gre+IPSE+NAT+策略路由实验
CCNP实验GRE隧道流量的IPSEC加密概况

CCNP实验GRE隧道流量的IPSEC加密由于IPSEC只支持对单播流量的加密,所以我们使用GRE隧道可以将广播、组播包封装在一个单播包中,再用IPSEC进行加密。
在进行IPSEC配置前应首先配置好GRE隧道,下面是R1上的GRE隧道配置:R1:interface tunnel0 ip address 192.168.3.1 255.255.255.0tunnel source s1/1tunnel destination 192.1.1.20exit interface s1/1 ip address 192.1.1.40 255.255.255.0ip access-group perimeter inexit interface lo0 ip address 192.168.1.1 255.255.255.0exit ip route 0.0.0.0 0.0.0.0 192.1.1.20!在这里我将总公司内部的骨干网络设为Area0,隧道部分和分公司内部网络设为Area1 (二)寒邪特性及致病特征ospf 1②寒性凝滞,易致疼痛 network 192.168.3.0 0.0.0.255 area 1exit(三)暑邪特性及致病特征①暑性炎热,易致发热②暑性升散,耗气伤津③暑多挟湿,易困脾胃(四)湿邪特性及致病特征①湿郁气机,易损脾阳②湿性重浊,其性趋下③湿性粘滞,缠绵难退ip(五)燥邪特性及致病特征(六)火 permit udp host 192.1.1.20 host 192.1.1.40①火为热极,其性炎上,permit esp③火邪易伤津液gre host 193.1.1.20 host 192.1.1.40内伤主要由于饲养管理不当引起,概括为饥、饱、劳、役四种。
ip三、其他致病因素四、病机(一)邪正消长(二)升降失常(三)阴阳失调第六章四诊(望、闻、问、切)(一)察口色的部位(二)口色1、舌诊所应舌色应心,唇色应脾,金关应肝,玉户应肺,排齿应肾,口角应三焦2、口色分类正色、病色、绝色R2:(1)白色:主虚证,为气血不足之征兆(2)赤色:赤色主热,为气血趋向于外的反应(3)青色:青色主寒、主痛、主风,为感受寒邪及疼痛的象征interface tunnel0ip3tunnel source s1/01)白苔:主表证和寒证,临床最常见(2)黄苔:主热证和里证,淡黄色为微热,深黄为热重ip)灰黑苔:主热、寒湿或虚寒证,表示湿浊重,病情危重ip(一)切脉的部位 access-group perimeter in、马切颌外动脉或颈总动脉2、牛切尾中动脉或颈总动脉、猪、羊切股内动脉1、平脉:正常脉象。
实验3GREoverIPSEC(精)

IKE的相关配置
设置域共享秘钥 修改IKE的工作模式,从模式修改成野蛮模式 修改验证模式为基于用户名验证
设定REMOTE-ADD 参数
设定remote-add 参数 配置nat穿越功能
专业务实 学以致用
实验拓扑图:
专业务实
学以致用
基本配置:
//本地IKE名字ike local-name center //OSPF的Router IDrouter id 1.1.1.1 //配置到分支1的IKE Peerike peer branch1 //配置成野蛮模式exchange-mode aggressive //配置预共享密钥pre-shared-key h3c-msr-branch1 //使用名字作为身份标识id-type name //配置对端名字remote-name branch1 //配置NAT穿越nat traversal //配置到分支1的IKE Peerike peer branch2 //配置成野蛮模式exchange-mode aggressive //配置预共享密钥pre-shared-key h3c-msr-branch2 //使用名字作为身份标识id-type name //配置对端名字remote-name branch2 //配置NAT穿越nat traversal //配置默认安全提议ipsec proposal default //配置分支1的安全模板,序号1ipsec policy-template branch1 1 //指定IKE Peerike-peer branch1 //指定安全提议proposal default //配置分支2的安全模板,序号1ipsec policy-template branch2 1 //指定IKE Peerike-peer branch2 //指定安全提议proposal default //根据安全模板branch1创建安全策略branch序号1ipsec policy branch 1 isakmp template branch1 //根据安全模板branch2创建安全策略branch序号2ipsec policy branch 2 isakmp template branch2 //用于建立GRE连接和OSPF Router ID的Loopback接口
两台出口路由器之间GRE OVER IPSEC+NAT+OSPF

两台出口路由器之间GRE OVER IPSEC+NAT+OSPF实验拓扑:拓扑描述:如上图所示:在两台出口路由器上分别实现站点内部PAT上网,同时通过在R1、R3的出接口之间建立GRE隧道来传递两个站点的动态OSPF路由,同时通过在R1、R3之间建立一个传输模式的IPSEC隧道来对两个出接口的GRE感兴趣流量实施保护。
具体配置:R1:1、接口和PAT配置interface FastEthernet0/0ip address 12.1.1.1 255.255.255.0ip nat outsideinterface FastEthernet0/1ip address 10.1.1.2 255.255.255.0ip nat insideip route 0.0.0.0 0.0.0.0 12.1.1.2ip nat inside source list nat interface FastEthernet0/0 overloadip access-list extended nat 扩展访问列表-定义NAT流量deny ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255拒绝到site B的流量(走GRE隧道)permit ip any any2、GRE隧道配置interface Tunnel0ip address 192.168.1.1 255.255.255.0tunnel source 12.1.1.1tunnel destination 23.1.1.23、OSPF配置router ospf 1 启用OSPF进程1log-adjacency-changesnetwork 10.1.1.2 0.0.0.0 area 0 将内网接口宣告进区域0network 192.168.1.1 0.0.0.0 area 0 将隧道接口宣告进区域0crypto isakmp policy 1 创建一阶段策略encr 3desauthentication pre-sharegroup 2crypto isakmp key 6 cisco address 23.1.1.2 指定对端地址和pre-share keycrypto ipsec transform-set myset esp-3des esp-sha-hmac 二阶段数据加密和完整性校验算法mode transport 传输模式(加密连个端点的数据)crypto map mymap 1 ipsec-isakmp 创建加密映射关联感兴趣流、转换集、对端地址set peer 23.1.1.2set transform-set mysetmatch address vpninterface FastEthernet0/0crypto map mymap 在出接口下应用加密映射ip access-list extended vpnpermit gre host 12.1.1.1 host 23.1.1.2 IPSEC VPN的感兴趣流就是两个出接口间的GRE流量R2:interface Loopback0ip address 2.2.2.2 255.255.255.255interface FastEthernet0/0ip address 12.1.1.2 255.255.255.0interface FastEthernet0/1ip address 23.1.1.1 255.255.255.0R3:1、接口和PAT配置interface FastEthernet0/0ip address 10.2.2.2 255.255.255.0ip nat insideinterface FastEthernet0/1ip address 23.1.1.2 255.255.255.0ip nat outsideip route 0.0.0.0 0.0.0.0 23.1.1.1ip nat inside source list nat interface FastEthernet0/1 overloadip access-list extended nat 扩展访问列表-定义NAT流量deny ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255拒绝到site A的流量(走GRE隧道)permit ip any any2、GRE隧道配置interface Tunnel0ip address 192.168.1.2 255.255.255.0tunnel source 23.1.1.2tunnel destination 12.1.1.1router ospf 1log-adjacency-changesnetwork 10.2.2.2 0.0.0.0 area 0network 192.168.1.2 0.0.0.0 area 04、IPSEC配置crypto isakmp policy 1 创建一阶段策略encr 3desauthentication pre-sharegroup 2crypto isakmp key 6 cisco address 12.1.1.1 指定对端地址和pre-share keycrypto ipsec transform-set myset esp-3des esp-sha-hmac 二阶段数据加密和完整性校验算法mode transport 传输模式(加密连个端点的数据)crypto map