3600配置实例
H3C3600配置文档

ospf 1 创建本地交换机的第一个OSPF area 0.0.0.2 OSPF的域设为全网统一规划的域中 network 11.176.77.0 0.0.0.255 将11.176.77.0的子网通过OSPF进行发布 network 11.176.107.204 0.0.0.3 将11.176.107.204的子网通过OSPF进行发布 network 11.176.107.208 0.0.0.3 将11.176.107.208的子网通过OSPF进行发布 FTP server enable
4、 命令行配置 sysname H3C (定义系统名称为h3c) local-user admin password simple admin service-type telnet terminal level 3 (创建一个用户名和密码都为admin的帐户,用来进行远程登录 服务,级别为3级,也就是最高级别,可以对交换机进行任何操作) local-user wj2s password simple wj2s level 3 service-type ftp (创建一个用户名和密码都为wj2s的帐户,用来进行FTP登录服 务,级别为3级,也就是最高级别,可以对交换机进行任何关于 FTP的操作)
H3C3600交换机配置
1、计算机的串口与交换机CONSOLE口进行连接
H3C3600的配置线与思科、港湾通用
2、使用超级终端进行设置
相关参数设置为: 1、名称设为任意即可; 2、端口设置每秒位数为9600; 3、数据位为8; 4、奇偶校验为无; 5、停止位为1; 6、数据流控制为无; 或直接还原为默认值即可。
3、命令行配置 1、出现username时输入用户名 admin,出现password时输入密码 admin 注:初始的用户名和密码都是admin 2、用户名和密码输入正确后进入交换机 用户配置界面<h3c>,该界面只能显示一般 配置信息,无法进行业务配置 3、在用户配置界面输入system-view, 进入系统配置界面[h3c],在该界面下可对 VLAN、IP及路由进行设置
H3C3600交换机配置及说明文档--38-信息中心命令

i
H3C S3600 系列以太网交换机 命令手册-Release 1510 信息中心
第 1 章 信息中心配置命令
第1章 信息中心配置命令
1.1 信息中心配置命令
1.1.1 display channel
【命令】 display channel [ channel-number | channel-name ]
H3C S3600 系列以太网交换机 命令手册-Release 1510 信息中心
目录
目录
第 1 章 信息中心配置命令 .......................................................................................................1-1
【举例】
# 查看当前系统中的信息中心工作状态、各信息输出通道的配置、时间戳格式以及 在 IRF 系统中的信息输出情况。
<H3C> display info-center Information Center: enabled Log host:
the interface name of the source address : Vlan-interface1 192.168.0.2, channel number : 2, channel name : loghost language : english, host facility local : 7 Console: channel number : 0, channel name : console Monitor: channel number : 1, channel name : monitor SNMP Agent: channel number : 5, channel name : snmpagent Log buffer: enabled,max buffer size : 1024, current buffer size : 512, current messages : 512, channel number : 4, channel name : logbuffer dropped messages : 0, overwrote messages : 586 Trap buffer: enabled,max buffer size : 1024, current buffer size : 256, current messages : 5, channel number : 3, channel name : trapbuffer dropped messages : 0, overwrote messages : 0 Information timestamp setting: log - date, trap - date, debug - boot
H3C3600交换机配置及说明文档--12-端口安全-端口绑定命令

1-1
H3C S3600 系列以太网交换机 命令手册-Release 1510 端口安全-端口绑定
第 1 章 端口安全命令
Байду номын сангаас
【视图】 任意视图
【参数】
interface-list:以太网端口列表,表示多个以太网端口,表示方式为 interface-list= { interface-type interface-number [ to interface-type interface-number ] } & <1-10>。 其中,interface-type 为端口类型,interface-number 为端口编号。& <1-10>表示前 面的参数最多可以输入 10 次。
【举例】 # 显示全局和所有端口的端口安全配置信息。
<H3C> display port-security Equipment port-security is enabled AddressLearn trap is Enabled Intrusion trap is Enabled Dot1x logon trap is Enabled Dot1x logoff trap is Enabled Dot1x logfailure trap is Enabled RALM logon trap is Enabled RALM logoff trap is Enabled RALM logfailure trap is Enabled Vlan id assigned is NULL Disableport Timeout: 20 s OUI value: Index is 5, OUI value is 00efec Ethernet1/0/1 is link-down Port mode is Userlogin NeedtoKnow mode is needtoknowonly Intrusion mode is disableport Max mac-address num is 100
H3C3600交换机配置及说明文档--27-Web Cache重定向命令

webcache MAC address: 000f-e20f-0000 webcache port: Ethernet1/0/1 webcache VLAN: 1 webcache TCP port: 80 webcache redirect VLAN:
1.1.3 webcache redirect-vlan
【命令】 webcache redirect-vlan vlan-id undo webcache redirect-vlan [ vlan-id ]
【视图】 系统视图
【参数】 vlan-id:参与 Web Cache 重定向的报文的 VLAN ID。
2. 以太网端口视图下的命令形式 webcache address ip-address mac mac-address vlan vlan-id [ tcpport tcpport-number ]
【视图】 系统视图/以太网端口视图
【参数】 ip-address:Web Cache 的 IP 地址。 mac-address:Web Cache 的 MAC 地址。 vlan-id:Web Cache 的所属 VLAN 的 ID。 port interface-type interface-number:交换机和 Web Cache 相连的端口。 tcpport tcpport-number:HTTP 使用的 TCP 端口号,缺省值为 80。
<H3C> system-view System View: return to User View with Ctrl+Z. [H3C] interface Ethernet 1/0/4 [H3C-Ethernet1/0/4] webcache address 1.1.1.1 mac 000f-e20f-0101 vlan 40
H3C3600交换机配置及说明文档--07-Voice VLAN命令

Voice VLAN 目录目录第1章 Voice VLAN配置命令..................................................................................................1-11.1 Voice VLAN配置命令.........................................................................................................1-11.1.1 display voice vlan error-info....................................................................................1-11.1.2 display voice vlan oui..............................................................................................1-11.1.3 display voice vlan status.........................................................................................1-21.1.4 display vlan..............................................................................................................1-31.1.5 voice vlan................................................................................................................1-41.1.6 voice vlan aging.......................................................................................................1-51.1.7 voice vlan enable....................................................................................................1-51.1.8 voice vlan mac-address..........................................................................................1-61.1.9 voice vlan mode......................................................................................................1-71.1.10 voice vlan security enable.....................................................................................1-8第1章 Voice VLAN配置命令1.1 Voice VLAN配置命令1.1.1 display voice vlan error-info【命令】display voice vlan error-info【视图】任意视图【参数】无【描述】display voice vlan error-info命令用来显示使能Voice VLAN特性失败的端口。
51CTO下载-华为三层交换机3600配置实例
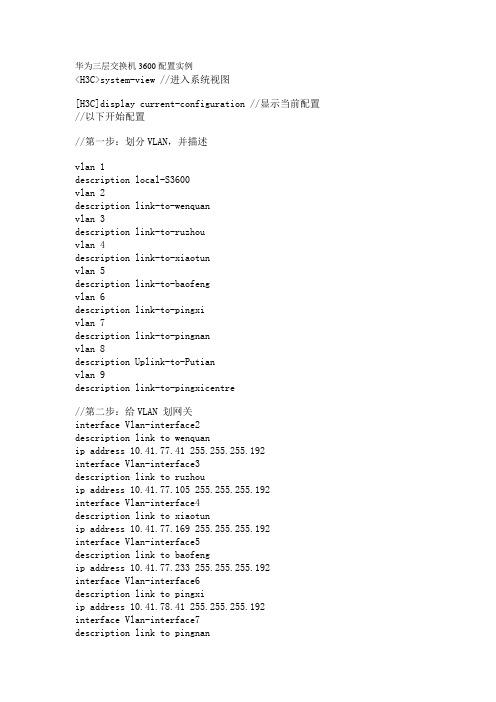
