直接portal认证实验总结
portal学习总结

特点: 1.整个交互过程radius服务器完全是被动的回应AC的请求,radius从不主动 发起报文。 2.交互过程以AC和radius保存的共享密钥做为开始的基础,任何密码在交互 过程中都是加密伪装的,即便使用PAP方式,也会经过md5算法改装。 3.一次用户上下线的周期里,连接只有一次,计费信息会有多次交互 4. RADIUS报文封装在UDP报文的数据域中。并且没有心跳报文,维护的策 略由AC自行决定,包括超时时间,重传次数与间隔等。
Portal 服务 器
Performance-Free Wireless LANs 10849_Icons_May2005
TM
© 2008 Autelan Technologies, Inc. All rights reserved.
Autelan Public
6
Chap和pap
用户密码
服 PAP和CHAP协议是目前的在PPP中普遍使 务 用的认证协议,CHAP在RFC1994中定义,
Performance-Free Wireless LANs 10849_Icons_May2005
TM
© 2008 Autelan Technologies, Inc. All rights reserved.
Autelan Public
5
用户和portal站点的交互
AC
用户和动态网页的交互,AC只起连接的作用。具 体交互过程中的加密等交互细节由portal网页的代 码实现。Portal获取用户的用户名和密码等信息。
都不一样,可以很有效地避免监听攻击。 但密码在服务器本地仍然是明文存储的,且挑战 的长度和随机性仍然是安全漏洞,另外单向hash 算法的选择至关重要。(md5只是hash单向算法 的一种,作用就是一个多对一得字串变换)
免费Portal(无线接入认证)系统解决方案

免费Portal无线接入认证系统解决方案蓝海卓越基于多年的产品运营经验及对无线网络运营需求的深刻理解,针对中低端用户推出一套免费的“Web Portal无线接入认证系统”,从打造可管理、可运营的无线网络角度出发,致力于为中低端用户建设一个高效可靠、运营成本低的商用无线网络,使无线网络的部署轻松、可靠、高效。
需求分析在众多的公共场所,如:酒店、咖啡厅、学校、车站、商场等人流众多的地方,商家为了留住客户、解决客户在购物消费和等待时的上网问题,往往配置无线接入点提供给广大客户上网使用,而这种传统的输入密码方式不仅给管理带来了极大的不便,同时也具有一定的不安全性。
为了实现方便易用、安全稳定的无线接入认证,需要满足以下需求:1、方便部署、易于维护;使用此种解决方案的客户,无线认证规模都不是很大,大部分意向用户看到网上此类方案繁琐的安装介绍就已经选择止步了。
而我们提供的免费Portal 系统方案,用户可以很方便的进行安装部署,中文管理界面,易于维护。
2、能够在系统中建立上网账户,对用户进行管理;本系统采用Radius认证的方式,支持标准的Radius协议,用户可以自行选择Radius系统或者和现有的Radius系统对接。
免费版Portal系统集成FreeRadius,能够方便的建立用户上网账户,对用户的上网时长、上传下载等进行有效管理。
3、可以设置认证界面,推送相关信息和广告内容;认证页面高度定制,可以随意的设置满足自己需求的认证页面,目前支持JAVA、PHP环境。
方案拓扑方案中所需要的设备主要包括:Portal服务器、胖AP。
Portal服务器:蓝海卓越免费版Portal系统,WINDOWS环境,安装在一台WIN 系统电脑上即可;胖AP:胖AP产品分为室内型吸顶式AP和室外型壁挂式AP,均为蓝海卓越自主开发的AP固件,集成AP、AC及路由等功能,与蓝海卓越免费版Portal系统完美对接。
方案及Portal服务器说明1、部署简单,不影响现有网络环境;Portal服务程序为WIN环境,大大降低的安装的复杂性,只需要安装在现有环境中任意一台电脑中即可;同时只需要购买蓝海卓越一台胖AP产品即可,胖AP支持多种接入方式,完全适应现有的网络环境。
portal测试报告

