A new algorithm for degree-constrained minimum spanning tree based on the reduction technique
外文文献文献列表
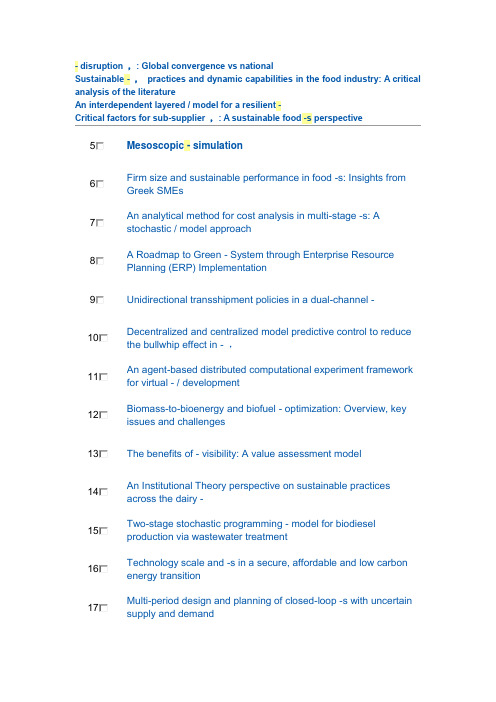
- disruption ,: Global convergence vs nationalSustainable - ,practices and dynamic capabilities in the food industry: A critical analysis of the literature5 Mesoscopic - simulation6 Firm size and sustainable performance in food -s: Insights from Greek SMEs7 An analytical method for cost analysis in multi-stage -s: A stochastic / model approach8 A Roadmap to Green - System through Enterprise Resource Planning (ERP) Implementation9 Unidirectional transshipment policies in a dual-channel -10 Decentralized and centralized model predictive control to reduce the bullwhip effect in - ,11 An agent-based distributed computational experiment framework for virtual - / development12 Biomass-to-bioenergy and biofuel - optimization: Overview, key issues and challenges13 The benefits of - visibility: A value assessment model14 An Institutional Theory perspective on sustainable practices across the dairy -15 Two-stage stochastic programming - model for biodiesel production via wastewater treatment16 Technology scale and -s in a secure, affordable and low carbon energy transition17 Multi-period design and planning of closed-loop -s with uncertain supply and demand18 Quality control in food - ,: An analytical model and case study of the adulterated milk incident in China19 - information capabilities and performance outcomes: An empirical study of Korean steel suppliers20 A game-based approach towards facilitating decision making for perishable products: An example of blood -21 - design under quality disruptions and tainted materials delivery22 A two-level replenishment frequency model for TOC - replenishment systems under capacity constraint23 - dynamics and the ―cross-border effect‖: The U.S.–Mexican border’s case24 Designing a new - for competition against an existing -25 Universal supplier selection via multi-dimensional auction mechanisms for two-way competition in oligopoly market of -26 Using TODIM to evaluate green - practices under uncertainty27 - downsizing under bankruptcy: A robust optimization approach28 Coordination mechanism for a deteriorating item in a two-level - system29 An accelerated Benders decomposition algorithm for sustainable - / design under uncertainty: A case study of medical needle and syringe -30 Bullwhip Effect Study in a Constrained -31 Two-echelon multiple-vehicle location–routing problem with time windows for optimization of sustainable - / of perishable food32 Research on pricing and coordination strategy of green - under hybrid production mode33 Agent-system co-development in - research: Propositions and demonstrative findings34 Tactical ,for coordinated -s35 Photovoltaic - coordination with strategic consumers in China36 Coordinating supplier׳s reorder point: A coordination mechanism for -s with long supplier lead time37 Assessment and optimization of forest biomass -s from economic, social and environmental perspectives – A review of literature38 The effects of a trust mechanism on a dynamic - /39 Economic and environmental assessment of reusable plastic containers: A food catering - case study40 Competitive pricing and ordering decisions in a multiple-channel -41 Pricing in a - for auction bidding under information asymmetry42 Dynamic analysis of feasibility in ethanol - for biofuel production in Mexico43 The impact of partial information sharing in a two-echelon -44 Choice of - governance: Self-managing or outsourcing?45 Joint production and delivery lot sizing for a make-to-order producer–buyer - with transportation cost46 Hybrid algorithm for a vendor managed inventory system in a two-echelon -47 Traceability in a food -: Safety and quality perspectives48 Transferring and sharing exchange-rate risk in a risk-averse - of a multinational firm49 Analyzing the impacts of carbon regulatory mechanisms on supplier and mode selection decisions: An application to a biofuel -50 Product quality and return policy in a - under risk aversion of a supplier51 Mining logistics data to assure the quality in a sustainable food -: A case in the red wine industry52 Biomass - optimisation for Organosolv-based biorefineries53 Exact solutions to the - equations for arbitrary, time-dependent demands54 Designing a sustainable closed-loop - / based on triple bottom line approach: A comparison of metaheuristics hybridization techniques55 A study of the LCA based biofuel - multi-objective optimization model with multi-conversion paths in China56 A hybrid two-stock inventory control model for a reverse -57 Dynamics of judicial service -s58 Optimizing an integrated vendor-managed inventory system for a single-vendor two-buyer - with determining weighting factor for vendor׳s ordering59 Measuring - Resilience Using a Deterministic Modeling Approach60 A LCA Based Biofuel - Analysis Framework61 A neo-institutional perspective of -s and energy security: Bioenergy in the UK62 Modified penalty function method for optimal social welfare of electric power - with transmission constraints63 Optimization of blood - with shortened shelf lives and ABO compatibility64 Diversified firms on dynamical - cope with financial crisis better65 Securitization of energy -s in China66 Optimal design of the auto parts - for JIT operations: Sequential bifurcation factor screening and multi-response surface methodology67 Achieving sustainable -s through energy justice68 - agility: Securing performance for Chinese manufacturers69 Energy price risk and the sustainability of demand side -s70 Strategic and tactical mathematical programming models within the crude oil - context - A review71 An analysis of the structural complexity of - /s72 Business process re-design methodology to support - integration73 Could - technology improve food operators’ innovativeness? A developing country’s perspective74 RFID-enabled process reengineering of closed-loop -s in the healthcare industry of Singapore75 Order-Up-To policies in Information Exchange -s76 Robust design and operations of hydrocarbon biofuel - integrating with existing petroleum refineries considering unit cost objective77 Trade-offs in - transparency: the case of Nudie Jeans78 Healthcare - operations: Why are doctors reluctant to consolidate?79 Impact on the optimal design of bioethanol -s by a new European Commission proposal80 Managerial research on the pharmaceutical - – A critical review and some insights for future directions81 - performance evaluation with data envelopment analysis and balanced scorecard approach82 Integrated - design for commodity chemicals production via woody biomass fast pyrolysis and upgrading83 Governance of sustainable -s in the fast fashion industry84 Temperature ,for the quality assurance of a perishable food -85 Modeling of biomass-to-energy - operations: Applications, challenges and research directions86 Assessing Risk Factors in Collaborative - with the Analytic Hierarchy Process (AHP)87 Random / models and sensitivity algorithms for the analysis of ordering time and inventory state in multi-stage -s88 Information sharing and collaborative behaviors in enabling - performance: A social exchange perspective89 The coordinating contracts for a fuzzy - with effort and price dependent demand90 Criticality analysis and the -: Leveraging representational assurance91 Economic model predictive control for inventory ,in -s92 - ,ontology from an ontology engineering perspective93 Surplus division and investment incentives in -s: A biform-game analysis94 Biofuels for road transport: Analysing evolving -s in Sweden from an energy security perspective95 - ,executives in corporate upper echelons Original Research Article96 Sustainable - ,in the fast fashion industry: An analysis of corporate reports97 An improved method for managing catastrophic - disruptions98 The equilibrium of closed-loop - super/ with time-dependent parameters99 A bi-objective stochastic programming model for a centralized green - with deteriorating products100 Simultaneous control of vehicle routing and inventory for dynamic inbound -101 Environmental impacts of roundwood - options in Michigan: life-cycle assessment of harvest and transport stages102 A recovery mechanism for a two echelon - system under supply disruption103 Challenges and Competitiveness Indicators for the Sustainable Development of the - in Food Industry104 Is doing more doing better? The relationship between responsible - ,and corporate reputation105 Connecting product design, process and - decisions to strengthen global - capabilities106 A computational study for common / design in multi-commodity -s107 Optimal production and procurement decisions in a - with an option contract and partial backordering under uncertainties108 Methods to optimise the design and ,of biomass-for-bioenergy -s: A review109 Reverse - coordination by revenue sharing contract: A case for the personal computers industry110 SCOlog: A logic-based approach to analysing - operation dynamics111 Removing the blinders: A literature review on the potential of nanoscale technologies for the ,of -s112 Transition inertia due to competition in -s with remanufacturing and recycling: A systems dynamics mode113 Optimal design of advanced drop-in hydrocarbon biofuel - integrating with existing petroleum refineries under uncertainty114 Revenue-sharing contracts across an extended -115 An integrated revenue sharing and quantity discounts contract for coordinating a - dealing with short life-cycle products116 Total JIT (T-JIT) and its impact on - competency and organizational performance117 Logistical - design for bioeconomy applications118 A note on ―Quality investment and inspection policy in a supplier-manufacturer -‖119 Developing a Resilient -120 Cyber - risk ,: Revolutionizing the strategic control of critical IT systems121 Defining value chain architectures: Linking strategic value creation to operational - design122 Aligning the sustainable - to green marketing needs: A case study123 Decision support and intelligent systems in the textile and apparel -: An academic review of research articles124 - ,capability of small and medium sized family businesses in India: A multiple case study approach125 - collaboration: Impact of success in long-term partnerships126 Collaboration capacity for sustainable - ,: small and medium-sized enterprises in Mexico127 Advanced traceability system in aquaculture -128 - information systems strategy: Impacts on - performance and firm performance129 Performance of - collaboration – A simulation study130 Coordinating a three-level - with delay in payments and a discounted interest rate131 An integrated framework for agent basedinventory–production–transportation modeling and distributed simulation of -s132 Optimal - design and ,over a multi-period horizon under demand uncertainty. Part I: MINLP and MILP models133 The impact of knowledge transfer and complexity on - flexibility: A knowledge-based view134 An innovative - performance measurement system incorporating Research and Development (R&D) and marketing policy135 Robust decision making for hybrid process - systems via model predictive control136 Combined pricing and - operations under price-dependent stochastic demand137 Balancing - competitiveness and robustness through ―virtual dual sourcing‖: Lessons from the Great East Japan Earthquake138 Solving a tri-objective - problem with modified NSGA-II algorithm 139 Sustaining long-term - partnerships using price-only contracts 140 On the impact of advertising initiatives in -s141 A typology of the situations of cooperation in -s142 A structured analysis of operations and - ,research in healthcare (1982–2011143 - practice and information quality: A - strategy study144 Manufacturer's pricing strategy in a two-level - with competing retailers and advertising cost dependent demand145 Closed-loop - / design under a fuzzy environment146 Timing and eco(nomic) efficiency of climate-friendly investments in -s147 Post-seismic - risk ,: A system dynamics disruption analysis approach for inventory and logistics planning148 The relationship between legitimacy, reputation, sustainability and branding for companies and their -s149 Linking - configuration to - perfrmance: A discrete event simulation model150 An integrated multi-objective model for allocating the limited sources in a multiple multi-stage lean -151 Price and leadtime competition, and coordination for make-to-order -s152 A model of resilient - / design: A two-stage programming with fuzzy shortest path153 Lead time variation control using reliable shipment equipment: An incentive scheme for - coordination154 Interpreting - dynamics: A quasi-chaos perspective155 A production-inventory model for a two-echelon - when demand is dependent on sales teams׳ initiatives156 Coordinating a dual-channel - with risk-averse under a two-way revenue sharing contract157 Energy supply planning and - optimization under uncertainty158 A hierarchical model of the impact of RFID practices on retail - performance159 An optimal solution to a three echelon - / with multi-product and multi-period160 A multi-echelon - model for municipal solid waste ,system 161 A multi-objective approach to - visibility and risk162 An integrated - model with errors in quality inspection and learning in production163 A fuzzy AHP-TOPSIS framework for ranking the solutions of Knowledge ,adoption in - to overcome its barriers164 A relational study of - agility, competitiveness and business performance in the oil and gas industry165 Cyber - security practices DNA – Filling in the puzzle using a diverse set of disciplines166 A three layer - model with multiple suppliers, manufacturers and retailers for multiple items167 Innovations in low input and organic dairy -s—What is acceptable in Europe168 Risk Variables in Wind Power -169 An analysis of - strategies in the regenerative medicine industry—Implications for future development170 A note on - coordination for joint determination of order quantity and reorder point using a credit option171 Implementation of a responsive - strategy in global complexity: The case of manufacturing firms172 - scheduling at the manufacturer to minimize inventory holding and delivery costs173 GBOM-oriented ,of production disruption risk and optimization of - construction175 Alliance or no alliance—Bargaining power in competing reverse -s174 Climate change risks and adaptation options across Australian seafood -s – A preliminary assessment176 Designing contracts for a closed-loop - under information asymmetry 177 Chemical - modeling for analysis of homeland security178 Chain liability in multitier -s? Responsibility attributions for unsustainable supplier behavior179 Quantifying the efficiency of price-only contracts in push -s over demand distributions of known supports180 Closed-loop - / design: A financial approach181 An integrated - / design problem for bidirectional flows182 Integrating multimodal transport into cellulosic biofuel - design under feedstock seasonality with a case study based on California183 - dynamic configuration as a result of new product development184 A genetic algorithm for optimizing defective goods - costs using JIT logistics and each-cycle lengths185 A - / design model for biomass co-firing in coal-fired power plants 186 Finance sourcing in a -187 Data quality for data science, predictive analytics, and big data in - ,: An introduction to the problem and suggestions for research and applications188 Consumer returns in a decentralized -189 Cost-based pricing model with value-added tax and corporate income tax for a - /190 A hard nut to crack! Implementing - sustainability in an emerging economy191 Optimal location of spelling yards for the northern Australian beef -192 Coordination of a socially responsible - using revenue sharing contract193 Multi-criteria decision making based on trust and reputation in -194 Hydrogen - architecture for bottom-up energy systems models. Part 1: Developing pathways195 Financialization across the Pacific: Manufacturing cost ratios, -s and power196 Integrating deterioration and lifetime constraints in production and - planning: A survey197 Joint economic lot sizing problem for a three—Layer - with stochastic demand198 Mean-risk analysis of radio frequency identification technology in - with inventory misplacement: Risk-sharing and coordination199 Dynamic impact on global -s performance of disruptions propagation produced by terrorist acts。
清华大学遗传算法PPT

