Abstract
英语摘要写法

摘要(Abstract)摘要(Abstract) 也成为内容提要,通常在学士论文中都必须附有摘要,其位置应放在论文的正文之前,对整个论文内容的概述。
无论对专业读者还是对非专业读者而言,摘要都是一个非常重要的文件。
摘要如果和论文一起发表,则被称为一次性出版物摘要,主要用于帮助读者评价文章内容及其潜在作用,使读者不必阅读全文就可以了解论文的内容。
除此之外,摘要也可以被单独收入文摘机构出版的摘要期刊如:生物学文摘(Biological Abstract)、化学文摘(Chemical Abstract)等、称为二次性出版物摘要。
此类脱离论文独立成篇的摘要主要用于方便读者检索文献、收集信息,帮助研究者寻找新的研究领域。
一.摘要的定义摘要的英文术语:有两个词汇,一个是abstract, 一个是summary.根据美国国家标准学会(American National Standard Institute)于1971年通过并颁布的《美国国家文摘写作标准》(American National Standard for Writing Abstracts)规定,Abstract 不应与summary 混同。
Abstract 对一篇论文的主要内容以精炼的文字进行高度概括,使读者不必阅读全文即可了解论文内容,或者让读者对即将阅读的文章有思想准备,或者让读者判断是否有通读全文的必要。
文中只对论文信息进行浓缩,而不加主观评论或解释,可以脱离原文而独立成篇。
字数通常在100~150个词左右,更确切地说,约为原文长度的1% ~ 5%(有的杂志规定摘要平均为全文的3% ~ 5%)。
现在越来越多的用法是abstract. 尤其是放在索引资料中一律要用abstract 这个术语,在论文的题目下也通常要用这个词。
Summary (概要) 与abstract 无明显差别。
严格地说,summary 一般附在论文的后面,对论文的主要结论和成果进行再叙述。
abstract方法

abstract方法Abstract方法。
在面向对象的编程中,抽象方法是一种非常重要的概念。
它是一种在抽象类或者接口中声明但不实现的方法,需要由子类去实现具体的逻辑。
本文将对抽象方法进行详细的介绍,包括其定义、特点、使用方法以及示例等内容。
首先,抽象方法是指在抽象类或者接口中声明但不实现的方法。
它只有方法的声明,没有方法体。
抽象方法的存在是为了让子类去实现具体的逻辑,从而达到代码的灵活性和可扩展性。
在Java中,使用关键字“abstract”来声明抽象方法,而在C#中,则使用关键字“abstract”来修饰方法。
其次,抽象方法的特点是必须在抽象类或者接口中声明,而且不能包含方法体。
另外,包含抽象方法的类必须被声明为抽象类,而包含抽象方法的接口则必须被实现。
在使用抽象方法时,需要注意的是子类必须实现父类中的所有抽象方法,否则子类也必须声明为抽象类。
使用抽象方法的好处在于可以定义一套规范,让子类去实现具体的逻辑。
这样一来,可以在不同的子类中实现不同的逻辑,从而提高代码的复用性和可维护性。
此外,抽象方法还可以降低代码的耦合度,使得程序更加灵活和易于扩展。
下面通过一个简单的示例来说明抽象方法的使用方法。
假设有一个图形类Shape,其中包含一个抽象方法calculateArea()用于计算图形的面积。
然后有两个子类Circle和Rectangle分别继承Shape类,并实现calculateArea()方法来计算圆形和矩形的面积。
这样一来,就可以通过多态的方式来调用不同子类的calculateArea()方法,而不需要关心具体是哪个子类。
总之,抽象方法是面向对象编程中非常重要的概念,它可以提高代码的灵活性和可扩展性,降低代码的耦合度,使得程序更加易于维护和扩展。
通过本文的介绍,相信读者对抽象方法有了更深入的理解,可以在实际的项目中更加灵活地运用抽象方法来设计和实现代码。
4个步骤教你如何写好abstract部分

4个步骤教你如何写好abstract部分A b s t r a c t,就是对英文论文的一个简短总结,目的是为了告诉读者论文研究的是什么课题,以此来吸引读者。
一个好的a b s t r a c t,对英文论文的作用是非常大的,是论文的核心部分,所以一定得写好。
下面就给大家讲解一下如何写好a b s t r a c t部分。
1.无论任何学科,a b s t rac t需要包括以下几个重要组成部分和重要元素1)动机或问题的陈述:为什么我们对这个研究问题这么关心?你的研究针对的是实践性的,科学性的,理论性的还是艺术性的?有些a b s t r a c t 写作的时候,在写作动机之前要简要介绍相关的背景信息。
2)措施/流程/解决方法以及调查范围:为了得到相关的结果,你做了什么?3)结果/发现/产品:在上述的调查研究完成后,你学会了什么?发现了什么?创造了什么?4)结论/影响:你得出的哪些结论会产生更大的影响?然而,需要注意的是,根据不同的学科,要注意相关的可变性因素。
2.a b s t rac t中的语法特点和要求1)注意到细微的变化在陈述主要目标和调查范围的时候,多采用陈述性语言。
2)采用合适的方法描述方法的时候多使用过去时态。
要注意时态的一致性。
如果有必要,要按照时间的顺序进行排列。
3)注意结果的呈现方式只需要呈现结果即可。
以过去时态呈现出来。
4)注意结论的可靠性陈述个人观点。
在陈述主要结论的时候要使用现在时。
不要表现出试探性的倾向。
3.a b s t rac t s的类型a b s t r a c t s分为两种类型,i n f o r m a t i o n a l a b s t r a c t s和d e s c r i p t i v ea b s t r a c t s。
I n f o r m a t i o n a l A b s t r a c t s--针对r e p o r t s的相关内容进行沟通。
Abstract写作常用句型及句式

Abstract写作常⽤句型及句式Abstract⼀、在摘要中直接提出论⽂主题的句型和句式1、In this paper, we present a … approach to …本⽂提出了⼀种针对…的…⽅法。
2、In this paper, we describe improved … models for …本⽂介绍⼏种针对…的改进的…模型。
3、We propose a new … model and … algorithm that enables us to …我们提出⼀种新的…模型和…算法,它让我们能够…4、We present a … model that enables …我们提出了⼀种…模型,它使我们能够…5、This paper demonstrates the ability of … to perform robust and accurate …本⽂证明了…进⾏…可靠准确的…的能⼒。
6、In this paper we report results of a … approach to …本⽂报导了…的…⽅法的实验结果。
7、This paper demonstrates that … can effectively … with very high accuracy.本⽂证明,…能够有效地准确地…8、The purpose/goal/intention/objective/object/emphasis/aim of this paper is …本⽂的⽬的是…9、The primary/chief/overall/main object of this study is to survey …本研究的⾸要⽬标是考察…10、The chief aim of this paper/research/study/experiment/the present work is …本⽂的主要⽬标是…11、 The emphasis of this study lies in …我们的研究重点是…12、The work presented in this paper focuses on …本⽂所述⼯作重点放在…13、Our goal has been to provide …我们的⽬标是提供…14、The main objective of our investigation has been to obtain some knowledge of …我们的研究⽬标是获取有关…的知识。
考研英语:词汇abstract的中文翻译解析

