第五章Chapter5-信赖域方法
悬疑烧脑智力测试题(3篇)

第1篇【前言】在这场悬疑烧脑的智力测试中,你将踏入一个充满谜团的世界。
每个问题都隐藏着不为人知的秘密,需要你运用智慧、逻辑和洞察力来解开。
准备好了吗?让我们开始这场寻找真相的冒险之旅。
【第一幕:迷雾森林】1. 在一片迷雾森林中,有五个小屋,分别住着一位医生、一位律师、一位画家、一位作家和一位侦探。
你知道每个职业对应的小屋颜色吗?(提示:根据职业特点,推测颜色)2. 迷雾中,一位神秘人向你走来,他自称是迷雾森林的守护者。
他告诉你,每个小屋都有一把钥匙,能打开森林深处的宝箱。
你应该如何选择钥匙?(提示:考虑每个职业的特长)【第二幕:古堡之谜】3. 你来到了一座古老的城堡,城堡里住着一位富有且神秘的贵族。
他告诉你,城堡中有一幅画,藏着解开整个谜团的线索。
你该如何找到这幅画?(提示:观察城堡的布局和装饰)4. 在城堡的地下密室中,你发现了一本日记。
日记的主人是一位曾经被困在城堡中的女子。
她提到了五个神秘数字:3、7、11、13、17。
这些数字有什么含义?(提示:数字之间的关系)【第三幕:时间的陷阱】5. 你被卷入了一场关于时间的谜团。
一位科学家告诉你,他发明了一种可以倒流的时光机。
但你必须完成一个任务,才能使用它。
任务是什么?(提示:考虑时间的特性)6. 在时光机中,你回到了过去。
你发现自己身处一个古老的市集。
市集上有五个摊位,分别卖着不同的商品:珠宝、药材、书籍、武器和食物。
你应该如何选择?(提示:根据任务需求,判断商品的价值)【第四幕:记忆的碎片】7. 你发现了一个神秘的箱子,里面装满了记忆碎片。
每个碎片都记录了一个人的一生。
你需要通过这些碎片,找出一个共同点。
(提示:分析人物经历,寻找规律)8. 在分析过程中,你发现了一个关键信息:每个人的记忆碎片都缺失了一段,这段记忆被某种力量封印。
你该如何解开封印?(提示:考虑封印的特性)【第五幕:真相大白】9. 经过一系列的推理和探索,你终于找到了解开所有谜团的线索。
英雄传说 闪之轨迹攻略
英雄传说闪之轨迹攻略序章·前刚开始是以倒叙的形式,可控教官,想欣赏她S技的趁现在,因为下次加入要到第五章了。
同时可以先练习下本作的Link系统,简易上手。
A组的成员分别是男主角黎恩、劳拉、尤西斯、艾玛、盖乌斯。
参战队伍随机,可在战斗中L1键换人。
前进不久有一场练习战。
直接强制战斗三位一体攻击者R2*3,方阵兵J9*2。
不要忘记分析情报,之后走一小段路出了迷宫剧情,强制战斗玉簾*2。
战后在男主角狂喊中结束倒叙- -。
进入开章。
序章托尔茲军官学院3/31时间回到5个月前,男主角黎恩坐火车到达了托利斯塔小镇。
我们可以发现他和亚莉莎,艾略特,马奇亚斯馬奇亚斯,还有艾玛是坐同一班车来的。
在和亚莉莎展开狗血相遇剧情后,可以自由行动。
但是小镇上的店铺还未开放。
①可以在公园遇到睡觉的菲。
②在教堂遇到盖乌斯。
(注:这两人可遇可不遇)之后进入学院又看到女汉子和高富帅。
同班的同学相遇方式都全了。
结束开学典礼后,所有红色校服的学生被留下来,带到旧校舍。
莎拉开启了机关,众人倒地。
然后男亚莉莎又开始了的剧情剧情过后,全员分成了几路,分配给主角的是艾略特和盖乌斯。
第一张地图有两个宝箱,分別是:地水火风时空幻之耀晶石x50和岩石之刺(回路)所以多使用艾略特的恢复技能。
在第一张地图快结束的时候,马奇亚斯加入。
主线任务:配送导力器(AP4)报酬:无时限:4/18①到技术栋乔治领取任务,分别要去三个地点②到主校舍2楼的家庭料理室,在这里还能获得「料理手册」,之后可以开始做料理了,1楼戴眼镜的汤玛斯教官专门收集古怪料理,可以在以后做出后交给他。
而第一学生宿舍门口的女仆罗德是收集独门料理。
这时和她对话还能获得女仆罗德的人物信息「学习做菜」③到小镇的当铺《密休特》,以后可以在这里兑换不错的道具*2周目后可以在这里用U物质换塞姆利亚石的碎片④到小镇西南地图的广播台⑤完成后,回去乔治交任务。
BOSS:通缉魔兽:人面鸟属于飞行系的,亚莉莎攻击有特效。
第8讲信赖域方法

