思科4506配置手册
思科AnyConnect安全移动客户端4.6版本说明书

思科系统公司 AnyConnect 安全移动客户端功能、许可证和操作系统,版本 4.6本文档将介绍 AnyConnect 4.6 版本的功能、许可证要求和 AnyConnect 功能支持的终端操作系统。
支持的操作系统思科 AnyConnect 安全移动客户端 4.6 支持以下操作系统。
*要将 AnyConnect 用于 macOS 10.13 (High Sierra),您必须执行手动流程才能使用 AnyConnect 的完整功能。
AnyConnect 4.5.02033 会通过提示信息来逐步引导您完成相关流程。
在 AnyConnect 4.5.02033 安装期间,系统会显示“系统扩展被阻止”消息。
这表示,如果要启用此内核扩展,必须打开“安全和隐私系统首选项”。
点击此消息中的“确定”,系统会弹出一个窗口,用于详细说明启用系统扩展需要注意的事项。
该窗口将提示您打开首选项并允许“安全和隐私”屏幕中的思科系统软件。
AnyConnect 版本 4.3.3086 和 4.2.6014 是 macOS 10.12 支持要求的最低版本。
注: 思科不再支持适用于 Windows XP 的 AnyConnect 版本。
有关操作系统要求和支持说明,请参阅思科 AnyConnect 安全移动客户端版本说明。
有关许可条款和条件,请参阅补充最终用户协议 (SEULA)。
有关各类许可证的订购信息明细以及具体条款和条件,请参阅思科 AnyConnect 订购指南。
有关适用于 AnyConnect 模块和功能的许可证信息及操作系统限制,请参阅以下功能表。
AnyConnect 4.3(及更高版本)已移至 Visual Studio (VS) 2015 版本环境,并且需要可再分发的 VS 文件以实现其网络访问管理器模块的功能。
这些文件作为安装文件包的组成部分安装。
您可以使用 .msi 文件将网络访问管理器模块升级到 4.3(或更高版本),但必须先升级 AnyConnect Security Mobility Client 并运行版本 4.3(或更高版本)。
思科4506路由器全网络配置方案

思科4506全网络配置方案1. 网络拓扑2. 配置文档中心机房配置2台Catalyst4506,互为冗余备份,通过一台PIX525防火墙连接互联网。
接入互换机配置Catalyst3750/3560,每台接入互换机配置2条TRUNK端口,别离连接到核心互换机。
整个网络部署9个Vlan,Vlan1为管理vlan,其余8个Vlan为用户Vlan。
每一个用户Vlan分派一个C类ip地址段,其中为网关,保留为手动ip配置,作为dhcp动态分派的Vlan用户利用。
设备名称管理ip备注Sw4500-1网管服务器(1)主核心互换机Catalyst4506配置。
SW4500-1#SW4500-1#wr tBuilding configuration...Current configuration : 9687 bytes!versionno service padservice timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice compress-config!hostname SW4500-1!boot-start-markerboot system flash bootflash: secret cisco!no aaa new-modelip subnet-zerono ip domain-lookupip host fw host sw2 dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp pool vlan2lease 0 8!ip dhcp pool vlan3network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan4network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan5network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan6network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan7network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan8network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan9network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan10network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan1lease 0 8!!!!power redundancy-mode redundantno file verify auto!spanning-tree mode pvstspanning-tree extend system-id spanning-tree vlan 1-10 priority 24576 !vlan internal allocation policy ascending !interface GigabitEthernet1/1!interface GigabitEthernet1/2!interface GigabitEthernet2/1 description LinkToSW4500-2 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/2 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/3 switchport mode trunk!interface GigabitEthernet2/4 switchport mode trunk!interface GigabitEthernet2/5 switchport mode trunk!interface GigabitEthernet2/6 switchport mode trunk!interface GigabitEthernet2/7 switchport mode trunk!interface GigabitEthernet2/8!interface GigabitEthernet2/9 switchport mode trunk!interface GigabitEthernet2/10 switchport mode trunk!interface GigabitEthernet2/11 switchport mode trunk!interface GigabitEthernet2/12 switchport mode trunk!interface GigabitEthernet2/13 switchport mode trunk!interface GigabitEthernet2/14 switchport mode trunk!interface GigabitEthernet2/15 switchport mode trunk!interface GigabitEthernet2/16 switchport mode trunk!interface GigabitEthernet2/17 switchport mode trunk!interface GigabitEthernet2/18 switchport mode trunk!interface GigabitEthernet3/1 description LinkToFirewall switchport mode access spanning-tree portfast!interface GigabitEthernet3/2 switchport mode access spanning-tree portfast!interface GigabitEthernet3/3 description Cisco net manager switchport mode access spanning-tree portfastinterface GigabitEthernet3/4 switchport mode access spanning-tree portfast!interface GigabitEthernet3/5 switchport mode access spanning-tree portfast!interface GigabitEthernet3/6 switchport mode access spanning-tree portfast!interface GigabitEthernet3/7 switchport mode access spanning-tree portfast!interface GigabitEthernet3/8 switchport mode access spanning-tree portfast!interface GigabitEthernet3/9 switchport mode access spanning-tree portfast!interface GigabitEthernet3/10 switchport mode access spanning-tree portfast!interface GigabitEthernet3/11 switchport mode access spanning-tree portfast!interface GigabitEthernet3/12 switchport mode access spanning-tree portfast!interface GigabitEthernet3/13 switchport mode access spanning-tree portfast!interface GigabitEthernet3/14 switchport mode access spanning-tree portfast!switchport mode access spanning-tree portfast!interface GigabitEthernet3/16 switchport mode access spanning-tree portfast!interface GigabitEthernet3/17 switchport mode access spanning-tree portfast!interface GigabitEthernet3/18 switchport mode access spanning-tree portfast!interface GigabitEthernet3/19 switchport mode access spanning-tree portfast!interface GigabitEthernet3/20 switchport mode access spanning-tree portfast!interface GigabitEthernet3/21 switchport mode access spanning-tree portfast!interface GigabitEthernet3/22 switchport mode access spanning-tree portfast!interface GigabitEthernet3/23 switchport mode access spanning-tree portfast!interface GigabitEthernet3/24 switchport mode access spanning-tree portfast!interface GigabitEthernet3/25 switchport mode access spanning-tree portfast!interface GigabitEthernet3/26spanning-tree portfast!interface GigabitEthernet3/27 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/28 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/29 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/30 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/31 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/32 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/33!interface GigabitEthernet3/34!interface GigabitEthernet3/35!interface GigabitEthernet3/36!interface GigabitEthernet3/37!interface GigabitEthernet3/38!interface GigabitEthernet3/39!interface GigabitEthernet3/40!interface GigabitEthernet3/41 switchport trunk encapsulation dot1q!interface GigabitEthernet3/42switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/43switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/44switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/45switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/46switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/47switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/48switchport trunk encapsulation dot1q switchport mode trunk!interface Vlan1ip address standby 1 ip standby 1 preempt !interface Vlan2ip address standby 1 ip standby 1 preempt!interface Vlan3ip address standby 1 ip standby 1 preempt!interface Vlan4ip address standby 1 ip standby 1 preempt!interface Vlan5ip address standby 1 ip standby 1 preempt!ip address standby 1 ip standby 1 preempt!interface Vlan7ip address standby 1 ip standby 1 preempt!interface Vlan8ip address standby 1 ip standby 1 preempt!interface Vlan9ip address standby 1 ip standby 1 preempt!ip route 0.0.0.0 http server!!!snmp-server community public-nm ROsnmp-server community private-nm RWsnmp-server chassis-idsnmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps ttysnmp-server enable traps fru-ctrlsnmp-server enable traps entitysnmp-server enable traps flash insertion removalsnmp-server enable traps cpu thresholdsnmp-server enable traps vtpsnmp-server enable traps vlancreatesnmp-server enable traps vlandeletesnmp-server enable traps envmon fan shutdown supply temperature statussnmp-server enable traps port-securitysnmp-server enable traps rfsnmp-server enable traps