AAA认证
华为&思科 AAA认证解析
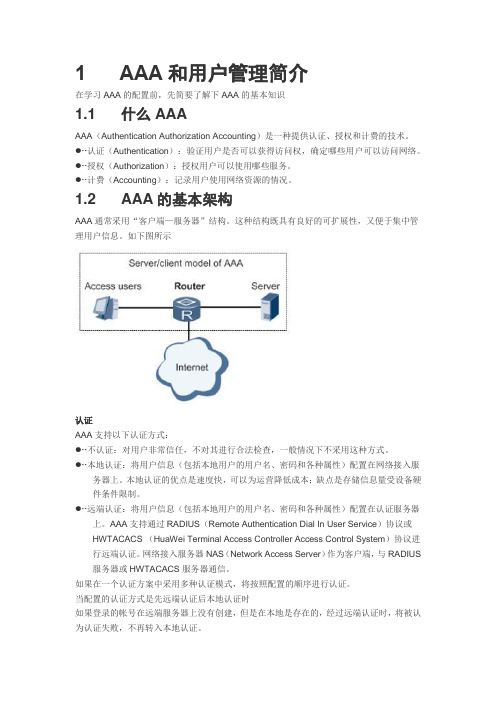
1 AAA和用户管理简介在学习AAA的配置前,先简要了解下AAA的基本知识1.1 什么AAAAAA(Authentication Authorization Accounting)是一种提供认证、授权和计费的技术。
●∙∙认证(Authentication):验证用户是否可以获得访问权,确定哪些用户可以访问网络。
●∙∙授权(Authorization):授权用户可以使用哪些服务。
●∙∙计费(Accounting):记录用户使用网络资源的情况。
1.2 AAA的基本架构AAA通常采用“客户端—服务器”结构。
这种结构既具有良好的可扩展性,又便于集中管理用户信息。
如下图所示认证AAA支持以下认证方式:●∙∙不认证:对用户非常信任,不对其进行合法检查,一般情况下不采用这种方式。
●∙∙本地认证:将用户信息(包括本地用户的用户名、密码和各种属性)配置在网络接入服务器上。
本地认证的优点是速度快,可以为运营降低成本;缺点是存储信息量受设备硬件条件限制。
●∙∙远端认证:将用户信息(包括本地用户的用户名、密码和各种属性)配置在认证服务器上。
AAA支持通过RADIUS(Remote Authentication Dial In User Service)协议或HWTACACS (HuaWei Terminal Access Controller Access Control System)协议进行远端认证。
网络接入服务器NAS(Network Access Server)作为客户端,与RADIUS 服务器或HWTACACS服务器通信。
如果在一个认证方案中采用多种认证模式,将按照配置的顺序进行认证。
当配置的认证方式是先远端认证后本地认证时如果登录的帐号在远端服务器上没有创建,但是在本地是存在的,经过远端认证时,将被认为认证失败,不再转入本地认证。
只有在远端认证服务器无响应时,才会转入本地认证。
如果选用了不认证(none)或本地认证(local),它必须作为最后一种认证模式。
AAA认证配置

44AAA配置访问控制是用来控制哪些人可以访问网络服务器以及用户在网络上可以访问哪些服务的。
身份认证、授权和记账(AAA)是进行访问控制的一种主要的安全机制。
44.1AAA基本原理AAA是Authentication Authorization and Accounting(认证、授权和记账)的简称,它提供了对认证、授权和记账功能进行配置的一致性框架,锐捷网络设备产品支持使用AAA。
AAA以模块方式提供以下服务:⏹认证:验证用户是否可获得访问权,可选择使用RADIUS协议、TACACS+协议或Local(本地)等。
身份认证是在允许用户访问网络和网络服务之前对其身份进行识别的一种方法。
⏹授权:授权用户可使用哪些服务。
AAA授权通过定义一系列的属性对来实现,这些属性对描述了用户被授权执行的操作。
这些属性对可以存放在网络设备上,也可以远程存放在安全服务器上。
⏹记账:记录用户使用网络资源的情况。
当AAA记账被启用时,网络设备便开始以统计记录的方式向安全服务器发送用户使用网络资源的情况。
每个记账记录都是以属性对的方式组成,并存放在安全服务器上,这些记录可以通过专门软件进行读取分析,从而实现对用户使用网络资源的情况进行记账、统计、跟踪。
部分产品的AAA仅提供认证功能。
所有涉及产品规格的问题,可以通过向福建星网锐捷网络有限公司市场人员或技术支援人员咨询得到。
尽管AAA是最主要的访问控制方法,锐捷产品同时也提供了在AAA范围之外的简单控制访问,如本地用户名身份认证、线路密码身份认证等。
不同之处在于它们提供对网络保护程度不一样,AAA提供更高级别的安全保护。
使用AAA有以下优点:⏹灵活性和可控制性强⏹可扩充性⏹标准化认证⏹多个备用系统44.1.1AAA基本原理AAA 可以对单个用户(线路)或单个服务器动态配置身份认证、授权以及记账类型。
通过创建方法列表来定义身份认证、记账、授权类型,然后将这些方法列表应用于特定的服务或接口。
aaa认证

