Demand Signal Management_SAPPHIRE_05_2012
Q.763 - Formats and codes of the ISDN User Part of Signalling System No. 7

The format of and the codes used in the service information octet are described in 14.2/Q.704. The service indicator for the ISDN User Part is coded 0101.
Recommendation Q.763 (03/93)
1
1.2 Circuit identification code The format of the circuit identification code (CIC) is shown in Figure 2.
8
7
6
5
4
3
2
1
Circuit identification code (least significant bits)
INTERNATIONAL TELECOMMUNICATION UNION
ITU-T
TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU
Q.763
(03/93)
SPECIFICATIONS OF SIGNALLING SYSTEM No. 7
SAPPHIRE系统用户指南说明书

The challengeThe RAF is a complex and diverse organisation. It's people and equipment carry out complicated, high-risk tasks both in the UK and on operations overseas which need to be completed against demanding time constraints, in a way that minimises the risk of failure and maximises efficient use of resources. The achievement of these tasks relies upon timely and well-informed decisions based upon a shared understanding of trends, the current position and the future outlook.However, prior to the selection of SAPPHIRE, the RAF did not have a consolidated view of its performance and risk position. For a commander to see one version of the truth, hundreds of emails and documents would have to be collated which could take weeks and there was no way for staff at all levels to have universal access to performance and risk data.There was a long-standing requirement for themeasurement of capability , the associated risks and issues such as threats, equipment problems, resource shortfalls and possible future adverse events.The solutionAfter conducting a requirements capture and analysis exercise at the RAF Headquarters at the former Strike Command, Fujitsu developed and delivered a new , bespoke Performance and Risk Management System, named ‘SAPPHIRE’, with balanced scorecard capabilities. The acronym ‘SAPPHIRE’ stands for Strike Applications Project Promoting High level Information Reporting and Evaluation. Whilst Strike Command has since transformed to become AIR Command, SAPPHIRE is in use across the whole of the RAF , providing a single performance and riskmanagement tool.SAPPHIRE is based on Oracle database technology , sitting on the MoD’s existing communicationsinfrastructure with (Trusted) access available to users not yet on DII. SAPPHIRE can take information from any other ODBC-compliant database and provide outputs in a variety of formats as defined (and thus easily understood) by the user as appropriate to their own organisation or unit’s needs.‘SAPPHIRE has become embedded in the management culture of the RAF , where it is finding an increasingly important role in both the conduct of day-to-day business at the producer level through to the conduct of senior management boards all the way up to the Defence Management Board.’Mark Williams - Group CaptainSUMMARY OF KEY FACTSOrganisation RAF Air Command Contract signing date February 2002Service/s deliveredSAPPHIRE Application Design, Application Integration, Application Development, Support, Managed Service and training on Application Management.Benefits For MOD• One database providing a consolidated view of performance & risks• Subjective assessment of performance displayed alongside the calculated value• Enter data once, use many times in different ways • See the big picture or focus in on detail • Capture all expertise, make better decisions • Shared aims, more effective working • Reduced reporting burden upon users • Emphasises forecasting• Compatible with legacy and future IT systems • Promotes corporate awarenessEmphasises forecasting SAPPHIRE providesimmediate access to history and trend information but focus is now on forecasting and managing the future. The application allows managers to enter performance and risk forecasts to any future time period based upon proposed management and mitigation strategies detailed in report narratives.Compatible with legacy and future systems, adding value to existing data Data from other sources can be imported without the need for manual transcription, saving time and improving consistency which adds value to that data.Promotes corporate awareness Training for users of the application and its subsequent use in everyday management has helped to remove silo thinking.Future DevelopmentsThe system will continue to be developed to reflect the unique business needs of new users and toenhance core functionality to existing users, including investigation of alternate user interfaces and automated data feeds from extant applications.An increasing user community as DII(F) rolls out across Defence, enabling business areas the opportunity to adopt SAPPHIRE as their preferred performance, risk and business management tool.Our ApproachSAPPHIRE was delivered in phases by Fujitsu, allowing early benefits as well as quick response to requirements for changes and enhancements. The SAPPHIRE training has contributed to the cultural and mind-set changes which were critical to achieving optimum ROI.The ExpertiseFujitsu were chosen because of their proven expertise in project management, application development, implementation, support and managed services.Wing Commander Nicky Mellings, the SAPPHIRE User Champion, stated: ‘SAPPHIRE continues to provide key benefits to (not just) AIR Command (but the RAF as a whole), enabling senior management at all levels to view, understand and manage their outputs effectively and efficiently. The ability to view the present position, married against risks, allows senior managers to make (better) informed decisions to mitigate future risks and improve future performance.’Fujitsu implements changes and additions to SAPPHIRE functionality as user needs evolve, and provides on-line support to users and system administrators as well as managed support services and training for instructors and those performing application management roles.Although it was the RAF’s requirements that drove SAPPHIRE’s development, it has been successfully adopted by other MoD departments as theperformance and risk management tool of choice. The system design is generic and because the user defines the business rules, it can be applied to any organisation.SAPPHIRE operates at SECRET and RESTRICTED data classifications, with user definable rules that allow access to pre-determined individuals whilst still promoting information sharing on a ‘need-to-know’ or ‘duty-to-share’ basis.Benefits for our CustomerOne version of the truth One database providing a consolidated view of operational performance, risks and issues giving a single version of the truth available in one place, transforming decision-making and operational management.Subjective assessment of performance displayed alongside the calculated value Subjective military assessment of performance can be added without overriding calculated, objective assessments so that the extent of the judgement applied is always apparent.Enter once, use many times in different ways Data is entered only once but can be used again and again, categorised in a variety of ways (for example, Defence Lines of Development, user-defined structures and keywords) and viewed or manipulated to suit user output needs through the generation of reports.See the big picture or focus on detail Huge amounts of information are consolidated into simple summaries by users, who can drill down to the supporting data if required.Capture all expertise, make better decisions Accurate information entered by experts in their area gives senior management a clearer understanding of the factors and impacts which lead to better, faster decisions.Shared aims, more effective working Senior officers are equally aware of a consistent big picture, which helps them work together more effectively .Reduced reporting burden upon users Previous reporting systems were labour intensive. WithSAPPHIRE, comprehensive reports are viewed easily on-screen and information can be selected then presented in various formats.。
D10 Training Outline说明书

- Omni ASIC for the DPIN96 - Octet analog instruments for DMSI - Program Developer for program generation - Test Developer for pattern generation - Debug tools adapted from multiple platforms - VI technology from SZ - RF and Power Management technology from ASL
Company Confidential
12
® Established 1981
Advanced Test Equipment Rentals
800-404-ATEC (2832)
Timing Examples in STIL
® Established 1981
TAwdhwveawn.SacteTecdoIrLTpe.csoFtmiElq8e0u0i-p4m04e-AnTtECR(e2n8t3a2l)s
Day1:
- Plateform Overview - Timing And STIL - Passive Load - Instrument Pin Introduction - Program Overview(.job, .res, .sig, user_main, user_load,
API etc)
Diamond DPIN96 96 200Mbps 200 Mbps
±500ps
19.5ps 1.2ns @ 3V 4ns @ 3V -1V to 6V 12V -2V to 12V, ± 25mA
Premise

