ccna2-6真题
思科认证CCNA认证试题和答案中文版

思科认证CCNA认证试题和答案中文版思科认证CCNA认证试题和答案中文版想要获得思科认证,首先要参加由思科推荐并授权的培训中心(Cisco Training Partner,简称CTP)所开设的培训课程。
完成学业后再到由全球考试机构Sylvan Prometric授权的.考试中心参加由思科指定的科目的认证考试。
通过指定的系列科目考试后,学员就可以获得相应分支系列等级的资格认证。
下面是店铺为大家搜集的相关试题,供大家参考练习。
16、路由器A串口0配置如下interface serial0link-protocol pppppp pap local-user huawei password simple quidwayip address 2.2.2.1 255.0.0.0路由器B串口及全局配置如下local-user huawei service-type ppp password simple quidway!interface serial0link-protocol pppppp authentication-mode papip address 2.2.2.2 255.0.0.0当两台路由器串口0相连时,两台路由器是否可以连接到对端()(A) 能(B) 不能答案:A17、关于千兆以太网,以下说法正确的是( )(A) IEEE802.3ab定义了千兆以太网(B) 在同一冲突域中,千兆以太网不允许中继器的互连(C) IEEE802.3z专门定义了千兆以太网在双绞线上的传输标准(D) 千兆以太网支持网络速率的自适应,可以与快速以太网自动协商传输速率答案:AB参考知识点:华为3com认证教材第一册3-8页18、高层的协议将数据传递到网络层后,形成( ),而后传送到数据链路层(A) 数据帧(B) 信元(C) 数据包(D) 数据段答案:C参考知识点:华为3com认证教材第一册1-20页19、在路由器上配置帧中继静态map必须指定( )参数(A) 本地的DLCI(B) 对端的DLCI(C) 本地的协议地址(D) 对端的协议地址答案:AD20、路由器的主要性能指标不包括( )(A) 延迟(B) 流通量(C) 帧丢失率(D) 语音数据压缩比答案:D【思科认证CCNA认证试题和答案中文版】。
ccna第二学期练习答案

ERouting Chapter 1 - CCNA Exploration: 路由协议和概念 (版本1口令可用于限制对 Cisco IOS 所有或部分内容的访问。
请选择可以用口令保护的模式和接口。
(选择三项。
)VTY 接口控制台接口特权执行模式2路由器从相连的以太网接口收到消息后,会更改哪项报头地址,再将消息从另一个接口发送出去第 2 层源地址和目的地址3请参见图示。
网络管理员已经为路由器连接到直连网络的接口配置了如图所示的 IP 地址。
从路由器 ping 相连网络上的主机口之间相互 ping 都会遭到失败。
此问题最可能的原因是什么必须使用no shutdown命令启用接口。
4请参见图示。
主机 A ping 主机 B。
当 R4 收到对以太网接口的 ping 时,哪两块报头信息包括在内(选择两项。
)目的 IP 地址:目的 MAC 地址:5网络管理员刚把新配置输入 Router1。
要将配置更改保存到 NVRAM,应该执行哪一条命令Router1# copy running-config startup-config6您需要配置图中所示的串行连接,必须在 Sydney 路由器上发出以下哪条配置命令才能与 Melbourne 站点建立连接(选择三Sydney(config-if)# ip addressSydney no shutdownSydney(config-if)# clock rate 560007请参见图示。
从路由器的运行配置输出可得出什么结论显示的命令决定了路由器的当前运行情况。
8请参见图示。
在主机 2 连接到 LAN 上的交换机后,主机 2 无法与主机 1 通信。
导致此问题的原因是什么主机 1 和主机 2 位于不同的网络中。
9输入以下命令的作用是什么R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# login设置通过 Telnet 连接该路由器时使用的口令10以下哪一项正确描述了路由器启动时的顺序加载 bootstrap、加载 IOS、应用配置11加载配置文件时的默认顺序是怎样的NVRAM、TFTP、CONSOLE12请参见图示。
完整版CCNA测试题库及答案

完整版CCNA测试题库及答案描述载波侦听多路由访问/冲突检测(CSMA/CD)的工作原理。
CSMA/CD是一种帮助设备均衡共享带宽的协议,可避免两台设备同时在网络介质上传输数据。
虽然他不能消除冲突,但有助于极大的减少冲突,进而避免重传,从而提高所的设备的数据传输效率。
区分半双工和全双工通信。
并指出两种方法的需求。
与半双工以太网使用一对导线不同,全双工以太网使用两队导线,全双工使用不同的导线来消除冲突,从而允许同时发送和接收数据,而半双工可接收或发送数据,但不能同时接收和发送数据,且仍会出现冲突。
要使用全双工,电缆两端的设备都必须支持全双工,并配置成一全双模式运行。
描述MAC地址的组成部分以及各部分包含的信息。
MAC(硬件)地址时一种使用十六进制表示的地址,长48位(6B)。
其中前24位(3B)称为OUI(Organizationally Unique Idebtifier,组织唯一表示符),有IEEE分配给NIC制造商;余下的部分呢唯一地标识了NIC识别十进制数对应的二进制值和十六进制值。
用这三种格式之一表示的任何数字都可以转换为其他两种格式,能够执行这种转换对理解IP地址和子网划分至关重要。
识别以太网帧中与数据链路层相关的字段。
在以太网中,与数据链路层相关的字段包括前导码,帧其实位置分隔符,目标MAC地址,源MAC地址,长度或者类型以及帧校验序列。
识别以太网布线相关的IEEE标准。
这些标准描述了各种电缆类型的功能和物理特征,包括(但不限于)10Base2、10Base5和10BaseT。
区分以太网电缆类型及其用途。
以太网电缆分3种:直通电缆,用于将PC或路由器的以太网接口连接到集线器或交换机;交叉电缆。
用于将集线器连接到集线器,集线器连接到交换机,交换机连接到交换机以及PC连接到PC;反转电缆,用于PC和路由器或交换机之间建立控制台连接。
描述数据封装过程及其在分组创建中的作用。
数据封装指的是在OSI模型各层给数据添加信息的过程,也成为分组创建。
ccna第2章考试题

1以下哪个事件发生于传输层三次握手期间?两个应用程序交换数据。
TCP 初始化会话的序列号。
UDP 确定要发送的最大字节数。
服务器确认从客户端接收的数据字节数。
2采用 TCP/IP 数据封装时,以下哪个端口号范围标识了所有常用应用程序?0 到255256 到 10220 到10231024 到204749153 到655353请参见图示。
主机 A 正在使用FTP 从服务器1 下载大型文件。
在下载期间,服务器1 没有收到主机 A 对若干字节传输数据的确认。
服执行什么操作?创建第1 层堵塞信号到达超时时间后重新发送需要确认的数据向主机发送 RESET 位更改第4 层报头中的窗口大小4下列哪项是UDP 的重要特征?确认数据送达数据传输的延迟最短数据传输的高可靠性同序数据传输5下列哪三项功能使 TCP 得以准确可靠地跟踪从源设备到目的设备的数据传输?封装流量控制无连接服务会话创建编号和定序尽力传输6下列哪两项是用户数据报协议(UDP) 的功能?(选择两项)流量控制系统开销低无连接面向连接序列和确认7OSI 模型哪一层负责规范信息从源设备到目的设备准确可靠地流动?应用层表示层会话层传输层网络层8以下哪两个选项代表第4 层编址?(选择两项)标识目的网络标识源主机和目的主机标识正在通信的应用程序标识主机之间的多个会话标识通过本地介质通信的设备9下列哪个传输层协议提供低开销传输因而可用于不需要可靠数据传输的应用场合?TCPIPUDPHTTPDNS10请参见图示。
图中显示的是两台主机之间的TCP 初始数据交换。
假设初始序列号为0,如果数据段6 丢失,确认2 中将包含哪个序列23618503431347511TCP 报头信息和UDP 报头信息中都包含下列哪项信息?定序流量控制确认源和目的12下列哪项由源主机在转发数据时动态选择?目的逻辑地址源物理地址默认网关地址13请参见图示。
从显示的输出中可以确定以下哪两项信息?(选择两项)本地主机使用公认端口号标识源端口。
ccna考试题库最新版

ccna考试题库最新版CCNA(Cisco Certified Network Associate)认证是全球范围内最受欢迎的网络工程师认证之一,具备CCNA认证可以证明一个人在建立、规划、运行、安装和配置中等规模的局域网和广域网方面的专业知识。
为了帮助广大考生顺利通过CCNA考试,不断更新的CCNA考试题库至关重要。
以下是最新版本的CCNA考试题库,希望对考生们有所帮助。
第一部分:网络基础知识1. 什么是OSI七层模型?简要介绍每一层的功能。
2. TCP和UDP之间有哪些区别?请分别举例说明。
3. 什么是IP地址?IP地址的类型有哪些?请列举并简要介绍各自的特点。
4. 什么是子网掩码?为什么在网络中使用子网掩码?5. 简述常见的网络设备有哪些,以及各自的功能与作用。
第二部分:路由和交换技术1. 路由器和交换机之间有何区别?请进行比较并指出各自的优势和劣势。
2. 什么是VLAN?VLAN的作用及在网络中的应用场景是什么?3. OSPF和EIGRP是两种常见的路由协议,请比较它们的特点并举例说明。
4. 请解释静态路由和动态路由的概念以及在网络中的应用。
5. 交换机在网络中扮演什么角色?交换机的MAC地址表是如何工作的?第三部分:网络安全和管理1. 网络安全的重要性是什么?请列举几种常见的网络安全威胁并介绍应对策略。
2. 什么是ACL(访问控制列表)?ACL的作用是什么?请给出一个ACL的配置示例。
3. VPN是什么?VPN的工作原理及在企业网络中的应用。
4. SNMP是网络管理中常用的协议,它的作用是什么?请解释SNMP中的几个重要概念。
5. 如何保护无线网络的安全?请列举几种方法。
第四部分:WAN技术1. 什么是WAN?WAN的主要特点是什么?2. PPP协议和HDLC协议分别是什么?请比较它们的异同。
3. 什么是Frame Relay?Frame Relay的工作原理及在WAN中的应用。
4. 请解释T1和E1的概念,以及它们在传输速率和应用方面的差异。
2023年CCNA考试真题

2023年CCNA考试真题2023年CCNA考试正式开考啦!本次考试涉及网络技术的基础知识,将对考生的技术水平进行全面考察。
下面是本次考试的真题,希望能够帮助考生更好地复习。
【第一部分:选择题】(共10题,每题2分,共计20分)1. OSI模型中,位于网络层的协议是:A. TCPB. IPC. HTTPD. UDP2. 下面哪个命令可以查看路由表信息:A. pingB. tracertC. ipconfigD. route print3. 在IP地址192.168.0.1/24中,/24表示什么意思:A. 子网掩码B. 路由器IP地址C. 网络IDD. 主机ID4. 下面哪个协议可以实现主机与交换机之间的通信:A. BGPB. ARPC. MPLSD. SNMP5. 下面哪个命令可以查看IP地址的连通性:A. telnetB. netstatC. pingD. tracert6. VLAN是指:A. 虚拟本地区域网络B. 可视化局域网C. 个人局域网D. 无线局域网7. 下面哪个设备可以实现不同局域网之间的互联:A. 集线器B. 路由器C. 交换机D. 网桥8. 下面哪个协议负责在网络中寻找设备的物理地址:A. ARPB. ICMPC. OSPFD. BGP9. 下面哪个命令可以查看交换机的端口信息:A. show ip interface briefB. show mac-address-tableC. show running-configD. show version10. 下面哪个协议可以实现安全的远程登录:A. FTPB. HTTPC. SSHD. Telnet【第二部分:填空题】(共5题,每题4分,共计20分)1. 在OSI模型中,位于物理层的设备是_________。
2. 在TCP/IP协议族中,位于传输层的协议是_________。
3. IP地址由_________位二进制数组成。
思科CCNA考试答案(全)

CCNA思科考试答案(全)第 1 章考试1一家拥有10 名员工的小型公司使用单个LAN 在计算机之间共享信息。
哪种类型连接适合此公司?由当地电话服务提供商提供的拨号连接能够使公司方便且安全地连接员工的虚拟专用网络通过当地服务提供商建立的私有专用线路通过当地服务提供商提供的宽带服务(如DSL)答案:4解析:对于这种小型办公室,比较适合通过被称为数字用户线路(DSL) 的常见宽带服务实现Internet 连接,这种服务由当地的电话服务提供商提供。
由于员工人数很少,带宽的问题并不突出。
如果公司较大,在远程站点有分支机构,则专用线路会更加适合。
如果公司员工需要通过Internet 与公司联系,则采用虚拟专用网。
2哪种网络情况需要使用WAN?员工工作站需要获取动态分配的IP 地址。
员工在出差时需要通过VPN 连接到公司电子邮件服务器。
分支机构的员工需要与同一园区网络上的另一座建筑物内的公司总部共享文件。
员工需要访问托管在其建筑物内DMZ 中的公司Web 服务器上的网页。
答案:2解析:当出差的员工需要通过WAN 连接到公司电子邮件服务器时,VPN 将通过WAN 连接在员工笔记本电脑与公司网络之间创建一个安全隧道。
通过DHCP 获取动态IP 地址是LAN 通信的功能。
在企业园区的不同建筑物之间共享文件可通过LAN 基础设施来实现。
DMZ 是企业LAN 基础设施内一个受保护的网络。
3以下哪项描述了WAN 的特征?WAN 和LAN 在同一地理范围内运行,但有串行链路。
WAN 网络归运营商所有。
所有串行链路均被视为WAN 连接。
WAN 可提供到园区主干网的终端用户网络连接。
答案:2解析:WAN 可用于将企业LAN 互连到远程分支机构站点LAN 和远程工作人员站点。
WAN 归运营商所有。
虽然WAN 连接一般通过串行接口实现,但并不是所有串行链路均连接至WAN。
LAN(而非WAN)可在组织中提供终端用户网络连接。
4电路交换WAN 技术的两个常见类型是什么?(请选择两项。
ccna考试试题库

ccna考试试题库CCNA(Cisco Certified Network Associate)考试是思科认证网络专家的初级认证,主要测试考生在网络基础、路由、交换、无线和安全等方面的知识。
以下是一些模拟CCNA考试的试题和答案:1. 什么是子网掩码,它有什么作用?答案:子网掩码是一种IP地址的附加信息,用于指定IP地址中网络部分和主机部分的界限。
它的作用是允许路由器区分IP地址中的网络地址和主机地址,从而实现不同网络之间的路由。
2. 描述静态路由和动态路由的区别。
答案:- 静态路由:由网络管理员手动配置的路由信息,不随网络结构的变化而自动调整。
- 动态路由:由路由器根据网络拓扑的变化自动生成和更新的路由信息。
3. 什么是VLAN,它有什么好处?答案: VLAN(虚拟局域网)是一种在交换机上划分不同网络的技术,即使物理上连接在同一交换机上,也可以属于不同的VLAN。
VLAN的好处包括提高安全性、减少广播域、提高网络管理的灵活性等。
4. 简述TCP和UDP的区别。
答案:- TCP(传输控制协议):提供可靠的、面向连接的传输服务,有流量控制和拥塞控制机制。
- UDP(用户数据报协议):提供不可靠的、无连接的传输服务,适用于对实时性要求高的应用。
5. 什么是DHCP,它的作用是什么?答案: DHCP(动态主机配置协议)是一种网络管理协议,用于自动分配IP地址和其他网络配置信息给网络中的设备。
它的作用是简化网络配置,避免IP地址冲突。
6. 什么是NAT,它在网络中扮演什么角色?答案: NAT(网络地址转换)是一种技术,允许多个设备共享一个公共IP地址与互联网通信。
它在网络中扮演的角色是节省IP地址资源,隐藏内部网络结构。
7. 什么是STP(生成树协议)?答案: STP(生成树协议)是一种网络协议,用于在局域网中防止网络环路的产生。
通过创建一个无环的逻辑拓扑,STP确保网络的稳定性和可靠性。
8. 描述OSPF(开放最短路径优先)协议的工作原理。
CCNAS chapter 6 Exam
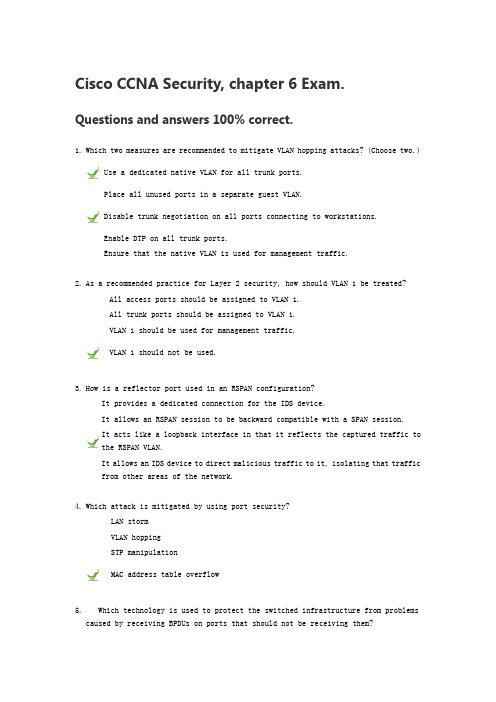
Cisco CCNA Security, chapter 6 Exam. Questions and answers 100% correct.1. Which two measures are recommended to mitigate VLAN hopping attacks? (Choose two.)Use a dedicated native VLAN for all trunk ports.Place all unused ports in a separate guest VLAN.Disable trunk negotiation on all ports connecting to workstations.Enable DTP on all trunk ports.Ensure that the native VLAN is used for management traffic.2. As a recommended practice for Layer 2 security, how should VLAN 1 be treated?All access ports should be assigned to VLAN 1.All trunk ports should be assigned to VLAN 1.VLAN 1 should be used for management traffic.VLAN 1 should not be used.3. How is a reflector port used in an RSPAN configuration?It provides a dedicated connection for the IDS device.It allows an RSPAN session to be backward compatible with a SPAN session.It acts like a loopback interface in that it reflects the captured traffic to the RSPAN VLAN.It allows an IDS device to direct malicious traffic to it, isolating that traffic from other areas of the network.4. Which attack is mitigated by using port security?LAN stormVLAN hoppingSTP manipulationMAC address table overflow5. Which technology is used to protect the switched infrastructure from problemscaused by receiving BPDUs on ports that should not be receiving them?RSPANPortFastRoot guardLoop