对于二次模型函数 ,定义其柯西点: 对于二次模型函数(2),定义其柯西点 二次模型函数
s c = −τ k k ∆k gk , gk
其中, 其中
T 1, if g k Bk g k ≤ 0; gk 3 τk = min ∆ g T B g ,1 , or. k k k k
7
5.信赖域算法 .信赖域算法 Step1. 给 出 初 始 点 x0 , 信 赖 域 半 径 的 上 界 ∆ , ∆ 0 ∈ ( 0, ∆ ) , 0 ≤ ε ,
0 < η1 ≤ η 2 < 1, 0 < γ 1 ≤ 1 < γ 2 , k := 0 .
Step2. 如果 g k ≤ ε ,停止 停止. 停止 Step3. (近似 求解子问题 得到 sk . 近似)求解子问题 近似 求解子问题(2),得到 Step4. 计算 f ( xk + sk ) 和 rk .令 令
xk + sk , if rk ≥ η1 . xk +1 = or. xk ,
Step5.校正信赖域半径 令 校正信赖域半径.令 校正信赖域半径
∆ k +1 ∈ ∆ k , min {γ 2 ∆ k , ∆}
∆ k +1 ∈ ( 0, γ 1∆ k ] ∆ k +1 ∈ [γ 1∆ k , ∆ k ]
if rk < η1; if rk ∈ [η1 ,η2 ) ;
if rk ≥ η 2 .
8
5.信赖域算法 .信赖域算法 Step6. 产生 Bk +1 ,校正 q( k ) ,令 k := k + 1, 转 Step 2. 很成功迭代: 很成功迭代 成功迭代: 成功迭代 不成功迭代: 不成功迭代 算法参数选择建议: 算法参数选择建议
(运筹学与控制论专业优秀论文)一类最优化问题的算法设计

知识水坝为您提供优质论文
承诺书
本人郑重声明:所呈交的学位论文,是本人在导师指导下,独立 进行研究工作所取得的成果。尽我所知,除文中已经注明引用的内容 外,本学位论文的研究成果不包含任何他人享有著作权的内容。对本 论文所涉及的研究工作做出贡献的其他个人和集体,均已在文中以明 确方式标明。
本人授权南京航空航天大学可以有权保留送交论文的复印件,允 许论文被查阅和借阅,可以将学位论文的全部或部分内容编入有关数 据库进行检索,可以采用影印、缩印或其他复制手段保存论文。
1.3 本文的主要内容
本文主要研究一类具有特殊形式的最优化问题,求解这一类最优化问题的全 局最优解,并应用到求解互补问题上。虽然目前已经有很多算法,但是我们考虑 到本最优化问题的约束条件是特殊的,因此可以利用约束条件的特殊性构造更为 简单有效的算法。
本文提出了一类新的函数,将它定义为半正定函数。利用这类函数将原问题; 分别转化为无约束最优化和含等式约束的最优化问,并分别设计了算法,进行了 数值实验,验证了算法的有效性。为了给出问题的全局最优解,我们又研究了算 法子问题的全局最优化算法,利用填充函数法来求解子问题。这样就保证了前面 设计的算法可以求得问题的全局最优解。最后,针对约束最优化问题(P),提出 了拟填充函数的概念,构造了一类拟填充函数并设计了算法。具体内容如下:
In this article we propose a new type of function, which is called a semi-positive function. We use this function to make another function, then we can turn the original problem into another one. We give algorithms and numerical results. Then we investigate the sub-problem. Also we propose the definition of quasi-filled function. We propose a quasi-filled function and design algorithm. It mainly contains the following six chapters:
信赖域方法

由于最优曲线的确定需要计算矩阵 的所有 特征值和特征向量,相当费时.
折线法在于用低维空间内满足一定要求的 折线,记为 代替最优曲线.通过求解:
信赖域半径的选择
根据模型函数 对目标函数 来调整信赖域半径
的拟合程度
对于问题(1)的解 定义比值:
它衡量模型函数 程度.
与目标函数 的一致性
注:(1) 越接近于1,表明模型函数与目标
函数的一致性程度越好,可以增大 以扩大 信赖域.
(2)
不接近于1,可以保持 不变.
(3) 接近于零或取负值,表明模型函数与目标
例1:设
在当前点
试用双折线法求
解:
由于
计算 有:
由于
使得 得 所以
故取双折线步长为:
解二次方程 因此
基本思想
牛顿法的基本思想是在迭代点 附近用二次
函数逼近
并以 的
的极小点 修正 得到:
以上方法只能保证算法的局部收敛性,为了建
立总体收敛性算法,我们采用了线搜索技术.虽然
这种策略是成功的,但它有一个缺点,即没有进一
步利用二次模型.
基本思想
牛顿法的基本思想是在迭代点 附近用二次
函数逼近
并以 的
的极小点 修正 得到:
信赖域子问题折线法基本思想如果令信赖域的半径在区间内连续变化则问题1的解在空间中形成一条光滑的连续曲线记为此时问题1等价于在信赖域内在最优曲线上确定一点使二次函数取极小即
信赖域方法
信赖域方法是求解最优化问题的另一类有效 方法.其最初的设计思想可追溯至Levenberg Marq和uart对Gauss-Newton法的修 正.线搜索方法是把一个复杂的最优化问题转化 成一系列简单的一维寻优问题.信赖域方法是把 最优化问题转化为一系列相对简单的局部寻优 问题.
最优化方法信赖域方法

