can be derived from Link Quality Indication (LQI) defined by the IEEE 802.15.4 standard [3]. Typically, the LQI associates with a received IEEE 802.15.4 packet and is used to provide strength and/or quality of the packet. It can be obtained from the hardware of IEEE 802.15.4/ZigBee’s RF transceiver such as MC1322x system-on-chip (SoC) platform from Freescale semiconductor [4]. In the literature, indoor positioning systems using wireless sensor network and their implementations have been presented in a number of research works since 2006. For instance, an implementation of ZigBee indoor location system was presented in [5] using Chipcon (now Texas Instrument)’s CC2420 RF transceiver and a ZigBee stack on ATmega128 microcontroller. The user’s position in [5] was estimated using both ultrasound and time-of-arrival (ToA) of RF signal. However, the authors did not report any measurement of the RSSI. Measurements of LQI versus transmitter-receiver distance using Jennic’s JN5121 and Texas Instrument’s CC2430 SoC were reported in [6] in which the authors used the measurement data to create path loss models in two different environments. The authors in [6] reported that they implemented a centralized localization algorithm that combines multidimensional scaling (MDS) and maximum likelihood estimator (MLE) methods to estimate distance between transmitter and receiver on a laptop.A study on variation of received signal strength in WSN due to various environmental factors using CC2430 was presented in [7]. The authors investigated on the influence of the temperature, the height of node’s position, the type of antenna, and the electromagnetic interference of human body on the RSSI. An interesting finding was pointed out that the RSSI could change according to the temperature. The larger attenuation of RF signal was observed when the surrounding temperature was higher. The effects of the rest of the factors on RSSI were similar to common understandings of RF propagation. Another experimental study on the variation of RSSI due to the effects of obstacles in indoor environment was reported in [8]. The measurement experiments were performed using RF230 and CC2420 RF transceivers. The authors in [8] investigated the attenuation of RSSI over different distances in both line-of-sight (LoS) and non line-of-sight (NLoS) environments. In the NLoS case, there were three types of obstacles between transmitter and receiver, which were glass (glazed door), glass and wood (compressed wood), and partial wall (brick and gypsum board). The authors concluded that the RSSI alone could not be used to accurately locate mobile nodes in an indoor environment with obstacles [8].Based on our literature survey, none of the existing research works has implemented the ZigBee’s RSSI location cluster in their systems. Moreover, none of them has considered the statistical properties of the RSSI such as its probability distribution and skewness. Therefore, in this work we implemented a ZigBee localization system using the framework of ZigBee Cluster Library (ZCL) and performed a data collection of RSSI over a small and closed laboratory room. The main objective of this work is to comparethestatistical properties of RSSI in ZigBee WSN with the known properties of RSSI in wireless local area network (WLAN) or Wi-Fi network reported in the literature.The organization of this paper is as follows. Section II describes the architecture of the indoor localization system, which consists of both hardware and software components. Section III explains the experimental design. Section IV reports on the measurement results. Section V discusses our findings on the properties of the RSSI from the ZigBee localization system. Finally, Section VI concludes our work and outlines the future work.II.S YSTEM A RCHITECTUREAn indoor localization system used in this study is implemented on a set of ZigBee wireless sensor nodes developed in our research laboratory. The network comprises of five ZigBee nodes in which there are four fixed nodes and one mobile node. One of the fixed nodes is connected to a laptop computer via a RS232-to-USB serial interface and the node is the ZigBee coordinator (ZC). The rest of the nodes in the network are implemented as ZigBee routers (ZR). The implemented localization system can be categorized as a centralized architecture as described in ZigBee Telecom Application Profile Specification [9]. The two-dimensional locations in this system are identified using Cartesian coordinate system or pair of numerical coordinates. Generally, ZigBee localization system can be implemented using four different techniques as outlined by ZigBee Cluster Library Specification [2], which are the lateration, the proximity or the signposting, the RF fingerprinting, and out-of-band localization device. First three of these techniques rely on the measurement of RSSI, while the last technique depends on non-ZigBee based device connected to each node to provide location information such as infrared or ultrasound localization device. In this work, the implemented system utilizes the RF fingerprinting technique that can be deployed in two phases: the offline phase and