AAA认证1. 简介AAA认证是指Authentication,Authorization和Accounting的缩写。
它是一种网络访问控制的方法,用于验证用户身份、授权用户访问权限以及记录用户的访问信息。
在网络安全领域,AAA认证是一种常见的认证授权技术。
2. 认证(Authentication)认证是AAA认证的第一步,用于验证用户的身份信息。
常见的认证方式包括用户名/密码认证、数字证书认证、生物特征认证等。
2.1 用户名/密码认证 (Username/Password Authentication)用户名/密码认证是最常见的认证方式之一。
用户通过提供正确的用户名和密码来验证身份。
这种方法简单易用,但也存在一些安全风险,比如密码被泄露、密码太弱等。
2.2 数字证书认证 (Digital Certificate Authentication)数字证书认证是一种使用公钥加密技术的认证方法。
用户需要拥有一个数字证书,由可信的证书颁发机构(CA)签发。
认证过程中,服务器会使用私钥对传输过来的数字证书进行解密和验证,从而确认用户身份的合法性。
2.3 生物特征认证 (Biometric Authentication)生物特征认证是利用人体特征进行身份验证的方法。
常见的生物特征包括指纹、虹膜、声纹等。
生物特征认证具有较高的安全性,因为这些生物特征是唯一的,难以被伪造。
3. 授权(Authorization)认证成功后,授权是AAA认证的下一步。
授权是指根据用户的身份和权限,决定用户可以访问网络中的哪些资源。
授权可以细分为角色授权和访问控制列表。
3.1 角色授权 (Role-Based Authorization)角色授权是一种将用户分组并为每个组分配特定权限的授权方法。
每个用户可以被分配一个或多个角色,不同的角色具有不同的权限。
通过角色授权,可以简化管理和控制用户访问权的过程。
3.2 访问控制列表 (Access Control Lists)访问控制列表是一种以列表形式记录了每个用户对特定资源的访问权限的授权方法。
AAA认证功能介绍

OLTAAA认证功能介绍VESION 1。
0 2011年7月7日AAA认证功能介绍 (1)一、相关知识点介绍 (3)1。
1. AAA简介 (3)1。
1.1。
认证功能 (3)1.1。
2. 授权功能 (3)1。
1.3. 计费功能 (3)1.2。
ISP Domain简介 (4)1.3。
Radius协议简介 (4)1.3.1。
RADIUS 服务的3个部分 (4)1。
3.2. RADIUS 的基本消息交互流程 (4)1.4. TACACS+协议简介 (5)1.5。
RADIUS和TACACS+实现的区别 (7)1.5。
1。
RADIUS使用UDP而TACACS+使用TCP (7)1.5。
2。
加密方式 (7)二、OLT上的AAA功能特点 (8)三、AAA认证命令行配置 (8)3.1. AAA配置 (8)3。
2。
配置ISP域 (9)3.3. 配置RADIUS协议 (10)3.4。
配置TACACS+协议 (11)四、AAA认证server简介 (12)4.1。
安装环境介绍: (12)4。
2。
安装和简要配置 (12)五、配置案例 (13)5.1。
Telnet用户通过RADIUS服务器认证的应用配置 (13)5.2. Telnet用户通过TACACS+服务器认证的应用配置 (15)5。
3. Telnet用户通过双服务器实现主备冗余的radius认证 (17)一、相关知识点介绍1。
1. AAA简介AAA 是Authentication,Authorization and Accounting(认证、授权和计费)的简称,它提供了一个对认证、授权和计费这三种安全功能进行配置的一致性框架,实际上是对网络安全的一种管理。
这里的网络安全主要是指访问控制,包括:● 哪些用户可以访问网络服务器;● 具有访问权的用户可以得到哪些服务;● 如何对正在使用网络资源的用户进行计费。
针对以上问题,AAA 必须提供认证功能、授权功能和计费功能.1.1.1. 认证功能AAA 支持以下认证方式:●不认证:对用户非常信任,不对其进行合法检查。
aaa认证是哪个部门认证

随着社会的快速发展和变化,市场经济逐渐进入了信用经济时代。
在这样一个时代背景下,无论对个人还是企业来说,信用都占据着举足轻重的地位。
如何判断一个企业的信誉需要有一个统一的标准,于是企业信用评级就诞生了。
该证书是指信用评级机构对企业的业务发展状况、财务状况和信用记录进行综合评价,以衡量其业绩能力和信用程度,用国际符号标注信用等级,发放信用评级证书和信用报告,并向社会公布评价结果。
而且该类证书是由信用评级公司评定,名义上这些公司都是民营的,所以不用去政府部门。
只需要认证的企业满足以下条件即可办理:1. 依法登记注册的企业法人和其他经济组织;
2. 企业成立已满二年或以上,近二年均有主营业务收入,企业处于持续经营状态(即无利润亏损),非即将关、停的企业;
3. 该企业单位无信用不良记录及违规违法行为记录。
同时能出具这个报告的第三方信用机构全国各地都有,因此企业在选择机构的时候还可以参考以下这几点:
第一该机构的营业执照经营范围;第二该机构的评价标准体系;第三企业信用报告等方面进行综合的判断和选择。
这里给大家推荐一家机构--北京中企普信国际信用评价有限公司,该企业经营时间久,办事效率快,是一家专业从事企业信用等级评定的公司。
简述用户认证和aaa技术原理。