1、PC机,全国portal 167 http://202.109.207.167:8088/省portal 167(河北)http://202.109.207.167:8088/HePortal/services/PortalServices测试认证失败,测试成功[loginV3]:userName:fjtest provinceCode:w.fj loginName:fjtest@w.fjipAddr:202.109.207.210LoginActionV3[LoginApply]:loginName:fjtest@w.fj ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:47:57url=http://202.109.207.167:8088/HePortal/services/PortalServices[LoginApply]:userName:fjtes loginName:fjtest@w.fj ipAddr:202.109.207.210PortalManagerImpl timeStamp=2011-11-16 15:47:57[LoginHandler]:[execute]:loginName:fjtest@w.fj ipAddr:202.109.207.210 loginOperation:2 [LoginHandler]:[execute]:ResultCode:44 ResultInfo:BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:47:57,515 method:{password=123, userName=fjtes,loginName=fjtest@w.fj, ipAddr=202.109.207.210}=>{loginOperation=2};44;BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:47:57,515 method:[LoginApply]:loginName:fjtest@w.fjipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:47:57 resultCode=44 description=BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:47:57,515 method:{password=123, userName=fjtest, pro=null, loginName=fjtest@w.fj, ipAddr=202.109.207.210, provinceCode=w.fj}=>null;44;BAS设备告诉PortalServer此用户认证失败(发生错误)2、手机,全国portal 167 http://202.109.207.167:8088/省portal 167(河北)http://202.109.207.167:8088/HePortal/services/PortalServices测试认证失败,测试成功[INFO ] 2011-11-16 15:45:03,296 method:[loginV3]:userName:fjtest provinceCode:w.fj loginName:fjtest@w.fj ipAddr:202.109.207.219LoginActionV3[INFO ] 2011-11-16 15:45:03,406 method:[LoginApply]:loginName:fjtest@w.fjipAddr:202.109.207.219RemoteClientPortalManager timeStamp=2011-11-16 15:45:03url=http://202.109.207.167:8088/HePortal/services/PortalServices[INFO ] 2011-11-16 15:45:03,609 method:[LoginApply]:userName:fjtes loginName:fjtest@w.fj ipAddr:202.109.207.219PortalManagerImpl timeStamp=2011-11-16 15:45:03[INFO ] 2011-11-16 15:45:03,671 method:[LoginHandler]:[execute]:loginName:fjtest@w.fj ipAddr:202.109.207.219 loginOperation:2[INFO ] 2011-11-16 15:45:03,687 method:[PortalInterfaceFactory]:[factory]:enter into method! [INFO ] 2011-11-16 15:45:03,687 method:[PortalInterfaceFactory]:[factory]:loginOperation:2 [INFO ] 2011-11-16 15:45:03,687 method:[PortalInterfaceFactory]:[factory]:UDPServer2 [INFO ] 2011-11-16 15:45:04,031 method:[LoginHandler]:[execute]:ResultCode:44 ResultInfo:BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:45:04,031 method:{password=qq, userName=fjtes,loginName=fjtest@w.fj, ipAddr=202.109.207.219}=>{loginOperation=2};44;BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:45:04,046 method:[LoginApply]:loginName:fjtest@w.fjipAddr:202.109.207.219RemoteClientPortalManager timeStamp=2011-11-16 15:45:03resultCode=44 description=BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 15:45:04,046 method:{password=qq, userName=fjtest, pro=null, loginName=fjtest@w.fj, ipAddr=202.109.207.219, provinceCode=w.fj}=>null;44;BAS设备告诉PortalServer此用户认证失败(发生错误)3、PC机,全国portal 167 省portal 166(福建)连接成功,下线成功[INFO ] 2011-11-16 15:16:44,187 method:[loginV3]:userName:fztest@fzlan provinceCode:w.fj loginName:fztest@fzlan@w.fj ipAddr:202.109.207.210LoginActionV3[INFO ] 2011-11-16 15:16:44,375 method:[LoginApply]:loginName:fztest@fzlan@w.fj ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:16:44url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 15:16:45,250 method:[LoginApply]:loginName:fztest@fzlan@w.fj ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:16:44 resultCode=0 description=请求成功[INFO ] 2011-11-16 15:16:45,250 method:{password=83330625, userName=fztest@fzlan, pro=fj, loginName=fztest@fzlan@w.fj, ipAddr=202.109.207.210, provinceCode=w.fj}=>null;0;请求成功[INFO ] 2011-11-16 15:18:57,578method:[PhoneLogoutAction]:[execute]:loginName=fztest@fzlan@w.fj[INFO ] 2011-11-16 15:18:57,578method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210[ERROR] 2011-11-16 15:18:57,578method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210&remoteAddr=202.109.207.210 [INFO ] 2011-11-16 15:18:57,734 method:[LogoutApply]:ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:18:57url=http://202.109.207.166:8080/FjPortal/services/PortalServices4、PC机,全国portal 167 省portal 166(福建)ip地址池没找到[INFO ] 2011-11-16 15:02:27,437 method:[loginV3]:userName:fjtest provinceCode:w.fj loginName:fjtest@w.fj ipAddr:202.109.207.210LoginActionV3[INFO ] 2011-11-16 15:02:27,562 method:[LoginApply]:loginName:fjtest@w.fjipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:02:27url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 15:02:28,125 method:[LoginApply]:loginName:fjtest@w.fjipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 15:02:27 resultCode=11001000 description=找不到SDX信息[INFO ] 2011-11-16 15:02:28,125 method:{password=f, userName=fjtest, pro=fj,loginName=fjtest@w.fj, ipAddr=202.109.207.210, provinceCode=w.fj}=>null;11001000;找不到SDX信息5、PC机,全国portal 167 省portal 166(福建)用户认证失败[INFO ] 2011-11-16 14:58:55,343 method:[LoginHandler]:[execute]:ResultCode:44 ResultInfo:BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 14:58:55,343 method:{password=ff, userName=fs, loginName=fse@w.fj, ipAddr=202.109.207.210}=>{loginOperation=2};44;BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 14:58:55,343 method:[LoginApply]:loginName:fse@w.fjipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 14:58:54 resultCode=44 description=BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 14:58:55,343 method:{password=ff, userName=fse, pro=null,loginName=fse@w.fj, ipAddr=202.109.207.210, provinceCode=w.fj}=>null;44;BAS设备告诉PortalServer此用户认证失败(发生错误)6、手机,全国portal 167 省portal 167(河北)测试上线下认证成功[INFO ] 2011-11-16 16:20:01,218 method:[loginV3]:userName:483752463@fzlan provinceCode:w.fj loginName:483752463@fzlan@w.fj ipAddr:202.109.207.210LoginActionV3 [INFO ] 2011-11-16 16:20:01,218method:[DefaultFilter]:[doFilter]:userAgent:Post_Multipart[202.109.207.210][INFO ] 2011-11-16 16:20:01,312 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 16:20:01url=http://202.109.207.167:8088/HePortal/services/PortalServices[INFO ] 2011-11-16 16:20:01,390 method:[LoginApply]:userName:48375246loginName:483752463@fzlan@w.fj ipAddr:202.109.207.210PortalManagerImpltimeStamp=2011-11-16 16:20:01[INFO ] 2011-11-16 16:20:01,406method:[DefaultFilter]:[doFilter]:userAgent:null[202.109.207.210][INFO ] 2011-11-16 16:20:01,453method:[LoginHandler]:[execute]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.210 loginOperation:2[INFO ] 2011-11-16 16:20:01,453 method:[PortalInterfaceFactory]:[factory]:enter into method! [INFO ] 2011-11-16 16:20:01,453 method:[PortalInterfaceFactory]:[factory]:loginOperation:2 [INFO ] 2011-11-16 16:20:01,453 method:[PortalInterfaceFactory]:[factory]:UDPServer2 [INFO ] 2011-11-16 16:20:01,671 method:[LoginHandler]:[execute]:ResultCode:0 ResultInfo:请求成功[INFO ] 2011-11-16 16:20:01,671 method:{password=j99ume, userName=48375246, loginName=483752463@fzlan@w.fj, ipAddr=202.109.207.210}=>{loginOperation=2};0;请求成功[INFO ] 2011-11-16 16:20:01,671 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 16:20:01 resultCode=0 description=请求成功[INFO ] 2011-11-16 16:20:01,671 method:{password=j99ume, userName=483752463@fzlan, pro=null, loginName=483752463@fzlan@w.fj, ipAddr=202.109.207.210,provinceCode=w.fj}=>null;0;请求成功[INFO ] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210[ERROR] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210&remoteAddr=202.109.207.210 [INFO ] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210[ERROR] 2011-11-16 16:20:19,734method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.210&remoteAddr=202.109.207.210 [INFO ] 2011-11-16 16:20:19,828 method:[LogoutApply]:ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 16:20:19url=http://202.109.207.167:8088/HePortal/services/PortalServices[INFO ] 2011-11-16 16:20:19,843 method:[LogoutApply]:ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 16:20:19url=http://202.109.207.167:8088/HePortal/services/PortalServices[INFO ] 2011-11-16 16:20:19,953 method:[PortalManagerImpl]:[LogoutApply]:loginName= [INFO ] 2011-11-16 16:20:19,953method:[PortalManagerImpl]:[LogoutApply]:ipAddr=202.109.207.210[ERROR] 2011-11-16 16:20:19,953method:[PortalManagerImpl]:[LogoutApply]:ipAddr=202.109.207.210&rememberAddr=202.109. 207.210[INFO ] 2011-11-16 16:20:19,968 method:[PortalInterfaceFactory]:[factory]:enter into method! [INFO ] 2011-11-16 16:20:19,968 method:[PortalInterfaceFactory]:[factory]:loginOperation:2 [INFO ] 2011-11-16 16:20:19,968 method:[PortalInterfaceFactory]:[factory]:UDPServer2 [INFO ] 2011-11-16 16:20:20,125 method:[LogoutHandler]:[execute]:ResultCode:0 ResultInfo:BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 16:20:20,125 method:[LogoutApply]:ipAddr:202.109.207.210RemoteClientPortalManager timeStamp=2011-11-16 16:20:19 resultCode=0 description=BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 16:20:35,671 method:[DefaultFilter]:[doFilter]:userAgent:Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; GTB7.1; .NET CLR 2.0.50727; .NET CLR 3.0.04506.30; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)[202.109.207.210]1、PC机,全国portal 167 省portal 166(福建)测试认证失败[INFO ] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214[ERROR] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214&remoteAddr=202.109.207.214 [INFO ] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214[ERROR] 2011-11-16 16:49:23,687method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214&remoteAddr=202.109.207.214 [INFO ] 2011-11-16 16:49:23,781 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:49:23url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 16:49:23,921 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:49:23url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 16:49:34,859 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:49:23 resultCode=0 description=BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 16:49:34,968method:[DefaultFilter]:[doFilter]:userAgent:Post_Multipart[202.109.207.214][INFO ] 2011-11-16 16:50:24,734 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:49:23 resultCode=51 description=PortalServer发给BAS设备没有收到BAS设备发来的对各种请求的响应报文,而定时器时间到(即超时)1、PC机,全国portal 167 省portal 166(福建)测试上线认证成功全国Portal167[INFO ] 2011-11-16 16:55:21,171 method:[loginV3]:userName:483752463@fzlan provinceCode:w.fj loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214LoginActionV3 [INFO ] 2011-11-16 16:55:21,265 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:55:21url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 16:55:22,000 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:55:21 resultCode=0 description=请求成功[INFO ] 2011-11-16 16:55:22,000 method:{password=j99ume, userName=483752463@fzlan, pro=null, loginName=483752463@fzlan@w.fj, ipAddr=202.109.207.214,provinceCode=w.fj}=>null;0;请求成功省Portal166[INFO ] 2011-11-16 16:55:22,675 method:[LoginHandler]:[execute]:ResultCode:0 ResultInfo:请求成功[INFO ] 2011-11-16 16:55:22,675 method:{password=j99ume, userName=48375246, loginName=483752463@fzlan@w.fj, ipAddr=202.109.207.214}=>{loginOperation=2};0;请求成功全国portal 167 省portal 166(福建)测试下线成功全国Portal167[INFO ] 2011-11-16 16:57:25,703method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 16:57:25,703method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214[ERROR] 2011-11-16 16:57:25,703method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214&remoteAddr=202.109.207.214 [INFO ] 2011-11-16 16:57:25,781 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:57:25url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 16:57:26,578 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:57:25resultCode=0 description=BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 16:57:26,593 method:[DefaultFilter]:[doFilter]:userAgent:Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; GTB7.1; .NET CLR 2.0.50727; .NET CLR 3.0.04506.30; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)[202.109.207.214]1、PC机,全国portal 167 省portal 166(福建)测试上线认证失败[INFO ] 2011-11-16 16:59:22,968 method:[loginV3]:userName:13333 provinceCode:w.fj loginName:13333@w.fj ipAddr:202.109.207.214LoginActionV3[INFO ] 2011-11-16 16:59:23,078 method:[LoginApply]:loginName:13333@w.fjipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:59:22url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 16:59:23,453 method:[LoginApply]:loginName:13333@w.fjipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 16:59:22 resultCode=44 description=BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 16:59:23,453 method:{password=111, userName=13333, pro=null, loginName=13333@w.fj, ipAddr=202.109.207.214, provinceCode=w.fj}=>null;44;BAS设备告诉PortalServer此用户认证失败(发生错误)[INFO ] 2011-11-16 17:02:27,484 method:[loginV3]:userName:483752463@fzlan provinceCode:w.fj loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214LoginActionV3 [INFO ] 2011-11-16 17:02:27,500method:[DefaultFilter]:[doFilter]:userAgent:Post_Multipart[202.109.207.214][INFO ] 2011-11-16 17:02:27,562 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:02:27url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 17:02:28,093 method:[LoginApply]:loginName:483752463@fzlan@w.fj ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:02:27 resultCode=0 description=请求成功[INFO ] 2011-11-16 17:02:28,093 method:{password=j99ume, userName=483752463@fzlan, pro=null, loginName=483752463@fzlan@w.fj, ipAddr=202.109.207.214,provinceCode=w.fj}=>null;0;请求成功[INFO ] 2011-11-16 17:04:17,812method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 17:04:17,812method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214[ERROR] 2011-11-16 17:04:17,812method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214&remoteAddr=202.109.207.214 [INFO ] 2011-11-16 17:04:17,828method:[PhoneLogoutAction]:[execute]:loginName=483752463@fzlan@w.fj[INFO ] 2011-11-16 17:04:17,828method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214[ERROR] 2011-11-16 17:04:17,828method:[PhoneLogoutAction]:[execute]:ipAddr=202.109.207.214&remoteAddr=202.109.207.214[INFO ] 2011-11-16 17:04:17,906 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:04:17url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 17:04:17,906 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:04:17url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 17:04:18,515 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:04:17 resultCode=0 description=BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 17:04:18,640method:[DefaultFilter]:[doFilter]:userAgent:Post_Multipart[202.109.207.214][INFO ] 2011-11-16 17:04:21,171 method:[LogoutApply]:ipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:04:17 resultCode=0 description=BAS设备告诉PortalServer此用户下线成功[INFO ] 2011-11-16 17:05:10,828 method:[loginV3]:userName:1234577 provinceCode:w.fj loginName:1234577@w.fj ipAddr:202.109.207.214LoginActionV3[INFO ] 2011-11-16 17:05:10,828method:[DefaultFilter]:[doFilter]:userAgent:Post_Multipart[202.109.207.214][INFO ] 2011-11-16 17:05:10,953 method:[LoginApply]:loginName:1234577@w.fjipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:05:10url=http://202.109.207.166:8080/FjPortal/services/PortalServices[INFO ] 2011-11-16 17:05:11,234 method:[LoginApply]:loginName:1234577@w.fjipAddr:202.109.207.214RemoteClientPortalManager timeStamp=2011-11-16 17:05:10 resultCode=44 description=BAS设备告诉PortalServer此用户认证失败(发生错误) [INFO ] 2011-11-16 17:05:11,234 method:{password=1234566, userName=1234577, pro=null, loginName=1234577@w.fj, ipAddr=202.109.207.214, provinceCode=w.fj}=>null;44;BAS设备告诉PortalServer此用户认证失败(发生错误)。
Portal技术概述