mymap 1 ipsec-isakmp 创建加密映射关联感兴趣流、转换集、对端地址set peer 12.1.1.1set transform-set mysetmatch address vpninterface FastEthernet0/1crypto map mymap 在出接口下应用加密映射ip access-list extended vpnpermit gre host 23.1.1.2 host 12.1.1.1 IPSEC VPN的感兴趣流就是两个出接口间的GRE流量R4:no ip routinginterface FastEthernet0/1ip address 10.1.1.1 255.255.255.0ip default-gateway 10.1.1.2R5:no ip routinginterface FastEthernet0/0ip address 10.2.2.1 255.255.255.0ip default-gateway 10.2.2.2实验测试:1、测试到对端的连通性R4-ping-R5NAT转换为空2、测试到公网的连通性R4-ping-R2的环回口有NAT转换3、在R1上show crypto isakmp sa5、在R1上show crypto ipsec sa6、在R1上show crypto engine connections active7、查看R1的路由表通过OSPF学到site B的路由,下一跳指向site B的隧道接口IP地址7、在R2的f0/1口抓包查看信息此时已看不到R4pingR5的ICMP包,在出接口IP头里面的ESP对GRE流量进行了加密在R1清除clear crypto isakmp可以看到IPSEC通道建立的ISAKMP包和后续发起的R4-45的ping包实验总结:测试做实验的时候,模拟内网如果用环回口带源地址ping的话可能不同(应尽量使用真实的一台模拟路由器);还有就是注意从NAT的流量里面DENY叼走GRE的流量。
IPSec VPN穿越NAT的通信实验

实验五 IPSec VPN 穿越NAT 的通信实验【实验名称】IPSec VPN 穿越NA T 的通信实验【实验目的】学习配置Site to Site 的IPSec VPN 隧道,加深对IPSec 协议的理解。
并且体会IPSec VPN 穿越NAT 的通信。
【背景描述】假设北京的某公司在上海开了新的分公司,分公司要远程访问总公司的各种服务器资源,例如:CRM 系统、FTP 系统等。
Internet 上的网络传输本身存在安全隐患,这家公司希望通过采用IPSec VPN 技术实现数据的安全传输。
上海的分公司组网的时候使用私有地址,在出口部署NA T 将私有地址转换为公有地址来接入互联网,就是说两台VPN 网关之间还存在NAT 设备。
从原理来说,NAT 和IPSec 存在一定的矛盾,因此当在有NAT 设备的环境,传统的IPSec VPN 会出现无法正常工作的现象。
但锐捷VPN 产品,遵循IETF 公布的最新穿越NAT 的标准,良好的实现了IPSec VPN 对NAT 设备的穿越。
【需求分析】需求: 解决上海分公司和北京总公司之间通过Internet 进行信息安全传输的问题 分析: IPSec VPN 技术通过隧道技术、加解密技术、密钥管理技术、和认证技术有效的保证了数据在Internet 网络传输的安全性,是目前最安全、使用最广泛的VPN 技术。
因此我们可以通过建立IPSec VPN 的加密隧道,实现分公司和总公司之间的信息安全传输。
另外,VPN 设备还必须支持NA T 穿越技术。
【实验拓扑】【实验设备】【预备知识】1、网络基础知识、网络安全基础知识、VPN 基础知识;2、IPSec 协议的基本内容、其工作模式;VPN 设备Aeht0 eht1eht0eht1PC 1PC 2 NAT-RVPN 设备BF0/0 F0/13、IKE协议的基本工作原理;4、IPSec VPN不能穿越NAT的原因;5、IPSec VPN穿越NAT的原理。
GRE Over IPSec+NAT经典配置

GRE Over IPSec VPN+NAT配置
试验拓扑
试验要求
Site1和Site2分别模拟需要建立VPN通讯的两个站点,其中202.100.1.1和61.128.1.1 这两个地址分别为Site1和Site2的VPN加密点,1.1.1.0/24和2.2.2.0/24分别是Site1和Site2的内网地址,用来模拟VPN的通讯点。
要求Site1和Site2之间配置GRE Over IPSec VPN,使两个站点的内网之间通过VPN的方式加密传输,同时要求内网也可以访问互联网上的任何站点。
在配置GRE Over IPSec VPN时采用ISAKMP Profile+IPSEC Profile配置方法
在Site1上发起VPN流量:
在Sit2上查看VPN建立的情况:
以上测试说明现在两个站点之间的内网已经可以通过VPN的方式进行传输。
测试Site1访问互联网的情况:
可以看到内网目前无法访问互联网,原因是没有在Site1上配置NAT。
测试
再次测试两个站点之间内网通讯情况:
测试Site1访问Internet的通讯情况:
通过测试Site1和Site2内网之间可以通过VPN方式传输,同时也可以访问互联网,试验成功!。
GRE配置及NAT路由策略参考

GRE配置【需求】两台路由器通过公网用GRE实现私网互通。
公网IP Tunnel IP Source IP Destnation IP RTA202.101.1.2/24192.168.0.1/30202.101.1.2202.101.2.2 RTB202.101.2.2/24192.168.0.2/30202.101.2.2202.101.1.2【Router A】#sysname RTA#interface Ethernet2/0ip address 202.101.1.2 255.255.255.0 /公网IP/#interface Ethernet2/1ip address 192.168.1.1 255.255.255.0 /内部私网IP/#interface Tunnel0 /创建tunnel 0/ip address 192.168.0.1 255.255.255.252 /tunnel IP和对方tunnel IP在同一网段/source 202.101.1.2 /源地址/destination 202.101.2.2 /目的地址/#ip route-static 0.0.0.0 0.0.0.0 202.101.1.1 preference 60 /到公网的默认路由/ip route-static 192.168.2.0 255.255.255.0 Tunnel 0 preference 60 /通过tunnel访问对方私网的路由/#【Router B】#sysname RTB#interface Ethernet2/0ip address 202.101.2.2 255.255.255.0 /内部私网IP/#interface Tunnel0 /创建tunnel 0/ip address 192.168.0.2 255.255.255.252 /tunnel IP和对方tunnel IP在同一网段/source 202.101.2.2 /源地址/destination 202.101.1.2 /目的地址/#ip route-static 0.0.0.0 0.0.0.0 202.101.2.1 preference 60 /到公网的默认路由/ip route-static 192.168.1.0 255.255.255.0 Tunnel 0 preference 60 /通过tunnel访问对方私网的路由/#returnACL路由策略:(用出接口地址做NAT)[A]acl number 2001[A-acl-basic-2001]rule permit source 允许通过的源地址段,反掩码[A-acl-basic-2001]rule deny[Quidway-Ethernet0/1] nat outbound 2000 在出接口上进行NAT转换[Quidway]ip route-static 0.0.0.0 0.0.0.0 出接口对端地址 preference 60 ACL路由策略:(地址池方式做nat)nat address-group 0 202.1.1.3 202.1.1.6用户NAT的地址池nat outbound 2000 address-group 0在出接口上进行NAT转换寻址策略:acl number 3000rule 1 permit ip destination 10.1.1.1 0acl number 3001rule 2 permit ip destination 10.1.2.1 0route-policy 1 permit node 1if-match acl 3000apply ip-address next-hop 192.168.1.3route-policy 1 permit node 2if-match acl 3001apply ip-address next-hop 192.168.4.2#。
实验6IPSECoverGRE_NAT穿越(精)

设备清单:MSR系列路由器5台
专业务实 学以致用
实验拓扑图:
专业务实
学以致用
基本配置:
/本地IKE名字 ike local-name center # //OSPF的Router ID router id 1.1.1.1 # //配置到分支1的IKE Peer ike peer branch1 //配置成野蛮模式 exchange-mode aggressive //配置预共享密钥 pre-shared-key h3c-msr-branch1 //使用名字作为身份标识 id-type name //配置对端名字 remote-name branch1 //配置NAT穿越 nat traversal //配置到分支1的IKE Peer ike peer branch2 //配置成野蛮模式 exchange-mode aggressive //配置预共享密钥 pre-shared-key h3c-msr-branch2 //使用名字作为身份标识 id-type name //配置对端名字 remote-name branch2 //配置NAT穿越 nat traversal //配置默认安全提议 ipsec proposal default //配置分支1的安全模板,序号1
专业务实
学以致用
谢谢收看! 请多指教!
