1_system characterization
systemrdl语法

systemrdl语法systemrdl是一种硬件描述语言,用于描述和设计数字系统的行为和结构。
本文将介绍systemrdl语法的主要特点和用法,并通过示例来展示其实际应用。
一、systemrdl语法的基本结构和语句systemrdl语法采用层次结构,可以描述整个数字系统的层级关系。
该语法主要由以下几个元素组成:1. 模块(Module):是systemrdl语法的最顶层结构,用于描述一个完整的数字系统。
一个模块可以包含多个寄存器(Register)和字段(Field)。
2. 寄存器(Register):用于描述数字系统中的寄存器。
每个寄存器可以包含多个字段,用于存储和操作数据。
3. 字段(Field):用于描述寄存器中的特定位。
每个字段可以设置位宽、访问权限、默认值等属性。
4. 地址空间(Address Space):用于描述寄存器和字段的地址范围。
一个地址空间可以包含多个寄存器和字段。
5. 枚举(Enumeration):用于描述字段的取值范围。
枚举可以定义一组预定义的符号值,用于表示字段的不同状态。
二、systemrdl语法的常用语句和关键字systemrdl语法提供了丰富的语句和关键字,用于描述数字系统的行为和结构。
以下是一些常用的语句和关键字:1. reg:用于定义一个寄存器。
语法格式为:reg <寄存器名称> { ... }。
2. field:用于定义一个字段。
语法格式为:field <字段名称> <位宽> { ... }。
3. access:用于定义字段的访问权限。
常用的访问权限有:read、write、read-write等。
4. default:用于定义字段的默认值。
默认值可以是一个具体的数值或一个枚举符号。
5. address:用于定义寄存器或字段在地址空间中的偏移地址。
语法格式为:address <偏移地址>。
6. width:用于定义字段的位宽。
L-system(L系统)

L-System公开2012-03-23 13:44 |(分类:默认分类)随着计算机图形学的飞速发展,人们一直研究在计算机上模拟各种植物形态的可能性。
目前,人们基本上利用Navier-Stokes 方程来模拟植物的形态,而其模拟出来的植物由于形态单一、逼真度不够高,已经不能满足农业、工业、军事、3D 等方面的要求。
通过对上述的情况进行研究和分析之后,我们寻找出一种能够逼真地模拟出植物的方法即BSP 的优化—L-System。
在BSP 和L-System的基础上,我们做了大量的实验,以验证这一方法的可行性、有效性。
(一)L-System 的数学模型及其构型的基本方法几个世纪以来,自然界中多彩多姿的植物深深地吸引了许多数学家,他们对其显著的几何特性作了广泛的研究,例如,叶子的左右对称,花的旋转对称,松果上鳞片的螺旋排列等。
1968 年,美国的生物学家Aristid Lindermayer(1925~1989)提出了Lindenmayer 系统,简称L-System。
它是描述植物生长的数学模型,其基本思想可解释为理想化的树木生长过程:从一条树枝(种子)开始,发出新的芽枝,而发过芽枝的枝干又都发新芽枝……最后长出叶子。
这一生长规律体现为斐波那契数列:1,1,2,3,5,8,13,21,34,55,…记该序列的第n 项为Fn,则有递推关系式:Fn+2=Fn+1+Fn (n=1,2,3,…)根据L-System 的基本思想,我们先建立二维树的数学模型:从树干开始,然后沿着树干逐渐扩展到连接的树枝,再以递归的方式进行同样的过程,该过程持续到最终分枝。
为简明起见,在这一模型中,每一树枝都化为一条直线,每次循环,树枝都被缩放,旋转和平移到其父枝的新位置上(如图3-1-1)。
图3-1-1以L-System 做为数学理论框架,研究植物的进化和造型,Smith、Anono 和Kunii 率先将L-System 引入到计算机图形学中,显示了L-System 在计算机模拟植物方面的潜力,为计算机模拟植物的真实感图形提供了强有力的工具。
布鲁姆的教育目标分类学说和加涅的学习结果分类

布鲁姆的教育⽬标分类学说和加涅的学习结果分类布卢姆的教学⽬标分类理论对教育⽬标分类体系的设想,最初是1948年由出席在波⼠顿召开的美国⼼理学年会的⼀些考试专家在⼀次正式会议上提出的。
其主要代表⼈物有布卢姆、克拉斯沃尔(D.R.Krathwohl)等⼈。
布卢姆等⼈把教育⽬标分为三⼤领域──认知领域(cognitive domain)、情感领域(affective domain)和动作技能领域(psychomotor domain)。
他们的教育⽬标分类强调指导教学过程和对结果进⾏评价,其实是⼀种教学⽬标分类。
(⼀)认知领域的⽬标分类布卢姆等⼈在1956年出版的《教育⽬标分类学,第⼀分册:认知领域》中把认知领域的⽬标分为六个亚领域,即知识(knowledge)、领会(comprehension)、运⽤(application)、分析(analysis)、综合(synthesis)和评价(evaluation)。
1.知识知识⽬标要求学⽣在学习情境中把某种信息储存在⼤脑中,以后所要做的就是回忆这些信息。
知识这⼀类别所涉及的主要⼼理过程是记忆。
在知识的测验情境中,提问的形式与最初的学习情境中的形式有所不同,这要求学⽣在回答问题时有⼀定程度上的联想和判断过程,但这仅仅是⼀⼩部分;在其他类别的学习和测验中也有记忆,同样这也只是⼀⼩部分。
知识包括具体的知识、处理具体事物的⽅式⽅法的知识、学科领域中的普遍原理和抽象概念的知识三⼤类,每⼀类型⼜包括若⼲个⼩类型。
(1)具体的知识是指对具体的、孤⽴的⽚断信息的回忆。
它包括:①术语的知识,即具体符号的指称事物的知识,如熟悉的⼤量词汇的⼀般意义;②具体事实的知识,指⽇期、事件、⼈物、地点等⽅⾯的知识,如对某些特定⽂化中的主要事实的回忆。
(2)处理事物的⽅式⽅法的知识,是指有关组织、研究、判断和批评的⽅式⽅法的知识。
它包括:①惯例的知识,即有关对待和表达各种现象和观念的独特⽅式的知识,如了解演讲与写作中的正确形式和习惯⽤法;②趋势和顺序的知识,即时间⽅⾯各种现象所发⽣的过程、⽅向和运动的知识,如最近50年美国政府的发展趋势;③分类和类别的知识,即有关类别、组织、部类及排列的知识,如各类⽂献的范围;④准则的知识,即有关检验和判断各种事实、原理、观点和⾏为所依据的准则的知识,如对某种作品及其阅读⽬的作出适当判断的准则;⑤⽅法论的知识,即有关在某⼀特定学科领域使⽤的以及在调查特定的问题和现象时所⽤的探究⽅法、技巧和步骤的知识,如有关⽤科学⽅法评价健全概念的知识。
systemc 心得

module constructor:
process由systemC kernel调用,所以不需要参数和返回值。
3. recome implemented using pointers instead of direct instantiation. This method allows for dynamicdesign configuration.
6. sc_start()也可指定timeout时间。
7. wait(sc_time)
1. SystemC使用simulation process来实现concurrency。simulation process运行了一段code segment之后我们期望它能返回,将控制权交给simulation kernel。
4.,sc_spawn(sc_bind(&dut::PCIX_rcv,this,sc_ref(d1)),"p2")
5.,sc_spawn(sc_bind(&dut::USB2,this,sc_ref(d1)), "p3")
6.,sc_spawn(sc_bind(&dut::HT1_xtm,this,sc_ref(d2)), "p4")
2. module
声明如下:[cpp]view plaincopyprint?
具体内容有:
1)ports 2) channel instance 3) data instance 4) sub-designs 5) constructor 6) destructor 7) simulation process
2)initialization:将没有特别声明dont initialized的process放入set of runable process,dont initialized process放入set of waiting process
intersystems caché语法-概述说明以及解释

intersystems caché语法-概述说明以及解释1.引言1.1 概述概述部分的内容可以从以下角度入手:Intersystems Cache是一种高效的数据库管理系统,它具有强大的功能和灵活的语法。
它被广泛应用于医疗、金融、物流等领域,并且在数据处理和存储方面表现出色。
首先,Intersystems Cache具有一套独特的数据库管理系统,它采用了高性能的数据存储引擎和先进的数据结构,可以高效地处理大量的数据。
同时,Cache的语法非常灵活,支持多种数据类型和数据操作,可以满足各种应用的需求。
其次,Intersystems Cache还支持多种编程语言的接口,包括Java、C、Python等,使开发人员可以使用自己熟悉的语言进行数据库开发。
这种多语言支持大大提高了开发的灵活性和效率。
另外,Intersystems Cache还具有强大的并发处理能力和事务支持,可以保证数据的一致性和可靠性。
同时,Cache还提供了丰富的安全功能,包括用户认证、权限管理等,可以保护数据的安全性。
总之,Intersystems Cache是一种功能强大、性能高效的数据库管理系统,具有灵活的语法和多语言支持。
它在各个领域都有广泛应用,并且得到了用户的高度认可和好评。
在接下来的文章中,我们将详细介绍Cache的语法和使用方法,希望能够帮助读者更好地了解和使用这一优秀的数据库管理系统。
1.2 文章结构文章结构部分的内容可以包括以下内容:文章结构部分旨在介绍整篇文章的组织架构,让读者能够清晰地了解文章的内容分布和逻辑顺序。
本文将按照以下几个部分进行讨论和展示。
首先,引言部分将以一个概述开始。
在这个部分,将对Intersystems Caché语法的基本特点进行简要介绍,并提出本文的目的和意义。
这将为读者提供一个整体的认识,并引导他们进一步了解和掌握该语言。
第二部分是正文部分,其中包含了要点1和要点2两个子部分。
紫 杉 醇 静 脉 输 注 的 注 意 事 项