最优化方法信赖域方法Trusted Domain Method of Optimization Methods一、概述信赖域(Trusted Domain)法是一种针对多目标最优化问题的优化方法,属于启发式优化技术,又被称为受信域法(Credible Domain)法或者受信域增强法(Credible Domain Enhancement)。
它由A.K.Chentsov在1980年提出,目前已经在工业优化、控制优化、混合模糊优化等领域有广泛的应用。
信赖域法使多目标最优化问题中的搜索变得更加有效和快捷,可以很好地处理多目标最优化问题中的非凸性和高维问题,使最优解更容易被获取。
二、原理信赖域方法优化的原理是:在解空间中划分子空间,在每个子空间中进行最优优化,同时进行领域大小的优化,以找到最优解。
(1)划分的子空间划分的子空间由一组不可分割的解空间,即称为“信赖域(Trusted Domain)”确定,有一种收敛性的在同一信赖域上的解空间集合,该信赖域中必须包含一个或多个最优解点。
(2)之分的子空间有效性在信赖域中,有一种收敛性的解空间,该解空间必须包含一个或多个最优解点,且此处解的收敛性可以满足要求。
由此可以看出,划分的子空间有效的充分利用解空间,能够使对最优解的搜索效率更高,更快地找到最优解。
(3)领域大小的优化在划分解空间时,信赖域方法重点考虑领域大小的优化,以缩小搜索空间大小,并引导搜索过程朝最优解的方向发展。
三、应用1.工业优化信赖域方法已经在工业优化领域得到应用,使多目标工业优化问题中的搜索更加有效和快捷,可以很好地处理多目标最优化问题中的非凸性和高维问题,使最优解更容易被获取。
2.控制优化由于信赖域方法能够有效地处理多目标非凸性和高维问题,因此已经在控制优化中得到应用,用于设计准确性好的控制系统。
3.混合模糊优化信赖域方法在混合模糊优化领域也有应用,可以用来解决特殊类型的模糊控制优化问题,来有效地提高优化中的效率和准确性。
《火焰纹章if》一周目困难难度规程攻略攻略_全通
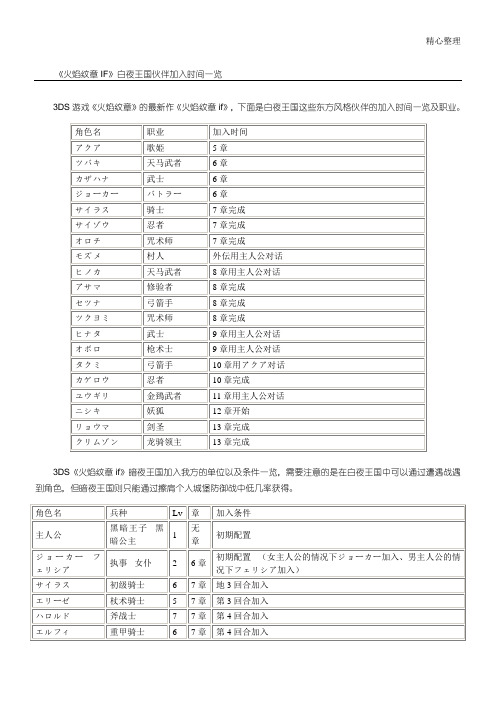
15
14章
主人公与フランネル对话
ギュンター
高级骑士
10
15章
初期配置
フェリシア
ジョーカー
女仆
执事
13
16章
出击准备时加入
(男主人公的情况下ジョーカー加入、女主人公的情况下フェリシア加入)
マークス
圣骑士
4
16章
初期配置
アシュラ
冒险者
2
16章
完成本章后选「いいえ」。
若选择「はい」则不会加入,取而代之获得移动+1的鞋子
在自宅中可以实现搞基和百合,增长人物的好感度开启支援对话。地图上按L键可以进入第一人称视角观看风景,但不能移动非常遗憾。斗技场战斗是
关于龙脉值的获取,这里暗夜的同学可能要悲剧了,因为白夜可以通过遭遇战获得龙脉,而且花钱可以开启遭遇战。当然也可以通信后通过拜访伙伴的城获得一点。前期基本建造一个房屋都是消耗一点龙脉,要升级建造可能就要花费三点以上。
サイラス
初级骑士
6
7章
地3回合加入
エリーゼ
杖术骑士
5
7章
第3回合加入
ハロルド
斧战士
7
7章
第4回合加入
エルフィ
重甲骑士
6
7章
第4回合加入
モズメ
村人
1
外伝
外传モズメ 主人公与モズメ对话
オーディン
暗黑法师
5
8章
第2回合加入
ゼロ
盗贼
8
8章
第2回合加入
アクア
歌姫
1
9章
初期配置
ニュクス
暗黑法师
9
9章
主人公与ニュクス对话
阿玛迪斯战记最详细攻略