config-copysnmp-server enable traps configsnmp-server enable traps hsrpsnmp-server enable traps ipmulticastsnmp-server enable traps mac-notification change move thresholdsnmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message snmp-server enable traps bridge newroot topologychangesnmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistency snmp-server enable traps syslogsnmp-server enable traps vlan-membershipsnmp-server host public-nm!control-plane!line con 0stopbits 1line vty 0 4password ciscologin!endSW4500-1# sh cdp neiCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDSW4500-2 Gig 2/1 136 R S I WS-C4506 Gig 2/1 bangonglou2 Gig 3/48 162 S I WS-C3750G Gig 1/0/23 bangonglou1 Gig 3/47 126 S I WS-C3750G Gig 1/0/23SW4500-1#sw2Trying sw2 OpenUser Access VerificationPassword:SW4500-2>enPassword:SW4500-2#wr tBuilding configuration...Current configuration : 9011 bytes!versionno service padservice timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice compress-config!hostname SW4500-2!boot-start-markerboot system flash bootflash: secret 5 $1$qdQu$9POGVGQrtfz7hMOiRKf/k.!ip subnet-zerono ip domain-lookupip host sw1 dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp excluded-address dhcp pool vlan2network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan3network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan4network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan5network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan6network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan7network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan8network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan9network dns-serverdefault-routerlease 0 8ip dhcp pool vlan10network dns-serverdefault-routerlease 0 8!ip dhcp pool vlan1network dns-serverdefault-routerlease 0 8!!!!power redundancy-mode redundantno file verify auto!spanning-tree mode pvstspanning-tree extend system-id spanning-tree vlan 1-10 priority 28672 !vlan internal allocation policy ascending !interface GigabitEthernet1/1!interface GigabitEthernet1/2!interface GigabitEthernet2/1 description LINkToSW4500-1 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/2!interface GigabitEthernet2/3!interface GigabitEthernet2/4!interface GigabitEthernet2/5!interface GigabitEthernet2/6!interface GigabitEthernet2/7!interface GigabitEthernet2/8interface GigabitEthernet2/9!interface GigabitEthernet2/10 !interface GigabitEthernet2/11 !interface GigabitEthernet2/12 !interface GigabitEthernet2/13 !interface GigabitEthernet2/14 !interface GigabitEthernet2/15 !interface GigabitEthernet2/16 !interface GigabitEthernet2/17 !interface GigabitEthernet2/18 !interface GigabitEthernet3/1 description LinkToFirewall switchport mode access spanning-tree portfast!interface GigabitEthernet3/2 switchport mode access spanning-tree portfast!interface GigabitEthernet3/3 description Cisco net manager switchport mode access spanning-tree portfast!interface GigabitEthernet3/4 switchport mode access spanning-tree portfast!interface GigabitEthernet3/5 switchport mode access spanning-tree portfast!interface GigabitEthernet3/6 switchport mode access!interface GigabitEthernet3/7 switchport mode access spanning-tree portfast!interface GigabitEthernet3/8 switchport mode access spanning-tree portfast!interface GigabitEthernet3/9 switchport mode access spanning-tree portfast!interface GigabitEthernet3/10 switchport mode access spanning-tree portfast!interface GigabitEthernet3/11 switchport mode access spanning-tree portfast!interface GigabitEthernet3/12 switchport mode access spanning-tree portfast!interface GigabitEthernet3/13 switchport mode access spanning-tree portfast!interface GigabitEthernet3/14 switchport mode access spanning-tree portfast!interface GigabitEthernet3/15 switchport mode access spanning-tree portfast!interface GigabitEthernet3/16 switchport mode access spanning-tree portfast!interface GigabitEthernet3/17 switchport mode access spanning-tree portfastinterface GigabitEthernet3/18 switchport mode access spanning-tree portfast!interface GigabitEthernet3/19 switchport mode access spanning-tree portfast!interface GigabitEthernet3/20 switchport mode access spanning-tree portfast!interface GigabitEthernet3/21 switchport mode access spanning-tree portfast!interface GigabitEthernet3/22 switchport mode access spanning-tree portfast!interface GigabitEthernet3/23 switchport mode access spanning-tree portfast!interface GigabitEthernet3/24 switchport mode access spanning-tree portfast!interface GigabitEthernet3/25 switchport mode access spanning-tree portfast!interface GigabitEthernet3/26 switchport mode access spanning-tree portfast!interface GigabitEthernet3/27 switchport mode access spanning-tree portfast!interface GigabitEthernet3/28 switchport mode access spanning-tree portfast!switchport mode accessspanning-tree portfast!interface GigabitEthernet3/30 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/31 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/32 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/33!interface GigabitEthernet3/34!interface GigabitEthernet3/35!interface GigabitEthernet3/36!interface GigabitEthernet3/37!interface GigabitEthernet3/38!interface GigabitEthernet3/39!interface GigabitEthernet3/40!interface GigabitEthernet3/41 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/42!interface GigabitEthernet3/43!interface GigabitEthernet3/44!interface GigabitEthernet3/45!interface GigabitEthernet3/46interface GigabitEthernet3/47!interface GigabitEthernet3/48!interface Vlan1ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan2ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan3ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan4ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan5ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan6ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan7ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan8ip address standby 1 ip standby 1 priority 95 standby 1 preempt!interface Vlan9ip address standby 1 ip standby 1 priority 95 standby 1 preempt!ip route 0.0.0.0 http server!!!snmp-server community private-nm RWsnmp-server chassis-idsnmp-server enable traps snmp authentication linkdown linkup coldstart warmstartsnmp-server enable traps ttysnmp-server enable traps fru-ctrlsnmp-server enable traps entitysnmp-server enable traps flash insertion removalsnmp-server enable traps cpu thresholdsnmp-server enable traps vtpsnmp-server enable traps vlancreatesnmp-server enable traps vlandeletesnmp-server enable traps envmon fan shutdown supply temperature statussnmp-server enable traps port-securitysnmp-server enable traps rfsnmp-server enable traps config-copysnmp-server enable traps configsnmp-server enable traps hsrpsnmp-server enable traps ipmulticastsnmp-server enable traps mac-notification change move thresholdsnmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message snmp-server enable traps bridge newroot topologychangesnmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistencysnmp-server enable traps syslogsnmp-server enable traps vlan-membershipsnmp-server host public-nm!control-plane!!line con 0stopbits 1line vty 0 4password ciscologin!endSW4500-2# sh cdp neiCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDSW4500-1 Gig 2/1 167 R S I WS-C4506 Gig 2/1 bangonglou2 Gig 3/48 142 S I WS-C3750G Gig 1/0/24SW4500-2#SW4500-2#SW4500-2#SW4500-2#SW4500-2#exit[Connection to sw2 closed by foreign host]SW4500-1#fwTrying fw OpenUser Access