紫杉醇静脉输注的注意事项唐跃年1*,陈颖2,孙朝荣1,张健1,胡松浩1 1上海交通大学医学院附属新华医院药剂科,上海市200092;2上海杨浦区中心医院药剂科,上海市200093中图分类号: R979 1 文献标志码: A 文章编号: 1001-0408(2006)12-0946-02紫杉醇问世于20世纪90年代,国内、外临床应用结果表明其在治疗卵巢癌、乳腺癌和肺癌中有较好疗效,是目前抗癌活性较强的化疗药。
其抗癌机制是通过刺激微管的聚合,促进微管双聚体装配成微管,使微管超稳定,最终使细胞增殖停止在有丝分裂期的G2/M期,其独特的作用机制和确切疗效,已成为迄今发现的最具有应用价值的抗癌药之一[1,2]。
紫杉醇注射液是由紫杉醇与聚氧乙基代蓖麻油(Cremop_hor,EL)和无水乙醇50∶50(V/V)配制而成。
使用时用生理盐水或5%葡萄糖注射液稀释后静脉滴注,紫杉醇注射液中的药物及EL在静脉输液的配制、输注方法对疗效有很大的影响[3]。
本文概述药物配制与输注方法对疗效的影响因素与避免的方法,让药物发挥更好的作用。
1 药物的配制1 1 配药前的注意事项紫杉醇是一种细胞毒类抗癌药,与其它具有潜在毒性的化合物一样应在配制专用柜内配制,防止吸入体内,避免被药物污染,配药时宜戴手套,如果皮肤接触该药,应立即用肥皂彻底清洗皮肤,一旦接触粘膜也应用水彻底冲洗。
配药前先检查5%葡萄糖注射液和紫杉醇溶液是否有颜色、沉淀等变化。
1 2 紫杉醇的配制在配制中,溶液可能显示雾状,这是配制中的赋型剂稀释液所致。
配制完毕,应检查是否有颗粒物或色泽变化。
配制好后立即使用,应使用特制的带有滤过装置的输液器输注,并于配药后24h内完成输注。
1 3 紫杉醇配制方法的影响13 1 溶解方法的影响:不同的溶解方法对药物的药理性能会产生不同的影响,正确的溶解方法既能使药物溶解,又不影响药效。
紫杉醇在加入输液时应缓慢加入,避免输液中药物的局部浓度过高;在输液中振摇使之均匀溶解,溶液中若有大颗粒或混浊出现,则不能使用。
数字信号处理 实验一 系统响应与系统稳定性

Experiment One the response and stability of systems1. Aims(1) Knowing how to compute the response of a system to an input.(2) Having a level of solid understanding of characterization in time-domain of systems.(3) To observe, verify and analyze the stability of systems.2. Principle and method:Discrete-Time LTI systems can be represented as a linear const difference equation or the impulse response in time domain and as a transform function in frequency-domain. The response of the system to an arbitrary input can be computed knowing the linear const difference equation or the impulse response.In this experiment, we compute the response of the system to an arbitrary input by two ways.1) Output computation using MATLAB, knowing the linear const difference equation.2) Output computation using linear convolution, knowing the impulse response of the systems.Signal processing toolbox in MATLAB provides us a convenient and efficient function to reach our objectives.Characterization in time-domain of systems refers to the linear, shift-invariant, causal and stable of a system. We focus on the stability of systems, including the steady and transient response.We defined a discrete-time system to be stable if and only if for every bounded input, the output is also bounded, or, its impulse response sequence is absolutely summable. The stability of a discrete-time system depends on the coefficients of its difference equation.It is impossible to examine the system whether the output is bound or not when all of whose input is bound ,or examine the response of the system satisfy the absolutely summable when examining whether the system is stable or not in practice .One of the feasible way is to add the unit step sequence to the input end, so we can decide the system is stable if its output tends to a constant (including zero).The steady state output is the output as n tends to infinity .If it is stable , the output at the initial period of time is defined to transient effect ,with n increasing ,the magnitude tends to be stable ,to reach the stable output .Pay attention that the initial state of the systems are supposed to be zero in thefollowing experiment .3. The contents and steps(1) Given a difference equation of low-pass filter following:)1(9.0)1(05.0)(05.0)(-+-+=n y n x n x n ythe input signal:)()(81n R n x = )()(2n u n x =① Solve the response of the system respectively when )()(81n R n x = and )()(2n u n x = ,and draw up their waveform.② Solve the unit impulse response of the system, and draw up their waveform .(2) Given the unit impulse response of the system following,)()(101n R n h =)3()2(5.2)1(5.2)()(2-+-+-+=n n n n n h δδδδSolve the output response of the system h1(n) and h2(n) by linear convolution respectively when the input )()(81n R n x = ,and draw up the waveform.(3) Given the difference equation of a resonator as following00() 1.8237(1)0.9801(2)()(2)y n y n y n b x n b x n =---+--Let 49.100/10=b , the frequency of the resonator is 0.4 rad.① Examine whether the system is stable or not by experiment. When the input is u(n), draw up the waveform of the system output.② Given the input signal is)4.0sin()014.0sin()(n n n x +=Solve the output response of the system, and draw up its waveform.4. Question for review(1) If the inputs are infinite long sequence, but the unit impulse response of systems are finite long sequence, can the response of the systems be solved by linear convolution? How?(2) If the signal passing a low-pass filter, filtrating the components of the high frequency, what will the change of the Time-Domain signal .Please analyze and illustrate by the results of the former experiment.5. The requirement of the report(1) Sketch the method of solving the response of systems in Time-Domain;(2) Sketch the method of justifying the stability of systems by experiment , analyze the stable output waveform of the above third experiment ;(3) Analyze and explain the results of each experiment simply ;(4) Answer the question for review simply;(5) Print the list of the procedures and each signal required.。
从 WINDOWS 7 安装光盘中提取一份纯净的 Windows 7 PE

从WINDOWS 7 安装光盘中提取一份纯净的Windows 7 PE (源码公开)关于PE,不需要多说了,大致相当于windows98时的dos,是安装、维护系统不可缺少的东西,总之吧,这是个好东西。
按照版本分,windows7的PE应该是PE3.0。
——有兴趣的筒靴,请搜索一下,网上关于PE 基础知识的介绍很多。
提起来这个东西,其实很多人都接触过,在windows7运行出现异常时,总会出现“修复计算机”之类的选项,其实,那时电脑启动的就是PE。
简言之,PE3.0就是骨头版的WINDOWS7。
下面直接贴出一套代码,运行后即可得到一份原汁原味的Windows 7 PE 。
此帖介绍的方法,好处就是:避开繁琐的制作步骤,舍弃人为添加的臃余工具,直接制作一份原汁原味的PE3.0。
代码中涉及到的,都是微软自己的东西,没有第三方工具。
纯绿色食品,本人品尝多次,无任何毒副作用,请放心食用。
也无需更多的解说,代码中的注释行,把各个步骤都已经介绍了。
以下内容,拷贝到文本文件,扩展名改为BAT,在WINDWOS7中以管理员身份运行即可。
================代码开始于下一行===================:: 本程序从WINDOWS 7 安装光盘中提取并生成纯净的Windows 7 PE 映像。
:: 请将WINDOWS 7 安装光盘放入光驱J:,也可以将安装映像加载到虚拟光驱J: 。
:: 请预先将imagex.exe 文件拷贝至%SYSTEMDRIVE% 根目录。
@echo offsetlocal enabledelayedexpansioncolor 2etitle 从WINDOWS 7 安装光盘中提取WinPE3.0 Code by Bootp.Lu:: 本代码开放源码,可随意拷贝使用。
引用或改写时请保留上面一行中的作者信息。
@echo 本程序从WINDOWS 7 安装光盘中提取并生成纯净的Windows 7 PE 映像。
Navigation System 1 用户手册.pdf_1702091176.4763625说明书