简述用户认证和aaa技术原理。
用户认证是指验证用户身份的过程,确保用户是合法的、有权访问特定资源的用户。
AAA技术是一种广泛应用于网络安全领域的技术,包括认证(Authentication)、授权(Authorization)和账号(Accounting)三个方面。
在用户认证中,认证是最关键的一步,它用于验证用户所提供的身份信息是否与系统中存储的身份信息相匹配。
常见的用户认证方式包括用户名/密码、证书、生物特征等。
其中,用户名/密码是最常见的一种方式,用户通过输入正确的用户名和密码来验证自己的身份。
证书认证则是通过使用数字证书对用户进行身份验证,证书中包含了用户的公钥和其他相关信息。
生物特征认证则是通过分析用户的生物特征如指纹、面部识别等来验证身份。
AAA技术是一种综合性的身份验证和授权技术,它包括认证、授权和账号三个环节。
认证环节用于验证用户身份,确保用户是合法的。
授权环节用于确认用户是否有权访问特定资源,授权策略可以根据用户的身份和权限级别进行灵活配置。
账号环节用于记录用户的访问行为和资源使用情况,为后续的安全审计和计费提供依据。
AAA技术的工作原理是通过客户端、认证服务器和目标资源服务器之间的交互来完成的。
当用户请求访问资源时,客户端将用户提供的身份信息发送给认证服务器。
认证服务器通过验证用户的身份信息,并将认证结果返回给客户端。
如果用户身份验证成功,客户端将会向授权服务器发送请求以获取访问特定资源的权限。
授权服务器根据用户的身份和权限级别进行授权,并将授权结果返回给客户端。
最后,客户端根据授权结果,向目标资源服务器发送请求以获取所需资源。
AAA技术的应用非常广泛,特别是在网络访问控制、远程访问控制、虚拟专用网(VPN)等场景中得到广泛应用。
它可以提供有效的身份验证和授权机制,确保系统和资源的安全性,并且方便管理和审计用户的访问行为。
AAA信用等级认证有什么作用,怎么办理

AAA信用等级认证有什么作用,怎么办理诚信是多元化社会组织以及政府之间建立互信关系的基石,是现代经济活动中的一种资源,有利于吸引投资,有利于增强客户合作信心,有利于产品销售和市场开拓,有利于迅速达成合作协议。
因此,很多企业会进行AAA信用等级认证。
而AAA等级认证具体有什么作用?办理流程是什么呢?一、企业信用等级评定实行百分制。
按得分高低,企业信用等级分为AAA、AA、A、B、C五个等级:1.AAA企业。
得分为90分(含)以上,且资产负债率、利息偿还率和到期信用偿付率指标得分均为满分,现金流量指标得分不得低于5分,有一项达不到要求,最高只能评定为AA级。
2·AA级企业。
得分为80分(含)~90分(不含),且资产负债率、利息偿还率指标得分均为满分,到期信用偿付率指标得分不得低于10.8分,现金流量指标得分不得低于3分,有一项达不到要求,最高只能评定为A级。
3.A级企业。
得分为70(含)~80分(不含),且资产负债率指标得分不得低于5分,利息偿还率指标得分不得低于8.1分,到期信用偿付率指标得分不得低于9.6分。
4.B级企业。
得分为60分(含)~70分(不含);或得分在70分以上,但具有下列情形之一的:(1)属于国家限制发展的行业;(2)资产负债率得分为5分以下;(3)利息偿还率得分在8.1分以下;(4)到期信用偿付率得分在9.6分以下。
5.C级企业。
得分为60分(不含)以下;或得分在60分以上,但具有下列情形之一的:(1)生产设备、技术和产品属国家明令淘汰;(2)资不抵债(3)企业已停产半年以上;(4)存在逃废银行债权的行为;(5)利息偿还率得分在2.7分以下;(6)到期信用偿付率得分在3.6分以下。
二、作用1、树立企业形象的有效途径。
企业信用评级对于塑造信用形象、降低交易成本、提升竞争能力、创建良好的竞争环境具有重要意义。
2、信用评级是企业赢取市场的通行证。
信用评级是获得政府扶持、竞标、商务往来、招商引资、融资担保、银行贷款的通行证。
华为AAA认证详解及配置