华为三层交换机3600配置实例<H3C>system-view //进入系统视图[H3C]display current-configuration //显示当前配置//以下开始配置//第一步:划分VLAN,并描述vlan 1description local-S3600vlan 2description link-to-wenquanvlan 3description link-to-ruzhouvlan 4description link-to-xiaotunvlan 5description link-to-baofengvlan 6description link-to-pingxivlan 7description link-to-pingnanvlan 8description Uplink-to-Putianvlan 9description link-to-pingxicentre//第二步:给VLAN 划网关interface Vlan-interface2description link to wenquanip address 10.41.77.41 255.255.255.192interface Vlan-interface3description link to ruzhouip address 10.41.77.105 255.255.255.192interface Vlan-interface4description link to xiaotunip address 10.41.77.169 255.255.255.192interface Vlan-interface5description link to baofengip address 10.41.77.233 255.255.255.192interface Vlan-interface6description link to pingxiip address 10.41.78.41 255.255.255.192interface Vlan-interface7description link to pingnanip address 10.41.78.105 255.255.255.192 interface Vlan-interface8description uplink to putianip address 10.41.244.102 255.255.255.252 interface Vlan-interface9description link to pingxicentreip address 10.41.80.233 255.255.255.192//第三步:给VLAN 指定端口interface Ethernet1/0/2description link to wenquanport access vlan 2interface Ethernet1/0/3description link to ruzhouport access vlan 3interface Ethernet1/0/4description link to xiaotunport access vlan 4interface Ethernet1/0/5description link to baofengport access vlan 5interface Ethernet1/0/6description link to pingxiport access vlan 6interface Ethernet1/0/7description link to pingnanport access vlan 7interface Ethernet1/0/8description uplink to putianport access vlan 8interface Ethernet1/0/9 to Ethernet1/0/24 description link to pingxicentreport access vlan 9//第四步:配置路由协议//(1)用RIP配动态路由ripnetwork 10.41.77.41network 10.41.77.105network 10.41.77.169network 10.41.77.233network 10.41.78.41network 10.41.78.105network 10.41.80.233network 10.41.244.102//(2)配静态路由(只用对远端设备配一条路由即可,本地自通)---推荐用此协议ip route 0.0.0.0 0.0.0.0 10.41.244.101Quidway>sys[Quidway]vlan 2[Quidway-vlan2]port e1/0/2[Quidway-vlan2]int vlan 2[Quidway-Vlan-interface2]ip add 10.41.77.41 255.255.255.192 [Quidway-Vlan-interface2]vlan 3[Quidway-vlan3]port e1/0/3[Quidway-vlan3]int vlan 3[Quidway-Vlan-interface3]ip add 10.41.77.105 255.255.255.192 [Quidway-Vlan-interface3]vlan 4[Quidway-vlan4]port e1/0/4[Quidway-vlan4]int vlan 4[Quidway-Vlan-interface4]ip add 10.41.77.169 255.255.255.192 [Quidway-Vlan-interface4]vlan 5[Quidway-vlan5]port e1/0/5[Quidway-vlan5]int vlan 5[Quidway-Vlan-interface5]ip add 10.41.77.233 255.255.255.192 [Quidway-Vlan-interface5]vlan 6[Quidway-vlan6]port e1/0/6[Quidway-vlan6]int vlan 6[Quidway-Vlan-interface6]ip add 10.41.78.41 255.255.255.192 [Quidway-Vlan-interface6]vlan 7[Quidway-vlan7]port e1/0/7[Quidway-vlan7]int vlan 7[Quidway-Vlan-interface7]ip add 10.41.78.105 255.255.255.192 [Quidway-Vlan-interface7]vlan 8[Quidway-vlan8]port e1/0/8[Quidway-vlan8]int vlan 8[Quidway-Vlan-interface8]ip add 10.41.244.102 255.255.255.252 [Quidway-Vlan-interface8]vlan 9[Quidway-vlan9]port e1/0/9 to e1/0/24[Quidway-vlan9]int vlan 9[Quidway-Vlan-interface9]ip add 10.41.80.233 255.255.255.192 //配置路由ip route 0.0.0.0 0.0.0.0 10.41.244.101。
H3C3600详细配置及说明

sysname H3C#super password level 3 simple zyg1949101 设置串口连接的密码#radius scheme system#domain system 说明性文字#local-user 123password simple zyg1949101service-type telnetlevel 3local-user zygpassword simple zyg1949101service-type telnetlevel 3 建立web账户密码和权限#acl number 3001rule 0 permit tcp source 192.168.50.0 0.0.0.255 destination 192.168.1.0 0.0.0.255rule 1 permit tcp source 192.168.50.0 0.0.0.255 destination 192.168.2.0 0.0.0.255rule 2 permit tcp source 192.168.50.0 0.0.0.255 destination 192.168.10.0 0.0.0.255rule 3 permit tcp source 192.168.80.0 0.0.0.255 destination 192.168.1.0 0.0.0.255rule 4 permit tcp source 192.168.80.0 0.0.0.255 destination 192.168.2.0 0.0.0.255rule 5 permit tcp source 192.168.80.0 0.0.0.255 destination 192.168.10.0 0.0.0.255rule 6 permit tcp source 192.168.130.0 0.0.0.255 destination 192.168.1.0 0.0.0.255rule 7 permit tcp source 192.168.130.0 0.0.0.255 destination 192.168.2.0 0.0.0.255rule 8 permit tcp source 192.168.130.0 0.0.0.255 destination 192.168.10.0 0.0.0.255rule 9 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.20.0 0.0.0.255rule 10 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.30.0 0.0.0.255rule 11 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.40.0 0.0.0.255rule 12 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.50.0 0.0.0.255rule 13 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.60.0 0.0.0.255rule 14 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.70.0 0.0.0.255rule 15 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.80.0 0.0.0.255rule 16 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.130.0 0.0.0.255rule 17 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.20.0 0.0.0.255rule 18 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.30.0 0.0.0.255rule 19 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.40.0 0.0.0.255rule 20 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.50.0 0.0.0.255rule 21 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.60.0 0.0.0.255rule 22 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.70.0 0.0.0.255rule 23 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.80.0 0.0.0.255rule 24 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.90.0 0.0.0.255rule 25 deny tcp source 192.168.80.0 0.0.0.255 destination 192.168.130.0 0.0.0.255rule 26 deny tcp source 192.168.50.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 27 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 28 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 29 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 30 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.50.0 0.0.0.255 rule 31 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 32 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 33 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 34 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.90.0 0.0.0.255 rule 35 deny tcp source 192.168.130.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 acl number 3002rule 0 permit tcp source 192.168.90.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 1 permit tcp source 192.168.90.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 rule 2 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 rule 3 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.10.0 0.0.0.255 rule 4 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 rule 5 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 rule 6 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.50.0 0.0.0.255 rule 7 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.60.0 0.0.0.255 rule 8 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.70.0 0.0.0.255 rule 9 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 rule 10 deny tcp source 192.168.90.0 0.0.0.255 destination 192.168.130.0 0.0.0.255 建立高级访问控制列表定义子规则#vlan 1description flieserver#vlan 2description Fanghuoqiang#vlan 10description FuWUQi#vlan 20description CaiWu#vlan 30description WaiMaoKe#vlan 40description DaBanGongShi#vlan 50description JiShuBu#vlan 60description CheJian#vlan 70description HuaYi#vlan 80description ZongCai---- More ----#vlan 90description webserver#vlan 130description WuXian vlan连接区域说明#interface Vlan-interface1ip address 192.168.1.1 255.255.255.0#interface Vlan-interface2ip address 192.168.2.2 255.255.255.0#interface Vlan-interface10ip address 192.168.10.1 