Table of ContentsIntroduction (4)Manual Overview (4)System Overview (4)Accessories Precautions (5)Important Safety Information (5)Map Overview (6)Current Street (6)Verified/Unverified Street (6)User Agreement (8)Getting Started (10)System Controls (10)Voice Control Basics (12)Using the Voice Control System (13)Improving Voice Recognition (13)Selecting an Item (Button) on theScreen (14)Selecting an Item in a List (14)Using the On-screen Keyboard (15)System Start-up (16)Map Screen Legend (18)Map Screen Description (19)Zoom In/Out (19)Map Scrolling (19)Displaying Current Location (19)System Function Diagram.............20Entering a Destination.. (21)By Address (22)Selecting the State or Province (22)Selecting the City (22)Selecting the Street (24)Entering the Street Number (26)By Intersection (26)Selecting the State or Province (27)Selecting the City (27)Selecting the Street (29)By Places (31)Finding the Place by Category (31)Finding the Place by Name (35)Finding the Place by PhoneNumber (35)Finding the Place by Zagat 2006 (35)By Map Input (36)Showing the Map of CurrentPosition (36)Showing the Map of City (37)Showing the Map of State (37)Showing the Map of ContinentalUSA (38)By Previous Destinations (39)By Today’s Destinations (40)Editing Today’s Destination List (40)Adding Destinations to the List (40)By Address Book (41)Adding Addresses to the PersonalAddress Book (42)By Go Home (42)Driving to Your Destination (44)Driving to Your Destination (44)Calculate Route to Screen (44)Changing the Routing Method (45)Viewing the Routes (45)Viewing the Destination Map (47)Map Screen (47)Route Line (47)Guidance Prompts (48)Map Screen Legend (49)Guidance Screen (50)Guidance Screen Legend (50)Distance and Time toDestination (51)Direction List (51)Exit Info(Freeway Exit Information) (52)Split Screen Guidance (52)Map Scale (53)Map Orientation (54)Destination Icon (55)Use these links (and links throughout this manual) to navigate through this reference.For a printed owner's manual, click on authorized manuals or go to .Refer to 2007Honda Pilot Owner's Manual for more information.1Table of ContentsLandmark Icons (55)Showing Icons on the Map (57)Icon Options (57)Going Off the Route (59)Off-road Tracking (59)Viewing/Saving the CurrentLocation (60)Pop-ups and Disclaimers (61)Changing the Route (62)Change Route By Screen (62)Waypoints (62)Reroute: Avoid Streets (64)Reroute: Detour (64)Reroute: Change Routing Method (64)Changing Your Destination (65)Find Nearest (Voice command) (65)Go Home (Voice command) (65)Using Joystick to ChangeDestination (65)Entering a Destination from theMenu Screen (while on route) (66)Continue Trip Screen (66)Information Features (67)Information Screen (67)Setup (67)Voice Command Help (67)Calendar (68)Entering Your Schedule (69)Map Legend (70)Calculator (70)Unit Conversion (71)Key to Zagat Ratings (71)System Set-up (73)Set up Mode (73)Setup Screen (first) (73)Brightness (73)Volume (73)Display (74)Guidance Prompts (75)Contrast (75)Setup Screen (second) (75)Personal Information (76)Address Book (76)Home Address (79)PIN Number (80)User Name (81)Previous Destinations (81)Routing & Guidance (82)Rerouting (82)Unverified Area Routing (83)Edit Avoid Area (87)Edit Waypoint Search Area (88)Guidance Mode (89)Vehicle (90)Off-road Tracking (90)Correct Vehicle Position (90)System Information (91)Basic Settings (92)Keyboard Layout (92)Units (mile or km) (92)Voice Recognition Feedback (92)Voice (92)Clock Adjustment (92)Auto Daylight Saving Time (93)Auto Time Zone by GPS (93)Time Adjustment (94)Color (94)Map Color (94)Menu Color (95)Rear View Camera (95)Rear View Camera BrightnessAdjustment (95)System Initialization (96)System Initialization (96)Entering the Security Code (96)GPS Initialization (97)Map Matching (97)System Limitations (98)Database Limitations (100)2Table of ContentsCustomer Assistance (101)Reporting Errors (101)Honda Automobile CustomerService (101)Visiting Your Dealer (102)Obtaining a Navigation UpdateDVD (102)Changing the DVD (103)PC Card (103)Coverage Areas (104)Map Coverage (104)U.S. Detailed Coverage Areas (104)Canada Detailed CoverageAreas (108)Frequently Asked Questions (113)Troubleshooting (120)Glossary (121)Glossary (121)Voice Command Index (124)Global Commands (124)Navigation General Commands..124 Navigation Display Commands (125)Find Place Commands (126)Climate Control Commands (127)Temperature Voice Commands (128)Radio Voice Commands (128)CD Voice Commands (129)Information Screen VoiceCommands (129)Setup Screen (first)Commands (129)On-Screen Commands (130)On-Screen Commands Assist (130)Index (132)3。
广西专版2023_2024学年新教材高中英语Unit5SectionⅡ课件新人教版必修第一册

尽管历史跌宕起伏,中国因其古代文明一直延续至今而闻名
于世。
考点despite prep.即使;尽管
despite=in spite of,后面搭配名词、动词-ing形式或名词性从句;
而though,although是连词,引导状语从句
语境领悟
(1)Their minds are bright despite their dirty hands and
in Chinese culture.
Paragraph 5 e.Written Chinese began as a picture-based language.
Paragraph 6 f.The Chinese writing system is one of the main factors that have
( T )
2.Ancient Chinese people carved symbols on animal bones
and shells,but these symbols have disappeared in today's
hanzi.( F )
3.There was a time when many kinds of dialects and
单句语法填空
Despite
(3)
what others said,he thought it was
worth reading.
(4) Although/Though what others said annoyed him,he
still carried out the plan.
2.【教材原文】 the
5.The Chinese writing system is respected so that Chinese
l-system的基本原理

l-system的基本原理
L-system(Lindenmayer system)是一种基于字符串替换的形式语言,用于模拟和描述生物体的生长过程。
它是由匈牙利生物学家阿里斯泰尔·林德马耶尔在1968年提出的,被广泛应用于计算机图形学、生物学模拟和自然语言处理等领域。
L-system的基本原理是通过定义一组规则来生成字符串,然后将字符串转化为图形或其他形式的输出。
这些规则通常包括一个初始字符串和一组替代规则,用于将字符串中的符号替换为新的符号序列。
通过多次迭代替换,可以生成越来越复杂的字符串,从而模拟生物体的生长过程。
例如,我们可以使用L-system来模拟植物的分枝生长。
初始时,我们可以定义一个简单的字符串,表示植物的主干。
然后,我们定义一组替代规则,用于将主干的符号替换为更复杂的分枝结构。
通过多次迭代替换,我们可以生成一个逼真的植物形态。
除了模拟植物的生长,L-system还可以用于模拟其他生物的形态,如藻类、菌类等。
它还可以用于生成自然景观、城市道路网络等图形。
L-system的应用不仅限于图形模拟,还可以用于自然语言处理。
通过将字符串中的符号映射为词汇或语法规则,我们可以生成自然语言的句子、段落甚至文章。
这种应用可以用于自动文本生成、信息
提取等领域。
L-system是一种基于字符串替换的形式语言,通过定义一组规则来模拟生物体的生长过程。
它可以用于生成图形、模拟生物形态,也可以用于生成自然语言文本。
L-system的应用领域广泛,具有重要的科学研究和实际应用价值。
1. System Safety