3. Degree-based Permutation GA for dc-MST
4.1 Basic Concept of lc-MST 4.2 Genetic Algorithms Approach 4.3 GA procedure for lc-MST 4.4 Numerical Experiments
Soft Computing Lab.
WASEDA UNIVERSITY , IPS
Stochastic MST
Ishii, H., H. Shiode, & T. Nishida: Stochastic spanning tree problem, Discrete Applied Mathematics, vol.3, pp.263-273,1981.
Quadratic MST
Leaf-constrained MST
Fernandes, L. M. & L. Gouveia: Minimal spanning trees with a constraint on the number of leaves, European J. of Operational Research, vol.104, pp.250-261, 1998. Soft Computing Lab. WASEDA UNIVERSITY , IPS 7
3.1 Concept on Degree-based Permutation GA 3.2 Genetic Algorithms Approach 3.3 Degree-based Permutation GA for dc-MST 3.4 Numerical Experiments
机器学习题库

机器学习题库一、 极大似然1、 ML estimation of exponential model (10)A Gaussian distribution is often used to model data on the real line, but is sometimesinappropriate when the data are often close to zero but constrained to be nonnegative. In such cases one can fit an exponential distribution, whose probability density function is given by()1xb p x e b-=Given N observations x i drawn from such a distribution:(a) Write down the likelihood as a function of the scale parameter b.(b) Write down the derivative of the log likelihood.(c) Give a simple expression for the ML estimate for b.2、换成Poisson 分布:()|,0,1,2,...!x e p x y x θθθ-==()()()()()1111log |log log !log log !N Ni i i i N N i i i i l p x x x x N x θθθθθθ======--⎡⎤=--⎢⎥⎣⎦∑∑∑∑3、二、 贝叶斯假设在考试的多项选择中,考生知道正确答案的概率为p ,猜测答案的概率为1-p ,并且假设考生知道正确答案答对题的概率为1,猜中正确答案的概率为1,其中m 为多选项的数目。
一个新的对于无约束非凸优化问题渐近的算法