255.255.255.0#interface Vlan-interface20ip address 192.168.20.1 255.255.255.0#interface Vlan-interface30ip address 192.168.30.1 255.255.255.0#interface Vlan-interface40ip address 192.168.40.1 255.255.255.0#interface Vlan-interface50ip address 192.168.50.1 255.255.255.0#interface Vlan-interface60ip address 192.168.60.1 255.255.255.0#interface Vlan-interface70ip address 192.168.70.1 255.255.255.0#ip address 192.168.80.1 255.255.255.0#interface Vlan-interface90ip address 192.168.90.1 255.255.255.0#interface Vlan-interface130ip address 192.168.130.1 255.255.255.0 配置vlan间路由#interface Aux1/0/0#interface Ethernet1/0/1 定义端口到vlanport access vlan 10#interface Ethernet1/0/2port access vlan 10#interface Ethernet1/0/3port access vlan 10line-rate inbound 2048#interface Ethernet1/0/4port access vlan 90packet-filter inbound ip-group 3002 rule 0 应用ACL规则到接口packet-filter inbound ip-group 3002 rule 1packet-filter inbound ip-group 3002 rule 2packet-filter inbound ip-group 3002 rule 3packet-filter inbound ip-group 3002 rule 4packet-filter inbound ip-group 3002 rule 5packet-filter inbound ip-group 3002 rule 6packet-filter inbound ip-group 3002 rule 7packet-filter inbound ip-group 3002 rule 8packet-filter inbound ip-group 3002 rule 9packet-filter inbound ip-group 3002 rule 10line-rate inbound 2048 限制出去的带宽为2048kbs#interface Ethernet1/0/5port access vlan 20#interface Ethernet1/0/6port access vlan 20#port access vlan 30#interface Ethernet1/0/8port access vlan 30#interface Ethernet1/0/9port access vlan 40line-rate inbound 1024#interface Ethernet1/0/10port access vlan 40line-rate inbound 1024#interface Ethernet1/0/11port access vlan 50packet-filter inbound ip-group 3001 rule 0 packet-filter inbound ip-group 3001 rule 1 packet-filter inbound ip-group 3001 rule 2 packet-filter inbound ip-group 3001 rule 3 packet-filter inbound ip-group 3001 rule 4 packet-filter inbound ip-group 3001 rule 5 packet-filter inbound ip-group 3001 rule 6 packet-filter inbound ip-group 3001 rule 7 packet-filter inbound ip-group 3001 rule 8 packet-filter inbound ip-group 3001 rule 9 packet-filter inbound ip-group 3001 rule 10 packet-filter inbound ip-group 3001 rule 11 packet-filter inbound ip-group 3001 rule 12 packet-filter inbound ip-group 3001 rule 13 packet-filter inbound ip-group 3001 rule 14 packet-filter inbound ip-group 3001 rule 15 packet-filter inbound ip-group 3001 rule 16 packet-filter inbound ip-group 3001 rule 17 packet-filter inbound ip-group 3001 rule 18 packet-filter inbound ip-group 3001 rule 19 packet-filter inbound ip-group 3001 rule 20 packet-filter inbound ip-group 3001 rule 21 packet-filter inbound ip-group 3001 rule 22 packet-filter inbound ip-group 3001 rule 23 packet-filter inbound ip-group 3001 rule 24 packet-filter inbound ip-group 3001 rule 25 packet-filter inbound ip-group 3001 rule 26 packet-filter inbound ip-group 3001 rule 27packet-filter inbound ip-group 3001 rule 29packet-filter inbound ip-group 3001 rule 30packet-filter inbound ip-group 3001 rule 31packet-filter inbound ip-group 3001 rule 32packet-filter inbound ip-group 3001 rule 33packet-filter inbound ip-group 3001 rule 34packet-filter inbound ip-group 3001 rule 35 应用ACL规则到接口line-rate inbound 1024 限制进来的带宽为1024kbs#interface Ethernet1/0/12port access vlan 50packet-filter inbound ip-group 3001 rule 0packet-filter inbound ip-group 3001 rule 1packet-filter inbound ip-group 3001 rule 2packet-filter inbound ip-group 3001 rule 3packet-filter inbound ip-group 3001 rule 4packet-filter inbound ip-group 3001 rule 5packet-filter inbound ip-group 3001 rule 6packet-filter inbound ip-group 3001 rule 7packet-filter inbound ip-group 3001 rule 8packet-filter inbound ip-group 3001 rule 9packet-filter inbound ip-group 3001 rule 10packet-filter inbound ip-group 3001 rule 11packet-filter inbound ip-group 3001 rule 12packet-filter inbound ip-group 3001 rule 13packet-filter inbound ip-group 3001 rule 14packet-filter inbound ip-group 3001 rule 15packet-filter inbound ip-group 3001 rule 16packet-filter inbound ip-group 3001 rule 17packet-filter inbound ip-group 3001 rule 18packet-filter inbound ip-group 3001 rule 19packet-filter inbound ip-group 3001 rule 20packet-filter inbound ip-group 3001 rule 21packet-filter inbound ip-group 3001 rule 22packet-filter inbound ip-group 3001 rule 23packet-filter inbound ip-group 3001 rule 24packet-filter inbound ip-group 3001 rule 25packet-filter inbound ip-group 3001 rule 26packet-filter inbound ip-group 3001 rule 27packet-filter inbound ip-group 3001 rule 28packet-filter inbound ip-group 3001 rule 29packet-filter inbound ip-group 3001 rule 30packet-filter inbound ip-group 3001 rule 31packet-filter inbound ip-group 3001 rule 33packet-filter inbound ip-group 3001 rule 34packet-filter inbound ip-group 3001 rule 35 应用ACL规则到接口line-rate inbound 1024 限制进来的带宽为1024kbs#interface Ethernet1/0/13port access vlan 60line-rate inbound 1024#interface Ethernet1/0/14port access vlan 60line-rate inbound 1024#interface Ethernet1/0/15port access vlan 70line-rate inbound 1024# 接口划入vlan并限速进入流量为1024kbs interface Ethernet1/0/16port access vlan 70line-rate inbound 1024#interface Ethernet1/0/17port access vlan 80packet-filter inbound ip-group 3001 rule 0packet-filter inbound ip-group 3001 rule 1packet-filter inbound ip-group 3001 rule 2packet-filter inbound ip-group 3001 rule 3packet-filter inbound ip-group 3001 rule 4packet-filter inbound ip-group 3001 rule 5packet-filter inbound ip-group 3001 rule 6packet-filter inbound ip-group 3001 rule 7packet-filter inbound ip-group 3001 rule 8packet-filter inbound ip-group 3001 rule 9packet-filter inbound ip-group 3001 rule 10packet-filter inbound ip-group 3001 rule 11packet-filter inbound ip-group 3001 rule 12packet-filter inbound ip-group 3001 rule 13packet-filter inbound ip-group 3001 rule 14packet-filter inbound ip-group 3001 rule 15packet-filter inbound ip-group 3001 rule 16packet-filter inbound ip-group 3001 rule 17packet-filter inbound ip-group 3001 rule 19 packet-filter inbound ip-group 3001 rule 20 packet-filter inbound ip-group 3001 rule 21 packet-filter inbound ip-group 3001 rule 22 packet-filter inbound ip-group 3001 rule 23 packet-filter inbound ip-group 3001 rule 24 packet-filter inbound ip-group 3001 rule 25 packet-filter inbound ip-group 3001 rule 26 packet-filter inbound ip-group 3001 rule 27 packet-filter inbound ip-group 3001 rule 28 packet-filter inbound ip-group 3001 rule 29 packet-filter inbound ip-group 3001 rule 30 packet-filter inbound ip-group 3001 rule 31 packet-filter inbound ip-group 3001 rule 32 packet-filter inbound ip-group 3001 rule 33 packet-filter inbound ip-group 3001 rule 34 packet-filter inbound ip-group 