guardBPDU guard6. Which three switch security commands are required to enable port security on a portso that it will dynamically learn a single MAC address and disable the port if a host with any other MAC address is connected? (Choose three.)switchport mode accessswitchport mode trunkswitchport port-securityswitchport port-security maximum 2switchport port-security mac-address stickyswitchport port-security mac-address mac-address7. When configuring a switch port for port security, what is the default violation mode?protectresetrestrictshutdown8. Which three statements are true regarding SPAN and RSPAN? (Choose three.)SPAN can send a copy of traffic to a port on another switch.RSPAN is required for syslog and SNMP implementation.SPAN can be configured to send a copy of traffic to a destination port on the same switch.SPAN can copy traffic on a source port or source VLAN to a destination port on the same switch.RSPAN is required to copy traffic on a source VLAN to a destination port on the same switch.RSPAN can be used to forward traffic to reach an IDS that is analyzing traffic for malicious behavior.9. Which Cisco endpoint security product helps maintain network stability by providingposture assessment, quarantining of noncompliant systems, and remediation of noncompliant systems?Cisco Access Control ServerCisco Security Agent workstationCisco Intrusion Prevention System routerCisco Network Admission Control appliance10. Which attack relies on the default automatic trunking configuration on most Ciscoswitches?LAN storm attackVLAN hopping attackSTP manipulation attackMAC address spoofing attack11. With IP voice systems on data networks, which two types of attacks target VoIPspecifically? (Choose two.)CoWPAttyKismetSPITvirusvishing12. Which two elements are part of the Cisco strategy for addressing endpoint security?(Choose two.)policy compliance using products such as Cisco NACnetwork infection monitoring using products such as Cisco Secure ACSthreat protection using products such as Cisco Security Agentattack detection using products such as Cisco NACrisk assessment compliance using products such as Cisco Security Agent 13. Which frames are spoofed in STP manipulation attacks?BPDUDTPISL802.1q14. Which option best describes a MAC address spoofing attack?An attacker gains access to another host and masquerades as the rightful user of that device.An attacker alters the MAC address of his host to match another known MAC address of a target host.An attacker alters the MAC address of the switch to gain access to the network device from a rogue host device.An attacker floods the MAC address table of a switch so that the switch can no longer filter network access based on MAC addresses.15. What happens when the MAC address notification feature is enabled on a switch?An SDEE alert is generated, and the switch resets the interface when an invalid MAC address is detected.An STP multicast notification packet is forwarded to all switches any time a change in the network topology is detected.A port violation occurs when a MAC address outside of the range of allowedaddresses transmits traffic over a secure port.An SNMP trap is sent to the network management system whenever a new MAC address is added to or an old address is deleted from the forwarding tables.16. Which device supports the use of SPAN to enable monitoring of malicious activity?Cisco NACCisco IronPortCisco Security AgentCisco Catalyst switch17. An administrator wants to prevent a rogue Layer 2 device from intercepting trafficfrom multiple VLANs on a network. Which two actions help mitigate this type of activity? (Choose two.)Disable DTP on ports that require trunking.Place unused active ports in an unused VLAN.Secure the native VLAN, VLAN 1, with encryption.Set the native VLAN on the trunk ports to an unused VLAN.Turn off trunking on all trunk ports and manually configure each VLAN asrequired on each port.18.Refer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?All traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded toFastEthernet 0/1.All traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded toFastEthernet 0/1.Native VLAN traffic received on VLAN 10 or transmitted from VLAN 20 is forwardedto FastEthernet 0/1.Native VLAN traffic transmitted from VLAN 10 or received on VLAN 20 is forwardedto FastEthernet 0/1.19. How many Cisco Security Agent clients can one Management Center for CSA consolesupport?1,00010,000100,0001,000,00020. Which three are SAN transport technologies? (Choose three.)Fibre ChannelSATAiSCSIIP PBXFCIPIDE21. If a switch is configured with the storm-control command and the action shutdownand action trap parameters, which two actions does the switch take when a storm occurs on a port? (Choose two.)The port is disabled.The switch is rebooted.An SNMP log message is sent.The port is placed in a blocking state.The switch forwards control traffic only.。
CCNA第二学期考试答案

以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1与固定配置的交换机相比,模块化交换机具有哪两个优点?(请选择两项。
)正确响应您的响应每台交换机的成本更低可扩展性更高转发率更低需要的电源插座数目更少带宽聚合可以使用多个端口固定配置交换机价格较低,但是它具有指定数量的端口且不能添加端口。
它们提供的高速端口通常比较少。
为了在包含固定配置交换机的网络上扩展交换,需要购买更多的交换机。
这增加了需要使用的电源插座数量。
模块化交换机只需要购买额外的线卡便可以扩展。
带宽聚合也更容易,因为机箱的背板可以为交换机端口线卡提供所需的带宽。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.2 交换网络2思科无边界架构接入层的基本功能是什么?正确响应您的响应聚合第 2 层广播域聚合第 3 层路由边界为用户提供访问权提供高可用性思科无边界架构接入层的功能是为用户提供网络访问。
第 2 层广播域聚合、第 3 层路由边界聚合和高可用性是分布层的功能。
也有说答案是聚合第 3 层路由边界此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络3思科无边界架构分布层的基本功能是什么?正确响应您的响应充当主干聚合所有园区块聚合第 3 层路由边界为用户提供访问权思科无边界架构的分布层的一项基本功能是在不同的VLAN 之间路由。
充当主干和聚合园区块是核心层的功能。
为用户提供访问是接入层的功能。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络4若将大端口密度、容错和低价作为重要指标,应使用哪个交换机外形因素?正确响应您的响应固定配置交换机模块化交换机可配备机架的1U 交换机可堆叠式交换机堆叠式交换机可以使用特殊电缆实现互联,从而在交换机之间提供高带宽的吞吐量,并像单个大型交换机一样运行。
ccna试题

ccna试题一、单选题1. 下面哪个是OSI模型的物理层?A. TCPB. IPC. EthernetD. HTTP答案:C2. 以下哪个是IPv6的全球未经分配地址?A. FC00::/7B. 2000::/3C. 8000::/4D. FFFF::/8答案:A3. 以下哪个在OSI模型的会话层工作?A. HTTPB. IPC. TCPD. NetBIOS答案:D二、多选题4. 下面哪些是用于路由器接口配置的命令?(选择两个)A. ip addressB. mac addressC. interfaceD. enable答案:A, C5. 下面哪些是IP协议的特点?(选择三个)A. 可靠传输B. 无连接C. 不可靠传输D. 面向连接答案:B, C, D6. 下面哪些是TCP的特点?(选择三个)A. 面向连接B. 可靠传输C. 无连接D. 面向字节流答案:A, B, D三、填空题7. TCP/IP协议族中,网络接口层对应的是__________。
答案:网络接口8. 在IPv6地址中,一个冒号表示__________。
答案:前缀和后缀之间的分隔符9. 在TCP连接终止过程中,主动关闭连接的一方发送的最后一个ACK分组中ACK标志位的值是__________。
答案:1四、解答题10. 请简要解释TCP/IP协议族中IP协议的作用。
答案:IP(Internet Protocol)协议是TCP/IP协议族中的一种网络层协议,主要负责在网络之间传输数据包。
它使用IP地址来标识网络上的设备,并通过路由选择算法实现数据包的正确传递。
IP协议是一种无连接的协议,不提供数据包的可靠传输,也不保证数据包按顺序到达目的地。
它使用IP头部来存储必要的控制信息,如源IP地址、目的IP地址、数据包长度等。
11. 请简要描述TCP三次握手的过程。
答案:TCP三次握手用于建立一个TCP连接。
过程如下:1. 客户端向服务器发送一个SYN(同步)分组,其中设置SYN标志位为1,并选择一个初始序列号。
CCNA认证考试真题

为⼤家收集整理了《CCNA认证考试真题》供⼤家参考,希望对⼤家有所帮助(1)TCP/IP Addressing and Protocol1: Your junior network administrator wants to know what the default subnet mask is for a Class C IP address. What do you tell him?A. 255.0.0.0B. 255.255.0.0C. 255.245.255.0D. 255.255.255.0E. 255.255.255.255 2: An application needs to have reliable, end-to-end connect-ivity. Which of the following protocols will give you reliable connectivity?A. TCPB. UDPC. IPD. ICMP 3: You are designing a network, which needs to support 55 users. You don't plan to extend the segment beyond the current number of users. Which subnet mask would best meet your needs?A. 255.255.0.0B. 255.255.255.0C. 255.255.255.192D. 255.255.255.160 4: You have added a new switch to your network. You want to manage it remotely, so you need to assign it an IP address. Your router that connects to the switch has an IP address of 172.16.12.33/27. Which of the following addresses can you assign to this switch?A. 172.16.12.33/28B. 172.16.12.32/27C. 172.16.12.33/27D. 172.16.12.34/27E. 172.16.12.35/28F. 172.16.12.38/28G. 172.16.12.63/27 5: The address 172.16.208.16/20 is a host address in which of the following subnets? A. 172.16.176.0–255.255.240.0B. 172.16.192.0–255.255.240.0C. 172.16.208.0–255.255.240.0D. 172.16.224.0–255.255.240.0 6: You are designing an IP address scheme for your brand new remote office. The vice president of IT calls to tell you that you will be in charge of the 192.168.1.64/26 subnetwork. This supplies you with a single subnetwork with 62 hosts. You need to have at least two subnets with 14 hosts in each subnet. What custom subnet mask should you use?A. 255.255.255.128B. 255.255.255.192C. 255.255.255.224D. 255.255.255.240E. 255.255.255.248 7: You have subnetted the 210.106.14.0 network with a /24 mask. Your boss at Acme, Inc. wants to know how