Portal技术概述引言Portal现在已经成为企业最关注的领域之一,是实现企业整合的第一步。
其重要价值在于它是企业现有投资与新投资的集成节点,使用户能够与人、内容、应用和流程进行个性化的、安全的、单点式的互动交流。
对企业来说,建立Portal的意义在于可以使员工共享各种系统和信息资源,并对其进行统一的管理。
对员工来说,通过Portal 可以了解和掌握有关企业的各种信息、参加讨论、协同工作等。
Portal 自动将分散于企业各处的信息资源整理并发送给员工,真正实现信息找人的目的。
企业信息化的主要内容涵盖了产品的信息化、产品设计制造的信息化、生产组织信息化和管理与决策信息化等多个方面。
针对不同的信息化工作,企业门户的建立也各有差异。
企业信息化工作从最初的办公自动化(OA)、企业局域网(LAN)、企业广域网(W AN)、管理信息系统(MIS)、企业内部网和Web网站的建设阶段一路发展至今,开始进入电子商务(Ebusiness)时代。
信息门户集中了IT领域的诸多概念,如商务智能(BI,business intelligence)和文档管理(DM,document management)等,是信息化工作的融合和发展。
1.1什么是Portal?Portal 是能提供以下功能的,基于Web技术的,针对具体用户或社区的应用平台:1.用户可通过统一平台享受不同服务和操作不同应用2.协同工作与社区服务3.把整合好的内容个性化地传给终端用户信息分类协作应用集成个性化1.1.1为什么需要Portal?随着中国入世和知识经济的到来,经济全球化与市场需求的多样化、个性化对企业提出了更高的要求。
如何对市场环境的急剧变化和顾客需求的瞬息万变做出灵活、快捷的响应,及时地把握顾客的需求,有效地组织生产和提供令顾客满意的产品和服务成为企业生存与发展的基本前提。
传统的信息系统让用户头痛的是:–有太多的没有集成在一起的系统需要访问–常常为了一个结果,就需要访问多个系统–为了得到结果,要花很长的时间–由于信息的分散,常常错过一些重要的信息–有太多的用户名和口令需要牢记–很难管理多个系统的用户等等Portal为企业提供了一个单一的访问企业各种信息资源的入口,将企业的应用、人员、信息与流程有机地结合起来,为信息化工作的开展提供了可行的思路和解决方案。
ARUBA AC实验(PSK、PORTAL、MAC和802.1X认证)

ARUBA AC实验(PSK、PORTAL、MAC和802.1X认证)2020-4-27作者:J|NQQ:342774473Aruba AC实验(PSK、PORTAL、MAC和802.1X认证)一、实验拓扑图二、无线控制器初始化配置三、 电脑设置手动IP 与无线控制器互联。
四、增加VLAN、无线控制器管理IP(192.168.53.107)和IPSET认证允许。
五、添加192.168.53.250默认路由。
六、添加VLAN默认网关七、添加DHCP服务器和网段八、新建无线组(HM和ZP)九、新建Guest无线配置文件(PSK+PORTAL认证VLAN10)9.1新建Guest角色配置9.2新建Guest AAA配置9.3新建Gues VAP配置9.4在VAP配置增加Guest 无线SSID9.5关联Guest VAP 无线VLAN9.6添加vlan nat 访问外网9.8添加Potal认证关联9.9建立内部用户测试Portal认证。
9.10设置Portal认证跳转页面和自动跳转时间十、新建Staff无线配置文件(802.1X认证VLAN20)10.1新建Staff角色配置10.2添加Radius服务器和Radius组10.3添加L2 802.1X配置文件10.4添加Staff AAA配置10.5添加VLAN NAT10.6新建Staff VAP 文件10.7新建Staff VAP 的SSID文件10.8关联Staff无线VLAN十一、新建VIP无线配置文件(MAC+PORTAL认证VLAN30)11.1新建VIP角色配置11.2新建VIP AAA配置11.3新建VIP VAP配置11.4新建VIP SSID配置11.5新建VLAN NAT11.6绑定电脑MAC地址11.6新建和绑定VIP角色PORTAL文件十二、新建Fasion无线配置文件(802.1X认证VLAN40)12.1新建Fasion角色文件12.2新建Fashion AAA配置12.3新建Fash VAP配置12.4新建Fashion SSID 配置12.5关联Fasion VLAN12.6添加Fasion VLAN NAT。
portal实验报告

目录一、实验拓扑 (2)二、实验需求 (2)三、实验步骤 (2)3.1.中间设备的配置 (2)3.2.IMC侧的配置 (4)四、实验测试 (15)一、实验拓扑二、实验需求如上图所示,用户通过DHCP自动获取地址,在中间设备和IMC服务器上做portal相关的配置,然后使得用户只有通过portal验证才可以正常访问相应的资源。
三、实验步骤3.1.中间设备的配置首先配置DHCP的:dhcp enabledhcp server ip-pool zrcgateway-list 192.168.1.1network 192.168.1.0 mask 255.255.255.0配置和IMC直连接口地址:interface Vlan-interface1ip address 10.88.142.221 255.255.254.0配置和用户侧直连的接口配置(地址以及portal相关配置):interface Vlan-interface2ip address 192.168.1.1 255.255.255.0portal enable method directportal domain zrcportal bas-ip 192.168.1.1portal apply web-server zrc将端口加入对应vlan:interface GigabitEthernet1/0/9port access vlan 2配置radius:radius session-control enableradius scheme zrcprimary authentication 10.88.142.171primary accounting 10.88.142.171key authentication cipher $c$3$g5++h5a3butLOgV9BBRAmQ9jrMWTLQ== key accounting cipher $c$3$mT2KHXDYm8uFW/tC5ShdhfQZIFCl+w== user-name-format without-domain配置验证域,调用radius方案:domainzrcauthentication portal radius-scheme zrcauthorization portal radius-scheme zrcaccounting portal radius-scheme zrc配置portal的web地址:portal web-server zrcurl 10.88.142.171:8080/portal配置portal server:portal server zrcip 10.88.142.171 key cipher $c$3$lhtCedxy1dqpYaqavy8ByOIi/P9ymg==3.2.IMC侧的配置首先配置一个接入设备:用户-----接入策略管理-----接入设备管理------接入设备配置点击增加,增加一台设备:点手工增加这里设置共享密钥为zrc之后确认。
直接portal认证实验总结