3001 rule 35line-rate inbound 1024#interface Ethernet1/0/18port access vlan 80packet-filter inbound ip-group 3001 rule 0 packet-filter inbound ip-group 3001 rule 1 packet-filter inbound ip-group 3001 rule 2 packet-filter inbound ip-group 3001 rule 3 packet-filter inbound ip-group 3001 rule 4 packet-filter inbound ip-group 3001 rule 5 packet-filter inbound ip-group 3001 rule 6 packet-filter inbound ip-group 3001 rule 7 packet-filter inbound ip-group 3001 rule 8 packet-filter inbound ip-group 3001 rule 9 packet-filter inbound ip-group 3001 rule 10 packet-filter inbound ip-group 3001 rule 11 packet-filter inbound ip-group 3001 rule 12 packet-filter inbound ip-group 3001 rule 13 packet-filter inbound ip-group 3001 rule 14 packet-filter inbound ip-group 3001 rule 15 packet-filter inbound ip-group 3001 rule 16 packet-filter inbound ip-group 3001 rule 17 packet-filter inbound ip-group 3001 rule 18 packet-filter inbound ip-group 3001 rule 19 packet-filter inbound ip-group 3001 rule 20packet-filter inbound ip-group 3001 rule 22 packet-filter inbound ip-group 3001 rule 23 packet-filter inbound ip-group 3001 rule 24 packet-filter inbound ip-group 3001 rule 25 packet-filter inbound ip-group 3001 rule 26 packet-filter inbound ip-group 3001 rule 27 packet-filter inbound ip-group 3001 rule 28 packet-filter inbound ip-group 3001 rule 29 packet-filter inbound ip-group 3001 rule 30 packet-filter inbound ip-group 3001 rule 31 packet-filter inbound ip-group 3001 rule 32 packet-filter inbound ip-group 3001 rule 33 packet-filter inbound ip-group 3001 rule 34 packet-filter inbound ip-group 3001 rule 35line-rate inbound 1024#interface Ethernet1/0/19port access vlan 130packet-filter inbound ip-group 3001 rule 0 packet-filter inbound ip-group 3001 rule 1 packet-filter inbound ip-group 3001 rule 2 packet-filter inbound ip-group 3001 rule 3 packet-filter inbound ip-group 3001 rule 4 packet-filter inbound ip-group 3001 rule 5 packet-filter inbound ip-group 3001 rule 6 packet-filter inbound ip-group 3001 rule 7 packet-filter inbound ip-group 3001 rule 8 packet-filter inbound ip-group 3001 rule 9 packet-filter inbound ip-group 3001 rule 10 packet-filter inbound ip-group 3001 rule 11 packet-filter inbound ip-group 3001 rule 12 packet-filter inbound ip-group 3001 rule 13 packet-filter inbound ip-group 3001 rule 14 packet-filter inbound ip-group 3001 rule 15 packet-filter inbound ip-group 3001 rule 16 packet-filter inbound ip-group 3001 rule 17 packet-filter inbound ip-group 3001 rule 18 packet-filter inbound ip-group 3001 rule 19 packet-filter inbound ip-group 3001 rule 20 packet-filter inbound ip-group 3001 rule 21 packet-filter inbound ip-group 3001 rule 22 packet-filter inbound ip-group 3001 rule 23packet-filter inbound ip-group 3001 rule 25 packet-filter inbound ip-group 3001 rule 26 packet-filter inbound ip-group 3001 rule 27 packet-filter inbound ip-group 3001 rule 28 packet-filter inbound ip-group 3001 rule 29 packet-filter inbound ip-group 3001 rule 30 packet-filter inbound ip-group 3001 rule 31 packet-filter inbound ip-group 3001 rule 32 packet-filter inbound ip-group 3001 rule 33 packet-filter inbound ip-group 3001 rule 34 packet-filter inbound ip-group 3001 rule 35 line-rate inbound 1024#interface Ethernet1/0/20port access vlan 130packet-filter inbound ip-group 3001 rule 0 packet-filter inbound ip-group 3001 rule 1 packet-filter inbound ip-group 3001 rule 2 packet-filter inbound ip-group 3001 rule 3 packet-filter inbound ip-group 3001 rule 4 packet-filter inbound ip-group 3001 rule 5 packet-filter inbound ip-group 3001 rule 6 packet-filter inbound ip-group 3001 rule 7 packet-filter inbound ip-group 3001 rule 8 packet-filter inbound ip-group 3001 rule 9 packet-filter inbound ip-group 3001 rule 10 packet-filter inbound ip-group 3001 rule 11 packet-filter inbound ip-group 3001 rule 12 packet-filter inbound ip-group 3001 rule 13 packet-filter inbound ip-group 3001 rule 14 packet-filter inbound ip-group 3001 rule 15 packet-filter inbound ip-group 3001 rule 16 packet-filter inbound ip-group 3001 rule 17 packet-filter inbound ip-group 3001 rule 18 packet-filter inbound ip-group 3001 rule 19 packet-filter inbound ip-group 3001 rule 20 packet-filter inbound ip-group 3001 rule 21 packet-filter inbound ip-group 3001 rule 22 packet-filter inbound ip-group 3001 rule 23 packet-filter inbound ip-group 3001 rule 24 packet-filter inbound ip-group 3001 rule 25 packet-filter inbound ip-group 3001 rule 26 packet-filter inbound ip-group 3001 rule 27packet-filter inbound ip-group 3001 rule 28packet-filter inbound ip-group 3001 rule 29packet-filter inbound ip-group 3001 rule 30packet-filter inbound ip-group 3001 rule 31packet-filter inbound ip-group 3001 rule 32packet-filter inbound ip-group 3001 rule 33packet-filter inbound ip-group 3001 rule 34packet-filter inbound ip-group 3001 rule 35line-rate inbound 1024#interface Ethernet1/0/21#interface Ethernet1/0/22#interface Ethernet1/0/23port access vlan 2#interface Ethernet1/0/24port access vlan 2#interface GigabitEthernet1/1/1#interface GigabitEthernet1/1/2#interface GigabitEthernet1/1/3#interface GigabitEthernet1/1/4#undo irf-fabric authentication-mode#interface NULL0#voice vlan mac-address 0001-e300-0000 mask ffff-ff00-0000#ip route-static 0.0.0.0 0.0.0.0 192.168.2.1 preference 60 配置到防火墙的默认路由并设定优先级#snmp-agentsnmp-agent local-engineid 800063A2000FE2820C5C6877snmp-agent sys-info version v3 简单网络管理协议的说明#user-interface aux 0 7 开启aux口和telnet访问的权限user-interface vty 0 4authentication-mode scheme#returnsaveacl必须进入接口模式。
H3C3600交换机配置及说明文档--28-镜像命令

【参数】
inbound:对端口接收的数据包进行镜像。 outbound:对端口发送的数据包进行镜像。 acl-rule:下发的 ACL,可以是多种 ACL 的组合。组合方式说明如下。
表1-1 组合下发 ACL 的方式
组合方式
acl-rule 的形式
单独下发一个 IP 型 ACL(包括基本 ACL 与高级 ACL) 中所有子规则
【描述】 display qos-interface mirrored-to 命令用来显示流镜像的参数设置。 显示信息包括:
z 端口名称和流镜像动作名称 z 流镜像的方向 z 进行流识别的 ACL z 镜像目的端口
1-2
H3C S3600 系列以太网交换机 命令手册-Release 1510 镜像
单独下发一个用户自定义 ACL 中所有子规则
user-group acl-number
单独下发一个用户自定义 ACL 中一条子规则
user-group acl-number rule rule-id
同时下发 IP 型 ACL 中一条子规则和二层型 ACL 的一 ip-group acl-number rule rule-id
H3C S3600 系列以太网交换机 命令手册-Release 1510 镜像
目录
目录