the online phase [10]. During the offline phase, the system must collect the RSSI patterns at each location and create a database of RF fingerprints, which will be used during the online phase to estimate a location based on the closest matching of RF fingerprint with the current RSSI pattern at a location.The rest of this section described three important parts of our ZigBee localization system. First, a brief description of ZigBee Location Cluster, which is implemented in a commercial ZigBee protocol stack, is explained. Second, the hardware and its characteristics are summarized. Third, a personal computer (PC) based localization application developed for controlling and visualizing the localization system is presented.A.ZigBee Location ClusterZigBee specification defines a cluster as standardized communication interface between ZigBee client and server devices. Inside each cluster, there is a collection of attributes and commands used by specific ZigBee application. For instance, ZigBee’s RSSI Location Cluster is defined in ZigBee Cluster Library (ZCL) and given a unique Cluster ID of 0x000b. The location cluster enables ZigBee devices to exchange relevant location information and channel parameters for localization application and optionally report collected data such as RSSI from networked devices to a centralized device which estimates locations of mobile nodes [2]. In this work, we utilize all these mechanisms inside the ZigBee protocol stack.Examples of related attributes, which are arranged into different sets, in the RSSI Location Cluster are location type, location method, location age, quality measure, number of devices, coordinates, power, path loss exponent, reporting period, calculation period, and number of RSSI measurements [2]. Some of these attributes are mandatory. Examples of related commands in this cluster are Set Absolute Location, Set Device Configuration, Get Device Configuration, Get Location Data, RSSI response, Send Pings, and Anchor Node Announce [2]. The cluster also defines payload format of each command and action upon receiving a command such as setting relevant attributes. Some of these attributes and commands are implemented in this work.Fig. 1 illustrates the ZigBee localization system deployed in this study. The nomenclature of each ZigBee node is defined in ZigBee Telecom Application Profile Specification [9]. The fixed node with a known location is called the anchor node, while the mobile node is called the location node. The centralized node that collects the RSSI data from all other nodes and relays the data to a computer is called the locationgateway.Fig. 1 ZigBee Localization System Architecture.The usage of ZigBee’s RSSI Location Cluster is summarized in Fig. 2 and can be explained as follows [2]. Initially, the location gateway, which is the centralized device, receives commands called “Anchor Node Announce” from all anchor nodes after they joined the network. If the localization system wants to locate the mobile location node, the location gateway will issue a “Send Pings” command to the location node. Upon receiving the “Send Pings” command, the location node will periodically send multiple “RSSI Ping” commands to all its single-hop anchor nodes in our system. Each anchor node that received “RSSI Ping” command will measure the RSSI of each “RSSI Ping” command and calculate an averagevalue of multiple RSSIs for the sending location node. Next, the location node will issue the “RSSI Request” command to all single-hop anchor nodes to ask for its averaged RSSI values. Each anchor node will reply to the requesting location node with “RSSI Response” command that contains coordinate data of the anchor node, the averaged RSSI value, and the number of RSSI measurements. Finally, the location node will send “Report RSSI Measurements” command to the location gateway to provide its measurement for localization.Fig. 2 RSSI Location Cluster Usage.B.ZigBee Wireless Sensor NodesFig. 3 shows the set of actual ZigBee wireless sensor nodesused in our experiment. There are two types of printed circuitboards (PCBs): the large board and the smaller board which isthe one in the middle of the figure. The different between thetwo types of the boards are the number of peripheralinput/output (I/O) interfaces in which the smaller board has noI/O connectors and is suitable for equipping as a mobiledevice and operating on small battery. The larger board hastwo RS232 serial interfaces, which can be used to connect to alaptop computer.Fig. 3 Actual ZigBee Wireless Sensor Nodes.The main component of each node is the ZFSM-201-1module from California Eastern Laboratories (CEL) [11]. Thisis an integrated transceiver module for ZigBee/IEEE 802.15.4that is based on Freescale’s MC13224V SoC platform [4] andan additional RF power amplifier front end. The MC13224Vitself is actually contained both IEEE 802.15.4 RF transceiverand a low power 32-bit ARM7TDMI-S microcontroller. TheMC13224V possesses the ability to report LQI for a receivedpacket. The LQI is an 8-bit hexadecimal value from 0x00 to0xFF defined in IEEE 802.15.4 standard [3]. The value 0xFFis approximately equal to -15dBm, while the value 