阿玛迪斯战记最详细攻略文章列表:一、关于隐藏关的进入方法。
二、《阿玛迪斯战记》角色点评三、战棋版英雄无敌——《阿玛迪斯战记》流程攻略, 女主角全篇四、《阿玛迪斯战记》全道具功能一览五、魔兽转职表;完美结局;龙(Dragron)的礼物;碧绿原石、漆黑原石、纯白原石这三块石头取得法。
六、LOB中获得物品的简单功略七、无限复制道具大法八、补充关于“龙的礼物”九、阿玛迪斯战记基本资料十、各属性相关内容资料一关于隐藏关:1、网上盛传的隐藏关达成条件(但实践证明是不行的)一、触发黑暗圣书事件1.在第十八章雷雨中时以最快的速度消灭第一波,及第二波魔兽,此时留一些人在NPC 的附近,但不能站在桥上,等到一定回合,会出现八只鸟身女魔,这些留在桥上附近的人必需把那八只解决,等到消灭所有魔兽后,桥上的NPC会告诉主角们,城里有一个疯术士。
2。
进入城后和术士对话,术士会跟欧森巴哈相认,并传达「黑暗圣书」事件.二、解救皇帝事件1。
在接近皇帝前,将部队分成二队,一队走左边,一队走右边,走右边的人将皇帝打到低于2000时,基尔巴特便会出会,此时右边的队伍最好限制皇帝的行动.2。
走左边的人把基尔巴特消灭后,皇帝便会清醒,众人便将黑暗圣书的事件告知。
三、放走圣骑士事件1。
过关时选择放走圣骑士四、打倒法王事件1。
当基尔巴特攻击我方人员时,我方只能忍耐,此时可派欧兰朵以特技降低基尔巴特的魔攻,这样他施放魔法时,我方人员只会损伤600而已,但千万不能打死他,因为一打死他,法王便会开始行动.2.消灭地毯上的魔兽后,我方一人走上台阶,此时圣骑士会赶过救驾,此时派会使用限制行动的我方人员,把圣骑士冰冻。
3。
这时我们怎么打法王,他都不会反击,也不会行动,我方尽情砍杀法王,等打死后,圣骑士会冲过来抵挡最一击。
4.圣骑士说:「法王…。
我就知道您会清醒的……」,这时法王十分的悲恸,和主角谈起黑暗圣书的事,原来不是基尔巴特搞的鬼,而是枢机主教的阴谋,此时背景音乐开始紧张,原来黑暗圣书放在后山,大家要一鼓作气攻打后山。
关于楔形信赖域半径更新的两种方法

C m u r ni ei d p laos op t g er g n A pi t n计算机 工程 与应凤霞, 周庆华, 张亚蕊, 耿 燕
X F n xa Z U e g i, HOU Qig u , HA au , E a n h aZ NG Y riG NG Y n
sd s te rdu p ae r ls h v to g if e c n te p roma c fa lo tm . i a e ,a e t e dsd a - ie , a is u d t ue a e a s n n u n e o efr n e o ag r h I t s p p rfc d wi t ia v n h r l h n i n h h h
XU F n xa Z e g i, HOU Qig u , HANG Y r ie 1 w to s O d e tu trgo a is u d t. o ue n i nh a Z a u, ta. o meh d N we g r s ein rdu p aeC mp tr E g- T n eig a d Ap l a o s2 1 ,7 3 )3 -8 ern n pi t n ,0 1 4 (0 :53 . ci
河北大学 数学与计算机学 院 , 河北 保定 0 10 702
解等式约束规划的信赖域SQP滤子方法

严格局 部解 时 , 全牛 顿步 可能会 使 目标 函数值 和 约束 违 反度 上 升 , 而不 被 滤子 接 受 , 是破 坏 了算 法 的 完 从 于
收敛性 . 文对 文献 [ 3中的信 赖域 S 本 3 QP滤子 方 法进 行 了修 改 : 果 完全 步不 被接 受 , 以通 过 一个 二 阶 校 如 可
能 是 一 个 超 线 性 收敛 步 , 是 当 迭 代 点 充 分 靠 近 原 问题 的严 格 局 部 解 时 。 全 牛 顿 步可 能会 使 目标 函 数 值 和 约 束 但 完 违 反 度 上升 。 而 不 被 算 法 接 受 , 是破 坏 了 算法 的 收 敛 性 . 出 一 种 修 改 后 的 信 赖 域 S P滤 子 算 法 , 完 全 步 从 于 给 Q 当 不 被 接 受 时 . 算 法 进 行 二 阶校 正 (OC , 以 减 小 其 不 可 行 性 . 改 后 的 算 法 可 以 避 免 Maao 效 应 。 算 法 达 对 S )可 修 rts 使
到局部超线 性收敛. ‘
关 键 词 : QP方 法 ; 赖 域 ;滤 子 ; 阶 校 正 ;Maa s 应 ;局 部 收 敛 S 信 二 rt 效 o
中 图 分 类 号 : ) 2 . ( 2 12 文 献标 识 码 : A 文 章 编 号 :1 0 - 7 5 2 O ) 1 o O 一 5 0 1 8 3 (o 8 O 一 O 1 O
基 金 项 目 :国 家 自然 科 学 基 金 资助 项 目 (0 7 1 7 1513)
作 者 简介 :王 华 (9 9 ) 女 , 东省 菏 泽 市 人 , 济 大 学 博 士 研 究 生 . 17 一 , 山 同 主要 从 事 非 线 性 规 划 研 究
维普资讯
信赖域方法实验报告