VerificationPassword:Type help or '?' for a list of available commands.YMMK-FIREWALL> enPassword: *****YMMK-FIREWALL# wr t: Saved:PIX Version (4)!hostname YMMK-FIREWALLdomain-nameenable password ciscopasswd cisconames!interface Ethernet0nameif outsidesecurity-level 0ip address!interface Ethernet1nameif insidesecurity-level 100ip address!ftp mode passivedns server-group DefaultDNSdomain-nameaccess-list intoout extended permit icmp any anyaccess-list intoout extended deny tcp any any eq 135 access-list intoout extended deny tcp any any eq netbios-ssnaccess-list intoout extended deny tcp any any eq 1025access-list intoout extended deny tcp any any eq 4444access-list intoout extended deny tcp any any eq 5554access-list intoout extended deny tcp any any eq 9996access-list intoout extended deny tcp any any eq 69access-list intoout extended deny tcp any any eq 1433access-list intoout extended deny tcp any any eq 1434access-list intoout extended permit ip any anypager lines 24mtu inside 1500mtu outside 1500no failovericmp unreachable rate-limit 1 burst-size 1icmp permit any insideicmp permit any outsideasdm image flash:/no asdm history enablearp timeout 14400global (outside) 1 interfacenat (inside) 1 (inside,outside) tcp interface 2741 1741 dnsaccess-group intoout in interface insideroute outside 0.0.0.0 1route inside 1route inside 1route inside 1route inside 1route inside 1route inside 1route inside 1route inside 1route inside 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolutedynamic-access-policy-record DfltAccessPolicyaaa authentication ssh console LOCALsnmp-server host inside community public-nmno snmp-server locationno snmp-server contactsnmp-server community public-nmsnmp-server enable traps snmp authentication linkup linkdown coldstartsnmp-server enable traps syslogcrypto ipsec security-association lifetime kilobytes 4608000telnet 0.0.0.0 insidetelnet timeout 5ssh 0.0.0.0 outsidessh timeout 20console timeout 0threat-detection basic-threatthreat-detection statistics access-listno threat-detection statistics tcp-interceptusername cisco password 3q8ZgbRKJMLMsGri encrypted!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect rtspinspect esmtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcp!service-policy global_policy globalprompt hostname contextCryptochecksum:3cf0203d19fdb4ac1e58ce9fd4c4af44: end[OK]YMMK-FIREWALL# sh routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is to network 0.0.0.0S [1/0] via insideS [1/0] via insideS [1/0] via insideC is directly connected, insideC is directly connected, outsideS [1/0] via insideS [1/0] via insideS [1/0] via insideS [1/0] via insideS [1/0] via insideS [1/0] via insideS* 0.0.0.0 [1/0] via outsideYMMK-FIREWALL# sh xlate172 in use, 389 most usedPAT Global LocalPAT Global LocalPAT Global LocalPAT Global LocalPAT Global Local…………YMMK-FIREWALL#$YMMK-FIREWALL# exiLogoff[Connection to fw closed by foreign host]SW4500-1#SW4500-1#SW4500-1#SW4500-1# ... OpenUser Access VerificationPassword:bangonglou1>enPassword:bangonglou1#wr tBuilding configuration...Current configuration : 3815 bytes!versionno service padservice timestamps debug uptime service timestamps log uptimeno service password-encryption!hostname bangonglou1!enable cisco!no aaa new-modelswitch 1 provision ws-c3750g-24t system mtu routing 1500ip subnet-zero!!!!no file verify autospanning-tree mode pvstspanning-tree extend system-id!vlan internal allocation policy ascending !interface GigabitEthernet1/0/1 switchport access vlan 8spanning-tree portfast!interface GigabitEthernet1/0/2 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/3spanning-tree portfast!interface GigabitEthernet1/0/4 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/5 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/6 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/7 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/8 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/9 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/10 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/11 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/12 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/13 switchport access vlan 2 spanning-tree portfast!interface GigabitEthernet1/0/14 switchport access vlan 2!interface GigabitEthernet1/0/15 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/16 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/17 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/18 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/19 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/20 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/21 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/22 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/23 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet1/0/24 switchport trunk encapsulation dot1q switchport mode trunk!interface Vlan1ip address default-gateway classless ip http serversnmp-server community public-nm ROsnmp-server community private-nm RWsnmp-server chassis-idsnmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps ttysnmp-server enable traps clustersnmp-server enable traps fru-ctrlsnmp-server enable traps entitysnmp-server enable traps cpu thresholdsnmp-server enable traps power-ethernet group 1-9snmp-server enable traps vtpsnmp-server enable traps vlancreatesnmp-server enable traps vlandeletesnmp-server enable traps flash insertion removalsnmp-server enable traps port-securitysnmp-server enable traps envmon fan shutdown supply temperature statussnmp-server enable traps mac-notificationsnmp-server enable traps stackwisesnmp-server enable traps licensesnmp-server enable traps config-copysnmp-server enable traps configsnmp-server enable traps hsrpsnmp-server enable traps rtrsnmp-server enable traps bridge newroot topologychangesnmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistency snmp-server enable traps syslogsnmp-server enable traps vlan-membershipsnmp-server host public-nm!control-plane!!line con 0line vty 0 4password ciscologinline vty 5 15login!endbangonglou1# exi[Connection to closed by foreign host]User Access VerificationPassword:bangonglou2>enPassword:bangonglou2#wr tBuilding configuration...Current configuration : 4341 bytes!versionno service padservice timestamps debug uptime service timestamps log uptimeno service password-encryption!hostname bangonglou2!enable secret cisco!no aaa new-modelswitch 1 provision ws-c3750g-24t system mtu routing 1500ip subnet-zero!!!!no file verify autospanning-tree mode pvstspanning-tree extend system-id!vlan internal allocation policy ascending !interface GigabitEthernet1/0/1 switchport access vlan 3switchport mode accessspanning-tree portfast!interface GigabitEthernet1/0/2 switchport access vlan 3switchport mode accessinterface GigabitEthernet1/0/3 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/4 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/5 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/6 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/7 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/8 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/9 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/10 switchport access vlan 3 switchport mode access spanning-tree portfast!interface GigabitEthernet1/0/11 switchport access vlan 3 switchport mode access。
Cisco Catalyst 4500 系列交换机配置指南说明书