many usable subnetworks and usable host addresses per subnet this would provide. What should you tell her?A. One network with 254 hostsB. Two networks with 128 hostsC. Four networks with 64 hostsD. Six networks with 30 hosts 8: Identify three valid host addresses in any subnet of the 201.168.27.0 network, assuming a fixed subnet mask of 255.255.255.240. (Choose three.)A. 201.168.27.33B. 201.168.27.112C. 201.168.27.119D. 201.168.27.126E. 201.168.27.175F. 201.168.27.208 9: What is the subnetwork address for a host with the IP address 201.100.5.68/28?A. 201.100.5.0B. 201.100.5.32C. 201.100.5.64D. 201.100.5.65E. 201.100.5.31F. 201.100.5.1 10: Which of the following protocols uses a three-way handshake mechanism to establish sessions?A. TCPB. IPC. UDPD. IPXE. Frame relay 11: Which of the following protocols is connection-oriented? A. TCPB. IPC. IPXD. Frame relay 12: You are using an application on your Windows 2000 client machines that provides error correction. You need a protocol to provide fast transport. Which protocol should your application use?A. TCPB. IPC. UDPD. SPXE. AppleTalk 13: When using TCP, after a session is open, the applications can adjust the number of segments they receive before sending an acknowledgment. This behavior is known as ______________.A. MTU adjustmentB. WindowingC. Flexible Send PathD. FCS 14: If the destination did not receive a segment, how will the TCP host know to resend the information?A. The ACK received will not include the segment number that was not received.B. The ACK received will include the segment number that was not received.C. The sending host will send a PACK to verify segment receipt.D. The destination host will send a YACK message back to the sending host. 15: You are planning on using a single network that supports 208 users. Which IP address class would you choose to be the most efficient?A. Class AB. Class BC. Class CD. Class DE. Class E 16: RFC 1918 defines the private IP address ranges. Which of the following IP addresses are considered part of these ranges? (Choose three.)A. 10.23.45.67B. 126.21.34.56C. 172.16.32.1D. 172.31.234.55E. 192.169.4.5 17: A new network is being designed for your company, Acme, Inc. If you use a Class C IP network, which subnet mask will provide one usable subnet per department while allowing enough usable host addresses for each department specified in the table?Department Number of Users Corporate 7 Customer Support 15 Financial 13 HR 7 Engineering 16 A. 255.255.255.0B. 255.255.255.192C. 255.255.255.224D. 255.255.255.240E. 255.255.255.248 18: Which of these protocols provides data transport, relying on the error correction capabilities of the application itself?A. UDPB. TCPC. SNMPD. ICMP 19: Which of the following are used by TCP to ensure reliable delivery of data? (Choose two.)A. MAC address resolutionB. Sequence numbersC. AcknowledgmentsD. PingE. Routing updates 20: You discover that you are able to adjust the window size of the TCP segment. You increase the window size to test the results. What will you observe happening on your network?A. Increased throughputB. Decreased throughputC. Increased latencyD. Decreased reliability21: Your organization is using the 192.168.1.0/24 address space. You need 28 subnets. What subnet mask would you use to create these subnets?A. 255.255.255.0B. 255.255.255.128C. 255.255.255.192D. 255.255.255.224E. 255.255.255.240F. 255.255.255.248 22: Which of the following protocols maps IP addresses to MAC addresses for connectivity to occur between two hosts?A. ARPB. RARPC. SLARPD. DHCP 23: Your junior network administrator cannot seem to ping a host in another network and asks you why it isn't working. Which of the following is not an answer that you would give him?A. The host's default gateway is down.B. The destination host is not powered on.C. The IP address of the router interface is incorrect.D. The IP address of the switch to which the destination host connects is incorrect.E. The host is in a different subnet. 24: Which of the following classes of IP addresses is utilized for multicasting?A. Class AB. Class BC. Class CD. Class D 25: You give your IT department a spreadsheet of IP addresses and their subnets. You receive a call from one of the junior techs asking what the /26 means next to the IP addresses. You tell her: A. It represents the number of hosts possible on that subnetwork.B. It represents the number of subnetworks that are being used.C. It represents the class of IP address being used.D. It represents the number of bits in the subnet mask that are 1. 26: You are given an IP network of 192.168.5.0 and told that you need to separate this network into subnetworks that can support a maximum of 16 hosts per subnet. This will help alleviate congestion on the network. What subnet mask can you use to create the subnets necessary to meet the given criteria?A. 255.0.0.0B. 255.255.0.0C. 255.255.255.0D. 255.255.255.224E. 255.255.255.240 27: Which of the following would a Class A network be assigned to?A. Government agencyB. Small-to-medium sized corporationD. An individual 28: A client has the IP address 192.168.5.98/27. Which of the following addresses are on the same subnet as this host? (Choose two.)A. 192.168.5.95B. 192.168.5.100C. 192.168.5.128D. 192.168.5.110 29: Which of the following IP addresses is not a public IP address that can be routed over the Internet?A. 2.3.4.5B. 11.12.13.14C. 165.23.224.2D. 172.31.45.34E. 203.33.45.22 30: You are given a Class B network. What is the default subnet mask assigned to the Class B network?A. 255.255.255.255B. 255.255.0.0C. 255.224.0.0D. 0.0.0.0 31: You are troubleshooting your router's interfaces. For some reason, the Ethernet interface will not accept the IP address of 192.168.5.95/27 that you've assigned. Which of the following explains the router's refusal to take the IP address?A. Class C addresses cannot be assigned to Ethernet interfaces.B. The /27 is an invalid mask.C. It is a broadcast address.D. It is a public IP address.E. It is a private IP address. 32: You are a network technician at Acme, Inc. You are required to divide the 172.12.0.0 network into subnets. Each subnet must have the capacity of 458 IP addresses. Also, according to the requirements, you must provide the maximum number of subnets. Which subnet mask should you use?A. 255.255.255.254B. 255.255.254.0C. 255.255.240.254D. 255.255.0.0 33: What is the subnetwork and broadcast IP address of 192.168.2.37 with the subnet mask of255.255.255.248?A. 192.168.2.24/192.168.2.31B. 192.168.2.32/192.168.2.39C. 192.168.2.40/192.168.2.47D. 192.168.2.48/192.168.2.55E. 192.168.2.56/192.168.2.63 34: One of your co-workers at Acme, Inc., needs to convert the binary number 11011010 into a decimal. What is the decimal equivalent?A. 218B. 219C. 220E. 222 35: One of your co-workers at Acme, Inc., needs to convert the binary number 01011010 into a decimal. What is the decimal equivalent?A. 75B. 83C. 90D. 97 36: One of your co-workers at Acme, Inc., needs to convert the binary num b e r 1 1 0 1 0 1 1 0 i n t o a d e c i m a l . W h a t i s t h e d e c i m a l e q u i v a l e n t ? / p > p b d s f i d = " 2 1 0 " > A . 1 9 8 / p > p b d s f i d = " 2 1 1 " > B . 2 1 4 / p > p b d s f i d = " 2 1 2 " > C . 2 5 2 / p > p b d s f i d = " 2 1 3 " > D . 2 5 5 3 7 : O n e o f y o u r c o - w o r k e r s a t A c m e , I n c . , n e e d s t o c o n v e r t t h e b i n a r y n u m b e r 1 0 1 1 0 1 1 0 i n t o a d e c i m a l . W h a t i s t h e d e c i m a l e q u i v a l e n t / p > p b d s f i d = " 2 1 4 " > A . 1 8 2 / p > p b d s f i d = " 2 1 5 " > B . 1 9 2 / p > p b d s f i d = " 2 1 6 " > C . 2 0 2 / p > p b d s f i d = " 2 1 7 " > D . 2 1 2 3 8 : Y o u a r e c o n f i g u r i n g a s u b n e t f o r t h e A c m e , I n c . , b r a n c h o f f i c e i n B e i j i n g . Y o u n e e d t o a s s i g n I P a d d r e s s e s t o h o s t s i n t h i s s u b n e t . Y o u h a v e b e e n g i v e n t h e s u b n e t m a s k o f 2 5 5 . 2 5 5 . 2 5 5 . 2 2 4 . W h i c h o f t h e s e I P a d d r e s s e s w o u l d b e v a l i d ? ( C h o o s e t h r e e . ) / p > p b d s f i d = " 2 1 8 " > A . 1 5 . 2 3 4 . 1 1 8 . 6 3 / p > p b d s f i d = " 2 1 9 " > B . 9 2 . 1 1 . 1 7 8 . 9 3 / p > p b d s f i d = " 2 2 0 " > C . 1 3 4 . 1 7 8 . 1 8 . 5 6 / p > p b d s f i d = " 2 2 1 " > D . 1 9 2 . 1 6 8 . 1 6 . 8 7 / p > p b d s f i d = " 2 2 2 " > E . 2 0 1 . 4 5 . 1 1 6 . 1 5 9 / p > p b d s f i d = " 2 2 3 " > F . 2 1 7 . 6 3 . 1 2 . 