专业务实 学以致用
此总部与分支之间配置成野蛮模式和NAT穿越,总部路由器不配置
ACL,而使用安全模板,总部和分支之间通过内网Loopback建立 GRE隧道,分支通过建立ACL使分支Loopback和总部Loopback
之间的GRE通过IPSec互通,建立好GRE隧道后,在隧道上运行
OSPF,使各内部路由互通,分支之间的流量通过总部转发,需要 注意的是Loopback口不能添加到OSPF中
IPSec over GRE实验文档

IPSec over GRE一、实验拓朴二、实验目的1.所有流量由IPSec保护2.所有流量通过GRE封装3.实现协议数据被GRE封装,用户数据被Ipsec保护三、实验配置Router>enableRouter#config tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#no ip domain-lookupRouter(config)#line console 0Router(config-line)#logging synRouter(config-line)#logging synchronousRouter(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#line vty 0 4Router(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#Router(config-line)#exitRouter(config)#hostname Rt1Rt1(config)#hostname RT1RT1(config)#RT1(config)#interface loopback 0 /设置loopback 口/*Mar 1 00:04:32.139: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to upRT1(config-if)#ip address 192.168.0.1 255.255.255.255RT1(config-if)#exitRT1(config)#interface e1/0RT1(config-if)#ip address 192.168.20.1 255.255.255.0RT1(config-if)#no shutdownRT1(config-if)#*Mar 1 00:05:04.431: %LINK-3-UPDOWN: Interface Ethernet1/0, changed state to up*Mar 1 00:05:05.431: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet1/0, changed state to upRT1(config-if)#exitRT1(config)#interface e0/0RT1(config-if)#ip address 172.1.1.2 255.255.255.240RT1(config-if)#no shutdownRT1(config-if)#exitRT1(config)#*Mar 1 00:05:48.111: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up*Mar 1 00:05:49.111: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to upRT1(config)#ip route 0.0.0.0 0.0.0.0 172.1.1.1RT1(config)#interface tunnel 0 /设置Tunnel通道/*Mar 1 00:11:59.435: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to downRT1(config-if)#ip address 192.168.1.1 255.255.255.252RT1(config-if)#tunnel mode gre ipRT1(config-if)#tunnel source 172.1.1.2 /定义tunnel源地址/RT1(config-if)#tunnel destination 172.1.2.2/定义/tunnel目标地址/*Mar 1 00:12:38.515: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to upRT1(config-if)#exitRT1(config)#interface tunnel 1/设置Tunnel通道/*Mar 1 00:12:50.019: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to downRT1(config-if)#ip address 192.168.1.5 255.255.255.252RT1(config-if)#tunnel mode gre ipRT1(config-if)#tunnel source 172.1.1.2定义tunnel源地址/RT1(config-if)#tunnel destination 172.1.3.2/tunnel目标地址/RT1(config-if)#exitRT1(config)#crypto isakmp enable /启动IKE/配置第一阶段策略(IKE):5 个参数(加密算法、认证算法、认证方法(RSA/pre-share)、DH 算法、IKE SA 生存期)RT1(config)#crypto isakmp policy 10RT1(config-isakmp)#encryption 3desRT1(config-isakmp)#hash shaRT1(config-isakmp)#authentication pre-shareRT1(config-isakmp)#group 2RT1(config-isakmp)#lifetime 86400RT1(config-isakmp)#exit配置pre-share 共享密钥RT1(config)#crypto isakmp key 0 ss address 192.168.0.2RT1(config)#crypto isakmp key 0 ss address 192.168.0.3配置第二阶段策略(IPSec):4 个参数,即IPSec 变换集(安全协议(ESP/AH)、加密算法、认证算法、封装模式(隧道/传输))RT1(config)#crypto ipsec transform-set tt esp-3des esp-sha-hmacRT1(cfg-crypto-trans)#mode tunnel /隧道模式/RT1(cfg-crypto-trans)#exit配置感兴趣流量RT1(config)#$ 102 permit ip 192.168.0.0 0.0.255.255 192.168.36.0 0.0.0.255RT1(config)#$ 103 permit ip 192.168.0.0 0.0.255.255 192.168.44.0 0.0.0.255配置加密图(crypto map):3 个参数绑定(IKE Peer、第二阶段策略(即IPSec 变换集)、感兴趣流量)RT1(config)#crypto map aa local-address loopback 0 /配置加密图对应本地的loobpbak口/RT1(config)#crypto map aa 10 ipsec-isakmp% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.RT1(config-crypto-map)#set peer 192.168.0.2RT1(config-crypto-map)#set transform-set ttRT1(config-crypto-map)#match address 102RT1(config-crypto-map)#exit配置加密图(crypto map):3 个参数绑定(IKE Peer、第二阶段策略(即IPSec 变换集)、感兴趣流量)RT1(config)#crypto map bb local-address loopback 0/配置加密图对应本地的loobpbak口/RT1(config)#crypto map bb 10 ipsec-isakmp% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.RT1(config-crypto-map)#set peer 192.168.0.3RT1(config-crypto-map)#set transform-set ttRT1(config-crypto-map)#match address 103RT1(config-crypto-map)#exit将加密图(crypto map)应用到接口(应用到感兴趣流量需要做IPSec VPN 的出接口)IPSec OVER GRE map是运用在tunnel 口RT1(config)#interface tunnel 0RT1(config-if)#crypto map aaRT1(config-if)#exitRT1(config)#*Mar 1 00:23:23.579: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON(应用到感兴趣流量需要做IPSec VPN 的出接口)IPSec OVER GRE map是运用在tunnel 口RT1(config)#interface tunnel 1RT1(config-if)#crypto map bbRT1(config-if)#exit配置静态路由RT1(config)#ip route 192.168.36.0 255.255.255.0 tunnel 0RT1(config)#ip route 192.168.44.0 255.255.255.0 tunnel 1RT1(config)#ip route 192.168.0.2 255.255.255.255 tunnel 0RT1(config)#ip route 192.168.0.3 255.255.255.255 tunnel 1Router>enableRouter#config tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#no ip domain-lookupRouter(config)#line console 0Router(config-line)#logging synRouter(config-line)#logging synchronousRouter(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#line vty 0 4Router(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#Router(config-line)#exitRT2(config)#interface loopback 0/配置loopback 口/*Mar 1 00:06:24.119: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to upRT2(config-if)#ip address 192.168.0.2 255.255.255.255RT2(config)#interface e1/0RT2(config-if)#ip address 192.168.36.1 255.255.255.0RT2(config-if)#no shutdownRT2(config-if)#exit*Mar 1 00:06:53.683: %LINK-3-UPDOWN: Interface Ethernet1/0, changed state to up*Mar 1 00:06:54.683: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet1/0, changed state to upRT2(config)#interface e0/0RT2(config-if)#ip address 172.1.2.2 255.255.255.240RT2(config-if)#no shutdownRT2(config-if)#exitRT2(config)#ip route 0.0.0.0 0.0.0.0 172.1.2.1 /配置静态路由RT2(config)#interface tunnel 0 /设置tunnel通道RT2(config-if)#ip address 192.168.1.2 255.255.255.252RT2(config-if)#tunnel mode gre ipRT2(config-if)#tunnel source 172.1.2.2 /定义tunnel源地址RT2(config-if)#tunnel destination 172.1.1.2/定义tunnel目标地址*Mar 1 00:14:18.519: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to upRT2(config-if)#exitRT2(config)#crypto isakmp enable 启动IKE(即ISAKMP)配置第一阶段策略(IKE):5 个参数(加密算法、认证算法、认证方法(RSA/pre-share)、DH 算法、IKE SA 生存期)RT2(config)#crypto isakmp policy 10RT2(config-isakmp)#encryption 3desRT2(config-isakmp)#hash shaRT2(config-isakmp)#authentication pre-shareRT2(config-isakmp)#group 2RT2(config-isakmp)#lifetime 86400RT2(config-isakmp)#exit配置pre-share 共享密钥RT2(config)#crypto isakmp key 0 ss address 192.168.0.1配置第二阶段策略(IPSec):4 个参数,即IPSec 变换集(安全协议(ESP/AH)、加密算法、认证算法、封装模式(隧道/传输))RT2(config)#crypto ipsec transform-set tt esp-3des esp-sha-hmacRT2(cfg-crypto-trans)#mode tunnel /隧道模式/RT2(cfg-crypto-trans)#exitRT2(config)#$ 101 permit ip 192.168.36.0 0.0.0.255 192.168.0.0 0.0.255.255 /匹配感兴趣流量/ RT2(config)#crypto map aa local-address loopback 0配置加密图对应本地的loobpbak口配置加密图(crypto map):3 个参数绑定(IKE