0x00 isapproximately equal to -100dBm [4]. The reference manual ofthe MC13224V defines the conversion expression between theRSSI or the power in dBm and the LQI in decimal as [4]:1003)()(−=decimalLQIdBmRSSI(1)The embedded software of each ZigBee node is developedbased on proprietary software templates and a proprietaryZigBee Stack called Freescale BeeStack [12], which is writtenin C programming language. Note that the ZigBeecoordinator’s and ZigBee router’s codes are different and haveto be modified independently. The provided softwaretemplates did not implement the RSSI Location Cluster andwe implemented additional codes to enable the localizationability in the system. The communication interface betweenthe location gateway and the laptop computer in Fig. 1 isbased on the Freescale’s BeeStack BlackBox ZigBee TestClient (ZTC) application programming interface (API) [13].The API defines the frame format of message exchangingbetween the location gateway and the laptop computer.The ZigBee network parameters are set as followings. TheZigBee stack profile is selected as Stack Profile 0x02, whichis the ZigBee PRO 2007 specification. The network topologyis formed as a mesh network without enabling securitymechanism. The maximum transmit power of each node is setto 20dBm. The RF channel is chosen as channel number 14 asdefined by IEEE 802.15.4 specification in 2.4GHz ISM band.The personal area network identification (PANID) is set to0x1aff.C.ZigBee Location ApplicationA PC software application is developed in this work usingJAVA programming language to provide graphical userinterface (GUI) for both ZigBee localization systemmanagement and visualization. After connecting the gatewaynode through the USB port of the laptop, the user can start theconnection to begin a communication with the gateway nodevia a play command icon. The application can automaticallydetect all nodes that have joined the ZigBee network. Then, itallows the user to perform each detected node’s placement ona map and to collect RF fingerprint of the location node ondifferent locations during the offline phase. The applicationutilizes proprietary Freescale’s ZTC API to communicate withthe location gateway node in which it allows the user to sendcommands to and gather the RSSI data from the ZigBeenetwork. Moreover, the application maintains a database ofRF fingerprints, which are collected through the locationgateway node. It also performs location estimation algorithm and shows the estimated location of mobile node on the map during the online phase. Initially, we implemented a simple algorithm using the single nearest neighbour pattern classification based on the Euclidean distance between the RF fingerprints in the database and the new RSSI pattern collected during the online phase.Fig. 4 is a screen capture of the developed PC application. There is a map on the right hand side of the screen that shows all location fingerprints (denoted by fingerprint icons) and thepositions of the gateway (denoted by small computer icon) and anchor nodes (denoted by base station icons). On the left hand side of the screen, there is a device list that itemizes all nodes with their IEEE 802.15.4 medium access control (MAC) addresses under their corresponding type of node. Note that the list of all RF fingerprints and their corresponding three dimensional coordinates (denoted by X, Y, Z) are also displayed. Note that all Z-axis values are zeros because we only use two-dimensional localization system in this work.Fig. 4 Screen Capture of ZigBee Localization Application.III.E XPERIMENTAL S ETUPThis section describes the preparation of the ZigBee wireless sensor network inside a small laboratory room for our measurement experiment. Fig. 5 illustrates a localization area which is defined as a square grid of locations with grid spacing of 1.4m×1.4m inside a small laboratory room. The positions of all ZigBee nodes are also labelled as L1 to L24 in the figure. There were 24 locations inside this room which were used to collect RF fingerprints. The anchor nodes are labelled with A1 to A4. There is no large obstacle that block in between any transmitters and receivers. This can be considered as an environment with clear line-of-sight (LoS). To form the ZigBee wireless sensor network, the location gateway was powered on first at the lower right corner of the Fig. 4 and connected to the laptop that ran our localization application as shown in Fig. 6. Then, we placed the rest of the anchor nodes at the other three corners as shown in the figure. After all nodes were detected, we sent a command via PCapplication to set their Cartesian coordinates.Fig. 5 Grid of locations with the positions of all nodes.Fig. 6 A photograph of the gateway node in the test room.The user collected the RF fingerprint during the offline phase at each location through the application’s command after placing the actual location node at that location. The process was repeated until RF fingerprints were collected for all locations. In this work, each sample of RF fingerprint consists of four different RSSI samples from the location gateway and the three anchor nodes. Note that the location gateway