C H A P T E R54-1Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-0154Configuring Storm ControlThis chapter describes how to configure port-based traffic control on the Catalyst 4500 series switch.This chapter consists of these sections:•About Storm Control, page 54-1•Enabling Broadcast Storm Control, page 54-3•Enabling Multicast Storm Control, page 54-4•Disabling Broadcast Storm Control, page 54-5•Disabling Multicast Storm Control, page 54-5•Displaying Storm Control, page 54-6NoteFor complete syntax and usage information for the switch commands used in this chapter, first look at the Cisco Catalyst 4500 Series Switch Command Reference and related publications at this location:/en/US/products//hw/switches/ps4324/index.htmlIf the command is not found in the Catalyst 4500 Series Switch Command Reference, it will be found in the larger Cisco IOS library. Refer to the Cisco IOS Command Reference and related publications at this location:/en/US/products/ps6350/index.htmlAbout Storm ControlThis section contains the following subsections:•Hardware-Based Storm Control Implementation, page 54-2•Software-Based Storm Control Implementation, page 54-2Storm control prevents LAN interfaces from being disrupted by a broadcast storm. A broadcast storm occurs when broadcast packets flood the subnet, creating excessive traffic and degrading network performance. Errors in the protocol-stack implementation or in the network configuration can cause a broadcast storm.54-2Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-01Chapter 54 Configuring Storm ControlAbout Storm ControlSoftware Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-01Chapter 54 Configuring Storm ControlEnabling Broadcast Storm ControlEnabling Broadcast Storm ControlTo enable storm control, perform this task:The following example shows how to enable storm control on interface:Switch# configure terminalEnter configuration commands, one per line. End with CNTL/Z.Switch(config)# interface fa3/1Switch(config-if)# storm-control broadcast level 50Switch(config-if)# endSwitch# show storm-controlInterface Filter State Broadcast Multicast Level --------- ------------- --------- --------- -----Fi3/1 Forwarding Enabled Disabled 50.00% Switch# show int fa2/1 capabilities FastEthernet2/1Model: WS-X4148-RJ45V-RJ-45 Type: 10/100BaseTX Speed: 10,100,autoCommandPurposeStep 1Switch# configure terminalEnters global configuration mode.Step 2Switch(config)# interface interface-id Enters interface configuration mode and enter the port to configure.Step 3Switch(config-if)# storm-control broadcast level [high level ]Configures broadcast storm control.Specifies the upper threshold levels for broadcast traffic. The storm control action occurs when traffic utilization reaches this level.(Optional) Specifies the falling threshold level. The normaltransmission restarts (if the action is filtering) when traffic drops below this level for interfaces that support software-based suppression.NoteFor ports that perform hardware-based suppression, the lower threshold is ignored.NoteFor the Catalyst 4500-X Series Switch, on ports operating at 1Gigabit, thresholds less than 0.02% are not supported.Step 4Switch(config-if)# storm-control action {shutdown | trap }Specifies the action to be taken when a storm is detected.The default is to filter out the broadcast traffic and not to send out traps.The shutdown keyword sets the port to error-disable state during a storm. If the recover interval is not set, the port remains in shutdown state.Step 5Switch(config-if)# exit Returns to configuration mode.Step 6Switch(config)# endReturns to privileged EXEC mode.Step 7Switch# show storm-control [interface ] broadcastDisplays the number of packets suppressed.Step 8Switch# copy running-config startup-config(Optional) Saves your entries in the configuration file.Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-01Chapter 54 Configuring Storm ControlEnabling Multicast Storm ControlDuplex: half,full,auto Auto-MDIX: noTrunk encap. type: 802.1QTrunk mode: on,off,desirable,nonegotiate Channel: yesBroadcast suppression: percentage(0-100), hw Multicast suppression: percentage(0-100), hw Flowcontrol: rx-(none),tx-(none) VLAN Membership: static, dynamic Fast Start: yes CoS rewrite: yes ToS rewrite: yesInline power: yes (Cisco Voice Protocol) SPAN: source/destination UDLD: yes Link Debounce: no Link Debounce Time: no Port Security: yes Dot1x: yesMaximum MTU: 1552 bytes (Baby Giants) Multiple Media Types: no Diagnostic Monitoring: N/AEnabling Multicast Storm ControlCatalyst 4900M, Catalyst 4948E, Supervisor Engine 6-E, Supervisor Engine 6L-E, Supervisor Engine 7-E, and Supervisor Engine 7L-E support per-interface multicast suppression, which allows you to subject incoming multicast and broadcast traffic to interface-level suppression.NoteMulticast and broadcast suppression share a common threshold per interface. Multicast suppression takes effect only if broadcast suppression is enabled. Disabling broadcast suppression on an interface also disables multicast suppression.To enable multicast suppression, perform this task:The following example shows how to enable multicast suppression on ports that have broadcast suppression already enabled:Switch# configure terminalEnter configuration commands, one per line. End with CNTL/Z.Switch(config)# int fa3/1Switch(config-if)# storm-control broadcast include multicastCommandPurposeStep 1Switch# configure terminalEnters global configuration mode.Step 2Switch(config)# interface interface-id Enters interface configuration mode and enter the port to configure.Step 3Switch(config-if)# storm-control broadcast include multicast Enables multicast suppression.Step 4Switch(config-if)# exit Returns to configuration mode.Step 5Switch(config)# endReturns to privileged EXEC mode.Step 6Switch# show storm-controlVerifies the configuration.Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-01Chapter 54 Configuring Storm ControlDisabling Broadcast Storm ControlSwitch(config-if)# end Switch#Switch# show storm-controlInterface Filter State Broadcast Multicast Level --------- ------------- --------- --------- -----Fi3/1 Forwarding Enabled Enabled 50.00%Disabling Broadcast Storm ControlTo disable storm control, perform this task:The following example shows how to disable storm control on interface.Switch# configure terminalEnter configuration commands, one per line. End with CNTL/Z.Switch(config)# int fa3/1Switch(config-if)# no storm-control broadcast level Switch(config-if)# endSwitch# show storm-controlInterface Filter State Broadcast Multicast Level --------- ------------- --------- --------- -----Switch#Disabling Multicast Storm ControlTo disable multicast suppression, perform this task:CommandPurposeStep 1Switch# configure terminalEnters global configuration mode.Step 2Switch(config)# interface interface-id Enters interface configuration mode and enter the port to configure.Step 3Switch(config-if)# no storm-control broadcast levelDisables port storm control.Step 4Switch(config-if)# no storm-control action {shutdown | trap }Disables the specified storm control action and returns to default filter action.Step 5Switch(config-if)# exit Returns to configuration mode.Step 6Switch(config)# endReturns to privileged EXEC mode.Step 7Switch# show storm-control broadcast Verifies your entries.Step 8Switch# copy running-config startup-config(Optional) Saves your entries in the configuration file.CommandPurposeStep 1Switch# configure terminalEnters global configuration mode.Step 2Switch(config)# [no ] storm-control broadcast include multicastEnables and disables multicast suppression.Step 