一个新的对于无约束非凸优化问题渐近的算法陈汝栋;吴成玉【摘要】For the optimization of nonconvex functions in mathematical programming,according to the know nconvex function optimization results and the corresponding algorithm,a new im-proved asymptotic algorithm is constructed,and by using Kurdyka-Lojasiewicz property,the convergence analysis of unconstrained nonconvex optimization problems for real lower semicon-tinuous nonconvex functions is considered.The sequence generated by the improved asymptotic algorithm has finite length and converges to a critical point of the function are obtained.Mean-while,the result representation of the convergence rate of the sequence is given.%针对数学规划中的非凸函数的优化问题,根据已知的凸函数的优化结果及相应算法,构造新的渐进算法,并运用Kurdyka-Lojasiewicz不等式,对真下半连续的非凸函数的无约束非凸优化问题进行了收敛分析,得到了由改进的渐进算法生成的序列具有有限长且收敛于该函数的一个临界点.同时给出了序列收敛速率的结果表示.【期刊名称】《纺织高校基础科学学报》【年(卷),期】2018(031)001【总页数】8页(P55-62)【关键词】渐近算法;Kurdyka-Lojasiewicz性质;无约束非凸优化问题;收敛速率【作者】陈汝栋;吴成玉【作者单位】天津工业大学理学院,天津 300387;天津工业大学理学院,天津300387【正文语种】中文【中图分类】O1770 引言在数学规划中,研究的大多数是凸函数的优化问题,而非凸函数优化很少涉及.非凸函数优化还是一个新兴的研究方向,发展较为缓慢,且主要应用于非凸优化方面的算法,Martient[1]和Rockafellar[2]在对极大单调算子的变分不等式的研究中引进渐近算法和在凸优化中引进一个渐近正则方法.文献[3-8]给出了凸优化中的非单调算子.文献[9-13]给出了关于非凸函数的概念以及非凸条件下的优化理论.文献[14]研究了f:X→(-∞,∞]和g:Y→(-∞,∞] 是真下半连续函数(未必是凸的)的优化问题,其中X⊂⊂Rn是闭凸集,目的在于找到关于下列函数的临界点f(x)+g(y),(1)使得min(f(x)+g(y)).(2)引进交替方向法去解决非凸的线性约束问题,其中目标函数是真下半连续的非凸函数构造的迭代方法如下:(3)通过收敛性分析,得到了交替方向法生成的序列{(xk,yk)}收敛于目标函数的一个临界点{(x*,y*)}以及{(xk,yk)}具有有限长.但所是构造的迭代方法中的罚参数的控制条件比较严格,且没有给出收敛速率的结果.本文借鉴文献[14]研究非凸函数无约束的优化问题,构造了新的渐进算法,并在适当条件下检验改进的迭代算法的收敛性.1 预备知识设H是一个定义了内积〈·,·〉和范数‖·‖的希尔伯特空间.命题1 (ⅰ) domf:={x∈Rn:f(x)<+∞}表示f的定义域;(ⅱ) 对于一点表示f在x的Fre′chet次微分,它是关于向量x*∈Rn的集合,该集合满足(ⅲ) ∂f(x)表示f在x∈Rn处的极限次微分,定义为∂f(x):={x*∈Rn:∃∀x∈Rn,显然有⊂∂f(x).其中第一个集合是闭的和凸的, 然而第二个集合是闭的. 用critf来表示f的临界点的集合, 即若0∈∂f(x):则有x∈crit.命题2 设f:Rn→(-∞,+∞]是一个真下半连续函数.如果C是Rn的一个闭子集,对x∈Rn,x到C的距离dist(x,C):=inf{‖x-y‖:y∈C}.(4)如果C是空的, 对所有的x∈Rn,有dist(x,C)=∞.若dist(x,C)=0,则x∈C.命题3 如果C是Rn中的一个闭子集,用δC表示其指示函数, 即对所有x∈Rn,有(5)在C上的投影PC(x):=argmin{‖x-z‖:z∈C}来表示.命题4 设η∈(0,+∞].用Φη来表示所有凹函数和连续函数φ:[0,η)→R+,该函数满足下列条件:(ⅰ) φ(0)=0;(ⅱ) φ在(0,η)上是C1和在0是连续的;(ⅲ) ∀x∈(0,η),φ′(x)>0.引理1[15] 设f:Rn→(-∞,+∞]是真下半连续函数,如果x∈Rn是f的局部极小值,则有0∈∂f(x).引理2(KL性质)[16] 设f:Rn→(-∞,+∞]是真下半连续函数.则(ⅰ) 设Dom∂f(x):={x∈Rn:∂f(x)≠φ}.f在具有Kurdyka-Lojasiewicz(KL)性质,如果∃η∈(0,+∞],对于的一个邻域U和一个函数φ∈Φη,使得∀(6)有(7)(ⅱ) 如果一个凹函数f在关于Dom∂f(x)的每一点满足KL性质,则f被称为KL函数.2 迭代算法首先构造与式(1)有关的目标函数:(8)然后,给出该方法的迭代序列:(9)上述方法就是所构造的新的渐近算法.针对不同非凸问题的渐近算法和相关知识可以参考文献[17-22].假设满足的条件如下:(H1) 式(9)的解集是非空的且(H2) f和g是下有界的KL函数;(H3) ∀k≥0,序列{λk},{μk}属于(λ-,λ+).引理3 假定满足(H1)-(H3),设由式(9)生成的序列是{(xk,yk)},且则(Δx,k,Δy,k)∈∂Ψ(xk,yk).故存在一个常数M>0,使得‖(Δx,k,Δy,k)‖≤M(‖xk-xk-1‖+‖yk-yk-1‖).证明由式(9),得(10)设αk∈∂f(xk),可得关于式(10)的优化条件为同理,(11)因为∂xΨ(xk,yk-1)=αk+‖xk-yk-1‖和∂yΨ(xk,yk)=βk-‖xk-yk‖, 有最后因此得到(Δx,k,Δy,k)∈∂Ψ(xk,yk).根据三角不等式,有其中3 收敛性分析定理1 假定满足(H1)~(H3), 由式(9)生成的序列是{(xk,yk)}. 则下面的假设成立: (ⅰ) 序列{Ψ(xk,yk)}是递增的且存在一个常数M1>0, 使得M1(‖xk+1-xk‖2+‖yk+1-yk‖2)≤Ψ(xk,yk)-Ψ(xk+1,yk+1)(12)(ⅱ)如果{(xk,yk)}是有界的, 则此外,和是有限的,则证明(ⅰ)由式(9)知(13)(14)∀k≥1,式(13)和(14)相加可得(15)根据Ψ(x,y)的定义, 有(16)这表明{Ψ(xk,yk)}是非增的. 其中(ⅱ) 对不等式(16)从0到N(N≥0)求和,得(17)因为{(xk,yk)}是有界的,∀ε1>0, 存在N1>0使得∀k>N1 dist((xk,yk),(x*,y*))<ε1.由f的下半连续性知(18)从式(9)知因(xk,yk)→(x*,y*)且{λk}是有界的, 设k→∞,则有(19)结合式(18)和(19), 得到同理故(20)即∀ε2>0,∃N2>0, 使得∀k>N2‖Ψ(xk,yk)-Ψ(x*,y*)‖<ε2.(21)因{Ψ(xk,yk)}是非增序列, 则可得∀k≥1Ψ(x*,y*)<Ψ(xk,yk).设N=max{1,N1,N2},∀k>N,有(xk,yk)∈ {(xk,yk)|dist((xk,yk),(x*,y*))<ε1}∩(Ψ(x*,y*)<Ψ(xk,yk)<Ψ(x*,y*)+ε2).由KL性质知, 有φ′(ψ(xk,yk)-ψ(x*,y*))dist((0,0),∂Ψ(xk,yk))≥1.(22)由引理3得(23)由φ的凹性有φ(Ψ(xk,yk)-Ψ(x*,y*))-φ(Ψ(xk,yk)-Ψ(x*,y*))≥φ,(Ψ(xk,yk)-Ψ(x*,y*))(Ψ(xk,yk)-Ψ(xk+1,yk+1)).(24)∀k>N, 由式(22),式(11)式和φ的凹性可得(25)其中Ωk,k+1=φ(Ψ(xk,yk)-Ψ(x*,y*))-φ(Ψ(xk,yk)-Ψ(x*,y*)).根据(a+b)2≤2a2+2b2和有2(‖xk+1-xk‖+‖yk+1-yk‖)≤M2Ωk,k+1+(‖xk-xk-1‖+‖yk-yk-1‖).(26)其中将式(26)从k=N+1,N+2,…,n相加,化简得到其中ΩN+1,n+1=ΩN+1,q+Ωq,n+1(q是一个正整数).然后由ΩN+1,n+1的定义和φ∈Φη,可得+M2φ(Ψ(xN+1,yN+1)-Ψ(x*,y*)).(27)设n→∞,根据式(27)可得到因此,由于得到是有限的.最终4 收敛结果定理2(收敛定理) 假定满足(H1)~(H3), 由式(9)生成的序列记作{(xk,yk)}. 用{(x*,y*)}表示关于Ψ(xk,yk)的极限点, 则{(xk,yk)}收敛于一个临界点{(x*,y*)}.证明设m>n>N,得到(28)式(28)表明{(xk,yk)}是一个收敛序列,从定理1(ⅱ)知,由引理2和定理1(ⅱ),有(Δx,k,Δy,k)∈∂Ψ(xk,yk),(Δx,k,Δy,k)→(0,0)当k→∞.因此,由∂Ψ的封闭性可知(0,0)∈∂Ψ(x*,y*),这表明(x*,y*)是Ψ的一个临界点.推论1 假定Ψ满足(H1)~(H3)且在处具有Kurdyka-Lojasiewicz性质,且是Ψ一个局部极小点.则∃ε3>0和υ>0,使得(ⅰ)(ⅱ) minΨ<Ψ(x0,y0)<minΨ+υ.这表明以(x0,y0)为起始点的序列(xk,yk)具有有限长性质且收敛于(x*,y*), 即Ψ(x*,y*)=minΨ.证明从定理1知(xk,yk)收敛于(x*,y*), 一个临界点Ψ满足minΨ<Ψ(x0,y0)<minΨ+υ,∀k>0.如果由引理2知这与(0,0)∈∂Ψ(x*,y*)矛盾.定理3(收敛速率定理) 假设Ψ(x,y)满足(H1)~(H3).假定(xk,yk)收敛于(x∞,y∞),Ψ(x,y)在(x∞,y∞)具有Kurdyka-Lojasiewicz性质.