考研英语:词汇abstract的中文翻译解析考研英语有许多题目组成,方便大家及时了解,下面为你精心准备了“考研英语:词汇abstract的中文翻译解析”,持续关注本站将可以持续获取的考试资讯!考研英语:词汇abstract的中文翻译解析abstract是什么意思及用法adj.1. 抽象的2. 抽象派的n.1. 抽象,抽象概念,抽象性2. 抽象派艺术作品3. 摘要,梗概及物动词:1. 提取,抽取2. 做…的摘要词形变化副词abstractly名称abstractness时态abstracted,abstracting,abstracts英语解释not representing or imitating external reality or the objects of naturemake off with belongings of othersdealing with a subject in the abstract without practical purpose or intentionconsider a concept without thinking of a specific example consider abstractly or theoreticallyconsider apart from a particular case or instancegive an abstract (of)a concept or idea not associated with any specific instancea sketchy summary of the main points of an argument or theoryexisting only in the mind separated from embodiment 例句She beheaded me, and flung my head into abstract space 她切下了我的头颅,把它扔进抽象的空间。
学术英语写作Unit-5----Abstract

Informative abstraห้องสมุดไป่ตู้ts
An informative abstract provides detail about the substance of a piece of writing because readers will sometimes rely on the abstract alone for information. Informative abstracts typically follow this format:
Unit 5 Abstract
What is an abstract? Types of abstracts Why write an abstract? What should the abstract include? How do you write an abstract? What is the style of an abstract? An outline for writing an abstract Common problems in writing an abstract Difference between an abstract and an introduction The Tricks, Conclusion of the lecture
3. evaluative abstracts: comment on the worth of the original are included.
Difference between descriptive abstracts and informative abstracts
abstract谐音法记忆

abstract谐音法记忆
谐音法是一种记忆技巧,通过将要记忆的内容与与之谐音或类似的词语联系起来,以便更容易记住。
对于"abstract"这个词,你可以通过与其他词语或短语的谐音来创建记忆联结。
以下是一些可能的谐音法:
抽象桃(Chouxiang Tao):将"abstract"谐音为"抽象桃",可以想象一个抽象的桃子,这个桃子可能有着奇特的形状或颜色,帮助你记住抽象的概念。
阿波士陶(A Bo Shi Tao):将"abstract"谐音为"阿波士陶",可以将这个词与阿波罗神或陶器联系起来,创造出一个与艺术和抽象相关的形象。
阿爸说道(A Ba Shuo Dao):将"abstract"谐音为"阿爸说道",你可以想象一个父亲在说一些深奥的道理,这有助于记住"abstract"这个词与深奥概念相关。
请记住,这只是一种辅助记忆的方法,效果因人而异。
如果这些谐音法不适合你,你可以尝试创建与"abstract"相关的其他词语或图像来帮助记忆。
abstract 的写法
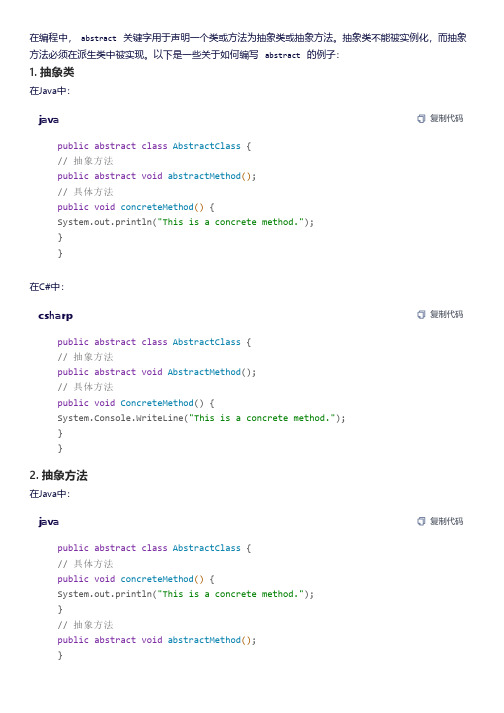
在编程中,abstract关键字用于声明一个类或方法为抽象类或抽象方法。
抽象类不能被实例化,而抽象方法必须在派生类中被实现。
以下是一些关于如何编写abstract的例子:1. 抽象类在Java中:java复制代码public abstract class AbstractClass {// 抽象方法public abstract void abstractMethod();// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}}在C#中:csharp复制代码public abstract class AbstractClass {// 抽象方法public abstract void AbstractMethod();// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}}2. 抽象方法在Java中:java复制代码public abstract class AbstractClass {// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}// 抽象方法public abstract void abstractMethod();}在C#中:csharp复制代码public abstract class AbstractClass {// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}// 抽象方法public abstract void AbstractMethod();}注意点:抽象类不能被实例化。
abstract 造句

abstract造句1、consider an abstract concept to be real.把一个抽象的概念作具体的考虑。
2、The choice of the data structure often begins from the choice of an abstract data type.所选择的数据结构往往首先从选择一个抽象的数据类型。
3、Abstract expressionism was at its peak in the 1940s and 1950s.20世纪45十时期是抽象体现主义艺术发展和进步的顶峰时期。
4、The param elements provide a value for each parameter reference used in the abstract pattern.param元素提供了抽象范式中每个参数引用的值。
5、For those of us living in China, there's nothing abstract about it.对于我们这些生活在中国的人来说,它一点也不抽象。
6、This is because you cannot create tooling for abstract types.这是因为您不能为抽象类型创建工具。
7、Many topological spaces with abstract convexity structure are all FC-spaces.许多具有抽象凸结构的拓扑空间都是FC-空间。
8、Platonism began the West’s pursuit of abstract truth from the times of ancient Greece.从古希腊时代起,柏拉图主义便开始了西方式的对抽象真理的追求。
9、It used abstract art and often childish language to ridicule the absurdity of the modern world.它使用抽象的艺术和幼稚的语言嘲弄了现代世界的荒谬。
abstract方法

用关键字abstract修饰的方法称为abstract方法(抽象方法)。
abstract int min (int x, int y );
对于abstract方法,只允许声明,不允许实现(没有方法体),而且不允许使用final和abstract同时修饰一个方法或类,也不允许使用static修饰abstract方法,即abstract方法必须是实例方法
1.abstract类中可以有abstract方法
和普通类(非abstract类)相比,abstract类中可以有abstract方法,
也可以有非abstract方法(非abstract类中不可以有abstract方法)。
注意:abstract类里也可以没有abstract方法。
2.abstract类不能用new运算符创建该类的对象。
3.abstract类的子类
如果一个非abstract类是abstract的子类,他必须重写父类的abstract
方法,即去掉abstract方法的abstract修饰,并给出方法体。
如果一个abstract 类是abstract类的子类,它可以重写父类的abstract方法,也可以继承父类的abstract方法。