第 1 章 镜像命令 .....................................................................................................................1-1 1.1 S3600-EI镜像命令 ............................................................................................................. 1-1 1.1.1 display mirroring-group ........................................................................................... 1-1 1.1.2 display qos-interface mirrored-to............................................................................. 1-2 1.1.3 mirrored-to............................................................................................................... 1-3 1.1.4 mirroring-group........................................................................................................ 1-4 1.1.5 mirroring-group mirroring-port ................................................................................. 1-5 1.1.6 mirroring-group monitor-port ................................................................................... 1-6 1.1.7 mirroring-group reflector-port .................................................................................. 1-6 1.1.8 mirroring-group remote-probe vlan ......................................................................... 1-7 1.1.9 mirroring-port........................................................................................................... 1-8 1.1.10 monitor-port ........................................................................................................... 1-9 1.1.11 remote-probe vlan ................................................................................................. 1-9 1.2 S3600-SI镜像命令 ........................................................................................................... 1-10 1.2.1 display mirror......................................................................................................... 1-10 1.2.2 display qos-interface mirrored-to........................................................................... 1-11 1.2.3 mirrored-to............................................................................................................. 1-11 1.2.4 mirroring-port......................................................................................................... 1-13 1.2.5 monitor-port ........................................................................................................... 1-14
H3C3600交换机配置及说明文档--41-HWPing命令

第 1 章 HWPing 配置命令
【举例】
# 使用 display hwping results 命令查看测试结果。
<H3C> display hwping results administrator icmp
HWPing entry(admin administrator, tag icmp) test result:
【描述】 count 命令用来配置发送测试报文的个数。undo count 命令用来将测试报文个数恢 复到缺省值。 如果设置该参数大于 1,那么系统收到第一个测试报文的响应报文之后,就发送第 二个测试报文。如果一直没有收到响应报文,则等到测试定时器超时,发送第二个 测试报文。如此直到发送完最后一个测试报文。 相关配置可参考命令 frequency。
【举例】 # 设置“administrator-icmp”测试组发送测试报文的个数为 10。
<H3C> system-view System View: return to User View with Ctrl+Z. [H3C] hwping administrator icmp [H3C-hwping-administrator-icmp] count 10
字段
描述
Destination ip address
目的 IP 地址
Send operation times
发送测试次数
Receive response times
成功测试次数
Min/Max/Average Round Trip Time
最小/最大/平均往返时间
Square-Sum of Round Trip Time
HWPing entry(admin administrator, tag icmp) history record:
H3C3600交换机配置及说明文档--21-VRRP命令

Interface
: Vlan-interface10
VRID
:1
CheckSum Errors
:0
Version Errors
:0
VRID Errors
:0
Advertisement Interval Errors : 0
IP TTL Errors
:0
Auth Failures
:0
Invalid Auth Type
1.1.4 vrrp method
【命令】 vrrp method { real-mac | virtual-mac } undo vrrp method
【视图】 系统视图
:0
Auth Type Mismatch
:0
Packet Length Errors : 0
Address List Errors
:0
Become Master
:2
Priority Zero Pkts Rcvd
:0
Advertise Rcvd
:0
Priority Zero Pkts Sent
:1
Invalid Type Pkts Rcvd: 0
【举例】 # 清除交换机上 VRRP 的统计信息。
<H3C> reset vrrp statistics
1.1.3 vrrp authentication-mode
【命令】 vrrp authentication-mode authentication-type authentication-key undo vrrp authentication-mode
当认证方式为 simple 和 md5 时,必须设置认证字。 这条命令是为一个接口上的所有 VRRP 备份组设置认证方式和认证字,这是由于协 议规定一个接口上的备份组应当使用相同的认证方式和认证字。另外,加入同一备 份组的成员也应该设置相同的认证方式和认证字。
H3C3600交换机配置及说明文档--23-ARP命令

目录
目录
第 1 章 ARP配置 .....................................................................................................................1-1 1.1 ARP配置命令 ..................................................................................................................... 1-1 1.1.1 arp check enable ..................................................................................................... 1-1 1.1.2 arp static.................................................................................................................. 1-1 1.1.3 arp timer aging ........................................................................................................ 1-2 1.1.4 display arp ............................................................................................................... 1-3 1.1.5 display arp | ............................................................................................................. 1-4 1.1.6 display arp count ..................................................................................................... 1-5 1.1.7 display arp timer aging ............................................................................................ 1-6 1.1.8 gratuitous-arp-learning enable ................................................................................ 1-7 1.1.9 reset arp .................................................................................................................. 1-7
h3c3600 建立超级终端,为交换机配置IP,到网关路由,web用户,telnet用户

建立超级终端点击开始-程序-附件-通讯-超级终端随便建个名字--选择第一个红色电话机的东西--确定--国家、区号、电话可以随便填写----使用COM口----确定----每秒位数:9600---数据位:8---奇偶校验:无----停止位:1----数据流控制:无----确定然后就进入超级终端。
回车一下焦点,交换机的信息自动读入我们一般做路由选择协议的时候用的一般都是secureCRT配置交换机IP[h3c] sys[h3c] interface vlan-interface 1 (进入管理vlan)[h3c-vlan-interfacce1] undo ip address(取消管理vlan原有的IP地址) [h3c-vlan-interfacce1] ip address 10.153.17.82 255.255.255.0(重新配置管理vlan的ip地址为10.153.17.82 )配置交换机到网关的静态路由[h3c] ip route-static 0.0.0.0 255.255.255.255 192.168.0.50 (网关的IP 地址)配置web用户[h3c] local-user admin (配置用户名admin)[h3c-1user-admin] service-type telnet level 3 (设置级别为3)[h3c-1user-admin] password simple admin (设置密码为admin)配置telnet用户[SwitchA]user-interface vty 0 4 (进入用户界面视图)[SwitchA-ui-vty0-4]authentication-mode scheme (配置本地或远端用户名+口令认证方式)[SwitchA-ui-vty0-4]user privilege level 3 (配置登陆用户的级别为最高级别3(缺省为级别1))添加TELNET管理的用户,用户类型为”telnet”,用户名为”huawei”,密码为” admin”[SwitchA]local-user huawei[SwitchA-luser-huawei]service-type telnet level 3[SwitchA-luser-huawei]password simple admin教你如何设置华为H3C交换机密码第一步:通过Console口在超级终端中执行以下命令,配置以太网交换机管理VLAN的IP 地址。
MD3600F安装配置图解
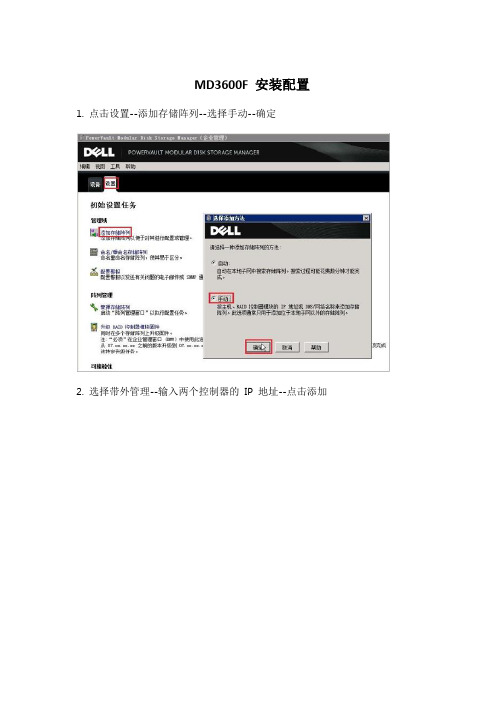
MD3600F 安装配置1.点击设置--添加存储阵列--选择手动--确定
2.选择带外管理--输入两个控制器的IP地址--点击添加
3.点击设备--选择发现的存储阵列
4.进入存储管理界面--选择逻辑--点击创建虚拟磁盘组
5.点击下一步
6.设置磁盘组名称(可按默认)--选择手动--点击下一步
7.选择RAID级别--选定物理磁盘--点击添加--点击计算容量--选择完成
8.添加热备--选择物理磁盘--点击热备用保护
9.选择查看/更改当前热备用保护--点击确定
10.选择硬盘--点击分配
11.选择要被分配的虚拟磁盘组--点击确定
12.在创建好的虚拟磁盘组中创建虚拟磁盘--选择逻辑--选择创建虚拟磁盘
13.选择下一步
14.选择虚拟磁盘容量--虚拟磁盘名称--点击完成
15.映射虚拟磁盘到主机(主机在连接到交换机后会自动扫描出来)--选择映射- -选择要映射的虚拟磁盘--点击定义附加映射
16.选择主机组或主机--选择LUN编号--选择虚拟磁盘--点击完成(完成这一步虚拟磁盘就可以在主机上正常使用了)
17.如何创建主机组--选择映射--点击默认组--定义--主机组