1 9 2 3 9 : Y o u a r e a n e t w o r k t e c h n i c i a n a t A c m e , I n c . Y o u h a v e s u b n e t t e d t h e 2 0 8 . 9 8 . 1 1 2 . 0 n e t w o r k w i t h a / 2 8 m a s k . Y o u r b o s s a s k s y o u h o w m a n y u s a b l e s u b n e t w o r k s a n d u s a b l e h o s t a d d r e s s e s p e r s u b n e t t h i s w i l l p r o v i d e . W h a t s h o u l d y o u t e l l h e r , a s s u m i n g y o u r r o u t e r i s u s i n g i p s u b n e t - z e r o ? / p > p b d s f i d = " 2 2 4 " > A . 62 n e t w o r k s a n d 2 h o s t s / p > p b d s f i d = " 2 2 5 " > B . 6 n e t w o r k s a n d3 0 h o s t s / p > p b d s f i d = " 2 2 6 " >C . 8 n e t w o r k s a n d 3 2 h o s t s / p > p b d s f i d = " 2 2 7 " >D . 1 6 n e t w o r k s a n d 1 6 h o s t s / p > p b d s f i d = " 22 8 " > E . 1 6 n e t w o r k s a n d 1 4 h o s t s 4 0 : W h a t i s a d i s a d v a n t a g e o f u s i n g a c o n n e c t i o n - o r i e n t ed p r o t o c o l s u c h a s T C P ? / p > p b d s f i d = " 2 2 9 " > A . P a c ke t a c k n o w l e d g m e n t m i g h t a d d o v e r h ea d . / p > pb d s f i d = " 2 3 0 " > B . P ac k e t s a r e n o t t a g g ed w i t h se q u e n c e n u m b e r s . / p > p b d sf i d = " 23 1 " > C . L o s s o r d u p l i c a t i o n o f d a t a p a c k e t s i s m o r e l i k e l y t o o c c u r . / p > p b d s f i d = " 2 3 2 " > D . Th e a p p l i c a t i o n l a y e r m u s t a s s u m e r e s p o n s i b i l i t y f o r t h e c o r r e c t s e q u e n c i n g o f t h e d a t a p ac k e t s . 4 1 : Y o u a r e a n e t w o r k t e c h n i c i a n a t A c m e , I n c . Y o u h a v e s u b n e t t ed t he 1 9 2 . 1 6 8 . 7 2 .0 n e t w o r k w i t h a / 3 0 m a s k f o r c o n n e c t i o n s b e t w e e n y o u r r o u t e r s . Y o u r b o s s a s k s y o u h o w m a n y u s a b l e s u b n e t w o r k s a n d u s a b l e h o s t a d d r e s s e s p e r s u b n e t t h i s w i l l p r o v i d e . W h a t s h o u l d y o u t e l l h e r , a s s u m i n g y o u r r o u t e r c a n n o t u s e i p s u b n e t - z e r o ? / p > p b d s f i d = " 2 3 3 " > A . 6 2 n e t w o r k s a n d 2 h o s t s / p > p b d s f i d = " 2 3 4 " > B . 6 n e t w o r k s a n d 3 0 h o s t s / p > p b d s f i d = " 2 3 5 " > C .8 n e t w o r k s a n d 3 2 h o s t s / p > p b d s f i d = " 2 3 6 " > D . 1 6 n e t w o r k s a n d 1 6 h o s t s / p > p b d s f i d = " 2 3 7 " > E . 1 4 n e t w o r k s a n d 1 4 h o s t s 4 2 : W h i c h o f t h e f o l l o w i n g I P a d d r e s s e s a r e c o n s i d e r e d " n e t w o r k " a d d r e s s e s w i t h a / 2 6 p r e f i x ? ( C h o o s e t w o . ) / p > p b d s f i d = " 2 3 8 " > A . 1 6 5 . 2 0 3 . 2 . 0 / p > p b d s f i d = " 2 3 9 " > B . 1 6 5 . 2 0 3 . 5 . 1 9 2 / p > p b d s f i d = " 2 4 0 " > C . 1 6 5 . 2 0 3 . 6 . 6 3 / p > p b d s f i d = " 2 4 1 " > D . 1 6 5 . 2 0 3 . 6 . 1 9 1 / p > p b d s f i d = " 2 4 2 " > E . 1 6 5 . 2 0 3 . 8 . 2 5 5 4 3 : I d e n t i f y t h r e e v a l i d h o s t s i n a n y s u b n e t o f 1 9 2 . 1 6 8 . 3 2 . 0 , a s s u m i n g t h e s u b n e t m a s k u s e d i s 2 5 5 . 2 5 5 . 2 5 5 . 2 4 0 . ( C h o o s e t h r e e . ) / p > p b d s f i d = " 2 4 3 " > A . 1 9 2 . 1 6 8 . 3 2 . 3 3 / p > p b d s f i d = " 2 4 4 " > B . 1 9 2 . 1 6 8 . 3 2 . 1 1 2 / p > p b d s f i d = " 2 4 5 " > C . 1 9 2 . 1 6 8 . 3 2 . 1 1 9 / p > p b d s f i d = " 2 4 6 " > D . 1 9 2 . 1 6 8 . 3 2 . 1 2 6 / p > p b d s f i d = " 2 4 7 " > E . 1 9 2 . 1 6 8 . 3 2 . 1 7 5 / p > p b d s f i d = " 2 4 8 " > F . 1 9 2 . 1 6 8 . 3 2 . 2 0 8 4 4 : A C l a s s C n e t w o r k a d d r e s s h a s b e e n s u b n e t t e d w i t h a / 2 7 m a s k . W h i c h o f t h e f o l l o w i n g a d d r e s s e s i s a b r o a d c a s t a d d r e s s f o r o n e o f t h e r e s u l t i n g s u b n e t s ? / p > p b d s f i d = " 2 4 9 " > A . 1 9 8 . 5 7 . 7 8 . 3 3 / p > p b d s fi d = " 2 5 0 " > B . 1 9 8 . 5 7 . 7 8 . 6 4 / p > p b d s f i d = " 2 5 1 " > C . 1 9 8 . 5 7 . 7 8 . 9 7 / p > p b d s f i d = " 2 5 2 " > D . 1 98 . 5 7 . 7 8 . 9 7 / p > p b d s f i d = " 2 5 3 " > E . 1 9 8 . 5 7 . 7 8 . 1 5 9 / p > p b d s f i d = " 2 5 4 " > F . 1 9 8 . 5 7 . 7 8 . 2 5 4 4 5 : W h a t i s t h e s u b n e t w o r k a d d r e s s f o r a h o s t w i t h I P a d d r e s s 1 6 5 . 1 0 0 . 5 . 6 8 / 2 8 ? / p > p b d s f i d = " 2 5 5 " > A . 1 6 5 . 1 0 0 . 5 . 0 / p > p b d s f i d = " 2 5 6 " > B . 1 6 5 . 1 0 0 . 5 . 3 2 / p > p b d s f i d = " 2 5 7 " > C . 1 6 5 . 1 0 0 . 5 . 6 4 / p > p b d s f i d = " 2 5 8 " > D . 1 6 5 . 1 0 0 . 5 . 6 5 / p > p b d s f i d = " 2 5 9 " > E . 1 6 5 . 1 0 0 . 5 . 3 1 / p > p b d s f i d = " 2 6 0 " > F . 1 6 5 . 1 0 0 . 5 . 1 4 6 : Y o u r b o s s w a n t s t o k n o w w h a t T C P s t a n d s f o r . W h a t d o y o u t e l l h i m ? / p > p b d s f i d = " 2 6 1 " > A . T r a n s m i s s i o n C h e c k P r o t o c o l / p > p b d s f i d = " 2 6 2 " > B . T r a n s p o r t C h e c k P r o t o c o l / p > p b d s f i d = " 2 6 3 " > C . T r a n s m i s s i o n C o n t r o l P r o t o c o l / p > p b d s f i d = " 2 6 4 " > D . T r a n s p o r t C o n t r o l P r o t o c o l 4 7 : Y o u r b o s s w a n t s t o k n o w w h a t U D P s t a n d s f o r . W h a t d o y o u t e l l h i m ? / p > p b d s f i d = " 2 6 5 " > A . U n r e l i a b l e D a t a P r o t o c o l / p > p b d s f i d = " 2 6 6 " > B . U n r e l i a b l e D a t a P r o g r a m / p > p b d s f i d = " 2 6 7 " > C . U s e r - D e f i n e d P r o t o c o l / p > p b d s f i d = " 2 6 8 " > D . U s e r D a t a g r a m P r o t o c o l 4 8 : W h i c h o f t h e f o l l o w i n g s t a t e m e n t s a c c u r a t e l y d e s c r i b e s U D P ? / p > p b d s f i d = " 2 6 9 " > A . U D P c o p i e s f i l e s b e t w e e n a c o m p u t e r a n d a s y s t e m r u n n i n g r s h d , t h e r e m o t e s h e l l s e r v i c e ( d a e m o n ) . / p > p b d s f i d = " 2 7 0 " > B . U D P i s a m e m b e r o f t h e T C P / I P s u i t e o f p r o t o c o l s t h a t g o v e r n s t h e e x c h a n g e o f e l e c t r o n i c m a i l b e t w e e n m e s s a g e t r a n sf e r ag e n t s . / p > p b d s f i d = " 2 7 1 " > C . U D P i s a m e m b e r o f th e T C P / I P s ui t e o f p r o t o c o l s a n d i s u s e d t o c o p y f i l e s b e t w e e n t w o c o m p u t e r s o n t h e I n t e r n e t . B o t h c o m p u t e r s m u s t s u p p o r t t h e i r r e s p e c t i v e r o l e s : o n e m u s t b e a c l i e n t , a n d t h e o t h e r a s e r v e r . / p > p b d s f i d = " 2 7 2 " > D . U D P i s a T C P c o m p l e m e n t t h a t o f f e r s a c o n n e c t i o n l e s s d a t a g r a m s e r v i c e g u a r a n t e e i n g n e i t h e r d e l i v e r y n o r c o r r e c t s e q u e n c i n g o f d e l i v e r e d p a c k e t s ( m u c h l i k e I P ) . 4 9 : W h i c h o f t h e f o l l o w i n g h o s t a d d r e s s e s a r e m e m b e r s o f n e t w o r k s t h a t c a n b e r o u t e d a c r o s s t h e p u b l i c I n t e r n e t ( C h o o s e t h r e e . ) / p > p b d s f i d = " 2 7 3 " > A . 1 0 . 2 0 . 1 2 . 6 4 / p > p b d s f i d = " 2 7 4 " > B . 1 7 2 . 1 6 . 3 2 . 12 9 / p > p b d s f i d = " 2 7 5 " > C . 1 7 2 . 6 4 .3 2 . 34 / p > p b d s f i d = " 2 7 6 " > D . 1 9 2 . 1 6 8 . 2 3 . 25 2 / p > p b d s f id = " 2 7 7 " > E . 1 9 6 . 1 0 4 . 1 2 . 9 5 / p > p b d s f i d = " 2 7 8 " > F . 2 1 4 . 1 9 2 . 4 8 . 2 5 4 5 0 : Y o u a re c o n n e c t i n g y o u r S e r i a l 0 / 1 i n t e rf a c e t o t h e I n t e r n e t . W h i c h o f t h e f o l l o w i ng n e e d t o b e d o n e f o r th e c o n n e c ti o n t o w o r k ? ( C h o o s e t w o . ) / p > p b d s f i d = " 2 7 9 " > A . A s s i g n a p u b l i c I P a d d r e s s . / p > p b d s f i d = " 2 8 0 " > B . U s e t h e s h u t d o w n c o m m a n d . / p > p b d s f i d = " 2 8 1 " > C . U s e t h e n o s h u t d o w n c o m m a n d . / p > p b d s f i d = " 2 8 2 " > D . M a k e s u r e t h e i n t e r f a c e i s r u n n i n g i n f u l l - d u p l e x . / p >。
ccna测试题及答案

ccna测试题及答案CCNA测试题及答案一、选择题1. 在Cisco设备上,以下哪个命令用于查看当前的路由表?A. show ip routeB. show running-configC. show interface statusD. show version答案:A2. 以下哪个协议用于在网络中自动发现其他设备?A. ARPB. CDPC. ICMPD. TCP答案:B3. 以下哪个命令用于配置Cisco设备上的接口?A. configure terminalB. interfaceC. ip addressD. hostname答案:A二、填空题4. 在Cisco设备上,使用命令_________可以查看接口的配置信息。
答案:show interface5. 静态路由配置中,_________命令用于指定下一跳地址。
答案:ip route6. 动态路由协议可以自动适应网络变化,其中_________是最常见的一种。