3Switch(config-if)# no storm-control broadcast levelDisables port storm control (broadcast and multicast).Chapter54 Configuring Storm Control Displaying Storm ControlCommand PurposeStep4Switch(config-if)# end Returns to configuration mode.Step5Switch(config)# end Returns to privileged EXEC mode.Displaying Storm ControlNote Use the show interface capabilities command to determine the mode in which storm control is supported on an interface.The following example shows an interface that supports broadcast suppression in software (sw):Switch# show int fa2/1 capabilitiesFastEthernet2/1Model: WS-X4148-RJ45V-RJ-45Type: 10/100BaseTXSpeed: 10,100,autoDuplex: half,full,autoAuto-MDIX: noTrunk encap. type: 802.1QTrunk mode: on,off,desirable,nonegotiateChannel: yesBroadcast suppression: percentage(0-100), hwMulticast suppression: percentage(0-100), hwFlowcontrol: rx-(none),tx-(none)VLAN Membership: static, dynamicFast Start: yesCoS rewrite: yesToS rewrite: yesInline power: yes (Cisco Voice Protocol)SPAN: source/destinationUDLD: yesLink Debounce: noLink Debounce Time: noPort Security: yesDot1x: yesMaximum MTU: 1552 bytes (Baby Giants)Multiple Media Types: noDiagnostic Monitoring: N/ANote Use the show interfaces counters storm-control command to display a count of discarded packets.Switch# show interfaces counters storm-controlPort Broadcast Multicast Level TotalSuppressedPacketsFa2/1 Enabled Disabled 10.00% 46516510Gi3/1 Enabled Enabled 50.00% 0Switch# show storm-controlInterface Filter State Broadcast Multicast Level--------- ------------- --------- --------- -----Fa2/1 Blocking Enabled Disabled 10.00%Gi3/1 Link Down Enabled Enabled 50.00%Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SGOL-25340-01。
Cisco Catalyst 4500 系列产品数据手册说明书

Data SheetCisco Catalyst 4500 SeriesCisco Catalyst 4500 Series integrates resiliency for advanced control of convergednetworks.Figure 1Cisco Catalyst 4503,4506, and 4507R SeriesOverviewThe Cisco Catalyst ® 4500 Series offers nonblocking Layer2/3/4 switching with integrated resiliency, further enhancing control of converged networks. Converged voice/video/data networks with high availability enable business resiliency forenterprise and metropolitan (metro) Ethernet customers deploying Internet-based business applications. A next-generation Cisco Catalyst 4000 Family platform, the Cisco Catalyst 4500 Series includes three new Cisco Catalyst chassis: Cisco Catalyst 4507R (seven slots),Cisco Catalyst 4506 (six slots), andCisco Catalyst 4503 (three slots). Integrated resiliency enhancements offeredin the Cisco Catalyst 4500 Seriesinclude 1 + 1 supervisor engine redundancy (Cisco Catalyst 4507R only), integrated inline power for IP telephony, software-based fault tolerance, and 1 + 1 power supply redundancy. Integrated resiliency in both hardware and softwareminimizes network downtime, ensuring workforce productivity, profitability, and customer success.As a key component of Cisco AVVID (Architecture for Voice, Video and Integrated Data), the Cisco Catalyst 4500 extends control to the network edge with intelligent network services, including sophisticated quality of service (QoS), predictable performance, advancedsecurity, comprehensive management, and integrated resiliency. Offering compatibility with Cisco Catalyst 4000 Family line cards and supervisor engines, the Cisco Catalyst 4500 Series enables an extended window of deployment for the Cisco Catalyst 4000 Family in converged networks. This reduces the cost of ownership by minimizing recurring operational expenses, thus improving return on investment (ROI). Cisco Catalyst 4500 Series ChassisThe Cisco Catalyst 4500 Series, with threechassis options and three supervisor engine options, provides a common architecture that scales to 240 ports of 10/100, 100BASE-FX Fast Ethernet, 1000BASE-LX, or 10/100/1000BASE-T Gigabit Ethernet. The Cisco Catalyst 4507R is the only Cisco Catalyst 4500 Series switch to support 1 + 1 redundant supervisor engines with sub-minute failovertime.Using the same line cards and supervisor engines (Supervisor Engines II and III) as the widely deployed Cisco Catalyst 4000 Series, the Cisco Catalyst 4500 Series enhances the Cisco commitment to affordable enterprise and branch scalability, providing a cost-effective, flexible network solution that scales to meet today’s high-performance needs with investment protection (refer to Table 1).Note:Supervisor engine slots do not support switching line-card modules; line-card slots do not support supervisorengines.Table 1Cisco Catalyst 4500 Series Chassis FeaturesFeatureChassis Chassis Chassis Total number of slots 367Supervisor engine slots 111.Slot 1 is reserved for supervisor engine only; slots 2 and higher are reserved for line cards.11222.Slots 1 and 2 are reserved for supervisor engines only in the Cisco Catalyst 4507R. Slots 3 and higher are reserved for line c ards.Supervisor engine redundancyNoNoYes (Supervisor Engine IV only)Supervisor engines supported Supervisor II Supervisor III Supervisor IVSupervisor II Supervisor III Supervisor IV Supervisor IVLine-card slots2552Number of power supply bays 222AC input power YesYesYesDC input powerYes (future)Yes (future)Yes (future)Integrated inline power (IP phone and wireless access point) supportYesYesYesMinimum number of power supplies111Number of fan-tray bays 111Location of 19-inch rack-mount FrontFrontFrontLocation of 23-inch rack-mountFront (option)Front (option)Front (option)Configuration AlternativesThe Cisco Catalyst 4500 Series offers a powerful and flexible network solution that can be built with three powerful supervisor engine alternatives. Each provides a high-performance, centralized, shared-memory switch fabric, while protecting your line-card investment by supporting the addition of optional higher-layer functionality engines (Table2).Note:For a detailed list of Cisco Catalyst 4000 Family Supervisor Engine III and IV features, refer to the Cisco Catalyst 4000 Family Supervisor Engine III and IV data sheet located on the Cisco Catalyst 4000 Family site: /warp/public/cc/pd/si/casi/ca4000/The Cisco Catalyst 4500 Series has flexible interface types and port densities that allow network configurations to be mixed and matched to meet the specific needs of any campus network (Table 3). Table 2Cisco Catalyst 4500 Series Supervisor Engine Support and PerformanceFeatureCisco Catalyst 4503 chassisSupported 24-Gbps engine, 18Mpps Supported 28Gbps, 21MppsSupported 28Gbps, 21MppsCisco Catalyst 4506 chassisSupported 24Gbps engine, 18Mpps Supported 64Gbps, 48Mpps Supported 64Gbps, 48MppsCisco Catalyst 4507R chassisNot supportedNot supportedSupported 64Gbps, 48MppsTable 3Cisco Catalyst 4500 Series Port Densities450345064507R Switched 10/100 FastEthernet (RJ-45)32 or 4896240240Switched 10/100 FastEthernet (RJ-21)4896240240Switched 100FastEthernet (MT-RJ) 4, 24, or 4896240240Switched 1000GigabitEthernet (fiber)2, 6, 18, or 4896240240Switched10/100/1000BASE-T Gigabit Ethernet12 (1000BASE-T only), 24 or 4896240240Configuration Flexibility and Modular SuperiorityThe Cisco Catalyst 4503, 4506, and 4507R offer the same comprehensive, scalable suite of 10/100/1000-Mbps Ethernet switch modules as the Cisco Catalyst 4003 and 4006. A variety of Cisco Catalyst 4000 Family modules areavailable, which can be mixed and matched to suit a wide range of wiring-closet, data-center, or branch-office deployments. Any Gigabit Ethernet port can be 1000BASE-SX, 1000BASE-LX/LH, 1000BASE-ZX, or coarse wavelength-division multiplexing (CWDM) by using flexible, hot-swappable gigabit-interface-converter (GBIC) modules. The Cisco Catalyst 4500 Series supports the following switching modules:•WS-X4148-FX-MT—Cisco Catalyst 4000 Fast Ethernet Switching Module, 48-port 100BASE-FX multimode fiber (MMF) (MT-RJ)•WS-X4148-RJ—Cisco Catalyst 4000 10/100 Module, 48 ports (RJ-45)•WS-X4148-RJ21—Cisco Catalyst 4000 10/100 Module, 48-port telco (4 x RJ-21)•WS-X4148-RJ45V—Cisco Catalyst 4000 Inline Power 10/100, 48 ports (RJ-45) for IP phones and wireless accesspoints•WS-X4232-GB-RJ—Cisco Catalyst 4000 32-Port 10/100 (RJ-45), 2-Gigabit Ethernet (GBIC) Module•WS-X4232-L31—Cisco Catalyst 4000 Layer 3 32-Port 10/100 (RJ-45), 2-Gigabit Ethernet (GBIC) Module •WS-X4232-RJ-XX—Cisco Catalyst 4000 Layer 3 Services 32-port 10/100 (RJ-45), plus modular uplink slot •WS-X4424-GB-RJ45—Cisco Catalyst 4000 24-Port 10/100/1000 Module (RJ-45)•WS-X4306-GB—Cisco Catalyst 4000 Gigabit Ethernet Module, 6 ports (GBIC)•WS-X4412-2GB-T—Cisco Catalyst 4000 Gigabit Ethernet Module, 12-port 1000BASE-T (RJ-45) + 2-port [1000BASE-X (GBIC)•WS-X4418-GB—Cisco Catalyst 4000 Gigabit Ethernet Module, server switching, 18 ports (GBIC)•WS-X4448-GB-LX—Cisco Catalyst 4000 48-port 1000BASE-LX (small form-factor pluggable [SFP])•WS-X4448-GB-RJ45—Cisco Catalyst 4000 48-port 10/100/1000 Module (RJ-45)•WS-U4504-FX-MT—Cisco Catalyst 4000 Fast Ethernet Uplink Daughter Card, 4-port 100BASE-FX (MT-RJ)•WS-X4604-GWY1—Cisco Catalyst 4000 Access Gateway Module with IP/firewall software•WS-X4095-PEM—Cisco Catalyst 4006 DC Power Entry Module•WS-X4124-FX-MT—Cisco Catalyst 4000 Fast Ethernet Switching Module, 24-port [100BASE-FX (MT-RJ)•WS-X40191—Cisco Catalyst 4000 Backplane Channel Module•WS-G54831—Cisco 1000BASE-T GBIC•WS-G5484—Cisco 1000BASE-SX Short-Wavelength GBIC (multimode only)•WS-G5486—Cisco 1000BASE-LX/LH Long-Haul GBIC (single mode or multimode)•WS-G5487—Cisco 1000BASE-ZX Extended-Reach GBIC (single mode)•Cisco CWDM GBIC solution1.Supported with Supervisor Engine II with Cisco Catalyst Operating System (CatOS) Version 7.4(1) and up at FCSSoftware RequirementsTable 4 gives requirements for the Cisco Catalyst Supervisor Engine Software, and Table 5 gives the differences between the Cisco Catalyst 4000 and 4500 Series switches.Standard Network Protocols •Ethernet–IEEE 802.3, 10BASE-T •Fast Ethernet–IEEE 802.3u, 100BASE-TX –IEEE 802.3, 100BASE-FXTable 4Cisco Catalyst Supervisor Engine Software Requirements SpecificationEngine IIMinimum software requirementCisco CatOS Software Version 7.4(1) or higherCisco IOS ® Software Version 12.1(12c)EW or higherCisco IOS Software Version 12.1(12c)EW or higherTable 5Key Differences Between Cisco Catalyst 4000 and 4500 SeriesFeature 40034006450345064507RInline powerNoYes—Withexternal power shelf Yes—IntegratedYes—IntegratedYes—IntegratedPower supply redundancy 1 + 1 2 + 11 + 1 1 + 1 1 + 1Supervisor engineredundancy No No No No YesSupported line cardsAll CiscoCatalyst 4000 line cards All CiscoCatalyst 4000 line cards All CiscoCatalyst 4000 line cards All CiscoCatalyst 4000 line cardsAll CiscoCatalyst 4000 switching line cards 11.WS-X4604-GWY will be supported in a future software release. WS-X4019 is not needed with Supervisor Engine IV.Supervisor engines supported Supervisor Engine ISupervisor Engines II, III, and IV Supervisor Engines II, III, and IV Supervisor Engines II, III, and IV Supervisor Engine IVPower supplies supported400-watt AC 400-watt DC400-watt AC 400-watt DC1000-watt AC 2800-watt ACV1000-watt AC 2800-watt ACV1000-watt AC 2800-watt ACV•Gigabit Ethernet–IEEE 802.3z–IEEE 802.3x–IEEE 802.3ab•1000BASE-X (GBIC)–1000BASE-SX–1000BASE-LX/LH–1000BASE-ZX•Virtual LAN (VLAN) trunking/tagging–IEEE 802.1Q•Spanning-Tree Protocol–IEEE 802.1D–IEEE 802.1w–IEEE 802.1s•Security–IEEE 802.1xNetwork Management•CiscoWorks Network Management Suite, Resource Manager Essentials support, including:–Inventory Manager–Change Audit–Device Configuration Manager–Software Image Manager–Availability Manager–Syslog Analyzer–Cisco Management Connection•CiscoWorks Network Management Suite, Campus Manager support, including:–Network topology discovery and display services–VLAN provisioning and logical display representation–Traffic monitoring and performance assessment–End-station tracking with search utilities–CiscoView graphical device management–Network topology integrity checking–Cisco Discovery Protocol–Cisco Virtual Trunking Protocol (VTP)–Simple Network Management Protocol (SNMP) agent Version 1 (RFCs 1155–1157)–SNMP Version 2c–Cisco Workgroup Management Information Base (MIB)–Ethernet MIB (RFC 1643)–Ethernet Repeater MIB (RFC 1516)–SNMP MIB II (RFC 1213)–Remote Monitoring (RMON) (RFC 1757)–Remote Monitoring II (RMON II) (RFC 2021)–Interface Table (RFC 1573)–Bridge MIB (RFC 1493)–Switched Port Analyzer (SPAN)–Enhanced Switched Port Analyzer (ESPAN)–Port snooping and connection steering–Text-based command-line interface (CLI) based on the familiar Cisco Catalyst 5000 Series interface (Supervisor Engine II only)–Standard Cisco IOS security capabilities: passwords and TACACS+–Telnet, Trivial File Transfer Protocol (TFTP), BOOTP for management access Physical SpecificationsTable 6 gives the physical specifications of the Cisco Catalyst 4500 Series chassis, and Table 7 gives Cisco Catalyst 4500 power supply specifications.Power Supply Indicators and Interfaces•Fan cooling: Integrated in hot-insertion/hot-extraction unit •Good: Green (good)•Fail: Red (faulty)•SNMP MIB supportedTable 6Physical Specifications of Cisco Catalyst 4500 SeriesChassisDimensions (H x W x D):(12.25 x 17.31 x 12.50 in.), (31.12 x 43.97 x 31.70 cm)(17.38 x 17.31 x 12.50 in.), (44.13 x 43.97 x 31.70 cm)(19.19 x 17.31 x 12.50 in.), (48.74 x 43.97 x 31.70 cm)Rack units 7 rack units high 10 rack units high 11 rack units high Minimum weight:52 lb 56 lb 57 lb Maximum weight:75 lb100 lb107 lbMounting:19- and 23-in. rackcompatible (19-in. rack and cable guide hardware included)19- and 23-in. rackcompatible (19-in. rack and cable guide hardware included)19- and 23-in. rackcompatible (19-in. rack and cable guide hardware included)Fan TraysEach Cisco Catalyst 4500 chassis uses a single fan tray for cooling. All fan trays are composed of independent fans. If one fan fails, the system will continue to operate without a significant degradation in cooling. The system will detect and notify the user (via LED, CLI, and SNMP) that a fan has failed and the tray needs to be replaced.Fabric Redundancy Modules (Cisco Catalyst 4507R only)The Cisco Catalyst 4507R redundancy scheme uses removable fabric redundancy modules on the passive backplane to switch traffic to the active supervisor. There is one fabric redundancy module per line card, for a total of five modules per chassis. All five fabric redundancy modules ship standard with every Cisco Catalyst 4507R chassis. The Cisco Catalyst 4507R also ships standard with redundant clocks. Spare fabric redundancy modules and clock modules are available for serviceability.Table 7Cisco Catalyst 4500 Power Supply SpecificationsIntegrated voice (48V inline power)No (data only)Yes (up to 1400 watts)Input current•13.2A maximum @ 100VAC • 6.6A maximum @ 200VAC•17.6A maximum @ 200VACAC Input Power Requirements•100–240V~•50/60 Hz •12–5A•220–240V~•50/60 Hz •16AOutput current (data)*********************************Output current (voice)n/a ****************KVA rating1.32 KVA3.52 KVAOutput power (data)1000W + 40W (fan)1360W + 40W (fan)Output power (voice)n/a1400W per power supply