无线直接portal认证1.组网需求●用户通过无线SSID接入,根据业务需求,接入用户通过vlan20、vlan30和vlan40,3个网段接入,AP管理地址使用vlan10网段,所有网关在AC上,并且通过AC上的DHCP 获取地址。
●用户接入时需要启用portal认证。
2.组网图3.配置思路●在WX3024E上配置portal功能●配置IMC服务器4.配置信息●AC配置如下:[H3C_AC-1]disp cu#version 5.20, Release 3507P18#sysname H3C_AC-1#domain default enable h3c#telnet server enable#port-security enable#portal server imc ip 192.168.1.11 key cipher $c$3$JE7u4JeHMC5L06LL4Jl1jaJZB0f86sEz url http://192.168.1.11:8080/portal server-type imc#oap management-ip 192.168.0.101 slot 0#password-recovery enable#vlan 1#vlan 10description to_AP#vlan 20description _User#vlan 30description to_User#vlan 40description to_User#vlan 100description to_IMC#vlan 1000description to_Router#radius scheme imcserver-type extendedprimary authentication 192.168.1.11primary accounting 192.168.1.11key authentication cipher $c$3$q+rBITlcE79qH12EH3xe3Rc8Nj/fcVy1key accounting cipher $c$3$Uiv1821RWnPK4Mi2fIzd29DJ6yKvp38inas-ip 192.168.1.254#domain h3cauthentication portal radius-scheme imcauthorization portal radius-scheme imcaccounting portal radius-scheme imcaccess-limit disablestate activeidle-cut disableself-service-url disabledomain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#dhcp server ip-pool vlan10network 192.168.10.0 mask 255.255.255.0gateway-list 192.168.10.254dns-list 8.8.8.8option 43 hex 80070000 01C0A80A FE#dhcp server ip-pool vlan20network 172.16.20.0 mask 255.255.255.0gateway-list 172.16.20.254dns-list 8.8.8.8#dhcp server ip-pool vlan30network 172.16.30.0 mask 255.255.255.0gateway-list 172.16.30.254dns-list 8.8.8.8#dhcp server ip-pool vlan40network 172.16.40.0 mask 255.255.255.0gateway-list 172.16.40.254dns-list 8.8.8.8#user-group systemgroup-attribute allow-guest#local-user adminpassword cipher $c$3$v9m2UEc3AWP3KbkKm480OAgOcpMkD0pD authorization-attribute level 3service-type telnet#wlan rrmdot11a mandatory-rate 6 12 24dot11a supported-rate 9 18 36 48 54dot11b mandatory-rate 1 2dot11b supported-rate 5.5 11dot11g mandatory-rate 1 2 5.5 11dot11g supported-rate 6 9 12 18 24 36 48 54 #wlan service-template 1 cryptossid H3C-VLAN20bind WLAN-ESS 20cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan service-template 2 cryptossid H3C-VLAN30bind WLAN-ESS 30cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan service-template 3 cryptossid H3C-VLAN40bind WLAN-ESS 40cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan ap-group default_groupap ap1#interface Bridge-Aggregation1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 #interface NULL0#interface Vlan-interface1ip address 192.168.0.100 255.255.255.0#interface Vlan-interface10description to_Userip address 192.168.10.254 255.255.255.0#interface Vlan-interface20description to_Userip address 172.16.20.254 255.255.255.0portal server imc method direct#interface Vlan-interface30description to_Userip address 172.16.30.254 255.255.255.0#interface Vlan-interface40description to_User_vlan40ip address 172.16.40.254 255.255.255.0#interface Vlan-interface100description to_IMCip address 192.168.1.254 255.255.255.0#interface Vlan-interface1000description to_Routerip address 10.1.1.2 255.255.255.252#interface GigabitEthernet1/0/1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000port link-aggregation group 1#interface GigabitEthernet1/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000port link-aggregation group 1#interface WLAN-ESS20port access vlan 20port-security port-mode pskport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678 #interface WLAN-ESS30port access vlan 30port-security port-mode pskport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678#interface WLAN-ESS40port access vlan 40ort-security port-mode pskpport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678 wlan ap ap1 model WA3620i-AGN id 1serial-id 210235A1BBC146000073radio 1service-template 1service-template 2service-template 3radio enableradio 2channel 6service-template 1service-template 2service-template 3radio enable#ip route-static 0.0.0.0 0.0.0.0 10.1.1.1#wlan ipsmalformed-detect-policy defaultsignature deauth_flood signature-id 1signature broadcast_deauth_flood signature-id 2 signature disassoc_flood signature-id 3 signature broadcast_disassoc_flood signature-id 4 signature eapol_logoff_flood signature-id 5 signature eap_success_flood signature-id 6 signature eap_failure_flood signature-id 7 signature pspoll_flood signature-id 8signature cts_flood signature-id 9signature rts_flood signature-id 10signature addba_req_flood signature-id 11 signature-policy defaultcountermeasure-policy defaultattack-detect-policy defaultvirtual-security-domain defaultattack-detect-policy defaultmalformed-detect-policy defaultsignature-policy defaultcountermeasure-policy default#dhcp server forbidden-ip 192.168.10.254 dhcp server forbidden-ip 172.16.20.254 dhcp server forbidden-ip 172.16.30.254 dhcp server forbidden-ip 172.16.40.254 #dhcp enable#user-interface con 0user-interface vty 0 4authentication-mode schemeuser privilege level 3#return交换机配置如下<H3C-SW01>disp cu#version 5.20, Release 3507P18#sysname H3C-SW01#domain default enable system#telnet server enable#oap management-ip 192.168.0.100 slot 1 #password-recovery enable#vlan 1#vlan 10description to_AP#vlan 20description to_User-vlan20#vlan 30description to_User-vlan30#vlan 40description to_User-vlan40#vlan 100description to_IMC#vlan 1000description to_Router#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#user-group system#local-user adminpassword cipher $c$3$078okxl+RPQFofPe76YXbYryBRI3uMKv authorization-attribute level 3service-type telnet#interface Bridge-Aggregation1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000#interface NULL0#interface Vlan-interface1ip address 192.168.0.101 255.255.255.0#interface GigabitEthernet1/0/1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 20 30 40port trunk pvid vlan 10poe enable#interface GigabitEthernet1/0/2port access vlan 100poe enable#interface GigabitEthernet1/0/3port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 1000poe enable#interface GigabitEthernet1/0/4 poe enable#interface GigabitEthernet1/0/5 poe enable#interface GigabitEthernet1/0/6 poe enable#interface GigabitEthernet1/0/7 poe enable#interface GigabitEthernet1/0/8 poe enable#interface GigabitEthernet1/0/9 poe enable#interface GigabitEthernet1/0/10 poe enable#interface GigabitEthernet1/0/11 poe enable#interface GigabitEthernet1/0/12 poe enable#interface GigabitEthernet1/0/13 poe enable#interface GigabitEthernet1/0/14 poe enable#interface GigabitEthernet1/0/15 poe enable#interface GigabitEthernet1/0/16 poe enable#interface GigabitEthernet1/0/17 poe enable#interface GigabitEthernet1/0/18poe enable#interface GigabitEthernet1/0/19poe enable#interface GigabitEthernet1/0/20poe enable#interface GigabitEthernet1/0/21poe enable#interface GigabitEthernet1/0/22poe enable#interface GigabitEthernet1/0/23poe enable#interface GigabitEthernet1/0/24poe enable#interface GigabitEthernet1/0/25shutdown#interface GigabitEthernet1/0/26shutdown#interface GigabitEthernet1/0/27shutdown#interface GigabitEthernet1/0/28shutdown#interface GigabitEthernet1/0/29port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 port link-aggregation group 1#interface GigabitEthernet1/0/30port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 port link-aggregation group 1#user-interface aux 0user-interface vty 0 4authentication-mode schemeuser-interface vty 5 15#Return5.IMC配置:配置接入设备:在导航栏中选择“用户->接入策略管理->接入设备管理->接入设备配置”,点击<增加>按钮。
浅谈WLAN运营中Portal认证安全性