4.abstract类的对象可以作为上转型对象
可以使用abstract类声明对象,尽管不能使用new运算符创建该对象,但该对象可以成为其子对象的上转型对象,那么该对象就可以调用子类重写的方法。
Abstract常用表达和句式

回顾某领域已取得的研究结果或介绍相关知识常用动词:present, summarize, review, outline句式:…is presented in this paper.This paper reviews the method for dealing with…This article summarizes the theory on...阐明论文写作和研究目的常用词:名词:purpose, aim, objective, goal动词:aim, attempt to, initiate, intend to, seek句式:The purpose of this study is to explore new methods on …The paper attempts to define ..in terms of.The study is aimed at finding out the basic similarities between … and …The main objective of the work is to justify.The primary goal of this research is …The main objective of our investigation has been to obtain some knowledge of …Based on recent research, the author intends to outline the framework of…The authors are now initiating some experimental investigation to establish.论文观点和作者观点常用词:argue, account for, address, characterize, concern, contribute, describe, disclose, deal with, devote to, explain, introduce, present, report句式:This paper presents the mathematical model and its algorithm used for …The calibration and experiment design of multivariate force sensors are discussed. This paper reports the preparation and quantum confinement effects of…The principles and methodology of language teaching are described in this article. This paper is mainly devoted to ...介绍研究过程和研究范围常用词:过程:analyze, consider, discuss, examine, study, investigate, state, propose 范围:contain, cover, include, outline, scope, field, domain句式:The characteristic of …was investigated.The paper analyzes the possibility of ...We study the one-step-synthesis method for …in this paper.This article discusses the method of calculation of …The principle of constructing … is proposedThis paper states the reasons for...This study identifies some procedures for …This article outlines the preliminary process of …The scope of the study covers.The study includes.The paper contains the specific topic on …介绍计算、测量常用词:calculate, compute, determine, estimate, measure, work out句式:This paper determines the proper temperature for …The cooling rate was calculated by means of.The rational rage of power is measured by …In the paper, we measured the orientation and estimated parameter for ...The author worked out the probability of ...The author has computed equilibrium constant K and …阐明论证常用词:confirm, demonstrate, find, identify, indicate, monitor, note, observe, point out, prove, provide句式:The initial particles are found to be …It is found that the amorphous silicon nitride show a tendency in...It is noted that …can be found in …The result provides a sound basis for …The study of those properties indicate…The experimental results demonstrate that…The effects of …were observed and monitored.说明试验过程常用词:experiment, test, sample句式:The samples of pyroelectric ceramics (电释热陶瓷)亚©[© collected by …We sampled the blood and urine of …The blood screening test for the AIDS antibody has been carried out on…We experimented on the sintering property(流延特性)of …The new protocol architecture for distributed multimedia systems has been tested in …介绍应用、用途常用词:application, use及其动词形式句式:In this paper, the czochralski crystal growth method has been applied in ……technique is used to …The application of the new design is to develop and maintain …展示研究结果常用词:result, cause, increase, lessen, as a result, result in, arrive at句式:As a result we have got pure particle of ...The finding of our research on methodologies in …is….The results of calculation show that the minimum velocity arrives at...The relationship between …and ...is characterized by …The room temperature resistivity is lessened to …介绍结论常用词:conclude, summary, to sum up, lead to, in conclusion, conclusion句式:It is concluded that the absorption spectra of two kinds of particles include... We concluded that …It is concluded that...The conclusion of our research is …On the basis of …,the following conclusion can be drawn …Finally, a summary is given