Market research for requirements analysis using linguistic tools1Mich Luisa*, Franch Mariangela°, Novi Inverardi Pierluigi°* Department of Computer and Telecommunication Technology, University of TrentoVia Sommarive 14, I 38050 Trento (I) - Tel. +39-0461-882087 – Fax +39-0461-882093E-mail: mich@dit.unitn.it° Department of Computer and Management Sciences, University of Trento Via Inama 5, 38100 Trento (I) - Tel: +39 0461 88213/2287 - Fax: +39 0461 882124E-mail: franch@cs.unitn.it, inverard@cs.unitn.itAbstractNumerous studies in recent months have proposed the use of linguistic instruments to support requirements analysis. There are two main reasons for this: (i) the progress made in natural language processing, (ii) the need to provide the developers of software systems with support in the early phases of requirements definition and conceptual modelling. This paper presents the results of an online market research intended (a) to assess the economic advantages of developing a CASE tool that integrates linguistic analysis techniques for documents written in natural language, and (b) to verify the existence of potential demand for such a tool. The research included a study of the language – ranging from completely natural to highly restricted – used in documents available for requirements analysis, an important factor given that on a technological level there is a trade-off between the language used and the performance of the linguistic instruments. To determine the potential demand for such tool, some of the survey questions dealt with the adoption of development methodologies and consequently with models and support tools; other questions referred to activities deemed critical by the companies involved. Through statistical correspondence analysis of the responses, we were able to outline two "profiles" of companies that correspond to two potential market niches which are characterised by their very different approach to software development.Keywords: Market research, Potential demand, NLP-based CASE tools, Requirements Analysis, Conceptual modelling1. Objectives and structure of the paperPremiseThis paper presents the results of an online market research conducted in the spring and summer of 1999 by the Department of Computer and Management Sciences of Trento University, Italy. The study is part of a larger project whose principal aim is to identify the advantages and disadvantages of market research done online with respect to traditional methods and channels, and to look at its applicability in diverse product markets2. In methodological terms the objective of the research presented in this paper was to demonstrate the benefits of conducting online market studies for innovative products. Problems with such innovative products derive firstly from the fact that their characteristics cannot be thoroughly defined before conducting the research, and secondly their availability in commercial form usually requires further sizeable investments in research and trialling. Both of these issues are critical for CASE (Computer Aided Software Engineering) tools, which use linguistic instruments to analyse documents in natural language, and are therefore based on technologies for natural language processing (NLP) developed in the field of Artificial1 Submitted to REJ.2 Multi-year project funded by the Department of Computer and Management Sciences of Trento University.Intelligence. Working from the perspective of a company attempting to decide which products to develop (from among different projects related to NLP-based applications), our objective was to evaluate potential demand for NLP-based CASE tools. In conducting the study we made the reasonable assumption that the respondents (people involved in developing software systems) could be contacted easily by Internet; this prerequisite could not be guaranteed principally at a national level for other sectors studied previously (e.g., tourism or electronic commerce of groceries)3. At the same time, a certain predisposition not to participate in the study was to be expected, whether because of time constraints (noted even at the initial explorative interviews) or because of an already high level of saturation. In fact, both of these assumptions were confirmed during the course of the research. Nonetheless, we emphasise that this paper focuses on the results of the actual content of the research, and hereinafter we describe only methodological aspects that are pertinent to the interpretation of the results obtained4.ObjectivesAs previously mentioned, the aim of the research was to analyse the potential demand for a CASE tool integrating linguistic instruments as a support to requirements analysis. To give the context in which such a tool could be designed and used, the following paragraph first describes the role of natural language in requirements engineering and then classifies the possible applications of linguistic instruments, making reference to the architecture of an ideal NLP system and to the three fundamental activities of requirements analysis: Elicitation, Modelling and Validation (Loucopoulos & Karakostas, 1995). Our market research refers principally to the support of conceptual modelling, an activity that to benefit from the use of linguistic instruments requires the design of a modelling module. The other activities could be supported by existing functionalities of an NLP system, with varying levels of performance.It was found early in the study that none of the commercial CASE tools exploited linguistic instruments to support requirements modelling (Chiocchetti & Mich, 2000); this meant, therefore, that the market research was to focus on a new product whose features could not be defined in relation to similar existing products (analysis of the competition). Numerous research projects do exist in this area, however, and serve as a testimony of the considerable interest in the use of linguistic instruments in requirements engineering5. The common objective is to carry out a linguistic analysis of requirements documents in order to produce conceptual models of them6. Among the most recent projects, as an example, we can cite those described in (Ambriola & Gervasi, 1999; Juristo & al., 2000). While a complete review is beyond the scope of this paper, it is worth noting how different approaches can be analysed by looking at two principal aspects (depending on the characteristics of the linguistic tools adopted):a) how “natural” the input language is, which is normally subject to restrictions regardinggrammar, vocabulary, or both;b) how much intervention by an analyst is needed in order to process "semi-automatically" the text or to identify the key elements for conceptual modelling.3 Some comparisons deriving from our research are described in (Franch & al., 2000).4 For further study of issues related to online market research, the interested reader can refer to the literature (see for example, the publications found at ESOMAR (European Society for Opinion and Marketing Research): http://www.esomar.nl/).5 See (Burg, 1997), (Ryan, 1992). A bibliography is available at: http://nl-oops.cs.unitn.it.6 The first proposals to use linguistic criteria for the extraction of entities and relations, and then objects and associations, from narrative descriptions of requirements date from the 1980s (Chen, 1983).The survey described in this paper focuses on the first of these points, one that we deem of vital importanc because whatever the approach adopted, the "naturalness" of the language directly affects the amount of effort needed to extract useful information from the documents. First, it was necessary to establish whether the documents gathered in the requirements elicitation phase were in 'real' natural language or in some type of restricted language, and if they were in natural language, whether the user or customer could be asked to describe the requirements using a more restricted language. In fact, if the documents are written in a 'controlled' language (restrictions on grammar or vocabulary), information can be extracted using syntactic or ‘shallow’ techniques, such as parse trees7. To obtain equivalent performances with documents in unrestricted natural language it is necessary to have a semantic representation of knowledge that embeds reasoning techniques. Such applications are currently being studied8. Moreover, the language used in the documents can be more or less linked to a particular application domain (for example, software for telecommunications), thus determining the degree of specialisation of the support linguistic tool to be used in the conceptual analysis, and therefore of its knowledge base. In other words, hypothesizing that the basic NLP technologies are available, for a company that must decide whether or not to invest in the development of an NLP-based tool for requirements analysis, it is important to establish first if it is possible to design and realise a general-purpose tool to support software development for different application domains or if instead it is necessary to make further investments later to customize the tool for the different companies or customers it will eventually serve. These are all essential considerations in determining the investment necessary to convert a research prototype - like those developed in the existing research projects - into a commercial tool.Results of preliminary interviews as well as the state of the art of existing prototypes led us to decide not to investigate the degree of analyst intervention requested nor performance requested of the tool (point b: we limit ourselves on this point to giving some general findings that emerged while conducting the research). To do so would have required further investment in a more extensive market research; such study would be justifiable only with a positive outcome, certainly not guaranteed, relative to the issues related to point a). Moreover, to assess the potential market for an NLP-based tool for requirements analysis, we studied aspects related to the diffusion of methods and instruments of software engineering. In particular, we intended to verify whether requirements analysis is in fact considered critical in relation to other important activities in software development (testing, documentation, etc.). Structure of the paperThe paper is organised as follows: the next section describes the context of an NLP-enabled CASE tool and summarises possible applications of linguistic tools for requirements engineering. This provides information on the design of the questionnaire and the eventual interpretation of the results. The third section outlines the plan of the market research, noting the different phases and focusing on the questionnaire and on the characteristics of the respondents. The main results of the online survey are presented in the fourth section, where they are analysed using a statistical technique referred to as correspondence analysis. The profiles obtained have revealed the existence of two market niches characterised by their diverse approaches to software development. Finally, some observations are given regarding the characteristics of the survey and the extendibility of the results. The conclusions summarise how the results of the survey can be used by those who develop software in7 Included in this category are, for example, the instruments described in (Fuchs, 1996) and (Deslise, 1999).8 For example, to recognise if Washington is the name of a person, of an airport, or of a city in a given document requires a semantic approach. Limitations on space do not permit a deeper discussion of this issue here; see for example (Mich & Garigliano 2000).general, and by those who design tools and environments for requirements analysis in particular.2. The role of natural language in requirements engineeringMuch has been written on the importance of requirements analysis. In order to show why environments and tools to support such analysis are less satisfactory than those available for the other phases of the software life-cycle, we shall briefly review the distinctive features of requirements engineering, defined as:“the systematic approach of developing requirements through an iterative cooperative process of analysing the problem, documenting the resulting observations in a variety of representationformats, and checking the accuracy of the understanding gained”.(Loucopoulos & Karakostas, 1995, p 13).Thus evident is the central importance of communication9 and knowledge. Compared with other phases of software engineering, requirements analysis and conceptual modelling (Mylopoulos, 1998) present unique difficulties. Many of the activities involved are cognitive and require creativity as well as knowledge about information technologies and the application domain. Moreover, the recent advances brought about by business process re-engineering (BPR) and the inclusion of innovative components in information systems are broadening the scope of projects. As a consequence, the number of the actors, interactions and languages involved have increased. Completing the picture are the needs of companies, which operate at ever higher levels of competitiveness and which demand increasingly flexible information systems.In this context, the use of linguistic tools – more precisely of NLP systems – to support the development of software systems in general and requirements analysis in particular, may help the analyst to:- concentrate on the problem rather than on the modelling;- interact with other actors;- take into account the various kinds of requirements (organisational, functional, etc.);- achieve traceability as from the first documents produced;- manage more efficiently the problem of the changing user requirements.10As regards the possible applications of NLP systems to requirements engineering, it is worth noting that they are able to process both vocal and textual input, sometimes imposing restrictions such as limiting the vocabulary or the grammar.NLP systems can be used to obtain, with different levels of performance, essentially three types of output:- syntactic, semantic or pragmatic analysis;- text either in the same language or another one, natural or artificial;- syntheses in the form of differently structured summaries or templates.Figure 1 is a simplified scheme of an ideal general-purpose NLP system. It is important to remember that the systems for real applications are usually highly dependent on the task and on the domain11.9 “The hard part, and the true essence of requirements, is trying to understand your customer’s needs. A person involved in requirements needs human skills, communication skills, understanding skills, feeling skills, listening skills” (Davis, 1998). See also (Nitto, 1995).10 For a recent study on why it is impossible for users to know their requirements beforehand, see (Rugg & Hooper, 1999).With reference to this scheme, linguistic tools of differing complexity and especially of differing maturity can be used:a) in the requirements elicitation phase:- to facilitate the digitising of requirements documents using speech recognition systems or NLP-based interrogation interfaces;- to reveal ambiguities and contradictions in documents describing user needs (see for example, Fabbrini & al., 1998; Laitenberg & al. 2000; Mich & Garigliano, 2000);- to design questionnaires or interviews, by verifying the ambiguity of the questions;- for automatic analysis of replies to open-ended questions, interpreting and classifying their contents (Canzano, 1999).b) to model requirements by extracting (directly from the text) the descriptions of theelements to include in the conceptual models envisaged by the development method adopted, in particular UML (Unified Modelling Language)12diagrams (see Figure 2).systems to produce descriptions in natural language based on the structures used to 11 On this point, see, for example, the tasks required by the MUC competitions (Message Understanding Competition) organised by the DARPA (Defense Advanced Research Projects Agency), (AAA, 1991, 1992, 1993, 1995, 1998).12 The official documents of the UML’s specifications can be find on the OMG (Object Management Group) web site: .represent knowledge.A complete vision requires noting that NLP tools can also be used for documentation, generating reports on the various stages of requirements collection and modelling; for traceability, allowing a link to be maintained between the texts used and the models produced; and for the translation of documents into various languages, something that becomes increasingly necessary in the design of international information systems.The survey described in this paper concerns the second of these points, that is, the use of NLP techniques to support the development of conceptual models, given that it requires the design of a modelling module. All the other activities could be supported by existing functionalities of an ideal NLP system, albeit with different performances. The most important assumption is that the requirements documents, once analysed, can contribute to a "knowledge base" from which to extract elements deemed useful for modelling activities. There are two important aspects to note regarding projects for developing this type of instrument: i) many of these projects are based on ad hoc NLP systems, and therefore do not appear to correspond to the requirements for scalability and robustness of real applications; ii) given the complexity of natural language, almost all of them expect that documents will be written in restricted language or that some revision of the text will have taken place before undergoing the automatic analysis. These two facts are worth remembering when interpreting the results of market research and when estimating potential investments in NLP technologies, and certainly when developing a CASE module to support requirements analysis.3. Plan and realisation of the market researchThe decision to investigate the market for an NLP-based tool for requirements analysis was taken in the context of a joint research project with the Department of Computer Sciences of Durham University (UK) in which a prototype was developed of a CASE tool - called NL-OOPS -,13 for requirements modelling according to the object-oriented approach (Mich, 1996, Mich & Garigliano, 1999).The market research described here was based on the administration of a questionnaire whose design required consideration of the experience gained throughout the development of NL-OOPS, and of the methodology and techniques of online market research. Specifically, the research progressed in the following phases:- preliminary survey- identification of interview subjects- designing and testing of the questionnaire- selection of the contact method- distribution of the questionnaire and reminders- collection and analysis of the data.A description of each phase follows, giving greater emphasis to the third phase (designing the questionnaire) and to the final stage (analysis of data).Preliminary survey The first step in the research project was to create a focus group composed of both companies that develop linguistic instruments as well as big and small businesses that develop software or offer services linked to the introduction of information technologies in the workplace. The goal of this phase was to collect information about the users' needs that could be satisfied with an NLP-based CASE tool and to gather other information useful in designing the questionnaire. The researchers were immediately confronted with pessimistic views of tools which use NLP techniques to support requirements 13 Natural Language – Object-Oriented Production System, http://nl-oops.cs.unitn.it.analysis. In particular, some focus group members expressed serious doubts that the language in the documents gathered for requirements analysis was sufficiently ‘natural’ to justify the adoption of a tool based on NLP techniques. Others questioned the technical feasibility of such tools, citing their own unsatisfatory experiences with other NLP applications such as translation programs.Identification of interview subjects In accordance with the objective of the study, the questionnaire was directed principally to persons involved in software development, and in addition to managers responsible for important decisions regarding the process of software development, including the decision to adopt methodologies and support instruments. From a statistical viewpoint, when dealing with a survey conducted via Internet, one of the main problems is to establish the degree to which the sample is representative of the target population, in this case the people or companies involved in software development. On one hand, it is reasonable to assume that the intended respondents are reachable by Internet, while on the other hand the population has characteristics (number, size, geographic distribution, etc.) that are not documented. Given this and also considering the chosen methods of contact, the approach to the study is conceptually similar to a sequential sampling. Statistically, this would classify it as a descriptive study, and as such requires caution when extending the results outside of the survey sample.Designing and testing of the questionnaire Again considering the objectives of the study, in terms of both methodology and content, the survey was conducted only via Internet and it consisted of a questionnaire on a Web page14 (see appendix A). This choice was the driving force during the design and testing stage, the aim being to have a concise questionnaire with closed-ended questions in language as clear as possible.15 As for the questions themselves, the choices were made as logical and pertinent issues emerged throughout the course of the focus group. After a phase of testing in which the questionnaire underwent the scrutiny - first directly and then online - of a select group of analysts and project managers, the final version was produced. The final questionnaire was divided into two sections, for a total of eighteen questions, and a final open question for further observations. The first group consisted of questions relating to the company (questions 1 – 4) and to the respondent (questions 5 and 6). The second part investigated processes of software production, so that one group of questions concerned the use of methodologies (questions 7 – 10) and tools (questions 13 and 14) in software development; another group dealt with documents used in requirements analysis (questions 11, 12 and 15) and the last three were about the efficiency of the development process (questions 16, 17 and 18). The respondents were also asked if they were interested in obtaining the results of the research or in viewing a demonstration of a prototype of an NLP-based CASE tool. The decision to introduce questions associated with an engineering approach to software development was made after verifying the possibility of using existing data. Surprisingly,16 only a small amount of data was found, whether for the diffusion of object-oriented methodology or for the use of ‘classic’ models such as the entity-relationships models. These are important because the early research and conceptual models for linguistic analysis of requirements (Chen, 1983) looked to produce entity-relationships diagrams; moreover, these models can be seen as a particular case of the class models foreseen by the object-oriented approach. As regards the market for CASE tools,17 in many cases they did not meet expectations and as a consequence did not have the desired market success (Glass, 14 The questionnaire is available along with the data gathered and other related research material at http://on-line.cs.unitn.it.15 For example, a questionnaire like the one used for the survey described in (Nikula & al., 2000) would have to be radically altered to be used on-line.16 In light of the observations in (Zvegintzov, 1998), this may not be so surprising.17 The choice of tools for question 14 was made on the basis of sales data for a period prior to the study.1998). We will have to wait for the adoption of the UML – developed about one year before the present research project began – as a standard for conceptual modelling by the OMG (Object Management Group); only then will there be a significant growth in the market for CASE tools, repackaged and renamed as object modelling tools or visual modelling tools. In short, the scarcity of data on the penetration and role of an engineering approach to software development influenced the choice of questions for the survey, but also, as we shall see, the ability to validate and extend the results.The questions considered most important to verifying the existence of a market niche for an NLP-based CASE tool are those related to the documents used to collect requirements. In fact, as we have already seen, if documents are in real NL, an even more sophisticated (and costly) technology is needed to develop an environment that effectively supports analysis using linguistic instruments. It is therefore useful to establish whether the company is in a position to require clients or analysts to describe requirements in a restricted language. Typical restrictions can regard: a) grammar - aiming to have syntactic constructions that are easier to analyse by requiring, for example, shorter phrases, using the active voice, by avoiding anaphorical references, etc.; b) vocabulary - aiming to reduce ambiguity of terms. Moreover, in order to determine the degree of customisation required of a possible NLP-based tool, further questions dealt with the level of specialisation of the terminology and the domain knowledge required to develop the software.In the questions related to the efficiency of production processes, respondents were asked in particular about the improvements that they would like to see (choosing from a list of eight possible activities considered critical, two of which are fundamental for the phase of requirements analysis) and how they could be achieved, the choice being among ‘internal delegation’, ‘outsourcing’ and ‘automation’. The final question was designed to ascertain whether the company was able to deliver the software systems or products without delays. Finally, in keeping with the general rule of market research, an incentive to participate was provided in the form of a random drawing among respondents for tickets to an opera performance at the Arena in Verona.18Selection of the contact method The objectives of the research and the characteristics of the tool inherently required a contact method that would permit efficient use of time and resources while at the same time reach the largest number of potential respondents. On this point, to take into account the fact that there is a high level of saturation - due to the large number of such survey requests that the respondents receive - we had initially thought to send the questionnaire to some specialised newsgroups,19 highlighting the academic nature of the research. In the first phase we identified three newsgroups whose work is related to the research topic (comp.object, comp.software-eng, p.software-tools); another twenty-one newsgroups were later added to the list (the complete list is available at http://on-line.cs.unitn.it). Nonetheless, after this method of contact proved less successful than expected,20 we decided to contact the companies directly by email, supplying them with the address of the Web page where they could find and complete the questionnaire. The companies’ addresses were acquired online using search engines, in particular a directory of Yahoo!21 (Computer > Software > Developers).18 Because the survey concluded at the end of the Arena opera season, the tickets were replaced by CDs of opera music by Verdi.19 One of the aims of the survey, in fact, was to investigate the conditions under which newsgroups can be usedto carry out online surveys.20 Limited number of questionnaires obtained (44) and accusations of spamming.21 .。
自动化测试系统顶层设计方法论说明书
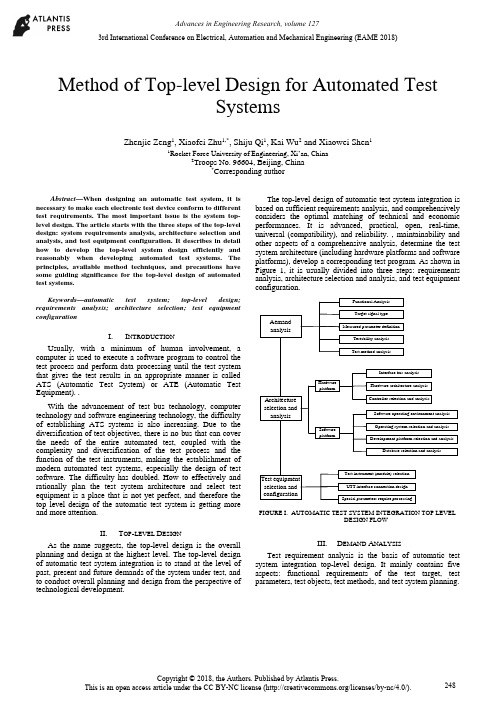
Method of Top-level Design for Automated TestSystemsZhenjie Zeng1, Xiaofei Zhu1,*, Shiju Qi1, Kai Wu2 and Xiaowei Shen11Rocket Force University of Engineering, Xi’an, China2Troops No. 96604, Beijing, China*Corresponding authorAbstract—When designing an automatic test system, it is necessary to make each electronic test device conform to different test requirements. The most important issue is the system top-level design. The article starts with the three steps of the top-level design: system requirements analysis, architecture selection and analysis, and test equipment configuration. It describes in detail how to develop the top-level system design efficiently and reasonably when developing automated test systems. The principles, available method techniques, and precautions have some guiding significance for the top-level design of automated test systems.Keywords—automatic test system; top-level design; requirements analysis; architecture selection; test equipment configurationI.I NTRODUCTIONUsually, with a minimum of human involvement, a computer is used to execute a software program to control the test process and perform data processing until the test system that gives the test results in an appropriate manner is called ATS (Automatic Test System) or ATE (Automatic Test Equipment). .With the advancement of test bus technology, computer technology and software engineering technology, the difficultyof establishing ATS systems is also increasing. Due to the diversification of test objectives, there is no bus that can cover the needs of the entire automated test, coupled with the complexity and diversification of the test process and the function of the test instruments, making the establishment of modern automated test systems, especially the design of test software. The difficulty has doubled. How to effectively and rationally plan the test system architecture and select test equipment is a place that is not yet perfect, and therefore the top level design of the automatic test system is getting more and more attention.II.T OP-LEVEL D ESIGNAs the name suggests, the top-level design is the overall planning and design at the highest level. The top-level design of automatic test system integration is to stand at the level of past, present and future demands of the system under test, and to conduct overall planning and design from the perspective of technological development.The top-level design of automatic test system integration is based on sufficient requirements analysis, and comprehensively considers the optimal matching of technical and economic performances. It is advanced, practical, open, real-time, universal (compatibility), and reliability. , maintainability and other aspects of a comprehensive analysis, determine the test system architecture (including hardware platforms and software platforms), develop a corresponding test program. As shown in Figure 1, it is usually divided into three steps: requirements analysis, architecture selection and analysis, and test equipment configuration.AemandanalysisArchitectureselection andanalysisTest equipmentselection andconfigurationFunctional AnalysisTarget signal typeMeasured parameter definitionTestability analysisTest method analysisInterface bus analysisHardware architecture analysisController selection and analysisHardwareplatformSoftware operating environment analysisOperating system selection and analysisDevelopment platform selection and analysisDatabase selection and analysisTest instrument (module) selectionUTT interface connection designSpecial parameters require processingSoftwareplatformFIGURE I. AUTOMATIC TEST SYSTEM INTEGRATION TOP LEVELDESIGN FLOWIII.D EMAND A NALYSISTest requirement analysis is the basis of automatic test system integration top-level design. It mainly contains five aspects: functional requirements of the test target, test parameters, test objects, test methods, and test system planning.3rd International Conference on Electrical, Automation and Mechanical Engineering (EAME 2018)A.Test Target Functional RequirementsThe different requirements of the test equipment working platform determine the test speed requirements, and also determine the different requirements of the online/offline test; the main control method and logic of the tested equipment determines the difference between the test procedures and methods; the input frequency of the tested equipment, Different parameters, such as amplitude and modulation method, determine the overall requirements for the operating frequency band, small signal level (minimum leakage), and waveform parameters of the automatic test system analog signal source; the output and content of the device under test determines the signal sampling of the automatic test system. The data acquisition method is different; the digital communication interface of the device under test determines that the digital communication interface that the automatic test system should have is different from the protocol; the testability interface of the device under test determines the final test capability and fault diagnosis ability of the automatic test system.B.Test ParametersThe test parameter analysis includes analysis: the form of the measured parameter (electrical or non-electrical, digital or analog, etc.), range and quantity; performance index (measurement accuracy and speed, etc.); the form and range of the excitation signal. In particular, when analyzing requirements for a top-level design of a general-purpose comprehensive automatic test system that is suitable for multiple systems, multiple protocols, and multiple equipment, comprehensive analysis is often required to integrate the test parameters.C.Test ObjectThe test objects vary widely. When analyzing the test objects, a comprehensive analysis must be performed in conjunction with the test system requirements of the test objects. In the face of a specific test object test system or subsystem, the description can use a variety of expressions to give different models of the test system at different levels of simplification, such as language descriptions, graphics, and mathematical formulas. As a simplified description of some test systems, their models merely express their basic characteristics, often ignoring irrelevant details in order to simplify their complexity. For a complex test object test system, a model is inevitably limited by some assumptions in its design and utility. These conditions often have some ambiguity and basically reflect an implicit conceptual idea. Therefore, when analyzing the requirements of a specific test object, it is usually necessary to establish a corresponding test system model.D.Test MethodsAccording to the functional requirements of the test target, a corresponding test method is formulated for the “face-to-face automatic test system” or “object-oriented automatic test system”.. E.Test System PlanningWhen developing an automated test system, it often takes a lot of time to complete the test-assisted tasks such as creating files and programming supporting test software. The test application software development platform can standardize all kinds of test processes and integrate an operating system that is suitable for various test and post-processing functions. It can help us to complete these test auxiliary work; therefore, we use this kind of test platform to conduct various tests. When testing, you can save a lot of time.IV.A RCHITECTURE S ELECTION AND A NALYSIS On the basis of sufficient requirements analysis, determining the architecture of the automated test system is the most critical step in the top-level design. That is how to determine the test plan from the perspective of the top-level design, and select the hardware platform and software platform architecture of the automatic test system, and the most important one is the selection of the test equipment digital communication interface bus.A.System Test Plan SelectionThe system test plan is the overall concept of product testing. It specifies the type of product testing, when (continuous or regular) testing, where (field or workshop, or which maintenance level), testing methods, and test methods used. The types of system test can be divided into: system-wide test and departmental system test, static test and dynamic test, online test and offline test, quantitative test and qualitative test, continuous test and periodic test, etc. The test level can be divided into three levels according to the location: production site, use site, and maintenance base. The test system (equipment) operating methods are generally:According to the use of the operation can be divided into three kinds of automatic, semi-automatic and artificial; according to the general degree of application can be divided into two kinds of special and general equipment; according to the association with the product can be divided into two kinds of BITE and external test equipment.Most of the test methods used in automated testing have so far been modeled on manual tests, from the measurement principles used, the testing techniques used, to the test procedures performed, except that computers were used instead of manual operations. As far as the characteristics and potential of automatic testing are concerned, fundamental reforms of the test plan are needed for future research.B.Selection of Test Equipment Digital CommunicationInterface Bus and ATS StructureThe development of automatic test systems has promoted the continuous emergence of various general-purpose test equipment interface buses and rapid technological advancement: from the early GPIB, CAMAC to the recent VXI, MXI, PCI, PCIe, PXI, PXIe, cPCI, MMS, IEEE1394 ( Firewire), USB, etc. Although technical characteristics are not the same, they are widely used.The structural elements of a modern automated test system are programmable test instruments, test controllers, interconnected standard digital interfaces, and software systems. At present, modern automatic testing has been widely used, and the test objects faced are large, complex, and diversified, making it impossible for an automatic test system based on any kind of bus technology to cover the needs of the entire test object.Multi-bus fusion automatic test system structure shown in Figure 2. It consists of test instruments, DUTs(design under test) and UUT(unit under test) interfaces, test controllers (computers), various general-purpose digital interface buses, and test software. The test controller is interconnected with the test instrument through the digital interface bus, and the device under test is connected to the input/output terminal of the test instrument through the UUT interface. The digital interface bus used may be GPIB, VXI, PXI, LXI, or even an internal computer bus (AT/EISA/PCI), or their convergence. Once the standard digital interface bus architecture used is determined, the automatic test system architecture is basically selected. In an automatic test system, regardless of the interface bus architecture, an external computer or built-in computer system can be selected as the test system controller. The choice of the test system controller should fully consider the optimal matching of technical and economic performance, and choose from real-time, practical, reliable, flexible and convenient.CAT test hostMaster control computerGPIB instrument PC card typeinstrumentVXIinstrumentPXIinstrumentUUT interfaceUUT……FIGURE II. MULTI-BUS FUSION AUTOMATIC TEST SYSTEMSTRUCTUREC.Test Software Platform Mode SelectionIn modern computer-based automated test systems, hardware is the foundation and software is the soul. Test software has increasingly become the main body of ATS, which determines the advanced nature, reliability, practicality, and real-time performance of the entire automated test system.The automatic test software platform mainly refers to the programming language and software support environment involved in the test application software design. It is an integrated software platform such as a computer operating system, a test programming language, a database software, and a program diagnosis software. The key element is Test programming language. Since the automatic test system was popularized and applied, there have been great developments in testing programming languages from low-level to high-level, to the current test application development environment.V.T EST E QUIPMENT C ONFIGURATION After the system structure of the test system is determined, the next task is to synthesize the test contents according to the requirements analysis, and to match the corresponding test equipment according to the test content requirements. There are three types of optional test equipment: general test equipment, special purpose equipment, and test interface adapter.A.Universal Test EquipmentThe universal test equipment includes a main box, a test controller, a main control interface, a zero slot controller, an instrument module, and a desktop instrument. The following factors should be considered when selecting the type of equipment: (1) The higher the degree of equipment automation, the shorter the time for detecting and isolating faults, and the less the manpower consumption, but the cost of test equipment will increase and more protection is needed. (2) Differences in capabilities between the two are to be considered when selecting a BIT (Built-in-Test) and an off-board automatic test equipment. (3) When the BIT is used in conjunction with the off-board automatic test, make full use of the BIT capability of each unit under test. (4) When selecting a dedicated or general-purpose device, it is necessary to consider that the special-purpose device is simple and convenient to use and has high efficiency, but the use range is narrow. (5) The main selection of instrument and equipment is based on the requirements of test parameters, characteristics of the signal to be measured, and range selection. When selecting the instrument module, pay attention to the size of the bus module, power, and number of slots.B.Special Purpose EquipmentWhen the test is not ready for selection, in addition to the above-mentioned common tests, when preparing for the following situations, it may be considered to develop or develop special purpose instrument (module) equipment. When the current product can not meet the test requirements, multiple instruments and equipments are required to complete the measurement together. However, the utilization rate of each instrument is very low or can be accomplished with one instrument. When the price is high and the utilization rate is low, the use of development or development is considered. Special purpose instrument.C.Test Interface Adapter DesignFor different test objects, the extraction and feeding of various test signals requires the design and manufacture of various test interfaces and special fixtures. In the automatic test system, especially the automatic test system assembly of complex electronic equipment, the requirements of the same type but different models and different test objects existuniversally, and often require the test system group to build a relatively universal automatic test platform. Through this platform, different test modules and test methods can be used to quickly and easily complete the automatic test system set-up (configuration) task for different test objects; however, the test interface and the dedicated test module cannot be matched and can only be tested according to the device under test. The test requires the development of a test interface adapter.VI.C ONCLUSIONThis article starts with the three steps of the top-level design: system requirements analysis, architecture selection and analysis, and test equipment configuration. It describes in detail how to perform top-level design efficiently and reasonably when developing automated test systems, and analyzes what the design must follow. Principles, methods, techniques, and precautions have certain guiding significance for the top-level design of automated test systems.R EFERENCES[1]LI Xing-shan, ZUO Yi, SUN Jie. Automatic Test System IntegrationTechnology[M]. Publishing House of Electronics Industry, 2004.[2]QIN Hong-lei, LU Hui et al. Automatic Test System. Beijing: HigherEducation Press, 2007[3]LIU Si-jiu, ZHANG Li-yong. Automatic Test System and VirtualInstrument. Beijing: Publishing House of Electronics Industry, 2009 [4]GU Zhi-yong, TENG Peng, HU Shi-guo, et al. Top-level design of ATSoverall plan for integrated helicopter display systems[J]. Electro-optics and Control, 2008, 15(11):59-62.[5]GU Ya-ping. Research on Top Design of VXI Bus TestingTechnology[J]. Electronic Testing, 1998(8):22-23.。
Probabilistic model checking of an anonymity system