答案:RIP(路由信息协议)三、简答题7. 请简述VLAN(虚拟局域网)的作用。
答案:VLAN是一种将局域网内不同物理位置的设备划分为同一逻辑网络的技术,主要用于隔离广播域,提高网络的安全性和效率。
8. 描述交换机和路由器在网络中的基本功能。
答案:交换机主要用于局域网内部,通过MAC地址表来转发数据帧,实现数据包在局域网内的快速交换。
路由器则工作在网络层,使用IP地址来转发数据包,连接不同的网络,并进行路径选择。
四、计算题9. 假设一个子网掩码为255.255.255.192,计算这个子网的可用IP地址范围。
答案:可用IP地址范围为192.168.1.0到192.168.1.62(包含两端)。
五、实验题10. 请根据以下配置文件,列出Router1的接口配置信息。
```Router1show running-configinterface FastEthernet0/0ip address 192.168.1.1 255.255.255.0duplex autospeed auto!interface FastEthernet0/1no ip addressshutdown!interface Serial0/0/0ip address 10.0.0.1 255.255.255.252clock rate 64000!router ospf 1network 192.168.1.0 0.0.0.255 area 0network 10.0.0.0 0.0.0.3 area 0!```答案:- FastEthernet0/0: IP地址为192.168.1.1,子网掩码为255.255.255.0,双工模式和速度均为自动。
CCNA第二学期官方章节考试题之《距离矢量路由协议》(附答案)46doc

数据包在路由器的两个环回接口之间来回传递
从目的地返回的路径与出发路径不同而形成
数据包在一系列路由器间不断传输却始终无法到达其真正的目的地的情况路由从一种路由协议到另一种路由协议的分布
2
用于在发送到其它路由器的更新中将路由标记为不可达
防止定期更新消息错误地恢复已经不可用的路由
防止从收到更新的接口通告同一网络
限制数据包在被丢弃之前在网络中传输的时间或跳数
通过设置最大跳数来为每一距离矢量路由协议定义最大度量值
4以
路由环路
不一致的流量转发
除非系统收敛,否则不会转发任何流量
路由表条目不一致
路由表更新被发送到错误的目的地
6运
立即将其加入路由表中
调整新路由的度量以显示增加的路由距离
将该路由从其传入接口以外的所有其它接口通告出去
发送
8下
它会在更新从路由器接口送出时缓冲更新,以此防止路由更新同步。
它会从下一次路由更新间隔中减去随机时间段(大小为指定间隔时间的
它会使路由器跳过每一个其它计划更新时间,以此防止路由更新同步。
它会强制路由器在发送自身更新之前侦听链路上的其它更新是何时发送的,以此防止路由更新同步10
13以15水
17R
19哪
抑制计时器将等候
如果在
更新计时器将请求有关从路由器Hello。
CCNA路由部分测试题(含答案)

CCNA路由部分测试题(共50题)1.当路由器接收的IP报文的目的地址不是本路由器的接口IP地址,并且在路由表中未找到匹配的路由项,采取的策略是什么?A.丢掉该分组B.将该分组分片C.转发该分组D.以上答案均不对ANSWER:A2.IGP 的作用范围是?A.区域内B.自然子网范围内C.局域网内D.自治系统内ANSWER:D3.距离矢量协议包括?(多选)A.RIPB.IS-ISC.OSPFD.EIGRPANSWER:A D4.解决路由环问题的办法是?(多选)A.定义路由权的最大值B.路由保持法C.水平分割D.路由器重启ANSWER:A B C5.在rip 中metric 等于什么值为不可达?A.8B.10C.15D.16ANSWER:D6.下列关于OSPF 协议的说法正确的是?(多选)A.OSPF 支持基于接口的报文验证B.OSPF 支持到同一目的地址的多条等值路由C.OSPF 是一个基于链路状态算法的边界网关路由协议D.OSPF 发现的路由可以根据不同的类型而有不同的优先级ANSWER:A B D7.如果一个内部网络对外的出口只有一个,那么最好配置?A.缺省路由B.主机路由C.动态路由ANSWER:A8.以下不属于动态路由协议的是?A.RIPB.ICMPC.EIGRPD.OSPFANSWER:B9.关于矢量距离算法以下哪些说法是错误的?A.矢量距离算法不会产生路由环路问题B.矢量距离算法是靠传递路由信息来实现的C.路由信息的矢量表示法是(目标网络,metric)D.使用矢量距离算法的协议只从自己的邻居获得信息ANSWER:A10.以下哪些路由表项要由网络管理员手动配置?(多选)A.静态路由B.直接路由C.缺省路由D.动态路由ANSWER:A C11.关于RIP 协议,下列说法正确的有?(多选)A.RIP 协议是一种IGPB.RIP 协议是一种EGPC.RIP 协议是一种距离矢量路由协议D.RIP 协议是一种链路状态路由协议ANSWER:A C12.下列关于链路状态算法的说法正确的是?(多选)A.链路状态是对路由的描述B.链路状态是对网络拓扑结构的描述C.链路状态算法本身不会产生自环路由D.OSPF 和RIP 都使用链路状态算法ANSWER:B C13.路由器中时刻维持着一张路由表,这张路由表可以是静态配置的,也可以是什么协议产生的?A.生成树协议B.链路控制协议C.动态路由协议D.被承载网络层协议ANSWER:C14.在路由器中,如果去往同一目的地有多条路由,则决定最佳路由的因素有?(多选)A.路由的优先级B.路由的发布者C.路由的metric 值D.路由的生存时间ANSWER:A C15.下面哪一项正确描述了路由协议?A.允许数据包在主机间转送的一种协议B.定义数据包中域的格式和用法的一种方式C.通过执行一个算法来完成路由选择的一个协议D.指定MAC 地址和IP 地址捆绑的方式和时间的一种协议ANSWER:C16.IGP 包括如下哪些协议?(多选)A.RIPB.BGPC.IS-ISD.EIGRPE.OSPFANSWER:A C D E17.RIP 协议引入路由保持机制的作用是?A.节省网络带宽B.防治网络中形成路由环路C.将路由不可达信息在全网扩散D.通知邻居路由器哪些路由是从其处得到ANSWER:B18.对路由理解正确的是?A.路由是路由器B.路由是信息在网络路径的交叉点C.路由是用以配置报文的目的地址D.路由就是指导报文发送的路径信息ANSWER:D19.路由协议RIP,OSPF和静态路由各自得到了条到达目标网络,在CISCO路由器默认情况下,最终选选定哪种路由作为最优路由?A.RIPB.OSPFC.静态路由ANSWER:C20.在RIP 协议中,计算metric 值的参数是?A.MTUB.时延C.带宽D.路由跳数ANSWER:D21.衡量路由算法好坏的原则不包括?A.快速收敛性B.灵活性,弹性C.拓扑结构先进D.选径是否是最佳ANSWER:C22.RIP 协议是基于?A.UDPB.TCPC.ICMPD.Raw IPANSWER:A23.禁止RIP 协议的路由聚合功能的命令是?A.no route ripB.summanyC.no auto summanyD.undo networkANSWER:C24.解决路由环路的方法有?(多选)A.水平分割B.抑制时间C.毒性逆转D.触发更新ANSWER:A B C D25.路由环问题会引起哪些问题?(多选)A.慢收敛B.广播风暴C.路由器重起D.路由不一致ANSWER:A D26.下列哪些路由协议存在路由自环问题?(多选)A.RIPB.IGRPC.OSPFD.IS-ISE.EIGRPANSWER:A B27.关于RIP V1 和RIP V2,下列说法哪些正确?(多选)A.RIP V1 报文支持子网掩码B.RIP V2 报文支持子网掩码C.RIP V2 缺省使用路由聚合功能D.RIP V1 只支持报文的简单口令认证,而RIP V2 支持MD5 认证ANSWER:B C28.在一个运行OSPF 的自治系统之内?(多选)A.骨干区域自身也必须连通的B.非骨干区域自身也必须连通的C.必须存在一个骨干区域(区域号为0)D.非骨干区域与骨干区域必须直接相连或逻辑上相连ANSWER:A C D29.以下关于Rip 路由聚合的说法正确的是?(多选)A.Rip V1 默认支持路由聚合,需要时可以关闭路由聚合功能B.华为Quidway 系列路由器Rip V2 的实现可以关闭路由聚合功能C.Rip V1 不支持子网路由聚合到一个非自然子网路由D.Rip V2 支持子网路由聚合到一个非自然子网路由ANSWER:B C D30.假设有这样的组网实例:两台路由器(假设为RTA 和RTB)通过串口相接,其中RTA 的串口IP 地址是,RTB 的串口IP 地址是,RTA 通过以太口连接的本地局域网的IP 地址是,RTB 通过以太口连接的本地局域网IP 地址是,在上面所有的接口上都启动RIP V1(仅仅RIP V1)协议,那么,下列说法正确的是?(多选)A.在RTA 的本地局域网上的计算机可以访问在RTB 本地局域网上的计算机B.在RTB 的本地局域网上的计算机可以访问在RTA 本地局域网上的计算机C.在RTA 的本地局域网上的计算机不能访问在RTB 本地局域网上的计算机D.在RTB 的本地局域网上的计算机不能访问在RTA 本地局域网上的计算机ANSWER:C D31.根据路由的目的地不同,路由表可被划分为?(多选)A.子网路由B.直连路由C.缺省路由D.主机路由E.静态路由ANSWER:A D32.对路由器A 配置RIP 协议,并在接口S0(IP 地址为路由协议,在全局配置模式下使用的第一条命令是?A.router ripwork allworkworkANSWER:A33.当接口运行在RIP-2 广播方式时,它可以接受的报文有?(多选)A.RIP-1 广播报文B.RIP-1 组播报文C.RIP-2 广播报文D.RIP-2 组播报文ANSWER:A C34.RIP 协议的路由项在多少时间内没有更新会变为不可达?A.90sB.120sC.180sD.240sANSWER:C35.VLSM 的含义是?A.Variable Length Subnet MaskingB.Variable Length Shortest MaskingC.Very Long/Shortest MaskingD.Variable Long Subnet MaskingE.Variable Length Short MeasurementANSWER:A36.距离矢量路由协议使用水平分割(split horizon)技术的目的是什么?(多选)A.避免在毗邻路由器之间产生路由环路B.确保路由更新数据报文沿着接收路线方向发送C.与保持间隔(holddown)机制协同工作,为保持间隔的计算提供更多的可靠性D.代替路由中毒(poison reverse)算法ANSWER:A C37.作为一个网络维护人员,对于OSPF 区域体系机构的原则必须有清楚地了解,下面的论述表达正确的是?(多选)A.所有的OSPF 区域必须通过边界路由器与区域0 相连,或采用OSPF 虚链路B.所有区域间通信必须通过骨干区域0,因此所有区域路由器必须包含到区域0 的路由C.单个区域不能包含没有物理链路的两个区域边界路由器D.虚链路可以穿越stub 区域ANSWER:A B38.支持可变长子网掩码的路由协议有?(多选)A.RIP v1B.RIP v2C.OSPFD.EIGRPANSWER:B C D39.因为在生成路由表的过程中,OSPF 协议需要进行复杂的SPF 算法来计算网络拓扑结构,所以相对距离矢量路由选择协议来说,它需要更大的开销,更多的延迟,更高的CPU 占用率。
CCNA2_final 6

CCNACCNA2_final 61 Which of the following are primary functions of a router? (Choose two.)packet switchingmicrosegmentationdomain name resolutionpath selectionflow control2 Using default settings, what is the next step in the router boot sequence after the IOS loads from flash?Perform the POST routine.Search for a backup IOS in ROM.Load the bootstrap program from ROM.Load the running-config file from RAM.Locate and load the startup-config file from NVRAM.3 Which two locations can be the source of the Cisco IOS that is used by a router during the bootup process? (Choose two.)flash memoryRAMNVRAMTFTP serverconfiguration register4 What are two switching functions of a router? (Choose two.)The router encapsulates the packet in the appropriate data link frame type for the outgoing data link.The router re-encapsulates the packet in a new frame, which results in a change of the Layer 2 header at each hop.The router determines the exit interface after data encapsulation.The router changes the source logical address to the forwarding router interface logical address. The router re-encapsulates the IP packet if no matching entry is found in the routing table and no default route is configured.5Refer to the exhibit. Which statement is true concerning the routing configuration?Using dynamic routing instead of static routing would have required fewer configuration steps. The 10.1.1.0/24 and 10.1.2.0/24 routes have adjacent boundaries and should be summarized. Packets routed to the R2 Fast Ethernet interface require two routing table lookups.The static route will not work correctly.6Refer to the exhibit. How many routes are ultimate routes?34577Refer to the exhibit. All routers are properly configured with default configurations and are running the OSPF routing protocol. The network is fully converged. A host on the 192.168.3.0/24 network is communicating with a host on the 192.168.2.0/24 network.Which path will be used to transmit the data?The data will be transmitted via R3-R2.The data will be transmitted via R3-R1-R2.The traffic will be load-balanced between two paths —one via R3-R2, and the other via R3-R1-R2.The data will be transmitted via R3-R2, and the other path via R3-R1-R2 will be retained as the backup path.8Refer to the exhibit. A network administrator adds this command to router R1: ip route 192.168.2.0 255.255.255.0 S0/0/0. What is the result of adding this command?This route is automatically propagated throughout the network.The traffic for network 172.16.1.0 is forwarded to network 192.168.2.0.A static route is established.The traffic for all Class C networks is forwarded to 172.16.1.2.9 Which two situations require the use of a link-state protocol? (Choose two.)Fast convergence of the network is critical.The network is very large.The network administrator has limited knowledge to configure and troubleshoot routing protocols.The network is a flat network.The capacity of the router is low.10 What are two ways that a router can learn of the paths to destination networks? (Choose two.) updates from other routersDHCP information broadcastsmanual configuration of routesARP requests from connected routersinspection of the destination IP address in data packetsupdates from the SMTP management information base11Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the value that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.12 Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.13 When presented with multiple valid routes to a