18.输入主机组名称--选择要添加到主机组的主机--点击添加--确定(主机组创建完毕)
19.修改控制器管理IP--点击设置--配置以太网管理端口--以太网管理端口--设置IP地址掩码及网关--点击确定完成
20.收集支持信息(发生故障报修时发送给技术支持)--点击支持--收集支持信息(下边还可查看日志)
21.选择浏览并制定文件名(也就是保存路径)--点击启动直到完成,生成文件后发送给戴尔技术支持。
H3C 5500 核心与 3600汇聚 配置

H3C 5500作为核心和3600作为汇聚运行OSPF配置实例一台5500作为核心交换机,下面连接了5台3600作为汇聚,各汇聚下面连接了5台3100最为接入交换机。
核心5500和汇聚3600之间运行OSPF路由协议。
5500配置dis current#version 5.20, Release 2210#sysname asd-s-bj-5500-1#irf mac-address persistent timerirf auto-update enableundo irf link-delay#domain default enable system#telnet server enable #vlan 1#vlan 12#vlan 15#vlan 21 to 25#vlan 31 to 35#vlan 100#vlan 111#radius scheme system server-type extendedprimary authentication 127.0.0.1 1645 primary accounting 127.0.0.1 1646user-name-format without-domain#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#dhcp server ip-pool v15poolnetwork 172.19.15.0 mask 255.255.255.0 gateway-list 172.19.15.1dns-list 172.19.12.16 172.18.1.16#dhcp server ip-pool v19poolnetwork 172.19.19.0 mask 255.255.255.0 gateway-list 172.19.19.1dns-list 172.19.12.16 172.18.1.16#user-group systemgroup-attribute allow-guest#interface NULL0#interface Vlan-interface12ip address 172.19.12.1 255.255.255.0#interface Vlan-interface15ip address 172.19.15.1 255.255.255.0#interface Vlan-interface21ip address 172.19.11.17 255.255.255.252 #interface Vlan-interface22ip address 172.19.11.21 255.255.255.252#interface Vlan-interface23ip address 172.19.11.25 255.255.255.252 #interface Vlan-interface24ip address 172.19.11.29 255.255.255.252 #interface Vlan-interface25ip address 172.19.11.33 255.255.255.252 #interface Vlan-interface31ip address 172.19.11.37 255.255.255.252 #interface Vlan-interface32ip address 172.19.11.41 255.255.255.252 #interface Vlan-interface33ip address 172.19.11.45 255.255.255.252#interface Vlan-interface34ip address 172.19.11.49 255.255.255.252 #interface Vlan-interface35ip address 172.19.11.53 255.255.255.252 #interface Vlan-interface100ip address 172.19.11.1 255.255.255.252 #interface Vlan-interface111ip address 172.19.11.57 255.255.255.252 #interface GigabitEthernet1/0/1port link-mode bridgeport access vlan 31#interface GigabitEthernet1/0/2port link-mode bridgeport access vlan 32#interface GigabitEthernet1/0/3 port link-mode bridgeport access vlan 33#interface GigabitEthernet1/0/4 port link-mode bridgeport access vlan 34#interface GigabitEthernet1/0/5 port link-mode bridgeport access vlan 35#interface GigabitEthernet1/0/6 port link-mode bridgeport access vlan 21#interface GigabitEthernet1/0/7 port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/8 port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/9 port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/10 port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/11port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/12 port link-mode bridgeport access vlan 12#interface GigabitEthernet1/0/13 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/14 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/15 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/16 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/17 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/18 port link-mode bridgeport access vlan 15#interface GigabitEthernet1/0/19 port link-mode bridge#interface GigabitEthernet1/0/20 port link-mode bridgeport access vlan 100#interface GigabitEthernet1/0/21 port link-mode bridgeport access vlan 15 shutdown#interface GigabitEthernet1/0/22 port link-mode bridgeport access vlan 15 shutdown#interface GigabitEthernet1/0/23 port link-mode bridgeport access vlan 111 shutdown#interface GigabitEthernet1/0/24port link-mode bridgeport access vlan 100 shutdown#interface GigabitEthernet1/0/25 port link-mode bridgeport access vlan 22#interface GigabitEthernet1/0/26 port link-mode bridgeport access vlan 23#interface GigabitEthernet1/0/27 port link-mode bridgeport access vlan 24#interface GigabitEthernet1/0/28 port link-mode bridgeport access vlan 25#ospf 1default-route-advertise always import-route staticarea 0.0.0.0network 172.19.12.0 0.0.0.255 network 172.19.11.36 0.0.0.3 network 172.19.11.40 0.0.0.3 network 172.19.11.44 0.0.0.3 network 172.19.11.48 0.0.0.3 network 172.19.11.52 0.0.0.3 network 172.19.15.0 0.0.0.255 network 172.19.11.56 0.0.0.3 network 172.19.11.16 0.0.0.3 network 172.19.11.20 0.0.0.3 network 172.19.11.24 0.0.0.3 network 172.19.11.28 0.0.0.3network 172.19.11.32 0.0.0.3#ip route-static 0.0.0.0 0.0.0.0 172.19.11.2#dhcp enable#load xml-configuration#load tr069-configuration#user-interface aux 0user-interface vty 0 4user privilege level 3set authentication password simple aisidimis user-interface vty 5 15#return一楼3600:dis current#sysname 1Floor-core-Switch #dhcp-server 1 ip 172.19.12.16 #radius scheme system#domain system#vlan 1#vlan 13#vlan 21#vlan 31#interface Vlan-interface13ip address 172.19.13.1 255.255.255.0 dhcp-server 1#interface Vlan-interface21ip address 172.19.11.18 255.255.255.252 #interface Vlan-interface31ip address 172.19.11.38 255.255.255.252 #interface Aux1/0/0#interface Ethernet1/0/1port access vlan 13#interface Ethernet1/0/2port access vlan 13#interface Ethernet1/0/3 port access vlan 13#interface Ethernet1/0/4 port access vlan 13#interface Ethernet1/0/5 port access vlan 13#interface Ethernet1/0/6 port access vlan 13#interface Ethernet1/0/7 port access vlan 13#interface Ethernet1/0/8 port access vlan 13#interface Ethernet1/0/9 port access vlan 13#interface Ethernet1/0/10 port access vlan 13#interface Ethernet1/0/11 port access vlan 13#interface Ethernet1/0/12 port access vlan 13#interface Ethernet1/0/13 port access vlan 13#interface Ethernet1/0/14 port access vlan 13#interface Ethernet1/0/15 port access vlan 13#interface Ethernet1/0/16 port access vlan 13#interface Ethernet1/0/17 port access vlan 13#interface Ethernet1/0/18 port access vlan 13#interface Ethernet1/0/19 port access vlan 13#interface Ethernet1/0/20 port access vlan 13#interface Ethernet1/0/21 port access vlan 13#interface Ethernet1/0/22 port access vlan 13#interface Ethernet1/0/23 port access vlan 13#interface Ethernet1/0/24 port access vlan 13#interface Ethernet1/0/25 port access vlan 13#interface Ethernet1/0/26 port access vlan 13#interface Ethernet1/0/27 port access vlan 13#interface Ethernet1/0/28 port access vlan 13#interface Ethernet1/0/29 port access vlan 13#interface Ethernet1/0/30 port access vlan 13#interface Ethernet1/0/31 port access vlan 13#interface Ethernet1/0/32 port access vlan 13#interface Ethernet1/0/33 port access vlan 13#interface Ethernet1/0/34 port access vlan 13#interface Ethernet1/0/35 port access vlan 13#interface Ethernet1/0/36 port access vlan 13#interface Ethernet1/0/37 