of …To sum up, we have revealed …Our argument proceeds in …The research has led to the discovery of …进行评述句式:There are hardly any data about …Middle management is considered as the go-between of …The shapes and locations of these inclusions are believed to be related to …The finding is acknowledged as essential to ...Existing methods are not sufficient for ...It is difficult to improve the therapy under the conditions of ...The disproportion of age groups will unfortunately lead to …The improper use of methods would seriously influence the performance of …The subject will deepen the understanding of …However, it does not mean that there is no limitation of ...It is well-known that in the field of .., there are still difficulties and challenges. Environmental protection has become the most important concern of …推荐和建议常用词:propose, suggest, recommend句式:The calculation suggests that…Bulk silk is proposed to be the alternative of ordinary silk because ...The finite element method is recommended to …提出进一步研究的可能性常用词:demand, desirable, expect, necessary, necessity, need, require, requirement 句式:Another term of the …need addressing because…However, the development of MRI is absolutely necessary for …To establish a .. .model continues to be a major concern for ...The underway measurement of sea surface temperature has made it necessary to... ..requires more work on …More concern about the blood cleaning point out the need for …There is a growing demand for …There is a surge in the use of …Although there is already an efficient procedure, more study is still needed.突出论文重点句式:The development of…is the primary concern of this paper.Particular attention is paid on the cultivation of …Interface structure is emphasized in the article because …This paper concentrates on the effects of …The chief consideration is …。
abstract是什么意思

abstract是什么意思abstract,他有几种词性?有形容词之外,还有哪些呢?下面店铺为大家带来abstract是什么意思,欢迎大家一起学习!abstract的英语音标英 [ˈæbstrækt] 美 [ˈæbˌstrækt]abstract的时态过去分词: abstracted 复数: abstracts 过去式: abstracted 现在分词: abstractingabstract的意思adj. 抽象的,理论上的; 难解的; 抽象派的; 茫然的;n. 抽象概念; 抽象派艺术作品; 摘要; [化]萃取物;vt. 提取,分离; 转移(注意等); 概括,摘录; <婉辞>剽窃; abstract的近义词n. [图情]摘要;抽象;抽象的概念brief , summary , resumeadj. 抽象的;深奥的deep , nonobjectivevt. [图情]摘要;提取;使……抽象化extract , briefabstract的同根词词根: abstractadj.abstracted 心不在焉的;出神的;分离出来的;抽出的abstractionist 抽象派艺术的abstractive 摘要式的;具有抽象能力的adv.abstractly 抽象地;理论上地abstractedly 茫然地;抽象地;心不在焉地n.abstraction 抽象;提取;抽象概念;空想;心不在焉abstractionism 抽象派艺术;抽象主义理论abstractionist 抽象派艺术家;理想主义者abstractor 萃取器;[图情] 摘录者abstract的词语辨析abstract, summary, resume, digest, outline这组词都有“摘要、概要、概括”的意思,其区别是:abstract 指论文、书籍等正文前的内容摘要,尤指学术论文或法律文件的研究提要。
(完整word版)如何写英文Abstract

How to Write an Abstract一、什么是摘要Abstract?an abstract comprises one paragraph which describes the main content of a paper and appears at the very beginning of the paper.摘要是叙述文章主要内容的一个段落,并且位于文章的开头部分.摘要是以梗概形式呈现的一篇文章要点的总结,它强调了一篇文章所包含的重要的信息.它也可以帮助读者快速的了解到是否这篇文章是他们感兴趣的,是否他们需要来阅读整篇文章。
而且,国家或国际出版社的编辑通常通过浏览投稿文章的摘要来决定是否投稿人的文章是可以被录用的。
因此,对于学者和研究人员来说,写一份好的摘要至关重要。
二、写作Abstract的目的对于科技论文的摘要,Abstract的目的有以下几点:1.Introduce journal articles.rm readers about article`s content.3.Help readers decide whether or not to read article.4.Overview conference programs,abstract collections,and book chapters.三、学习写作Abstract的必要性1。
Helps you present complex information in a clear,concise manner。
2.Helps you read abstracts more effectively.3。
Helps you conduct research.4.Helps you write abstracts for future publications。
5.Helps you condense report information into a short format for database searches。
abstract

}
7)接口可以定义变量来引用实现类的对象。(接口的多态)
接口多态的体现:
a.接口可以作为变量来引用对象
b.接口可以作为参数来引用对象。
c.接口可以作为返回值来引用对象。
3)抽象类中的抽象方法也需要使用 修饰,同时,
不能存在方法体。
抽象方法:使用abstract关键字修饰的方法,
不能有方法体。
4)抽象类中不一定有抽象方法。有无抽象方法对
3)抽象类可以被抽象类和具体类所继承。
类也可以被抽象类和具体类所继承。
2.JavaBean规范:
1)什么是JavaBean规范?
缩写方式: int i=10;
4)接口中的方法:
public abstract 返回值 方法名(参数列表);
缩写方式: public 返回值 方法名(参数列表);
修饰符 class 类名 implements 接口1,接口2{
//类体
}
d.接口的特性:
1)接口不能实例化。
2)接口中包含的全部方法都是抽象方法。全部属性都是常量.