Probabilistic Model Checking ofan Anonymity SystemVitaly ShmatikovSRI International333Ravenswood AvenueMenlo Park,CA94025U.S.A.shmat@AbstractWe use the probabilistic model checker PRISM to analyze the Crowds system for anonymous Web browsing.This case study demonstrates howprobabilistic model checking techniques can be used to formally analyze se-curity properties of a peer-to-peer group communication system based onrandom message routing among members.The behavior of group mem-bers and the adversary is modeled as a discrete-time Markov chain,and thedesired security properties are expressed as PCTL formulas.The PRISMmodel checker is used to perform automated analysis of the system and ver-ify anonymity guarantees it provides.Our main result is a demonstration ofhow certain forms of probabilistic anonymity degrade when group size in-creases or random routing paths are rebuilt,assuming that the corrupt groupmembers are able to identify and/or correlate multiple routing paths originat-ing from the same sender.1IntroductionFormal analysis of security protocols is a well-establishedfield.Model checking and theorem proving techniques[Low96,MMS97,Pau98,CJM00]have been ex-tensively used to analyze secrecy,authentication and other security properties ofprotocols and systems that employ cryptographic primitives such as public-key en-cryption,digital signatures,etc.Typically,the protocol is modeled at a highly ab-stract level and the underlying cryptographic primitives are treated as secure“black boxes”to simplify the model.This approach discovers attacks that would succeed even if all cryptographic functions were perfectly secure.Conventional formal analysis of security is mainly concerned with security against the so called Dolev-Yao attacks,following[DY83].A Dolev-Yao attacker is a non-deterministic process that has complete control over the communication net-work and can perform any combination of a given set of attacker operations,such as intercepting any message,splitting messages into parts,decrypting if it knows the correct decryption key,assembling fragments of messages into new messages and replaying them out of context,etc.Many proposed systems for anonymous communication aim to provide strong, non-probabilistic anonymity guarantees.This includes proxy-based approaches to anonymity such as the Anonymizer[Ano],which hide the sender’s identity for each message by forwarding all communication through a special server,and MIX-based anonymity systems[Cha81]that blend communication between dif-ferent senders and recipients,thus preventing a global eavesdropper from linking sender-recipient pairs.Non-probabilistic anonymity systems are amenable to for-mal analysis in the same non-deterministic Dolev-Yao model as used for verifica-tion of secrecy and authentication protocols.Existing techniques for the formal analysis of anonymity in the non-deterministic model include traditional process formalisms such as CSP[SS96]and a special-purpose logic of knowledge[SS99].In this paper,we use probabilistic model checking to analyze anonymity prop-erties of a gossip-based system.Such systems fundamentally rely on probabilistic message routing to guarantee anonymity.The main representative of this class of anonymity systems is Crowds[RR98].Instead of protecting the user’s identity against a global eavesdropper,Crowds provides protection against collaborating local eavesdroppers.All communication is routed randomly through a group of peers,so that even if some of the group members collaborate and share collected lo-cal information with the adversary,the latter is not likely to distinguish true senders of the observed messages from randomly selected forwarders.Conventional formal analysis techniques that assume a non-deterministic at-tacker in full control of the communication channels are not applicable in this case. Security properties of gossip-based systems depend solely on the probabilistic be-havior of protocol participants,and can be formally expressed only in terms of relative probabilities of certain observations by the adversary.The system must be modeled as a probabilistic process in order to capture its properties faithfully.Using the analysis technique developed in this paper—namely,formalization of the system as a discrete-time Markov chain and probabilistic model checking of2this chain with PRISM—we uncovered two subtle properties of Crowds that causedegradation of the level of anonymity provided by the system to the users.First,if corrupt group members are able to detect that messages along different routingpaths originate from the same(unknown)sender,the probability of identifyingthat sender increases as the number of observed paths grows(the number of pathsmust grow with time since paths are rebuilt when crowd membership changes).Second,the confidence of the corrupt members that they detected the correct senderincreases with the size of the group.Thefirstflaw was reported independently byMalkhi[Mal01]and Wright et al.[W ALS02],while the second,to the best ofour knowledge,was reported for thefirst time in the conference version of thispaper[Shm02].In contrast to the analysis by Wright et al.that relies on manualprobability calculations,we discovered both potential vulnerabilities of Crowds byautomated probabilistic model checking.Previous research on probabilistic formal models for security focused on(i)probabilistic characterization of non-interference[Gra92,SG95,VS98],and(ii)process formalisms that aim to faithfully model probabilistic properties of crypto-graphic primitives[LMMS99,Can00].This paper attempts to directly model andanalyze security properties based on discrete probabilities,as opposed to asymp-totic probabilities in the conventional cryptographic sense.Our analysis methodis applicable to other probabilistic anonymity systems such as Freenet[CSWH01]and onion routing[SGR97].Note that the potential vulnerabilities we discovered inthe formal model of Crowds may not manifest themselves in the implementationsof Crowds or other,similar systems that take measures to prevent corrupt routersfrom correlating multiple paths originating from the same sender.2Markov Chain Model CheckingWe model the probabilistic behavior of a peer-to-peer communication system as adiscrete-time Markov chain(DTMC),which is a standard approach in probabilisticverification[LS82,HS84,Var85,HJ94].Formally,a Markov chain can be definedas consisting in afinite set of states,the initial state,the transition relation such that,and a labeling functionfrom states to afinite set of propositions.In our model,the states of the Markov chain will represent different stages ofrouting path construction.As usual,a state is defined by the values of all systemvariables.For each state,the corresponding row of the transition matrix de-fines the probability distributions which govern the behavior of group members once the system reaches that state.32.1Overview of PCTLWe use the temporal probabilistic logic PCTL[HJ94]to formally specify properties of the system to be checked.PCTL can express properties of the form“under any scheduling of processes,the probability that event occurs is at least.”First,define state formulas inductively as follows:where atomic propositions are predicates over state variables.State formulas of the form are explained below.Define path formulas as follows:Unlike state formulas,which are simplyfirst-order propositions over a single state,path formulas represent properties of a chain of states(here path refers to a sequence of state space transitions rather than a routing path in the Crowds speci-fication).In particular,is true iff is true for every state in the chain;is true iff is true for all states in the chain until becomes true,and is true for all subsequent states;is true iff and there are no more than states before becomes true.For any state and path formula,is a state formula which is true iff state space paths starting from satisfy path formula with probability greater than.For the purposes of this paper,we will be interested in formulas of the form ,evaluated in the initial state.Here specifies a system con-figuration of interest,typically representing a particular observation by the adver-sary that satisfies the definition of a successful attack on the protocol.Property is a liveness property:it holds in iff will eventually hold with greater than probability.For instance,if is a state variable represent-ing the number of times one of the corrupt members received a message from the honest member no.,then holds in iff the prob-ability of corrupt members eventually observing member no.twice or more is greater than.Expressing properties of the system in PCTL allows us to reason formally about the probability of corrupt group members collecting enough evidence to success-fully attack anonymity.We use model checking techniques developed for verifica-tion of discrete-time Markov chains to compute this probability automatically.42.2PRISM model checkerThe automated analyses described in this paper were performed using PRISM,aprobabilistic model checker developed by Kwiatkowska et al.[KNP01].The toolsupports both discrete-and continuous-time Markov chains,and Markov decisionprocesses.As described in section4,we model probabilistic peer-to-peer com-munication systems such as Crowds simply as discrete-time Markov chains,andformalize their properties in PCTL.The behavior of the system processes is specified using a simple module-basedlanguage inspired by Reactive Modules[AH96].State variables are declared in thestandard way.For example,the following declarationdeliver:bool init false;declares a boolean state variable deliver,initialized to false,while the followingdeclarationconst TotalRuns=4;...observe1:[0..TotalRuns]init0;declares a constant TotalRuns equal to,and then an integer array of size,indexed from to TotalRuns,with all elements initialized to.State transition rules are specified using guarded commands of the form[]<guard>-><command>;where<guard>is a predicate over system variables,and<command>is the tran-sition executed by the system if the guard condition evaluates to mandoften has the form<expression>...<expression>, which means that in the next state(i.e.,that obtained after the transition has beenexecuted),state variable is assigned the result of evaluating arithmetic expres-sion<expression>If the transition must be chosen probabilistically,the discrete probability dis-tribution is specified as[]<guard>-><prob1>:<command1>+...+<probN>:<commandN>;Transition represented by command is executed with probability prob,and prob.Security properties to be checked are stated as PCTL formulas (see section2.1).5Given a formal system specification,PRISM constructs the Markov chain and determines the set of reachable states,using MTBDDs and BDDs,respectively. Model checking a PCTL formula reduces to a combination of reachability-based computation and solving a system of linear equations to determine the probability of satisfying the formula in each reachable state.The model checking algorithms employed by PRISM include[BdA95,BK98,Bai98].More details about the im-plementation and operation of PRISM can be found at http://www.cs.bham. /˜dxp/prism/and in[KNP01].Since PRISM only supports model checking offinite DTMC,in our case study of Crowds we only analyze anonymity properties offinite instances of the system. By changing parameters of the model,we demonstrate how anonymity properties evolve with changes in the system configuration.Wright et al.[W ALS02]investi-gated related properties of the Crowds system in the general case,but they do not rely on tool support and their analyses are manual rather than automated.3Crowds Anonymity SystemProviding an anonymous communication service on the Internet is a challenging task.While conventional security mechanisms such as encryption can be used to protect the content of messages and transactions,eavesdroppers can still observe the IP addresses of communicating computers,timing and frequency of communi-cation,etc.A Web server can trace the source of the incoming connection,further compromising anonymity.The Crowds system was developed by Reiter and Ru-bin[RR98]for protecting users’anonymity on the Web.The main idea behind gossip-based approaches to anonymity such as Crowds is to hide each user’s communications by routing them randomly within a crowd of similar users.Even if an eavesdropper observes a message being sent by a particular user,it can never be sure whether the user is the actual sender,or is simply routing another user’s message.3.1Path setup protocolA crowd is a collection of users,each of whom is running a special process called a jondo which acts as the user’s proxy.Some of the jondos may be corrupt and/or controlled by the adversary.Corrupt jondos may collaborate and share their obser-vations in an attempt to compromise the honest users’anonymity.Note,however, that all observations by corrupt group members are local.Each corrupt member may observe messages sent to it,but not messages transmitted on the links be-tween honest jondos.An honest crowd member has no way of determining whether6a particular jondo is honest or corrupt.The parameters of the system are the total number of members,the number of corrupt members,and the forwarding probability which is explained below.To participate in communication,all jondos must register with a special server which maintains membership information.Therefore,every member of the crowd knows identities of all other members.As part of the join procedure,the members establish pairwise encryption keys which are used to encrypt pairwise communi-cation,so the contents of the messages are secret from an external eavesdropper.Anonymity guarantees provided by Crowds are based on the path setup pro-tocol,which is described in the rest of this section.The path setup protocol is executed each time one of the crowd members wants to establish an anonymous connection to a Web server.Once a routing path through the crowd is established, all subsequent communication between the member and the Web server is routed along it.We will call one run of the path setup protocol a session.When crowd membership changes,the existing paths must be scrapped and a new protocol ses-sion must be executed in order to create a new random routing path through the crowd to the destination.Therefore,we’ll use terms path reformulation and proto-col session interchangeably.When a user wants to establish a connection with a Web server,its browser sends a request to the jondo running locally on her computer(we will call this jondo the initiator).Each request contains information about the intended desti-nation.Since the objective of Crowds is to protect the sender’s identity,it is not problematic that a corrupt router can learn the recipient’s identity.The initiator starts the process of creating a random path to the destination as follows: The initiator selects a crowd member at random(possibly itself),and for-wards the request to it,encrypted by the corresponding pairwise key.We’ll call the selected member the forwarder.The forwarderflips a biased coin.With probability,it delivers the request directly to the destination.With probability,it selects a crowd member at random(possibly itself)as the next forwarder in the path,and forwards the request to it,re-encrypted with the appropriate pairwise key.The next forwarder then repeats this step.Each forwarder maintains an identifier for the created path.If the same jondo appears in different positions on the same path,identifiers are different to avoid infinite loops.Each subsequent message from the initiator to the destination is routed along this path,i.e.,the paths are static—once established,they are not altered often.This is necessary to hinder corrupt members from linking multiple7paths originating from the same initiator,and using this information to compromise the initiator’s anonymity as described in section3.2.3.3.2Anonymity properties of CrowdsThe Crowds paper[RR98]describes several degrees of anonymity that may be provided by a communication system.Without using anonymizing techniques, none of the following properties are guaranteed on the Web since browser requests contain information about their source and destination in the clear.Beyond suspicion Even if the adversary can see evidence of a sent message,the real sender appears to be no more likely to have originated it than any other potential sender in the system.Probable innocence The real sender appears no more likely to be the originator of the message than to not be the originator,i.e.,the probability that the adversary observes the real sender as the source of the message is less thanupper bound on the probability of detection.If the sender is observed by the adversary,she can then plausibly argue that she has been routing someone else’s messages.The Crowds paper focuses on providing anonymity against local,possibly co-operating eavesdroppers,who can share their observations of communication in which they are involved as forwarders,but cannot observe communication involv-ing only honest members.We also limit our analysis to this case.3.2.1Anonymity for a single routeIt is proved in[RR98]that,for any given routing path,the path initiator in a crowd of members with forwarding probability has probable innocence against collaborating crowd members if the following inequality holds:(1)More formally,let be the event that at least one of the corrupt crowd members is selected for the path,and be the event that the path initiator appears in8the path immediately before a corrupt crowd member(i.e.,the adversary observes the real sender as the source of the messages routed along the path).Condition 1guarantees thatproving that,given multiple linked paths,the initiator appears more often as a sus-pect than a random crowd member.The automated analysis described in section6.1 confirms and quantifies this result.(The technical results of[Shm02]on which this paper is based had been developed independently of[Mal01]and[W ALS02],be-fore the latter was published).In general,[Mal01]and[W ALS02]conjecture that there can be no reliable anonymity method for peer-to-peer communication if in order to start a new communication session,the initiator must originate thefirst connection before any processing of the session commences.This implies that anonymity is impossible in a gossip-based system with corrupt routers in the ab-sence of decoy traffic.In section6.3,we show that,for any given number of observed paths,the adversary’s confidence in its observations increases with the size of the crowd.This result contradicts the intuitive notion that bigger crowds provide better anonymity guarantees.It was discovered by automated analysis.4Formal Model of CrowdsIn this section,we describe our probabilistic formal model of the Crowds system. Since there is no non-determinism in the protocol specification(see section3.1), the model is a simple discrete-time Markov chain as opposed to a Markov deci-sion process.In addition to modeling the behavior of the honest crowd members, we also formalize the adversary.The protocol does not aim to provide anonymity against global eavesdroppers.Therefore,it is sufficient to model the adversary as a coalition of corrupt crowd members who only have access to local communication channels,i.e.,they can only make observations about a path if one of them is se-lected as a forwarder.By the same token,it is not necessary to model cryptographic functions,since corrupt members know the keys used to encrypt peer-to-peer links in which they are one of the endpoints,and have no access to links that involve only honest members.The modeling technique presented in this section is applicable with minor mod-ifications to any probabilistic routing system.In each state of routing path construc-tion,the discrete probability distribution given by the protocol specification is used directly to define the probabilistic transition rule for choosing the next forwarder on the path,if any.If the protocol prescribes an upper bound on the length of the path(e.g.,Freenet[CSWH01]),the bound can be introduced as a system parameter as described in section4.2.3,with the corresponding increase in the size of the state space but no conceptual problems.Probabilistic model checking can then be used to check the validity of PCTL formulas representing properties of the system.In the general case,forwarder selection may be governed by non-deterministic10runCount goodbad lastSeen observelaunchnewstartrundeliver recordLast badObserve4.2Model of honest members4.2.1InitiationPath construction is initiated as follows(syntax of PRISM is described in section 2.2):[]launch->runCount’=TotalRuns&new’=true&launch’=false;[]new&(runCount>0)->(runCount’=runCount-1)&new’=false&start’=true;[]start->lastSeen’=0&deliver’=false&run’=true&start’=false;4.2.2Forwarder selectionThe initiator(i.e.,thefirst crowd member on the path,the one whose identity must be protected)randomly chooses thefirst forwarder from among all group mem-bers.We assume that all group members have an equal probability of being chosen, but the technique can support any discrete probability distribution for choosing for-warders.Forwarder selection is a single step of the protocol,but we model it as two probabilistic state transitions.Thefirst determines whether the selected forwarder is honest or corrupt,the second determines the forwarder’s identity.The randomly selected forwarder is corrupt with probability badCbe next on the path.Any of the honest crowd members can be selected as the forwarder with equal probability.To illustrate,for a crowd with10honest members,the following transition models the second step of forwarder selection: []recordLast&CrowdSize=10->0.1:lastSeen’=0&run’=true&recordLast’=false+0.1:lastSeen’=1&run’=true&recordLast’=false+...0.1:lastSeen’=9&run’=true&recordLast’=false;According to the protocol,each honest crowd member must decide whether to continue building the path byflipping a biased coin.With probability,the forwarder selection transition is enabled again and path construction continues, and with probability the path is terminated at the current forwarder,and all requests arriving from the initiator along the path will be delivered directly to the recipient.[](good&!deliver&run)->//Continue path constructionPF:good’=false+//Terminate path constructionnotPF:deliver’=true;The specification of the Crowds system imposes no upper bound on the length of the path.Moreover,the forwarders are not permitted to know their relative position on the path.Note,however,that the amount of information about the initiator that can be extracted by the adversary from any path,or anyfinite number of paths,isfinite(see sections4.3and4.5).In systems such as Freenet[CSWH01],requests have a hops-to-live counter to prevent infinite paths,except with very small probability.To model this counter,we may introduce an additional state variable pIndex that keeps track of the length of the path constructed so far.The path construction transition is then coded as follows://Example with Hops-To-Live//(NOT CROWDS)////Forward with prob.PF,else deliver13[](good&!deliver&run&pIndex<MaxPath)->PF:good’=false&pIndex’=pIndex+1+notPF:deliver’=true;//Terminate if reached MaxPath,//but sometimes not//(to confuse adversary)[](good&!deliver&run&pIndex=MaxPath)->smallP:good’=false+largeP:deliver’=true;Introduction of pIndex obviously results in exponential state space explosion, decreasing the maximum system size for which model checking is feasible.4.2.4Transition matrix for honest membersTo summarize the state space of the discrete-time Markov chain representing cor-rect behavior of protocol participants(i.e.,the state space induced by the abovetransitions),let be the state in which links of the th routing path from the initiator have already been constructed,and assume that are the honestforwarders selected for the path.Let be the state in which path constructionhas terminated with as thefinal path,and let be an auxiliary state. Then,given the set of honest crowd members s.t.,the transi-tion matrix is such that,,(see section4.2.2),i.e.,the probability of selecting the adversary is equal to the cumulative probability of selecting some corrupt member.14This abstraction does not limit the class of attacks that can be discovered using the approach proposed in this paper.Any attack found in the model where indi-vidual corrupt members are kept separate will be found in the model where their capabilities are combined in a single worst-case adversary.The reason for this is that every observation made by one of the corrupt members in the model with separate corrupt members will be made by the adversary in the model where their capabilities are combined.The amount of information available to the worst-case adversary and,consequently,the inferences that can be made from it are at least as large as those available to any individual corrupt member or a subset thereof.In the adversary model of[RR98],each corrupt member can only observe its local network.Therefore,it only learns the identity of the crowd member imme-diately preceding it on the path.We model this by having the corrupt member read the value of the lastSeen variable,and record its observations.This cor-responds to reading the source IP address of the messages arriving along the path. For example,for a crowd of size10,the transition is as follows:[]lastSeen=0&badObserve->observe0’=observe0+1&deliver’=true&run’=true&badObserve’=false;...[]lastSeen=9&badObserve->observe9’=observe9+1&deliver’=true&run’=true&badObserve’=false;The counters observe are persistent,i.e.,they are not reset for each session of the path setup protocol.This allows the adversary to accumulate observations over several path reformulations.We assume that the adversary can detect when two paths originate from the same member whose identity is unknown(see sec-tion3.2.2).The adversary is only interested in learning the identity of thefirst crowd mem-ber in the path.Continuing path construction after one of the corrupt members has been selected as a forwarder does not provide the adversary with any new infor-mation.This is a very important property since it helps keep the model of the adversaryfinite.Even though there is no bound on the length of the path,at most one observation per path is useful to the adversary.To simplify the model,we as-sume that the path terminates as soon as it reaches a corrupt member(modeled by deliver’=true in the transition above).This is done to shorten the average path length without decreasing the power of the adversary.15Each forwarder is supposed toflip a biased coin to decide whether to terminate the path,but the coinflips are local to the forwarder and cannot be observed by other members.Therefore,honest members cannot detect without cooperation that corrupt members always terminate paths.In any case,corrupt members can make their observable behavior indistinguishable from that of the honest members by continuing the path with probability as described in section4.2.3,even though this yields no additional information to the adversary.4.4Multiple pathsThe discrete-time Markov chain defined in sections4.2and4.3models construc-tion of a single path through the crowd.As explained in section3.2.2,paths have to be reformulated periodically.The decision to rebuild the path is typically made according to a pre-determined schedule,e.g.,hourly,daily,or once enough new members have asked to join the crowd.For the purposes of our analysis,we sim-ply assume that paths are reformulated somefinite number of times(determined by the system parameter=TotalRuns).We analyze anonymity properties provided by Crowds after successive path reformulations by considering the state space produced by successive execu-tions of the path construction protocol described in section4.2.As explained in section4.3,the adversary is permitted to combine its observations of some or all of the paths that have been constructed(the adversary only observes the paths for which some corrupt member was selected as one of the forwarders).The adversary may then use this information to infer the path initiator’s identity.Because for-warder selection is probabilistic,the adversary’s ability to collect enough informa-tion to successfully identify the initiator can only be characterized probabilistically, as explained in section5.4.5Finiteness of the adversary’s state spaceThe state space of the honest members defined by the transition matrix of sec-tion4.2.4is infinite since there is no a priori upper bound on the length of each path.Corrupt members,however,even if they collaborate,can make at most one observation per path,as explained in section4.3.As long as the number of path reformulations is bounded(see section4.4),only afinite number of paths will be constructed and the adversary will be able to make only afinite number of observa-tions.Therefore,the adversary only needsfinite memory and the adversary’s state space isfinite.In general,anonymity is violated if the adversary has a high probability of making a certain observation(see section5).Tofind out whether Crowds satisfies16。
BLUE FOCUS CHINA The Booming PR Industry in China 0419【精选】

International companies entering the Chinese market
New comer foreign enterprises in the Chinese market: Most of them are sales companies who only set up offices in China. Their market share in China is waiting to be expanded and most of their brands are promoted by distributors or agents, without the setup of PR department. These companies are not yet well-known in China. They don’t have a clear long-term promotion strategy. They mainly need services such as activity management, exhibition promotion and crisis management.
Since the reform and opening up in the 1970’s, many special economic zones have been set up in coastal cities of China to draw foreign investment.
This brought in many multi-national companies into the Chinese market. They built factories and sold products here, and also established their PR department, which gave birth to an emerging industry.
T.W. ANDERSON (1971). The Statistical Analysis of Time Series. Series in Probability and Ma