信赖域方法实验报告引言信赖域方法是一种用于数值优化问题的数值方法,其主要应用于非线性优化问题。
本实验旨在探究信赖域方法在解决优化问题中的适用性和效果,并通过实验结果分析其优缺点。
实验内容本实验使用Python编程语言实现了一个简单的信赖域方法算法,并使用一组标准测试问题来验证该算法的正确性和性能。
这些测试问题包括标准的最小化和最大化问题,涵盖了不同类型的非线性函数。
实验步骤1. 信赖域方法概述首先,我们先对信赖域方法进行了概述。
信赖域方法是一种迭代算法,其基本思想是在每一步迭代中,通过在局部区域内逼近目标函数的二次模型来求解更新方向,并在每次迭代中更新信赖域半径以控制步长。
2. 算法实现接下来,我们实现了信赖域方法的算法。
该算法的输入包括目标函数、初始点、信赖域半径等参数,输出为最优解。
具体实现过程中,我们使用了Python中的数值计算库来进行优化计算。
算法的核心步骤包括计算目标函数的一阶导数和二阶导数,以及利用这些导数计算二次模型的系数。
3. 标准测试问题的求解我们选择了一组标准测试问题来验证算法的正确性和性能。
这些测试问题包括无约束的最小化和最大化问题,以及带有约束的优化问题。
通过将这些问题输入我们实现的信赖域方法算法,我们得到了最优解,并计算了相应的函数值。
4. 实验结果分析最后,我们对实验结果进行了分析。
从结果可以看出,在大多数情况下,我们的信赖域方法算法能够得到最优解,且在较短的时间内收敛。
然而,对于某些问题,算法可能会陷入局部最优解,无法达到全局最优解。
此外,算法的收敛速度也可能受到信赖域半径的选择影响。
结论本实验通过实现信赖域方法算法,并使用一组标准测试问题进行了验证和分析。
实验结果表明,信赖域方法是一种有效的数值优化方法,能够在较短的时间内得到最优解。
然而,算法的表现仍受到问题的特性和信赖域半径的选择的影响。
因此,在实际应用中,需要根据问题的特点和要求合理选择信赖域半径以获得更好的优化结果。
圣光之魔石游戏攻略

序章路尼斯陷落路尼斯王宫内,传令兵向国王通报了敌军即将入侵的消息,而出国请求援兵的王子艾弗拉姆也没有了音信。
国王无可奈何的下令让圣骑士塞图(セド)保护携带着王家腕轮的公主艾莉柯(エイリ—ク)逃出王都,一个人留下来面对侵略军……逃出城外的一行人又遇上了格蓝多的龙骑士团的伏击,其中的首领居然是格蓝多帝国军将之一的“月长石”维尔达,因为不敌,塞图只能带着艾莉柯暂时逃离,两人决定先赶往佛雷利亚,而塞图也将王家剑(系列作里领主都用这个武器)交给了艾莉柯,这时侵略军追来,艾莉柯出击迎敌。
胜利条件:BOSS击破。
战斗:可以说是上手关了,三个敌人都交给女主角吧。
因为王家剑比较珍贵,所以建议把塞图身上的钢之剑交给艾莉柯,需要留意的是如果走近BOSS的攻击范围他就会主动出击,如果之前的战斗女主角有损失HP最好补充一下。
经过一场战斗,艾莉柯终于振作精神,决定勇敢的面对一切。
第一章脱出行侵略的战火也烧到了佛雷利亚,公主达娜(タ—ナ)正在穆兰(ミュラン)城焦急的等待着艾莉柯的到来,结果却等来了侵略军,守城的将士被打败后,达娜也成为了人质,艾莉柯和塞图赶到发现这里已经被敌人占领了,艾莉柯给塞图讲述她听到的格蓝多军曾经做出的种种残酷之事,并请求他协助自己将打倒占领这里的敌人。
胜利条件:城门制压战斗:基本上没什么难度,第二回合开始:布莱茨(フランツ)和基利亚姆(ギリアム)加入,第五回合开始右下有敌人增援,利用地形妥善作战便可,布莱茨与塞图有剧情对话。
战斗结束后,艾利柯救出了达娜,感动的会面后,一行人决定先前往王都。
见到了贤王海德,他对格蓝多的侵略行为也非常不满,不过令艾莉柯高兴的是,哥哥艾弗拉姆并没有失去消息,宾德告诉她艾弗拉姆正在前线英勇的孤军奋战中,于是海德决定让凡妮莎,莫尔达,基利亚姆和输送队协助艾莉柯前往格蓝多的兰哈鲁城支援奋战中艾弗拉姆,达娜很担心艾莉柯的此行,但艾莉柯坚决的决定一定要前去,因为父亲和兄长都离开了她身边,很多事情都等待着她的面对……第一章结束:凡妮纱(天马骑士)和莫尔达(神官)加入,得到5000G。
炎龙骑士团外传风之纹章攻略