port access vlan 13#interface Ethernet1/0/38 port access vlan 13#interface Ethernet1/0/39 port access vlan 13#interface Ethernet1/0/40 port access vlan 13#interface Ethernet1/0/41 port access vlan 13#interface Ethernet1/0/42 port access vlan 13#interface Ethernet1/0/43 port access vlan 13#interface Ethernet1/0/44 port access vlan 13#interface Ethernet1/0/45 port access vlan 13#interface Ethernet1/0/46 port access vlan 13#interface Ethernet1/0/47 port access vlan 21#interface Ethernet1/0/48 port access vlan 31#interface GigabitEthernet1/1/1 #interface GigabitEthernet1/1/2 #interface GigabitEthernet1/1/3#interface GigabitEthernet1/1/4#undo irf-fabric authentication-mode#interface NULL0#ospf 1area 0.0.0.0network 172.19.11.16 0.0.0.3network 172.19.11.36 0.0.0.3network 172.19.13.0 0.0.0.255#voice vlan mac-address 0001-e300-0000 mask ffff-ff00-0000 #dhcp server forbidden-ip 172.19.13.1#user-interface aux 0 7user-interface vty 0 4user privilege level 3set authentication password simple aisidimis #return[1Floor-core-Switch][1Floor-core-Switch][1Floor-core-Switch]二楼3600:dis current#sysname 2Floor-Core-Switch#dhcp-server 1 ip 172.19.12.16#radius scheme system#domain system#vlan 1#vlan 14#vlan 22#vlan 32#interface Vlan-interface1#interface Vlan-interface14ip address 172.19.14.1 255.255.255.0 dhcp-server 1#interface Vlan-interface22ip address 172.19.11.22 255.255.255.252 #interface Vlan-interface32ip address 172.19.11.42 255.255.255.252 #interface Aux1/0/0#interface Ethernet1/0/1port access vlan 14#interface Ethernet1/0/2port access vlan 14#interface Ethernet1/0/3port access vlan 14#interface Ethernet1/0/4port access vlan 14#interface Ethernet1/0/5port access vlan 14#interface Ethernet1/0/6 port access vlan 14#interface Ethernet1/0/7 port access vlan 14#interface Ethernet1/0/8 port access vlan 14#interface Ethernet1/0/9 port access vlan 14#interface Ethernet1/0/10 port access vlan 14#interface Ethernet1/0/11port access vlan 14#interface Ethernet1/0/12 port access vlan 14#interface Ethernet1/0/13 port access vlan 14#interface Ethernet1/0/14 port access vlan 14#interface Ethernet1/0/15 port access vlan 14#interface Ethernet1/0/16 port access vlan 14#interface Ethernet1/0/17port access vlan 14#interface Ethernet1/0/18 port access vlan 14#interface Ethernet1/0/19 port access vlan 14#interface Ethernet1/0/20 port access vlan 14#interface Ethernet1/0/21 port access vlan 14#interface Ethernet1/0/22 port access vlan 14#interface Ethernet1/0/23port access vlan 14#interface Ethernet1/0/24 port access vlan 14#interface Ethernet1/0/25 port access vlan 14#interface Ethernet1/0/26 port access vlan 14#interface Ethernet1/0/27 port access vlan 14#interface Ethernet1/0/28 port access vlan 14#interface Ethernet1/0/29port access vlan 14#interface Ethernet1/0/30 port access vlan 14#interface Ethernet1/0/31 port access vlan 14#interface Ethernet1/0/32 port access vlan 14#interface Ethernet1/0/33 port access vlan 14#interface Ethernet1/0/34 port access vlan 14#interface Ethernet1/0/35port access vlan 14#interface Ethernet1/0/36 port access vlan 14#interface Ethernet1/0/37 port access vlan 14#interface Ethernet1/0/38 port access vlan 14#interface Ethernet1/0/39 port access vlan 14#interface Ethernet1/0/40 port access vlan 14#interface Ethernet1/0/41port access vlan 14#interface Ethernet1/0/42 port access vlan 14#interface Ethernet1/0/43 port access vlan 14#interface Ethernet1/0/44 port access vlan 14#interface Ethernet1/0/45 port access vlan 14#interface Ethernet1/0/46 port access vlan 14#interface Ethernet1/0/47#interface Ethernet1/0/48port access vlan 32#interface GigabitEthernet1/1/1port access vlan 22#interface GigabitEthernet1/1/2#interface GigabitEthernet1/1/3#interface GigabitEthernet1/1/4#undo irf-fabric authentication-mode #interface NULL0#ospf 1area 0.0.0.0network 172.19.11.20 0.0.0.3network 172.19.11.40 0.0.0.3network 172.19.14.0 0.0.0.255#voice vlan mac-address 0001-e300-0000 mask ffff-ff00-0000 #dhcp server forbidden-ip 172.19.14.1 172.19.14.4#user-interface aux 0 7user-interface vty 0 4user privilege level 3set authentication password simple aisidimis#return[2Floor-Core-Switch][2Floor-Core-Switch][2Floor-Core-Switch]三楼3600:dis current#sysname 3Floor-Core-Switch #dhcp-server 1 ip 172.19.12.16 #radius scheme system#domain system#vlan 1#vlan 16#vlan 23#vlan 33#interface Vlan-interface16ip address 172.19.16.1 255.255.255.0 dhcp-server 1#interface Vlan-interface23ip address 172.19.11.26 255.255.255.252 #interface Vlan-interface33ip address 172.19.11.46 255.255.255.252 #interface Aux1/0/0#interface Ethernet1/0/1port access vlan 16#interface Ethernet1/0/2port access vlan 16#interface Ethernet1/0/3 port access vlan 16#interface Ethernet1/0/4 port access vlan 16#interface Ethernet1/0/5 port access vlan 16#interface Ethernet1/0/6 port access vlan 16#interface Ethernet1/0/7 port access vlan 16#interface Ethernet1/0/8 port access vlan 16#interface Ethernet1/0/9 port access vlan 16#interface Ethernet1/0/10 port access vlan 16#interface Ethernet1/0/11 port access vlan 16#interface Ethernet1/0/12 port access vlan 16#interface Ethernet1/0/13 port access vlan 16#interface Ethernet1/0/14 port access vlan 16#interface Ethernet1/0/15 port access vlan 16#interface Ethernet1/0/16 port access vlan 16#interface Ethernet1/0/17 port access vlan 16#interface Ethernet1/0/18 port access vlan 16#interface Ethernet1/0/19 port access vlan 16#interface Ethernet1/0/20 port access vlan 16#interface Ethernet1/0/21 port access vlan 16#interface Ethernet1/0/22 port access vlan 16#interface Ethernet1/0/23 port access vlan 16#interface Ethernet1/0/24 port access vlan 16#interface Ethernet1/0/25 port access vlan 16#interface Ethernet1/0/26 port access vlan 16#interface Ethernet1/0/27 port access vlan 16#interface Ethernet1/0/28 port access vlan 16#interface Ethernet1/0/29 port access vlan 16#interface Ethernet1/0/30 port access vlan 16#interface Ethernet1/0/31 port access vlan 16#interface Ethernet1/0/32 port access vlan 16#interface Ethernet1/0/33 port access vlan 16#interface Ethernet1/0/34 port access vlan 16#interface Ethernet1/0/35 port access vlan 16#interface Ethernet1/0/36 port access vlan 16#interface Ethernet1/0/37 port access vlan 16#interface Ethernet1/0/38 port access vlan 16#interface Ethernet1/0/39 port access vlan 16#interface Ethernet1/0/40 port access vlan 16#interface Ethernet1/0/41 port access vlan 16#interface Ethernet1/0/42 port access vlan 16#interface Ethernet1/0/43 port access vlan 16#interface Ethernet1/0/44 port access vlan 16#interface Ethernet1/0/45 port access vlan 16#interface Ethernet1/0/46 port access vlan 16#interface Ethernet1/0/47#interface Ethernet1/0/48 port access vlan 33#interface GigabitEthernet1/1/1 port access vlan 23#interface GigabitEthernet1/1/2 #interface GigabitEthernet1/1/3#interface GigabitEthernet1/1/4#undo irf-fabric authentication-mode#interface NULL0#ospf 1area 0.0.0.0network 172.19.11.24 0.0.0.3network 172.19.11.44 0.0.0.3network 172.19.16.0 0.0.0.255#voice vlan mac-address 0001-e300-0000 mask ffff-ff00-0000 #dhcp server forbidden-ip 172.19.16.1#user-interface aux 0 7user-interface vty 0 4user privilege level 3set authentication password simple aisidimis #return[3Floor-Core-Switch][3Floor-Core-Switch][3Floor-Core-Switch]四楼3600:dis current#sysname 4Floor-Core-Switch#dhcp-server 1 ip 172.19.12.16#radius scheme system#domain system#vlan 1#vlan 17#vlan 24#vlan 34#interface Vlan-interface17ip address 172.19.17.1 255.255.255.0 dhcp-server 1#interface Vlan-interface24ip address 172.19.11.30 255.255.255.252 #interface Vlan-interface34。