425 BibliographyH.A KAIKE(1974).Markovian representation of stochastic processes and its application to the analysis of autoregressive moving average processes.Annals Institute Statistical Mathematics,vol.26,pp.363-387. B.D.O.A NDERSON and J.B.M OORE(1979).Optimal rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.T.W.A NDERSON(1971).The Statistical Analysis of Time Series.Series in Probability and Mathematical Statistics,Wiley,New York.R.A NDRE-O BRECHT(1988).A new statistical approach for the automatic segmentation of continuous speech signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-36,no1,pp.29-40.R.A NDRE-O BRECHT(1990).Reconnaissance automatique de parole`a partir de segments acoustiques et de mod`e les de Markov cach´e s.Proc.Journ´e es Etude de la Parole,Montr´e al,May1990(in French).R.A NDRE-O BRECHT and H.Y.S U(1988).Three acoustic labellings for phoneme based continuous speech recognition.Proc.Speech’88,Edinburgh,UK,pp.943-950.U.A PPEL and A.VON B RANDT(1983).Adaptive sequential segmentation of piecewise stationary time rmation Sciences,vol.29,no1,pp.27-56.L.A.A ROIAN and H.L EVENE(1950).The effectiveness of quality control procedures.Jal American Statis-tical Association,vol.45,pp.520-529.K.J.A STR¨OM and B.W ITTENMARK(1984).Computer Controlled Systems:Theory and rma-tion and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.M.B AGSHAW and R.A.J OHNSON(1975a).The effect of serial correlation on the performance of CUSUM tests-Part II.Technometrics,vol.17,no1,pp.73-80.M.B AGSHAW and R.A.J OHNSON(1975b).The influence of reference values and estimated variance on the ARL of CUSUM tests.Jal Royal Statistical Society,vol.37(B),no3,pp.413-420.M.B AGSHAW and R.A.J OHNSON(1977).Sequential procedures for detecting parameter changes in a time-series model.Jal American Statistical Association,vol.72,no359,pp.593-597.R.K.B ANSAL and P.P APANTONI-K AZAKOS(1986).An algorithm for detecting a change in a stochastic process.IEEE rmation Theory,vol.IT-32,no2,pp.227-235.G.A.B ARNARD(1959).Control charts and stochastic processes.Jal Royal Statistical Society,vol.B.21, pp.239-271.A.E.B ASHARINOV andB.S.F LEISHMAN(1962).Methods of the statistical sequential analysis and their radiotechnical applications.Sovetskoe Radio,Moscow(in Russian).M.B ASSEVILLE(1978).D´e viations par rapport au maximum:formules d’arrˆe t et martingales associ´e es. Compte-rendus du S´e minaire de Probabilit´e s,Universit´e de Rennes I.M.B ASSEVILLE(1981).Edge detection using sequential methods for change in level-Part II:Sequential detection of change in mean.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-29,no1,pp.32-50.426B IBLIOGRAPHY M.B ASSEVILLE(1982).A survey of statistical failure detection techniques.In Contribution`a la D´e tectionS´e quentielle de Ruptures de Mod`e les Statistiques,Th`e se d’Etat,Universit´e de Rennes I,France(in English). M.B ASSEVILLE(1986).The two-models approach for the on-line detection of changes in AR processes. In Detection of Abrupt Changes in Signals and Dynamical Systems(M.Basseville,A.Benveniste,eds.). Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York,pp.169-215.M.B ASSEVILLE(1988).Detecting changes in signals and systems-A survey.Automatica,vol.24,pp.309-326.M.B ASSEVILLE(1989).Distance measures for signal processing and pattern recognition.Signal Process-ing,vol.18,pp.349-369.M.B ASSEVILLE and A.B ENVENISTE(1983a).Design and comparative study of some sequential jump detection algorithms for digital signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-31, no3,pp.521-535.M.B ASSEVILLE and A.B ENVENISTE(1983b).Sequential detection of abrupt changes in spectral charac-teristics of digital signals.IEEE rmation Theory,vol.IT-29,no5,pp.709-724.M.B ASSEVILLE and A.B ENVENISTE,eds.(1986).Detection of Abrupt Changes in Signals and Dynamical Systems.Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York.M.B ASSEVILLE and I.N IKIFOROV(1991).A unified framework for statistical change detection.Proc.30th IEEE Conference on Decision and Control,Brighton,UK.M.B ASSEVILLE,B.E SPIAU and J.G ASNIER(1981).Edge detection using sequential methods for change in level-Part I:A sequential edge detection algorithm.IEEE Trans.Acoustics,Speech,Signal Processing, vol.ASSP-29,no1,pp.24-31.M.B ASSEVILLE, A.B ENVENISTE and G.M OUSTAKIDES(1986).Detection and diagnosis of abrupt changes in modal characteristics of nonstationary digital signals.IEEE rmation Theory,vol.IT-32,no3,pp.412-417.M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987a).Detection and diagnosis of changes in the eigenstructure of nonstationary multivariable systems.Automatica,vol.23,no3,pp.479-489. M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987b).Optimal sensor location for detecting changes in dynamical behavior.IEEE Trans.Automatic Control,vol.AC-32,no12,pp.1067-1075.M.B ASSEVILLE,A.B ENVENISTE,B.G ACH-D EVAUCHELLE,M.G OURSAT,D.B ONNECASE,P.D OREY, M.P REVOSTO and M.O LAGNON(1993).Damage monitoring in vibration mechanics:issues in diagnos-tics and predictive maintenance.Mechanical Systems and Signal Processing,vol.7,no5,pp.401-423.R.V.B EARD(1971).Failure Accommodation in Linear Systems through Self-reorganization.Ph.D.Thesis, Dept.Aeronautics and Astronautics,MIT,Cambridge,MA.A.B ENVENISTE and J.J.F UCHS(1985).Single sample modal identification of a nonstationary stochastic process.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.66-74.A.B ENVENISTE,M.B ASSEVILLE and G.M OUSTAKIDES(1987).The asymptotic local approach to change detection and model validation.IEEE Trans.Automatic Control,vol.AC-32,no7,pp.583-592.A.B ENVENISTE,M.M ETIVIER and P.P RIOURET(1990).Adaptive Algorithms and Stochastic Approxima-tions.Series on Applications of Mathematics,(A.V.Balakrishnan,I.Karatzas,M.Yor,eds.).Springer,New York.A.B ENVENISTE,M.B ASSEVILLE,L.E L G HAOUI,R.N IKOUKHAH and A.S.W ILLSKY(1992).An optimum robust approach to statistical failure detection and identification.IFAC World Conference,Sydney, July1993.B IBLIOGRAPHY427 R.H.B ERK(1973).Some asymptotic aspects of sequential analysis.Annals Statistics,vol.1,no6,pp.1126-1138.R.H.B ERK(1975).Locally most powerful sequential test.Annals Statistics,vol.3,no2,pp.373-381.P.B ILLINGSLEY(1968).Convergence of Probability Measures.Wiley,New York.A.F.B ISSELL(1969).Cusum techniques for quality control.Applied Statistics,vol.18,pp.1-30.M.E.B IVAIKOV(1991).Control of the sample size for recursive estimation of parameters subject to abrupt changes.Automation and Remote Control,no9,pp.96-103.R.E.B LAHUT(1987).Principles and Practice of Information Theory.Addison-Wesley,Reading,MA.I.F.B LAKE and W.C.L INDSEY(1973).Level-crossing problems for random processes.IEEE r-mation Theory,vol.IT-19,no3,pp.295-315.G.B ODENSTEIN and H.M.P RAETORIUS(1977).Feature extraction from the encephalogram by adaptive segmentation.Proc.IEEE,vol.65,pp.642-652.T.B OHLIN(1977).Analysis of EEG signals with changing spectra using a short word Kalman estimator. Mathematical Biosciences,vol.35,pp.221-259.W.B¨OHM and P.H ACKL(1990).Improved bounds for the average run length of control charts based on finite weighted sums.Annals Statistics,vol.18,no4,pp.1895-1899.T.B OJDECKI and J.H OSZA(1984).On a generalized disorder problem.Stochastic Processes and their Applications,vol.18,pp.349-359.L.I.B ORODKIN and V.V.M OTTL’(1976).Algorithm forfinding the jump times of random process equation parameters.Automation and Remote Control,vol.37,no6,Part1,pp.23-32.A.A.B OROVKOV(1984).Theory of Mathematical Statistics-Estimation and Hypotheses Testing,Naouka, Moscow(in Russian).Translated in French under the title Statistique Math´e matique-Estimation et Tests d’Hypoth`e ses,Mir,Paris,1987.G.E.P.B OX and G.M.J ENKINS(1970).Time Series Analysis,Forecasting and Control.Series in Time Series Analysis,Holden-Day,San Francisco.A.VON B RANDT(1983).Detecting and estimating parameters jumps using ladder algorithms and likelihood ratio test.Proc.ICASSP,Boston,MA,pp.1017-1020.A.VON B RANDT(1984).Modellierung von Signalen mit Sprunghaft Ver¨a nderlichem Leistungsspektrum durch Adaptive Segmentierung.Doctor-Engineer Dissertation,M¨u nchen,RFA(in German).S.B RAUN,ed.(1986).Mechanical Signature Analysis-Theory and Applications.Academic Press,London. L.B REIMAN(1968).Probability.Series in Statistics,Addison-Wesley,Reading,MA.G.S.B RITOV and L.A.M IRONOVSKI(1972).Diagnostics of linear systems of automatic regulation.Tekh. Kibernetics,vol.1,pp.76-83.B.E.B RODSKIY and B.S.D ARKHOVSKIY(1992).Nonparametric Methods in Change-point Problems. Kluwer Academic,Boston.L.D.B ROEMELING(1982).Jal Econometrics,vol.19,Special issue on structural change in Econometrics. L.D.B ROEMELING and H.T SURUMI(1987).Econometrics and Structural Change.Dekker,New York. D.B ROOK and D.A.E VANS(1972).An approach to the probability distribution of Cusum run length. Biometrika,vol.59,pp.539-550.J.B RUNET,D.J AUME,M.L ABARR`E RE,A.R AULT and M.V ERG´E(1990).D´e tection et Diagnostic de Pannes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).428B IBLIOGRAPHY S.P.B RUZZONE and M.K AVEH(1984).Information tradeoffs in using the sample autocorrelation function in ARMA parameter estimation.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-32,no4, pp.701-715.A.K.C AGLAYAN(1980).Necessary and sufficient conditions for detectability of jumps in linear systems. IEEE Trans.Automatic Control,vol.AC-25,no4,pp.833-834.A.K.C AGLAYAN and R.E.L ANCRAFT(1983).Reinitialization issues in fault tolerant systems.Proc.Amer-ican Control Conf.,pp.952-955.A.K.C AGLAYAN,S.M.A LLEN and K.W EHMULLER(1988).Evaluation of a second generation reconfigu-ration strategy for aircraftflight control systems subjected to actuator failure/surface damage.Proc.National Aerospace and Electronic Conference,Dayton,OH.P.E.C AINES(1988).Linear Stochastic Systems.Series in Probability and Mathematical Statistics,Wiley, New York.M.J.C HEN and J.P.N ORTON(1987).Estimation techniques for tracking rapid parameter changes.Intern. Jal Control,vol.45,no4,pp.1387-1398.W.K.C HIU(1974).The economic design of cusum charts for controlling normal mean.Applied Statistics, vol.23,no3,pp.420-433.E.Y.C HOW(1980).A Failure Detection System Design Methodology.Ph.D.Thesis,M.I.T.,L.I.D.S.,Cam-bridge,MA.E.Y.C HOW and A.S.W ILLSKY(1984).Analytical redundancy and the design of robust failure detection systems.IEEE Trans.Automatic Control,vol.AC-29,no3,pp.689-691.Y.S.C HOW,H.R OBBINS and D.S IEGMUND(1971).Great Expectations:The Theory of Optimal Stop-ping.Houghton-Mifflin,Boston.R.N.C LARK,D.C.F OSTH and V.M.W ALTON(1975).Detection of instrument malfunctions in control systems.IEEE Trans.Aerospace Electronic Systems,vol.AES-11,pp.465-473.A.C OHEN(1987).Biomedical Signal Processing-vol.1:Time and Frequency Domain Analysis;vol.2: Compression and Automatic Recognition.CRC Press,Boca Raton,FL.J.C ORGE and F.P UECH(1986).Analyse du rythme cardiaque foetal par des m´e thodes de d´e tection de ruptures.Proc.7th INRIA Int.Conf.Analysis and optimization of Systems.Antibes,FR(in French).D.R.C OX and D.V.H INKLEY(1986).Theoretical Statistics.Chapman and Hall,New York.D.R.C OX and H.D.M ILLER(1965).The Theory of Stochastic Processes.Wiley,New York.S.V.C ROWDER(1987).A simple method for studying run-length distributions of exponentially weighted moving average charts.Technometrics,vol.29,no4,pp.401-407.H.C S¨ORG¨O and L.H ORV´ATH(1988).Nonparametric methods for change point problems.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.403-425.R.B.D AVIES(1973).Asymptotic inference in stationary gaussian time series.Advances Applied Probability, vol.5,no3,pp.469-497.J.C.D ECKERT,M.N.D ESAI,J.J.D EYST and A.S.W ILLSKY(1977).F-8DFBW sensor failure identification using analytical redundancy.IEEE Trans.Automatic Control,vol.AC-22,no5,pp.795-803.M.H.D E G ROOT(1970).Optimal Statistical Decisions.Series in Probability and Statistics,McGraw-Hill, New York.J.D ESHAYES and D.P ICARD(1979).Tests de ruptures dans un mod`e pte-Rendus de l’Acad´e mie des Sciences,vol.288,Ser.A,pp.563-566(in French).B IBLIOGRAPHY429 J.D ESHAYES and D.P ICARD(1983).Ruptures de Mod`e les en Statistique.Th`e ses d’Etat,Universit´e deParis-Sud,Orsay,France(in French).J.D ESHAYES and D.P ICARD(1986).Off-line statistical analysis of change-point models using non para-metric and likelihood methods.In Detection of Abrupt Changes in Signals and Dynamical Systems(M. Basseville,A.Benveniste,eds.).Lecture Notes in Control and Information Sciences,LNCIS77,Springer, New York,pp.103-168.B.D EVAUCHELLE-G ACH(1991).Diagnostic M´e canique des Fatigues sur les Structures Soumises`a des Vibrations en Ambiance de Travail.Th`e se de l’Universit´e Paris IX Dauphine(in French).B.D EVAUCHELLE-G ACH,M.B ASSEVILLE and A.B ENVENISTE(1991).Diagnosing mechanical changes in vibrating systems.Proc.SAFEPROCESS’91,Baden-Baden,FRG,pp.85-89.R.D I F RANCESCO(1990).Real-time speech segmentation using pitch and convexity jump models:applica-tion to variable rate speech coding.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-38,no5, pp.741-748.X.D ING and P.M.F RANK(1990).Fault detection via factorization approach.Systems and Control Letters, vol.14,pp.431-436.J.L.D OOB(1953).Stochastic Processes.Wiley,New York.V.D RAGALIN(1988).Asymptotic solutions in detecting a change in distribution under an unknown param-eter.Statistical Problems of Control,Issue83,Vilnius,pp.45-52.B.D UBUISSON(1990).Diagnostic et Reconnaissance des Formes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).A.J.D UNCAN(1986).Quality Control and Industrial Statistics,5th edition.Richard D.Irwin,Inc.,Home-wood,IL.J.D URBIN(1971).Boundary-crossing probabilities for the Brownian motion and Poisson processes and techniques for computing the power of the Kolmogorov-Smirnov test.Jal Applied Probability,vol.8,pp.431-453.J.D URBIN(1985).Thefirst passage density of the crossing of a continuous Gaussian process to a general boundary.Jal Applied Probability,vol.22,no1,pp.99-122.A.E MAMI-N AEINI,M.M.A KHTER and S.M.R OCK(1988).Effect of model uncertainty on failure detec-tion:the threshold selector.IEEE Trans.Automatic Control,vol.AC-33,no12,pp.1106-1115.J.D.E SARY,F.P ROSCHAN and D.W.W ALKUP(1967).Association of random variables with applications. Annals Mathematical Statistics,vol.38,pp.1466-1474.W.D.E WAN and K.W.K EMP(1960).Sampling inspection of continuous processes with no autocorrelation between successive results.Biometrika,vol.47,pp.263-280.G.F AVIER and A.S MOLDERS(1984).Adaptive smoother-predictors for tracking maneuvering targets.Proc. 23rd Conf.Decision and Control,Las Vegas,NV,pp.831-836.W.F ELLER(1966).An Introduction to Probability Theory and Its Applications,vol.2.Series in Probability and Mathematical Statistics,Wiley,New York.R.A.F ISHER(1925).Theory of statistical estimation.Proc.Cambridge Philosophical Society,vol.22, pp.700-725.M.F ISHMAN(1988).Optimization of the algorithm for the detection of a disorder,based on the statistic of exponential smoothing.In Statistical Problems of Control,Issue83,Vilnius,pp.146-151.R.F LETCHER(1980).Practical Methods of Optimization,2volumes.Wiley,New York.P.M.F RANK(1990).Fault diagnosis in dynamic systems using analytical and knowledge based redundancy -A survey and new results.Automatica,vol.26,pp.459-474.430B IBLIOGRAPHY P.M.F RANK(1991).Enhancement of robustness in observer-based fault detection.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.275-287.P.M.F RANK and J.W¨UNNENBERG(1989).Robust fault diagnosis using unknown input observer schemes. In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R.Clark,eds.). International Series in Systems and Control Engineering,Prentice Hall International,London,UK,pp.47-98.K.F UKUNAGA(1990).Introduction to Statistical Pattern Recognition,2d ed.Academic Press,New York. S.I.G ASS(1958).Linear Programming:Methods and Applications.McGraw Hill,New York.W.G E and C.Z.F ANG(1989).Extended robust observation approach for failure isolation.Int.Jal Control, vol.49,no5,pp.1537-1553.W.G ERSCH(1986).Two applications of parametric time series modeling methods.In Mechanical Signature Analysis-Theory and Applications(S.Braun,ed.),chap.10.Academic Press,London.J.J.G ERTLER(1988).Survey of model-based failure detection and isolation in complex plants.IEEE Control Systems Magazine,vol.8,no6,pp.3-11.J.J.G ERTLER(1991).Analytical redundancy methods in fault detection and isolation.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.9-22.B.K.G HOSH(1970).Sequential Tests of Statistical Hypotheses.Addison-Wesley,Cambridge,MA.I.N.G IBRA(1975).Recent developments in control charts techniques.Jal Quality Technology,vol.7, pp.183-192.J.P.G ILMORE and R.A.M C K ERN(1972).A redundant strapdown inertial reference unit(SIRU).Jal Space-craft,vol.9,pp.39-47.M.A.G IRSHICK and H.R UBIN(1952).A Bayes approach to a quality control model.Annals Mathematical Statistics,vol.23,pp.114-125.A.L.G OEL and S.M.W U(1971).Determination of the ARL and a contour nomogram for CUSUM charts to control normal mean.Technometrics,vol.13,no2,pp.221-230.P.L.G OLDSMITH and H.W HITFIELD(1961).Average run lengths in cumulative chart quality control schemes.Technometrics,vol.3,pp.11-20.G.C.G OODWIN and K.S.S IN(1984).Adaptive Filtering,Prediction and rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.R.M.G RAY and L.D.D AVISSON(1986).Random Processes:a Mathematical Approach for Engineers. Information and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.C.G UEGUEN and L.L.S CHARF(1980).Exact maximum likelihood identification for ARMA models:a signal processing perspective.Proc.1st EUSIPCO,Lausanne.D.E.G USTAFSON, A.S.W ILLSKY,J.Y.W ANG,M.C.L ANCASTER and J.H.T RIEBWASSER(1978). ECG/VCG rhythm diagnosis using statistical signal analysis.Part I:Identification of persistent rhythms. Part II:Identification of transient rhythms.IEEE Trans.Biomedical Engineering,vol.BME-25,pp.344-353 and353-361.F.G USTAFSSON(1991).Optimal segmentation of linear regression parameters.Proc.IFAC/IFORS Symp. Identification and System Parameter Estimation,Budapest,pp.225-229.T.H¨AGGLUND(1983).New Estimation Techniques for Adaptive Control.Ph.D.Thesis,Lund Institute of Technology,Lund,Sweden.T.H¨AGGLUND(1984).Adaptive control of systems subject to large parameter changes.Proc.IFAC9th World Congress,Budapest.B IBLIOGRAPHY431 P.H ALL and C.C.H EYDE(1980).Martingale Limit Theory and its Application.Probability and Mathemat-ical Statistics,a Series of Monographs and Textbooks,Academic Press,New York.W.J.H ALL,R.A.W IJSMAN and J.K.G HOSH(1965).The relationship between sufficiency and invariance with applications in sequential analysis.Ann.Math.Statist.,vol.36,pp.576-614.E.J.H ANNAN and M.D EISTLER(1988).The Statistical Theory of Linear Systems.Series in Probability and Mathematical Statistics,Wiley,New York.J.D.H EALY(1987).A note on multivariate CuSum procedures.Technometrics,vol.29,pp.402-412.D.M.H IMMELBLAU(1970).Process Analysis by Statistical Methods.Wiley,New York.D.M.H IMMELBLAU(1978).Fault Detection and Diagnosis in Chemical and Petrochemical Processes. Chemical Engineering Monographs,vol.8,Elsevier,Amsterdam.W.G.S.H INES(1976a).A simple monitor of a system with sudden parameter changes.IEEE r-mation Theory,vol.IT-22,no2,pp.210-216.W.G.S.H INES(1976b).Improving a simple monitor of a system with sudden parameter changes.IEEE rmation Theory,vol.IT-22,no4,pp.496-499.D.V.H INKLEY(1969).Inference about the intersection in two-phase regression.Biometrika,vol.56,no3, pp.495-504.D.V.H INKLEY(1970).Inference about the change point in a sequence of random variables.Biometrika, vol.57,no1,pp.1-17.D.V.H INKLEY(1971).Inference about the change point from cumulative sum-tests.Biometrika,vol.58, no3,pp.509-523.D.V.H INKLEY(1971).Inference in two-phase regression.Jal American Statistical Association,vol.66, no336,pp.736-743.J.R.H UDDLE(1983).Inertial navigation system error-model considerations in Kalmanfiltering applica-tions.In Control and Dynamic Systems(C.T.Leondes,ed.),Academic Press,New York,pp.293-339.J.S.H UNTER(1986).The exponentially weighted moving average.Jal Quality Technology,vol.18,pp.203-210.I.A.I BRAGIMOV and R.Z.K HASMINSKII(1981).Statistical Estimation-Asymptotic Theory.Applications of Mathematics Series,vol.16.Springer,New York.R.I SERMANN(1984).Process fault detection based on modeling and estimation methods-A survey.Auto-matica,vol.20,pp.387-404.N.I SHII,A.I WATA and N.S UZUMURA(1979).Segmentation of nonstationary time series.Int.Jal Systems Sciences,vol.10,pp.883-894.J.E.J ACKSON and R.A.B RADLEY(1961).Sequential and tests.Annals Mathematical Statistics, vol.32,pp.1063-1077.B.J AMES,K.L.J AMES and D.S IEGMUND(1988).Conditional boundary crossing probabilities with appli-cations to change-point problems.Annals Probability,vol.16,pp.825-839.M.K.J EERAGE(1990).Reliability analysis of fault-tolerant IMU architectures with redundant inertial sen-sors.IEEE Trans.Aerospace and Electronic Systems,vol.AES-5,no.7,pp.23-27.N.L.J OHNSON(1961).A simple theoretical approach to cumulative sum control charts.Jal American Sta-tistical Association,vol.56,pp.835-840.N.L.J OHNSON and F.C.L EONE(1962).Cumulative sum control charts:mathematical principles applied to their construction and use.Parts I,II,III.Industrial Quality Control,vol.18,pp.15-21;vol.19,pp.29-36; vol.20,pp.22-28.432B IBLIOGRAPHY R.A.J OHNSON and M.B AGSHAW(1974).The effect of serial correlation on the performance of CUSUM tests-Part I.Technometrics,vol.16,no.1,pp.103-112.H.L.J ONES(1973).Failure Detection in Linear Systems.Ph.D.Thesis,Dept.Aeronautics and Astronautics, MIT,Cambridge,MA.R.H.J ONES,D.H.C ROWELL and L.E.K APUNIAI(1970).Change detection model for serially correlated multivariate data.Biometrics,vol.26,no2,pp.269-280.M.J URGUTIS(1984).Comparison of the statistical properties of the estimates of the change times in an autoregressive process.In Statistical Problems of Control,Issue65,Vilnius,pp.234-243(in Russian).T.K AILATH(1980).Linear rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.L.V.K ANTOROVICH and V.I.K RILOV(1958).Approximate Methods of Higher Analysis.Interscience,New York.S.K ARLIN and H.M.T AYLOR(1975).A First Course in Stochastic Processes,2d ed.Academic Press,New York.S.K ARLIN and H.M.T AYLOR(1981).A Second Course in Stochastic Processes.Academic Press,New York.D.K AZAKOS and P.P APANTONI-K AZAKOS(1980).Spectral distance measures between gaussian pro-cesses.IEEE Trans.Automatic Control,vol.AC-25,no5,pp.950-959.K.W.K EMP(1958).Formula for calculating the operating characteristic and average sample number of some sequential tests.Jal Royal Statistical Society,vol.B-20,no2,pp.379-386.K.W.K EMP(1961).The average run length of the cumulative sum chart when a V-mask is used.Jal Royal Statistical Society,vol.B-23,pp.149-153.K.W.K EMP(1967a).Formal expressions which can be used for the determination of operating character-istics and average sample number of a simple sequential test.Jal Royal Statistical Society,vol.B-29,no2, pp.248-262.K.W.K EMP(1967b).A simple procedure for determining upper and lower limits for the average sample run length of a cumulative sum scheme.Jal Royal Statistical Society,vol.B-29,no2,pp.263-265.D.P.K ENNEDY(1976).Some martingales related to cumulative sum tests and single server queues.Stochas-tic Processes and Appl.,vol.4,pp.261-269.T.H.K ERR(1980).Statistical analysis of two-ellipsoid overlap test for real time failure detection.IEEE Trans.Automatic Control,vol.AC-25,no4,pp.762-772.T.H.K ERR(1982).False alarm and correct detection probabilities over a time interval for restricted classes of failure detection algorithms.IEEE rmation Theory,vol.IT-24,pp.619-631.T.H.K ERR(1987).Decentralizedfiltering and redundancy management for multisensor navigation.IEEE Trans.Aerospace and Electronic systems,vol.AES-23,pp.83-119.Minor corrections on p.412and p.599 (May and July issues,respectively).R.A.K HAN(1978).Wald’s approximations to the average run length in cusum procedures.Jal Statistical Planning and Inference,vol.2,no1,pp.63-77.R.A.K HAN(1979).Somefirst passage problems related to cusum procedures.Stochastic Processes and Applications,vol.9,no2,pp.207-215.R.A.K HAN(1981).A note on Page’s two-sided cumulative sum procedures.Biometrika,vol.68,no3, pp.717-719.B IBLIOGRAPHY433 V.K IREICHIKOV,V.M ANGUSHEV and I.N IKIFOROV(1990).Investigation and application of CUSUM algorithms to monitoring of sensors.In Statistical Problems of Control,Issue89,Vilnius,pp.124-130(in Russian).G.K ITAGAWA and W.G ERSCH(1985).A smoothness prior time-varying AR coefficient modeling of non-stationary covariance time series.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.48-56.N.K LIGIENE(1980).Probabilities of deviations of the change point estimate in statistical models.In Sta-tistical Problems of Control,Issue83,Vilnius,pp.80-86(in Russian).N.K LIGIENE and L.T ELKSNYS(1983).Methods of detecting instants of change of random process prop-erties.Automation and Remote Control,vol.44,no10,Part II,pp.1241-1283.J.K ORN,S.W.G ULLY and A.S.W ILLSKY(1982).Application of the generalized likelihood ratio algorithm to maneuver detection and estimation.Proc.American Control Conf.,Arlington,V A,pp.792-798.P.R.K RISHNAIAH and B.Q.M IAO(1988).Review about estimation of change points.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.375-402.P.K UDVA,N.V ISWANADHAM and A.R AMAKRISHNAN(1980).Observers for linear systems with unknown inputs.IEEE Trans.Automatic Control,vol.AC-25,no1,pp.113-115.S.K ULLBACK(1959).Information Theory and Statistics.Wiley,New York(also Dover,New York,1968). K.K UMAMARU,S.S AGARA and T.S¨ODERSTR¨OM(1989).Some statistical methods for fault diagnosis for dynamical systems.In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R. Clark,eds.).International Series in Systems and Control Engineering,Prentice Hall International,London, UK,pp.439-476.A.K USHNIR,I.N IKIFOROV and I.S AVIN(1983).Statistical adaptive algorithms for automatic detection of seismic signals-Part I:One-dimensional case.In Earthquake Prediction and the Study of the Earth Structure,Naouka,Moscow(Computational Seismology,vol.15),pp.154-159(in Russian).L.L ADELLI(1990).Diffusion approximation for a pseudo-likelihood test process with application to de-tection of change in stochastic system.Stochastics and Stochastics Reports,vol.32,pp.1-25.T.L.L A¨I(1974).Control charts based on weighted sums.Annals Statistics,vol.2,no1,pp.134-147.T.L.L A¨I(1981).Asymptotic optimality of invariant sequential probability ratio tests.Annals Statistics, vol.9,no2,pp.318-333.D.G.L AINIOTIS(1971).Joint detection,estimation,and system identifirmation and Control, vol.19,pp.75-92.M.R.L EADBETTER,G.L INDGREN and H.R OOTZEN(1983).Extremes and Related Properties of Random Sequences and Processes.Series in Statistics,Springer,New York.L.L E C AM(1960).Locally asymptotically normal families of distributions.Univ.California Publications in Statistics,vol.3,pp.37-98.L.L E C AM(1986).Asymptotic Methods in Statistical Decision Theory.Series in Statistics,Springer,New York.E.L.L EHMANN(1986).Testing Statistical Hypotheses,2d ed.Wiley,New York.J.P.L EHOCZKY(1977).Formulas for stopped diffusion processes with stopping times based on the maxi-mum.Annals Probability,vol.5,no4,pp.601-607.H.R.L ERCHE(1980).Boundary Crossing of Brownian Motion.Lecture Notes in Statistics,vol.40,Springer, New York.L.L JUNG(1987).System Identification-Theory for the rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.。
基尔斯特 LabAmp 5167Ax0 型号 电荷放大器和数据采集器 多通道测量说明书