φ(s)=cs1-θ,θ∈[0,1),c>0.其中θ是关于(x∞,y∞)的一个Lojasiewicz指数. 则下列假设成立: (ⅰ) 如果θ=0,序列(xk,yk)收敛于有限步长;(ⅱ) 如果使得‖(xk,yk)-(x∞,y∞)‖≤cτk.(ⅲ) 如果证明(ⅰ) 假设θ=0. 如果Ψ(xk,yk)是固定的, 根据定理2,(xk,yk)收敛于有限步长.如果Ψ(xk,yk)不是固定的, 则对于任意k充分大, 由Kurdyka-Lojasiewicz不等式可得cdist((0,0),∂Ψ(xk,yk))≥1.这与(0,0)∈∂Ψ(x k,yk)矛盾.(ⅱ) 假设θ>0.∀k≥0, 设由定理1知它是有限的. 因为Δk≥‖xk-x∞‖+‖yk-y∞‖,估计Δk就足够了. 接下来有Δk≤Δk-1-Δk+M2Ωk,k+1.由Kurdyka-Lojasiewicz不等式可得φ′[Ψ(xk,yk)-Ψ(x*,y*)]dist[(0,0),∂Ψ(xk,yk)]=c(1-θ)[Ψ(xk,yk)-Ψ(x*,y*)]-θdist[(0,0),∂Ψ(xk,yk)]≥1.因此(Ψ(xk,yk)-Ψ(x*,y*))θ≤c(1-θ)dist[(0,0),∂Ψ(xk,yk)].又因为dist((0,0),∂Ψ(xk,yk))≤ ‖Δx,k,Δy,k‖≤M(‖(xk-1-xk)‖+‖(yk-1-xk)‖)≤M(Δk-1-Δk).最后得到然后由Ωk,k+1的定义可得Ωk,k+1≤φ(Ψ(xk,yk)-Ψ(x*,y*))=[c(Ψ(xk,yk)-Ψ(x*,y*))]1-θ.最后给出其中再结合文献[23]可以得到(ⅱ)和(ⅲ).5 结束语研究解决无约束非凸可分离规划的算法, 该目标函数是真下半连续的, 但未必是凸的. 目标函数具有KL性质,证明了算法的收敛性,也获得了收敛速率结果.通过Lojasiewicz指数相关的函数获得了收敛速率的结果.参考文献(References):[1] MARTINET B. Regularisation d′inequations variationnelles par approximations successives(French)[J].Rev Francaise informat.Recherche Operationnelle, 1970,4(4):154-158.[2] ROCKAFELLAR R T.Augmented Lagrangians and applications of the proximal point algorithm in convex programming[J].Mathematics ofOperations Research 1976,1(2):97-116.[3] COMBETTES P,PENNANEN T. Proximal methods for cohypomonotone operators[J].SIAM J Control Optim,2004,43(2):731-742.[4] KAPLAN A,TICHATSCHKE R.Proximal point methods and nonconvex optimization[J].Journal of Globl Optimization,1998,13(4):389-406.[5] MIETTNEN M,MKEL M M,HASLINGER J.On numerical solution of hemivariational inequalities by nonsmooth optimizationmethods[J].Journal of Global Optimization,1995,6(4):401-425.[6] MIFFLIN R,SAGASTIZABAL C.νμ-smoothness and proximal point results for some nonconvex functions[J].Optimization Methods &Software,2004,19(5):463-478.[7] PENNANEN T.Local convergence of the proximal point algorithm and multiplier methods without monotonicity[J].Mathematics of Operations Research,2002,27(1):170-191.[8] Spingarn J E.Submonotone mappings and the proximal point algorithm[J].Numerical Functional Analysis & Optimization,1982,4(2):123-150.[9] ATTOUCH H,SOUBEYRAN A.Inertia and reactivity in decision making as cognitive variational inequalities[J].Journal of ConvexAnalysis,2006,13(13):207-224.[10] CLARKE F H,STERN R J,LEDYAEV Y S,et al.Nonsmooth analysis and control theory[J].Graduate Texts in Mathematics,1998,178(7):137-151. [11] MORDUKHOVICH B S.Maximum principle in the problem of time optimal response with nonsmooth constraints[J].Journal of AppliedMathematics and Mechanics,1976,40(6):960-969.[12] MORDUKHOVICH B.Variational analysis and generalized differentiation[M].Heidelberg:Springer,1998.[13] ROCKAFELLAR R T,WETS R.Variationalanalysis[M].Heidelberg:Springer,1998.[14] WANG X Y,LI S J,KOU X P,et al.A new alternating direction method for linearly constrained nonconvex optimization problems[J].Journal of Global Optimization,2015,62(4):695-709.[15] NOCEDAL J,WRIGHT S J.Numerical optimization[M].NewYork:Springer,2006.[16] BOLTE J,DANIILIDIS A,LEWIS A.The Lojasiewicz inequality for nonsmooth subanalytic functions with applications to subgradient dynamical systems[J].SIAM Journal of Optimization,2006,17(4):1205-1223.[17] REDONT P,SOUBEYRAN A.Proximal alternating minimization and projection methods for nonconvex problems:An approach based on the Kurdyka-jasiewicz inequality[J].Mathematics of Operations Research,2010,35(2):438-457.[18] BOLTE J,SABACH S,TEBOULLE M.Proximal alternating linearized minimization for nonconvex and nonsmooth problems[J].Mathematical Programming,2014,146(1-2):459-494.[19] LEMAIRE B.The proximal algorithm[J].New Methods in Optimization and Their Industrial Uses,International Series of Numerical,1987,87:73-87.[20] ROCKAFELLAR R T.Monotone operators and the proximal point algorithm[J].Siam Journal on Control & Optimization,1976,14(5):877-898.[21] SPINGARN J E.Submonotone mappings and the proximal point algorithm[J].Numerical Functional Analysis & Optimization,1982,4(2):123-150.[22] ATTOUCH H,BOLTE J,SVAITER B F.Convergence of descent methods for semi-algebraic and tame problems:Proximal algorithms,forward-backward splitting, and regularized Gauss-Seidel methods[J].Mathematical Programming, 2013,137(1-2):91-129.[23] ATTOUCH H,BOLTE J.On the convergence of the proximal algorithm for nonsmooth functions involving analytic features[J].Mathematical Programming,2009,116(1-2):5-16.。
中国科学英文版模板