华为AAA认证详解及配置⼀、AAA的基本架构AAA 通常采⽤“客户端—服务器”结构。
这种结构既具有良好的可扩展性,⼜便于集中管理⽤户信息。
如图1所⽰。
图 1 AAA 的基本构架⽰意图认证:不认证:对⽤户⾮常信任,不对其进⾏合法检查,⼀般情况下不采⽤这种⽅式。
本地认证:将⽤户信息配置在⽹络接⼊服务器上。
本地认证的优点是速度快,可以为运营降低成本,缺点是存储信息量受设备硬件条件限制。
远端认证:将⽤户信息配置在认证服务器上。
⽀持通过 RADIUS(Remote Authentication Dial In User Service)协议或HWTACACS(HuaWei Terminal Access Controller Access Control System)协议进⾏远端认证。
授权: AAA ⽀持以下授权⽅式:不授权:不对⽤户进⾏授权处理。
本地授权:根据⽹络接⼊服务器为本地⽤户账号配置的相关属性进⾏授权。
HWTACACS 授权:由 HWTACACS 服务器对⽤户进⾏授权。
if-authenticated 授权:如果⽤户通过了认证,⽽且使⽤的认证模式是本地或远端认证,则⽤户授权通过。
RADIUS 认证成功后授权:RADIUS 协议的认证和授权是绑定在⼀起的,不能单独使⽤ RADIUS 进⾏授权。
计费:AAA ⽀持以下计费⽅式:不计费:不对⽤户计费。
远端计费:⽀持通过 RADIUS 服务器或 HWTACACS 服务器进⾏远端计费。
⼆、RADIUS协议远程认证拨号⽤户服务 RADIUS(Remote Authentication Dial-In User Service)是⼀种分布式的、客户端/服务器结构的信息交互协议,能保护⽹络不受未授权访问的⼲扰,常应⽤在既要求较⾼安全性、⼜允许远程⽤户访问的各种⽹络环境中。
该协议定义了基于UDP 的 RADIUS 帧格式及其消息传输机制,并规定 UDP 端⼝ 1812、1813 分别作为认证、计费端⼝。
3A认证是什么

3A认证是什么3A体系是信用标准化领域中一个十分重要的认证。
是促进全国范围内的企业信用标准化体系,以利于企业产品与服务的信用交流,以及在知识、科学、技术和经济活动中发展企业间的信用相互合作。
一、3A证书有哪些:1、企业信用等级证书AAA2、企业资信等级证书AAA3、重服务守信用企业AAA4、重合同守信用企业AAA5、质量服务诚信单位AAA6、诚信经营示范单位AAA7、诚信供应商企业AAA8、中国诚信企业家荣誉证书-法人名字9、企业信用评价AAA级信用企业-铜牌二、申报条件:在中华人民共和国范围内(不含港、澳、台地区)依法注册、合法经营,并在经营活动中未发生不正当经营,包括恶意竞争、劳资纠纷、偷税漏税等重大失信行为的,均可提交申请,取得信用等级证书或报告。
三、证书的公示和查询:信用证书带有二维码扫描查询,二维码动态跟踪客户信用状况,记录信用代码和信用等级。
是国内招投标领域通用性较高的评级机构。
1、招投标网查询:点击信用公示,输入证书编号即可查询。
2、中国信用等级查询方式:在中国信用企业公示网输入证书编号即可查询。
四、企业信用评级的作用3A企业是指企业的信用经过行业、机构评审达到3A信用标准的企业,获评企业都会得到机构出具的牌匾、证书。
其最直接的作用是在招投标、政府采购、工程建设中,作为企业的资信证明,帮助投标人获得竞标加分的优势。
1、企业获得政府扶持招商投资、融资担保、银行贷款的“通行证”;2、衡量企业履约能力、招投标信誉、综合能力的“荣誉证”;3、企业洞察社会经济发展、提升现代管理走向国际化的“导向证”;4、企业提升品牌价值与品牌竞争力的“无形资产证”;5、企业降低筹募资金成本的“减负证”;6、企业在市场活动中塑造企业形象的“身份证”;7、优先获得科技贷款、低息贷款、贴息贷款;优先获得政府津贴、补贴等等。
3A信用认证是什么?AAA信用评级的好处是什么?

3A信用认证是什么?AAA信用评级的好处是什么?企业信用评估主要有以下意义:1、按照政策规定:政府各部门和社会其他组织对优质信用企业在政府采购、融资担保、技术改造、技术合作、产品进出口、项目立项、招标投标、招商引资、土地使用、人才引进、进入各类园区等方面应给予重点扶持。
2、信用评级为政府部门间接调控市场提供强有力的手段,是很重要的一个监管指标。
3、信用评级是树立企业形象的有效途径,企业信用评级对于企业塑造信用品牌,降低交易成本,提升信用形象,创造良好的市场经济秩序和信用环境具有重要的意义。
4、信用评级是企业赢取市场的通行证。
信用评级是获得政府扶持以及企业商务来往、招商、投资、信用担保、融资的通行证。
5、信用评级是企业综合竞争力的证明。
信用状况是企业履约能力、投标信誉的主要因素,通过信用评级可为企业综合竞争力提供最有利的证明。
信用评级是强化企业管理和防范风险的必要手段。
通过客观评级,企业可以发现自身的不足和存在的隐患,从而改善经营管理和加强风险防范.1、投标加分。
招投标加分,入围政府采购名单,有限考虑AAA信用企业。
2、政策扶持。
面向政府扶持基金、政府机构监管展示的企业信用等级证明。
3、贷款优惠。
争取机构风投、融资担保、银行房贷等提供的信用等级证明。
4、提升成交。
企业履约能力、投标信誉,综合实力的体现,提高成交率。
5、商务合作使用。
在企业招商、政府招标、签约合作等提供信用证明。
6、供销买卖依据。
与交易伙伴赊销、拓展上下游合作关系时可作为权威证明。
7、提升企业软实力。
AAA信用是企业的无形资产,是企业品牌的身份证。
8、国际贸易的通行证。
在国际合作与贸易时,可出示的信用证明。
AAA安全认证