Page 1/7Electronics & SoftwareKistler LabAmpCharge amplifier and data acquisition for multi-channel measurement5167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland . Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Type 5167Ax0This universal laboratory charge amplifier can be used wher-ever mechanical quantities are measured with multiple piezo-electric sensors. It covers slow, quasi-static signals as well as dynamic processes.Piezoelectric sensors produce an electric charge which varies in direct proportion with the load acting on the sensor. The amplifier converts this charge directly into digital values or a proportional output voltage.• 4- or 8-channel amplifier for piezoelectric sensors• Integrated 24-bit data acquisition with up to 100 kSps per channel• Continuous digital signal processing at minimal latency • Fully flexible low-pass, high-pass and notch filter adjust-ment• Low-noise design• 4 or 8 analog outputs with fully flexible 2-point scaling and internal routing• Status indication via LED• Virtual channels for real-time calculations using one or more sensor channels• Configuration and control in a standard web-browser • Virtual instrument driver for LabVIEW• Two Ethernet interfaces with included switch functionality • Digital inputs for Reset/Measure and TriggerDescriptionThe Kistler LabAmp Type 5167Ax0 is not only an outstanding low-noise charge amplifier for dynamic signals but also a pow-erful data acquisition device delivering the digitized measure-ment values directly to a host computer for further analysis. It is configured and operated in a web-interface, conveniently accessible by a standard web-browser.Thanks to advanced signal processing technology, the Kistler LabAmp Type 5167Ax0 offers impressive flexibility. The fre-quencies of the high-pass, low-pass and notch filters can be directly entered as numeric values in Hertz. The input signals can be flexibly routed to the analog outputs.The graphical user interface not only offers a simple and in-tuitive way to configure the device but also displays different measurement values (e.g. live value, peak value, root mean square). The virtual channel functionality allows real-time summation of different input signals.Furthermore, the browser-based data download allows the ac-quired data to be processed in an analysis software. For more advanced tasks or direct analysis, the amplifier can be inte-grated directly into LabVIEW thanks to the provided Virtual Instruments Driver.ApplicationWith its ability to measure quasi-static signals, Type 5167Ax0 is particularly suitable for multi-component force measure-ments in various applications in the laboratory as well as in research and development. For example, wheel force mea-surement on a tire test stand, reaction force measurements on engine-transmission units, monitoring of forces and torques in vibration tests etc.For higher channel counts, the synchronization feature allows acquiring data from multiple Type 5167A... devices. Kistler LabAmp Type 5165A... devices can be synchronized with the Type 5167A... as well which allows the combined acquisition of pure dynamic signals from other charge or Piezotron (IEPE)sensors or any voltage signals.Page 2/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Technical dataConnections Number of channels Type 5167A404Type 5167A808Input connector type BNC neg.Analog output connector type BNC neg.Ethernet interface 2xRJ45Remote control D-Sub 9fCharge input Measuring ranges pC ±100 … 1 000 000Frequency range (–3 dB)≤195 000 pC Hz ≈0 … >45 000>195 000 pC Hz≈0 … >15 000Input noise (typ.)1 Hz ... 100 kHz 100 pC pC rms 0,0091 000 pC pC rms 0,01910 000 pC pC rms 0,43100 000 pC pC rms 4,01 000 000 pC pC rms 8,51 Hz ... 10 kHz 100 pC pC rms 0,0071 000 pC pC rms 0,01210 000 pC pC rms 0,25100 000 pC pC rms 3,01 000 000 pCpC rms3,4Drift, measuring mode DC (Long)at 25 °C, max. relative humidity RH of 60 % (non-condensing)pC/s <±0,03at 25 °C, max. relative humidity RH of 70 % (non-condensing)pC/s <±0,05at 50 °C, max. relative humidity RH of 50 % (non-condensing)pC/s<±0,2Measure-jumpCompensatedMeasure-jump pC <±0,1Correction time ms<20Measurement uncertaintyMeasuring range <100 pC %<1Measuring range ≥100 pC %<0,5Temperature coefficient, typ.ppm/°C <50Linearity error, typ.%FSO <0,01Crosstalk between channels dB <–80Sensor impedanceΩ>1010Voltage output Nominal output rangeV ±10Output impedanceΩ10Max. common mode voltage between input and output ground V50Output noise (all ranges)1 Hz ... 100 kHz, typ.mV rms 0,0301 Hz ... 10 kHz, typ.mV rms 0,012Frequency range (–3 dB)Hz 0 ... 100 000Group delay (input to output, filters off)μs ≤14Zero errormV <±2DAC resolution (analog out)Bit16Data acquisition ADC resolutionBit 24Internal ADC sampling ratekSps 625Acquisition data rate per channel (adjustable)kSps100Note: For the data acquisition with ≥25 kSps an anti-aliasing filter is automatically set with a cut-off frequency of 0,3 ... 0,43 x selected output update rate.High-Pass filter Order1.Analog high-pass filter Time constant DC (Long)<45 000 pC s >10 000≥45 000 pC s>100 000Time constant Short <45 000 pCs 10≥45 000 pC s 110Tolerance (typ.)%20Digital High-Pass Filter Cutoff-frequency (–3 dB) selection in 0,1 Hz steps Hz ≥0,1 ... 10 000Tolerance (typ.)%<1Digital Low-Pass filter Filter type Bessel or ButterworthOrder2./4.Cutoff-frequency (–3 dB) selection in 0,1 Hz steps Hz ≥10Tolerance (typ.)%<1Page 3/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Technical data (continuation)Digital Notch filter Center frequency (–3 dB) selection in 0,1 Hz steps Hz ≥10Tolerance (typ.)%<1Q factor 0,9 ... 1 000Virtual channels Number of channelsType 5167A402Type 5167A806Ethernet interface Data rateMBit100Remote control(Digital input and 24 V supply)Remote measure and trigger with 10 k Ω pullup to +5 V Connector type D-Sub 9fInput levelHigh (Reset, Stop trigger)V>3,5orInput openLow (Measure, Start trigger)V <1Max. input voltage V ±30Supply (output)V DC +24/±10 %Output current (short circuit proof)mA ≤200OperationAll settings are configured in a standard web-browser through the graphical user interface. Simply connect to the Kistler LabAmp Type 5167A... by its network name and start working.Power supply requirements Supply voltage range VDC 18 (30)Power consumption W <15Socket for barrel jack plug (IEC 60130-10 Type A) mm5,5x2,5x9,5Power supply requirements– galvanic isolation – PE and GND not connectedGeneral dataOperating temperature range °C 0 ... 60Storage temperature range °C –10 (70)Rel. humidity, not condensing %≤90Degree of protection (EN 60529)IP20Outer dimensions incl. feet and connectors (WxHxD)Type 5167A40mm ≈218x50x223Type 5167A80mm≈218x93x223WeightType 5167A40kg 1,2Type 5167A80kg1,8Fig. 1: Web user interface Type 5167Ax0A simple data acquisition is also implemented, offering a data download controlled by a start/stop button. In addition, an API is available to perform automated measuring tasks PC-based.Page 4/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Block diagramFig. 2: Block diagram of the Kistler LabAmp Type 5167Ax0Sensor 1Sensor 2Sensor 3Sensor 4Sensor 5 (8)ControlPage 5/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting DimensionsFig. 3: Dimensions of Kistler LabAmp Type 5167A40Page 6/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Fig. 4:Dimensions of Kistler LabAmp Type 5167A80Page 7/75167A x 0_003-277e -10.18© 2017 ... 2018 Kistler Group, Eulachstrasse 22, 8408 Winterthur, Switzerland Tel.+41522241111,****************,. Kistler Group products are This information corresponds to the current state of knowledge. Kistler reserves the right to make technical changes. Liability for consequential damage resulting Included accessories Type/Mat. No.• Calibration sheet –• Quick-start guide –• Power supply 24 V 5779A2 incl. country-specific plug • Ethernet cable, l = 2 m tbd Optional accessories Type/Mat. No.• 19" rack mounting tablet for 5748A1 Type 5167A40• Dummy panel for empty 5748A2 19" position (1 height unit)• 19" rack mounting tablet for 5748A3 Type 5167A80• Dummy panel for empty 5748A4 19" position (2 height units)• DynoWare software 2825A-03-2 Full license with HASP license key • Inductive proximity switch 2233B generates an external trigger signal tostart measurementOrdering keyLabVIEW is a registered trade mark of National Instruments Corporation.。
HP Z22n G2 21.5英寸显示器说明书

Datasheet HP Z22n G2 21.5-inch Display Color consistency and performance for the project perfectionist Be a productive powerhouse with thesleek HP Z22n G2 21.5-inch Display.This virtually seamless Full HD displayis factory-tested for reliability andlongevity with integrated colorcalibration, uninterrupted multi-screen tiling, and expansive deviceconnections.Streamline productivity with screens for every projectMulti-task without disruptions across multiple displays with a 3-sided micro-edge bezel on each screen.Get stunning visuals from the 1920 x 1080 resolution , 16:9 aspect ratio, 21.5” diagonal IPS screen and over 2 million pixels.Out-of-this-world color right out of the boxConsistent, accurate color between displays and from project to project is easier than ever with factory color calibration from the very first time you power on.Quality from the startWe rigorously test each HP Z Display to help ensure it’s a reliable, long-life visual solution, and back it up with the HP Zero Bright Dot Guarantee , HP’s most stringent pixel policy, which replaces the screen if even one bright sub-pixel fails.Big ideas for small spacesMake the most of your available workspace by mounting powerful machines like the HP Z2 MiniWorkstation directly behind the display for a compact, efficient, single-footprint solution.FeaturingConnect easily with ports that include a two-port USB 3.0 hub and VGA, HDMI, and DisplayPort™connections tested for use with legacy, current, and future HP Workstations.Work comfortably with adjustable tilt, height, and swivel settings. Use pivot rotation to conveniently customize portrait or landscape views on multiple displays.Design the screen for how you work with HP Display Assistant software, which enables screen partitioning and helps deter theft by dimming a display that’s disconnected without approval.Reduce power consumption and help lower costs with an intelligent, energy-efficient, low-halogen display that is ENERGY STAR® certified, TCO qualified, and EPEAT® 2019 registered with mercury-free display backlights and arsenic-free display glass.Build a complete solution with optional HP accessories designed and tested to work with your display.Rest assured that your IT investment is supported by a three-year standard limited warranty. To extend your protection, select an optional HP Care service.112345HP Z22n G2 21.5-inch Display Specifications TableDisplay typeIPS w/LED backlight Panel Active Area18.74 x 10.54 in 47.6 x 26.77 cm Display size (diagonal)54.6 cm (21.5")Viewing angle178° horizontal; 178° vertical Brightness250 cd/m²Contrast ratio1000:1 static; 10000000:1 dynamic Response Ratio5 ms gray to gray Product colourBlack Aspect ratio16:9Native resolutionFHD (1920 x 1080 @ 60 Hz)Resolutions supported1920 x 1080; 1680 x 1050; 1600 x 900; 1440 x 900; 1280 x 1024; 1280 x 800; 1280 x 720; 1024 x 768; 800x 600; 720 x 480; 640 x 480Display featuresAnti-glare; In plane switching; Language selection; LED Backlights; On-screen controls; Pivot rotation; Plug and Play; User programmable; Low Haze User controlsBrightness; Contrast; Color Control; Input Control; Image Control; Power; Menu; Management; Language;Information; Exit; OK Input signal1 VGA; 1 HDMI 1.4; 1 DisplayPort™ 1.2with HDCP support on DisplayPort™ and HDMI Ports and Connectors3 USB 3.0 (one upstream, two downstream)EnvironmentalOperating temperature: 5 to 35°C; Operating humidity: 20 to 80% RH PowerInput voltage: 100 to 240 VAC Power consumption30 W (maximum), 17 W (typical), 0.5 W (standby)Dimensions19.22 x 1.7 x 11.55 in 48.83 x 4.33 x 29.33 cm (Without stand)Weight11.7 lb 5.3 kg (With stand)Ergonomic featuresTilt: -5 to +22°; Swivel: ±45°; Pivot rotation: 90°; Height: 150 mm Physical security featuresSecurity lock-ready (lock is sold separately)Energy efficiency complianceENERGY STAR® certified; EPEAT® 2019 registered Certification and complianceAustralian-New Zealand MEPS; BSMI; CB; CCC; CE; CEL; cTUVus; CU; ErP; E-standby; FCC; ICES; ISC; ISO 9241-307; KC; Mexico CoC; Microsoft WHQL Certification (Windows 10); MSIP; PSB; RCM; SEPA; SmartWay Transport Partnership - NA only; TUV-S; VCCI; Vietnam MEPS; WEEE Environmental specificationsArsenic-free display glass; Mercury-free display backlights; Low halogen What's in the box Monitor; AC power cord; USB cable (Type A male to Type B male); DisplayPort™ 1.2 cable; CD (includes UserGuide, warranty, drivers); HP Display Assistant111,31Accessories and services (not included)HP B300 PC Mounting BracketCustomize an altogether better solution with the HP B300 PC Mounting Bracket, which lets you attach your HP Workstation, HP Desktop Mini, HP Chromebox or select HP Thin Client directly behind select 2017 and 2018 HP EliteDisplays and HP Z Displays.Product number: 2DW53AAHP S100 Speaker Bar Add rich stereo audio to select 2017 and 2018 HP ProDisplays, HP EliteDisplays, and HP Z Displays without crowding your desk with the HP S100 Speaker Bar, which fits neatly underneath the display head and connects through USB.Product number: 2LC49AAHP Single Monitor ArmThe HP Single Monitor Arm is the perfect desk accessory for your work life. Sleek and streamlined, the HP Single Monitor Arm is designed to complement the way you work. Product number: BT861AAHP UHD USB Graphics AdapterBoost your productivity by extending or mirroring your desktop to a UHD display with the HP UHD USB Graphics Adapter.Product number: N2U81AA11Messaging FootnotesAdditional displays required and sold separately.All performance specifications represent the typical specifications provided by HP's component manufacturers; actual performance may vary either higher or lower.The HP Pixel Policy allows no bright sub-pixel defects for this display. For complete details, see /us-en/document/c00288895.HP Care Packs sold separately. Service levels and response times for HP Care Packs may vary depending on your geographic location. Service starts on date of hardware purchase. Restrictions and limitations apply. For details, visit/go/cpc. HP Services are governed by the applicable HP terms and conditions of service provided or indicated to Customer at the time of purchase. Customer may have additional statutory rights according to applicable local laws,and such rights are not in any way affected by the HP terms and conditions of service or the HP Limited Warranty provided with your HP Product.Workstation sold separately. Requires HP B500 PC Mounting Bracket for Monitors, sold separately.Each sold separately.External power supplies, power cords, cables and peripherals are not Low Halogen. Service parts obtained after purchase may not be Low Halogen. Based on US EPEAT® registration according to IEEE 1680.1-2018 EPEAT®. Status varies by country. Visit for more information.Technical Specifications FootnotesAll specifications represent the typical specifications provided by HP's component manufacturers, actual performance may vary either higher or lower.External power supplies, power cords, cables and peripherals are not Low Halogen. Service parts obtained after purchase may not be Low Halogen. Product default is 14 ms response time and can be adjusted to as low as 5.4 ms in the display menu. See user guide for more information.Sign up for updates Sign up for updates /go/getupdated© Copyright 2017 HP Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in theexpress warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorialerrors or omissions contained herein. EPEAT® registered where applicable. EPEAT registration varies by country. See for registration status by country. Search keyword generator onHP’s 3rd party option store for solar generator accessories at /go/optionsENERGY STAR® and the ENERGY STAR® mark are registered trademarks of the U.S. Environmental Protection Agency. DisplayPort™ and the DisplayPort™ logo are trademarks owned by the VideoElectronics Standards Association (VESA®) in the United States and other countries.May 201912345678123。
绿色MAX DRC 0-10V智能包说明书

Leviton Manufacturing Co., Inc. Lighting & Controls10385 SW Avery Street, Tualatin, OR 97062 tel 800-736-6682 tech line (6:00AM-4:00PM PT Mon-Fri) 800-959-6004 ©2023 Leviton Manufacturing Co., Inc. All rights reserved. Subject to change without notice.DescriptionThe GreenMAX ® DRC 0-10V Smart Pack enables switching and 0-10V dimming control of a single zone of fixtures, allowing for a distributed control solution. Used to control multiple fixtures in a zone or for plug load control solutions, the DRC uses distributed relays, which eliminates the need to run wires back to a cabinet. This distributed system architecture saves on installation and equipment costs. DRC relays can be used as a normal or emergency relay; a remote relay with the GreenMAX DRC system; or as a single room control relay with the Sapphire™ Touch Screen.System DescriptionThe GreenMAX DRC Room Control System offers a fully distributed room control system, with each room operating independently of others—no dependence on network processors or centralized controllers. This revolutionary system is fully configurable via the GreenMAX DRC app for smart devices, and can be used to comply with IECC, ASHRAE 90.1, and 2022 Title 24, Part 6 occupancy/vacancy sensing, multi-level lighting, daylight harvesting, partial-ON, partial-OFF, scheduling, exterior lighting, demand response and receptacle control requirements.GreenMAX DRC AppWirelessly commission, configure, control, monitor and provision the GreenMAX DRC system using the GreenMAX DRC App designed for any WiFi-enabled Android or iOS smart device.Applications• Single channel LumaCAN 0-10V relay • Distributed controls• GreenMAX DRC remote relay • GreenMAX remote relay• Direct load control from Sapphire™ Use With These Leviton Systems • GreenMAX DRC• GreenMAX relay panels •Sapphire TouchscreenGreenMAX ® DRC 0-10V Smart PackFeatures• Single channel device—(1) 0-10V output plus (1) relay • Plug load controls • UL924 Emergency• Utilizes Leviton High Inrush Stability (H.I.S.) circuitry for increased reliability• Connects via the LumaCAN network using RJ45 connectors and CAT6 wiring• 0-10V control can be Class 1 or Class 2 wiring• Used for both switching only loads and dimming loads controllable with a 0-10V control signal• All relay models are latching to reduce parasitic energy waste over NO/NC relays• UL2043 Plenum rated—for use in Chicago Plenum applications—see technical article Install Notes• Installs as 4” square electrical box cover or via 1/2” nipple • When Class 2 in conduit is required, use 4” square extension ring and blank cover on low voltage side• May be field-painted to match surroundings (requires 4Sblank cover to protect Class 2 side)Wiring Diagram*Can be used to monitor normal power on emergency circuits, see solution sheet for details.**Depending on manufacture date, pink wire may be gray.LumaCANFor 120-277VAC applications only:Dimensions DiagramLeviton Manufacturing Co., Inc. Lighting & Controls10385 SW Avery Street, Tualatin, OR 97062 tel 800-736-6682 tech line (6:00AM-4:00PM PT Mon-Fri) 800-959-6004Visit our Website at: /greenmaxdrc©2023 Leviton Manufacturing Co., Inc. All rights reserved. Subject to change without notice.G-9664E/G23-mmREV JUL 2023。
USAMADE INPCI-GPIB高性能IEEE-488.2接口和驱动软件说明书