中国科学英文版模板1.Identification of Wiener systems with nonlinearity being piece wise-linear function HUANG YiQing,CHEN HanFu,FANG HaiTao2.A novel algorithm for explicit optimal multi-degree reduction of triangular surfaces HU QianQian,WANG GuoJin3.New approach to the automatic segmentation of coronary arte ry in X-ray angiograms ZHOU ShouJun,YANG Jun,CHEN WuFan,WANG YongTian4.Novel Ω-protocols for NP DENG Yi,LIN DongDai5.Non-coherent space-time code based on full diversity space-ti me block coding GUO YongLiang,ZHU ShiHua6.Recursive algorithm and accurate computation of dyadic Green 's functions for stratified uniaxial anisotropic media WEI BaoJun,ZH ANG GengJi,LIU QingHuo7.A blind separation method of overlapped multi-components b ased on time varying AR model CAI QuanWei,WEI Ping,XIAO Xian Ci8.Joint multiple parameters estimation for coherent chirp signals using vector sensor array WEN Zhong,LI LiPing,CHEN TianQi,ZH ANG XiXiang9.Vision implants: An electrical device will bring light to the blind NIU JinHai,LIU YiFei,REN QiuShi,ZHOU Yang,ZHOU Ye,NIU S huaibining search space partition and search Space partition and ab straction for LTL model checking PU Fei,ZHANG WenHui2.Dynamic replication of Web contents Amjad Mahmood3.On global controllability of affine nonlinear systems with a tria ngular-like structure SUN YiMin,MEI ShengWei,LU Qiang4.A fuzzy model of predicting RNA secondary structure SONG D anDan,DENG ZhiDong5.Randomization of classical inference patterns and its applicatio n WANG GuoJun,HUI XiaoJing6.Pulse shaping method to compensate for antenna distortion in ultra-wideband communications WU XuanLi,SHA XueJun,ZHANG NaiTong7.Study on modulation techniques free of orthogonality restricti on CAO QiSheng,LIANG DeQun8.Joint-state differential detection algorithm and its application in UWB wireless communication systems ZHANG Peng,BI GuangGuo,CAO XiuYing9.Accurate and robust estimation of phase error and its uncertai nty of 50 GHz bandwidth sampling circuit ZHANG Zhe,LIN MaoLiu,XU QingHua,TAN JiuBin10.Solving SAT problem by heuristic polarity decision-making al gorithm JING MingE,ZHOU Dian,TANG PuShan,ZHOU XiaoFang,ZHANG Hua1.A novel formal approach to program slicing ZHANG YingZhou2.On Hamiltonian realization of time-varying nonlinear systems WANG YuZhen,Ge S. S.,CHENG DaiZhan3.Primary exploration of nonlinear information fusion control the ory WANG ZhiSheng,WANG DaoBo,ZHEN ZiYang4.Center-configur ation selection technique for the reconfigurable modular robot LIU J inGuo,WANG YueChao,LI Bin,MA ShuGen,TAN DaLong5.Stabilization of switched linear systems with bounded disturba nces and unobservable switchings LIU Feng6.Solution to the Generalized Champagne Problem on simultane ous stabilization of linear systems GUAN Qiang,WANG Long,XIA B iCan,YANG Lu,YU WenSheng,ZENG ZhenBing7.Supporting service differentiation with enhancements of the IE EE 802.11 MAC protocol: Models and analysis LI Bo,LI JianDong,R oberto Battiti8.Differential space-time block-diagonal codes LUO ZhenDong,L IU YuanAn,GAO JinChun9.Cross-layer optimization in ultra wideband networks WU Qi,BI JingPing,GUO ZiHua,XIONG YongQiang,ZHANG Qian,LI ZhongC heng10.Searching-and-averaging method of underdetermined blind s peech signal separation in time domain XIAO Ming,XIE ShengLi,F U YuLi11.New theoretical framework for OFDM/CDMA systems with pe ak-limited nonlinearities WANG Jian,ZHANG Lin,SHAN XiuMing,R EN Yong1.Fractional Fourier domain analysis of decimation and interpolat ion MENG XiangYi,TAO Ran,WANG Yue2.A reduced state SISO iterative decoding algorithm for serially concatenated continuous phase modulation SUN JinHua,LI JianDong,JIN LiJun3.On the linear span of the p-ary cascaded GMW sequences TA NG XiaoHu4.De-interlacing technique based on total variation with spatial-t emporal smoothness constraint YIN XueMin,YUAN JianHua,LU Xia oPeng,ZOU MouYan5.Constrained total least squares algorithm for passive location based on bearing-only measurements WANG Ding,ZHANG Li,WU Ying6.Phase noise analysis of oscillators with Sylvester representation for periodic time-varying modulus matrix by regular perturbations FAN JianXing,YANG HuaZhong,WANG Hui,YAN XiaoLang,HOU ChaoHuan7.New optimal algorithm of data association for multi-passive-se nsor location system ZHOU Li,HE You,ZHANG WeiHua8.Application research on the chaos synchronization self-mainten ance characteristic to secret communication WU DanHui,ZHAO Che nFei,ZHANG YuJie9.The changes on synchronizing ability of coupled networks fro m ring networks to chain networks HAN XiuPing,LU JunAn10.A new approach to consensus problems in discrete-time mult iagent systems with time-delays WANG Long,XIAO Feng11.Unified stabilizing controller synthesis approach for discrete-ti me intelligent systems with time delays by dynamic output feedbac k LIU MeiQin1.Survey of information security SHEN ChangXiang,ZHANG Hua ngGuo,FENG DengGuo,CAO ZhenFu,HUANG JiWu2.Analysis of affinely equivalent Boolean functions MENG QingSh u,ZHANG HuanGuo,YANG Min,WANG ZhangYi3.Boolean functions of an odd number of variables with maximu m algebraic immunity LI Na,QI WenFeng4.Pirate decoder for the broadcast encryption schemes from Cry pto 2005 WENG Jian,LIU ShengLi,CHEN KeFei5.Symmetric-key cryptosystem with DNA technology LU MingXin,LAI XueJia,XIAO GuoZhen,QIN Lei6.A chaos-based image encryption algorithm using alternate stru cture ZHANG YiWei,WANG YuMin,SHEN XuBang7.Impossible differential cryptanalysis of advanced encryption sta ndard CHEN Jie,HU YuPu,ZHANG YueYu8.Classification and counting on multi-continued fractions and its application to multi-sequences DAI ZongDuo,FENG XiuTao9.A trinomial type of σ-LFSR oriented toward software implemen tation ZENG Guang,HE KaiCheng,HAN WenBao10.Identity-based signature scheme based on quadratic residues CHAI ZhenChuan,CAO ZhenFu,DONG XiaoLei11.Modular approach to the design and analysis of password-ba sed security protocols FENG DengGuo,CHEN WeiDong12.Design of secure operating systems with high security levels QING SiHan,SHEN ChangXiang13.A formal model for access control with supporting spatial co ntext ZHANG Hong,HE YePing,SHI ZhiGuo14.Universally composable anonymous Hash certification model ZHANG Fan,MA JianFeng,SangJae MOON15.Trusted dynamic level scheduling based on Bayes trust model WANG Wei,ZENG GuoSun16.Log-scaling magnitude modulated watermarking scheme LING HeFei,YUAN WuGang,ZOU FuHao,LU ZhengDing17.A digital authentication watermarking scheme for JPEG image s with superior localization and security YU Miao,HE HongJie,ZHA NG JiaShu18.Blind reconnaissance of the pseudo-random sequence in DS/ SS signal with negative SNR HUANG XianGao,HUANG Wei,WANG Chao,L(U) ZeJun,HU YanHua1.Analysis of security protocols based on challenge-response LU O JunZhou,YANG Ming2.Notes on automata theory based on quantum logic QIU Dao Wen3.Optimality analysis of one-step OOSM filtering algorithms in t arget tracking ZHOU WenHui,LI Lin,CHEN GuoHai,YU AnXi4.A general approach to attribute reduction in rough set theory ZHANG WenXiuiu,QIU GuoFang,WU WeiZhi5.Multiscale stochastic hierarchical image segmentation by spectr al clustering LI XiaoBin,TIAN Zheng6.Energy-based adaptive orthogonal FRIT and its application in i mage denoising LIU YunXia,PENG YuHua,QU HuaiJing,YiN Yong7.Remote sensing image fusion based on Bayesian linear estimat ion GE ZhiRong,WANG Bin,ZHANG LiMing8.Fiber soliton-form 3R regenerator and its performance analysis ZHU Bo,YANG XiangLin9.Study on relationships of electromagnetic band structures and left/right handed structures GAO Chu,CHEN ZhiNing,WANG YunY i,YANG Ning10.Study on joint Bayesian model selection and parameter estim ation method of GTD model SHI ZhiGuang,ZHOU JianXiong,ZHAO HongZhong,FU Qiang。
求解RCPSP问题的迭代局部搜索算法研究