Heat dissipation 943 BTU/hr 2387 BTU/hr Holdup time20 ms 20 ms Cisco phones supported with integrated inline powerNoneUp to 24011.240 phones are supported in power supply combined mode. Refer to the Cisco Catalyst 4500 IP Telephony white paper at the following URL for details on phonesupport.Place url here Note:1.Output power is per power supply, but total output power from two supplies is not twice the output of one power supply. See the specifications.2.Heat dissipation numbers represent the power conversion losses of the power supply in operation.Environmental Conditions•Operating temperature: 32º to 104ºF (0º to 40ºC)•Storage temperature: –40º to 167ºF (–40º to 75ºC)•Relative humidity: 10 to 90%, noncondensing•Operating altitude: –60 to 4000 mRegulatory Standards ComplianceTable 8 gives information regarding compliance of the Cisco Catalyst 4500 Series to regulatory standards. Table 8Regulatory Standards Compliance of Cisco Catalyst 4500 SeriesRegulatory compliance CE markingSafety•UL 60950•CAN/CSA-C22.2 No. 60950•EN 60950•IEC 60950•TS 001•AS/NZS 3260EMC•FCC Part 15 (CFR 47) Class A•ICES-003 Class A•EN55022 Class A•CISPR22 Class A•AS/NZS 3548 Class A•VCCI Class A•EN 55022•EN 55024•EN 61000-6-1•EN 50082-1•EN 61000-3-2•EN 61000-3-3•ETS 300 386Industry EMC, safety, and environmental standards •GR-63-Core Network Equipment Building Standards (NEBS) Level 3•GR-1089-Core Level 3•ETS 300 019 Storage Class 1.1•ETS 300 019 Transportation Class 2.3 (pending)•ETS 300 019 Stationary Use Class 3.1•ETS 300 386Telecom (E1)•CTR 12/13•CTR 4•ACA TS016Telecom (T1)•FCC Part 68•Canada CS-03•JATE Green BookOrdering InformationTable 9 lists Cisco Catalyst 4500 common equipment ordering information details.Table 9Cisco Catalyst 4500 Common Equipment Ordering InformationWS-C4503Cisco Catalyst 4500 (3-slot chassis), fan, nopower supplyWS-C4506Cisco Catalyst 4500 (6-slot chassis), fan, nopower supplyWS-C4507R Cisco Catalyst 4500 (7-slot chassis), fan, nopower supply, redundant supervisor capable PWR-C45-1000AC Cisco Catalyst 4500 1000-watt AC power supply (data only)PWR-C45-2800ACV Cisco Catalyst 4500 2800-watt AC power supply (with integrated voice)WS-X4013Cisco Catalyst 4000 Family Supervisor Engine IIWS-X4014Cisco Catalyst 4000 Family Supervisor Engine IIIWS-X4515Cisco Catalyst 4000 Family Supervisor Engine IVWS-X4515/2Cisco Catalyst 4507R Series Redundant Supervisor Engine IVS4KL3-12112EW Cisco IOS Software for the Cisco Catalyst 4000 Family Supervisor Engines III and IV; basic Layer 3 software image (Routing Information Protocol [RIP], static routes, IPX, AppleTalk)S4KL3E-12112EW Cisco IOS Software for the Cisco Catalyst 4000 Family Supervisor Engines III and IV;enhanced Layer 3 software image, including Open Shortest (OSPF), Interior GatewayRouting Protocol (IGRP), and Enhanced IGRP (EIGRP)MEM-C4K-FLD64M Cisco Catalyst 4000 Family compact Flash memory for Supervisor III or IV, 64-MB option MEM-C4K-FLD128M Cisco Catalyst 4000 Family compact Flash memory for Supervisor III or IV, 128-MB optionLicensingUse of RMON on the Cisco Catalyst 4500 Series switches requires the purchase of the RMON agent license. Use of Border Gateway Protocol Version 4 (BGP4) on the Supervisor Engine III or IV requires an InterDomain Routing license. Only one RMON agent license or InterDomain Routing license is required per chassis.WS-C4503-EMS-LIC(=)Cisco Catalyst 4503 RMON Agent LicenseWS-C4506-EMS-LIC(=)Cisco Catalyst 4506 RMON Agent LicenseWS-C4507R-EMS-LIC(=)Cisco Catalyst 4507R RMON Agent LicenseFR-IRC4(=)Cisco Catalyst 4000 Supervisor III and IV InterDomain Routing Feature LicenseWarrantyThe warranty for the Cisco Catalyst 4500 Series is 90 days; it includes hardware replacement with a 10-day turnaround from return to manufacturer authorization (RMA).Service and SupportCisco offers life-cycle service and support for the Cisco Catalyst 4000 Family (including Cisco Catalyst 4000 and 4500 Series) directly and for resale through Cisco distributors. From implementation to operation and optimization, Cisco offers advanced service and technical support services.Advanced ServiceTotal Implementation Solutions (TIS) offers a full range of implementation solutions, including project management, project engineering, configuration, staging and rollout coordination, and ensuring correct installation, anddeployment. For more information on TIS, visit:/warp/public/cc/serv/mkt/sup/ent/tis/.Technical Support ServicesCisco SMARTnet® support augments the resources of your operations staff by providing them with access to a wealth of expertise, both online and via telephone, including the ability to refresh their system software at will, anda range of hardware Advance Replacement options. Cisco SMARTnet Onsite support provides all services andcomplements the hardware Advance Replacement feature by adding the services of a field engineer, services that can be critical for those locations where staffing is insufficient or unavailable to perform parts replacement activities. For more information on Cisco SMARTnet support, visit:/warp/public/cc/serv/mkt/sup/ent/snet/.For additional information on Cisco products, contact:United States and Canada: 800 553-NETS (6387)Europe: 32 2 778 4242Australia: 612 9935 4107Other: 408 526-7209Cisco Systems, Inc.All contents are Copyright © 1992–2002 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement.Page 11 of 12Corporate Headquarters Cisco Systems, Inc.170 West Tasman Drive San Jose, CA 95134-1706 USATel:408 526-4000800 553-NETS (6387) Fax:408 526-4100European HeadquartersCisco Systems International BVHaarlerbergparkHaarlerbergweg 13-191101 CH AmsterdamThe NetherlandsTel:31 0 20 357 1000Fax:31 0 20 357 1100Americas HeadquartersCisco Systems, Inc.170 West Tasman DriveSan Jose, CA 95134-1706USATel:408 526-7660Fax:408 527-0883Asia Pacific HeadquartersCisco Systems, Inc.Capital Tower168 Robinson Road#22-01 to #29-01Singapore 068912Tel:+65 317 7777Fax:+65 317 7799Cisco Systems has more than 200 offices in the following countries and regions. Addresses, phone numbers, and fax numbers are listed on theC i s c o W e b s i t e a t w w w.c i s c o.c o m/g o/o f f i c e sArgentina • Australia • Austria • Belgium • Brazil • Bulgaria • Canada • Chile • China PRC • Colombia • Costa Rica • Croatia CzechRepublic • Denmark • Dubai, UAE • Finland • France • Germany • Greece • Hong Kong SAR • Hungary • India • Indonesia • Ireland Israel • Italy • Japan • Korea • Luxembourg • Malaysia • Mexico • TheNetherlands • New Zealand • Norway • Peru • Philippines • P oland Portugal • Puerto Rico • Romania • Russia • Saudi Arabia • Scotland • Singapore • Slovakia • Slovenia • South Africa • Spain • S weden Switzerland • Taiwan • Thailand • Turkey • Ukraine • United Kingdom • United States • Venezuela • Vietnam • Zimbabwe All contents are Copyright © 1992–2002, Cisco Systems, Inc. All rights reserved. SMARTnet is a trademark, and Catalyst, Cisco, Cisco IOS, Cisco Systems, and the Cisco Systems logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries.All other trademarks mentioned in this document or Web site are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0206R)LW33760802。
Cisco路由器配置手册(大全)之欧阳歌谷创作

Cisco路由器配置手册(大全)欧阳歌谷(2021.02.01)第一章路由器配置基础一、基本设置方式一般来说,可以用5种方式来设置路由器:1.Console口接终端或运行终端仿真软件的微机;2.AUX口接MODEM,通过电话线与远方的终端或运行终端仿真软件的微机相连;3.通过Ethernet上的TFTP服务器;4.通过Ethernet上的TELNET程序;5.通过Ethernet上的SNMP网管工作站。
但路由器的第一次设置必须通过第一种方式进行,此时终端的硬件设置如下:波特率:9600数据位:8停止位:1奇偶校验: 无二、命令状态1. router>路由器处于用户命令状态,这时用户可以看路由器的连接状态,访问其它网络和主机,但不能看到和更改路由器的设置内容。