炎龙骑士团外传---风之纹章电玩族的家提供索尔完成了2代的冒险旅行后,回到罗特帝亚继承了王位,虽然励精图治,使得罗特帝亚成为当时最强的军事大国,但是由于索尔天性豪爽刚直,与宫廷中那种庄重的气氛始终格格不入,隐忍了十多年后,终于忍不住来个“离家出走”,溜到马拉大陆去透透气,哪知这个举动却给阴谋家带来了可乘之机。
他们派人假冒索尔,混进了罗特帝亚,将罗特帝亚搞得一团糟,还到处派人搜杀索尔,结果索尔身中巨毒,危在旦夕!所幸危急之时,遇见了男主角兰迪斯.兰迪斯即时伸出援手,救出了索尔 .这个事件是巧遇,也是命运之神的安排.一个是旧时代的英雄,一个是新时代的勇者 .两个人在生命的旅途中交会,彷彿两棵巨星一般,瞬间发出闪耀的光芒.索尔在疗伤的日子中,知道兰迪斯的父亲已经去世,母亲也在幼年时失踪,于是劝说兰迪斯与他结伴同行.在索尔的殷勤劝诱下,兰迪斯答应离开故乡,踏上未知的探险旅程......第一章英雄之出发秘密商店密码: 无开始时,索尔因中毒生命值较低,需用兰迪斯身上的解毒剂给他解毒。
然后就是索尔大发神威啦,冲到敌人前面当你的“肉盾”,对敌人是一剑消灭一个。
本关的战斗很简单,重要之处是你如何从索尔的手中抢到经验值。
几个树洞中都有宝物。
第二章恶魔之窟秘密商店密码: 无我方加入人物:尤利安本法关依然是从索尔的手中抢经验值,由于尤利安会治疗法术,应好好利用。
第三章石巨神的封印秘密商店密码: 无我方加入人物:亚克由于地形狭窄,加之石巨神会从路边出现,因此队员之间不应距离太远,以免被包围。
挣得经验值依然是重点。
第四章谜之女秘密商店密码: 84268我方加入人物:法连娜本关可让兰迪斯等在前面当“肉盾”,一面用法连娜杀伤面积大的电系法术打,一面用尤利安的治疗术医,挣经验值很爽啊。
求解信赖域子问题的混合双割线折线法

阵的 f( ) 对称矩阵 , △ 是 信 赖 域 半 径. 当 △ 变
化时 , ( 1 ) 的解 6 形 成 一 条 空 间 曲线 , 称 为 最 优 曲线 .
的特 征值 来构 造对 称正定 阵 G . 现不 妨记 D 的特 征 值为 A 1 , 人 2 , …, A , P , P , …, P 为 D 对 应 于特 征 值 A , A , …, A 的特 征 向量 , 令P =( P 。 , P , …, P ) T .
( d , d 2 , …d ) ,
1
情况 , 提 出一 种 混 合 双 割 线 折 线 法 解 决 信 赖 域 子
问题 .
A,
A, >0
1 . 对称 正定 矩 阵 G 的构 造
d = 1 一e一 A.
t
A < 0 , 1 2
A =0
2 0 1 3年 4月
江苏 教育 学 院学报 (自然科 学)
J o u r n a l o f J i a n g s u I n s t i t u t e o f E d u c a t i o n( N a t u r a l S c i e n c e s )
当日 不正定 时 , 利用 H e s s i a n阵 的特 征值 性 质 , 构 造对 称正 定 阵 G , 有 一G g 是 拟牛顿 方 向. 设 最优 曲线 的参数 方程 为 :
= 一
( 一 6 ) , 其中l 的取值 使 I I l l=△ ;
B = L D L . ( 3 ) 基于 D 与 B 具 有 相 同 的惯 性 ] , 本文利用 D
1
一
m i n q ( ) = g 6 + 寺6 日 , s . t .1 l 6 l I ≤△ ( 1 )
一个带线搜索的自适应信赖域算法