求解RCPSP问题的迭代局部搜索算法研究赵轩【摘要】Iterated Local Search algorithm is a simple and efficient metaheuristic. Presents a new iterated local search algorithm for resource-con-strained project scheduling problem (RCPSP) . Through the iterated exchange of current solution to achieve local search process, and the way of further perturbation of multiple tasks can also prevent local optimization. During the iterative process further reduces the solution space by prioritizing critical chain tasks for local search. Uses the double justification techniques to improve the quality of the solution. Uses the standard library to determine the parameters and verify the quality of the algorithm.%迭代局部搜索(Iterated Local Search)算法是一个简单、高效的元启发式算法。
提出一种新的求解资源受限项目调度问题(RCPSP)的迭代局部搜索算法。
通过对当前解进行迭代交换实现局部搜索过程,再通过扰动多个任务的方式进行有效的扰动,防止陷入局部最优。
迭代过程中通过优先对关键链的任务进行局部搜索进一步缩小解空间,通过双对齐技术提高解的质量。
非晶态物质凝固过程分子动力学仿真

第38卷第2期计算机仿真2021年2月文章编号:1006-9348(2021)02-0192-05非晶态物质凝固过程分子动力学仿真李艽(四川大学锦城学院,四川成都611731)摘要:针对非晶态物质凝固过程中分子捕捉的准确度较低的问题,从多项分子力场人手,提出非晶态物质凝固时分子动力学仿真方法。
根据非晶态物质分子凝固过程中的排斥和吸引作用,建立分子势函数,组成分子动力学力场。
通过力场作用的约束能力,结合分子动力学相关数据,进行分子约束动力捕捉,并引人分子动力学约束性算法,解决捕捉后无法描述正态分子的问题。
将约束后的分子公式汇聚,引人量子力学计算公式,根据分子体系波函和本征函数进行数据计算,通过计算结果 结合量子体系实现对非晶态物质分子的动力模拟。
实验数据表明,所设计方法下模拟过程分子的集散度得到了大幅度提高,能够完成提高分子捕捉准确度的目标,具有有效性。
关键词:非晶态物质;色散作用;仿真;量子力学;晶体分子中图分类号:F272 文献标识码:BMolecular Dynamics Simulation of SolidiflcationProcess Of Amorphous MaterialLI Peng(Jin c h en g C o lleg, S ich u an U n iv ersity, S ichuan C hengdu 611731, C h in a)A B S T R A C T: T h is article p u ts forw ard a m ethod of m olecular dynam ics sim ulation for th e solidification of am orphousm aterials. A ccording to the rep u lsio n an d attra c tio n of am orphous m olecules d uring so lid ificatio n, the m olecular poten tial function was estab lish ed to form the m olecular dynam ics force field. B ased on th e constraint ability of force field an d th e related d ata of m o lecu lar d y n a m ic s, the m o lecu lar co n strain t dynam ic cap tu re was carried out. M eanw h ile, th e co n strain t algorithm of m o lecu lar dynam ics w as introduced to solve th e problem that norm al m olecules could not be d escrib ed after ca p tu re. On th is b a s is, th e co n strain ed m olecular form ulas w ere aggregated an d form ulas of q u an tu m m ech an ics w ere in tro d u ced. T he d a ta were c alcu lated by the wave function an d eigen function of m olecular system. T h u s, th e dynam ic sim u latio n for am orphous su b stan ce m olecules w as realized by com bining the calcu lation re su lts w ith the q u an tu m system. S im ulation results show that the collecting an d d istrib u tin g degree of m olecules in the sim ulation pro cess have b een im proved g re atly, w hich can ach iev e the goal of im proving the accuracy of m olecu la r cap tu re. T h u s, this m ethod is effective.K E Y W O R D S:Am oq3hous m a tte r;C hrom atic d isp e rs io n;S im u latio n;Q uantum m e c h a n ic s;Crystal m oleculesi引言非晶态物质分子本征排列方式一直是凝聚态物理学和 材料学特征分析中最有研究价值的领域之一m。
一种新的线性约束恒模算法

一种新的线性约束恒模算法李晓陆;林文长;江瑾【摘要】The LSCCMA can solve the problem of interference capture, however the algorithm can not form obvious null in the DOA of interference signal. A new algorithm which regards the interference signal steering vector as its constrained condition (LICCMA) is applied in the situation with strong interference signal. Different from the LSCCMA, the null formed in DOA of interference signal is added as a necessary constrained condition to the original CM A. Hence, LICCMA is optimized to the situation of avoiding the interference signal while LSCCMA is optimized to the situation of aiming the expected signal. LICCMA is more suitable for the situation when the interference signal is stronger than the expected signal, which can form obvious null in the DOA of interference signal and improve the signal-to-interference ratio of the expected signal.%针对LSCCMA在干扰信号来波方向上不能形成明显零限的局限性,以及需要避开强干扰来波信号的应用场合,提出基于干扰信号导向矢量算法(LICCMA),该算法在常规CMA的基本条件上增加了干扰零陷的约束条件,以干扰信号零陷为目标进行算法优化设计.与LSCCMA相比,LICCMA在干扰信号强于期望信号的环境,在干扰信号来波方向上形成明显的零陷,提高了信号的信干比.【期刊名称】《桂林电子科技大学学报》【年(卷),期】2012(032)006【总页数】4页(P456-459)【关键词】恒模算法;线性约束;干扰零陷;盲波束形成【作者】李晓陆;林文长;江瑾【作者单位】广州海格通信集团股份有限公司,广州 510663【正文语种】中文【中图分类】TN911.23恒模算法(CMA)是一种盲波束形成算法,它无需训练信号,收敛速度相对较快,可用于PSK、FM 等恒模信号,也可用于某些非恒模信号(如QAM 信号)[1-2]。
算法设计技巧与分析英文版课后练习题含答案

Algorithm Design Techniques and Analysis: English VersionExercise with AnswersIntroductionAlgorithms are an essential aspect of computer science. As such, students who are part of this field must master the art of algorithm design and analysis. Algorithm design refers to the process of creating algorithms that solve computational problems. Algorithm analysis, on the other hand, focuses on evaluating the resources required to execute those algorithms. This includes computational time and memory consumption.This document provides students with helpful algorithm design and analysis exercises. The exercises are in the formof questions with step-by-step solutions. The document is suitable for students who have completed the English versionof the Algorithm Design Techniques and Analysis textbook. The exercises cover various algorithm design techniques, such as divide-and-conquer, dynamic programming, and greedy approaches.InstructionEach exercise comes with a question and its solution. Read the question carefully and try to find a solution withoutlooking at the answer first. If you get stuck, look at the solution. Lastly, try the exercise agn without referring to the answer.Exercise 1: Divide and ConquerQuestion:Given an array of integers, find the maximum possible sum of a contiguous subarray.Example:Input: [-2, -3, 4, -1, -2, 1, 5, -3]Output: 7 (the contiguous subarray [4, -1, -2, 1, 5]) Solution:def max_subarray_sum(arr):if len(arr) ==1:return arr[0]mid =len(arr) //2left_arr = arr[:mid]right_arr = arr[mid:]max_left_sum = max_subarray_sum(left_arr)max_right_sum = max_subarray_sum(right_arr)max_left_border_sum =0left_border_sum =0for i in range(mid-1, -1, -1):left_border_sum += arr[i]max_left_border_sum =max(max_left_border_sum, left_b order_sum)max_right_border_sum =0right_border_sum =0for i in range(mid, len(arr)):right_border_sum += arr[i]max_right_border_sum =max(max_right_border_sum, righ t_border_sum)return max(max_left_sum, max_right_sum, max_left_border_s um+max_right_border_sum)Exercise 2: Dynamic ProgrammingQuestion:Given a list of lengths of steel rods and a corresponding list of prices, determine the maximum revenue you can get by cutting these rods into smaller pieces and selling them. Assume the cost of each cut is 0.Lengths: [1, 2, 3, 4, 5, 6, 7, 8]Prices: [1, 5, 8, 9, 10, 17, 17, 20]If the rod length is 4, the maximum revenue is 10.Solution:def max_revenue(lengths, prices, n):if n ==0:return0max_val =float('-inf')for i in range(n):max_val =max(max_val, prices[i] + max_revenue(length s, prices, n-i-1))return max_valExercise 3: Greedy AlgorithmQuestion:Given a set of jobs with start times and end times, find the maximum number of non-overlapping jobs that can be scheduled.Start times: [1, 3, 0, 5, 8, 5]End times: [2, 4, 6, 7, 9, 9]Output: 4Solution:def maximum_jobs(start_times, end_times):job_list =sorted(zip(end_times, start_times))count =0end_time =float('-inf')for e, s in job_list:if s >= end_time:count +=1end_time = ereturn countConclusionThe exercises presented in this document provide a practical way to master essential algorithm design and analysis techniques. Solving the problems without looking at the answers will expose students to the type of problems they might encounter in real life. The document’s solutionsprovide step-by-step instructions to ensure that students can approach the problems with confidence.。
工程管理外文文献