this.idCard = idCard;
this.balance = balance;
}
public String getIdCard() {
return idCard;
}
(根据名词中存在相同行为,根据is-a 关系去建立,
根据系统的重点研究对象来确定)
(2)定义接口
将所有的行为在接口中定义出来,形成规范和约束。
(3)建立实现类并且实现接口。
d.面向接口编程好处:
public void setIdCard(String idCard) {
abstract怎么写

1.abstract怎么写abstract(抽象)修饰符,可以修饰类和方法1,abstract修饰类,会使这个类成为一个抽象类,这个类将不能生成对象实例,但可以做为对象变量声明的类型,也就是编译时类型,抽象类就像当于一类的半成品,需要子类继承并覆盖其中的抽象方法。
2,abstract修饰方法,会使这个方法变成抽象方法,也就是只有声明(定义)而没有实现,实现部分以";"代替。
需要子类继承实现(覆盖)。
注意:有抽象方法的类一定是抽象类。
但是抽象类中不一定都是抽象方法,也可以全是具体方法。
abstract修饰符在修饰类时必须放在类名前。
abstract修饰方法就是要求其子类覆盖(实现)这个方法。
调用时可以以多态方式调用子类覆盖(实现)后的方法,也就是说抽象方法必须在其子类中实现,除非子类本身也是抽象类。
注意:父类是抽象类,其中有抽象方法,那么子类继承父类,并把父类中的所有抽象方法都实现(覆盖)了,子类才有创建对象的实例的能力,否则子类也必须是抽象类。
抽象类中可以有构造方法,是子类在构造子类对象时需要调用的父类(抽象类)的构造方法。
举个简单的例子下面有一个抽象类abstract class E{public abstract void show();//public abstract 可以省略}然后其它类如果继承它通常为了实现它里面的方法class F extends E{void show(){//写具体实现的代码}}最后再主方法里面定义一个父类引用指向子类对象,就会发生多态现象,比如E e=new F();e.show();实际调用了子类里面的show()方法这是从网上粘贴的,不知道符不符合你的意思2.abstract怎么写abstract(抽象)修饰符,可以修饰类和方法 1,abstract修饰类,会使这个类成为一个抽象类,这个类将不能生成对象实例,但可以做为对象变量声明的类型,也就是编译时类型,抽象类就像当于一类的半成品,需要子类继承并覆盖其中的抽象方法。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Syntax-based Vulnerability Testing of Frame-based Network ProtocolsOded Tal Department of Electrical and ComputerEngineering, RoyalMilitary College of Canada, Ontario, Canada odedtal1@Scott KnightDepartment of Electricaland ComputerEngineering, RoyalMilitary College ofCanada, Ontario, Canadaknight-s@rmc.caTom DeanDepartment of Electrical andComputer Engineering,Queen’s University, Ontario,Canadathomas.dean@ece.queensu.caAbstractSyntax-based vulnerability testing is a static black-box testing method for protocol implementations. It involves testing the Implementation Under Test (IUT) with a large number of mutated Protocol Data Units (PDUs), built by intentionally disobeying the protocol’s syntax. Security vulnerabilities can be discovered by detecting anomalous behaviour or crashes in the IUT (e.g. segmentation faults, buffer, heap or stack overflows, etc.) when it attempts to parse and use a mutated PDU. Previous research has led to the development of a protocol testing framework and methodology for syntax-based testing of protocols, whose abstract syntax is based on ASN.1 (Abstract Syntax Notation), and whose transfer syntax is based on BER or DER (Basic or Distinguished Encoding Rules). These protocols have syntactic structure information embedded in the PDU. However, many protocols are not specified using such standards and do not include embedded syntactic structure information. Instead the byte sequence of the data in the PDUs is specified using frame-based PDU definitions in the protocol specification. This paper presents research that extends the previous testing tools and techniques to include frame-based protocols. OSPF is such a protocol. Several well-known OSPF protocol implementations are tested for protocol vulnerabilities. Security vulnerabilities have been found in some implementations.1. Introduction1.1.PrefaceComputer network communications are subject to attack. Manufacturers of network products need efficient techniques to perform vulnerability testing on their product offerings. Security vulnerabilities can reveal themselves in many forms, such as segmentation faults, or stack, heap or buffer overflows, which cause the implementation of a theoretically sound protocol to fail. This can enable an attacker to gain privileges, or to disrupt or interfere with the functionality of the system implementing the protocol.Previous work in syntax-based vulnerability testing by the PROTOS project is described in [1]. We describe in a related work [2] a general methodology and tools for security assessment of network protocol-implementations whose abstract syntax is based on ASN.1 (Abstract Syntax Notation) and whose transfer syntax is based on the BER/DER encoding schemes (Basic or Distinguished Encoding Rules) [3]. The testing framework is called Protocol-tester.This work extends the testing framework to frame-based protocols. Frame-based protocols are those in which the structure of each PDU (Protocol Data Unit) is specified by a “frame,” which explicitly defines the order of data fields in the PDU, as well as the exact length of each field. It involves testing the Implementation Under Test (IUT) with a large number of mutated PDUs, which are built by intentionally violating the protocol’s syntax. The paper will describe the application of the vulnerability testing technique to the OSPF (Open Shortest Path First) protocol- a common routing protocol for local area networks.1.2. ObjectiveThe objective of this work is to extend the current work with Protocol-tester to frame-based and mixed protocols.A language and mechanism are required for supplying the syntactic structural information for a frame-based protocol such that individual PDUs can be parsed and test cases can be generated from them by using the existing generic Protocol-tester tools.1.3. Paper OutlineSection 2 provides the background for the current work. Section 3 describes previous work in syntax testing and in OSPF testing. The approach and the tools are described in Section 4. Section 5 describes the test environment and test-suite design. Section 6 describes the results of testing OSPFv2 protocol implementations and Section 7 concludes the paper.2. Background2.1. Protocol Types2.1.1. Frame-based Protocols : PDU structure is specified by a “frame,” which explicitly defines the order and the exact length of each data field. For example, the checksum field of the Hello packet of the OSPF protocol (Table 1) always starts at byte #13, and is 2-byte long. The number of “neighbours” can vary, but the first one always starts at byte #45, and each neighbour is 4-byte long. Other well-known frame-based protocols are ICMP, IP and UDP.Table 1. The OSPF Hello packetByte 1 2 3 4Version Type Packet length Router IDArea IDChecksum AuthenticationTypeAuthentication OSPFHeader Authentication Network Mask Hello Interval Options RouterPriorityRouter Dead Interval Designated Router HelloHeader Backup Designated RouterNeighbour Neighbours……2.1.2. ASN.1 based protocols : The abstract syntax is specified using ASN.1- a formal notation standard. An important characteristic of ASN.1 is that the field length is not specified, and therefore a separate transfer syntax specification is needed, usually based on BER or DER. BER is a transfer syntax based on octets (8-bit bytes). DER- a subset