Peer、第二阶段策略(即IPSec 变换集)、感兴趣流量)RT2(config)#crypto map aa 10 ipsec-isakmp% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.RT2(config-crypto-map)#set peer 192.168.0.1RT2(config-crypto-map)#set transform-set ttRT2(config-crypto-map)#match address 101RT2(config-crypto-map)#exit将加密图(crypto map)应用到接口(应用到感兴趣流量需要做IPSec VPN 的出接口)RT2(config)#interface tunnel 0 /IPSec OVER GRE是应用在Tunnel口/RT2(config-if)#crypto map aaRT2(config-if)#*Mar 1 00:29:10.371: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON配置静态路由RT2(config)#ip route 192.168.0.1 255.255.255.255 tunnel 0RT2(config)#ip route 192.168.0.3 255.255.255.255 tunnel 0Router>enableRouter#config tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#no ip domain-lookupRouter(config)#line console 0Router(config-line)#logging synRouter(config-line)#logging synchronousRouter(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#line vty 0 4Router(config-line)#no loginRouter(config-line)#privilege level 15Router(config-line)#exitRouter(config)#hostname RT3RT3(config)#interface loopback 0 /配置loopback 口/RT3(config-if)#*Mar 1 00:07:44.479: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to upRT3(config-if)#ip address 192.168.0.3 255.255.255.255RT3(config-if)#exitRT3(config)#interface e1/0RT3(config-if)#ip address 192.168.44.1 255.255.255.0RT3(config-if)#no shutdownRT3(config-if)#*Mar 1 00:08:42.679: %LINK-3-UPDOWN: Interface Ethernet1/0, changed state to up*Mar 1 00:08:43.679: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet1/0, changed state to upRT3(config-if)#exitRT3(config)#interface e0/0RT3(config-if)#ip address 172.1.3.2 255.255.255.240RT3(config-if)#no shutdownRT3(config-if)#exitRT3(config)#ip ro*Mar 1 00:09:02.171: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up*Mar 1 00:09:03.171: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to upRT3(config)#ip route 0.0.0.0 0.0.0.0 172.1.3.1 /配置静态路由/RT3(config)#interface tunnel 0 /设置tunnel通道*Mar 1 00:14:33.871: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to downRT3(config-if)#ip address 192.168.1.6 255.255.255.252RT3(config-if)#tunnel mode gre ipRT3(config-if)#tunnel source 172.1.3.2 /定义tunnel源地址RT3(config-if)#tunnel destination 172.1.1.2 /定义tunnel目标地址RT3(config-if)#*Mar 1 00:15:15.155: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up*Mar 1 00:25:14.959: %SYS-5-CONFIG_I: Configured from console by consoleRT3(config)#crypto isakmp enable 启动IKE(即ISAKMP)配置第一阶段策略(IKE):5 个参数(加密算法、认证算法、认证方法(RSA/pre-share)、DH 算法、IKE SA 生存期)RT3(config)#crypto isakmp policy 10RT3(config-isakmp)#encryption 3desRT3(config-isakmp)#hash shaRT3(config-isakmp)#authentication pre-shareRT3(config-isakmp)#group 2RT3(config-isakmp)#lifetime 86400RT3(config-isakmp)#exit配置pre-share 共享密钥RT3(config)#crypto isakmp key 0 ss address 192.168.0.1配置第二阶段策略(IPSec):4 个参数,即IPSec 变换集(安全协议(ESP/AH)、加密算法、认证算法、封装模式(隧道/传输))RT3(config)#crypto ipsec transform-set tt esp-3des esp-sha-hmacRT3(cfg-crypto-trans)#mode tunnel /隧道模式/RT3(cfg-crypto-trans)#exitRT3(config)#$ 101 permit ip 192.168.44.0 0.0.0.255 192.168.0.0 0.0.255.255 /匹配感兴趣流量/ RT3(config)#crypto map bb local-address loopback 0配置加密图对应本地的loobpbak口配置加密图(crypto map):3 个参数绑定(IKE Peer、第二阶段策略(即IPSec 变换集)、感兴趣流量)RT3(config)#crypto map bb 10 ipsec-isakmp% NOTE: This new crypto map will remain disabled until a peerand a valid access list have been configured.RT3(config-crypto-map)#set peer 192.168.0.1RT3(config-crypto-map)#set transform-set ttRT3(config-crypto-map)#match address 101RT3(config-crypto-map)#exitRT3(config)#interface tunnel 0 将加密图(crypto map)应用到接口(应用到感兴趣流量需要做IPSec VPN 的出接口)*Mar 1 00:33:40.167: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to downRT3(config-if)#crypto map bb /IPSec OVER GRE是应用在Tunnel口/RT3(config-if)#*Mar 1 00:33:44.259: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON配置静态路由RT3(config)#ip route 192.168.0.1 255.255.255.255 tunnel0RT3(config)#ip route 192.168.0.2 255.255.255.255 tunnel0测试结果RT1#ping 192.168.36.1 source 192.168.20.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.36.1, timeout is 2 seconds: Packet sent with a source address of 192.168.20.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/79/184 ms RT1#ping 192.168.44.1 source 192.168.20.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.44.1, timeout is 2 seconds: Packet sent with a source address of 192.168.20.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/76/184 ms RT2#ping 192.168.20.1 source 192.168.36.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds: Packet sent with a source address of 192.168.36.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/92/144 ms RT2#ping 192.168.44.1 source 192.168.36.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.44.1, timeout is 2 seconds: Packet sent with a source address of 192.168.36.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/132/316 ms RT3#ping 192.168.20.1 source 192.168.44.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds: Packet sent with a source address of 192.168.44.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/75/200 ms RT3#ping 192.168.36.1 source 192.168.44.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.36.1, timeout is 2 seconds: Packet sent with a source address of 192.168.44.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 36/146/324 ms业务数据均通过udp传输,封装isakmp头部报文格式为:IP头为set peer的地址:S:192.168.0.1 D:192.168.0.2 UDP源目端口均为500所有业务数据都被IPSec保护。
GER OVER IPSEC 穿越 NAT

GRE OVER IPSEC 穿越 NAT 1、实验环境:2、实验配置:Branch 1:[RT1]dis cur#sysname RT1#ike local-name r1#ike peer r3exchange-mode aggressivepre-shared-key cipher TEzJOUGCmuE=id-type nameremote-name r3remote-address 1.0.0.60nat traversal#ipsec proposal 1#ipsec policy 1 1 isakmpsecurity acl 3000ike-peer r3proposal 1#acl number 3000rule 0 permit gre source 192.168.1.1 0 destination 172.16.1.1 0 #interface Serial0/2/0link-protocol pppip address 10.0.1.1 255.255.255.0ipsec policy 1#interface LoopBack0ip address 192.168.11.1 255.255.255.255#interface LoopBack1ip address 192.168.1.1 255.255.255.255#interface Tunnel0ip address 10.0.2.1 255.255.255.0source LoopBack1destination 172.16.1.1#ip route-static 0.0.0.0 0.0.0.0 10.0.1.2ip route-static 172.1.1.1 255.255.255.255 Tunnel0 #NAT:[NAT]dis cur#sysname NAT#nat address-group 0 11.0.0.1 11.0.0.10#acl number 2000rule 0 permit source 10.0.1.0 0.0.0.255#interface Serial0/2/0link-protocol pppip address 10.0.1.2 255.255.255.0#interface Serial0/2/2link-protocol pppnat outbound 2000 address-group 0ip address 1.0.0.1 255.255.255.0#Center:[RT3]dis cur#sysname RT3#ike local-name r3#ike peer r1exchange-mode aggressivepre-shared-key cipher TEzJOUGCmuE= id-type nameremote-name r1nat traversal#ipsec proposal 