node also acted as an anchor node. We collected 30 RSSI samples from each anchor node at each location and averaged them out to obtain one of the components in the RF fingerprint. The sampling rate was one sample every nine seconds. Thus the measurement period per location was 9×30 = 270 seconds or 4.5 minutes. Note that only the integer value of the averaged data is kept in the database. There were a total of 30×24 = 720 samples. This set of RSSI samples will be used in our statistical data analysis in Section V.To measure the localization performance of the system, the software can be switched to operate in the online phase in which the user can locate or track the current location of the mobile location node. Note that we only test the system by placing the mobile location node on the same grid locations as those locations that were collected the RSSI. The localization application will use the location estimation algorithm to provide an estimated location. We compared the estimated location with the actual location and calculated the error distance for each user’s request as illustrated in Fig. 5. The online experiments were performed for 50 times at each location. Consequently, there are a total of 50×24 = 1,200 test results. The measurement results will be reported in the next section.IV.P ERFORMANCE M EASUREMENT R ESULTSThe localization performance measurement results are reported in Table I. The first column is the error distance which is the coordinate’s difference between the correct location and the estimated location returned by our application. The second column, which is labelled as probability density, is counted and normalized from the frequency of test results with corresponding error distance. The last column is the cumulative value of the probability density given in the second column. Note that these results were reported previously as a plot of cumulative distribution function in our two-page short paper [14]. The numerical data are included here for completeness of our study. In the literature, the localization performance is usually reported in terms of location accuracy and location precision. The location accuracy is defined as an error distance (in meters) that the estimated location is deviated from the actual location [15]. On the other hand, the location precision is defined as a percentage or a cumulative probability density value that the system returns all correct locations within a given distance of accuracy [15]. Based on the results in the table, our system achieved 2.8 meters of accuracy with approximately 92 percent of precision. The mean accuracy of the system can be calculated by summing all products of error distances and their corresponding probability densities, which is approximately 0.77m.TABLE IL OCALIZATION P ERFORMANCE R ESULTSError Distance(m.) ProbabilityDensityCumulative ProbabilityDensity (CDF)0 0.7025 0.70251.4 0.1050 0.80751.98 0.0592 0.86672.8 0.0517 0.91843.13 0.0108 0.92924.43 0.0633 0.99255.77 0.0075 1V.S TATISTICAL D ATA A NALYSISIn the literature, there is a comprehensive research work in [16] that analyses statisticalparameters of RSSI measured from a number of Wi-Fi interfaces. The authors of that work pointed out that there is a need to understand characteristics of RSSI beyond typical RF propagation in order to better design and implement an indoor localization system. An interesting finding in that work is that most of the RSSI data collected from various indoor environments,if it is considered as a random variable, possesses a unique probability distribution function. Most of RSSI’s distributions were not Gaussian but rather had left-skew distributions [16]. Minority of the distributions was found to have symmetry shape which is similar to Gaussian distribution. The skewness parameters were calculated for various RSSI data sets from a number of WLAN access points and most of them were found to be negative. The standard deviation of the distribution was observed to be larger when the RSSI samples were collected at a location that was closer to the WLAN access points.In this work, we performed similar statistical data analysis in term of the shape of RSSI distribution, the standard deviation, and the skewness. Fig. 7 compares the normalized histograms of RSSI from all locations where each sub-graph represents data from different anchor nodes. We observe that most of the histograms are symmetry which could be modelled by Gaussian distribution. This is different from the results reported in LoS environment of Wi-Fi in [16].Fig. 7 Normalized Histograms of RSSI from All Locations Fig. 8 plots the mean RSSI values of RSSI collected at each anchor node (from anchor 1 to 4) against each location (from location 1 to 24). The combination of mean RSSI values from all four anchor nodes forms a RF fingerprint at a location. A visual inspection of the pattern of mean RSSI values at each location is quite different from other locations. This enables the localization algorithm to separate one location from another through the unique pattern of RSSIs.Fig. 8 Mean of RSSI from All LocationsFig. 