工程管理外文文献编者按:很多朋友寻找工程管理类的外文文献,以下是本人收集的一部分外文文献,希望能对朋友们有所帮助。
工程管理外文文献:[1](美)杰克.吉多詹姆斯P.克莱门斯著张金成等译成功的项目管理Successful Project Mamagement . 北京:机械工业出版社,2003:p171-186.[2]Demeulemeester, E. L. and Herroelen.A Branch and Bound Procedure for theMultiple Resource-Constrained Projects Scheduling Problem. ManagementScience, 1992, 38: 1803~1881.[3]Joel P.Stinson, Edward W.Davis and Bsheer M. Khumawala. MultipleResource-Constrained Scheduling Using Branch and Bound.ALLE Transaction,1 987, 10:252~259.[4]Demeulemeester, E.L. and Willy Herroelen.New Benchmark Results for theResource-Constrained Project Scheduling Problem.Management Science,1997,43:1485~1492.[5]Fayez F.Boctor.Some efficient multi heuristic procedures forResource-Constrained Project Scheduling. European Journal of OperationalResearch, 1990, 49:3~13.[6]Rainer Kolisch.Serial and Parallel Resource-Constrained Project Schedulingmethods revisited: Theroy and computation.European Journal of OperationalResearch, 1996,90:320~333.[7]K.Bouleimen, H.Lecocq.A new efficient simulated annealing algorithm for theresource-constrained scheduling problem.Technical Report, service deRobotique et Automatisation, University de Liege, 1998.[8]S.Hartmann.A Competitive Genetic Algorithm for Resource-Constrained ProjectScheduling.Naval Research Logistics, 1998, 45:733~750.[9]S.Hartmann and R.Kolisch,Experimental evaluation of state-of-the-art heuristicsfor the resource-constrained project scheduling problem, European Journal of Operational Research, 2000,127:394~408.[10]Fendley, L.G.Towards the Development of a Complete Multi-project SchedulingSystem. Journal of Industrial Engineering, 1968, 12:505~515.[11]Kurtulus.I, E.W.Davis. Multi-Project Scheduling: Categorization of HeuristicRules Performance.Management Science, 1982, 2:25~31.[12]Shigeru Tsubakitani, Richard F.Deckro. A heuristic for multi-project schedulingwith limited resources in the housing industry.European Journal of Operational Research, 1990, 49:80~91.[13]Soo-Young Kim, Robert C. Leachman.Multi-Project Scheduling with ExplicitLateness Costs. IIE Transactions, 1993, 25:34~43.[14]Paul C .Dinsmore,Winning in Business With Enterprise Project Management,PMI,1999.[15]Leach L P. Critical chain project management [M]. London: Artech House Inc,2000, 236~257[16]鲍伯,弗斯特.IS09001: 2000质量管理体系.中国标准出版社.2001:P.22-P.283.[17](美)杰克.吉多詹姆斯P.克莱门斯著张金成等译成功的项目管理Successful Project Mamagement . 北京:机械工业出版社,2003:p171-186.[18]项目管理知识体系(PMBOK, Project Management Body ofKnowledge) 是美国项目管理学会(PMI, Project ManagementInstitute)开发的一个关于项目管理的标准。
【5A文】关于序列二次规划(SQP)算法求解非线性规划问题研究

关于序列二次规划(SQP)算法求解非线性规划问题研究兰州大学硕士学位论文关于序列二次规划(SQP)算法求解非线性规划问题的研究姓名:石国春申请学位级别:硕士专业:数学、运筹学与控制论指导教师:王海明20090602兰州大学2009届硕士学位论文摘要非线性约束优化问题是最一般形式的非线性规划NLP问题,近年来,人们通过对它的研究,提出了解决此类问题的许多方法,如罚函数法,可行方向法,Quadratic及序列二次规划SequentialProgramming简写为SOP方法。
本文主要研究用序列二次规划SOP算法求解不等式约束的非线性规划问题。
SOP算法求解非线性约束优化问题主要通过求解一系列二次规划子问题来实现。
本文基于对大规模约束优化问题的讨论,研究了积极约束集上的SOP 算法。
我们在约束优化问题的s一积极约束集上构造一个二次规划子问题,通过对该二次规划子问题求解,获得一个搜索方向。
利用一般的价值罚函数进行线搜索,得到改进的迭代点。
本文证明了这个算法在一定的条件下是全局收敛的。
关键字:非线性规划,序列二次规划,积极约束集Hl兰州人学2009届硕二t学位论文AbstractNonlinearconstrainedarethemostinoptimizationproblemsgenericsubjectsmathematicalnewmethodsareachievedtosolveprogramming.Recently,Manyasdirectionit,suchfunction,feasiblemethod,sequentialquadraticpenaltyprogramming??forconstrainedInthisthemethodspaper,westudysolvinginequalityabyprogrammingalgorithm.optimizationproblemssequentialquadraticmethodaofSQPgeneratesquadraticprogrammingQPsequencemotivationforthisworkisfromtheofsubproblems.OuroriginatedapplicationsinanactivesetSQPandSQPsolvinglarge-scaleproblems.wepresentstudyforconstrainedestablishontheQPalgorithminequalityoptimization.wesubproblemsactivesetofthesearchdirectionisachievedQPoriginalproblem.AbysolvingandExactfunctionsaslinesearchfunctionsubproblems.wepresentgeneralpenaltyunderobtainabetteriterate.theofourisestablishedglobalconvergencealgorithmsuitableconditions.Keywords:nonlinearprogramming,sequentialquadraticprogrammingalgorithm,activesetlv兰州大学2009届硕士学位论文原创性声明本人郑重声明:本人所呈交的学位论文,是在导师的指导下独立进行研究所取得的成果。
DB33∕T 1136-2017 建筑地基基础设计规范

5
地基计算 ....................................................................................................................... 14 5.1 承载力计算......................................................................................................... 14 5.2 变形计算 ............................................................................................................ 17 5.3 稳定性计算......................................................................................................... 21
主要起草人: 施祖元 刘兴旺 潘秋元 陈云敏 王立忠 李冰河 (以下按姓氏拼音排列) 蔡袁强 陈青佳 陈仁朋 陈威文 陈 舟 樊良本 胡凌华 胡敏云 蒋建良 李建宏 王华俊 刘世明 楼元仓 陆伟国 倪士坎 单玉川 申屠团兵 陶 琨 叶 军 徐和财 许国平 杨 桦 杨学林 袁 静 主要审查人: 益德清 龚晓南 顾国荣 钱力航 黄茂松 朱炳寅 朱兆晴 赵竹占 姜天鹤 赵宇宏 童建国浙江大学 参编单位: (排名不分先后) 浙江工业大学 温州大学 华东勘测设计研究院有限公司 浙江大学建筑设计研究院有限公司 杭州市建筑设计研究院有限公司 浙江省建筑科学设计研究院 汉嘉设计集团股份有限公司 杭州市勘测设计研究院 宁波市建筑设计研究院有限公司 温州市建筑设计研究院 温州市勘察测绘院 中国联合工程公司 浙江省电力设计院 浙江省省直建筑设计院 浙江省水利水电勘测设计院 浙江省工程勘察院 大象建筑设计有限公司 浙江东南建筑设计有限公司 湖州市城市规划设计研究院 浙江省工业设计研究院 浙江工业大学工程设计集团有限公司 中国美术学院风景建筑设计研究院 华汇工程设计集团股份有限公司
高三英语计算机编程单选题50题

高三英语计算机编程单选题50题1. In a software development project, when you want to create a new variable to store an integer value, which of the following is the correct keyword in many programming languages?A. varB. intC. strD. bool答案:B。
解析:在许多编程语言中,“int”是用于声明整数类型变量的关键字。
选项A“var”通常是一种更通用的变量声明方式,但不特定表示整数类型。
选项C“str”是用于声明字符串类型的变量,用于存储文本数据。
选项D“bool”是用于声明布尔类型的变量,用于表示真或假的值。
2. When debugging a program, you find an error that occurs when the program tries to access an element in an array that doesn't exist. What is this type of error called?A. Syntax errorB. Runtime errorC. Compile - time errorD. Logical error答案:B。
解析:运行时错误是指程序在运行期间发生的错误,如访问不存在的数组元素这种情况。
选项A语法错误是指代码违反了编程语言的语法规则,在编译阶段就会被发现。
选项C编译时错误也是在编译过程中发现的错误,通常与语法或编译环境有关。
选项D 逻辑错误是指程序的逻辑存在问题,导致结果不符合预期,但不是这种访问不存在元素的错误类型。
3. In object - oriented programming, what is a class?A. A single instance of an objectB. A blueprint or template for creating objectsC. A method that operates on objectsD. A variable that stores object references答案:B。
基于布尔异或掩码转算术加法掩码的安全设计

基于布尔异或掩码转算术加法掩码的安全设计饶金涛;李军;何卫国【摘要】针对布尔异或掩码转算术加法掩码算法需要额外引入随机数的缺点,提出了一种基于数字电路设计的高效转换方法.该方法站在高效电路设计的角度,将布尔异或掩码转换成算术加法掩码,同时保证在数据转换过程中泄露的能量消耗和敏感中间值无依赖关系,有效保护了敏感信息.该电路逻辑结构简单,并在FPGA开发板上进行了实测攻击分析.实验结果表明,该方法具有有效性,拓展了安全防护电路的设计思路.%Aiming at the shortcoming that the additional random numbers need to be added when converting from Boolean XOR masking to arithmetic addition masking, a new efficient conversion method based on digital circuit design is proposed. From the perspective of efficient circuit design, the method converts Boolean XOR masking to arithmetic add masking, and ensures that the energy consumption and the sensitive intermediate value have no dependencies in data transformation process, thus effectively protecting sensitive information. The logic structure of the circuit is simple, and the analysis of measured attack is done on the FPGA development board. The experimental results show that this method is effective and could expand the design idea of the safety protection circuit.【期刊名称】《通信技术》【年(卷),期】2018(051)003【总页数】4页(P696-699)【关键词】能量攻击;电磁攻击;布尔异或掩码;算术加法掩码【作者】饶金涛;李军;何卫国【作者单位】成都三零嘉微电子有限公司,四川成都 610041;成都三零嘉微电子有限公司,四川成都 610041;成都三零嘉微电子有限公司,四川成都 610041【正文语种】中文【中图分类】TP3090 引言能量攻击分析自1996年被提出后[1],各种能量攻击方法被提出,包括简单能量攻击分析、差分能量攻击分析[2]、相关性能量攻击分析[3]、碰撞攻击[4]、互信息能量攻击分析和模板攻击分析[5]等。
入侵杂草算法的一种改进实现