浅谈WLAN运营中Portal认证安全性WLAN运营有多种认证方式,但最常用的方式为弹出Portal登录页面。
即:用户搜索到运营商的AP后,连接进去获得IP地址,打开浏览器,输入账号和密码便可登录,如下图展示的是Saiver的热点登录界面:这种方式虽然简单方便,但由于AP的接入没有采用WEP和WPA2等加密方式,空中信道很容易被侦查破解,黑客能够截获空中传输的账号和密码。
因此直接采用该方式安全性较低。
如何提高登录页面的安全性呢?目前大部分WLAN运营商采用以下几种辅助方案:1.Portal服务器与NAS和Radius服务器采用CHAP的认证方式2.HTTPS的登录页面方式3.手机短信获得动态密码的方式下面对这三种方式进行论述与比较。
1.方案1的认证方式最为简单实用,也非常安全。
其中Radius标准提供了两种可选的身份认证方法:口令验证协议PAP(PasswordAuthenticationProtocol,PAP)和质询握手协议(ChallengeHandshake Authentication Protocol,CHAP)。
如果双方协商达成一致,也可以不使用任何身份认证方法。
质询握手协议认证(CHAP)相比口令验证协议认证(PAP)安全性更高,因为CHAP不在线路上发送明文密码,而是发送经过摘要算法加工过的随机序列,也被称为"挑战字符串".处理算法和过程如下图所示。
与此同时,身份认证可以随时进行,包括在双方正常通信过程中。
因此,这种方式下传输的密码具有时效性。
采用PAP的认证方式,密码是明码或者采用可逆算法传输,而且可以通过查看登录页面的源代码查到加密的算法,因此可以很容易地找到破解的算法。
而CHAP采用MD5的加密方式是不可逆的,算法是公开的,也就是说侦听者无法从加密后的结果去反算出密码,在整个认证过程中的只有Radiusserver和用户知道密码,包括BRAS 等接入设备也只是传输MD5加密后的结果,加密采用一个挑战值的方式,每次认证都不一样,加密的结果也是每次不同,即使被黑客获得,也会在下一次认证时失效。
PLC1200实验报告
输入输出
起动按钮:I0.0南北红灯:Q0.0东西红灯:Q0.3
南北黄灯:Q0.1东西黄灯:Q0.4
南北绿灯:Q0.2东西绿灯:Q0.5
南北车灯(乙):Q0.6东西车灯(甲):Q0.7
3.按图所示的梯形图输入程序。
4.调试并运行程序。
三、交通灯控制梯形图
2,绘制梯形图
回到portal视图,选择PLC编程
基本逻辑指令
3,转到在线
选择后显示“在线连接”,接口类型选择PG/PC,开始搜索
将程序块下载到设备,并“启动CPU”
观察结果
实验三S7-1200PLC定时器计数器的应用
实验目的:掌握s7-1200中定时器计数器的应用并完成相应程序
实验设备:同上
实验原理:
画出梯形图及时序图
3计数器的用法:
S7-1200有3种计数器:加计数器(CTU)、减计数器(CTD)和加减计数器(CTUD)。它们属于软件计数器,其最大计数速率受到它所在的OB的执行速率的限制。
如果需要速率更高的计数器,可以使用CPU内置的高速计数器。
调用计数器指令时,ຫໍສະໝຸດ 要生成保存计数器数据的背景数据块。
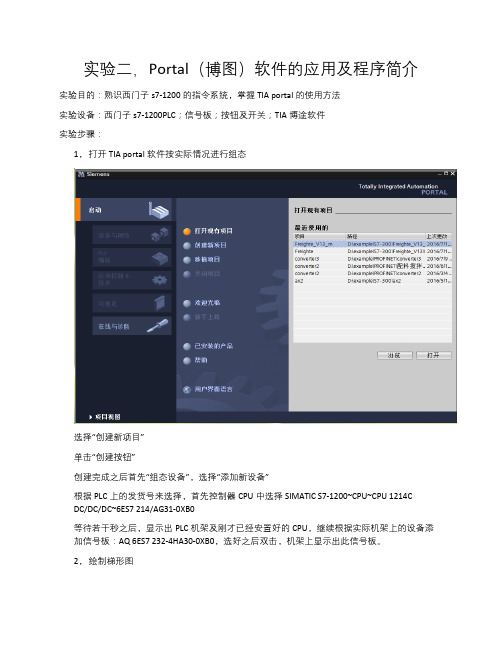
根据PLC上的发货号来选择,首先控制器CPU中选择SIMATIC S7-1200~CPU~CPU 1214C DC/DC/DC~6ES7 214/AG31-0XB0
等待若干秒之后,显示出PLC机架及刚才已经安置好的CPU,继续根据实际机架上的设备添加信号板:AQ 6ES7 232-4HA30-0XB0,选好之后双击,机架上显示出此信号板。
●RT:通过清除存储在指定定时器背景数据块中的时间数据来重置定时器。
每个定时器都使用一个存储在数据块中的结构来保存定时器数据。在编辑器中放置定时器指令时可分配该数据块。
IMC的portal认证测试方案

鉴于IMC与7506E之portal认证(测试方案)---------Ring组网图(二层)iMC配置以下配置均以V3.60-E6301版本为例,以系统管理员admin的权限登录iMC配置台(%iMCIP%:8000/imc,如http://192.168.1.10:8000/imc/ ),缺省密码为admin。
//解释:当时主要是在装服务器的时候system占用了8080端口,不过这个是不影响接下来的IMC的环境搭建好以后WEB站点的访问,但是有一点要注意就是1812(认证)和1813(计费)号端口是千万不能够占用的。
我在安装的时候就有出现该两个端口占用的情况(解决办法是直接在控制面板上添加删除Windows组件将除了IMC需要的IIS 服务保留以外其他服务全部删除如以后有需要再开启某个服务然后重启服务器)。
IMC登录界面:在做portal认证之前需要先做EAD安全策略以备以后再修改服务时时关联使用(这是在做portal认证之前需要做的事情很重要)增加SNMP协议增加telnet协议1.Portal配置创建portal地址组,这个地址组需包括所有认证客户端的IP地址,但注意要排除S7506E 的地址和portal服务器的地址。
//此处的ip地址组名是看情况而定添加portal设备这个IP地址必须配置为启用portal认证的接口地址。
在某些设备的新版本中,可以通过portal nas-ip命令指定这个地址(指着是IMC的ip地址),但如果没有配置或者设备不支持该命令的情况下,必须配置为启用portal认证的接口地址,在本例中就是192.168.7.1。
配置端口组信息管理将刚才定义的IP地址组加入进来。
2.配置“服务”配置服务3.账号开户,申请定义好的服务增加用户为用户添加账号添加账号及密码成功4.增加接入设备增加了一个接入设备,若交换机上有多个地址,优先填写上行口地址。
手动将配置生效生效成功,基本配置至此完毕,可以用在客户端进行测试了。
portal认证学习小结

portal认证学习小结portal简介portal是用来进行网页认证的认证机制,在认证成功前用户不能真正上网,只能查看到portal server的页面,如图:访问任何页面都会被强制转换到如图所示的portal 页面,需要手动输入用户名和密码后才能够正常上网。
Portal的优点是用户不需要安装专门的客户端就可以直接进行认证和上网。
Portal协议流程Portal认证拓扑图如下:认证流程如下:如图:1,首先wlan用户上网,AC侦测到http连接后,强制发送http重定向报文给wlan用户2,Wlan用户接收到重定向报文后,按照重定向报文提供的目的IP地址访问portal 服务器,推送出认证页面3,用户通过认证界面,输入用户名密码给portal server4,Portal server向AC发送需要认证用户的用户名5,AC向portal server发送认证挑战6,Portal server回应认证挑战7,AC向radius发起认证8,如果认证成功,则AC把认证成功信息发送给portal服务器,推送出认证成功界面,同时AC上下发规则,认证成功。
下面按照一次实际抓包来分析一次实际认证过程:如上抓图,分别为从AC端口的抓包和从PC端口的抓包1,首先在PC的IE上数据url地址后,pc发起http访问,该访问被AC连接,并直接返回重定向报文:http 302报文给PC,把pc直接重定向到portal server上去,如图:2,然后PC根据http的重定向信息向portal server发起请求并获得认证页面,在认证页面中输入用户名密码后进行认证。
整个过程对于AC来说和普通IP包的处理是相同的,由于实现配置了portal server的IP 地址在白名单中,所以AC对这次访问不进行阻止,按照普通的IP包进行处理使用tcp.port eq 7080作为过滤条件可以看到pc和portal server交互的整个过程3,portal server得到用户名和密码后开始和AC联系,出发AC进行portal认证,如图:Portal协议根据移动规定采用的是udp的2000端口进行认证的具体的数据包分析如下第一个包:如图,portal server向AC发送认证请求,数据包的类型为01,表示为认证请求报文。
传送门2——portal深度分析与和hl关系谈