Chapter 1System Safety1.1INTRODUCTIONWe live in a world comprised of systems and risk.When viewed from an engineer-ing perspective,most aspects of life involve systems.For example,houses are a type of system,automobiles are a type of system,and electrical power grids are another type of mercial aircraft are systems that operate within an economical transportation system and a worldwide airspace control system.Systems have become a necessity for modern living.With systems and technology also comes exposure to mishaps because systems can fail or work improperly resulting in damage,injury,and deaths.The possibility that a system fails and results in death,injury,damage,and the like is referred to as mishap risk.For example,there is the danger that a traffic light will fail,resulting in the mishap of another auto colliding with your auto.Automobiles,traffic,and traffic lights form a unique system that we use daily,and we accept the mishap risk poten-tial because the risk is small.There is the danger that the gas furnace in our house will fail and explode,thereby resulting in the mishap of a burned house,or worse.This is another unique system,with known adverse side effects that we choose to live with because the mishap risk is small and the benefits are great.Our lives are intertwined within a web of different systems,each of which can affect our safety.Each of these systems has a unique design and a unique set of com-ponents.In addition,each of these systems contains inherent hazards that present unique mishap risks.We are always making a trade-off between accepting the benefits of a system versus the mishap risk it presents.As we develop and build sys-tems,we should be concerned about eliminating and reducing mishap risk.Some risks are so small that they can easily be accepted,while other risks are so large 1Hazard Analysis Techniques for System Safety ,by Clifton A.Ericson,IICopyright #2005John Wiley &Sons,Inc.2SYSTEM SAFETYthey must be dealt with immediately.Mishap risk is usually small and acceptable when system design control(i.e.,system safety)is applied during the development of the system.Risks are akin to the invisible radio signals thatfill the air around us,in that some are loud and clear,some very faint,and some are distorted and unclear.Life,as well as safety,is a matter of knowing,understanding,and choosing the risk to accept. System safety is the formal process of identifying and controlling mishap risk.As systems become more complex and more hazardous,more effort is required to understand and manage system mishap risk.The key to system safety and effective risk management is the identification and mitigation of hazards.To successfully control hazards,it is necessary to understand hazards and know how to identify them.The purpose of this book is to better under-stand hazards and the tools and techniques for identifying them,in order that they can be effectively controlled during the development of a system.1.2SYSTEM SAFETY BACKGROUNDThe ideal objective of system safety is to develop a system free of hazards.However, absolute safety is not possible because complete freedom from all hazardous conditions is not always possible,particularly when dealing with complex inherently hazardous systems,such as weapons systems,nuclear power plants,and commercial aircraft.Since it is generally not possible to eliminate all hazards,the realistic objective becomes that of developing a system with acceptable mishap risk.This is accom-plished by identifying potential hazards,assessing their risks,and implementing cor-rective actions to eliminate or mitigate the identified hazards.This involves a systematic approach to the management of mishap risk.Safety is a basic part of the risk management process.Hazards will always exist,but their risk must and can be made acceptable.There-fore,safety is a relative term that implies a level of risk that is measurable and accep-table.System safety is not an absolute quantity,but rather an optimized level of mishap risk management that is constrained by cost,time,and operational effective-ness(performance).System safety requires that risk be evaluated,and the level of risk accepted or rejected by an appropriate decision authority.Mishap risk manage-ment is the basic process of system safety engineering and management functions. System safety is a process of disciplines and controls employed from the initial sys-tem design concepts,through detailed design and testing,to system disposal at the completion of its useful life(i.e.,“cradle to grave”or“womb to tomb”).The fundamental objective of system safety is to identify,eliminate or control, and document system hazards.System safety encompasses all the ideals of mishap risk management and design for safety;it is a discipline for hazard identification and control to an acceptable level of risk.Safety is a system attribute that must be intentionally designed into a product.From an historical perspective it has been learned that a proactive preventive approach to safety during system design and development is much more cost effective than trying to add safety into a system1.3SYSTEM SAFETY CHARACTERIZATION3 after the occurrence of an accident or mishap.System safety is an initial investment that saves future losses that could result from potential mishaps.1.3SYSTEM SAFETY CHARACTERIZATIONSystem safety is the process of managing the system,personnel,environmental,and health mishap risks encountered in the design development,test,production,use, and disposal of systems,subsystems,equipment,materials,and facilities.A system safety program(SSP)is a formal approach to eliminate hazards through engineering,design,education,management policy,and supervisory control of con-ditions and practices.It ensures the accomplishment of the appropriate system safety management and engineering tasks.The formal system safety process has been primarily established by the U.S.Department of Defense(DoD)and its military branches and promulgated by MIL-STD-882.However,this same process is also fol-lowed in private industry for the development of commercial products,such as commer-cial aircraft,rail transportation,nuclear power,and automobiles,to mention just a few.The goal of system safety is the protection of life,systems,equipment,and the environment.The basic objective is the elimination of hazards that can result in death,injury,system loss,and damage to the environment.When hazard elimination is not possible,the next objective is to reduce the risk of a mishap through design control measures.Reducing mishap risk is achieved by reducing the probability of the mishap and/or the severity of the mishap.This objective can be attained at minimum cost when the SSP is implemented early in the conceptual phase and is continued throughout the system development and acquisition cycle.The overall complexity of today’s systems,particularly weap-ons systems,is such that system safety is required in order to consciously prevent mishaps and accidents.Added to complexity is the inherent danger of energetic materials,the effects of environments,and the complexities of operational require-ments.In addition,consideration must be given to hardware failures,human error, software interfaces,including programming errors,and vagaries of the environment.System safety is defined in MIL-STD-882D as follows:The application of engineering and management principles,criteria,and techniques to achieve acceptable mishap risk,within the constraints of operational effectiveness and suitability,time,and cost,throughout all phases of the system life cycle.The intent of system safety is mishap risk management through hazard identifi-cation and mitigation techniques.System safety engineering is an element of sys-tems engineering involving the application of scientific and engineering principles for the timely identification of hazards and initiation of those actions necessary to prevent or control hazards within the system.It draws upon professional knowledge and specialized skills in the mathematical and scientific disciplines,together with the principles and methods of engineering design and analysis to specify,predict, evaluate,and document the safety of the system.4SYSTEM SAFETYSystem safety management is an element of program management that ensures accomplishment of the correct mix of system safety tasks.This includes identifi-cation of system safety requirements;planning,organizing,and controlling those efforts that are directed toward achieving the safety goals;coordinating with other program elements;and analyzing,reviewing,and evaluating the program to ensure effective and timely realization of the system safety objectives.The basic concept of system safety is that it is a formal process of intentionally designing in safety by designing out hazards or reducing the mishap risk of hazards. It is a proactive process performed throughout the system life cycle to save lives and resources by intentionally reducing the likelihood of mishaps to an insignificant level.The system life cycle is typically defined as the stages of concept,preliminary design,detailed design,test,manufacture,operation,and disposal(demilitarization). In order to be proactive,safety must begin when system developmentfirst begins at the conceptual stage.The goal of system safety is to ensure the detection of hazards to the fullest extent possible and provide for the introduction of protective measures early enough in sys-tem development to avoid design changes late in the program.A safe design is a pre-requisite for safe operations.Things that can go wrong with systems are predictable, and something that is predictable is also preventable.As Murphy’s law states“what-ever can go wrong,will go wrong.”The goal of system safety is tofind out what can go wrong(before it does)and establish controls to prevent it or reduce the probability of occurrence.This is accomplished through hazard identification and mitigation. 1.4SYSTEM SAFETY PROCESSMIL-STD-882D establishes the core system safety process in eight principal steps, which are shown in Figure1.1.The core system safety process involves establishing an SSP to implement the mishap risk management process.The SSP is formally documented in the system safety program plan(SSPP),which specifies all of the safety tasks that will be performed,including the specific hazard analyses,reports, and so forth.As hazards are identified,their risk will be assessed,and hazard miti-gation methods will be established to mitigate the risk as determined necessary. Hazard mitigation methods are implemented into system design via system safetyrecordsrequirements(SSRs).All identified hazards are converted into hazard action Array Figure1.1Core system safety process.1.5SYSTEM CONCEPT5 (HARs)and placed into a hazard tracking system(HTS).Hazards are continually tracked in the HTS until they can be closed.It can be seen from the core system safety process that safety revolves around hazards.Hazard identification and elimination/mitigation is the key to this process. Therefore,it is critical that the system safety analyst understand hazards,hazard identification,and hazard mitigation.The core system safety process can be reduced to the process shown in Figure1.2. This is a mishap risk management process whereby safety is achieved through the identification of hazards,the assessment of hazard mishap risk,and the control of hazards presenting unacceptable risk.This is a closed-loop process whereby hazards are identified and tracked until acceptable closure action is implemented and veri-fied.It should be performed in conjunction with actual system development,in order that the design can be influenced during the design process,rather than trying to enforce design changes after the system is developed.System safety involves a life-cycle approach based on the idea that mishap and accident prevention measures must be initiated as early as possible in the life of a sys-tem and carried through to the end of its useful life.It is usually much cheaper and more effective to design safety features into an item of equipment than it is to add the safety features when the item is in production or in thefield.Also,experience indi-cates that that some of the hazards in a newly designed system will escape detection, no matter how aggressive the safety program.Therefore,the safety program for a sys-tem must remain active throughout the life of the system to ensure that safety problems are recognized whenever they arise and that appropriate corrective action is taken.The key to system safety is the management of hazards.To effectively manage hazards,one must understand hazard theory and the identification of hazards.The purpose of this book is to better understand hazards and the tools and techniques for identifying them.When hazards are identified and understood,they can then be properly eliminated or mitigated.1.5SYSTEM CONCEPT1.5.1General System ModelAs implied in the name,system safety is involved with“systems”and with the manyorderdifferent characteristics and attributes associated with systems.Therefore,in Array Figure1.2Closed-loop hazard control process.to effectively apply the system safety process,it is necessary to completely under-stand the term system and all of its ramifications.This includes understanding what comprises a system,how a system operates,system analysis tools,the life cycle of a system,and the system development process.A proactive and preventive safety process can only be effectively implemented if the proper system-oriented safety tasks are performed during the appropriate system life-cycle phases,in con-junction with utilizing the appropriate system engineering tools.The timing and content of safety tasks must coincide with certain system development domains to ensure safety success.The standard definition of a system from MIL-STD-882is:A system is a composite,at any level of complexity,of personnel,procedures,materials,tools,equipment,facilities,and software.The elements of this composite entity are used together in the intended operational or support environment to perform a given task or achieve a specific purpose,support,or mission requirement.Essentially a system is a combination of subsystems interconnected to accomplish the system objective.A subsystem is a subset of the system that could include equipment,components,personnel,facilities,processes,documentation,procedures,and software intercon-nected in the system to perform a specific function that contributes to accomplishing the system objective.The system objective is a desired result to be accomplished by the system.The system objective defines the purpose for the system.System functions are the oper-ations the system must perform in order to accomplish its objective.System func-tions are generally performed by subsystems and define how the system operates.Figure 1.3depicts the generic concept of a system.This diagram shows a system comprised of many subsystems,with an interface between each subsystem.TheInterfaces SystemFunctionsFigure 1.3System model.6SYSTEM SAFETYsystem has an objective and is surrounded by a boundary and an environment.Sys-tem safety analysis involves evaluation of all system aspects,including functions,subsystems,interfaces,boundaries,and environments and the overall system itself.1.5.2System AttributesSystems have many different attributes of interest to system safety.Defining and understanding a system’s key attributes is necessary because they provide the frame-work for designing,building,operating,and analyzing systems.Key system attri-butes are shown in Table 1.1,where the major attribute categories are listed on the top row,with subelements identified below.Each of these attributes is usually addressed in system safety hazard analyses at some point in the system development program.Each of the system attributes must be understood in order to perform a complete and thorough hazard analysis.Examples of safety considerations for the elements attribute are as follows:.Hardware Failure modes,hazardous energy sources .Software Design errors,design incompatibilities .Personnel Human error,human injury,human control interface .Environment Weather,external equipment .Procedures Instructions,tasks,warning notes .Interfaces Erroneous input /output,unexpected complexities .Functions Fail to perform,performs erroneously .Facilities Building faults,storage compatibility,transportation faultsAn SSP must adequately address each of these system attributes in order to ensure that an optimum degree of safety is achieved in the system.All of the system elements and their interrelationships must be considered in the safety analyses,assessments,and evaluations to ensure it truly is a system safety analysis.For example,it is possible for each operational phase or mode to have a different and /or significant impact upon system safety.Different functions are performed TABLE 1.1Key System AttributesHierarchyElements Domains Operations Types SystemsHardware Boundaries Functions Static SubsystemsSoftware Complexity Tasks Dynamic UnitsHumans Criticality Modes Robotic AssembliesProcedures Phases Process ComponentsInterfaces Weapon Piece part EnvironmentsAircraft FacilitiesSpacecraft Documentation ...1.5SYSTEM CONCEPT 7during each phase that could have a direct impact on subsequent phases.During cer-tain phases safety barriers or interlocks are often removed,making the system more susceptible to the occurrence of a hazard,for example,at one point in the operational mission of a missile,the missile is powered and armed.This means that fewer poten-tial failures are now necessary in order for a mishap to occur,and there are fewer safeguards activated in place to prevent hazards from occurring.1.5.3System TypesThe types of systems dealt with in system safety are typically physical,human-made objects comprised of hardware,software,user interfaces,and procedures.These types of systems include ships,weapons,electrical power,railroads,aircraft,and the like that are used for some specific purpose or objective.Table1.2provides some example systems,showing their intended purpose and some of the subsystems comprising these systems.It is interesting to note that many of the systems are com-prised of similar types of subsystems,which means that they may have similar types of hazards.Understanding system type and scope is very important in system safety and hazard analysis.The system type can be an indication of the safety criticality involved.The scope of the system boundaries establishes the size and depth of the system.The system limitations describe basically what the system can and can-not safely do.Certain limitations may require the system to include special design safety features.Every system operates within one or more different environments. The specific environment establishes what the potential hazardous impact will be on the system.System criticality establishes the overall safety rating for the system.A nuclear power plant system has a high consequence safety rating,whereas a TV set as a system has a much lower safety criticality rating.TABLE1.2Example System TypesSystem Objective SubsystemsShip Transport people/deliver weapons Engines,hull,radar,communications,navigation, software,fuel,humansAircraft Transport people/deliver weapons Engines,airframe,radar,fuel,communications, navigation,software,humansMissile Deliver ordnance Engines,structure,radar,communications,navigation,softwareAutomobile Transportation Engine,frame,computers,software,fuel,humansNuclearpower plant Deliver electricalpowerStructure,reactor,computers,software,humans,transmission lines,radioactive materialTelevision View video media Structure,receiver,display,electrical power Toaster Browning of bread Structure,timer,electrical elements,electricalpowerTelephone Communication Structure,receiver,transmitter,electrical power,analog converter8SYSTEM SAFETY1.5SYSTEM CONCEPT9 1.5.4System Life CycleThe system life cycle involves the actual phases a system goes through from concept through disposal.This system life cycle is analogous to the human life cycle of con-ception,birth,childhood,adulthood,death,and burial.The life cycle of a system is very generic and generally a universal standard.The system life-cycle stages are generally condensed and summarized into thefive major phases shown in Figure1.4. All aspects of the system life cycle willfit into one of these major categories.The life-cycle stages of a system are important divisions in the evolution of a pro-duct and are therefore very relevant to the system safety process.Safety tasks are planned and referenced around thesefive phases.In order to proactively design safety into a product,it is essential that the safety process start at the concept defi-nition phase and continue throughout the life cycle.Phase1:Concept Definition This phase involves defining and evaluating a potential system concept in terms of feasibility,cost,and risk.The overall project goals and objectives are identified during this basic concept evaluation phase. Design requirements,functions,and end results are formulated.The basic system is roughly designed,along with a thumbnail sketch of the subsystems required and how they will interact.During this phase,safety is concerned with hazardous components and functions that must be used in the system.The system safety pro-gram plan(SSPP)is generally started during this phase to outline the overall system risk and safety tasks,including hazard analyses that must be performed.Phase2:Development and Test This phase involves designing,developing, and testing the actual system.Development proceeds from preliminary through detailed tasks.The development phase is generally broken into the following stages: .Preliminary Design Initial basic design.Detailed Design Final detailed design.Test System testing to ensure all requirements are metThe preliminary design translates the initial concept into a workable design. During this phase subsystems,components,and functions are identified and established.Design requirements are then written to define the systems,subsystems, and software.Some testing of design alternatives may be performed.During this phase,safety is concerned with hazardous system designs,hazardous com-ponents/materials,and hazardous functions that can ultimately lead to mishaps and actions to eliminate/mitigate the hazards.Figure1.4Major system life-cycle phases.10SYSTEM SAFETYThe preliminary design evolves into thefinal detailed design.Thefinal design of the system involves completing development of the design specifications,sketches, drawings,and system processes and all subsystem designs.During thefinal design phase,safety is concerned with hazardous designs,failure modes,and human errors that can ultimately lead to mishaps during the life cycle of the system.The system test phase involves verification and validation testing of the design to ensure that all design requirements are met and are effective.In addition,safety is concerned with potential hazards associated with the conduct of the test and additional system hazards identified during testing.Phase3:Production Thefinal approved design is transformed into the oper-ational end product during the production phase.During this phase,safety is con-cerned with safe production procedures,human error,tools,methods,and hazardous materials.Phase4:Operation The end product is put into actual operation by the user(s) during the operation phase.This phase includes use and support functions such as transportation/handling,storage/stowage,modification,and maintenance.The operational phase can last for many years,and during this phase performance and technology upgrades are likely.Safe system operation and support are the prime safety concerns during this phase.Safety concerns during this phase include operator actions,hardware failures,hazardous system designs,and safe design changes and system upgrades.Phase5:Disposal This phase completes the useful life of the product.It involves disposing of the system in its entirety or individual elements,following completion of its useful life.This stage involves phase-out,deconfiguration,or decommissioning where the product is torn down,dismantled,or disassembled. Safe disassembly procedures and safe disposal of hazardous materials are safety concerns during this phase.Normally each of these life-cycle phases occurs sequentially,but occasionally development tasks are performed concurrently,spirally,or incrementally to shorten the development process.Regardless of the development process used,sequential, concurrent,spiral,or incremental,the system life-cycle phases basically remain the same.1.5.5System DevelopmentSystem development is the process of designing,developing,and testing a system design until thefinal product meets all requirements and fulfills all objectives. System development consists primarily of phases1and2of the system life cycle. It is during the development stages that system safety is“designed into”the product for safe operational usage.Figure3.13shows thefive system life-cycle phases,with phase2expanded into preliminary design,final design,and test.These are the most significant phases for applying system safety.1.5SYSTEM CONCEPT11There are several different models by which a system can be developed.Each of these models has advantages and disadvantages,but they all achieve the same end—development of a system.These development models include:Engineering Development Model This is the standard traditional approach that has been in use for many years.This method performs the system life-cycle phases sequentially.The development and test phase is subdivided into preliminary design,final design,and test for more refinement.Under this model,each phase must be complete and successful before the next phase is entered.This method normally takes the longest length of time because the system is developed in sequential stages. Three major design reviews are conducted for exit from one phase and entry into the next.These are the system design review(SDR),preliminary design review(PDR), and critical design review(CDR).These design reviews are an important aspect of the hazard analysis types discussed in Chapter3.Figure1.5depicts the traditional engineering development model.Concurrent Engineering This method performs several of the development tasks concurrently in an attempt to save development time.This method has a higher probability for technical risk problems since some items are in preproduction before full development and testing.Spiral Development In the spiral development process,a desired capability is identified,but the end-state requirements are not known at program initiation. Requirements are refined through demonstration,risk management,and continuous user feedback.Each increment provides the best possible capability,but the require-ments for future increments depend on user feedback and technology maturation. Incremental Development In the incremental development process,a desired capability is identified,an end-state requirement is known,and that requirement is met over time by developing several increments,each dependent on available mature technology.This method breaks the development process into incremental stages in order to reduce development risk.Basic designs,technologies,anddeveloped.methods are developed and proven before more detailed designs are12SYSTEM SAFETY1.6SUMMARYThis chapter discussed the basic concept of system safety.The following are basic principles that help summarize the discussion in this chapter:1.The goal of system safety is to save lives and preserve resources by preventingmishaps.2.Mishaps can be predicted and controlled through the system safety process.3.The focus of system safety is on hazards,mishaps,and mishap risk.4.Hazard analysis is essential because hazards are the key to preventing ormitigating mishaps.5.System safety should be consistent with mission requirements,cost,andschedule.6.System safety covers all system life-cycle phases,from“cradle to grave.”7.System safety must be planned,proactive,integrated,comprehensive,andsystem oriented.。
EDA试题