9 considers standard deviations of the RSSI samples collected by all anchor nodes at each location. We found that most of the standard deviations were below 2 and were not larger than 4. This is different from the results reported by small area scenario with LoS propagation of [16] where Wi-Fitends to have larger standard deviation than 4. We observed that when mobile location node is at the same location as anchor node, the standard deviation of RSSI is zero. For example, when mobile node is at location 1, the standard deviation of RSSI measured at Anchor 1 is 0. In other words, Wi-Fi signal is more fluctuate than ZigBee signal under theLoS environment.Fig. 9 Standard Deviation of RSSI from All Locations.Fig. 10 compares the skewness values of all RSSI distributions from different locations and anchor nodes. Skewness is a measure of symmetry of distribution. A probability density function (PDF) is said to be left-skewed (has a long tail on the left) when it has its mean less than its median which is less than its mode [17]. Note that the left-skewed distribution will have a large negative skewness value. However, in this figure we observed that most of the distributions were not left-skewed. This is also different fromthe Wi-Fi results reported in [16].Fig. 10 Skewness of RSSI from All Locations.VI. C ONCLUSIONS AND F UTURE W ORK An implementation of ZigBee localization system, whichconsists of both hardware and software components, is described in this work. Preliminary localization performancein term of location accuracy and location precision is also summarized where the average accuracy was 0.77m. Atapproximately 92% of precision, the system can achieve the accuracy of 2.8m. The main contribution of this paper is the study of statistical data analysis on the RSSI in RF fingerprint database. We found that for small area with LoS RF propagation most of the distributions of RSSI in ZigBee WSN are symmetry which is different from Wi-Fi results in [16]. Moreover, the standard deviation was also different in which ZigBee RSSI signal is less fluctuate in this work. The majority left-skew distributions were not observed in this work, while it is prevalent in the Wi-Fi system. However, in term of statistics the total number of measured samples in this work is still small. Our preliminary findings reported in this work may not be valid in all environments and scenarios because we only collected the data from a small room environment. We are planning to deploy the ZigBee localization system in a larger area and perform more extensive measurement experiments, which will include NLoS environment and low signal strength condition.R EFERENCES[1]L. Atzori et al., “The Internet of Things: A survey,” Computer Networks , vol. 54, no. 15, pp. 2787-2805, Oct. 2010.[2] ZigBee Cluster Library Specification, ZigBee Document No. 075123r04ZB, May, 2012.[3] Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (WPANs), IEEE Std 802.15.4TM – 2006, Sep. 2006.[4] MC1322x Advanced ZigBee TM – Compliant SoC Platform for the 2.4 GHz IEEE® 802.15.4 Standard Reference Manual, Freescale Semiconductor, Document Number: MC1322xRM, Rev. 1.6, Jan. 2012. [5] W.-C. Park and M.-H. Yoon, “The Implementation of Indoor Location System to Control ZigBee Home Network,” in SICE-ICASE Int’ Joint Conf., 2006, pp.2158-2161.[6] Y. Zhao et al., "Implementing indoor positioning system via ZigBee devices," Signals, Systems and Computers, 42nd Asilomar Conf. on , pp.1867-1871, 26-29 Oct. 2008.[7] L. Xu et al., "Variation of Received Signal Strength in Wireless Sensor Network," Advanced Computer Control (ICACC), 2011 3rd Int. Conf. on , pp.151-154, 18-20 Jan. 2011.[8]K. Subaashini, G. Dhivya, and R. Pitchiah, "Zigbee RF signal strength for indoor location sensing - Experiments and results," Advanced Communication Technology (ICACT), 2012 14th Int’ Conf. on , pp.12-17, 19-22 Feb. 2012.[9] ZigBee Telecom Applications Profile Specification, ZigBee Document No. 075307r07, Apr. 2010.[10] P. Bahl and V. N. Padmanabhan, “RADAR: an in-building RF-based user location and tracking system," in Proc. INFOCOM 2000, Tel Aviv, Israel, pp. 775-784, Mar. 2000.[11] “Freestar Pro Series Transceiver Modules ZFSM-201-1 datasheet”, California Eastern Laboratories, Doc. No. 0006-00-07-00-0000, Aug. 17, 2009.[12] Freescale BeeStack TM Software Reference Manual for ZigBee 2007, Freescale Semiconductor, Doc. No. BSSRMZB2007, rev.1.1, Dec. 2008.[13]BeeStack TM BlackBox ZigBee TM Test Client (ZTC) Reference Manual, Freescale Semiconductor, Doc. No. BSBBZTCRM, rev. 1.0, May 2010. [14]R. Ranron and K. Kaemarungsi, “Implementation of ZigBee Localization Using RSSI Location Cluster,” in Proc. ECTI-CARD 2013, Nakhon Ratchasima, Thailand, May 2013.[15]J. Hightower and G. Brriello, “Location Systems for Ubiquitous Computing,” IEEE Computer , vol. 34, no. 8, pp. 57-66, Aug. 2001. [16] K. Kaemarungsi and P. Krishnamurthy, “Analysis of WLAN's received signal strength indication for indoor location fingerprinting,” Pervasive and Mobile Computing , vol. 8, no. 2, pp. 292-316, Apr. 2012.[17] R. Jain, The Art of Computer Systems Performance Analysis: Techniques for Experimental Design, Measurement, Simulation, and Modeling . New York, NY: John Wiley & Sons, 1991.。