A A AAAA是一种后台服务,是一种对网络用户进行控制的安全措施,可用于对想要接入网络的用户进行认证(身份验证)、授权、审计。
Authentication认证认证的作用是确定你是谁,是否是合法用户,是否有资格进入。
认证强度跟元素有关,用于认证的元素越多越安全,元素包括密码,指纹,证书,视网膜等等Authorization授权授权决定了你能做什么授权用户能够使用的命令授权用户能够访问的资源授权用户能够获得的信息Accounting审计审计确定你做了什么,对你的所做的事进行记录两类审计:1、时间审计2、命令审计AAA的基本拓扑:NAS--网络访问服务器,或者叫网络接入服务器。
其实就是你网络的边缘网关,外部节点需要通过这台路由器来访问你的网络。
需要在这台路由器上对接入的用户进行控制。
AAA--通过在服务器上装上CISCO的ACS软件,就能构建出一台AAA服务器。
NAS是AAA服务器的client端为什么要用AAA:通过AAA技术,我们能对接入网络的用户进行控制,可以控制哪些用户能接入网络,能得到什么样的权限,还能记录用户上来之后做了啥事。
1、跟网络设备数量有关,也就是跟NAS的数量有关2、跟用户数量有关3、由于用户的频繁变动三大类的需要认证的流量类型client-----NAS(网络访问服务器)也就是三种到达NAS的流量1、登入nastelnet/ssh/http/https(也叫网管流量)2、拔入naspptp/l2tp/pppoe/ipsecvpn.....3、穿越nasauth-proxy(ios)认证代理/cut-through(pix)其实上面的分类也可以换个说法:AAA的接入模式分为两类:1、字符模式---------用于VTY、TTY、AUX、CON端口,该模式一般用来配置设备。
2、包模式--------用于串行端口或其它远程接口,以及拨号接口。
该模式用于用户与网络内不同设备的通信。
AAA安全服务器的选择:1、本地安全数据库2、远程安全服务器,也就是AAA服务器本地安全数据库:本地安全数据库运行在NAS上为一小部分用户提供服务,实现起来容易,但是功能不够强大。
AAA认证
1、首先需要安装虚拟机VMware工作环境。
然后建立两个虚拟机,一个是windows xp,另一个是windows server2003。
我遇到的问题:server2003成功安装,没有问题。
而安装xp的时候总是不成功,换了另一个系统镜像文件也不行。
后来发现,原来是没有对分配给xp的虚拟硬盘空间进行分区并且格式化。
这个可以在安装的时候进入PE模式,选择自动分区,一般系统安装目录都有这样子的选项。
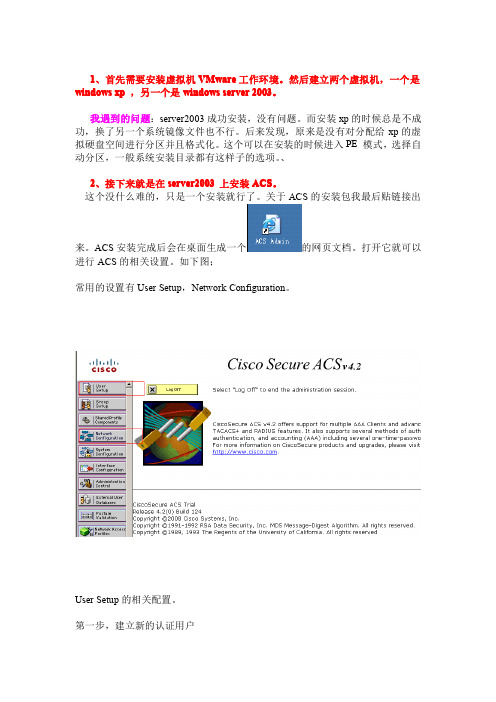
、2、接下来就是在server2003上安装ACS。
这个没什么难的,只是一个安装就行了。
关于ACS的安装包我最后贴链接出来。
ACS安装完成后会在桌面生成一个的网页文档。
打开它就可以进行ACS的相关设置。
如下图;常用的设置有User Setup,Network Configuration。
User Setup的相关配置。
第一步,建立新的认证用户第二步,创建用户密码,然后点击SUBMIT。
Network Configuration的配置第一步:新建AAA客户端,客户端一般是交换机。
第二步:配置AAA服务端ACS基本上就可以配置完成了。
我遇到的问题:安装完ACS后,一定要安装java运行环境否则在进行ACS配置时网页可能会打不开,或者某些设置不会生效。
同时要关闭IE的安全特性,还有防火墙。
(xp上的防火墙也需要关闭)3、网卡的选择和配置第一步:虚拟机安装完成后会在本机上生成两个虚拟网卡启用他们,并且这两个网卡都不需要配置地址。
我遇到的问题:刚开始我以为这两个虚拟网卡就是windows server2003和xp的网卡,于是给他们设置了地址,造成的问题是两台虚拟机ping不通网关。
后来思考了下,如果把这两个虚拟网卡当成交换机的话,就解释的通了,而且不给他们设置IP,两台虚拟机就可以ping通网关。
第二步:server2003上的配置。
右击server2003标签,选择设置第三步:同理第二步,在xp上配置第一步:Windows server2003第二步:windows xp5、实验拓扑的设计用GNS设计实验拓扑,需要一台交换机,一台路由器,两个终端。
3A认证
1概述基本信息3A认证,即AAA认证AAA:分别为Authentication、Authorization、Accounting认证(Authentication):验证用户的身份与可使用的网络服务;授权(Authorization):依据认证结果开放网络服务给用户;计帐(Accounting):记录用户对各种网络服务的用量,并提供给计费系统。
详解AAA ,认证(Authentication):验证用户的身份与可使用的网络服务;授权(Authorization):依据认证结果开放网络服务给用户;计帐(Accounting):记录用户对各种网络服务的用量,并提供给计费系统。
整个系统在网络管理与安全问题中十分有效。
首先,认证部分提供了对用户的认证。
整个认证通常是采用用户输入用户名与密码来进行权限审核。
认证的原理是每个用户都有一个唯一的权限获得标准。
由AAA服务器将用户的标准同数据库中每个用户的标准一一核对。
如果符合,那么对用户认证通过。
如果不符合,则拒绝提供网络连接。
接下来,用户还要通过授权来获得操作相应任务的权限。
比如,登陆系统后,用户可能会执行一些命令来进行操作,这时,授权过程会检测用户是否拥有执行这些命令的权限。
简单而言,授权过程是一系列强迫策略的组合,包括:确定活动的种类或质量、资源或者用户被允许的服务有哪些。
授权过程发生在认证上下文中。
一旦用户通过了认证,他们也就被授予了相应的权限。
最后一步是帐户,这一过程将会计算用户在连接过程中消耗的资源数目。
这些资源包括连接时间或者用户在连接过程中的收发流量等等。
可以根据连接过程的统计日志以及用户信息,还有授权控制、账单、趋势分析、资源利用以及容量计划活动来执行帐户过程。
验证授权和帐户由AAA服务器来提供。
AAA服务器是一个能够提供这三项服务的程序。
当前同AAA服务器协作的网络连接服务器接口是“远程身份验证拨入用户服务(RADIUS)”。
目前最新的发展是Diameter协议。
AAA安全认证