二、单选题1、可擦除可编程逻辑器件的英文简称是(C )。
A.PLD B.CPLD C.EPLD D.FPGA2、FPGA 的配置存储器是( C)。
A.ROM B.RAM C.SRAM D.DRAM3、FPGA 的配置存储器是(A )。
A.SRAM B.EPROM C.EEPROM D.FLASH ROM4、复杂可编程逻辑器件的英文简称是( B)。
A.PLD B.CPLD C.EPLD D.FPGA5、现场可编程门阵列的英文简称是( D)。
A.PLD B.CPLD C.EPLD D.FPGA6、可编程逻辑器件的英文简称是( A)。
A.PLD B.CPLD C.EPLD D.FPGA二、单选题1、EDA 软件开发工具 Quartues II 要求源程序文件的名字与(B )必须一致。
A.端口名 B.实体名 C.结构体名 D.配置名2、VHDL 语言标准库中的程序包使用时不用 USE 语句显式打开调用的是(E )。
A.STD_LOGIC_1164 B.STD_LOGIC_ARITH C.STD_LOGIC_UNSIGNEDD.STD_LOGIC_SIGNED E.STANDARD F.TEXTIO3、VHDL 语言共支持四种常用库,其中哪种库是用户的 VHDL 设计现行工作库。
( C)A.IEEE 库 B.STD 库 C.WORK 库 D.VITAL 库4、描述项目所实现的逻辑功能的是(B )。
A.实体 B.结构体 C.配置 D.进程5、VHDL 语言是一种结构化设计语言,一个设计实体(电路模块)的结构体部分描述的是( B)。
A.模块的外部特性 B.模块的内部功能 C.模块的综合约束D.模块的整体特性6、关键字 CONFIGURATION 定义的是( D)。
A.结构体 B.进程 C.实体 D.配置一、单选题1、在 VHDL 语法规则中,变量是一个局部量,只能在(C )和子程序中使用。
A.实体 B.结构体 C.进程 D.配置2、下面数据中属于位矢量的是(D )。
setting.system-全局属性的设定
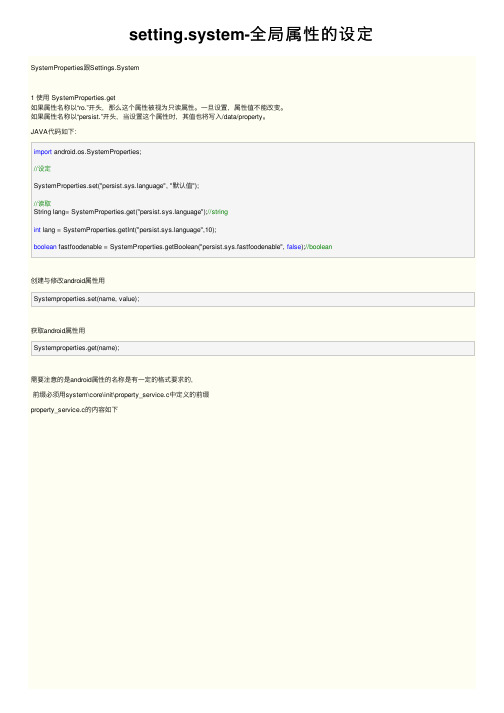
setting.system-全局属性的设定SystemProperties跟Settings.System1 使⽤ SystemProperties.get如果属性名称以“ro.”开头,那么这个属性被视为只读属性。
⼀旦设置,属性值不能改变。
如果属性名称以“persist.”开头,当设置这个属性时,其值也将写⼊/data/property。
JAVA代码如下:import android.os.SystemProperties;//设定SystemProperties.set("nguage", "默认值");//读取String lang= SystemProperties.get("nguage");//stringint lang = SystemProperties.getInt("nguage",10);boolean fastfoodenable = SystemProperties.getBoolean("persist.sys.fastfoodenable", false);//boolean创建与修改android属性⽤Systemproperties.set(name, value);获取android属性⽤Systemproperties.get(name);需要注意的是android属性的名称是有⼀定的格式要求的,前缀必须⽤system\core\init\property_service.c中定义的前缀property_service.c的内容如下property_perms[] = {{ "net.rmnet0.", AID_RADIO, 0 },{ "net.gprs.", AID_RADIO, 0 },{ "net.ppp", AID_RADIO, 0 },{ "net.qmi", AID_RADIO, 0 },{ "net.lte", AID_RADIO, 0 },{ "net.cdma", AID_RADIO, 0 },{ "ril.", AID_RADIO, 0 },{ "persist.ril.", AID_RADIO, 0 },{ "persist.ril.cfu.querytype", AID_APP, 0 },{ "mux.", AID_RADIO, 0 },{ "mux.", AID_SYSTEM, 0 },{ "mtk_telephony_mode_slot1", AID_SYSTEM, 0 }, { "mtk_telephony_mode_slot2", AID_SYSTEM, 0 }, { "gsm.", AID_RADIO, 0 },{ "persist.radio", AID_RADIO, 0 },{ "net.dns", AID_RADIO, 0 },{ "b.config", AID_RADIO, AID_SYSTEM },{ "net.", AID_SYSTEM, 0 },{ "net.", AID_DHCP, 0 },{ "dev.", AID_SYSTEM, 0 },{ "runtime.", AID_SYSTEM, 0 },{ "hw.", AID_SYSTEM, 0 },{ "sys.", AID_SYSTEM, 0 },{ "sys.powerctl", AID_SHELL, 0 },{ "service.", AID_SYSTEM, 0 },{ "wlan.", AID_SYSTEM, 0 },{ "bluetooth.", AID_BLUETOOTH, 0 },{ "dhcp.", AID_SYSTEM, 0 },{ "bwc.mm.", AID_SYSTEM, 0 },{ "dhcp.", AID_DHCP, 0 },{ "debug.", AID_SYSTEM, 0 },{ "debug.", AID_SHELL, 0 },{ "log.", AID_SHELL, 0 },{ "service.adb.root", AID_SHELL, 0 },{ "service.adb.tcp.port", AID_SHELL, 0 },{ "persist.sys.", AID_SYSTEM, 0 },{ "persist.service.", AID_SYSTEM, 0 },{ "persist.security.", AID_SYSTEM, 0 },{ "persist.service.bdroid.", AID_BLUETOOTH, 0 },{ "selinux." , AID_SYSTEM, 0 },{ "gps.", AID_GPS, AID_SYSTEM },{ "persist.af.", AID_MEDIA, 0 },进⾏系统属性设置的程序也必须有 system或root权限如果我们要添加⼀个property:例如:zhang路径:system/core/rootdir/init.rc它的内容如下on post-fs-data# We chown/chmod /data again so because mount is run as root + defaultschown system system /datachmod 0771 /data# We restorecon /data in case the userdata partition has been reset.restorecon /data# Avoid predictable entropy pool. Carry over entropy from previous boot.copy /data/system/entropy.dat /dev/urandom# Create dump dir and collect dumps.# Do this before we mount cache so eventually we can use cache for# storing dumps on platforms which do not have a dedicated dump partition.mkdir /data/dontpanic 0750 root log# Collect apanic data, free resources and re-arm triggercopy /proc/apanic_console /data/dontpanic/apanic_consolechown root log /data/dontpanic/apanic_consolechmod 0640 /data/dontpanic/apanic_consolecopy /proc/apanic_threads /data/dontpanic/apanic_threadschown root log /data/dontpanic/apanic_threadschmod 0640 /data/dontpanic/apanic_threadswrite /proc/apanic_console 1# If there is no fs-post-data action in the init..rc file, you# must uncomment this line, otherwise encrypted filesystems# won't work.# Set indication (checked by vold) that we have finished this action#setprop vold.post_fs_data_done 1在on post-fs-data ⽬录下setprop persist.sys.zhang 1//persist.sys 前缀名; 1为初始值PS:不同前缀名权限不同,这⾥就不⼀⼀说明;还有为什么要加载on post-fs-data⽬录下,这和int.rc的语法有关2 使⽤ Settings.System.putInt这种⽅式会保存变量到Settings 数据库中,飞⾏模式等的开关就是⽤这种⽅式实现的。
character set名词解释