传送门2——portal深度分析与和hl关系谈 ⼀、关于P O RTA L游戏 p o r t a l这个游戏是第⼀⼈称纯解谜类的游戏,游戏中玩家扮演⼀名叫做C h e l l的⼥性,在⼀个叫做g l A D O S的智能机器⼈的引导下,不断破关并且探索整个A p e r t u r e L a b o r a t o r i e s光圈实验室的真相。
p o r t a l⼀经发售便受到了全球玩家的好评。
⼀般资格⽐较⽼的游戏玩家都知道,这类游戏在市场上是相当罕见的。
谈到“第⼀⼈称”,我们⾸先想到的就是使命召唤,反恐精英等这些射击游戏⼤作,但是Va l v e希望突破这样⼀个局限,于是独具特⾊的p o r t a l传送门风格就诞⽣了。
玩家的好评,笔者认为原因就在于以下本游戏⼏个特别出彩的地⽅。
⾸先,p o r t a l⼤部分关卡的主⾊调采⽤的都是⽩⾊以及少许的浅蓝⾊,不难理解,⽩⾊象征着纯洁,浅蓝⾊能够让⼈联想到⼤海和⽔,⽣命的起源地。
主⾊调能够充分地让玩家享受祥和和安全的⽓氛。
其⼆,p o r t a l的⼤部分关卡极度规则化,玩家在引导下能够产⽣对游戏世界的强烈可控感。
在⼤部分关卡中,游戏仅仅⽤到了圆形,椭圆(主要是传送门),⽴⽅体,长⽅体,以及⼀些简单的组合,没有其他复杂的多边形或者⾼级贴图等。
并且地图⽅⾯,实验室中的事物屈指可数。
完全⼀模⼀样的电梯,光球发射机,⽅块掉落器,防弹玻璃,监视器,⼩收⾳机,双扇门,移动平台,升降平台等。
破关⽅法⽅⾯,⽆⾮就是使⽤⽅块压住门的开关,或者把光球引导到接收器上⾯去,这两种⽅式。
P o r t a l极度规则化的游戏世界给解谜提供了充⾜和灵活的元素。
其三,玩家⼿持的传送门设备也起到了⾮常⼤的作⽤。
在⼤多数的解谜游戏中,玩家都是通过⾛路,奔跑,飞⾏,跳跃等复杂的⼀系列动作来探索关卡,然⽽p o r t a l则给予了玩家⼀种⾮常便捷的瞬间移动的⽅式。
portal认证故障排查

版权所有:杭州华三通信技术有限公司portal认证故障排查一、开始定位故障的思路是:以Portal认证流程为排查方向,先确保终端正常获取IP地址及DNS解析正常,然后查看终端Web页面是否可以重定向成功,再查看设备侧Portal、PortalServer相关状态是否正常,最后查看客户端、Server上记录的下线原因及设备上的相关Log。
1、检查Portal、AAA、Domain等配置检查Portal、AAA、Domain等配置,各部分注意事项如下:Portal 部分:在全局配置Portal Server且在三层接口下使能Portal认证。
例如:通过当前配置可确认在全局配置的Portal1中使能了Portal认证。
Server为6.6.6.6且在vlan配置Radius Scheme认证方案,指定认证、计费服务器。
配置Nas-Ip且保证Nas-Ip到认证、计费服务器可达。
同时保证User-Name-Format和Server-Type与Radius Server匹配。
例如:通过当前配置可知Radius Scheme的Server-Type为Extended,User-Name-Format为Without-Domain。
认证计费Server都为1.1.1.1。
版权所有:杭州华三通信技术有限公司Domain部分:在Domain视图下引用相应的RadiusScheme方案,认证授权方案必须同时指定。
例如:通过当前配置可知,Domain下引用的Radius Scheme方案为h3c 。
2、确保终端正常获取IP地址且DNS解析成功Portal根据终端发送的HTTP报文来进行重定向,必须确保终端在认证前通过D HCP或者静态配置的方式获取到正确的IP地址且DNS解析成功,这样浏览器才可以正常发送HTTP版权所有:杭州华三通信技术有限公司报文。
3、推送认证页面是否成功在浏览器中访问任意网站,设备都会将其重定向至认证页面。
portal认证系统服务器原理及应用

portal认证系统服务器原理及应用Portal认证方式具有:不需要安装认证客户端,减少客户端的维护工作量、;便于运营,可以在Portal页面上开展业务拓展、技术成熟等优点而被广泛应用于运营商、学校等网络。
目前在公共场合也有很多的WIFI热点.WIFI本身不加密,但是当用户访问网络的时候,会要求用户输入用户名和密码.认证成功后就可以上网了.WEB认证的特点显而易见,就是不需要特殊的客户端,有浏览器就可以了.所以,手机也可以方面的使用.下图是WEB认证的原理图(CHAP认证):本文所要描述的就是PortalServer的原理与算法.PortalServer 和BAS 之间的通讯遵循华为的PORTAL v1.0协议.以下是协议格式:以下是部分源代码和说明.typedef struct portal_header{u_int8_t ver; //版本,在本例中为1u_int8_t type; //报文类型u_int8_t auth_type; //认证类型,CHAP或者PHP,本文为CHAP协议u_int8_t rsv; //保留字段,恒为零u_int16_t sn; //序列号,用于关联报文用,在一定时间是不能重复的u_int16_t reqid; //应答IDu_int32_t userip; //用户的IPu_int16_t userport; //用户端口,恒为零u_int8_t errcode; //错误码,非常有用的字段u_int8_t attrnum; //属性个数}portal_header_t;定义了PORTAL协议的协议头.如果属性个数不为零,那么后面将跟attrnum个属性.以下是构造挑战报文的代码:sn=(u_int16_t)(1+(int)(9098.0*rand()/(RAND_MAX+1.0))); //随机码req_chap->ver=ver;req_chap->type=REQ_CHALLENGE;req_chap->auth_type=CHAP;req_chap->rsv=0x00;req_chap->sn=sn;req_chap->reqid=0x00;;req_chap->userip = in->s_addr; //客户的IPreq_chap->userport=0x0;req_chap->errcode=0x0;req_chap->attrnum=0x0;当收到了type为0x02的报文,并且errcode=0x00时,说明挑战成功.接下来就可以发送认证请求报文了,以下是构造请求报文的代码: (ra->header).ver = 0x01;(ra->header).type=REQ_AUTH;(ra->header).auth_type=CHAP;(ra->header).rsv=0x00;(ra->header).sn= //新的随机码(ra->header).reqid = req_chap->reqid;(ra->header).userip = req_chap->userip;(ra->header).userport=0x0;(ra->header).errcode=0x0;(ra->header).attrnum=0x2;这个请求报文带两个属性.关键的CHAP密码构造代码如下:MD5_Init(&ctx);MD5_Update(&ctx, &reqid, 1);MD5_Update(&ctx, passwd, strlen(passwd));MD5_Update(&ctx, challenge, 16);MD5_Final(d3, &ctx);如果收到CHAP应答报文,错误代码为零的话,就说明认证成功了.本程序的使用命令如下:cr ver protocol basip username password client_ipver 协议版本,本文只实现了V1protocol CHAP 或者PAP ,本文只实现了CHAP,PAP实现起来更简单.basip BAS的ip ,就是报文发送到的设备IPusername 从WEB过来的用户名password 从WEB PORTAL 过来的密码client_ip 客户的IP地址蓝海卓越Web Portal的组网方式通常如下:蓝海卓越Web Portal的基本认证过程为:(1)用户连接到网络后,终端通过DHCP由BAS做DHCP-Relay,向DHCP Server要IP地址(私网或公网);(也可能由BAS直接做DHCP Server)。
(完整版)portal认证介绍