of BER- follows the format of a TLV triplet (Type, Length, Value). Well-known ASN.1-based and BER/DER-encoded protocols are LDAP and SNMP.2.1.3. Mixed protocols : A frame-based protocol, where at least one field consists of one or more TLV triplets or LV doublets. BGP, TCP and SSL are mixed protocols.2.2. The OSPF ProtocolOSPF is based on the exchange of Link State Advertisements (LSAs) containing information on attached neighbours, including the cost (“metric”) of sending packets to each of them. Routers store LSAs in their databases and use Dijkstra's Algorithm to calculatethe shortest path between source and target. In OSPFv2[4] there are five types of OSPF packets (Table 2).Table 2. OSPF packet types# Type name Sub-unit Comments 1 H e l oNeighbour Sent periodically 2 Database Description LSA header Sent when a newneighbour join in 3 Link State Request (LSR) LSA sub-header Sent when partsof the link-state database are out-of-date. 4 Link State Update (LSU) LSA Sent in responseto an LSR. 5 Link State Acknowledg ementLSA header Sent in responseto an LSU. 3. Previous work3.1. Syntax testingSyntax testing is a static, black-box testing technique for protocol implementations. Beizer [5] proposes that one specify the syntax for the protocol in a convenient notation such as Backus-Naur Form (BNF) [6]. Mutations are then made to the syntactic elements, and the modified grammar is used to produce aberrant test vectors (PDUs). Beizer suggests using an “anti-parser” to compile the grammar to produce “structured garbage.” He also suggests targeting one field of the input at a time at first, and then designing test cases with combinations of input. As in other black-box testing techniques, syntax testing does not have a clear stopping criterion. Test engineers have to use their experience, common sense or time/cost constraints while designing the test-suite.3.2. The PROTOS projectThe PROTOS project group from Oulu University, Finland, [1] followed Beizer’s approach. They have specified the grammar for the WAP, HTTP, LDAP and SNMP protocols. They parse the grammar specifications to produce a parse-tree representation of the protocol. They then manipulate the tree and use the mutated tree to generate thousands of malformed PDUs whose purpose is revealing faults in the handling of input data in the IUT. An IUT is considered to have passed the test if it has rejected the anomalous input without exhibiting such phenomena as crashing, hanging, or causing an illegal access to memory.3.3. Protocol-testerProtocol-tester [2] is a testing environment that uses a different approach for syntax-based vulnerability testing of protocol implementations, by mutating the PDUs rather than a complete expression of a specific protocol’s grammar. The basis for PDU mutation is a general ASN.1 grammar and a general DER grammar, both written in TXL1 [7]. A mark-up/implement architecture and various tools enable the test engineer to specify test-case parameters in a script-like language, and to automatically generate test cases, each containing one or more syntax errors, from a single, valid PDU. Test-case generation by Protocol-tester is driven by a number of mutation rules. The rules specify different kinds of changes to be made to the fields of the PDU based on the type of the field. Mutations can also involve a number of fields (e.g. swapping elements), or structural modifications (e.g. adding or removing sub-components of the PDU). PDU mutation is carried out in two phases: (1) An optional error-code is added to each ASN.1 type, in order to specify the nature of the mutation to be performed at the next phase. (2) Various mutations are executed on a valid PDU, using the transformation definitions specific to each mutation type. Each legitimate PDU can be used to generate many test-case PDUs (in the order of thousands). The methodology was demonstrated on the X.509, PCKS7 and SNMP protocols and is suitable for ASN.1 based protocols using BER or DER.3.4. Previous work in OSPF testingJou et al. [8] have used several dynamic attacks, called Seq++, MaxAge, MaxSeq++ and LSID attack to disrupt the operation of a target OSPF implementation. These attacks use white-box techniques to exploit specific perceived vulnerabilities in the protocol by using specific exchanges of PDUs with the IUT. They do not attempt to compromise the integrity of the router itself, only its routing tables. Jacob [9] carried out extensive conformance testing on an OSPFv2 package. Some of the test-cases were based on static black-box attacks using invalid packets. All the test cases were individually conceived, and manually constructed. Wu et al. [10] carried out conformance, interoperability and performance tests on OSPF using a dynamic black-box testing approach. Their main contribution was the addition of passive testing to the more traditional active testing. Passive testing focuses on protocol abnormalities such as route oscillations, useless route advertisements and exhausted routers, which usually appear only a long time after the network enters a “stable” state.1TXL is a functional programming language, specifically designed to handle transformation tasks. 4. Approach4.1. OverviewThe general approach taken for this work is based on automatic, active, static black-box testing, (Figure 1). After using Snort [11] to gather OSPF packets from the test environment and saving them in separate binary files, each packet is transformed into a TXL-readable text file by Packet-parser. Each text file is then mutated by Protocol-tester, based on user-specified mutation commands. This results in numerous mutated PDUs, saved as binary files. The mutated packets are re-injected to the test environment by Packet Injector and Monitor. The same program also monitors the health of the target application by sending a good Link State Request (LSR) packet after each mutated packet, and waiting for the target’s reply in the form of a Link State Update (LSU) packet. When the target fails to reply, the testing is stopped in order to investigate the cause of the failure.Fig. 1. The general approach4.2. Packet-parserPacket-parser is a C program developed as part of this work, which can parse a frame-based/mixed protocol PDU into its fields. It creates a text file, which serves as the input to Protocol-tester. This intermediate file has an ASN.1 style, so that the existing Protocol-tester tool can perform mutations on a generic, abstract representation