1#ipsec policy-template r3 1ike-peer r1proposal 1#ipsec policy 1 1 isakmp template r3#interface Serial0/2/0link-protocol pppip address 1.0.0.60 255.255.255.0 ipsec policy 1#interface LoopBack0ip address 172.1.1.1 255.255.255.255 #interface LoopBack1ip address 172.16.1.1 255.255.255.255 #interface Tunnel0ip address 10.0.2.2 255.255.255.0source LoopBack1destination 192.168.1.1#ip route-static 11.0.0.0 255.0.0.0 1.0.0.1ip route-static 192.168.1.1 255.255.255.255 1.0.0.1 ip route-static 192.168.11.1 255.255.255.255 Tunnel0 #3、测试:<RT1>ping -a 192.168.11.1 172.1.1.1PING 172.1.1.1: 56 data bytes, press CTRL_C to breakReply from 172.1.1.1: bytes=56 Sequence=1 ttl=255 time=26 msReply from 172.1.1.1: bytes=56 Sequence=2 ttl=255 time=5 msReply from 172.1.1.1: bytes=56 Sequence=3 ttl=255 time=5 msReply from 172.1.1.1: bytes=56 Sequence=4 ttl=255 time=20 msReply from 172.1.1.1: bytes=56 Sequence=5 ttl=255 time=15 ms--- 172.1.1.1 ping statistics ---5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 5/14/26 ms<RT1>ping -a 192.168.11.1 172.1.1.1PING 172.1.1.1: 56 data bytes, press CTRL_C to break*Nov 24 14:35:26:531 2011 RT1 GRE/7/debug:Tunnel0 packet:Before encapsulation,Outer packet header 192.168.11.1->172.1.1.1(length = 84)*Nov 24 14:35:26:531 2011 RT1 GRE/7/debug:Tunnel0 packet:After encapsulation,Outgoing packet header 192.168.1.1->172.16.1.1(length = 108)*Nov 24 14:35:26:531 2011 RT1 GRE/7/debug:Tunnel0 packet: GRE physical transmit a packet(len = 108, protocol = 0x800).*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:--- Send IPSec packet ---*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Tunnel mode. Adding outer IP header succeed!*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Src:10.0.1.1 Dst:1.0.0.60SPI:211544224(0x0c9be8a0)*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:New ESP(RFC2406) Enc Alg:DES Auth Alg:HMAC-MD5-96*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Encryption finished! New ESP(RFC2406) SN:10*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:IPSEC packet encapsulates udp dst port:[62465] src port:[62465]*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Now send it to IP output process...*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:--- Receive IPSec(ESP) packet --- *Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Src:1.0.0.60 Dst:10.0.1.1SPI:458514610(0x1b5460b2)*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:New ESP(RFC2406) Enc Alg:DES Auth Alg:HMAC-MD5-96*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Replay Checking Enabled! SN:10 *Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:ESP new input: Authentication succeed!*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:IPSEC Task: Decryption succeed!*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Tunnel mode. Org Src:172.16.1.1 Org Dst:192.168.1.1*Nov 24 14:35:26:531 2011 RT1 IPSEC/7/DBG:Now send it to IP input process...。
GREover IPsec实验报告

GRE over IPsec一、实验拓扑:二、实验目的:总部与分部业务网段通过GRE实现互访,同时要通过IPsec对其进行保护。
三、实验配置:1、首先配置好基本信息及接口配置;2、GRE的相关配置;R1 tunnel的配置:interface Tunnel0ip address 192.168.1.1 255.255.255.252 tunnel source 172.1.1.2tunnel destination 172.1.2.2interface Tunnel1ip address 192.168.1.5 255.255.255.252 tunnel source 172.1.1.2tunnel destination 172.1.3.2R2 tunnel 的配置:interface Tunnel0ip address 192.168.2.1 255.255.255.252 tunnel source 172.1.2.2tunnel destination 172.1.1.2R3 tunnel的配置:interface Tunnel1ip address 192.168.2.5 255.255.255.252tunnelsource 172.1.3.2tunnel destination 172.1.1.2在RT1上配置ip route 192.168.36.0 255.255.255.0 Tunnel0 ip route 192.168.44.0 255.255.255.0 Tunnel1 在RT2上配置ip route 192.168.20.0 255.255.255.0 Tunnel0在RT3上配置ip route 192.168.20.0 255.255.255.0 Tunnel13、IPsec的相关配置;RT1配置:crypto isakmppolicy 10encr 3deshash md5authentication pre-sharegroup 2crypto isakmp keycisco address 172.1.2.2crypto isakmp keycisco address 172.1.3.2 crypto ipsectransform-set t esp-3des esp-md5-hmacmode trancrypto map mymap 10 ipsec-isakmpset peer172.1.2.2set transform-set testmatch address 101crypto map mymap 20 ipsec-isakmpset peer172.1.3.2 settransform-set tmatch address 102access-list 101 permit gre host 172.1.1.2 host 172.1.2.2access-list 102 permit gre host 172.1.1.2 host 172.1.3.2int e0/0crypto map mymapRT2配置:crypto isakmp policy 10encr 3deshash md5authentication pre-sharegroup 2crypto isakmp keycisco address 172.1.1.2crypto ipsectransform-set t esp-3des esp-md5-hmacmode trancrypto map mymap 10 ipsec-isakmpset peer 172.1.1.2set transform-set tmatch address 101access-list 101 permit gre host 172.1.2.2 host 172.1.1.2 int e0/0crypto map mymapRT3配置:crypto isakmp policy 10encr 3deshash md5authentication pre-sharegroup 2crypto isakmp key cisco address 172.1.1.2crypto ipsectransform-set t esp-3des esp-md5-hmacmode trancrypto map mymap 20 ipsec-isakmpset peer 172.1.1.2set transform-set tmatch address 102access-list 102 permit gre host 172.1.3.2 host 172.1.1.2 int e0/0crypto map mymap四、实验抓包GRE over ipsec 是使用IPsec保护GRE分组,使用GRE封装和承载路由信息和业务数据。
GRE+IPSEC+OSPF实验
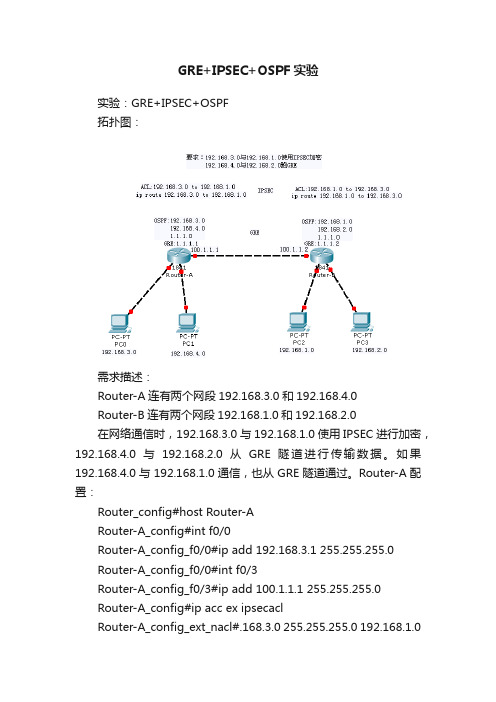
GRE+IPSEC+OSPF实验实验:GRE+IPSEC+OSPF拓扑图:需求描述:Router-A连有两个网段192.168.3.0和192.168.4.0Router-B连有两个网段192.168.1.0和192.168.2.0在网络通信时,192.168.3.0与192.168.1.0使用IPSEC进行加密,192.168.4.0与192.168.2.0从GRE隧道进行传输数据。
如果192.168.4.0与192.168.1.0通信,也从GRE隧道通过。
Router-A配置:Router_config#host Router-ARouter-A_config#int f0/0Router-A_config_f0/0#ip add 192.168.3.1 255.255.255.0Router-A_config_f0/0#int f0/3Router-A_config_f0/3#ip add 100.1.1.1 255.255.255.0Router-A_config#ip acc ex ipsecaclRouter-A_config_ext_nacl#.168.3.0 255.255.255.0 192.168.1.0255.255.255.0Router-A_config#ip route 192.168.1.0 255.255.255.0 100.1.1.2Router-A_config#crypto ipsec tr aRouter-A_config_crypto_trans#tr ah-md5 esp-3deRouter-A_config_crypto_trans#exitRouter-A_config#crypto isakmp key 123456 100.1.1.2Router-A_config#crypto isakmp policy 1Router-A_config_isakmp#hash md5Router-A_config_isakmp#hash md5Router-A_config_isakmp#exitRouter-A_config#crypto map mm 1 ipsec-isakmpRouter-A_config_crypto_map#set peer 100.1.1.2Router-A_config_crypto_map#set tr aRouter-A_config_crypto_map#match add ipsecaclRouter-A_config_crypto_map#exitRouter-A_config#int f0/3Router-A_config_f0/3#crypto map mmRouter-A_config#router ospf 1Router-A_config_ospf_1#network 192.168.3.0 255.255.255.0 area 0 Router-A_config_ospf_1#network 192.168.4.0 255.255.255.0 area 0 Router-A_config_ospf_1#network 1.1.1.0 255.255.255.0 area 0Router-A_config#int tunnel 1Router-A_config_t1#ip add 1.1.1.1 255.255.255.0Router-A_config_t1#tu so 100.1.1.1Router-A_config_t1#tu de 100.1.1.2Router-B配置Router_config#host Router-BRouter-B_config#int f0/0Router-B_config_f0/0#ip add 192.168.1.1 255.255.255.0Router-B_config_f0/0#exitRouter-B_config#int g0/3Router-B_config_g0/3#ip add 100.1.1.2 255.255.255.0Router-B_config_g0/3#exitRouter-B_config#ip route 192.168.3.0 255.255.255.0 100.1.1.1Router-B_config#ip acc ex ipsecaclRouter-B_config_ext_nacl#.