destination, what criteria does a router use to determine which routes to add to the routing table?The router selects the routes with the best metric. All routes that have the same best metric are added to the routing table.The router first selects routes with the lowest administrative distance. The resulting routes are then prioritized by metric and the routes with the best metric are added to the routing table.The router selects the routes with the lowest administrative distance. All routes with the same lowest administrative distance are added to the routing table.The router installs all routes in the routing table but uses the route with the best metric most when load balancing.14Refer to the exhibit. What are two of the routes added to the routing table of R1? (Choose two.) R 172.16.1.0/24 [120/1] via 192.168.3.0, 00:00:24, Serial0/0/0R 192.168.1.0/24 [120/1] via 172.16.2.1, 00:00:24, Serial0/0/1R 192.168.9.0/24 [120/1] via 172.16.1.2, 00:00:24, Serial0/0/0R 192.168.100.0/24 [120/1] via 172.16.1.1, 00:00:24, Serial0/0/0R 192.168.2.0/24 [120/1] via 172.16.1.2, 00:00:24, Serial0/0/015Refer to the exhibit. Two remote sites are connected to the HQ router. The router New is configured using RIPv2 and the router BR1 is configured using EIGRP. If HQ is configured with RIPv2 and EIGRP, how will the 172.16.10.0/24 network be added to the routing table of HQ after the network converges?with two paths of the same cost to the 172.16.10.0/24 networkwith one path to the 172.16.10.0/24 network via router BR1with one path to the 172.16.10.0/24 network via router NEWwith two paths of different cost to the 172.16.10.0/24 network16Refer to the exhibit. A device is required to complete the connection between router R1 and the WAN. Which two devices can be used for this? (Choose two.)a CSU/DSU devicea modeman Ethernet switcha huba bridge17Refer to the exhibit. Which two components are required to complete the configuration? (Choose two.)a crossover cablea DCE devicea DTE devicea modema V.35 cable18Refer to the exhibit. Why is the state of the serial0/0/0 interface administratively down?An IP address has not been configured on the interface.The WIC was installed into the incorrect slot on the router.The default encapsulation on the interface has been modified.The no shutdown command has not been executed on the interface.19 A network administrator is setting up a new router with a device name of Admin, an encrypted password of cangetin, and the IP address 192.168.1.22/29 assigned to the first FastEthernet interface. Which command sequence correctly configures this router?Router(config)# hostname AdminAdmin(config)# enable secret cangetinAdmin(config)# interface fa0/1Admin(config-if)#ip address 192.168.1.22 255.255.255.248Router(config)# hostname AdminAdmin(config)# enable password cangetinAdmin(config)# interface fa0/1Admin(config-if)# ip address 192.168.1.22 255.255.255.248Router(config)# hostname AdminAdmin(config)# enable secret cangetinAdmin(config)# interface fa0/0Admin(config-if)# ip address 192.168.1.22 255.255.255.248Router(config)# hostname AdminAdmin(config)# enable password cangetinAdmin(config)# interface fa0/0Admin(config-if)# ip address 192.168.1.22 255.255.255.24820Refer to the exhibit. A network administrator is accessing router R1 from the console port. Once the administrator is connected to the router, which password should the administrator enter at the R1> prompt to access the privileged EXEC mode?Cisco001Cisco123Cisco789Cisco90121Refer to the exhibit. A PC is unable to communicate outside of the local network. A network technician views the host configuration and determines that the correct subnet mask but incorrect gateway was entered. What gateway IP address should be configured on the PC if the company policy requires that the IP address on a router interface is the highest in the subnet?192.168.1.46192.168.1.54192.168.1.62192.168.1.12622 An administrator is configuring Router1 so that it can connect to Router2 by using IP. Which protocol can be used by Router1 to determine the IP address of Router2 when they are directly connected and only Layer 2 connectivity exists between them?ARPCDPICMPTelnet23Refer to the exhibit. The output of the show ip route command for three routers on a network is displayed. All routers are operational, pings are not blocked on this network. Which two pings will fail? (Choose two.)from R1 to 10.3.3.1from R1 to 172.16.1.1from R1 to 192.168.3.1from R2 to 192.168.1.1from R2 to 192.168.3.124 What is the advantage of configuring a static route with an exit interface instead of a next-hop address?The router will perform a recursive lookup.This route will automatically be used as the gateway of last resort.The exit interface configuration consumes less router processing time.The exit interface configuration has an administrative distance value of 1.25 In which situation would a default static route be recommended?when connecting an edge router to the Internetwhen variable length subnet masking is in effectwhen there is more than one valid route for a destination networkwhen a destination network has a larger mask than any routes in the routing table26Refer to the exhibit. How was the OSPF default gateway entry for R2 determined?Default routes are automatically injected by OSPF into all advertisements.A static default gateway route is defined in the configuration of R2.The default-information originate command is applied on R1.The ISP defines the gateway of last resort and automatically passes it to R1 and R2.The ip default-gateway command is applied on R2.27 The command ip route 192.168.2.0 255.255.255.0 172.16.2.2 was entered into the router. After network changes were made, the new next hop for the 192.168.2.0/24 network is 172.16.5.1. What should an administrator do so that the router will use the new next hop to reach the 192.168.2.0 network?Enter the command clear ip route *.Lower the administrative distance for the new path to ensure that it is used first.Negate the original command and enter a new static route with the new next hop.Nothing. The router will learn of the new next hop and automatically update the route table.28Refer to the exhibit. The users on the local network 172.16.1.0/24 complain that they are unable to connect to the Internet. What step should be taken to remedy the problem?A new static route must be configured on R1 with the R3 serial interface as the next hop.A new default route must be configured on R1 with the R3 serial interface as the next hop.The default route on R2 should be configured with the R3 serial interface as the next hop.The default route on R2 must be replaced with a new static route and the next hop should be the R1 FastEthernet interface.29Refer to the exhibit. Based on the output, what can be concluded about the routes on router R1 ?Only one static route is configured on R1.Network 172.16.4.0 is directly connected to R1.Static routing is configured using the exit interface option.R1 is configured with three static routes to the three subnets of the 172.16.0.0/24 network.30Refer to the exhibit. The entire 192.168.1.0 network has been allocated to address hosts in the diagram. Utilizing VLSM with contiguous address blocks, which set of addresses and prefixes could be used to create an addressing solution with a minimum waste of IP addresses?