for PCI Bus ComputersߜIEEE 488.2 StandardInterfaceߜComplete Talker/Listener/Controllerߜ1024 Word FIFO BufferߜIndustry Standard 32-BitPCI BusߜData Transfer Rates Over1Mega Bytes/SecߜIncludes GPIB-LibraryComplete SoftwareSupport DescriptionThe PCI-GPIB IEEE-488 interfaceconverts any PCI bus personalcomputer into an instrumentationcontrol and data acquisition system.Connect up to 14 instruments usingstandard IEEE-488 cables such asthe C-488-2M, 2 meter IEEE-488interface cable. The PCI-GPIB isdesigned around an industry standardGPIB chip.Greater than 1MB/sTransfer RatesThe PCI-GPIB transfers data overthe GPIB at rates in excess of1 million bytes per second using themaximum IEEE-488 specificationcable length (2 meters times the #of devices). A 1024-Word FIFObuffer and the advanced REP-INSWISR transfer method provide all thehorsepower required to achieve thehighest possible rates.Plug & Play - No Switchesor JumpersThe PCI-GPIB is a true plug andplay. Plug in the PCI-GPIB and runthe installation software then startcommunicating. The Plug and Playspecification is a standard for systemconfiguration of boards and softwarethat automatically configures theaddress and interrupt level of thePCI-GPIB. Note, the PCI-GPIB doesnot use DMA in favor of the superi-or REP-INSW high speed transfer.Windows NT, Windows 98,Windows 95, Windows 3.1and DOS CompatibilityThe PCI-GPIB hardware supportsall of the operating systems andlanguages regardless of the operatingsystems support for plug and play.The installation software will manageresources for you on non-plug andplay systems.ProgramModel PCI-GPIB$399D4-5D4-6D4SpecificationsThe PCI-GPIB is compatible with IEEE-488.1 and IEEE-488.2 specifications.Transfer Rate: >1Mbyte/secPower: 5 VDC @ 375 mA typical Dimensions: 5.26 X 3.8´´I/O Connector:IEEE-488 Standard 24 pinOperating Temp. & Humidity:0 to 60°C @ 10 to 90%Storage Temp. & Humidity:-40 to 100°C @ 5 to 90%GPIB LibraryThe GPIB Library includes complete Windows Language programming support. You receive installation software and complete DOS,Windows 3.x, Windows 95, Windows 98 and Windows NT language drivers.The GPIB Library for Windows is a Dynamic Link Library (DLL). It can be used with most Windowsprogramming languages including Microsoft Visual C++ and C, Visual Basic, Borland C/C++, Watcom C and Pascal.The GPIB Library is modeled after the National Instruments Library. As of the time of this writing, the Library is syntactically and functionally identical with the NI-488.2 library. This means that a program written for the NI-488.2library may be recompiled for the GPIB Library and will compile, run and function without error in exactly the manner it did when compiled and run with the National Instruments software.IEEE-488.2 (GPIB)CompatibilityThe PCI-GPIB adheres toANSI/IEEE Standard 488-1978.Often referred to as the IEEE-488.2bus or HPIB (Hewlett-Packard Interface Bus), the GPIB (General Purpose Interface Bus) is a standard for instrumentation communication and control forinstruments from manufacturers the world over. The GPIB provides handshaking and interfacecommunications over an 8 bit data bus employing 5 control and 3handshake signals.IEEE-488 ConnectionConnecting GPIB devices together is straightforward. Since the signal lines are connected in parallel, a direct pin-to-pin wiring cable is used. GPIB, or IEEE-488, uses a standardized connector, whichadditionally simplifies interconnecting different instruments.The optional C-488-2M cable is a standard 2 meter IEEE-488 cable. It can be used to connect any of OMEGA’s IEEE-488 devices to other IEEE-488 instruments. Since each connector has two parallel GPIB connections, a user caneasily attach other GPIB devices to either end for expansion.Ordering Example: PCI-GPIB card, C-488-2M cable and OMEGACARE SM 1-year extended warranty for PCI-GPIB (adds 1 year to standard 3-year warranty) $399 + 59 + 30 = $488CANADA www.omega.ca Laval(Quebec) 1-800-TC-OMEGA UNITED KINGDOM www. Manchester, England0800-488-488GERMANY www.omega.deDeckenpfronn, Germany************FRANCE www.omega.frGuyancourt, France088-466-342BENELUX www.omega.nl Amstelveen, NL 0800-099-33-44UNITED STATES 1-800-TC-OMEGA Stamford, CT.CZECH REPUBLIC www.omegaeng.cz Karviná, Czech Republic596-311-899TemperatureCalibrators, Connectors, General Test and MeasurementInstruments, Glass Bulb Thermometers, Handheld Instruments for Temperature Measurement, Ice Point References,Indicating Labels, Crayons, Cements and Lacquers, Infrared Temperature Measurement Instruments, Recorders Relative Humidity Measurement Instruments, RTD Probes, Elements and Assemblies, Temperature & Process Meters, Timers and Counters, Temperature and Process Controllers and Power Switching Devices, Thermistor Elements, Probes andAssemblies,Thermocouples Thermowells and Head and Well Assemblies, Transmitters, WirePressure, Strain and ForceDisplacement Transducers, Dynamic Measurement Force Sensors, Instrumentation for Pressure and Strain Measurements, Load Cells, Pressure Gauges, PressureReference Section, Pressure Switches, Pressure Transducers, Proximity Transducers, Regulators,Strain Gages, Torque Transducers, ValvespH and ConductivityConductivity Instrumentation, Dissolved OxygenInstrumentation, Environmental Instrumentation, pH Electrodes and Instruments, Water and Soil Analysis InstrumentationHeatersBand Heaters, Cartridge Heaters, Circulation Heaters, Comfort Heaters, Controllers, Meters and SwitchingDevices, Flexible Heaters, General Test and Measurement Instruments, Heater Hook-up Wire, Heating Cable Systems, Immersion Heaters, Process Air and Duct, Heaters, Radiant Heaters, Strip Heaters, Tubular HeatersFlow and LevelAir Velocity Indicators, Doppler Flowmeters, LevelMeasurement, Magnetic Flowmeters, Mass Flowmeters,Pitot Tubes, Pumps, Rotameters, Turbine and Paddle Wheel Flowmeters, Ultrasonic Flowmeters, Valves, Variable Area Flowmeters, Vortex Shedding FlowmetersData AcquisitionAuto-Dialers and Alarm Monitoring Systems, Communication Products and Converters, Data Acquisition and Analysis Software, Data LoggersPlug-in Cards, Signal Conditioners, USB, RS232, RS485 and Parallel Port Data Acquisition Systems, Wireless Transmitters and Receivers。
RAL_国标色彩对照表

RAL色彩对照表数字"1"开头的1000 Green beige 米绿色1001 Beige 米色,淡黄或灰黄1002 Sand yellow 沙黄色1003 Signal yellow 信号黄1004 Goldenyellow 金黄色1005 Honey yellow 蜜黄色1006 Maize yellow 玉米黄1007 Daffodil yellow 灰黄色1011 Brown beige 米褐色1012 Lemon yellow 柠檬黄1013 Oyster white 近于白色的浅灰1014 Ivory 象牙色1015 Light ivory 亮象牙色1016 Sulfur yellow 硫磺色1017 Saffron yellow 深黄色1018 Zinc yellow 绿黄色1019 Grey beige 米灰色1020 Olive yellow 橄榄黄1021 Rape yellow 油菜黄1023 Traffic yellow 交通黄1024 Ochre yellow 赭黄色1026 Luminous yellow 亮黄色1027 Curry 咖喱色1028 Melon yellow 浅橙黄1032 Broom yellow 金雀花黄1033 Dahlia yellow 大丽花黄1034 Pastel yellow 粉黄色1035 Pearl beige 米珍珠色1036 Pearl gold 金黄珍珠1037 Sun yellow 日光黄数字“2”开头的2000 Yellow orange 黄橙色2001 Red orange 橘红2002 Vermilion 朱红2003 Paster orange 淡橙2004 Pure orange 纯橙2005 Luminous orange 亮橙2007 Luminous bright orange 亮浅橙2008 Bright red orange 浅红橙2009 Traffic orange 交通橙2011 Deep orange 深橙色数字“4”开头的4001 Red lilac 丁香红4002 Red violet 紫红色4003 Heather violet 石南紫4004 Claret violet 酒红紫4005 Blue lilac 丁香蓝4006 Traffic purple 交通紫4007 Purple violet 紫红蓝色4008 Signal violet 信号紫罗兰4009 Pastel violet 崧蓝紫色4010 Telemagenta 电视品红色4011 Pearl violet 珍珠紫4012 Peal blackberry 珍珠黑数字“5”开头的5000 Violet blue 紫蓝色5001 Green blue 蓝绿色5002 Ultramarine blue 群青蓝5003 Sapphire blue 蓝宝石蓝5004 Black blue 蓝黑色5005 Signal blue 信号蓝5007 Brillant blue 亮蓝色5008 Grey blue 灰蓝色5009 Azure blue 天青蓝5010 Gentian blue 龙胆蓝色5011 Steel blue 钢蓝色5012 Light blue 淡蓝色5013 Cobalt blue 钴蓝色5014 Pigeon blue 鸽蓝色5015 Sky blue 天蓝色5017 Traffic blue 交通蓝5018 Turquoise blue 绿松石蓝5019 Capri blue 卡布里蓝色5020 Ocean blue 海蓝色5021 Water blue 不来梅蓝色5022 Night blue 夜蓝色5023 Distant blue 冷蓝色5024 Pastel blue 崧蓝蓝色5025 Pearl gentian blue 珍珠龙胆蓝5026 Pearl night blue 珍珠夜蓝数字“6”开头的6002 Leaf green 叶绿色数字“7”开头的7000 Squirrel grey 松鼠灰7001 Silver grey 银灰色7002 Olive grey 橄榄灰绿色7003 Moss grey 苔藓绿7004 Signal grey 信号灰7005 Mouse grey 鼠灰色7006 Beige grey 米灰色7008 Khaki grey 土黄灰色7009 Green grey 绿灰色7010 Tarpaulin gey 油布灰7011 Iron grey 铁灰色7012 Basalt grey 玄武石灰7013 Brown grey 褐灰色7015 Slate grey 浅橄榄灰7016 Anthracite grey 煤灰7021 Black grey 黑灰7022 Umbra grey 暗灰7023 Concrete grey 混凝土灰7032Pebble grey 卵石灰7033 Cement grey 水泥灰7034 Yellow grey 黄灰色7035 Light grey 浅灰色7036 Platinum grey 铂灰色7037 Dusty grey 土灰色7038 Agate grey 玛瑙灰7039 Quartz grey 石英灰7040 Window grey 窗灰色7042 Traffic grey A 交通灰A7043 Traffic grey B 交通灰B7044 Silk grey 深铭灰色7045 Telegrey 1 电视灰17046 Telegrey 2 电视灰27047 Telegrey 4 电视灰47048 Pearl mouse grey 珍珠鼠灰7024 Graphite grey 石墨灰7026 Granite grey 花岗灰7030 Stone grey 石灰色7031 Blue grey 蓝灰色数字“8”开头的8000 Green brown 绿褐色8001 Ochre brown 赭石棕色2012 Salmon orange 鲑鱼橙2013 Pearl orange 珍珠橙数字“3”开头的3000 Flame red 火焰红3001 Signal red 信号红3002 Carmine red 胭脂红3003 Ruby red 宝石红3004 Purple red 紫红色3012 Beige red 米红色3013 Tomato red 番茄红3014 Antique pink 古粉红色3015 Light pink 淡粉红色3016 Coral red 珊瑚红色3017 Rose 玫瑰色3018 Strawberry red 草莓红3020 Traffic red 交通红3022 Salmon pink 鲑鱼粉红色3024 Luminous red 亮红色3026 Luminous bright red 淡亮红色3027 Raspbery red 悬钩子红色3031 Orient red 戈亚红色3005 Wine red 葡萄酒红3007 Black red 黑红色3009 Oxide red 氧化红3011 Brown red 红玄武土色3032 Pearl ruby red 红宝石珍珠红3033 Pearl pink 珍珠红色6003 Olive green 橄榄绿6004 Blue green 蓝绿色6005 Moss green 苔藓绿6006 Grey olrve 橄榄灰绿6000 Patina green 铜锈绿色6001 Emerald greet 翡翠绿色6032Signal greet 信号绿6033 Mint turquoise 薄荷绿蓝色6034 Pastel turquoies 崧蓝绿松石色6035 Pearl green 珍珠绿6036 Pearl opal green 不透明蓝白绿6007 Bottle green 瓶绿6008 Brown green 褐绿6009 Fir greet 冷杉绿6010 Grass greet 草绿色6011 Reseda green 淡橄榄绿6012 Black green 墨绿色6013 Reed green 芦苇绿6014 Yellow olive 橄榄黄6015 Black olive 黑齐墩果色6016 Turquoise green 绿松石绿色6017 May green 五月红6018 Yellow green 黄绿色6019 Pastel green 崧蓝绿色6020 Chrome green 铭绿色6021 Pale green 浅绿色6022 Olive drab 橄榄土褐色6024 Traffic green 交通绿6025 Fern green 蕨绿色6026 Opal green 蛋白石绿色6027 Light green 浅绿色6028 Pine green 松绿色6029 Mint green 薄荷绿8002 Signal brown 信号褐8003 Clay brown 土棕褐色8004 Coper brown 铜棕色8007 Fawn brown 鹿褐色8008 Olive brown 橄榄棕色8011 Nut brown 深棕色8012 Red brown 红褐色8014 Sepia brown 乌贼棕色8015 Chestnut brown 粟棕色8016Mahogany brown 桃花心木褐8017 Chocolate brown 巧克力棕色8019 Grey brown 灰褐色8022 Black brown 黑褐色8023 Orange brown 桔黄褐8024 Beige brown 哔叽棕色8025 Pale brown 浅褐色8028 Terra brown 浅灰褐色8029 Pearl copper 珍珠铜棕色数字“9”开头的9001 Cream 彩黄色9002 Grey white 灰白色9003 Signal white 信号白9004 Signal black 信号黑9005 Jet black 墨黑色9006 White aluminium 白铝灰色9007 Grey aluminium 灰铝色9010 Pure white 纯白色9011 Graphiack 石墨黑9016 Traffic white 交通白9017 Traffic black 交通黑9018 Papyrus white 草纸白9022 Pearl light grey 珍珠浅灰9023 Pearl dark grey 珍珠深灰国标色卡号>>GSB05-1426-2001(代替GSB G51001-94)>>共83种颜色国际色标卡配方比P01淡紫(钛白99.712% 、甲苯胺红0.204%、酞菁蓝0.084%)P02 紫(钛白98.619%、酞菁蓝0.731%、大红粉0.650%)PB01深(铁)蓝(酞菁蓝71.61%、铁蓝13.88%、钛白8.20%、甲苯胺红6.32%)PB02深(酞)蓝(酞菁蓝93.605%、钛白6.395%)PB03 中(铁)蓝(酞菁蓝60.65%、铁蓝19.02%、钛白20.33%)PB04 中(酞)蓝(酞菁蓝81.773%、钛白18.227%)PB05 海蓝(钛白73.17%、酞菁蓝25.00%、铁蓝1.730%、软碳黑0.10%)PB06 淡(酞)蓝(钛白75.345%、群青16.788%、铁蓝7.234%、柠檬黄0.632%)PB07 淡(铁)蓝(钛白93.38%、铁蓝6.33%、软碳黑0.29%)PB08 蓝灰(钛白78.321%、铁蓝15.431%、中铬黄3.799%、碳黑2.449%)PB09 天(酞)蓝(钛白87.949%、群青9.535%、酞菁蓝1.270%、柠檬黄1.246%)PB10 天(铁)蓝(钛白97.888%、铁蓝1.109%、柠檬黄0.662%、铁黄0.341%)PB11 孔雀蓝(钛白51.086%、酞菁蓝45.922%、柠檬黄2.922%)B01 深灰(钛白80.178%、碳黑12.666%、铁黄6.375%、铁蓝0.781%)B02 中灰(钛白87.523%、柠檬黄5.959% 、碳黑5.348%、铁红1.170%)B03 淡灰(钛白94.123%、铁黄3.165%、碳黑2.639%、铁蓝0.074%)B04 银灰(钛白93.748%、铁黄4.472%、碳黑1.640%、铁蓝0.140%)B05 海灰(钛白97.628%、柠檬黄1.697%、碳黑0.641%、铁蓝0.034%)B06 淡天(酞)蓝(钛白99.676%、铁黄0.232%、铁蓝0.057%、酞菁蓝0.035%)B07 蛋青(钛白98.573%、浅铬黄1.042%、铁蓝0.221%、铁红0.164%)B08 稚蓝(钛白97.561%、柠檬黄2.174%、酞菁蓝0.243%、甲苯胺红0.023%)B09 宝石蓝(钛白83.579%、柠檬黄12.996%、酞菁蓝3.224%、碳黑0.201%)B10 鲜蓝(钛白79.151%、柠檬黄11.810%、酞菁蓝9.039%)B11 淡海(铁)蓝(钛白79.269%、铁黄10.935%、酞菁蓝9.029%、甲苯胺红0.767%)B12 中海(铁)蓝(钛白60.714%、深铬黄19.507%、铁蓝12.151%、酞菁蓝7.628%)B13 深海(铁)蓝(铁蓝34.161%、钛白33.119%、铁黄30.874%、酞菁蓝1.846%)B14 景蓝(柠檬黄51.670%、钛白34.315%、酞菁蓝14.015%)B15 艳蓝(钛白53.236%、柠檬黄35.255%、酞菁蓝7.939%、浅铬黄3.570%)BG01 中绿灰(钛白92.306%、浅铬黄5.887%、碳黑1.671%、铁蓝0.316%)BG02 湖绿(钛白82.92%、柠檬黄16.30%、铁蓝0.39%、软碳黑0.39%)BG03 宝绿(钛白66.96%、柠檬黄31.39%、酞菁蓝1.58%、软碳黑0.07%)BG04 鲜绿(柠檬黄55.82%、钛白40.41%、酞菁蓝3.54%、铁蓝0.23%)BG05 淡湖绿(钛白95.527%、柠檬黄3.185%、中铬黄0.785%、铁蓝0.504%)G01 苹果绿(钛白79.95%、柠檬黄19.65%、酞菁蓝0.20%、软碳黑0.19%)G02 淡绿(柠檬黄98.121%、酞菁蓝1.879%)G03 艳绿(柠檬黄96.24%、酞菁蓝3.32%、艳佳丽黄0.44%)G04 中绿(酞菁绿57.55%、中铬黄37.59%、钛白6.50%、碳黑0.44%)G05 深绿(酞菁绿76.90%、中铬黄16.15%、钛白6.50%、碳黑0.44%)G06 橄榄绿(铁黄53.49%、酞菁绿33.74%、碳黑9.97%、钛白2.81%)G07 蛋壳绿(钛白97.724%、柠檬黄1.654%、铁红0.565%、酞菁蓝0.056%)G08 淡苹果绿(钛白93.131%、柠檬黄4.452%、铁黄2.199%、酞菁蓝0.219%)G09 深豆绿(钛白49.621%、铁黄32.463%、浅铬黄15.446%、酞菁蓝2.470%)G10 飞机灰(钛白97.361%、铁黄1.810% 、碳黑0.799%、铁蓝0.031%)GY01 豆绿(钛白76.45%、柠檬黄19.39%、中铬黄3.92%、酞菁蓝0.25%)GY02 纺绿(钛白54.85%、中铬黄42.18%、软碳黑2.02%、铁蓝0.95%)GY03 橄榄灰(钛白69.14%、中铬黄25.63%、软碳黑3.99%、柠檬黄1.24%)GY04 草绿(中铬黄87.71%、软碳黑8.69%、铁蓝2.25%、钛白1.35%)GY05 褐绿(中铬黄68.99%、钛白17.40%、软碳黑13.21%、大红粉0.40%)GY06 军车绿(中铬黄57.864%、铁红24.070%、钛白13.028%、铁蓝5.038%)GY07 豆蔻绿(钛白54.848%、柠檬黄42.427%、铁黄2.213%、酞菁蓝0.462%)GY08 果(酞)绿(钛白90.536%、柠檬黄8.545%、铁黄0.833%、酞菁蓝0.085%)GY09 冰灰(钛白98.984%、浅铬黄0.806%、碳黑0.161% 、中铬黄0.049%)GY10 机床灰(钛白78.632%、铁黄16.718%、碳黑4.458% 、酞菁蓝0.192%)GY11 玉灰(钛白91.065%、铁黄8.364%、碳黑0.390%、酞菁蓝0.180%)Y01 驼灰(钛白72.69%、中铬黄25.32%、软碳黑1.52%、大红粉0.47%)Y02 珍珠(钛白97.43%、中铬黄2.55% 、软碳黑0.02%)Y03 奶油(钛白86.59%、柠檬黄13.31% 、大红粉0.10%)Y04 象牙(钛白84.89%、中铬黄11.98%、柠檬黄3.12%)Y05 柠黄(浅铬黄83.639%、钛白16.351%、铁蓝0.005%)Y06 淡黄(浅铬黄86.108%、钛白13.888%、铁蓝0.004%)Y07 中黄(中铬黄97.25%、钛白2.75%)Y08 深黄(钛白51.53%、艳佳丽黄48.40%、大红粉0.07%)Y09 铁黄(铁黄77.93%、中铬黄14.87%、钛白7.19%、软碳黑0.01%)Y10 军黄(深铬黄71.218%、铁红18.397%、钛白7.010%、碳黑3.374%)Y11 乳白(钛白98.81%、浅铬黄0.586%、深铬黄0.378%、铁红0.226%)Y12 米黄(钛白95.200%、柠檬黄2.311%、深铬黄2.002%、铁红0.487%)Y13 浅黄灰(钛白91.849%、深铬黄3.805%、铁黄3.358%、碳黑0.987%)YR01 淡棕(铁黄71.20%、铁红28.51%、软碳黑0.29%)YR02 赫黄(铁黄62.38%、铁红32.61%、软碳黑4.23%、钛白0.78%)YR03 紫棕(铁红70.88%、软碳黑14.12%、铁黄12.39%、钛白2.61%)YR04 桔黄YR05 棕色(铁红74.87%、铁黄17.14%、软碳黑5.83%、钛白2.16%)YR06 棕黄(中铬黄94.969%、钛白2.555%、甲苯胺红2.202%、碳黑0.274%)YR07 深棕色(中铬黄52.850%、铁红44.536%、碳黑1.520%、钛白1.093%)R01 铁红(铁红97.27%、中铬黄2.73%)R02朱红(钼铬红87.074%、大红粉12.926%)R03 大红R04 紫红R05 桔红RP01 粉红(钛白99.570%、大红粉0.250%、甲苯胺紫红0.180%)RP02 淡粉红RP03 玫瑰红RP04 淡玫瑰红空白处表示该颜料很微量,或为单纯颜料。
国标及劳尔色卡对照表