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0 Router-B_config_ext_nacl#exitRouter-B_config#crypto ipsec tr aRouter-B_config_crypto_trans#tr ah-md5 esp-3deRouter-B_config_crypto_trans#exitRouter-B_config#crypto isakmp key 123456 100.1.1.1Router-B_config#crypto isakmp policy 1Router-B_config_isakmp#hash md5Router-B_config_isakmp#exitRouter-B_config#crypto map mm 1 ipsec-isakmpRouter-B_config_crypto_map#set peer 100.1.1.1Router-B_config_crypto_map#set tr aRouter-B_config_crypto_map#match add ipsecaclRouter-B_config_crypto_map#exitRouter-B_config#int g0/3Router-B_config_g0/3#crypto map mmRouter-B_config#int tunnel 1Router-B_config_t1#ip add 1.1.1.2 255.255.255.0Router-B_config_t1#tu so 100.1.1.2Router-B_config_t1#tu de 100.1.1.1Router-B_config#router ospf 1Router-B_config_ospf_1#network 192.168.1.0 255.255.255.0area 0Router-B_config_ospf_1#network 192.168.2.0 255.255.255.0 area 0Router-B_config_ospf_1#network 1.1.1.0 255.255.255.0 area 0测试:1、在192.168.3.2上和192.168.1.2做连通性测试,测试机为192.168.1.2路由追踪,显示是由物理接口通过显示ipsec有数据通过2、在192.168.4.2上和192.168.2.2做连通性测试,测试机为192.168.2.2由于路由器都有两个接口,在做第二次测试时,要重新配置路由器接PC口IP。
gre over ipsec 穿越nat
MSR系列路由器
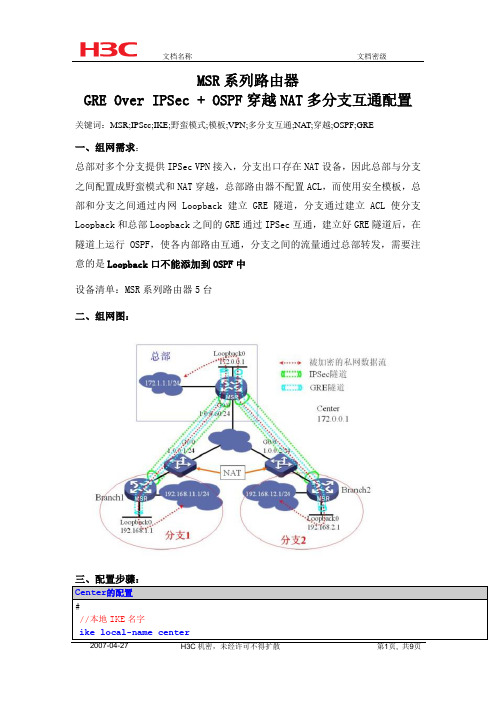
GRE Over IPSec + OSPF穿越NAT多分支互通配置关键词:MSR;IPSec;IKE;野蛮模式;模板;VPN;多分支互通;NA T;穿越;OSPF;GRE
一、组网需求:
总部对多个分支提供IPSec VPN接入,分支出口存在NAT设备,因此总部与分支之间配置成野蛮模式和NAT穿越,总部路由器不配置ACL,而使用安全模板,总部和分支之间通过内网Loopback建立GRE隧道,分支通过建立ACL使分支Loopback和总部Loopback之间的GRE通过IPSec互通,建立好GRE隧道后,在隧道上运行OSPF,使各内部路由互通,分支之间的流量通过总部转发,需要注意的是Loopback口不能添加到OSPF中
设备清单:MSR系列路由器5台
二、组网图:
三、配置步骤:
四、配置关键点:
1) 大部分配置参考IPSec VPN多分支NAT穿越模板方式功能的配置;
2) 分支的ACL可以配置成精确的GRE流量;
3) 建立GRE隧道的地址必须是内网地址;
4) 不能将建立GRE隧道连接的Loopback接口加入到OSPF,否则连接会失效。
华为路由器 IPSec 与 GRE 结合实验

华为路由器 IPSec 与 GRE 结合实验大家好,今天给大家带来的是华为GRE/I P SEC,本篇文章也是应粉丝要求所写。
直接开始:l二者结合的目的GRE支持单播、组播、广播,I P S ec仅支持单播。
GRE不支持对于数据完整性以及身份认证的验证功能,并且也不具备数据加密保护。
而I P S ec恰恰拥有强大的安全机制。
达到了互补的功效!GREGRE (G eneric Routing E ncapsulation, 通用路由封装)协议是对某些网络层协议(I P X, AppleTalk, I P, I P S ec, DVMRP, etc.)的数据报文进行封装,使这些被封装的数据报文能够在另一个网络层协议(如I P)中传输。
GRE采用了Tunnel(隧道)技术,是VPN(Virtual P rivate Network)的第三层隧道协议。
IPSecN o . Tim eS o u r c e D es t i n a t i o n Pr o t o c o I I n fo 1 0.000000202.100.1.1 61.128.1.1 ESP ESP (SP I =O x 9a63f8d b ) 2 0. 01500061. 128.1.1 202.100.1.1 ESP ESP (S P I =O x 1a 669ddd ) 3 0. 499000202.100.1.1 61.128.1.1 ESP ES P (S P I =O x9a 63f8d b ) 4 0. 51400061.128.1.1 202.100.1.1 ESP ESP (S P I =Ox 1a 669ddd ) 5 0. 998000202.100.1.1 61. 128.1.1 E S P ESP (SP I =O x 9a 63f 8db ) 6 1. 01400061.128.1.1 202.100.1.1 ESP ESP (S P I =O x 1a 669ddd ) 7 1. 513000202.100.1.1 61.128.1.1 E S P E S P (S P I =O x 9a 63f 8db ) 8 1. 51300061.128.1.1 202.100.1.1 ESP ESP (S P I =O x 1a669d dd ) 9 2. 012000202.100.1.1 61.128.1.1 ESP ESP (S P I =O x 9a63f 8d b ) 10 2. 012000 61.128.1.1 202.100.1.1 ESP ESP (S P I =O x.l a669dd d )田F r am e 1: 182 bytes o n w i r e (1456 b i ts ), 182 bytes c apt u r e d (1456 b i ts )曰E t h er n et II, s rc : H u a w ei T e _f9: 5e :lc (OO :eo :fc :f9: 5e :l c ), Dst: H u a w ei T e _a2:25: 52 (OO :eo :fc :a2:25: 52) 田De s t i n at i o n:H u a w ei T e _a2:25:52 (OO :e 0:f c :a 2:25:52)田s o u r ce :H u a w ei T e _f9:5e :l c (OO :e O :fc :f9:5e :l c )Ty p e : I P (O x 0800)曰I nt e r n e t Prot o c o l , s rc: 202.100.1.1 (202.100.1.1), Dst: 61.128.1.1 (61.128.1.1)v e rs 1o n : 4He ad e r 7 e n g t h : 20 b yt es田D if fere n ti ate d se r v i ces F ie l d : OxcO (DS CP Ox 30: class selector 6; E C N : OxOO )T o t a l L e n g t h : 168I d e n t i f icatio n: O x0004 (4)田F la g s :Ox 00F r ag m e n t of fs e t : O0000 00 eO fc a2 25 52 00 eO fc f9 5e le 08 00 45 co 0010 00 a8 00 04 00 00 fe 32 bl 79 ca 64 01 01 3d 80 0020 01 01 0030 0040 0050 0060 0070 0080 0090 oo a o OObO 吓40105555 6000012a 0a 5b 0444b 4c 470012a 97210333a e 1d 000125 a 241b 222b e 3003012d 0f 013111a 200601242f 0b e 0000 6f 07d 0124000304f f 4 00090b 010 00841b e e 6 000b 0a 0100101b 6d d 60100a 00104鹹f 0f f c c c 5002f c 9010 01054b b 44 000a b 0104 8010g e a a 30 700a 40100 3000099929 6c 81040104a 5d f 80881b 943005010b 814207773 05000122a 10106669 00000120 疆赡.. P I N ... _ 艾j网络抸木干货图,_ ... 薯'OJ-纽二旗反E 卢问I跷干。
ospf+gre+ipsec+l2tp研究
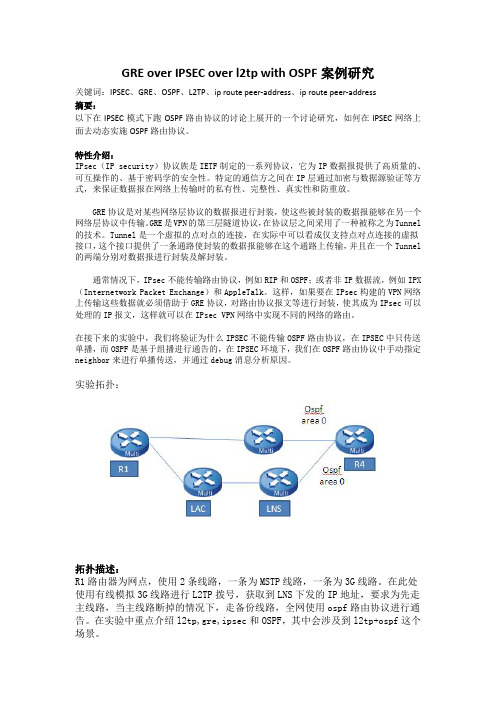
GRE over IPSEC over l2tp with OSPF案例研究关键词:IPSEC、GRE、OSPF、L2TP、ip route peer-address、ip route peer-address摘要:以下在IPSEC模式下跑OSPF路由协议的讨论上展开的一个讨论研究,如何在IPSEC网络上面去动态实施OSPF路由协议。
特性介绍:IPsec(IP security)协议族是IETF制定的一系列协议,它为IP数据报提供了高质量的、可互操作的、基于密码学的安全性。
特定的通信方之间在IP层通过加密与数据源验证等方式,来保证数据报在网络上传输时的私有性、完整性、真实性和防重放。
GRE协议是对某些网络层协议的数据报进行封装,使这些被封装的数据报能够在另一个网络层协议中传输。
GRE是VPN的第三层隧道协议,在协议层之间采用了一种被称之为Tunnel 的技术。
Tunnel是一个虚拟的点对点的连接,在实际中可以看成仅支持点对点连接的虚拟接口,这个接口提供了一条通路使封装的数据报能够在这个通路上传输,并且在一个Tunnel 的两端分别对数据报进行封装及解封装。
通常情况下,IPsec不能传输路由协议,例如RIP和OSPF;或者非IP数据流,例如IPX (Internetwork Packet Exchange)和AppleTalk。
这样,如果要在IPsec构建的VPN网络上传输这些数据就必须借助于GRE协议,对路由协议报文等进行封装,使其成为IPsec可以处理的IP报文,这样就可以在IPsec VPN网络中实现不同的网络的路由。
在接下来的实验中,我们将验证为什么IPSEC不能传输OSPF路由协议,在IPSEC中只传送单播,而OSPF是基于组播进行通告的,在IPSEC环境下,我们在OSPF路由协议中手动指定neighbor来进行单播传送,并通过debug消息分析原因。
实验拓扑:拓扑描述:R1路由器为网点,使用2条线路,一条为MSTP线路,一条为3G线路。
GRE_IPSEC_VPN_试验

第一节 Gre VPN一.按照以上拓扑先把网络配置好,但不要设置路由。
PC1和 PC2不能相互ping 通二.路由器A 上配置:1.R-A (config )#interface tunnel 1 //创建序号为1的通道2.R-A (config-if )#ip address 3.3.3.1 255.255.255.0 //为通道设置ip 地址。
3.R-A (config-if )# tunnel source 2.2.2.1 //设置创建通道使用的真实源地址。
4.R-A (config-if )# tunnel destination 2.2.2.2 //设置创建通道使用的真实目的地址。
5.R-A (config-if )# tunnel mode gre ip //设置通道封装协议为gre6.R-A (config )#ip route 0.0.0.0 0.0.0.0 3.3.3.2 //使用通道地址作为路由目标地址。
三.路由器B 重复以上设置。
四.测试,PC1和 PC2可以相互ping 通。
7.R-A (config-if )# tunnel key 123456 //给R-A 设置通道key ,PC1断开PC2。
8.R-B (config-if )# tunnel key 123456 //给R-B 设置通道key ,PC1连通PC2。
9.R-A#debug tunnel 1 //显示tunnel 通信信息,刷新很快,不容易停止,断网后隔一段时间会停下来。
10.R-A#show ip interface brief //显示接口信息R-A#show ip interface brief tunnel 1***********************Interface IP-Address OK? Method Status ProtocolTunnel1 3.3.3.1 YES manual up up************************以上显示配置隧道成功。
网络设备安装与调试chp24GRE和IPSec-VPN_24.1GRE工作原理和配置实验指导

GRE配置1.实验目的通过本实验可以掌握:① GRE工作原理② GRE Tunnel的配置2.实验拓扑实验拓扑如图所示。
任务:两地已经度连上了internet,现要把两个的网络通过Internet进行互联,使用GRE TUNNEL。