答案:D31Refer to the exhibit. Which combination of IP address and subnet mask can be used on the serial interface of Router2 in order to put the interface in the same network as the serial interface of Router1?IP 172.16.0.18, subnet mask 255.255.255.0IP 172.16.32.15, subnet mask 255.255.255.240IP 172.16.0.18, subnet mask 255.255.255.252IP 172.16.32.18, subnet mask 255.255.255.25232Refer to the exhibit. The LANs on routers R1, R2, and R3 must be configured to use the 192.168.1.0 network space. If VLSM is used and contiguous blocks of addresses are assigned, which network number and prefix value would be associated with interface Fa0/0 on router R2?192.168.1.32/28192.168.1.80/27192.168.1.96/28192.168.1.120/29192.168.1.128/2933Refer to the exhibit. The networks that are connected to R1 have been summarized for R2 as192.168.136.0/21. Which packet destination address will R2 forward to R1?192.168.135.1192.168.142.1192.168.144.1192.168.128.134Refer to the exhibit. A new PC was deployed in the Sales network. It was given the host address of 192.168.10.31 with a default gateway of 192.168.10.17. The PC is not communicating with the network properly. What is the cause?The default gateway is incorrect.The address is in the wrong subnet.The host address and default gateway are swapped.192.168.10.31 is the broadcast address for this subnet.35Refer to the exhibit. The network is running the RIP routing protocol. Network 10.0.0.0 goes down. Which statement is true regarding how the routers in this topology will respond to this event?Router4 will learn about the failed route 30 seconds later in the next periodic update.Split horizon will prevent Router4 from fowarding packets to the 10.0.0.0 network until the holddown timer expires.Router5 immediately flushes the unreachable route from its routing table.Router5 will send Router4 a triggered update with a metric of 16 for network 10.0.0.0.36Refer to the exhibit. The 10.4.0.0 network fails. What mechanism prevents R2 from receiving false update information regarding the 10.4.0.0 network?split horizonhold-down timersroute poisoningtriggered updates37 Which feature of RIPv2 enables it to function as a classless routing protocol?Subnet masks are included in routing updates.Routing updates are triggered by topology changes.Next-hop addresses are included in routing updates.Multicast addresses are used to send routing updates.38Refer to the exhibit. Both routers are using the RIPv2 routing protocol and static routes are undefined. R1 can ping 192.168.2.1 and 10.1.1.2, but is unable to ping 192.168.4.1.What is the reason for the ping failure?The serial interface between two routers is down.R2 is not forwarding the routing updates.The 192.168.4.0 network is not included in the RIP configuration of R2.RIPv1 needs to be configured.39Refer to the exhibit. The network is configured with RIPv2. However, network administrators notice that communication cannot be successfully completed from one LAN to another. A network administrator issues the show ip route command on the HQ router. Based on the output, what should be done to correct the problem?Disable the load balancing feature of RIPv2.Issue the no auto-summary command for RIPv2.Replace RIPv2 with EIGRP which supports VLSM.Make sure that the network statements include the correct subnet mask.40 A network administrator is using an application that is monitoring packets on the network and sees an EIGRP update packet. What is the purpose of the update packet?The packet is sent to discover neighbors within the EIGRP network.The packet is sent to search for network devices within an EIGRP network.The packet is used to propagate routing information within the EIGRP network.The packet is used to send an unreachable reply to another router within the EIGRP network. The packet is used to notify all routers that EIRGP has failed on one of the routers within the EIGRP network.41 Which protocol is used by EIGRP to deliver and receive update packets?FTPRTPTCPTFTPUDP42Refer to the exhibit. Which two interface variables will determine the metric that is used on EIGRP routes? (Choose two.)loaddelayreliabilityhop countbandwidth43Refer to the exhibit. What information can be determined from the displayed output?EIGRP packets are waiting to be sent to the neighbors.The adjacencies between the routers are yet to be established.The IP address 192.168.10.10 is configured at serial interface S0/0/1 of router R2.Router R2 is receiving hello packets from a neighbor with the IP address 192.168.10.10 via the R2 S0/0/1 interface.44Refer to the exhibit. What will happen if interface Serial0/0/1 goes down on Router1?The Dijkstra algorithm will calculate the feasible successor.DUAL will query neighbors for a route to network 192.168.1.0.Neighbor 172.16.3.2 will be promoted to the feasible successor.Traffic destined to the 192.168.1.0 network will be dropped immediately due to lack of a feasible successor.45Refer to the exhibit. A network designer is testing a prototype of WAN connections. All of the routers in the exhibit are configured for OSPF routing. The design requires that the path between routers A and D through ISP-A is the primary and the path through ISP-B servers as a backup. Thedesigner notices that router A has two equal-cost paths to the LAN on router D. How can the designer correct this problem?Issue a clock rate 2000000 interface command on S0/0/1 of router ISP-B.Change the default OSPF reference bandwidth on router A.Configure two static routes with administrative distances of 10.Use the bandwidth command to change the default bandwidth on the link to router B.46Refer to the exhibit. R1 and R2 are unable to establish an adjacency. What two configuration changes will correct the problem? (Choose two.)Set a lower priority on R2.Configure the routers in the same area.Set a lower cost on R2 compared to R1.Add a backup designated router to the network.Match the hello and dead timers on both routers.47 All routers in a network are configured in a single OSPF area with the same priority value. No loopback interface has been set on any of the routers. Which secondary value will the routers use to determine the router ID?The highest MAC address among the active interfaces of the network will be used.There will be no router ID until a loopback interface is configured.The highest IP address among the active FastEthernet interfaces that are running OSPF will be used.The highest IP address among the active interfaces will be used.48Refer to the exhibit. All the routers boot at the same time and enter the OSPF election process. Which router will be elected as the BDR?router Arouter Brouter Crouter Dboth A and D49Refer to the exhibit. R1 is configured properly for a single area OSPF, and R2 has been recently installed in the network. Which set of commands is required to configure a single area OSPF for the networks that are connected to R2?R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.1.1.0 0.0.0.3 area 0R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config)# router ospf 2R2(config-router)# network 10.1.1.0 0.0.0.3 area 0R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.1.1.0 0.0.0.3 area 1R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.0.0.0 0.0.0.3 area 150Refer to the exhibit. A network administrator has configured OSPF using the following command: network 192.168.1.32 0.0.0.31 area 0Which router interface will participate in OSPF?FastEthernet0/0FastEthernet0/1Serial0/0/0Serial0/0/1。
ccna真题

C C N A测试真题1router1下面有120个PCrouter2下面有60个PCrouter3下面有28个PCrouter4下面有12个PC解决方案:根据题目的要求,进行子网划分router1router2router3router4直连地址:router0*router1:地址242/30router0*router2:246/30router0*router3:250/30router0*router4:254/30配置:Router0(config)#ints0/3/0Router0(config-if)#noshRouter0(config-if)#ipaddRouter0(config-if)#ints0/3/1Router0(config-if)#noshRouter0(config-if)#ipaddRouter0(config-if)#ints0/2/0Router0(config-if)#noshRouter0(config-if)#ipaddRouter0(config-if)#ints0/2/1Router0(config-if)#noshRouter0(config-if)#ipaddRouter1(config)#intg0/0Router1(config-if)#noshRouter1(config-if)#ipaddRouter1(config-if)#ints0/3/0Router1(config-if)#noshRouter1(config-if)#ipaddRouter2(config)#intg0/0Router2(config-if)#noshRouter2(config-if)#ipaddRouter2(config)#ints0/3/0Router2(config-if)#noshRouter2(config-if)#ipaddRouter3(config)#intg0/0Router3(config-if)#noshRouter3(config-if)#ipaddRouter3(config-if)#ints0/3/0Router3(config-if)#noshRouter3(config-if)#ipaddRouter4(config-if)#intg0/0Router4(config-if)#ipaddRouter4(config-if)#noshRouter4(config-if)#ints0/3/0Router4(config-if)#ipaddRouter4(config-if)#nosh配置rip路由,在这5个路由器上都去宣告RIP路由,routerripversion2networknoauto-summary保证网络能进行畅通接下来在router0上配置DHCP服务器Router0(config)#ipdhcppoolrouter1Router0(dhcp-config)#networkRouter0(dhcp-config)#default-routerRouter0(dhcp-config)#dns-serverRouter0(dhcp-config)#exRouter0(config)#ipdhcpexcluded-addressRouter0(config)#ipdhcppoolrouter2Router0(dhcp-config)#networkRouter0(dhcp-config)#default-routerRouter0(dhcp-config)#dns-serverRouter0(dhcp-config)#exRouter0(config)#ipdhcpexcluded-addressRouter0(config)#ipdhcpexcluded-addressSwitch6(config)#intfa0/1 