国标及劳尔色卡对照表国标号 >>GSB05-1426-20__1(代替 GSB G51001-94) >>共 83 种颜色国际色标卡配方比 P01 淡紫(钛白 99.712% 、甲苯胺红0.204%、酞菁蓝 0.084%)P02 紫(钛白 98.619%、酞菁蓝 0.731%、大红粉 0.650%)PB01 深(铁)蓝(酞菁蓝 71.61%、铁蓝 13.88%、钛白8.20%、甲苯胺红 6.32%)PB02 深(酞)蓝(酞菁蓝 93.605%、钛白 6.395%)PB03 中(铁)蓝(酞菁蓝 60.65%、铁蓝 19.02%、钛白20.33%)PB04 中(酞)蓝(酞菁蓝 81.773%、钛白 18.227%)PB05 海蓝(钛白 73.17%、酞菁蓝 25.00%、铁蓝 1.730%、软碳黑 0.10%)PB06 淡(酞)蓝(钛白 75.345%、群青 16.788%、铁蓝7.234%、柠檬黄 0.632%)PB07 淡(铁)蓝(钛白 93.38%、铁蓝 6.33%、软碳黑0.29%)PB08 蓝灰(钛白 78.321%、铁蓝 15.431%、中铬黄3.799%、碳黑 2.449%)PB09 天(酞)蓝(钛白 87.949%、群青 9.535%、酞菁蓝1.270%、柠檬黄 1.246%)PB10 天(铁)蓝(钛白 97.888%、铁蓝 1.109%、柠檬黄0.662%、铁黄 0.341%)PB11 孔雀蓝(钛白 51.086%、酞菁蓝 45.922%、柠檬黄2.922%)B01 深灰(钛白 80.178%、碳黑 12.666%、铁黄 6.375%、铁蓝 0.781%)B02 中灰(钛白 87.523%、柠檬黄 5.959% 、碳黑 5.348%、铁红 1.170%)B03 淡灰(钛白 94.123%、铁黄 3.165%、碳黑 2.639%、铁蓝 0.074%)B04 银灰(钛白 93.748%、铁黄 4.472%、碳黑 1.640%、铁蓝 0.140%)B05 海灰(钛白 97.628%、柠檬黄 1.697%、碳黑 0.641%、铁蓝 0.034%)B06 淡天(酞)蓝(钛白 99.676%、铁黄 0.232%、铁蓝0.057%、酞菁蓝 0.035%)B07 蛋青(钛白 98.573%、浅铬黄 1.042%、铁蓝 0.221%、铁红 0.164%)B08 稚蓝(钛白 97.561%、柠檬黄 2.174%、酞菁蓝0.243%、甲苯胺红 0.023%)B09 宝石蓝(钛白 83.579%、柠檬黄 12.996%、酞菁蓝3.224%、碳黑 0.201%)B10 鲜蓝(钛白 79.151%、柠檬黄 11.810%、酞菁蓝9.039%)B11 淡海(铁)蓝(钛白 79.269%、铁黄 10.935%、酞菁蓝9.029%、甲苯胺红 0.767%)B12 中海(铁)蓝(钛白 60.714%、深铬黄 19.507%、铁蓝12.151%、酞菁蓝 7.628%)B13 深海(铁)蓝(铁蓝 34.161%、钛白 33.119%、铁黄30.874%、酞菁蓝 1.846%)B14 景蓝(柠檬黄 51.670%、钛白 34.315%、酞菁蓝14.015%)B15 艳蓝(钛白 53.236%、柠檬黄 35.255%、酞菁蓝7.939%、浅铬黄 3.570%)BG01 中绿灰(钛白 92.306%、浅铬黄 5.887%、碳黑1.671%、铁蓝 0.316%)BG02 湖绿(钛白 82.92%、柠檬黄 16.30%、铁蓝 0.39%、软碳黑 0.39%)BG03 宝绿(钛白 66.96%、柠檬黄 31.39%、酞菁蓝 1.58%、软碳黑 0.07%)BG04 鲜绿(柠檬黄 55.82%、钛白 40.41%、酞菁蓝 3.54%、铁蓝 0.23%)BG05 淡湖绿(钛白 95.527%、柠檬黄 3.185%、中铬黄0.785%、铁蓝 0.504%)G01 苹果绿(钛白 79.95%、柠檬黄 19.65%、酞菁蓝0.20%、软碳黑 0.19%)G02 淡绿(柠檬黄 98.121%、酞菁蓝 1.879%)G03 艳绿(柠檬黄 96.24%、酞菁蓝 3.32%、艳佳丽黄0.44%)G04 中绿(酞菁绿 57.55%、中铬黄 37.59%、钛白 6.50%、碳黑 0.44%)G05 深绿(酞菁绿 76.90%、中铬黄 16.15%、钛白 6.50%、碳黑 0.44%)G06 橄榄绿(铁黄 53.49%、酞菁绿 33.74%、碳黑 9.97%、钛白 2.81%)G07 蛋壳绿(钛白 97.724%、柠檬黄 1.654%、铁红0.565%、酞菁蓝 0.056%)G08 淡苹果绿(钛白 93.131%、柠檬黄 4.452%、铁黄2.199%、酞菁蓝 0.219%)G09 深豆绿(钛白 49.621%、铁黄 32.463%、浅铬黄15.446%、酞菁蓝 2.470%)G10 飞机灰(钛白 97.361%、铁黄 1.810% 、碳黑 0.799%、铁蓝 0.031%)GY01 豆绿(钛白 76.45%、柠檬黄 19.39%、中铬黄 3.92%、酞菁蓝 0.25%)铁蓝 0.95%)GY03 橄榄灰(钛白 69.14%、中铬黄 25.63%、软碳黑3.99%、柠檬黄 1.24%)GY04 草绿(中铬黄 87.71%、软碳黑 8.69%、铁蓝 2.25%、钛白 1.35%)GY05 褐绿(中铬黄 68.99%、钛白 17.40%、软碳黑13.21%、大红粉 0.40%)GY06 军车绿(中铬黄 57.864%、铁红 24.070%、钛白13.028%、铁蓝 5.038%)GY07 豆蔻绿(钛白 54.848%、柠檬黄 42.427%、铁黄2.213%、酞菁蓝 0.462%)GY08 果(酞)绿(钛白 90.536%、柠檬黄 8.545%、铁黄0.833%、酞菁蓝 0.085%)GY09 冰灰(钛白 98.984%、浅铬黄 0.806%、碳黑0.161% 、中铬黄 0.049%)GY10 机床灰(钛白 78.632%、铁黄 16.718%、碳黑4.458% 、酞菁蓝 0.192%)GY11 玉灰(钛白 91.065%、铁黄 8.364%、碳黑 0.390%、酞菁蓝 0.180%)Y01 驼灰(钛白 72.69%、中铬黄 25.32%、软碳黑 1.52%、大红粉 0.47%)Y03 奶油(钛白 86.59%、柠檬黄 13.31% 、大红粉 0.10%)Y04 象牙(钛白 84.89%、中铬黄 11.98%、柠檬黄 3.12%)Y05 柠黄(浅铬黄 83.639%、钛白 16.351%、铁蓝 0.005%)Y06 淡黄(浅铬黄 86.108%、钛白 13.888%、铁蓝 0.004%)Y07 中黄(中铬黄 97.25%、钛白 2.75%)Y08 深黄(钛白 51.53%、艳佳丽黄 48.40%、大红粉0.07%)Y09 铁黄(铁黄 77.93%、中铬黄 14.87%、钛白 7.19%、软碳黑 0.01%)Y10 军黄(深铬黄 71.218%、铁红 18.397%、钛白 7.010%、碳黑 3.374%)Y11 乳白(钛白 98.81%、浅铬黄 0.586%、深铬黄 0.378%、铁红 0.226%)Y12 米黄(钛白 95.20__%、柠檬黄 2.311%、深铬黄2.002%、铁红 0.487%)Y13 浅黄灰(钛白 91.849%、深铬黄 3.805%、铁黄3.358%、碳黑 0.987%)YR01 淡棕(铁黄 71.20%、铁红 28.51%、软碳黑 0.29%)YR02 赫黄(铁黄 62.38%、铁红 32.61%、软碳黑 4.23%、钛白 0.78%)YR03 紫棕(铁红 70.88%、软碳黑 14.12%、铁黄 12.39%、钛白 2.61%)YR04 桔黄YR05 棕色(铁红 74.87%、铁黄 17.14%、软碳黑 5.83%、钛白 2.16%)YR06 棕黄(中铬黄 94.969%、钛白 2.555%、甲苯胺红2.202%、碳黑 0.274%)YR07 深棕色(中铬黄 52.850%、铁红 44.536%、碳黑1.520%、钛白 1.093%)R01 铁红(铁红 97.27%、中铬黄 2.73%)R02 朱红(钼铬红 87.074%、大红粉 12.926%)R03 大红 R04 紫红 R05 桔红 RP01 粉红(钛白 99.570%、大红粉 0.250%、甲苯胺紫红 0.180%)RP02 淡粉红 RP03 玫瑰红RP04 淡玫瑰红空白处表示该颜料很微量,或为单纯颜料。
Designandsynthesisofanexceptionallystableand

Supporting Information (Manuscript No. Y05730).This information is also available directly from the).Design and synthesis of an exceptionally stable andhighly porous metal-organic framework†Hailian Li, Mohamed Eddaoudi†, M. O'Keeffe & 0. M. Yaghi*’Materials Design and Discovery GroupDepartment of Chemistry and BiochemistryArizona State UniversityTempe, Arizona 85287-1604, USA†Current Address for : Department of ChemistryUniversity of Michigan930 North UniversityAnn Arbor, Michigan 48109-1055, USAIncluded Crystallography data:Zn4O(BDC)3·(DMF)8(C6H5CI)Zn4O(BDC)3 desolvatedZn4O(BDC)3 desolvated and heated to 300°C in airData were collected using a Siemens SMART CCD (charge coupled device) based diffractometer equipped with an LT-2 low-temperature apparatus operating at 213 K. A suitable crystal was chosen and mounted on a glass fiber using grease. Data were measured using omega scans of ' per frame for 10 seconds, such that a hemisphere was collected. A total of 1271 frames were collected with a final resolution of A. The first 50 frames were recollected at the end of data collection to monitor for decay. Cell parameters were retrieved using SMART' software and refined usinc, SAINT on all observed reflections. Data reduction was performed using the SAINT software- which corrects for Lp and decay. Absorption corrections were applied using SADABS6 supplied by George Sheldrick. The structures are solved by the direct method using the2SHELXS-97' program and refined by least squares method on F , SHELXL -97,' incorporated in SHELXTL-PC V . -The structure was solved in the space group Fm-3m (# 225 ) by analysis of systematic absences. All non-hydrogen atoms are refined anisotropically. Hydrogens were found by difference fourier methods and refined. The crystal used for the diffraction study showed no decomposition during data collection. Serveral other space groups were tried with no success as was the search for merohedral twin which may have contributed to the high R(int) value. The authors thank Seimens for examination of the data set.ReferencesI .SMART V Software for the CCD Detector System, Siemens Analytical Instruments Division, Madison, WI (I 995).V Software for the CCD Detector System, Siemens Analytical Instruments Division, Madison, WI (1995)., G. M. SHELXS-90, Program for the Solution of Crystal Structure, University of G6ttingen, Germany, 1986., G. M. SHELXL-97, Program for the Refinement of Crystal Structure, University of G6ttingen, Germany, 1993.(PC-Version), Program library for Structure Solution and Molecular Graphics, Siemens Analytical Instruments Division, Madison,WI (1995).. Program for absorption corrections using Siemens CCD based on the method of Bob Blessing. Acta Cryst. A51 (1995) 33-38.Table 1. Crystal data and structure refinementIdentification code oy01Empirical formulaFormula weightTemperature 213(2) KWavelength ACrystal system CubicSpace group Fm-3mUnit cell dimensions a = (3) A alpha = 90 deg.b = (3) A beta = 90 deg.c = (3) A gamma = 90 deg.Volume, Z (3) A^3, 30Density (calculated) mg/m^3Absorption coefficient mm^-1F(000) 3040Crystal size x x mmTheta range for data collection to deg.Limiting indices -27<=h<=27, -27<=k<=25, -23<=l<=27Reflections collected 16272Independent reflections 616 [R(int) = ]Absorption correction Semi-empirical from psi-scansMax. and min. transmission andRefinement method Full-matrix least-squares on F^2Data / restraints / parameters 616 / 0 / 26Goodness-of-fit on F^2Final R indices [I>2sigma(I)] R1 = , wR2 =R indices (all data) R1 = , wR2 = Extinction coefficient (2)Largest diff. peak and hole and ^-3Table 2. Atomic coordinates ( x 10^4) and equivalent isotropic displacement parameters (A^2 x 10^3) for 1. U(eq) is definedas one third of the trace of the orthogonalized Uij tensor.________________________________________________________________ x y z U(eq)________________________________________________________________ Zn(1) 2935(1) 2065(1) 2065(1) 51(1) O(1) 2500 2500 2500 42(5)O(2) 2818(3) 2182(3) 1339(4) 96(3) C(1) 2500 2500 1105(7) 87(6) C(2) 2831(4) 2169(4) 263(6) 123(8) C(3) 2500 2500 538(6) 98(8) ________________________________________________________________Table 3. Bond lengths [A] and angles [deg] for 1._____________________________________________________________Zn(1)-O(2) (9)Zn(1)-O(2)#1 (9)Zn(1)-O(2)#2 (9)Zn(1)-O(1) (2)Zn(1)-Zn(1)#3 (4)Zn(1)-Zn(1)#4 (4)Zn(1)-Zn(1)#5 (4)O(1)-Zn(1)#3 (2)O(1)-Zn(1)#4 (2)O(1)-Zn(1)#5 (2)O(2)-C(1) (12)C(1)-O(2)#5 (12)C(1)-C(3) (2)C(2)-C(2)#6 (3)C(2)-C(3) (2)C(3)-C(2)#5 (2)O(2)-Zn(1)-O(2)#1 (4)O(2)-Zn(1)-O(2)#2 (4)O(2)#1-Zn(1)-O(2)#2 (4)O(2)-Zn(1)-O(1) (3)O(2)#1-Zn(1)-O(1) (3)O(2)#2-Zn(1)-O(1) (3)O(2)-Zn(1)-Zn(1)#3 (3)O(2)#1-Zn(1)-Zn(1)#3 (3)O(2)#2-Zn(1)-Zn(1)#3 (3)O(1)-Zn(1)-Zn(1)#3O(2)-Zn(1)-Zn(1)#4 (3)O(2)#1-Zn(1)-Zn(1)#4 (3)O(2)#2-Zn(1)-Zn(1)#4 (3)O(1)-Zn(1)-Zn(1)#4Zn(1)#3-Zn(1)-Zn(1)#4O(2)-Zn(1)-Zn(1)#5 (3)O(2)#1-Zn(1)-Zn(1)#5 (3)O(2)#2-Zn(1)-Zn(1)#5 (3)O(1)-Zn(1)-Zn(1)#5Zn(1)#3-Zn(1)-Zn(1)#5Zn(1)#4-Zn(1)-Zn(1)#5Zn(1)#3-O(1)-Zn(1)#4Zn(1)#3-O(1)-Zn(1)#5Zn(1)#4-O(1)-Zn(1)#5Zn(1)#3-O(1)-Zn(1)Zn(1)#4-O(1)-Zn(1)Zn(1)#5-O(1)-Zn(1)C(1)-O(2)-Zn(1) (11)O(2)-C(1)-O(2)#5 125(2)O(2)-C(1)-C(3) (9)O(2)#5-C(1)-C(3) (9)C(2)#6-C(2)-C(3) (8)C(2)-C(3)-C(2)#5 119(2)C(2)-C(3)-C(1) (8)C(2)#5-C(3)-C(1) (8)_____________________________________________________________Symmetry transformations used to generate equivalent atoms: #1 -y+1/2,z,-x+1/2 #2 -z+1/2,-x+1/2,y#3 x,-y+1/2,-z+1/2 #4 -x+1/2,y,-z+1/2 #5 -x+1/2,-y+1/2,z #6 x,y,-zTable 4. Anisotropic displacement parameters (A^2 x 10^3) for 1. The anisotropic displacement factor exponent takes the form:-2 pi^2 [ h^2 a*^2 U11 + ... + 2 h k a* b* U12 ]_____________________________________________________________________ __U11 U22 U33 U23 U13 U12_____________________________________________________________________ __ Zn(1) 51(1) 51(1) 51(1) -1(1) 1(1) 1(1)O(1) 42(5) 42(5) 42(5) 0 0 0O(2) 117(5) 117(5) 54(6) -5(4) 5(4) 29(6)C(1) 99(9) 99(9) 64(13) 0 0 2(14)C(2) 160(12) 160(12) 49(8) 4(5) -4(5) 93(14)C(3) 130(12) 130(12) 36(9) 0 0 40(15)_____________________________________________________________________ __Table 5. Hydrogen coordinates ( x 10^4) and isotropicdisplacement parameters (A^2 x 10^3) for 1.________________________________________________________________ x y z U(eq)________________________________________________________________ H(2A) 3059 1941 452 148________________________________________________________________2Crystallographic data for Zn4O(BDC)3 desolvatedIntroductionThe structure consists of Zn4O tetrahedra centered at 1/4 1/4 1/4 (and equivalent positions) in the unit cell. Each edge of the tetrahedron is bridged by one end of a bdc ligand, which form the edges of a latticework of hollow cubes centered at 0 0 0, 1/2, 1/2, 1/2 and the faces of the cell.The space group is Fm3m with the ligand lying on the diagonal mirror planes.The final refinement of the cage showed several low angle data with values of Fobs > Fcalc, as expected for a model which did not account for the scattering of air in the open structure. The final refinement removed all reflections with a sin(O)/A < . This marginally improved the residuals and removed all large residual values of AF/,7(F).The highest peaks (lowest valleyes) in the AF map are and e- /Al, scattered randomly both near the molecular framework and in the void space. This contrasts with the relatively large values found in the non-evacuated sample. Clearly there is nothing in the hollows except freely moving air.ExperimentalData CollectionA colorless cubic crystal of Zn4Ol3C24Hl2 having approximate dimensions of x x mm was mounted on a glass fiber using Paratone N hydrocarbon oil. All measurements were made on a SMART" CCD area detector with graphite monochromated Mo-Kce radiation.Cell constants and an orientation matrix , obtained from a least-squares refinement using the measured positions of 5451 reflections in the range < 20 < ' corresponded to an F-centered cubic cell (laue class:m@m) with dimensions:a = (7)V =(8) A3For Z = 8 and . = , the calculated density is g/cm'. Based on the systematic absences of:hkl: h+k,k+l,h+l i4 2npacking considerations, a statistical analysis of intensity distribution, and the successful solution and refine-ment of the structure, the space group was determined to be:Fm3m (#225)The data were collected at a temperature of -104 ± I'C. Frames corresponding to an arbitrary hemi-sphere of data were collected using w scans of ' counted for a total of seconds per frame.Data ReductionData were integrated by the program SAINT" to a maximum 20 value of '. The data were corrected for Lorentz and polarization effects. Data were analyzed for agreement and possible absorption using XPREP 12 . An empirical absorption correction based on comparison of redundant and equivalent reflections as applied using SADABS 13 (Tmax = , Tmin = .Structure Solution and RefinementThe structure was solved by and expanded using Fourier techniques2. The non-hydrogen atoms were refined anisotropically. Hydrogen atoms were included but not refined. The final cycle of full-matrix least- squares refinement' was based on 563 observed reflections (I > (I)) and 25 variable parameters and converged (largest parameter shift was times its esd) with unweighted and weighted agreement factors of:R = EllFol - lFclllFlFol =R,, = (Ew(IFol - lFcl)2/EwFo2)] =The standard deviation of an observation of unit weight' was . The weighting scheme was based on counting statistics and included a factor (p = to downweight the intense reflections. Plots of Ew(IFol - lFcl)2 versus IFol, reflection order in data collection, sin O/A and various classes of indices showed no unusual trends. The maximum and minimum peaks on the final difference Fourier map corresponded to e-/A3, respectively.Neutral atom scattering factors were taken from Cromer and Waber5 . Anomalous dispersion effects were included in Fcalc6; the values for Af' and Af' were those of Creagh and McAuley7. The values for the mass attenuation coefficients are those of Creagh and Hubbel'. All calculations were performed using the teXsan9 crystallographic software package of Molecular Structure Corporation.Table 1. Atomic coordinates and Bi,,/B,q and occupancyatom x y z B,q occZn(l) (9) (2) 1/160(i) (5) (6) (2) 1/20(2) (16) 1/24C(l) (13) (4) 1/4C (2) (12) (4) 1/4C (3) (8) (10) (4) 1/2H(l) 1/2B,q = 872(Ull(aa*)2 + U22(bb')2 + U33(CC* )2 + 2Ul2aa*bb' cos -y + 2Ul3aa*cc* cos + 2U23bb*cc* cos a)Table 2. Anisotropic Displacement ParametersAtom Ull U22 U33 U12 U13 U23Zn(l) (17) (13)0(i) (7) (9) (8) (6)0(2) (12)C(l) (13) (2) (2)C (2) (13) (2) (2)C(3) (13) 0,0651 (14) (17) (g)The general temperature factor expression:exp(-27r2(a*2U,lh2 + b*2 U22k2 + C*2 U33 12 + 2a*b*Ul2hk + 2a*c*Ul3hi + 2b*c*U'-)3kl))Table 3. Bond Lengths(A)atom atom distance atom atom distanceZNl 01 (16) ZNI 01 (16)ZNI 02 (4) 01 ci (2)ci C2 (4) C2 C3 (3)C2 C3 (3) C3 C3 (5)Table 5. Bond Angles(')atom atom atom angle atom atom atom angle01 ZNl 01 (5) 01 ZNI 02 (5)01 ZNI 02 (5) ZNI 01 ci (2)ZNI 02 ZNI (7) ZNl 02 ZNI (7)ZNI 02 ZNI (15) ZNl 02 ZNI (15)ZNI 02 ZNI (7) ZNI 02 ZNl (7)01 ci 01 (3) 01 ci C2 (16)01 ci C2 (16) ci C2 C3 (16)ci C2 C3 (16) C3 C2 C3 (3)C2 C3 C3 (16)Zn4O(BDC)3 desolvated and heated to 300°C in airT=-124C1. 14834E+01 +00 2 0。
绿松 DRC房间控制系统2说明书