H3C 3600及3100交换机配置方法

进入管理模式<H3C>system-view显示正在运行的配置信息[H3C] dis cur保存配置信息[H3C]quit<H3C>save配置telnet 管理的用户和口令[H3C]local-user admin[H3C-]password simple password123[H3C-]service-type telnet[H3C-]level 3[H3C-]quit[H3C]user-interface vty 0 4[H3C-]authentication-mode scheme一、H3C 3600交换机1、划分VLAN,并对VLAN进行IP路由创建vlan 1[H3C]vlan 1[H3C]int vlan 1[H3C-Vlan-interface1]ip add 192.168.1.253 255.255.255.0 [H3C-Vlan-interface1]quit[H3C]int e1/0/1[H3C-Ethernet1/0/1]port access vlan 1[H3C-Ethernet1/0/1]quit[H3C]int e1/0/2[H3C-Ethernet1/0/2]port access vlan 1[H3C-Ethernet1/0/2]quit创建vlan 2[H3C]vlan 2[H3C]int vlan 2[H3C-Vlan-interface1]ip add 192.168.2.253 255.255.255.0 [H3C-Vlan-interface1]quit[H3C]int e1/0/3[H3C-Ethernet1/0/3]port access vlan 2[H3C-Ethernet1/0/3]quit[H3C]int e1/0/4[H3C-Ethernet1/0/4]port access vlan 2[H3C-Ethernet1/0/4]quit[H3C]int g1/0/1[H3C-G1/0/1]port access vlan 2[H3C-G1/0/1]quit3100及3600交换机TRUNK口应用:两台交换机级联SwitchA与SwitchB用trunk互连,相同VLAN的PC 之间可以互访,不同VLAN的PC之间禁止互访l 配置方法:# 进入GigabitEthernet 1/1 以太网端口视图。
华三3600交换机配置步骤

华为3600交换机命令说明及资料整理一.基本命令1.基本设置命令display current-configuration 显示当前配置system-view 进入系统视图sysname XXXXX 设置交换机名称2.IP地址配置命令Display ip interface 显示接口的详细信息ip address 192.168.1.1 255.255.255.0 设置IP地址和子网掩码3.Vlan设置命令vlan X 创建vlan接口并进入vlan视图 vlan X to Y 创建X到Y多个vlanshutdown 关闭vlan接口undo vlan X 初始化vlan xdisplay vlan x 查看vlan x配置信息display vlan all 查看所有vlan配置信息port Ethernet 1/0/x 向vlan中加入ethernet 1/0/xport Ethernet 1/0/x to Ethernet 1/0/y 向vlan中加入ethernet 1/0/x到ethernet 1/ 0/y(只对access端口类型有效,将Trunk端口和Hybrid端口加入VLAN,只能通过以太网端口视图下的port trunk permit vlan和port hybrid vlan命令实现)Dis cu 查看命令(yangxiaojun)Quit 退出Save 保存4.端口设置命令copy configuration source ethernet 1/0/1 destination ethernet 1/0/2 ethernet 1/ 0/3将端口1的配置信息拷贝到端口2和端口3Description XXXXX 对端口进行描述display brief interface ethernet 1/0/1 显示端口1的简要配置信息display interface ethernet1/0/1 显示端口1的配置信息port link-type XXXXX 设置端口类型access:设置端口为Access端口。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
配置本地TELNET用户,用户名为”huawei”,密码为”huawei”,权限为最高级别3(缺省为级别1)
[SwitchA]local-user huawei
[SwitchA-user-huawei]password simple huawei
[SwitchA-user-huawei]service-type telnet level 3
[H3C-vlan2]save 将配置信息保存
[H3C-vlan2]quit 退出vlan2
[H3C]interface Vlan-interface 2 进入VLAN2接口模式
[H3C-Vlan-interface2]ip address 192.168.4.1 255.255.255.0 给vlan 2分配IP地址和子网掩码
[SwitchA]local-user huawei
[SwitchA-user-huawei]password simple huawei
[SwitchA-user-huawei]service-type telnet level 3
H3C S3600 交换机堆叠配置
主交换机上的配置
注意:
1) 主交换机的光纤跳线一定要插在箭头向上的光口上,也就是所谓的up。重交换机配置光纤跳线插在箭头向下的光口上,也就是所谓的down。
2) 重交换机上一般不配IP,除需要在重交换机上单独配置堆叠口外,其他配置基本都在主交换机上进行。
3) 主交换机和重交换机的名字必须是一样的,否则在主交换机看不到重交换机上的信息,用sysname给交换机取名字。
Dis ftm information 此条命令用来显示当前Fabric中的协议信息或拓扑数据库信息,也就是所谓的查看交换机当前堆叠状态。
display irf-fabric 此条命令用来查看整个Fabric的信息,包括设备的Unit ID、Unit name、系统运行模式等。如果是从某台设备的Console口查看Fabric信息,则显示信息中在本设备的Unit ID处打上一个*号。
Ftm fabric-vlan 4093(必选命令) 用这条命令指定交换机VLAN的类型
Fabric-port GigabitEthernet 1/1/4 enable 打开1/1/4光口
Save 保存配置
undo fabric-port interface-type interface-number enable(关闭打开的光口)
Trunk配置
#interface GigabitEthernet1/1/1
port link-type trunk# port trunk permit vlan all
不用通过console或telnet到交换机上就可以看端口速率:
看一下D/S灯是否是亮的,如果不是,可以通过按“MODE”键来切换,然后可以通过查看接口上speed灯闪耀的频率看出 (12Hz频率闪烁:端口工作在100Mbps;3Hz频率闪烁:端口工作在10Mbps),即100M时灯闪的更快。
关闭和打开VLAN接口命令
1)首先进入VLAN的接口模式,命令如下
[H3C]interface Vlan-interface ID 后边跟要进入的VLAN的ID
[H3C-Vlan-interface3]shutdown 关闭VLAN接口[H3C-Vlan-interface3]undo shutdown 打开VLAN接口
[H3C]vlan 2
[H3C-vlan2]port Ethernet 1/0/1 to Ethernet 1/0/5
端口配置及指定VLAN
#interface Ethernet1/0/1
stp disable
# port access vlan 103(或port link-type access)
需要输入username和password才可以登陆交换机。
[Quidway]user-interface aux 0
配置本地或远端用户名和口令认证
[Quidway-ui-aux0] authentication-mode scheme
配置本地TELNET用户,用户名为”huawei”,密码为”huawei”,权限为最高级别3(缺省为级别1)
set authentication password simple jinguang
user privilege level 3
3) 配置辅助端口登录验证
user-interface aux 0 4(AUX是通过同异步串口拨号进行远程登入的)
authentication-mode password
(3)、通过con口只需输入password即可远程登陆交换机。
进入用户界面视图
[Quidway]user-interface aux 0
设置认证方式为密码验证方式
[Quidway-ui-aux0] authentication-mode password
设置登陆验证的password为明文密码”huawei”
常用命令
[H3C]sysname 交换机名称 给交换机取个名字,用这条命令后边跟交换机名称即可
[H3C]dis interface Vlan-interface 4 查看VLAN 4接口的信息
[H3C]dis vlan 4 查看VLAN 4上的配置信息
[H3C]dis current-configuration 查看当前的配置信息
如何在H3C的设备上配置本地和远程用户名
(1)只需输入password即可远程登陆交换机。
进入用户界面视图
[SwitchA]user-interface vty 0 4
设置认证方式为密码验证方式
[SwitchA-ui-vty0-4]authentication-mode password
set authentication password simple jinguang
user privilege level 3
IP配置
interface Vlan-interface1
ip address 172.16.1.175 255.255.255.0
创建VLAN及将端口加入到指定的VLAN中
(2)【TELNET本地用户名和密码验证配置】
需要输入username和password才可以登陆交换机。
进入用户界面视图
[SwitchA]user-interface vty 0 4
配置本地或远端用户名和口令认证
[SwitchA-ui-vty0-4]authentication-mode scheme
设置登陆验证的password为明文密码”huawei”
[SwitchA-ui-vty0-4]set authentication password simple huawei
配置登陆用户的级别为最高级别3(缺省为级别1)
[SwitchA-ui-vty0-4]user privilege level 3
删除一个VLAN的IP,如要删除上边VLAN 2的IP,操作如下
[H3C] interface Vlan-interface 2 首先进入VLAN2的接口模式
[H3C-Vlan-interface2]undo ip add 192.168.4.1 255.255.255.0 执行这条命令即可删除VLAN 2上的IP
重交换机上的配置
Fabric-port GigabitEthernet 1/1/4 enable 打开1/1/4光口
Save 保存配置
重交换机上的堆叠这样就算完事了,到此为止两台交换机的堆叠配置就完成了,非常简单。
H3C S3600 Series交换机VLAN配置
基于端口的vlan配置
Telnet服务配置
1) 配置用户信息
local-user jinguang
password simple jinguang
service-type telnet
level 3
2) 配置telnet登录验证
user-interface vty 0 4
auห้องสมุดไป่ตู้hentication-mode password
<H3C>sys 进入配置模式
[H3C]vlan 2 创建vlan2
[H3C-vlan2] description caiwu 给vlan 2取个名字叫caiwu
[H3C-vlan2]port Ethernet 1/0/10 Ethernet 1/0/11 Ethernet 1/0/12 Ethernet 1/0/13 将1/0/10-13端口一起加入到vlan2中
[Quidway-ui-aux0] set authentication password simple huawei
配置登陆用户的级别为最高级别3(缺省为级别1)
[Quidway-ui-aux0] user privilege level 3
(4)、【CON口本地用户名和密码验证配置】