Switch6(config-if)#swmotrSwitch6(config-if)#intfa0/2Switch6(config-if)#swmotrSwitch6(config-if)#exSwitch6(config)#vtpdomainCCIESwitch7(config)#vtpmodeclientSwitch7(config)#intfa0/1Switch7(config-if)#swmotrSwitch7(config-if)#intfa0/2Switch7(config-if)#swmotrSwitch7(config-if)#vtpdomainCCIE配置完成后,在Switch6和Switch7上能看到VLAN同步Switch6(config)#intfa0/3Switch6(config-if)#swmoacSwitch6(config-if)#swacv5Switch6(config-if)#intfa0/4Switch6(config-if)#swmoacSwitch6(config-if)#swacv6Switch7(config)#intfa0/3Switch7(config-if)#swmoacSwitch7(config-if)#swacv5Switch7(config-if)#intfa0/4Switch7(config-if)#swmoacSwitch7(config-if)#swacv6Router7(config)#intfa0/0Router7(config-if)#noshRouter7(config-if)#exRouter7(config)#intfa0/Router7(config-subif)#end5Router7(config-subif)#ipaddRouter7(config-subif)#intfa0/Router7(config-subif)#end6Router7(config-subif)#ipaddRouter7(config-subif)#exRouter7(config)#ipdhcppoolvlan5Router7(dhcp-config)#netRouter7(dhcp-config)#defRouter7(dhcp-config)#dnsRouter7(dhcp-config)#exRouter7(config)#ipdhcppoolvlan6Router7(dhcp-config)#netwoRouter7(dhcp-config)#defRouter7(dhcp-config)#dnsRouter7(config)#ipdhcpexRouter7(config)#ipdhcpexRouter7(config)#intfa0/1Router7(config-if)#noshRouter7(config-if)#ipaddRouter7(config-if)#iprouteRouter7(config)#intfa0/1Router7(config-if)#ipnatoutsideRouter7(config-if)#intfa0/Router7(config-subif)#ipnatinsideRouter7(config-subif)#intfa0/Router7(config-subif)#ipnatinsideRouter7(config-subif)#exRouter7(config)#access-list1permitRouter7(config)#access-list1permitRouter7(config)#ipnatinsidesourcelist1interfacefa0/1overloadRouter7(config)#iproute20设置管理距离为20,默认是0,越小是越优先Router0(config)#ints0/1/0Router0(config-if)#ipnatinsideRouter0(config-if)#exRouter0(config)#access-list1permitRouter0(config)#access-list1permit13Router7(config)#intfa0/Router7(config-subif)#encapsulationdot1Q99Router7(config-subif)#ipaddSwitch8(config)#vlan99Switch8(config-vlan)#exSwitch8(config)#intvlan99Switch8(config-if)#ipaddSwitch8(config-if)#exSwitch8(config)#ipdefault-gatewaySwitch8(config)#linevty04Switch8(config-line)#passwordciscoSwitch8(config-line)#exiSwitch8(config)#enablepasswordciscoSwitch6(config-if)#intvlan99Switch6(config-if)#ipaddSwitch6(config-if)#exSwitch6(config)#ipdefault-gatewaySwitch6(config)#linevty04Switch6(config-line)#loginlocalSwitch6(config-line)#exiSwitch6(config)#enablepasswordciscoSwitch6(config)#usernamecciepasswordwanheSwitch7(config-if)#intvlan99Switch7(config-if)#ipaddSwitch7(config-if)#exSwitch7(config)#ipdefault-gatewaySwitch7(config)#linevty04Switch7(config-line)#nologin不需要密码Switch7(config-line)#privilegelevel15直接给最高权限14Router0(config)#access-list101denyicmphostechoRouter0(config)#access-list101denyicmphostecho Router0(config)#access-list101denytcphosteq80 Router0(config)#access-list101denytcphosteq80 Router0(config)#access-list101permitipanyany Router0(config)#ints0/1/0Router0(config-if)#ipaccess-group101in。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1.What two advantages does CIDR provide to a network? (Choose two.)reduced routing table sizedynamic address assignmentautomatic route redistributionreduced routing update trafficautomatic summarization at classful boundaries2.Refer to the exhibit. The network administrator wants to create a subnet for the point-to-point connection between the two routers. Which subnetwork mask would provide enough addresses for the point-to-point link with the least number of wasted addresses?255.255.255.192255.255.255.224255.255.255.240255.255.255.248255.255.255.2523.Refer to the exhibit. A network engineer is summarizing the two groups of routes on router R1 shown in the exhibit. Which summarization will work for all the subnets?192.168.0.0/23192.168.0.0/22192.168.0.0/21192.168.0.0/204. Which of the following are contained in the routing updates of classless routing protocols? (Choose two.)32-bit addressnext hop router interfacesubnet maskunicast host addressLayer 2 address5. Which of the following problems does VLSM help to alleviate(缓解,减轻)?the shortage of IP addressesthe difficulty of assigning static IP addresses to hosts in large enterprisesthe complexity of implementing advanced routing protocols such as OSPF and EIGRPthe shortage of network administrators qualified in the use of RIP v1 and IGRP6. What does VLSM allow a network administrator to do?utilize one subnet mask throughout an autonomous systemutilize multiple subnet masks in the same IP address spaceutilize IGRP as the routing protocol in an entire autonomous systemutilize multiple routing protocols within an autonomous system7.Refer to the exhibit. What subnet mask will be applied if Router A sends a RIPv1 update for the network 172.16.1.0 to Router B?none816248.Refer to the exhibit. The network administrator wants to minimize the number of entries in Router1’s routing table. What should the ad ministrator implement on the network?VLSMCIDRprivate IP addressesclassful routing9. A router has a summary route to network 192.168.32.0/20 installed in its routing table. What range of networks are summarized by this route?192.168.0.0 – 192.168.32.0/24192.168.0.0 – 192.168.47.0/24192.168.32.0 – 192.168.47.0/24192.168.32.0 – 192.168.48.0/24192.168.32.0 – 192.168.63.0/2410. A network administrator is tasked with dividing up a class C network among the QA, Sales, and Administration departments. The QA department is made up of 10 people, the Sales is made up of 28 people, and the Administration has 6. Which two subnets masks adequately address the QA and Sales departments? (Choose two.)255.255.255.252 for QA255.255.255.224 for Sales255.255.255.240 for QA255.255.255.248 for QA255.255.255.0 for Sales11.In the network shown in the graphic, three bits were borrowed from the host portion of a Class C address. How many valid host addresses will be unused on the three point-to-point links combined if VLSM is not used?3412368418012.A Class C address has been assigned for use in the network shown in the graphic. Using VLSM, which bit mask should be used to provide for the number of host addresses required on Router A, while wasting the fewest addresses?/31/30/29/28/27/2613.An additional subnet is required for a new Ethernet link between Router1 and Router2 as shown in the diagram. Which of the following subnet addresses can be configured in this network to provide a maximum of 14 useable addresses for this link while wasting the fewest addresses?192.1.1.16/26192.1.1.96/28192.1.1.160/28192.1.1.196/27192.1.1.224/28192.1.1.240/2814. Which three interior routing protocols support VLSM? (Choose three.)OSPFRIP v1RIP v2EIGRPBGPSTP15.Refer to the exhibit. The number of required host addresses for each subnet in a network is listed in the exhibit. This number includes the host address requirements for all router ports and hosts on that subnet. After all device and router port address assignments are determined, what will be the total number of unused host addresses available?6142934406216.Refer to the exhibit. In the network that is shown, the router interfaces are assigned the first address in each subnet. Which IP address would be usable for a host on one of the LANs in this network?192.168.1.5/30192.168.2.17/28192.168.2.63/27192.168.2.130/2517.Refer to the exhibit. Which address is a broadcast address for one of the subnets that are shown in the exhibit?192.168.4.3/29192.168.4.15/29192.168.4.65/26192.168.4.255/2418.Refer to the exhibit. A network administrator needs to create two subnetworks from 10.0.0.0/8 for a router running RIPv2. The Admin subnet requires 120 hosts and the Sales subnet requires 58 hosts. The network administrator assigned 10.0.1.128/25 to the Admin subnet. The Sales subnet is given 10.0.1.192/26. What will be the result of this addressing scheme?Because RIPv2 does not support VLSM, the subnet masks will not be allowed.The subnets will not have enough host addresses for the given network requirements.The subnets overlap and will be rejected by the router.The router will support the addressing scheme.19.Refer to the exhibit. A network technician enters the static route in R1 needed to reach network 10.1.1.0/24. A ping from the S0/0/0 interface on R1 to host B fails. The technician begins testing the network and has the following results:1. pings from R1 to the S0/0/0 interface on R2....successful2. pings from R1 to the Fa0/0 interface on R2....successful3. pings from host B to hosts on the 10.1.1.0/24 network....successful4. pings from host B to the Fa0/0 interface on R2....successful5. pings from R2 to host B....successful.What is the likely cause of the failure of the ping from R1 to host B?The default gateway on host B is not correctly set.There are no routes back to networks connected to R1 from R2.There is a Layer 2 problem between R2 and host B.Host B has a defective Ethernet card.20. What is a supernet?the network for a default routea summarization of classful addressesa network that contains both private and public addressesa set of discontiguous networks that are controlled by an ISP。