3.实验步骤1)R1、R2、R3上如图配置IP地址,打开接口,配置路由:RouterA(R1):R1(config)#int s1/1R1(config-if)#no shutdownR1(config-if)#clock rate 128000R1(config-if)#ip add 202.96.134.1 255.255.255.252R1(config)#int loopback0R1(config-if)#ip add 10.1.1.1 255.255.255.0R1(config-if)#ip route 0.0.0.0 0.0.0.0 s1/1Internet(R2):R2(config)#int s1/0R2(config-if)#no shutdownR2(config-if)#clock rate 128000R2(config-if)#ip add 202.96.134.2 255.255.255.252R2(config)#int s1/1R2(config-if)#no shutdownR2(config-if)#clock rate 128000R2(config-if)#ip add 61.0.0.1 255.255.255.252RouterB(R3):R3(config)#int s1/0R3(config-if)#no shutdownR3(config-if)#clock rate 128000R3(config-if)#ip add 61.0.0.02 255.255.255.252R3(config)#int loopback0R3(config-if)#ip add 10.2.2.2 255.255.255.0R3(config-if)#ip route 0.0.0.0 0.0.0.0 s1/02)配置GRE TUNNEL:R1:R1(config)#interface Tunnel1R1(config-if)#ip address 10.13.13.1 255.255.255.0R1(config-if)#tunnel source Serial1/1R1(config-if)#tunnel destination 61.0.0.2R3:R3(config)#interface Tunnel1R3(config-if)#ip address 10.13.13.3 255.255.255.0R3(config-if)#tunnel source Serial1/0R3(config-if)#tunnel destination 202.96.134.13)配置路由协议:R1:R1(config-if)#router ripR1(config-router)#network 10.0.0.0R3:R3(config-if)#router ripR3(config-router)#network 10.0.0.04. 实验调试R1/R3上,检查路由表,并从自己的loopback接口ping对方的loopback接口。
网络设备安装与调试chp24GRE和IPSec-VPN_24.2IPSecVPN实验指导

IPSec VPN配置1.实验目的通过本实验可以掌握:① IPSec VPN的原理② IPSec VPN的配置2.实验拓扑实验拓扑如图所示。
任务:两地已经度连上了internet,现要把两个的网络通过Internet进行互联。
数据在Internet传输时要保证安全性,使用Site To Site VPN。
3.实验步骤1)R1、R2、R3上如图配置IP地址,打开接口,配置路由:RouterA(R1):enconf thost R1int s1/1no shutdownclock rate 128000ip add 202.96.134.1 255.255.255.252int loopback0ip add 10.1.1.1 255.255.255.0ip route 0.0.0.0 0.0.0.0 s1/1Internet(R2):enconf thost Internetint s1/0no shutdownclock rate 128000ip add 202.96.134.2 255.255.255.252int s1/1no shutdownclock rate 128000ip add 61.0.0.1 255.255.255.252RouterB(R3):enconf thost R3int s1/0no shutdownclock rate 128000ip add 61.0.0.02 255.255.255.252int loopback0ip add 10.2.2.2 255.255.255.0ip route 0.0.0.0 0.0.0.0 s1/02)配置RouterA(R1):R1(config)#crypto isakmp policy 10R1(config-isakmp)# hash md5R1(config-isakmp)# authentication pre-shareR1(config-isakmp)#crypto isakmp identity addressR1(config)#crypto isakmp key 0 cisco1234 address 61.0.0.2R1(config)#crypto ipsec transform-set TEST-TRAN esp-des esp-md5-hmacR1(cfg-crypto-trans)#crypto ipsec security-association lifetime seconds 86400 R1(config)#access-list 110 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255 R1(config)#crypto map TEST-MAP 10 ipsec-isakmpR1(config-crypto-map)# set peer 61.0.0.2R1(config-crypto-map)# set transform-set TEST-TRANR1(config-crypto-map)# match address 110R1(config-crypto-map)# set security-association lifetime seconds 1200R1(config)#interface Serial1/1R1(config-if)# crypto map TEST-MAP3)配置RouterB(R3)R3(config)#crypto isakmp enableR3(config)#crypto isakmp policy 10R3(config-isakmp)# hash md5R3(config-isakmp)# authentication pre-shareR3(config-isakmp)#crypto isakmp identity addressR3(config)#crypto isakmp key 0 cisco1234 address 202.96.134.1R3(config)#crypto ipsec transform-set TEST-TRAN esp-des esp-md5-hmacR3(cfg-crypto-trans)#crypto ipsec security-association lifetime seconds 86400 R3(config)#access-list 110 permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255R3(config)#crypto map TEST-MAP 10 ipsec-isakmpR3(config-crypto-map)# set peer 202.96.134.1R3(config-crypto-map)# set transform-set TEST-TRANR3(config-crypto-map)# match address 110R3(config-crypto-map)# set security-association lifetime seconds 1200R3(config)#interface Serial1/0R3(config-if)# crypto map TEST-MAP4. 实验调试从RouterA的loopback0接口ping RouterB的loopback0RouterA:ping 10.2.2.2 source 10.1.1.1RouterB:ping 10.1.1.1 source 10.2.2.2◆show crypto isakmp policyR1#show crypto isakmp policyGlobal IKE policyProtection suite of priority 10encryption algorithm: DES - Data Encryption Standard (56 bit keys). hash algorithm: Message Digest 5authentication method: Pre-Shared KeyDiffie-Hellman group: #2 (1024 bit)lifetime: 86400 seconds, no volume limitDefault protection suiteencryption algorithm: DES - Data Encryption Standard (56 bit keys). hash algorithm: Secure Hash Standardauthentication method: Rivest-Shamir-Adleman SignatureDiffie-Hellman group: #1 (768 bit)lifetime: 86400 seconds, no volume limit◆show cry ipsec transform-setR1#show crypto ipsec transform-setTransform set TRAN: { esp-des esp-md5-hmac }will negotiate = { Tunnel, },◆show crypto mapR1#show crypto mapCrypto Map "MAP" 10 ipsec-isakmpPeer = 61.0.0.2Extended IP access list 100access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255 Current peer: 61.0.0.2Security association lifetime: 4608000 kilobytes/3600 secondsPFS (Y/N): NTransform sets={TRAN,}Interfaces using crypto map MAP:Serial1/1◆show crypto isakmp sa◆show crypto ipsec sa◆show crypto engine connections active:看加密、解密数据包数量R1#show crypto engine connections activeID Interface IP-Address State Algorithm Encrypt Decrypt1 Serial1/1 202.96.134.1 set HMAC_MD5+DES_56_CB 0 02001 Serial1/1 202.96.134.1 set DES+MD5 0 192002 Serial1/1 202.96.134.1 set DES+MD5 19 0◆clear crypto sa◆clear crypto isakmp5. 完整配置===============================R2===============================!version 12.4service timestamps debug datetime msecservice timestamps log datetime msecno service password-encryption!hostname R2!boot-start-markerboot-end-marker!!no aaa new-modelmemory-size iomem 5!!ip cef!!!!!!!!!!!!!!!!!!!!!!!!interface Ethernet0/0no ip addressshutdownhalf-duplex!interface Ethernet0/1no ip addressshutdownhalf-duplex!interface Ethernet0/2no ip addressshutdownhalf-duplex!interface Ethernet0/3no ip addressshutdownhalf-duplex!interface Serial1/0ip address 202.96.134.2 255.255.255.252 serial restart-delay 0clock rate 128000no fair-queue!interface Serial1/1ip address 61.0.0.1 255.255.255.252serial restart-delay 0clock rate 128000!interface Serial1/2no ip addressshutdownserial restart-delay 0 !interface Serial1/3no ip addressshutdownserial restart-delay 0 !ip http serverno ip http secure-server !!!!!!control-plane!!!!!!!!!!line con 0line aux 0line vty 0 4!!End。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