① 收稿 日期 : 1 o D 2 2一 3一 8 0 基金项 目: 国家 自 然科学基金 重点 资助项 目(0 7 07 . 16 15 ) 作者简介 : 苗荣 (18 一)。 , 95 女 河南焦作人 , 河南理工大学硕士 , 研究方 f为最优化理 论与应用. 句
考虑无约束优化问题 :
mi ) ∈R n ,
其中 ) 是二阶连续可微 函数. 通常 的信赖域方 法在 每步迭 代求 子 问题 :
一
1
一
mi ks 5+ nq( )=
厶
Gs
() 1
st 1 『 . l I≤△ . s 其 中 s: 一 = )g 为 ) , 在 处 的梯
个 自动确定初始信赖域半径 的 IR T R算法 , 其基本 思想是通过近似模型 ( ) 目标 函数 粕 +d d 和 ) 沿负梯度方向的近似程 度 , 调节初 始信赖域半径. H i 提出当前迭代的信赖域半 径是关 于比值 e 的函数与 上次迭 代 的步 长 l ¨ I 积. a I d l乘 F n与
度 , ER 是 ) 钆 处 的 Hes n矩 阵或 其 在 si a
带线搜索的非单调 自动确定信赖域半径的算法 , 并
在一定条件下证 明其收敛性.
1 算 法
令
a =。 m x { }k=0 12 … , 中 O , , ,, 其
近似 , △ 为信赖 域半径. 近几年 出现 了非 单调算 法 【 ]数值结果表明非单调算法 比单调算法有了 l , 很大的改进.在信赖域方法的实现过程 中, 信赖域 半径的选取是一个关键因素 , 它直接决定着当前迭
信赖域算法 参数解释

信赖域算法参数解释
信赖域算法是一种求解非线性优化问题的数值方法。
以下是信赖域算法的参数解释:
初始点:算法开始时选择的初始解,用于启动迭代过程。
信赖域半径:在每次迭代中,给定一个信赖域,这个信赖域一般是当前迭代点的小邻域。
信赖域半径的大小根据试探步的好坏进行调整,粗略地说,如果试探步较好,在下一步信赖域扩大或者保持不变,否则减小信赖域。
目标函数:在优化问题中需要最小化或最大化的函数。
在信赖域算法中,目标函数被用于评估迭代步骤的效果。
梯度:目标函数在当前迭代点的梯度,用于确定搜索方向和步长。
子问题:在信赖域内求解的近似二次函数极小化子问题。
通过求解子问题,可以找到一个可能使目标函数下降的解。
下降量与近似问题的下降量:通过比较真实下降量和近似问题的下降量,可以评估近似解的质量。
接受准则:根据下降量和近似解的质量等因素,确定是否接受当前试探步,以及如何调整信赖域半径。
通过这些参数和调整策略,信赖域算法在非线性优化问题中寻找一个合适的近似最优解。
请注意,以上解释是基于一般的理解和常见的术语,具体的参数和解释可能会根据具体问题和算法实现有所不同。
无约束优化问题的信赖域半径趋于0的信赖域方法

1 提 出 问 题
考 虑 无 约 束 问 题 mif z , n ( )
∈ R
比值 在 决 定 是 否 接 受 试 探 步 以 及 如 何 调 节 信 赖 域 半 径 方 面 起 着 关 键 作 用 。粗 略 的 说 , 越 大 , 明 日 说
标 函数 下 降越多 , 的点 +d 也就 越好 , 以 胂 新 所
赖 域 子问题 来确定 d :
1
具体 通 过 下 面 的 公 式 来 确 定 下 一 个 迭 代 点
Z^ 1 : +
a V +寺 ^ () r n gd i k Bd一 ^d
dE R
f + d , 若 r ≥ f1 ^ 。
St ..
1 l l △ l≤ d
第 3 O卷 第 6期 2 1 0 0年 1 2月
桂 林 电 子 科 技 大 学 学 报
J u n lo ii ie st f Elc r n c T c n l g o r a fGuln Un v r iy o e t o i e h o o y
Vo1 O, O. .3 N 6
如下 :
一 ' 1 I z l
L
只 『 其也 1 他 . l
J
其 中 : 一 Vf( g x ),B ∈ R 对 称 ,B 为 ,( z)的 He s s e阵 在 点 z 处 的 近 似 , > 0为 信 赖 域 半 径 。 △
其 中 : ∈ E , )为常数 , 赖域半 径 △ 的选 取规 则 o1 信 c l ^l,4 ^ 若 < c 3 l l CA , d 2
A b ta t I hi ap r we pr s nta ne t u tr gin e h or un o ta n d optm iat ih he tu t r gin s r c :n t s p e , e e w r s e o m t od f c ns r i e i z i w t t r s e o on c nv r i g t e o T h i f no o e g n O z r . e ads o nm on o us t c nia e ot no e h c lr duc he al rt om pu a i e t go ihm c t ton. The r os d l — p op e ago
信赖域法