Character Set (字符集)是一种用于编码字符的电脑数据表示形式。
它是由一组用于表示字符的数字或符号组成的集合,通常用于编码文字和符号。
字符集是计算机系统中用于表示和处理文本的基本组成部分,因此对字符集的理解和运用至关重要。
在计算机编程中,字符集通常用于表示和存储文本数据,包括字母、数字、标点符号和其他特殊字符。
不同的字符集可以包含不同的字符,以满足不同语言和文化的需求。
其中,最常用的字符集之一是Unicode字符集,它可以表示几乎所有世界上使用的字符,包括各种语言的文字、符号和表情符号等。
在网络通信和数据传输中,字符集的选择和转换也是至关重要的。
不同系统和应用程序可能使用不同的字符集,因此在数据交换和通信过程中,需要进行字符集的转换和处理,以确保数据的正确传输和解释。
总结来说,字符集是计算机系统中表示和处理文本数据的基本组成部分,对于文本的存储、传输和处理都起着至关重要的作用。
在计算机编程和网络通信中,对字符集的理解和应用是必不可少的。
个人观点和理解上,字符集的选择和处理在计算机科学领域中具有重要意义。
随着全球化和多语言环境的发展,对于不同语言和文化的字符集需求也越来越多样化。
了解和掌握字符集的概念和运用方法,对于计算机行业的从业者来说是非常重要的。
在日常使用计算机和互联网的过程中,对字符集的了解也可以帮助我们更好地处理和理解文字数据,提高工作效率和沟通准确度。
本文就字符集的概念、作用和应用进行了全面的介绍和探讨,希望读者可以从中了解字符集的重要性,并在实际工作和生活中加以应用和运用。
CharacterSet名词解释CharacterSet名词解释:字符集(CharacterSet)是一种用于编码字符的电脑数据表示形式。
它是由一组用于表示字符的数字或符号组成的集合,通常用于编码文字和符号。
字符集是计算机系统中用于表示和处理文本的基本组成部分,因此对字符集的理解和运用至关重要。
在计算机编程中,字符集通常用于表示和存储文本数据,包括字母、数字、标点符号和其他特殊字符。
神经符号原理 system 1