A A AAAA是一种后台服务,是一种对网络用户进行控制的安全举措,可用于对想要接入网络的用户进行认证(身份考证)、受权、审计。
Authentication认证认证的作用是确立你是谁,是不是合法用户,能否有资格进入。
认证强度跟元素有关 , 用于认证的元素越多越安全,元素包含密码,指纹,证书,视网膜等等Authorization受权受权决定了你能做什么受权用户能够使用的命令受权用户能够接见的资源受权用户能够获取的信息Accounting 审计审计确立你做了什么,对你的所做的事进行记录两类审计:1、时间审计2、命令审计AAA的基本拓扑:NAS--网络接见服务器,或许叫网络接入服务器。
其实就是你网络的边沿网关,外部节点需要经过这台路由器来接见你的网络。
需要在这台路由器上对接入的用户进行控制。
AAA--经过在服务器上装上 CISCO的ACS软件,就能建立出一台AAA服务器。
NAS是 AAA服务器的 client端为何要用 AAA:经过AAA技术,我们能对接入网络的用户进行控制,能够控制哪些用户能接入网络,能获取什么样的权限,还可以记录取户上来以后做了啥事。
1、跟网络设施数目有关,也就是跟NAS的数目有关2、跟用户数目有关3、因为用户的屡次改动三大类的需要认证的流量种类client-----NAS(网络接见服务器)也就是三种抵达 NAS的流量1、登入 nastelnet/ssh/http/https(也叫网管流量)2、拔入 naspptp/l2tp/pppoe/ipsecvpn.....3、穿越 nasauth-proxy(ios)认证代理/cut-through(pix)其实上边的分类也能够换个说法:AAA的接入模式分为两类 :1、字符模式 ---------用于VTY、TTY、AUX、CON端口,该模式一般用来配置设施。
2、包模式 --------用于串行端口或其余远程接口,以及拨号接口。
该模式用于用户与网络内不同设施的通讯。
31.AAA认证和授权