of the PDU. Packet-parser parses the PDU by using syntactic structural specifications, specified by the test engineer using a set of structure-files. The structure-files are based on a Protocol Description Language (PDL). Each structure-file represents a stand-alone component of the protocol structure. For example, the structure-file for the Hello Header + Neighbours (Table 1) includes:1) Meta dataH eader length: 20 bytesS ub-unit length: 4 bytes (for each neighbour)T ype field number: 0 (no type field in this unit)L ength field number: 0 (ditto)N umber of sub-units field number: 0 (ditto).2) Next_filesBinary packetfilesTXL-readablefilesMutated OSPFpacketsNumber of next_files: 0(the Hello packet endsafter the last neighbour. No other structure-files arerequired for describing/parsing the rest of thepacket).Next_file numbers: none (ditto).3) Number of structural tokens: 14 (see next section)4) Structural tokens (numbers from 1-24):5 (Sequence)6 (open)4 (4 byte integer- Network Mask)2 (2 byte integer- Hello Interval)1 (1 byte integer- Options)1 (1 byte integer- Router Priority)4 (4 byte integer- Router Dead Interval)4 (4 byte integer- Designated router)4 (4 byte integer- Backup Designated Router)7 (close)9 (Set of)4 (4 byte integer- Neighbour)7 (close)12 (end of structure-file)The Hello structure-file is a numerically encoded file, containing the above numbers in a specific order: 14H, 4, 0, 0, 0, 0, E, 5, 6, 4, 2, 1, 1, 4, 4, 4, 7, 9, 4, 7, C.It is one of 13 structure-files, which describe OSPF packets to Packet-parser. Packet-parser parses a binary OSPF packet by consecutively reading bytes from the packet, according to the information in the relevant structure-file. It starts with the first structure-file (OSPF header) and then opens, uses and closes other structure-files recursively, as required.The current numerically encoded structure files are created manually. Currently a friendlier, human-readable language is being developed to specify the packet structure of the protocol to be tested.Packet-parser has been used for parsing frame-based protocols (OSPF, RIP) and mixed protocols (BGP, TCP).4.3. Packet Injector and MonitorPacket Injector and Monitor is a C program used to inject IP packets onto a network and monitor the health of the target IUT. The program uses the set of mutated test PDUs produced by Protocol-tester. It iterates over the set by reading a mutated packet, calculating and updating its OSPF header checksum and length, and adding an IP header. It then injects the packet onto the network. The monitor part of the tool then injects a good Link State Request (LSR) packet in order to trigger a response from the target IUT. The injection of the next mutated packet is carried out immediately after receiving a valid Link State Update packet from the target. If the target does not respond, the program halts and the test packet causing the failure in the IUT is investigated. 5. Conducting the tests5.1. Test EnvironmentFigure 2 describes the network topology of the test environment. There were three OSPF IUTs involved in the testing: Zebra, Windows 2000 Advanced Server, and Cisco IOS. Workstations CSL3 and CSL7 are physical computers running Linux Red Hat 8.0 [12] and VMware 3.2 [13]. All other machines are virtual VMware machines on the respective Linux host workstations.The Zebra 0.93 OSPF daemon [14] was tested on three platforms: Red Hat 8.0 Linux on a real physical machine and on a virtual machine and OpenBSD 3.3 [15] on a virtual machine.The Windows 2000 Advanced Server [16] was tested on a virtual machine. A Cisco 2621 Router running IOS 12.0(7)T was also tested. A Windows 2000 virtual machine was used to run Packet Injector and Monitor. 5.2. Test-suite DesignFifteen test-suites, each containing between 3,000 – 4,000 mutated packets, were produced for each IUT by mutating all five OSPF packet types, using three mutation strategies:1.Replacement: Replacing one field at a time withboundary and mid-way values, i.e. 00, 7F, 80, FF, 0000, 7FFF, 8001, FFFF, 00000000, 7FFFFFFF, 80000001, FFFFFFFF, 0000000000000000 and FFFFFFFFFFFFFFFF.2.Removal: Removing one field at a time, and thenremoving pairs of fields, one pair at a time.3.Permutation: Permutating pairs of fields withineach SEQUENCE and SET.Fig. 2. Test environment topologyLinux03Windows2000Linux076. Results6.1. GeneralTable 3 summarizes the results of attacking OSPF implementations on 5 different targets. It shows for each test-suite the OSPF type of the original, unmutated PDU, the mutation strategies and the results. A “+” sign means that the OSPF implementation crashed at least once.6.2. Test Results for Zebra OSPF Daemon6.2.1. Overview . The OSPF daemon crashed at least onceon 10 out of 15 test-suites on Linux and VMware/Linux, and on 8 out of 15 test-suites on OpenBSD. After each crash the operating system continued to function normally, however the OSPF daemon had to be reset to continue with testing. Therefore, at the very least the systems seem to be vulnerable to Denial of Service (DoS) attacks.The test cases were run against each IUT a number of times. It is interesting to note that the crashing behaviour of the OSPF daemon on the targets was inconsistent; the same test cases sometimes caused the target to crash and at other times they did not. This behaviour was investigated by using debugging tools and examining the IUT source code. The observed crashes were caused by three security vulnerabilities.Table 3. Test resultsOSPF daemon crashes*ZebraOSPF daemonon Original packet type Mutation strategy 1 2 3Win Cis Replace + + + +Remove Hello Permutate + + +Replace + + + RemoveDatabase Description Permutate + + +Replace + + RemoveLink State Request Permutate + + +Replace + + + + Remove +Link State Update Permutate + + +Replace + + RemoveLink State Ack. Permutate + +Successful test-suites 15 test-suites 10 10 8 2 0* 1: VMware 3.2 + Red Hat 8.0 Linux 2: Red Hat 8.0 Linux3: VMware 3.2 + OpenBSD 3.3 Win: Windows 2000 Advanced Server Cis: Cisco 2621 Router, IOS 12.0(7)T6.2.2. A security vulnerability in the OSPF checksum routine. The OSPF checksum routine (in_cksum in checksum.c) does not compare the length field in the OSPF header to the length field in the IP header. When the length field in the mutated OSPF header is larger than the actual packet size, the routine can crash due to a segmentation fault. This occurs because the packet is stored in a buffer in the heap. As the checksum algorithm