Portal认证技术认证技术是AAA(认证,授权,计费)的初始步骤,AAA一般包括用户终端、AAAClient、AAA Server和计费软件四个环节。
用户终端与AAA Client之间的通信方式通常称为"认证方式"。
目前的主要技术有以下三种:PPPoE、Web+Portal、IEEE802.1x。
基于web方式的认证技术最广为人知的一点是不需要在客户端安装任何拨号与认证软件。
它能够处理高层协议,在网络应用日益复杂的形势下,很多复杂的管理要求已经涉及到高层协议,面对这些要求,基于2、3层的认证技术入PPPoE,802.1x就无能为力。
1.PPPoE通过PPPoE(Point-to-Point Protocol over Ethernet)协议,服务提供商可以在以太网上实现PPP协议的主要功能,包括采用各种灵活的方式管理用户。
PPPoE(Point-to-Point Protocol over Ethernet)协议允许通过一个连接客户的简单以太网桥启动一个PPP对话。
PPPoE的建立需要两个阶段,分别是搜寻阶段(Discovery stage)和点对点对话阶段(PPP Session stage)。
当一台主机希望启动一个PPPoE对话,它首先必须完成搜寻阶段以确定对端的以太网MAC地址,并建立一个PPPoE的对话号(SESSION_ID)。
在PPP协议定义了一个端对端的关系时,搜寻阶段是一个客户-服务器的关系。
在搜寻阶段的进程中,主机(客户端)搜寻并发现一个网络设备(服务器端)。
在网络拓扑中,主机能与之通信的可能有不只一个网络设备。
在搜寻阶段,主机可以发现所有的网络设备但只能选择一个。
当搜索阶段顺利完成,主机和网络设备将拥有能够建立PPPoE的所有信息。
搜索阶段将在点对点对话建立之前一直存在。
一旦点对点对话建立,主机和网络设备都必须为点对点对话阶段虚拟接口提供资源(1)PPPoE方式其整个通信过程都必须进行PPPoE封装,效率较低,由于宽带接入服务器要终结大量的PPP会话,将其转换为IP数据包,使宽带接入服务器成为网络性能的“瓶颈”。
局域网Portal认证研究及应用

会提供一些 内部关键 资源给外部用户访 问, 并且希 望 经过 有 效认 证 的用 户才 可 以访 问这 些资 源 。
现有 的 82 1 0 .x和 P PE等访 问控 制 方式 , Po 都需
要 客户 端 的配 合 , 且 只 能 在 接 人层 对 用户 的访 问 并 进 行控 制 。P r l 证 技 术 则 提 供 一 种灵 活 的访 问 ot 认 a 控 制方 式 , 不需 要安 装 客户 端 , 可 以在 接 人层 以及 就 需 要保 护 的关键 数据 人 口处 实 施访 问控 制 。
2 P r l 能 特 点 ot 功 a
2 1 不 需要 安装 客户 端软件 . 相对 于其 他 的认 证 方 式 , oa 认 证 通 过 网 页 Pr l t 即可 实 现认证 , 需 安 装 客 户端 。不 但 减少 了用 户 无 机 器 的 负担 , 而且 方便 了上 网用户 的使 用 , 同时 管理 者 也 不用 逐一 为每 个上 网用户 安装 和升级 客户端 软 件 , 大减 轻 管理难 度 。 极
理并对其 实施方案进行 了初 步探索 。 关键词 :otl P r 认证 ; a 局域 网; A ;0 . x; A; B S 82 1 从 复合查询 中图分 类号 :P 3 T 19
在传统的组网环境 中, 用户 只要能接人局域 网 设 备 , 可 以访 问 网络 中 的设 备 或 资源 , 就 为加 强 网络
户 的访 问进行 控制 。例 如 , 一 些公 共场 合 、 区或 在 小 公 司的 网络接 人 点 , 供 接 入 服 务 的供 应 商 希 望 只 提
允许付费的合法用户接 人 , 以供应商为每个用户 所
portal认证的优势 试题

portal认证的优势试题
Portal认证的优势有很多,我会从多个角度来回答这个问题。
首先,Portal认证可以提供统一的身份验证和访问控制。
通过Portal认证,用户可以使用单一的身份验证信息(如用户名和密码)来访问多个不同的应用程序和资源。
这样可以简化用户的登录流程,提高用户体验,同时也方便了管理员对用户身份进行统一管理和控制。
其次,Portal认证可以增强安全性。
通过Portal认证,管理
员可以实施多种身份验证机制,如双因素身份验证、单点登录等,
从而提高系统的安全性,减少身份盗用和信息泄露的风险。
此外,Portal认证还可以提供个性化的用户体验。
通过Portal
认证,用户可以根据其身份和权限获得定制化的应用程序和资源访
问权限,从而提高工作效率和用户满意度。
另外,Portal认证还能够简化管理员的管理工作。
通过Portal
认证,管理员可以集中管理用户的身份和访问权限,简化用户帐户
的创建、修改和删除等操作,降低管理成本,提高管理效率。
最后,Portal认证还可以促进应用程序和资源的集成和共享。
通过Portal认证,不同的应用程序和资源可以集成到统一的门户中,实现统一的访问入口和统一的身份验证,从而促进资源的共享和协作,提高整体的工作效率。
综上所述,Portal认证的优势包括提供统一的身份验证和访问
控制、增强安全性、提供个性化的用户体验、简化管理员的管理工
作以及促进应用程序和资源的集成和共享。
这些优势使得Portal认
证成为企业和组织提高信息系统安全性和管理效率的重要工具。
Capvgynportal认证笔记

Time will pierce the surface or youth, will be on the beauty of the ditch dug a shallow groove ; Jane will eat rare!A born beauty, anything to escape his sickle sweep.-- Shakespeare Portlet学习笔记1. Portal基础1.1. 什么是Portal]s-e r d3S&j:h OPortal 一词是在Internet 的发展中提出来的,原意为“门户网站”即是人们上网后想要访问的第一个网站,例如雅虎、搜狐这类网站。
在这个阶段,Portal 还是作为一个面向广泛群体的信息平台,把人们所需要的各种信息(或者访问这类信息的途径)聚合在一起,是一个信息集中平台。
很快企业应用中也开始采用Portal 这个概念,根据Portal 在企业应用中的不同作用,业界对Portal 有着不同的定义如企业信息门户、知识门户、专业门户、应用门户等等。
随着时间的推移,业界对Portal 的定义趋向一致,也就是在JSR168 种对Portal 的定义:y I S-|{portal爱好者_ H |p.N F J hA portal is a web based application that ?commonly- provides personalization, single sign on, content aggregation from different sources and hosts the presentation layer of Information Systems. Aggregation is the action of integrating content from different sources within a web page. A portal may have sophisticated personalization features to provide customized content to users. Portal pages may have different set of portlets creating content for different users. T1Z(_1G'r o c,l从上述定义中我们可以知道Portal 是企业用户访问各种企业信息、应用的入口,如下图:oo"M].|T*U1.2. 什么是Portlet作为企业信息、应用的入口,Portal 的每个页面(Page )包含了多种不同的信息,一般来说Portal 的显示如下:K w+@h l,z9[+Ss}*^n(v YQ h d _6}1U5D上图中你可以看到有多个小窗口,每个窗口是一个独立的应用,这些窗口称之为Portlet ,一个Portal 可以看作是Portlet 的集合。
IMC portal快速认证