AAA域
服务器A
@partner
NAS
目的网络
@huawei
服务器B AAA服务器
AAA可以通过域来对用户进行管理,不同的域可以关联不同的认证、授 权和计费方案。
Page 8
AAA配置
主机A G0/0/0 10.1.1.1/24 RTA
[RTA]aaa [RTA-aaa]authentication-scheme auth1 [RTA-aaa-authen-auth1]authentication-mode local [RTA-aaa-authen-auth1]quit [RTA-aaa]authorization-scheme auth2 [RTA-aaa-author-auth2]authorization-mode local [RTA-aaa-author-auth2]quit [RTA-aaa]domain huawei [RTA-aaa-domain-huawei]authentication-scheme auth1 [RTA-aaa-domain-huawei]authorization-scheme auth2 [RTA-aaa-domain-huawei]quit
用户名 主机A
AAA服务器
密码 Huawei123 Pass123
服务器B
主机X
…
…
认证:验证用户是否可以获得网络访问的权限。 AAA支持的认证方式有:不认证,本地认证,远端认证。
Page 5
授权
RTA NAS RTA
服务器A 设备组: Public
主机A 用户组:Staff
AAA服务器
设备组
aaa信用等级认证有什么用

aaa信用等级认证的作用有很多,那具体是什么呢?下面就给大家分享一下,以便大家进行了解。
1、为投标企业提供公平竞争的机会
评级之前,投标企业不被招标方所熟悉,信用评级让招标方可以正确、充分了解各企业的实力和财务状况,作为评标、定标参考依据。
2、正视自身信用问题维护信用记录
守信企业进行信用等级评定,可以让自己脱颖而出;失信企业进行信用等级评定,可以让自己回归理性。
3、为招标单位防范潜在的合作风险
可以让招标单位避开雷区,有效解决由于信用不对称造成的商业欺诈、制造售假等问题。
4、政府政策扶持
各地政府主管部门要加强社会信用管理体系建设,积极支持企业诚信体系必备的基础设施建设,鼓励社会资源向诚信企业倾斜。
信用是企业的生命线,现代企业间进行商务合作一般都会事先查询、考量合作方的信用状况。
在项目招投标的过程中,招标方有时还会要求投标方出具企业信用报告,而在这关键时刻,拥有足够优质的信用报告,就会成为企业掌握市场先机,发挥差异化竞争优势,获得市场领先地位的一张“王牌”。
如有不明白的,可以咨询--北京中企普信国际信用评价有限公司,该企业经营时间久,办事效率快,是一家专业从事企业信用等级评定的公司。
aaa信用等级认证多少钱

企业信用等级aaa证书不仅属于一种荣誉资质,同时,还是提升企业公信力和影响力保障的一项资质,因此,越来越多的企业为提高自身的竞争力而加入到认证的队伍中,那认证需要多少钱呢,下边带您一起来了解。
1、aaa信用等级认证机构不同,其费用也会不同
这是因为目前大大小小的3a企业信用认证较多,且不同的机构具有不同的收费标准,加之不同的认证机构其公示平台、备案资质等也有所差异,所以,也导致价格也会不同,因此,认证的费用也是从3000带上万都有。
2、通用区域不同,其费用也会不同
如,省级型的等级认证价格低于全国通用性的,省级型的认证费用一般在5000元左右;通用型的认证费用大概在10000元左右,因此,aaa信用等级认证通用区域不同,其费用也会不同。
3、证书权威性、可查询性以及公信力不同,费用也会不同
这是因为不同的申报机构所具备的资质不同,那么它所颁发的证书权威性、
可查询性以及公信力都不尽相同,当然需要企业提交的材料和认证工作流程也就不同,这些因素是造成价格上下有较大出入的根本原因。
当然,收费也跟证书的含金量有关,含金量低的就便宜一般在3000元左右,含金量高的就贵一些大概在5000元左右。
以上就是aaa信用等级认证费用的简单介绍,希望对大家进一步的了解有所帮助,同时,如有不清楚的,可咨询北京中质环宇认证咨询中心,该中心为国家认证认可监督管理委员会批准备案的具有独立法人资格的认证咨询服务机构,不仅咨询程序科学规范、专业人才经验丰富、通过率高且办事效率快,因此,现深受客户的好评。
企业信用aaa认证报告