continues to read past the actual end of the packet due to the erroneous length field it can end up reading past the end of the heap into unauthorized memory space.6.2.3. A security vulnerability in the LSA checksum routine. The LSA checksum routine (ospf_lsa_checksum in ospf_lsa.c) does not verify the validity of the length field in the LSA header. When the length field in the mutated LSA header is larger than the actual packet size, the routine can crash due to a segmentation fault. This can happen only with LSU packets. The causes of this error are very similar to those in section 6.2.2 above.6.2.4. A security vulnerability in the OSPF daemon’s main routine. The implementation crashed because of a segmentation fault caused while calling the dynamic memory allocation function calloc(). This class of error is often due to heap overflow. It can obviously be exploited by a hacker for DoS attack. However in some cases this class of error can be exploited with more dangerous results such as the execution of arbitrary malicious code.6.3. Test Results for Windows 2000 Advanced Server6.3.1. Overview. The OSPF daemon crashed at least once on 2 out of 15 test-suites. Three types of crashes were observed: 1.Temporary crash: the Operating System (OS) continued to function normally, and the OSPF daemon started working again after about 10 minutes.2. Semi-permanent crash: the OS continued to function normally. Stopping and restarting the OSPF daemon restored it to service.3.Permanent crash: the OS unexpectedly terminated several services, including System Event Notification, Routing and Remote Access, Removable Storage, Network Connections, Internet Authentication and COM + Event System. It had to be rebooted.Again the test cases were run against the IUT a number of times. The crashing behaviour of the OSPF daemon was inconsistent. The same test-suite sometimes caused it to crash at different mutated packets, to crash differently, or not to crash at all. This suggests that the vulnerability is related to the heap and is sensitive to the location of the packet in the heap.6.3.2. Causes for crashing.The root causes for the crashes have not been isolated since the source code is not available, and the vendor may not welcome reverse engineering of the mechanism in question. Further investigation will involve additional black-box syntax-based testing to identify recurring fault scenarios and then working with the vendor to identify the cause.6.4. Test results for the Cisco RouterThe OSPF implementation in Cisco 2621 Router did not crash. Therefore, it was also tested by manually mutated packets, based on additional mutation strategies, including:1.Structure-level mutations, e.g. Router LSAs,where the number of Links is smaller or larger than specified in the Router header, including zero.2.Contents-level mutations, e.g. LSA sequencenumber is 7FFFFFFF (MaxSeq# attack).3.Stress testing: sending maximum length packets(64k bytes) for two hours.The implementation did not crash as a result of any of the test scenarios.7. ConclusionsThe paper describes a vulnerability testing technique for frame-based network communication protocols. The vulnerability-testing framework was used to test several commercial implementations of the OSPF protocol.The Zebra 0.93 OSPF daemon was shown to be vulnerable to Denial of Service attacks (at least) due to bugs in its OSPF checksum function, LSA checksum function and the main routine.The OSPF daemon in Windows 2000 Advances Server was also shown to be vulnerable to Denial of Service attacks.No vulnerabilities were discovered in the Cisco 2621 (IOS 12.0) OSPF daemon.The test trials of these OSPF products yielded some interesting results but they are more interesting as a proof-of-concept for the technique.This work is novel in that it is a static black-box technique specifically suited to security vulnerability testing. A vendor or system integrator using the technique does not need to know the internal structure of the network products being tested. The technique is easily portable to new protocols. Future work includes improving the protocol description language to allow PDU structural information to be more easily specified by a test engineer. There is also important work that can be done in identifying common semantic relationships between syntactic elements of a protocol. These tend to be captured in the textual descriptions in the protocol specifications. Identifying common relationships and can be useful in identifying more complex testing strategies that can be used to improve the current mutation command libraries.References1.R. Kaksonen, M. Laasko and A. Takanen. (2000).“Vulnerability analysis of software through syntax testing”.University of Oulu, Finland.Available:http://www.ee.oulu.fi/research/ouspg/protos/analysis/WP20 00-robustness/index.html.2. Y. Turcotte, O. Tal, S. Knight and T. Dean, “Universalmethodology and tools for syntax-based vulnerability testing of protocol implementations”. Accepted for publication in MILCOM 2004.3. O. Dubuisson, ASN.1 Communication betweenHeterogeneous Systems. Academic Press, San Diego, 2001.4. J. Moy, “OSPF Version 2, RFC 2328” (1988, April).Available: /rfcs/rfc2328.html.5. B. Beizer, Software Testing Techniques, 2nd Edition. VanNostrand Reinhold, New York, 1990.6. P. Naur, (ed.), “Revised report on the algorithmic languageALGOL 60”, Communications of the ACM, vol. 3, May 1960, pp. 299-314.7. J. Cordy. (2000). “The TXL programming language v.10”.Available: http://www.txl.ca/nabouttxl.html.8. Y.F. Jou, F. Gong, C. Sargor, X. Wu, S.F. Wu, H.C. Changand F. Wang, “Design and implementation of a scalable intrusion detection system for the protection of network infrastructure,” in Proc. DARPA Information Survivability Conference and Exposition, 2000.9. D. Jacob, “Testing intra-domain routing in a networksimulator”. Universität des Saarlandes, Germany, Diploma Thesis, Jan. 2002.10. J. Wu, Y. Zhao and X. Yin, “From active to passive:Progress in testing of Internet protocols”, in Proc. 21st International Conference on Formal Techniques for Networked and Distributed Systems, 2001.11. Snort. Available: /.12. Red Hat 8.0. (2002, Sep.). Available:/about/presscenter/2002/press_eightoh.html.13. VMware 3.2. Available:/support/ws3/doc/releasenotes_ws32.html.14. Zebra 0.93. Available: /.15. OpenBSD 3.3 (2003, May).Available: /33.html.16. Windows 2000 Advanced Server. Available:/windows2000/advancedse rver/default.as.。