实例1 站点-站点IPSEC VPN+NA T+策略路由配置要求:(1)网络10.2.2.0/24 与10.1.1.0/2通信使用VPN(2)网络10.2.2.0/24 、10.1.1.0/2与Internet通信使用NA T1.R1的配置hostname r1!!crypto isakmp policy 10hash md5authentication pre-sharecrypto isakmp key cisco123 address 200.1.1.2!!crypto ipsec transform-set myset esp-des esp-md5-hmac!crypto map mymap 10 ipsec-isakmpset peer 200.1.1.2set transform-set mysetmatch address 100!interface Ethernet0/0ip address 10.2.2.1 255.255.255.0ip nat insideip virtual-reassemblyhalf-duplex!interface Ethernet0/1ip address 100.1.1.1 255.255.255.0ip nat outsidecrypto map mymap!ip route 0.0.0.0 0.0.0.0 100.1.1.2!ip nat inside source route-map nonat interface Ethernet0/1 overload !access-list 100 permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255 access-list 120 deny ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255 access-list 120 permit ip 10.2.2.0 0.0.0.255 any!route-map nonat permit 10match ip address 120!2.R3的配置:hostname r3!crypto isakmp policy 10hash md5authentication pre-sharecrypto isakmp key cisco123 address 100.1.1.1!!crypto ipsec transform-set myset esp-des esp-md5-hmac!crypto map mymap 10 ipsec-isakmpset peer 100.1.1.1set transform-set mysetmatch address 100!interface Ethernet0/0ip address 10.1.1.1 255.255.255.0ip nat inside!interface Ethernet0/1ip address 200.1.1.2 255.255.255.0ip nat outsidecrypto map mymap!ip route 0.0.0.0 0.0.0.0 200.1.1.1!ip nat inside source route-map nonat interface Ethernet0/1 overload!access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255access-list 120 deny ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255access-list 120 permit ip 10.1.1.0 0.0.0.255 any!route-map nonat permit 10match ip address 120!3.R2的配置hostname r2!interface Ethernet0/0ip address 200.2.2.1 255.255.255.0!interface Ethernet0/1ip address 100.1.1.2 255.255.255.0!interface Ethernet0/2ip address 200.1.1.1 255.255.255.0测试:r1#show crypto isakmp sadst src state conn-id slot status100.1.1.1 200.1.1.2 QM_IDLE 1 0 ACTIVE r1#show crypto ipsec sainterface: Ethernet0/1Crypto map tag: mymap, local addr 100.1.1.1protected vrf: (none)local ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)current_peer 200.1.1.2 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 149, #pkts encrypt: 149, #pkts digest: 149#pkts decaps: 64, #pkts decrypt: 64, #pkts verify: 64#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 100.1.1.1, remote crypto endpt.: 200.1.1.2 path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/1current outbound spi: 0xD81B7A10(3625679376)inbound esp sas:spi: 0x124FC348(307217224)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }conn id: 2001, flow_id: SW:1, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4418170/856)IV size: 8 bytesreplay detection support: YStatus: ACTIVEinbound ah sas:inbound pcp sas:outbound esp sas:spi: 0xD81B7A10(3625679376)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }conn id: 2002, flow_id: SW:2, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4418155/848)IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound ah sas:outbound pcp sas:实例2:GRE over IPSEC VPN+NA T+策略路由配置r1#show runhostname r1!crypto isakmp policy 10hash md5authentication pre-sharecrypto isakmp key cisco123 address 200.1.1.2!!crypto ipsec transform-set myset esp-des esp-md5-hmacmode transport!crypto map mymap 10 ipsec-isakmpset peer 200.1.1.2set transform-set mysetmatch address 100!interface Tunnel0ip address 192.168.1.1 255.255.255.252tunnel source 100.1.1.1tunnel destination 200.1.1.2!interface Ethernet0/0ip address 10.2.2.1 255.255.255.0ip nat insideip virtual-reassemblyhalf-duplex!interface Ethernet0/1ip address 100.1.1.1 255.255.255.0ip nat outsideip virtual-reassemblyhalf-duplexcrypto map mymap!ip route 0.0.0.0 0.0.0.0 100.1.1.2ip route 10.1.1.0 255.255.255.0 Tunnel0!ip nat inside source route-map nonat interface Ethernet0/1 overload !access-list 100 permit ip host 100.1.1.1 host 200.1.1.2access-list 120 deny ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255 access-list 120 permit ip 10.2.2.0 0.0.0.255 any!route-map nonat permit 10match ip address 120!r3#show run!hostname r3!!crypto isakmp policy 10hash md5authentication pre-sharecrypto isakmp key cisco123 address 100.1.1.1!!crypto ipsec transform-set myset esp-des esp-md5-hmacmode transport!crypto map mymap 10 ipsec-isakmpset peer 100.1.1.1set transform-set mysetmatch address 100!interface Tunnel0ip address 192.168.1.2 255.255.255.252tunnel source 200.1.1.2tunnel destination 100.1.1.1!interface Ethernet0/0ip address 10.1.1.1 255.255.255.0ip nat insideip virtual-reassemblyhalf-duplex!interface Ethernet0/1ip address 200.1.1.2 255.255.255.0ip nat outsideip virtual-reassemblyhalf-duplexcrypto map mymap!ip route 0.0.0.0 0.0.0.0 200.1.1.1ip route 10.2.2.0 255.255.255.0 Tunnel0!ip nat inside source route-map nonat interface Ethernet0/1 overload !access-list 100 permit ip host 200.1.1.2 host 100.1.1.1access-list 120 deny ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255 access-list 120 permit ip 10.1.1.0 0.0.0.255 any!route-map nonat permit 10match ip address 120!测试:r3#show crypto isakmp sadst src state conn-id slot status100.1.1.1 200.1.1.2 QM_IDLE 1 0 ACTIVE r3#show crypto ipsec sainterface: Ethernet0/1Crypto map tag: mymap, local addr 200.1.1.2protected vrf: (none)local ident (addr/mask/prot/port): (200.1.1.2/255.255.255.255/0/0)remote ident (addr/mask/prot/port): (100.1.1.1/255.255.255.255/0/0)current_peer 100.1.1.1 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20#pkts decaps: 20, #pkts decrypt: 20, #pkts verify: 20#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 200.1.1.2, remote crypto endpt.: 100.1.1.1 path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/1current outbound spi: 0xB147A485(2974262405)inbound esp sas:spi: 0xAC202182(2887786882)transform: esp-des esp-md5-hmac ,in use settings ={Transport, }conn id: 2004, flow_id: SW:4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4576701/3131)IV size: 8 bytesreplay detection support: YStatus: ACTIVEinbound ah sas:inbound pcp sas:outbound esp sas:spi: 0xB147A485(2974262405)transform: esp-des esp-md5-hmac ,in use settings ={Transport, }conn id: 2003, flow_id: SW:3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4576700/3130)IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound ah sas:outbound pcp sas:r3#show interfaces tunnel 0Tunnel0 is up, line protocol is upHardware is TunnelInternet address is 192.168.1.2/30MTU 1514 bytes, BW 9 Kbit, DLY 500000 usec,reliability 255/255, txload 1/255, rxload 1/255 Encapsulation TUNNEL, loopback not setKeepalive not setTunnel source 200.1.1.2, destination 100.1.1.1Tunnel protocol/transport GRE/IPKey disabled, sequencing disabledChecksumming of packets disabledTunnel TTL 255Fast tunneling enabledTunnel transmit bandwidth 8000 (kbps)Tunnel receive bandwidth 8000 (kbps)Last input 00:09:41, output 00:09:41, output hang neverLast clearing of "show interface" counters neverInput queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifoOutput queue: 0/0 (size/max)5 minute input rate 0 bits/sec, 0 packets/sec5 minute output rate 0 bits/sec, 0 packets/sec20 packets input, 2244 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants, 0 throttles0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort20 packets output, 2484 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 output buffer failures, 0 output buffers swapped out。