if rk 2 .
6
5.信赖域算法 Step6. 产生 Bk 1 ,校正 q k ,令 k : k 1, 转 Step 2. 很成功迭代: 成功迭代: 不成功迭代: 算法参数选择建议:
1 1 0.01,2 0.75, 1 0.5, 2 2, 0 1, 或者 0 g0 . 10
(2)
其中,gk 是目标函数 f ( x) 在当前迭代点 xk 处的梯度,Bk R nn 对称, 是 f ( x) 在 xk 处Hessian阵的近似. k 为信赖域半径, s 为待求变量. 当 k 变化时, s 的解形成一条空间曲线, 称为最优曲线. Powell [1970 ]给出了求解(2) 的单折线法, 当 Bk 可逆时,用
rk 2 ,
k 1 k , 信赖域扩大;
rk 1 ,2 ;
rk ,
信赖域缩小.
7
7.解信赖域子问题 信赖域方法在每步迭代中求解下列形式的子问题:
1 T k T min q s f ( x ) g s s Bk s k k 2 , s.t. s k 2
xk sk , if rk 1 xk 1 . or. xk ,
Step5.校正信赖域半径.令
k 1 0, 1 k k 1 1 k , k
if rk 1; if rk 1 ,2 ;
k 1 k , min 2 k ,
Hale Waihona Puke xk 1 xk sk ,
否则,
xk 1 xk .
新的信赖域的大小取决于试探步的好坏,粗略地说,如果 试探步较好, 在下一步信赖域扩大或保持不变, 否则减小信赖域 .
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Lingfeng NIU, FEDS
Chapter V
11/63
Outline of the Trust-Region Approach
Define the ratio ρk =
Lingfeng NIU, FEDS
Chapter V
7/63
Outline of the Trust-Region Approach
To obtain each step, we seek a solution of the subproblem 1 T minn mk (p) = fk + gk p + p T Bk p, p∈ 2 where ∆k > 0 is the trust-region radius. s.t. p ≤ ∆k , (3)
Lingfeng NIU, FEDS
Chapter V
9/63
Outline of the Trust-Region Approach
The size of the trust region is critical to the effectiveness of each step. If the region is too small, the algorithm misses an opportunity to take a substantial step that will move it much closer to the minimizer of the objective function. If too large, the minimizer of the model may be far from the minimizer of the objective function in the region, so we may have to reduce the size of the region and try again.
2
f (xk + tp)p,
(1)
where fk = f (xk ), gk = f (xk ) and t ∈ (0, 1).
Lingfeng NIU, FEDS
Chapter V
6/63
Outline of the Trust-Region Approach
In this chapter, we will assume that the model function mk that is used at each iteration xk is quadratic. Moreover mk is based on the Taylor-series expansion of f around xk , which is 1 T f (xk + p) = fk + gK p + p T 2
Lingfeng NIU, FEDS
Chapter V
10/63
Outline of the Trust-Region Approach
In practical algorithms, we choose the size of the region according to the performance of the algorithm during previous iterations. If the model is consistently reliable, producing good steps and accurately predicting the behavior of the objective function along these steps, the size of the trust region may be increased to allow longer, more ambitious, steps to be taken. A failed step is an indication that our model is an inadequate representation of the objective function over the current trust region. After such a step, we reduce the size of the region and try again.
6/63
Outline of the Trust-Region Approach
When Bk = 2 f (xk ), the approximation error in the model function mk is O( p 2 ), so this model is especially accurate when p is small. This choice Bk = 2 f (xk ) leads to the trust-region Newton method. In the other part, we emphasis the generality of the trust-region approach by assuming little about Bk except symmetry and uniform boundedness.
Lingfeng NIU, FEDS
Chapter V
1/63
Outline
Outline of the Trust-Region Approach Algorithms Based on the Cauchy Point Global Convergence Iterative Solution of the Subproblem Local Convergence of Trust-Region Newton Methods Other Enhancements Notes and References
Lingfeng NIU, FEDS
Chapter V
3/63
Outline of the Trustห้องสมุดไป่ตู้Region Approach
Line search methods and trust-region methods both generate steps with the help of a quadratic model of the objective function, but they use this model in different ways. Line search methods use it to generate a search direction, and then focus their efforts on fining a suitable step length α along this direction. Trust-region define a region around the current iterate within which they trust the model to be an adequate representation of the objective function, and then choose the step to be the approximate minimizer of the model in this region. In effect, they choose the direction and length of the step simultaneously. If a step is not acceptable, they reduce the size of the region and find a new minimizer. In general, the direction of the step changes whenever the size of the trust region is altered.
Lingfeng NIU, FEDS
Chapter V
8/63
Outline of the Trust-Region Approach
The classification of trust-region methods are decided by the choice of Bk and norm for trust region in the model (3). For example, If Bk = 0 in (3) and define the trust region using the Euclidean norm, the trust-region method identifies with the steepest descent line search approach; If Bk is chosen to be the exact Hessian 2 fk , the resulting approach is called the trust-region Newton method; If Bk is defined by means of a quasi-Newton approximation, we obtain a trust-region quasi-Newton method.
where Bk is some symmetric matrix. The difference between mk (p) and f (xk + p) is O( p 2 ), which is small when p is small.
Lingfeng NIU, FEDS
Chapter V
Chapter V: Trust-Region Methods
Lingfeng NIU
Research Center on Fictitious Economy & Data Science, Graduate University of Chinese Academy of Sciences niulf@