GreenMAX®DRC Room Control SystemSystem Objectives•Fully distributed room control system•Room Agnostic –Each room operates independently of other rooms and is not dependent on network processors or centralized controllers for operation•Not dependent on internet connectivity for operation or configuration•Uses wired LumaCAN high-performance networking for communication between devices •Uses wireless Ethernet for configuration and backbone connectivity•Fully configurable from a smart device app•Can be used to comply with IECC, ASHRAE 90.1 and 2019 Title 24, Part 6 0-10V dimming, occupancy/vacancy sensing, partial-ON, partial-OFF, daylighting and demand response requirementsSystem Features•Programmable via any WiFi-enabled Android or iOS smart device using the GreenMAX®DRC App•Multi-location switching•Fully programmable digital keypads/buttons with integral scene support•Occupancy/vacancy detection•Multi-zone occupancy•Partial-ON and partial-OFF functionality with configurable timeouts and levels for each•Operating Modes: Manual-ON, ON to Fixed Level, ON to Last Level•Multi-zone daylight harvesting•Closed loop•Auto or manual target level detection•Operating Mode: Cap at target or override multiple operation•User groups separate from daylighting or occupancy groups for simplified control•Control from GreenMAX DRC App, Sapphire touchscreen, GreenMAX DRC App, or LumaGraphics•Security –Fully encrypted and secure communication, multiple levels of user privilege and controlled user accessUser Interface •Keypads •Touchscreens •Smartphone AppSensors•Light Level Detection•Occupancy Detection•Network Sensors•Analog Sensors•Analog InterfaceLoad Controls•Phase Control•0-10V•DMX•DALI•GreenMAX Relay (no AI)Room Controllers•Line Voltage•Includes RC, 0-10V, & Relay•J-Box Mount•Low Voltage•Surface or Cabinet Mount•Control Only•Room Controller—Line Voltage•Includes 0-10V and relay• 1 required per room•Requires 225mA power•Can be connected to 100 “things.”All of the below = 1 thing•Smart pack• 1 channel of a phase control dimmer•Keypad (1,2,4,8 btn)• 1 Input of an AI•DALI input or output•DMX channel•Relay in a GreenMAX relay cabinet•Installation methods -install into knockout or act as cover for 4” square box •Primary Use•Coordinating the business logic within the room •Wi-Fi/Ethernet <->LumaCAN interface•Configuration interface for the system•Interfaces•LumaCAN In/Out•Termination provided via plug•Wi-Fi•ZigBee (future)•Room Controller—Low Voltage• 1 required per room•Requires 225mA power•Can be connected to 100 “things.” All of the below =1 thing•Smart pack• 1 channel of a phase control dimmer•Keypad (1,2,4,8 btn)• 1 Input of an AI•DALI input or output•DMX channel•Relay in a GreenMAX relay cabinet•Installation methods -surface or DIN rail•(1) Analog input, terminals: +24V, common, input •Can also be used to insert power to network, pairwith PST24-I10•Primary Use•Coordinating the business logic within the room •Wi-Fi/Ethernet <->LumaCAN interface•Configuration interface for the system•Interfaces•LumaCAN In/Out•Termination provided via plug•Wi-Fi•ZigBee (future)•Digital Switch (Keypads)•0-Many required per room•25mA Current draw each, powered from LumaCAN network•Buttons out of the box turn the LED ON/OFF but have no system interaction•All buttons are programmable•Engraving provided with every unit through Quotes, ASAP will include it when the engraving field iscompleted•Available in White, other colors via color change kit •Primary Use•Communicates to Room Controller (Sapphire too!), no functionality without Room Controller on-line•Each button is assigned an “Input” number •Interfaces•LumaCAN•Termination provided via dip switch•Sensors•0-Many required per room•450sqft occupancy•0-50fc photocell•Major motion detection only•35mA current draw, powered from LumaCAN network •Available in White, flush mount•2” Mounting hole•Class 2 in conduit? Drill 2” hole in side of junction box and install junction box in ceiling directly aboveceiling •Primary Use•Occupancy detection•Communicates to Room Controller (Sapphire too!), no functionality without Room Controller on-line•Each of the two sensors is assigned an inputnumber, when using with Sapphire, input is assignedvia dip switch and the two are consecutive•Interfaces•LumaCAN•Termination provided via dip switch•Analog Interface•(2) Analog Inputs•Powered from LumaCAN network•Current Draw: 35mA + connected devices•Things you can connect•0-10V photocell•Potentiometer•Low voltage switch•Low voltage occupancy sensor•Not dry contact or current loop•Install•Surface mount•Lid of 4-11/16” square box•One or More in DIN rail cabinet•7 on one rail of DINRK—001, or (6)+(1) PST24-I10•Primary Use•Interface to non-LumaCAN devices•Demand response interface•Fire alarm/security system interface•Communicates to network and/or Room Controller (including Sapphire) depending on configuration •Interfaces•(2) Analog In•+24VDC/Common Out•Termination provided via jumper•Smart Pack•(1) 20A relay + 0-10V controls•Self-powered, no current draw from network•No power supply to network•Install•Nipple mount•Lid of 4” square box•Sandwich when all must be in conduit •Assigned a single LumaCAN channel •Primary Use•Control of switching load•Control of 0-10V loads•Contact closure to other device•Interfaces•LumaCAN•Termination via jumper•Phase Control Dimmer•(4) 2.5A 120-277V 50/60Hz Phase ControlDimmers•Each Channel can be forward or reversephased•AMPlify Features –combine multiplechannels for increased capacity•200mA Network power required (transition)•Install•Requires Enclosure, DINRK-001 or larger •Assigned 1-4 LumaCAN Channels•Contact Closure Input (NOT AI!!)•Fully configurable dimmer curve •Primary Use•Control of phase control (Hot/Neutral) loads •Interfaces•LumaCAN•Termination via plug•DALI Gateway•(2) Channel DALI Gateway•Powered from LumaCAN network or adjacent power supply•60mA for interface•250mA for each DALI channel•Supports dedicated supply for DALI network •Patching device•DALI load = LumaCAN Channel•DALI actuator = LumaCAN Input•Fixed fade time for all DALI devices •Primary Use•Interface to DALI fixtures•Interfaces•LumaCAN•Termination via jumper•(2) DALI channels•LumaCAN Gateway•BACnet Interface•One required per LumaCAN sub-net•Limited to 500 points per interface•Object list•AO for each load control•AI for each actuator•Schedule with MSV for behaviors•DMX output interface•Patch 512 consecutive LumaCAN channels to DMX output•DMX input interface•Patch DMX Input to 512 consecutive LumaCANchannels•Luma-Net interface •Primary use•Interface to other network•(2) Protocols / interface•Powered from LumaCAN network or dedicated supply•Installs into ½ RU•PST24-R41•Sapphire Touchscreen•Touch-based user interface•325mA power draw + connected devices•Analog inputs can be any•Occupancy sensor•Switch•Potentiometer•Photocell•Patched to LumaCAN input•Screen configured from Sapphire Studio•May work with (or in some cases without) GreenMAX DRC Room Controller; app cannot be used toconfigure at this time •Primary Use•Touchscreen interface•LumaCAN interface•Ethernet interface for switcher/scaler, BC4, HiFiProgrammable Keypad Functions•Programmable Keypad Room Controller buttons—assignable with one of the following behaviors•Room commands—impacts everything controlled by the Room Controller•ON—Configurable level & fade time, observesdaylighting target•OFF•Toggle ON/OFF•Raise/Lower—Configurable % change/press,also support press/hold/release•Group commands•ON•OFF•Toggle ON/OFF•Raise/Lower •Scene—collection of groups at a level and recalled via a fade time. Also can include fixture attributes•Last Select Scene Raise/Lower—increases/decreases the selected scene and only things in that sceneApplicationsApplication Rules•One Room Controller per room•100 network devices (network nodes) per Room Controller•Photocell and sensor are 2 nodes•8-button is 1 node•One(and only one) Room Controller in every room•Observe power and data requirements for LumaCAN networks•Link rooms together via WiFi network•GreenMAX DRC is a new system and not an extension of GreenMAX Relay Panels although GreenMAX relays can be used with the system. GreenMAX components that do not work with GreenMAX DRC are as follows:•HDU•Scheduler•Analog input•Digital switchesWiFi and BACnet•What is WiFi used for?•Configuration•App control•One controller controlling things in another room•What is BACnet used for?•Control from a BMS system•LumaGraphics•Some system may need both•LumaCAN connectivity between rooms only required for BACnetSmart Packs, Keypads, & SensorGreenMAX DRC AppConfiguration and controlGreenMAX DRCRoom ControllerGreenMAX DRC Smart PacksGreenMAX DRCOccupancy and Photocell SensorGreenMAX DRC KeypadsGreenMAX DRCRoom ControllerGreenMAX DRC Smart PacksGreenMAXDRCOccupancy andPhotocellSensorGreenMAX DRC KeypadsAdd Phase Control Dimmer ControlDimmerGreenMAX DRC AppConfiguration and controlGreenMAX DRCRoom ControllerGreenMAX DRC Smart PacksGreenMAXDRCOccupancy andPhotocellSensorBACnet Interface ControlDimmerLumaCAN Gateway GreenMAX DRC AppConfiguration and controlGreenMAX DRC KeypadsDALI InterfaceGreenMAX DRC AppConfiguration and controlGreenMAX DRC RoomControllerLED LightingGreenMAXDRCOccupancy and Photocell SensorPower SupplyGreenMAX DRC KeypadsDMX InterfaceGreenMAX DRC AppConfiguration and controlGreenMAX DRC RoomControllerGreenMAXDRCDMX InterfaceLED LightingGreenMAXDRCOccupancy andPhotocellSensorPower SupplyGreenMAX DRC KeypadsBuilding Rooms into SystemsGreenMAX DRCGreenMAX DRC AppConfiguration and controlGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC AppGreenMAX DRCRoom ControllerGreenMAX DRCSmart PacksGreenMAXDRCOccupancyand PhotocellSensor GreenMAX DRCKeypadsGreenMAX DRCPhase ControlDimmerGreenMAX DRC App•Configuration over WiFi•Each Room Controller is its own AP•BACnet interface connected to LumaCANnetwork•LumaCAN network connection between rooms•One BACnet interface connection required perLumaCAN network•LumaCAN rules with GreenMAX DRC are thesame as LumaCAN rules with GreenMAX•250 nodes per network•1600 feet per segment• 6 port and 2 port repeaters for longer networksand home run topologyMultiple Rooms on BACnetTo BACnet/IP networkWi-Fi & BACnet NetworkCeiling Room ControllerSmartPacksKeypadsPhase ControlDimmersCeiling Room Controller Smart PacksKeypads Phase Control DimmersCeiling Room Controller Smart PacksKeypads Phase Control DimmersCeiling Room Controller Smart PacksKeypadsPhase Control DimmersCeiling Room ControllerSmart PacksKeypadsPhase Control DimmersCeiling Room ControllerSmart PacksKeypadsPhase Control DimmersCeiling Room ControllerSmart PacksKeypadsPhase Control DimmersCeiling Room ControllerSmart PacksKeypadsPhase Control DimmersTo BACnet/IP networkTo BACnet/IP networkCommissioning Flow•Create the project (internet connection required)•Assign other users to the project if more then one person commissioning•All commission is done one room at a time from within the room•Create the room through the building hierarchy•Connect to the Room Controller over WiFi—System broadcasts as “GreenMax DRC xxxxxx” —sticker with serial number is on the device•Use “identify” to confirm you have the DRC you want•Update firmware if required•Connect to building access point if needed•Add devices to this Room Controller, use identify and name devices—remove devices that belong to other rooms •Set up groups, scenes, daylighting/occupancy zones, and keypad programming•Move to next room•Sync to cloudConnectivity to Leviton Cloud Servers•System does not require cloud connectivity for operation; however, we use Leviton cloud services as a central point of authority for security•Connectivity is required to create a new project and add/modify/remove users•Periodic internet connectivity is required to•Update project access list•Sync new rooms with the cloud during commissioning•Move access permissions between users•During Commissioning•Rooms can be created without internet connectivity•GreenMAX DRC App—communicates to you when changes need to be synchronizedEnergy Code Compliance2018 IECC vs. ASHRAE 90.1 2019 vs. 2019 Title 24Control Type2018 IECCASHRAE 90.1 20192019Title 24Summary of RequirementsManual Space Control ✓✓✓•Every area enclosed by walls or floor-to-ceiling partitions must have a manual control•Controls must be located within the area served by the controls, or must be a remote switch clearly identifying the lights it controls with a status indicatorAutomatic Shutoff ✓✓✓•Automatic time switches are required in most areas that are not controlled by an occupancy sensor. The switch must also have a manual override•Different applications have specific guidelines for partial-OFF, bi-level and auto-OFF sensors Multi-Level Area Lighting Controls ✓✓✓•Manual-ON/OFF override control is required in each area enclosed by ceiling-height partitions •Each area required to have manual control is also required to be able to reduce the lighting by 50%Automatic Daylight Control ✓✓✓•Control required in daylight control zones that provide these areas with separate control that is independent of the general lighting in the space, which can be stepped or continuous dimming •Calibration cannot be located on the photocontrolReceptacle Control ✓✓✓•Required in specific applications to keep certain receptacles powered OFF based on occupancyDemand Response✓•Required in buildings > 10,000sqft to reduce the energy usage from a signal supplied from the power company. Interface to utility may be provided by Leviton or by others, interface to GreenMAX DRC is via analog interface.Ordering InformationOrdering InformationCat. No.Product DescriptionDRC07-ED0GreenMAX DRC Line Voltage Room Controller, 120-277VAC, 50/60 Hz DRC00-0L0GreenMAX DRC Low Voltage Room Controller, DIN Rail form factor DRC00-030GreenMAX DRC Line Voltage Room Controller, 347VAC, 60 HzOSR05-ICW GreenMAX DRC Occupancy Sensor and PhotocellDRDDP-A40GreenMAX DRC Phase Control DimmerDRID0-C02GreenMAX DRC 2-Port AIDRD07-ED0GreenMAX DRC Smart Pack, 120-277VACDRD07-E30GreenMAX DRC Smart Pack, 347VACOrdering Information—SwitchesCat. No.Product DescriptionDRKDN-1Cx GreenMAX DRC Digital Switch, 1-Button, LumaCAN3 (inc.single-gang wallplate) DRKDN-2Cx GreenMAX DRC Digital Switch, 2-Button, LumaCAN3 (inc.single-gang wallplate) DRKDN-4Cx GreenMAX DRC Digital Switch, 4-Button, LumaCAN3 (inc.single-gang wallplate) DRKDN-8CW GreenMAX DRC Digital Switch, 1-Button, LumaCAN3 (inc.single-gang wallplate) CKDNK-10y GreenMAX DRC 1-Button Color Change Kit (inc.single-gang wallplate)CKDNK-20y GreenMAX DRC 2-Button Color Change Kit (inc.single-gang wallplate)CKDNK-40y GreenMAX DRC 4-Button Color Change Kit (inc.single-gang wallplate)CKDNK-80y GreenMAX DRC 8-Button Color Change Kit (inc.single-gang wallplate)CKDNK-1Ey GreenMAX DRC 1-Button Color Change Kit w/engraving (inc.single-gang wallplate) CKDNK-2Ey GreenMAX DRC 2-Button Color Change Kit w/engraving (inc.single-gang wallplate) CKDNK-4Ey GreenMAX DRC 4-Button Color Change Kit w/engraving (inc.single-gang wallplate) CKDNK-8Ey GreenMAX DRC 8-Button Color Change Kit w/engraving (inc.single-gang wallplate)Thank You。
英语作文打分软件

When it comes to evaluating English compositions,a scoring software can be an invaluable tool for educators and students alike.Here are some key features and considerations for such software:1.Automated Scoring:The software should be able to automatically score essays based on preset criteria such as grammar,punctuation,vocabulary usage,and sentence structure.2.Customizable Rubrics:To cater to different educational levels and objectives,the software should allow users to customize scoring rubrics.This means educators can define what aspects of writing are most important for their specific needs.3.Feedback Generation:Beyond just scoring,the software should provide constructive feedback.It should highlight errors and suggest corrections,as well as commend good usage and structure.4.Speed and Efficiency:The software should process and score essays quickly, especially when dealing with large volumes of student work.5.Consistency:One of the main advantages of using software is the consistency in scoring.It should apply the same standards to all essays,reducing the subjectivity that can occur in human scoring.6.Integration with Learning Management Systems LMS:For seamless workflow,the software should integrate with existing LMS platforms,allowing for easy assignment submission and grading.erFriendly Interface:The software should be easy to navigate for both teachers and students.It should have a clean interface that makes uploading,scoring,and reviewing essays straightforward.8.Data Analytics:It should offer analytics on student performance over time,helping teachers to identify trends and areas for improvement.9.Security and Privacy:The software must ensure the privacy and security of student work and data,complying with educational data protection regulations.10.Multilingual Support:For a diverse student body,the software should support multiple languages,allowing for the scoring of essays in different languages.11.Adaptive Learning:Advanced software may include features that adapt to thestudents skill level,providing personalized feedback and suggestions for improvement.12.Accessibility:The software should be accessible to all students,including those with disabilities,ensuring that the interface and feedback are easy to understand and navigate.13.Professional Development:The software provider may offer training and support for educators to make the most of the tools capabilities.14.CostEffectiveness:While its important to have a robust tool,it should also be affordable,especially for schools with limited budgets.15.Regular Updates:Language evolves,and so should the software.Regular updates to the scoring algorithms and feedback mechanisms ensure the software remains relevant and effective.When selecting an English composition scoring software,its important to consider these features and how they align with the specific needs of your educational environment.。
Editorial-Board_2016_Signal-Processing

SIGNAL PROCESSINGAn International JournalA publication of the European Association for Signal Processing (EURASIP)Printed in the NetherlandsEditorial Policy. Signal Processing is an Interdisciplinary Journal presenting the theory and practice of signal processing. Its primary objectives are the following: – D issemination of research results and of engineering developments to all signal processing groups and individuals.– P resentation of practical solutions to current signal processing problems in engineering and science.The editorial policy and the technical content of the Journal are the responsibility of the Editor-in-Chief and the Editorial Board. The Journal is self-supporting from subscription income and contains a minimum amount of advertisements. The journal welcomes contributions from every country in the world.Scope. Signal Processing incorporates all aspects of the theory and practice of signal processing (analogue and digital). It features original research work, tutorial and review articles, and accounts of practical developments. It is intended for a rapid dissemination of knowledge and experience to engineers and scientists working in signal processing research, development or practical application.Subjects. Subject areas covered by the Journal include:Signal Theory, Stochastic Processes, Detection and Estimation, Spectral Analysis, Filtering, Signal Processing Systems, Software Developments, Image Processing, Pattern Recognition, Optical Signal Processing, Digital Signal Processing, Multidimensional Signal Processing, Communication Signal Processing, Biomedical Signal Processing, Geophysical and Astrophysical Signal Processing, Earth Resources Signal Processing, Acoustic and Vibration Signal Processing, Data Processing, Remote Sensing, Signal Processing Technology, Speech Processing, Radar Signal Processing, Sonar Signal Processing, Special Signal Processing, Industrial Applications, New Applications.Publication information: Signal Processing (ISSN 0165–1684). For 2016, volume 118-129 (12 issues) is scheduled for publication.Subscription prices are available upon request from the Publisher or from the Elsevier Customer Service Department nearest you or from this journal’s website (/locate/sigpro ). Further information is availableon this journal and other Elsevier products through Elsevier’s website (). Subscriptions are accepted on a prepaid basis only and are entered on a calendar year basis. Issues are sent by standard mail (surface within Europe, air delivery outside Europe). Priority rates are available upon request. Claims for missing issues should be made within six months of the date of dispatch.Orders, claims, an d journ al in quiries: please contact the Elsevier Customer Service Department nearest you:St. Louis: Elsevier Customer Service Department, 3251 Riverport Lane, Maryland Heights, MO 63043, USA; phone: (877) 8397126 [toll free within the USA]; (+1) (314) 4478878 [outside the USA]; fax: (+1) (314) 4478077; e-mail: Journal CustomerService-usa@Oxford: Elsevier Customer Service Department, The Boulevard, Langford Lane, K idlington OX5 1GB, UK ; phone: (+44) (1865) 843434; fax: (+44) (1865) 843970; e-mail: JournalsCustomerServiceEMEA@ Tokyo: Elsevier Customer Service Department, 4F Higashi-Azabu, 1-Chome Bldg, 1-9-15 Higashi-Azabu, Minato-ku, Tokyo 106-0044, Japan; phone: (+81) (3) 5561 5037; fax: (+81) (3) 5561 5047; e-mail: JournalsCustomerServiceJapan@Singapore: Elsevier Customer Service Department, 3 K illiney Road, #08-01 Winsland House I, Singapore 239519; phone: (+65) 63490222; fax: (+65) 67331510; e-mail: JournalsCustomerServiceAPAC@ Advertisin g in formation. If you are interested in advertising or other commercial opportunities please e-mail Commercialsales@ and your inquiry will be passed to the correct person who will respond to you within 48 hours.For full membership information of the Association, possibly combined with a subscription at a reduced rate, please contact: EURASIP, P.O. Box 134,CH-10000 Lausanne 13, Switzerland.The paper used in this publication meets the requirements of ANSI/NISO Z39.48-1992 (Permanence of Paper).Editor-in-ChiefBjörn Ottersten R oyal Institute of Technology SE-100 44 Stockholm, Sweden E-mail: bjorn.ottersten@ee.kth.seEditorial BoardB. Amblard (Saint Martin d'hères cedex, France)A.K. Barros (Sao Luis, Brazil)P. Bianchi (Paris, France)H. Boche (Berlin, Germany)T.D. Bui (Montréal, Canada)M. Cagnazzo (Paris, France)A. Carini (Urbino, Italy)R. Chellappa (College Park, MD, USA)S. Chen (Southampton, UK)N.I. Cho (Seoul, Korea)P.L. Correia (Lisboa, Portugal)J.P. Delmas (Evry, France)I. Djurovic (Podgorica, Montenegro)K. Dogancay (Mawson Lakes, SA, Australia)A. Ertüzün (Istanbul, Turkey)J. Fonollosa (Barcelona, Spain)X. Gao (Xi’an, China)G. B. Giannakis (Twin Cities, MN, USA)F. Gini (Pisa, Italy)J.-M. Guo (Taipei, Taiwan)R. Hong (Hefei, China)A. Jakobsson Lund (Sweden)M. Jansen (Eindhoven, the Netherlands)M. Jansson (Stockholm, Sweden)M. Jiang (Beijing, China)C. Jutten (Grenoble, France)M. Kieffer (Paris, France)P. Larzabal (Cachan, France)H. Li (Hoboken, New Jersey)X. Li (Shaanxi, China)Q. Liu (Beijing, China)K. Ma (Shatin, Hong Kong)L. Mihaylova (Lancaster, UK)A. Napolitano (Naples, Italy)A. Nehorai (St. Louis, MO, USA)A.I. Perez (Catalunya Spain)M. Pesavento (Darmstadt, Germany)W. Puech (Montpellier, France)M. Renfors (Tampere, Finland)C. Richard (Cedex, France)A. Rontogiannis (Athens, Greece)A. H. Sayed (Los Angeles, CA, USA)P. Shi (Adelaide, Australia)H.C. So (Hong Kong, China)L. Stankovic (Montpellier, France)P. Stoica (Uppsala, Sweden)D. Tao (Sydney, Australia)J.-Y. Tourneret (Cedex, France)C.-C. Tseng (Kaohsiung, Taiwan, ROC)H. Wendt (Toulouse, France)S. Werner (Helsinki, Finland)L. Wu (Harbin, China)H. Yu (Blacksburg, VA, USA)Y. Zhang (Villanova, PA, USA)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
(2) Average ROI of trade promotions
Average out of stock rate Lost sales: $3.19 per store visit / $69 billion for top 100(3), (4) retailers Of all product launches fail (while average time to market is (5) 27.5 months)
All forward-looking statements are subject to various risks and uncertainties that could cause actual results to differ materially from expectations. Readers are cautioned not to place undue reliance on these forward-looking statements, which speak only as of their dates, and they should not be relied upon in making purchasing decisions.
3
Todays Challenges of Consumer Goods Companies
20%
-19% 20%
(1) Of Overall revenue is spend for sales and marketing Return On Investment (ROI) is priority #1
Demand Management in Real Time
Retail Demand – Aggregated POS Data Point-of-Sales Data – Individual Consumer Demand
Consumer Level
■ Analysis of Point-of-Sales Data via
© 2011 SAP AG. All rights reserved.
Customer
2
Agenda
■ ■ ■
Demand Signal Management Overview & Value
Deep Dive Summary
© 2011 SAP AG. All rights reserved.
Customer
Network Demand Structures
Central Demand – Procure or Manufacture Wholesale Demand – Aggregated Retail Data
Wholesale Level
Retail Level
Point-of-Sale Data
Consistent, centralized in-memory database for BIG DATA
Store massive volume of external demand data (e.g. point-of-sales data) and integrate internal SAP Business Suite data (e.g. master data). Automated data mapping and harmonization.
■
Current status
Under development
■
Planned time to market
Release 1.0: Q4 2012 Focus on POS, social media and market research & SAP suite data (harmonizing internal & external data), analytics, integration with select SAP suite apps
Increase consumer demand visibility with SAP Demand Signal Management on HANA
Stephan Kreipl – Chief Product Owner Demand Signal Management May 2012 Customer
Data provider for consuming applications
Valuable input for different applications (e.g. Trade Promotion Optimization) and analytics (e.g. Market Share Analysis, On-Shelf-Availability, New Product Launch, …)
Source: Accenture (1), Capgemini (2), GS1 (3), IHL/RIS (4), AMR (5)
75%
© 2011 SAP AG. All rights reserved.
Customer
4
POS Data Provides Instant Information On Consumer Demand
NEW!!!
Distribution Network
Finished Goods Supplier Level Central / OEM Level
SAP Demand Signal Management
Integration to consumer demand
Existing Approach
Disclaimer
The information in this document is confidential and proprietary to SAP and may not be disclosed without the permission of SAP. This document is not subject to your license agreement or any other service or subscription agreement with SAP. SAP has no obligation to pursue any course of business outlined in this document or any related presentation, or to develop or release any functionality mentioned therein. This document, or any related presentation and SAP's strategy and possible future developments, products and or platforms directions and functionality are all subject to change and may be changed by SAP at any time for any reason without notice. The information on this document is not a commitment, promise or legal obligation to deliver any material, code or functionality. This document is provided without a warranty of any kind, either express or implied, including but not limited to, the implied warranties of merchantability, fitness for a particular purpose, or non-infringement. This document is for informational purposes and may not be incorporated into a contract. SAP assumes no responsibility for errors or omissions in this document, except if such damages were caused by SAP intentionally or grossly negligent.
Central source of truth for enhanced reporting
Powerful capabilities to process and analyze terabytes of market research and demand data on-the-fly and in real-time
■ Creation of logistics corrective measures
out of real time analytics
■ Central level allways gets falsified
(delayed / agregated ) demand signals from the final consumer level
© 2011 SAP AG. All rights reserved.
Customer
5
SAP Demand Signal Management on HANA
Definition
SAP’s Demand Signal Management solution is a consistent centralized in-memory database
© 2011 SAP AG. All rights reserved.