入侵杂草算法的一种改进实现陈林;潘大志【摘要】针对入侵杂草算法寻优精度不高、收敛速度慢和易早熟等缺陷,提出一种改进的入侵杂草算法.新算法将每个杂草的所有种子作为一个小生境,先对每个小生境进行学习算子操作,再引用复合形法引导种群进行协同寻优,最后对种群进行有向的扰动操作,从而得出最优解.实验测试表明,新算法在寻优效率、解的稳定性和鲁棒性等方面都较好.%Aiming at the defects of low precision,slow convergence rate and easy early maturity of the invasive weed algorithm,an improved algorithm is proposed.The new algorithm will first of all take each weed as a niche,and learning operator of each niche is presented.Then,the complex method is introduced to guide the population of collaborative optimization.Finally,the disturbance to the operation of the population is conducted to obtain the optimal solution.Experimental results show that the new algorithm is better in the aspects of optimizationefficiency,stability and robustness of the solution.【期刊名称】《西华师范大学学报(自然科学版)》【年(卷),期】2017(038)003【总页数】6页(P304-309)【关键词】小生境;学习算子;复合形法;扰动【作者】陈林;潘大志【作者单位】西华师范大学数学与信息学院,四川南充637009;西华师范大学数学与信息学院,四川南充637009【正文语种】中文【中图分类】TP3992006年由Mehrabian 等人[1] 提出了一种新的智能算法——入侵杂草算法(IWO)。
概率优化设计理论

学位论文版权使用授权书本学位论文作者完全了解学校有关保留、使用学位论文的规定,同意学校保留并向国家有关部门或机构送交论文的复印件和电子版,允许论文被查阅和借阅。
本人授权江苏大学可以将本学位论文的全部内容编入有关数据库进行检索,可以采用影印、缩印或扫描等复制手段保存和汇编本学位论文。
保密本学位论文属于 ,在 年我解密后适用本授权书。
学位论文作者签名: 指导教师签名:年 月 日 年 月日独创性申明本人郑重声明:所呈交的学位论文,是本人在导师的指导下,独立进行研究工作所取得的成果。
除文中已经注明引用的内容以外,本论文不包含任何其他个人或集体已经发表或撰写过的作品成果。
对本文的研究做出重要贡献的个人和集体,均已在文中以明确方式标明。
本人完全意识到本声明的法律结果由本人承担。
学位论文作者签名:年 月 日江苏大学博士学位论文概率优化设计理论及其在汽车零部件设计中的应用研究生:高翔指导教师:蔡兰教授专业名称:车辆工程研究方向:汽车及其零部件设计理论与方法江苏大学二〇〇五年三月The Jiangsu UniversitySchool of Automotive and Traffic EngineeringThe Theory of Probabilistic-Optimal Design and Applications in Automobile Components DesignA Thesis in Vehicle EngineeringBy Gao XiangAdvised byProfessor Cai Lan© 2005 Gao XiangSubmitted in Partial FulfitmentOf the Requirementsfor the Degree of Doctor of PhilosophyMarch 2005摘要本学位论文结合原机械工业部“膜片弹簧离合器概率优化设计方法研究”、“汽车关键零部件(离合器)可靠性优化设计技术”项目的研究,以汽车膜片弹簧离合器为对象,研究复杂随机变量统计模型建立、概率设计理论及应用、概率优化设计模型及应用、机械零件性能向量离散程度的度量与分析等。
Optimization Algorithms

Optimization AlgorithmsOptimization algorithms are a crucial tool in various fields, including engineering, economics, and computer science. These algorithms are designed tofind the best solution to a problem from a set of possible solutions, often with the goal of maximizing or minimizing a particular objective function. However, the effectiveness of optimization algorithms can vary depending on the specific problem at hand, and there are numerous factors to consider when selecting the most appropriate algorithm for a given situation. One of the key considerations when choosing an optimization algorithm is the nature of the problem itself. Some problems may be relatively simple and well-behaved, making them suitable for straightforward optimization techniques such as gradient descent or genetic algorithms. However, other problems may be highly complex, non-linear, or non-convex, requiring more advanced algorithms such as simulated annealing or particle swarm optimization. Understanding the characteristics of the problem is essential for selecting the most effective algorithm. Another important factor to consider is the computational resources available for running the optimization algorithm. Some algorithms may be highly computationally intensive, requiring significant time and memory resources to find a solution. In contrast, other algorithms may be more lightweight and suitable for use in resource-constrained environments. The availability of computational resources can significantly impact the choice of optimization algorithm. In addition to the nature of the problem and computational resources, the specific requirements and constraints of the problem must also be taken into account when selecting an optimization algorithm. For example, some problems may have strict constraints on the feasible solution space, requiring the use of constrained optimization algorithms. Likewise, certain problems may have multiple objectives that need to be simultaneously optimized, necessitating the use of multi-objective optimization algorithms. Understanding the specific requirements and constraints of the problem is crucial for choosing the most appropriate algorithm. Furthermore, the performance and robustness of optimization algorithms can vary depending on the specific problem and input parameters. Some algorithms may perform well on certain types of problems but poorly on others, while some algorithms may be sensitive to the choice ofparameters and initialization. It is essential to carefully evaluate the performance and robustness of different algorithms on a given problem to ensurethat the selected algorithm can reliably find high-quality solutions. Moreover, the interpretability and ease of implementation of optimization algorithms arealso important considerations. Some algorithms may produce highly complex and opaque solutions, making it challenging to understand the reasoning behind the optimized solution. In contrast, other algorithms may produce more interpretable solutions, which can be valuable in certain applications where explainability is critical. Additionally, the ease of implementation and integration of thealgorithm into existing systems and workflows should also be taken into account. Finally, the ethical and societal implications of using optimization algorithms should not be overlooked. In some cases, the use of optimization algorithms may have unintended consequences or ethical implications, such as reinforcing biasesor creating unfair outcomes. It is important to consider the potential ethical and societal impacts of using optimization algorithms and to take proactive measuresto mitigate any negative effects. In conclusion, the selection of an optimization algorithm is a complex and multifaceted decision that requires careful consideration of the problem at hand, computational resources, specific requirements and constraints, algorithm performance and robustness,interpretability and ease of implementation, and ethical and societal implications. By taking into account these various factors, practitioners can make informed decisions about which optimization algorithm is best suited for a given problem, ultimately leading to more effective and responsible use of optimization techniques.。
内点罚函数法的英文缩写

内点罚函数法的英文缩写Interior Point Penalty Function Method (IPPFM)The Interior Point Penalty Function Method (IPPFM) is a widely used numerical optimization algorithm for solving constrained optimization problems. It is based on the idea of penalizing constraint violations and transforming the original constrained problem into an unconstrained one that can be solved using an interior point method.The acronym for the Interior Point Penalty Function Method is IPPFM.The penalty function allows the optimization algorithm to search for a solution that simultaneously minimizes theobjective function and satisfies the constraints. The idea behind the penalty function is that as the algorithm progresses, the penalty for constraint violations increases, encouraging the algorithm to find a feasible solution.The IPPFM uses an interior point method to solve the penalized problem. The interior point method is an optimization algorithm that works by iteratively solving a sequence of unconstrained subproblems with a barrier function. The barrier function reduces the feasibility violation and brings the algorithm closer to a feasible solution at each iteration.The main advantage of the IPPFM over other methods is that it can handle both linear and nonlinear constraints, as well as inequality and equality constraints. It is also effective for problems with a large number of constraints and variables.The IPPFM has found applications in various fields, including engineering design, economics, logistics, and operations research. It has been successfully used to optimize the design of mechanical systems, allocate resources in supply chain management, and solve scheduling problems.In conclusion, the Interior Point Penalty Function Method (IPPFM) is an effective optimization algorithm for solving constrained optimization problems. It uses a penalty function to transform the problem into an unconstrained one and an interior point method to solve the penalized problem. The IPPFM is widely used in various industries and has proven to be efficient and applicable to a wide range of problems.。