神经符号原理 system 1
神经符号原理系统1是一个集成了神经科学、人工智能和哲学思考的理论框架,旨在描述人类思维和行为的基本机制。
神经符号原理系统1的主要观点包括:
1. 人类思维是由神经元网络构成的,这些神经元网络通过信息传递和加工来产生思维和行为。
2. 人类思维是符号化的,这意味着思维是通过符号来表示和理解的,而这些符号在神经元网络中也有对应的物理表示。
3. 人类思维和行为是受神经系统和环境交互影响的,这种交互是通过信息传递和加工来实现的。
神经符号原理系统1提供了一种理解人类思维和行为的框架,它有助于我们更好地了解人类大脑的工作原理,以及人类如何通过符号化的思维来理解和应对世界。
同时,它也为我们提供了一种新的思路,用于开发更加智能和有效的机器学习系统。
总之,神经符号原理系统1是一个具有重要意义的理论框架,它为我们提供了一种新的视角来理解人类思维和行为的基本机制,并为人工智能技术的发展提供了新的思路。
System1专题学习之一

System1专题学习之一:System 1如何通过TDI CP(3500/22M)采集数据一、什么是TDITDI CP的英文名称是Transient Data Interface Communications Processor,解释成中文是瞬态数据接口模块,其实就是我们平时说的3500/22M模块。
如下图:3500/22M模块直接安装在3500框架的1号槽位,如下图:二、TDI CP的功能是什么TDI CP是3500框架和System 1软件之间的接口。
通过3500框架母板上的一组特殊接头,TDI CP接收3500每个通道的瞬态、报警和稳态数据(包括静态和动态数据)。
TDI CP对这些数据进行处理,存储,并通过以太网将处理后的数据传送给System 1软件。
三、TDI、System 1和机器保护系统之间的关系机器保护系统是由连接到现场传感器的多个监测模块组成的测量和保护系统。
TDI将保护系统中的数据传送给System 1软件,延伸了保护系统的功能。
System1和机器保护系统二者独立运行。
保护系统不能复位或者影响System 1软件的运行。
反之,System 1软件,TDI CP的运行,或者计算机不能影响保护系统的运行。
四、TDI数据采集的时序TDI从3500监测模块的每个通道采集静态或者动态数据,并将这些数据存放在TDI CP 的缓冲区内。
这个采集工作是持续进行的,而不会理会从System 1计算机发来的指令。
当System 1数据采集计算机从TDI CP请求数据的时候,System 1接收到数据并将这些数据从TDI CP的缓冲区中删除,以允许缓冲区进行更多更快的数据采集。
系统事件被关联到TDI CP 内的状态标签。
五、TDI采集的数据的类型分为两种数据:静态数据和动态数据。
1.静态数据静态数据描述被测量参数的量化特征。
静态数据也包括这样的可量化值,这些量化值描述了被测量参数的测量条件。
作为预测性维修目的,静态数据通常以不同形式的趋势图和当前值的形式表现出来。
system相关英语单词

system相关英语单词System-Related English VocabularyIntroduction:In today's interconnected world, computer systems play a crucial role in various aspects of our lives. Understanding system-related English vocabulary is essential for effective communication in fields such as technology, business, and academia. This article explores a range of system-related English terms, encompassing hardware, software, and networking.I. Hardware Terminology:1. Central Processing Unit (CPU):The CPU is the brain of a computer system, responsible for executing instructions, performing calculations, and managing data flow.2. Random Access Memory (RAM):RAM is a type of computer memory that provides short-term storage for data and instructions currently in use by the CPU. It allows for faster access compared to other types of memory.3. Hard Disk Drive (HDD):An HDD is a non-volatile storage device used for long-term data storage. It utilizes rotating magnetic disks to store and retrieve digital information.4. Solid-State Drive (SSD):Unlike an HDD, an SSD uses flash memory to store data. It offers faster access times and improved durability, making it more suitable for modern systems.II. Software Terminology:1. Operating System (OS):An OS is a set of programs that manages computer hardware and software resources. It provides a user-friendly interface and enables the execution of applications.2. Graphical User Interface (GUI):GUI refers to the visual interface that allows users to interact with software applications using graphics, icons, and menus rather than text commands.3. Application Software:This term encompasses programs designed for specific tasks, such as word processors, spreadsheet applications, and graphic design software.4. Firmware:Firmware refers to software programs embedded into hardware devices. It provides low-level control and is responsible for device initialization and operational functions.III. Networking Terminology:1. Local Area Network (LAN):A LAN connects devices within a limited geographic area, such as a home, office, or school. It facilitates the sharing of resources and enables communication between connected devices.2. Wide Area Network (WAN):A WAN spans large geographical areas, connecting multiple LANs through public or private networks. The internet is the most extensive WAN globally.3. Router:A router is a networking device that forwards data packets between computer networks. It directs traffic within a network and between different networks.4. Firewall:A firewall is a security device that monitors and controls incoming and outgoing network traffic. It protects against unauthorized access and potential threats.IV. Systems Development Terminology:1. Agile Methodology:Agile is an iterative approach to software development, emphasizing adaptive planning and constant collaboration between cross-functional teams.2. Waterfall Model:The waterfall model is a sequential software development process, where progress flows in one direction, similar to water cascading down a waterfall. Each phase must be completed before moving to the next.3. Software Development Life Cycle (SDLC):The SDLC is the overall process for planning, designing, developing, testing, deploying, and maintaining software systems.V. Database Terminology:1. Relational Database:A relational database organizes data into tables with defined relationships between them. It uses structured query language (SQL) to manage and retrieve data.2. Primary Key:A primary key is a unique identifier for a record in a database table. It ensures each record can be identified uniquely and provides efficient data retrieval.3. Data Warehouse:A data warehouse is a large centralized repository that stores integrated data from various sources. It facilitates data analysis and reporting.4. Data Mining:Data mining involves discovering patterns, relationships, and trends within large datasets. It assists in making informed business decisions and identifying valuable insights.Conclusion:Mastering system-related English vocabulary enhances communication and understanding in today's technology-driven world. This article has provided an overview of essential terms related to hardware, software, networking, systems development, and databases. By familiarizing ourselves with these terms, we can effectively discuss and navigate the ever-advancing realm of computer systems.。
1.测试环境变慢原因分析-20100906