*红色区域为配置portal认证启用快速认证需要注意的地方UAM服务器地址为192.168.1.252,接入设备用户侧地址为192.168.30.50。
PC IP地址为192.168.30.134配置UAM服务器1. 增加接入设备选择“用户”页签。
单击导航树中的“接入策略管理> 接入设备管理> 接入设备配置”菜单项,进入接入设备配置页面,单击<增加>按钮,进入增加接入设备页面单击<手工增加>按钮,弹出手工增加接入设备窗口,输入接入设备IP地址192.168.30.50,该IP地址需要与设备配置中RADIUS scheme的NAS IP一致;(如果未配置NAS IP,则使用接入设备与UAM相连接口所在VLAN的IP地址,即192.168.1.50),即设备配置中的NAS IP为192.168.30.50。
单击<确定>按钮,返回增加接入设备页面。
公共参数只需要输入共享密钥\确认共享密钥“movie”,选择设备类型H3C(General),其他保持默认即可,认证端口和计费端口默认为1812、1813,且与设备配置保持一致。
单击<确定>按钮,增加接入设备完毕,进入结果显示页面。
点击“返回接入设备列表”链接,返回接入设备配置页面,在列表中查看新增的接入设备。
2. 增加接入策略选择“用户”页签。
单击导航树中的“接入策略管理> 接入策略管理”菜单项,进入接入策略管理页面单击<增加>按钮,进入增加接入策略页面,因为不需要任何接入控制,所以输入接入策略名“my permit”,其他参数保持默认即可单击<确定>按钮,返回接入策略管理页面,新增的接入策略显示在列表中3. 增加接入服务选择“用户”页签。
单击导航树中的“接入策略管理> 接入服务管理”菜单项,进入接入服务管理页面单击<增加>按钮,进入增加接入服务页面输入服务名“my portal”、服务后缀“portal”,缺省接入策略选择之前配置的“my permit”,其他参数保持默认即可,如果要启用快速认证勾选上Portal无感知认证(v5版本)、勾选上mac无感知认证(v7版本)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
无线直接portal认证1.组网需求●用户通过无线SSID接入,根据业务需求,接入用户通过vlan20、vlan30和vlan40,3个网段接入,AP管理地址使用vlan10网段,所有网关在AC上,并且通过AC上的DHCP 获取地址。
●用户接入时需要启用portal认证。
2.组网图3.配置思路●在WX3024E上配置portal功能●配置IMC服务器4.配置信息●AC配置如下:[H3C_AC-1]disp cu#version 5.20, Release 3507P18#sysname H3C_AC-1#domain default enable h3c#telnet server enable#port-security enable#portal server imc ip 192.168.1.11 key cipher $c$3$JE7u4JeHMC5L06LL4Jl1jaJZB0f86sEz url http://192.168.1.11:8080/portal server-type imc#oap management-ip 192.168.0.101 slot 0#password-recovery enable#vlan 1#vlan 10description to_AP#vlan 20description _User#vlan 30description to_User#vlan 40description to_User#vlan 100description to_IMC#vlan 1000description to_Router#radius scheme imcserver-type extendedprimary authentication 192.168.1.11primary accounting 192.168.1.11key authentication cipher $c$3$q+rBITlcE79qH12EH3xe3Rc8Nj/fcVy1key accounting cipher $c$3$Uiv1821RWnPK4Mi2fIzd29DJ6yKvp38inas-ip 192.168.1.254#domain h3cauthentication portal radius-scheme imcauthorization portal radius-scheme imcaccounting portal radius-scheme imcaccess-limit disablestate activeidle-cut disableself-service-url disabledomain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#dhcp server ip-pool vlan10network 192.168.10.0 mask 255.255.255.0gateway-list 192.168.10.254dns-list 8.8.8.8option 43 hex 80070000 01C0A80A FE#dhcp server ip-pool vlan20network 172.16.20.0 mask 255.255.255.0gateway-list 172.16.20.254dns-list 8.8.8.8#dhcp server ip-pool vlan30network 172.16.30.0 mask 255.255.255.0gateway-list 172.16.30.254dns-list 8.8.8.8#dhcp server ip-pool vlan40network 172.16.40.0 mask 255.255.255.0gateway-list 172.16.40.254dns-list 8.8.8.8#user-group systemgroup-attribute allow-guest#local-user adminpassword cipher $c$3$v9m2UEc3AWP3KbkKm480OAgOcpMkD0pD authorization-attribute level 3service-type telnet#wlan rrmdot11a mandatory-rate 6 12 24dot11a supported-rate 9 18 36 48 54dot11b mandatory-rate 1 2dot11b supported-rate 5.5 11dot11g mandatory-rate 1 2 5.5 11dot11g supported-rate 6 9 12 18 24 36 48 54 #wlan service-template 1 cryptossid H3C-VLAN20bind WLAN-ESS 20cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan service-template 2 cryptossid H3C-VLAN30bind WLAN-ESS 30cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan service-template 3 cryptossid H3C-VLAN40bind WLAN-ESS 40cipher-suite ccmpsecurity-ie wpaservice-template enable#wlan ap-group default_groupap ap1#interface Bridge-Aggregation1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 #interface NULL0#interface Vlan-interface1ip address 192.168.0.100 255.255.255.0#interface Vlan-interface10description to_Userip address 192.168.10.254 255.255.255.0#interface Vlan-interface20description to_Userip address 172.16.20.254 255.255.255.0portal server imc method direct#interface Vlan-interface30description to_Userip address 172.16.30.254 255.255.255.0#interface Vlan-interface40description to_User_vlan40ip address 172.16.40.254 255.255.255.0#interface Vlan-interface100description to_IMCip address 192.168.1.254 255.255.255.0#interface Vlan-interface1000description to_Routerip address 10.1.1.2 255.255.255.252#interface GigabitEthernet1/0/1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000port link-aggregation group 1#interface GigabitEthernet1/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000port link-aggregation group 1#interface WLAN-ESS20port access vlan 20port-security port-mode pskport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678 #interface WLAN-ESS30port access vlan 30port-security port-mode pskport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678#interface WLAN-ESS40port access vlan 40ort-security port-mode pskpport-security tx-key-type 11keyport-security preshared-key pass-phrase 12345678 wlan ap ap1 model WA3620i-AGN id 1serial-id 210235A1BBC146000073radio 1service-template 1service-template 2service-template 3radio enableradio 2channel 6service-template 1service-template 2service-template 3radio enable#ip route-static 0.0.0.0 0.0.0.0 10.1.1.1#wlan ipsmalformed-detect-policy defaultsignature deauth_flood signature-id 1signature broadcast_deauth_flood signature-id 2 signature disassoc_flood signature-id 3 signature broadcast_disassoc_flood signature-id 4 signature eapol_logoff_flood signature-id 5 signature eap_success_flood signature-id 6 signature eap_failure_flood signature-id 7 signature pspoll_flood signature-id 8signature cts_flood signature-id 9signature rts_flood signature-id 10signature addba_req_flood signature-id 11 signature-policy defaultcountermeasure-policy defaultattack-detect-policy defaultvirtual-security-domain defaultattack-detect-policy defaultmalformed-detect-policy defaultsignature-policy defaultcountermeasure-policy default#dhcp server forbidden-ip 192.168.10.254 dhcp server forbidden-ip 172.16.20.254 dhcp server forbidden-ip 172.16.30.254 dhcp server forbidden-ip 172.16.40.254 #dhcp enable#user-interface con 0user-interface vty 0 4authentication-mode schemeuser privilege level 3#return交换机配置如下<H3C-SW01>disp cu#version 5.20, Release 3507P18#sysname H3C-SW01#domain default enable system#telnet server enable#oap management-ip 192.168.0.100 slot 1 #password-recovery enable#vlan 1#vlan 10description to_AP#vlan 20description to_User-vlan20#vlan 30description to_User-vlan30#vlan 40description to_User-vlan40#vlan 100description to_IMC#vlan 1000description to_Router#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#user-group system#local-user adminpassword cipher $c$3$078okxl+RPQFofPe76YXbYryBRI3uMKv authorization-attribute level 3service-type telnet#interface Bridge-Aggregation1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000#interface NULL0#interface Vlan-interface1ip address 192.168.0.101 255.255.255.0#interface GigabitEthernet1/0/1port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 20 30 40port trunk pvid vlan 10poe enable#interface GigabitEthernet1/0/2port access vlan 100poe enable#interface GigabitEthernet1/0/3port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 1000poe enable#interface GigabitEthernet1/0/4 poe enable#interface GigabitEthernet1/0/5 poe enable#interface GigabitEthernet1/0/6 poe enable#interface GigabitEthernet1/0/7 poe enable#interface GigabitEthernet1/0/8 poe enable#interface GigabitEthernet1/0/9 poe enable#interface GigabitEthernet1/0/10 poe enable#interface GigabitEthernet1/0/11 poe enable#interface GigabitEthernet1/0/12 poe enable#interface GigabitEthernet1/0/13 poe enable#interface GigabitEthernet1/0/14 poe enable#interface GigabitEthernet1/0/15 poe enable#interface GigabitEthernet1/0/16 poe enable#interface GigabitEthernet1/0/17 poe enable#interface GigabitEthernet1/0/18poe enable#interface GigabitEthernet1/0/19poe enable#interface GigabitEthernet1/0/20poe enable#interface GigabitEthernet1/0/21poe enable#interface GigabitEthernet1/0/22poe enable#interface GigabitEthernet1/0/23poe enable#interface GigabitEthernet1/0/24poe enable#interface GigabitEthernet1/0/25shutdown#interface GigabitEthernet1/0/26shutdown#interface GigabitEthernet1/0/27shutdown#interface GigabitEthernet1/0/28shutdown#interface GigabitEthernet1/0/29port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 port link-aggregation group 1#interface GigabitEthernet1/0/30port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 10 20 30 40 100 1000 port link-aggregation group 1#user-interface aux 0user-interface vty 0 4authentication-mode schemeuser-interface vty 5 15#Return5.IMC配置:配置接入设备:在导航栏中选择“用户->接入策略管理->接入设备管理->接入设备配置”,点击<增加>按钮。