企业信用aaa认证报告1. 引言企业信用AAA认证报告是对某企业信用状况进行评估和认证的重要文件。
本报告将对某企业进行全面的信用评估,包括企业基本信息、经营状况、财务状况、市场竞争力等方面进行深入分析,以确定该企业的信用等级。
2. 企业基本信息- 企业名称:X公司- 成立时间:20XX年X月X日- 企业类型:有限责任公司- 注册资本:XXX万元- 法定代表人:XXX- 经营范围:XXX3. 经营状况评估3.1 行业地位X公司在所属行业中具有较高的知名度和影响力。
其产品/服务在市场上占据一定份额,并与同行业的其他企业形成竞争关系。
3.2 经营策略X公司坚持以质量为先导,注重技术创新和产品研发。
同时,该企业还积极拓展市场,寻找新的合作伙伴,并通过在线渠道和传统渠道开展销售。
3.3 客户和供应链关系X公司与众多客户建立稳定的合作关系,客户满意度较高。
在供应链管理方面,企业确保供应商的质量和交货准时,以维护供应链的稳定性。
3.4 品牌形象X公司在品牌建设方面投入了大量的资源,形成了较为完善的品牌形象。
企业的品牌在市场上享有较高的声誉和知名度。
4. 财务状况评估4.1 资产状况X公司资产规模较大,资产结构相对稳定。
具有一定数量和质量的固定资产和流动资产,为企业的持续经营提供了坚实的基础。
4.2 负债状况X公司负债水平相对较低,负债结构合理。
企业有稳定的还款来源,能够按时偿还债务,保持清偿能力。
4.3 盈利能力X公司连续多年保持较高的盈利水平,利润率稳定。
企业能够有效控制成本,提高盈利能力。
同时,其经营效益也在逐年提高。
4.4 现金流状况X公司的现金流状况良好,现金流量稳定且充裕。
企业具备良好的资金周转能力和偿债能力。
5. 信用AAA认证结果综合考虑企业基本信息、经营状况和财务状况等方面的评估结果,X公司被评定为信用AAA级企业。
这意味着该企业具备极高的信用等级,具有较低的违约风险。
AAA信用级别在市场上享有极高声誉,为X公司获得更多的商业机会和合作伙伴带来了巨大优势。
人行备案AAA企业信用等级认证简介

人行备案AAA企业信用等级认证简介
企业在经济交往中,无论是签订购销合同、申请资质,还是参加招投标、争取政府采购等,都需要一个有效的信用等级证书,才能获取对方的信任。
尤其是在招投标过程中,招标方对投标人的资质审核是非常严格的,其中投标人的信用等级是重要的信用资质,拥有AAA级信用等级证书,不仅可以提升企业诚信形象,还能够获得3-5分的投标加分,提高企业整体竞标能力。
为了企业发展和品牌建设,无论企业规模大小,申请办理AAA级企业信用等级证书都很有必要。
目前很多地方招投标对于投标人的社会信用信息要求信用等级证书及报告,信用报告必须有再中国人民银行备案的从事企业征信和信用评级等级业务的社会信用服务机构出具。
因此,如果企业以前在不知情的情况下办理了协会的或者一些没有在人行备案的征信机构出具的证书和报告,将无法满足投招标需要,只能重新找具备备案要求的机构重新办理了,浪费钱财不说,更耽误时间。
以后招投标都只认人行有备案的,不是拥用普通的AAA企业信用等证书就可以的。
办理AAA信用等级要有人行备案的机构出具才有含金量。
需要人行机构备案的AAA企业信用等级证书的企业可以找我们武汉好地科技咨询老师。
AAA资信等级加分规定(一般情况):1A级加1分;2A级加2分;3A级加3分。
(政府集采项目有B级以上才能入围投标的情况,也有AAA级企业加5分的情况)我国法律规定企业征信和评级机构的管理机关为中国人民银行。
“AAA资信证明由中国人民银行备案的第三方评级机构出具”。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
RADIUS Authentication and Authorization
• The example shows how RADIUS exchange starts once the NAS is in possession of the username and password.
• The ACS can reply with Access-Accept message, or AccessReject if authentication is not successful.
• Includes only two security features: – Encryption of passwords – Authentication of packets (MD5 fingerprinting)
© 2006 Cisco Systems, Inc. All rights reserved.
Accounting: – What did you do? How long and how often did you do it? – “User student accessed host serverXYZ using Telnet for 15 minutes.” – “User student was connected to VPN for 25 minutes.” – “EXEC session of user student lasted 20 minutes and only show
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-8
RADIUS Features
• Standard protocol (RFC 2865)
• Uses UDP on standard port numbers (1812 and 1813; Cisco Secure ACS uses 1645 and 1646 by default)
commands were executed.”
Байду номын сангаас
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-3
Implementing AAA
• Administrative access: Console, Telnet, and AUX access • Remote user network access: VPN access
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-11
Configuring the AAA - Server 在NAS上指SERVER
TACACS+
RADIUS
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-9
TACACS+ Authentication
• The example shows how TACACS+ exchange starts before the user is prompted for username and password.
• The prompt text can be supplied by the TACACS+ server.
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-6
AAA Protocols: RADIUS and TACACS+
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-7
ISCW v1.0—5-12
Configure AAA Login Authentication on Cisco Routers Using CLI
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-13
AAA Authentication Commands
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-4
Router Access Modes
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-5
AAA Protocols: RADIUS and TACACS+
ISCW v1.0—5-2
AAA Model
• Authentication: – Who are you? – “I am user student and my password validateme proves it.”
• Authorization: – What can you do? What can you access? – “User student can access host serverXYZ using Telnet.”
Cisco Device Hardening
Configuring AAA on Cisco Routers
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-1
Introduction to AAA
© 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
ISCW v1.0—5-10
TACACS+ Network Authorization
• The example shows the process of network authorization which starts after successful authentication.