测试环境变慢原因分析-20100906测试环境经常变慢,变慢时甚至无法访问登陆界面。
在系统缓慢时,连续抓取IIS进程调用栈,并无明显异常,只是所有代码的执行速度都变慢了。
2.1. 分析过程收集了一个问题出现时的Dump进行检查,线程池存在异常,一万多个工作请求被积压,请求线程名称:AsyncTimerCallbackCompletion TimerInfo@000000001XXXXXXX,看名字,是Timer的回调请求。
察看托管堆上的Timer对象,只有78个。
自己写程序模拟了一下Timer对象积压请求的过程,有两处发现:<1> Timer回调线程积压后,在ThreadPool中看到的情况,与上面一致,存在大量AsyncTimerCallbackCopletion TimerInfo@XXXXXXXX。
<2> 同一个Timer对象所积压的回调请求,TimerInfo@XXXXXXX这个名字是一样的。
这样一来,就有思路了,将当前的TimerInfo名称全部导入数据库,用名称过滤查询出来,实际只有76个Timer对象,与托管堆上的Timer对象数量基本一致。
再统计一下每个回调线程出现的次数,最高的8个回调线程,每个出现733次。
2.2. 小结系统运行缓慢时,线程池异常,有大量Timer的Callback积压,这些被积压的Callback初步判定来自由于托管堆上的70多个Timer。
3.1. 分析过程为了进一步弄清楚Timer回调线程大量积压的原因,我们需要查一下回调线程想要做什么,既然明确了有问题的对象是System.Threading.Timer,先看一下从这个对象中能挖掘到什么信息。
没什么有价值的内容,反射看一下Timer的代码Timer的构造函数,一些参数检查后,调用TimerSetupTimerSetup方法,调用timerBase.AddTimer。
timerBase.AddTimer方法,可以看到,内部创建了一个_TimerCallback对象,包含了我们感兴趣的callback参数。
abaqus中的局部坐标系2013

abaqus中的局部坐标系在abaqus中,在不同的模块中使用不同的局部坐标系类型,主要有下面几种局部坐标系:1、定义节点的局部坐标系2、定义节点自由度的局部坐标系3、单元局部坐标系1.定义节点的局部坐标系(*SYSTEM)有时在一个局部坐标系中定义节点坐标是方便的,然后再转换这些坐标值到总体坐标系中。
用户可以定义一个局部节点坐标系,Abaqus将转换和旋转局部坐标值()到总体坐标系。
在input完成后立刻完成该转换,并且该转换将施加到在定义了节点坐标系后的所有输入的节点坐标上。
【1】关键字*SYSTEM关键字*SYSTEM使用规则:先定义坐标系,再使用。
先用*SYSTEM 定义局部坐标系,然后在node definition(如*NODE关键字)里面选择定义的坐标系。
返回到整体的坐标系使用*SYSTEM+ 空白的数据行。
*SYSTEM第一行1、, global X-coordinate of the origin of the local coordinate system (point a in Figure 18.58–1).2、, global Y-coordinate of the origin of the local coordinate system.3、, global Z-coordinate of the origin of the local coordinate system.The following entries are not needed for a pure translation:4、, global X-coordinate of a point on the -axis of the local coordinate system (point b in Figure 18.58–1).5、, global Y-coordinate of a point on the -axis of the local coordinate system.6、, global Z-coordinate of a point on the -axis of the local coordinate system.第二行(optional; if not provided, the Z-axis direction remains unchanged, and the -axis is projected onto the plane):1、, global X-coordinate of a point in the plane of the localcoordinate system, on the side of the positive -axis (for example, point c in Figure 18.58–1).2、, global Y-coordinate of a point in the plane of the local coordinate system, on the side of the positive -axis.3、, global Z-coordinate of a point in the plane of the local coordinate system, on the side of the positive -axis.如果*SYSTEM中只给出一个点(原点),Abaqus假设用户只需要平移。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
•
How large can the system handle (with “acceptable” distortions)?
Assume equal signal level A1 = A2 = A
ω1 , ω2 → a1 A + a3 A2ω2 →
•
9 4
ω1 ± ω2 → a2 A2
3 a3 A3 4 3 2ω2 ± ω1 → a3 A3 4 2ω1 ± ω2 →
C-N Kuo, Fall 2005
1-12
RF Integrated Circuit Design
Characterization
Cascaded Nonlinear Stages
y1(t) = a1 * x(t) + a2 * x2(t) + a3 * x3(t) +K
y2(t) = b1 * y1(t) + b2 * y1 (t) + b3 * y1 (t) +K
Non-Linear System2
2
3
x (t )
•
Non-Linear System1
y1 (t )
y2 (t )
Cascaded IIP3
1
2 AIIP 3, t
=
1
2 AIIP 3,1
+
a12 a12b12 + +K 2 2 AIIP A IIP 3, 3 3, 2 a1 AIIP 2, 2
Pout ( dBm )
OIP3
ω1 , ω2 → a1 A + a3 A3
9 4
Pout ( dBm )
OIP2
ω1 , ω2 → a1 A + a3 A3
9 4
∆
2ω1 − ω2 →
3 a3 A3 4
Pin ( dBm )
ω1 + ω2 → a2 A2
Pin ( dBm )
IIP2
AIIP 2 = a1 a2
•
Cascade IIP2
1 AIIP 2,t
=
1 AIIP 2,1
+
C-N Kuo, Fall 2005
1-13
RF Integrated Circuit Design
3dB
Pin 2 ( dBm)
Pin 2, −3dB
•
Cross modulation
A2 (1 + m cos ωmt ) cos ω2t
A1 cos ω1t
Desired signal Large blocker Desired signal Large blocker
NLS
C-N Kuo, Fall 2005
C-N Kuo, Fall 2005
1-4
RF Integrated Circuit Design
Characterization
Linearity Analysis
• For memoryless nonlinear system (or frequency independent nonlinear), power series approach can be employed. For most weakly nonlinear system, third-order polynomial is good enough to analyze most nonlinear effects. e.g. amplifier circuit
x(t ) = A cos ω1t x(t ) = A cos ω1t + A cos(ω2t + θ 2 )
•
Æ 0dB Æ 3dB
PAR is a stochastic process in digital communication. This demands higher linearity requirement in circuit and system design.
2ω2 − ω1
ω1 + ω2
ωs ω1 ω2
C-N Kuo, Fall 2005
ωs ω1 ω2
2ω1 2ω2
3ω1 3ω2
1-8
RF Integrated Circuit Design
Characterization
Intermodulation (cont’)
• Third-order intermodulation (IMD3) • Second-order intermodulation (IMD2)
•
x (t )
Non-Linear System
y(t) = a1 * x(t) + a2 * x2 (t) + a3 * x3(t) +K
VIN VBQ +VS VT
VIN = VBQ + VS
I C = I CO e VT = I CO e
Q1
VBQ VS = I CO e VT . eVT
C-N Kuo, Fall 2005
1-3
RF Integrated Circuit Design
Characterization
Analysis Method
Available in various CAD tools • • • • Time domain numerical integration method Frequency domain harmonic balance method Circuit envelope method … Handy formulation • • Power series analysis Volterra series analysis
2rd-order IMD
3rd-order IMD
Practical consideration. When ω1 – ωs = ω2 - ω1, third-order IMD falls into frequency band of interest.
Desired signal
2ω1 − ω2
Pin ,−1dB
C-N Kuo, Fall 2005 1-6
RF Integrated Circuit Design
Characterization
Distortion in Nonlinear System (cont’)
• Desensitization & blocking G
Desired signal Large blocker Nonlinear System Desired signal Large blocker
ω1 ± ω2 ± ω3 → a3 A3
C-N Kuo, Fall 2005 1-10
3 2
RF Integrated Circuit Design
Characterization
Broadband Signal
• In wide-bandwidth systems
– Adjacent channel power ratio (ACPR)
RF Integrated Circuit Design
Characterization
System Characterization
Linearity analysis Noise figure Dynamic range Types of noise sources Calculation with noise quantities
A
nonlinear system
a1 A
1 a2 A 2 2
ω
• Gain compression
Gain (dB)
3 a3 A3 4
1 a2 A 2 2
1 a3 A3 4
DC
ω
2ω
(2-H)
3ω
(3-H)
1dB
Pin ( dBm )
⇒ A−1dB = 0.145
a1 a = 0.381 1 a3 a3
BW
C-N Kuo, Fall 2005
1-11
RF Integrated Circuit Design
Characterization
Peak-to-Average Ratio
• In multi-carrier system, peak amplitude is much higher than the average.
AIIP 3 =
4 a1 3 a3
IIP3
⇒ IIP 3( dBm ) = 9.6dB + Pin , −1dB ( dBm )
C-N Kuo, Fall 2005
1-9
RF Integrated Circuit Design
Characterization
Broadband Characterization
frequency
Harmonics Intermodulation Triple Beat
2 2 2 2 + 3 x12 x2 + 3 x12 x3 + 3 x2 x1 + 3 x2 x3 + 3 x3 x1 + 3 x3 x2
+ 6 x1 x2 x3
Twice as large as the IM3 products
x (t )
•
Linear System