2. router#在router>提示符下键入enable,路由器进入特权命令状态router#,这时不但可以执行所有的用户命令,还可以看到和更改路由器的设置内容。
3. router(config)#在router#提示符下键入configure terminal,出现提示符router(config)#,此时路由器处于全局设置状态,这时可以设置路由器的全局参数。
4. router(config-if)#; router(config-line)#; router(config-router)#;…路由器处于局部设置状态,这时可以设置路由器某个局部的参数。
5. >路由器处于RXBOOT状态,在开机后60秒内按ctrl-break可进入此状态,这时路由器不能完成正常的功能,只能进行软件升级和手工引导。
6. 设置对话状态这是一台新路由器开机时自动进入的状态,在特权命令状态使用SETUP命令也可进入此状态,这时可通过对话方式对路由器进行设置。
三、设置对话过程1. 显示提示信息2. 全局参数的设置3. 接口参数的设置4. 显示结果利用设置对话过程可以避免手工输入命令的烦琐,但它还不能完全代替手工设置,一些特殊的设置还必须通过手工输入的方式完成。
网络技术培训-思科路由器配置指南

参考带宽
(建议配置成ISP给你的 实际带宽)
RouterX(config-if)#bandwidth 64 RouterX(config-if)#exit
show interfaces
RouterX#show interfaces Ethernet0 is up, line protocol is up
81833 packets input, 27556491 bytes, 0 no buffer Received 42308 broadcasts, 0 runts, 0 giants, 0 throttles 1 input errors, 0 CRC, 0 frame, 0 overrun, 1 ignored, 0 abort 0 input packets with dribble condition detected 55794 packets output, 3929696 bytes, 0 underruns 0 output errors, 0 collisions, 1 interface resets 0 babbles, 0 late collision, 4 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out
Hardware is Lance, address is 00e0.1e5d.ae2f (bia 00e0.1e5d.ae2f) Internet address is 10.1.1.11/24 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, rely 255/255, load 1/255 Encapsulation ARPA, loopback not set, keepalive set (10 sec) ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:07, output 00:00:08, output hang never Last clearing of "show interface" counters never Queueing strategy: fifo Output queue 0/40, 0 drops; input queue 0/75, 0 drops 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec
两台cisco4506如何做端口的聚合

两台cisco4506如何做端口的聚合?[size=2]我们单位上新购了两台cisco4506交换机,并架设了两条光缆。
领导要求两台交换机通过光缆连接在一起,当其中一条光缆中断时,交换机之间可通过另一条光缆正常工作。
因为本人没学过cisco的东东,问了一下别人,说是可以做端口聚合还可以做通道,具体怎么做也不很清楚。
请各位帮忙,解释一下该怎样实现,最好能具体一些。
另外,cisco上做端口镜像是什么命令啊?我在网上暂时没查到,也劳烦各位指教一下。
[/size]edwayoung 发表于 2008-1-14 14:09回复 #1 mywonder 的帖子二层int range g0/1 -2channel-group 1 mode desirableinterface Port-channel 1switchport access vlan 1switchport mode accesswolf530 发表于 2008-1-15 02:55做以太通道两个交换机的端口模式等要完全一致channel-group 1 mode desirableinterface Port-channel 1switchport trunk vlan 10switchport mode trunkvlan 1是管理vlan 最好不要弄到那里去roc5668 发表于 2008-1-15 11:09ddddddddmywonder 发表于 2008-1-28 14:33噢,谢谢maomao4512 发表于 2008-1-28 14:57不明白。
学习中125994452 发表于 2008-1-28 15:01用的到端口聚合么?用热备份夕阳流水发表于 2008-1-28 17:49汗一个,你不做任何配置也可以实现你所说的前一条,端口镜像还是要的小侠唐在飞发表于 2008-1-29 10:21链路聚合有成端口聚合,端口捆绑,英文名port trunking.功能是将交换机的多个低带宽端口捆绑成一条高带宽链路,可以实现链路负载平衡。
CISCO Catalyst系列交换机配置简易手册

no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service compress-config
! hostname gzcss4506
//交换机命名
定义网关:
GZCSS4506(config)#ip default-gateway 192.168.129.1
端口上划分VLAN:
GZCSS4506(config)#int G4/2 GZCSS4506(config-if)# switchport GZCSS4506(config-if)#switchport access vlan 200 GZCSS4506(config-if)#no shutdown
CISCO CATALYST 系列交换机配置 简易手册
广州中软信息技术有限公司 二○○四年十二月
CISCO Catalyst 系列交换机配置简易手册
CISCO Catalyst 系列交换机配置简易手册
CISCO Catalyst 系列交换机 IOS 操作系统主要配置命令基本相同,在中小型 企业局域网实施过程中,通常使用如下的一些基本命令来配置,包括:用户密码、 管理 IP、以太通道、VTP 域、VLAN 划分、SNMP,HSRP,DHCP RELAY 以及 一些基本的信息查看命令等,此类配置命令在 CISCO IOS(Catalyst2950,3550, 3750,4506,6509 等)基本通用。
这里仅是最基本的简易配置。如需详细的配置onfig)#hostname GZCSS4506
设置密码:
核心交换机Cisco4506E(2台)

核心交换机:Cisco 4506E(2台)
中央政府采购网络交换机产品协议供应商,需要上传原厂保修和售后服务承诺函。
一、结款:
先收取货物、发票、电子验收单及合同,设备经验收合格,登记我单位固定资产后3个月以支票或电汇方式支付全额货款。
二、售后服务:
由供货商提供上门服务。
保修期满免人工费,仅支付零配件费。
提供三年原厂保修和原厂售后服务承诺函,7*24小时技术支持,出现问题2个小时到达现场,4小时解决问题,24小时内免费提供备用机。
由供货商到医院上门维修或取件送修,医院不承担交通、人工等任何费用。
其余请遵循政府采购投标时厂家承诺标准。
其他:报价时请注明设备保修期,报价为最终成交价,无其他额外费用。
报价须知:提供产品应当是未经拆封、全新的原装正品。
报价总额应包括运输、安装调试以及上门培训服务等费用。
本产品须是cisco(中国)有限公司原厂发货的正品行货新品,在cisco网络产品的销售记录中最终用户须是中国医学科学院阜外心血管病医院;投标商必须在用户规定的时间内,免费将产品送到用户指定的地点并安装调试;
提供设备原厂出具3年服务承诺书原件,以保证产品为国内行销原装正货,用户在购买产品后能够获得服务保障。
产品安装及维护需要原厂认证工程师。
cisco4506简版交换机配置维护手册

Switch(config-vlan)# name test20
Switch(config-vlan)# end
也可以在enable状态下,进行VLAN配置:
Switch# vlan database
Switch(vlan)# vlan 20 name test20
Switch(config-if)#
Switch# configure terminal
Switch(config)# interface fastethernet2/5
Switch(config-if)# no shutdown
配置VLAN
Switch# configure terminal
end
Switch#
三层物理端口配置
Switch# configure terminal 进入配置状态
Switch(config)# interface fastethernet 5/4 进入物理端口配置模式
Switch(config-if)# no switchport 改变该端口为三层接口
Switch# configure terminal 进入配置状态
Switch(config)# interface fastethernet2/1 进入端口配置
Switch(config-if)# switchport trunk allowed vlan remove 2
Switch(config-if)# end
Switch(config-if)# end 退出
Switch(config)# show interface fastethernet2/1 验证端口的管理模式和VLAN情况
Cisco Catalyst 2950、2960、3550、4006、4506交换机IOS升级

Cisco Catalyst 2950、2960、3550、4006、4506交换机IOS升级[复制链接]一、对于正常联网使用的交换机,可以通过Telent登录交换机并通过TFTP升级IOS。
(1)假设网管计算机的IP地址为192.168.1.2/255.255.255.0(2)在网管计算机上运行TFTP Server,配置目录位置并将新IOS拷贝到相关目录,配置允许发送和接收。
(3)网管计算机使用Telnet登录交换机。
(4)升级//备份原IOSSwitch#copy flash:/c2950-*.bin tftpAddress or name of remote host[]?192.168.1.2Destination filename [c2950-*.bin]?//删除原IOSSwitch#delete flash:/c2950-*.bin//释放存储空间Switch#squeeze//上传新IOSSwitch#copy t ftp://192.168.1.2/c2950-*.bin flash:(5)上传完成后可以使用reload命令重启交换机,或关机重新加电开机。
二、对于Cisco Catalyst 2950、2960、3550、4006、4506等交换机,如果未联网使用而作为冗余备用交换机时,也可以通过TFTP升级IOS。
(1)将管理计算机的IP地址设置为192.168.1.2/255.255.255.0。
(2)网管计算机的COM1口使用控制线连接交换机的Console口;网口使用普通网线连接交换机的Fa0/1口。
如果是4006或4506,则可以使用其WS-X4548-GB-RJ45或WS-X4232-GB-RJ45模块上的RJ45口。
(3)在网管计算机上运行TFTP Server,配置目录位置并将新IOS拷贝到相关目录,配置允许发送和接收。
(4)交换机加电开机,在网管计算机上运行超级终端并登录交换机。
cisco 4506-e

Cisco4506的DHCP服务配置本文将介绍如何在Cisco4506下配置dhcp服务,现有Cisco4506三层交换机一台,作为核心交换,并配置若干vlan,vlan端口下接Cisco2950划分不通部门。
其中要在vlan5下的一台服务器(名:Server,IP:192.168.10.100)作DHCP服务。
要求在其他vlan的PC可以动态分配到IP。
PC客户具有一天的租期。
以满足带笔记本上班的同志可以自动获得IP,减少自己胡乱分配ip,造成地址冲突对网络造成影响,也可在服务器端对接入端进行控制。
具体拓扑见下图。
图(一)网络拓扑通过上图可以看出DHCP 服务器与DHCP客户端分别位于不同的网段内,因为DHCP信息是以广播为主,可是绝大部分网络内的IP router 并不会将广播信息传递到不同的网段内,因此限制了DHCP有效的使用范围。
下面将对4506进行相关配置,使不同网段的客户端可以获得ip。
Cisco 4506 上的配置1、创建vlanSwitch>enSwitch#Vlan DatabaseSwitch(vlan)#Vlan 2Switch(vlan)#Vlan 3Switch(vlan)#Vlan 4Switch(vlan)#Vlan 52、:设置VLAN IP地址:Switch#Config tSwitch(Config)#int vlan 2Switch(Config-if)#ip address 192.168.0.1 255.255.255.0(Config-if)#no shut(Config)#int vlan 3(Config-if)#ip address 192.168.5.1 255.255.255.0(Config-if)#no shut(Config)#int vlan 4(Config-if)#ip address 192.168.4.1 255.255.255.0(Config-if)#no shut(Config)#int vlan 5(Config-if)#ip address 192.168.10.1 255.255.255.0(Config-if)#no shut(Config-if)#exit3:将端口添加到VLAN中将端口10-15添加到VLAN 5Switch(Config)#Interface Range gi 3/10 -15Switch(Config-if-range)#Switchport Access Vlan 5其他以此类推。
思科路由器命令行手册
CISCO路由器配置手册返回教程第一章路由器配置基础一、基本设置方式二、命令状态三、设置对话过程四、常用命令五、配置IP寻址六、配置静态路由第二章广域网协议设置一、HDLC二、PPP三、X.25四、Frame Relay五、ISDN六、PSTN第三章路由协议设置一、RIP协议二、IGRP协议三、OSPF协议四、重新分配路由五、IPX协议设置第四章服务质量及访问控制一、协议优先级设置二、队列定制三、访问控制第五章虚拟局域网(VLAN)路由一、虚拟局域网(VLAN)二、交换机间链路(ISL)协议三、虚拟局域网(VLAN)路由实例参考第一章路由器配置基础一、基本设置方式一般来说,可以用5种方式来设置路由器:1.Console口接终端或运行终端仿真软件的微机;2.AUX口接MODEM,通过电话线与远方的终端或运行终端仿真软件的微机相连;3.通过Ethernet上的TFTP服务器;4.通过Ethernet上的TELNET程序;5.通过Ethernet上的SNMP网管工作站。
但路由器的第一次设置必须通过第一种方式进行,此时终端的硬件设置如下:波特率:9600数据位:8停止位:1奇偶校验: 无二、命令状态1.router>路由器处于用户命令状态,这时用户可以看路由器的连接状态,访问其它网络和主机,但不能看到和更改路由器的设置内容。
2.router#在router>提示符下键入enable,路由器进入特权命令状态router#,这时不但可以执行所有的用户命令,还可以看到和更改路由器的设置内容。
3.router(config)#在router#提示符下键入configure terminal,出现提示符router(config)#,此时路由器处于全局设置状态,这时可以设置路由器的全局参数。
4.router(config-if)#; router(config-line)#; router(config-router)#;…路由器处于局部设置状态,这时可以设置路由器某个局部的参数。
4506-2950参数配置文档

CATALYST4506/2950交换机配置文档1交换机操作基础 (2)1.1 登录 (2)1.2 工作模式 (2)1.2.1用户模式 (2)1.2.2特权模式 (3)1.2.3全局配置模式 (3)1.2.4端口配置模式 (4)1.2.5路由配置模式 (4)1.3 基本操作命令 (4)1.3.1保存配置 (4)1.3.2帮助 (5)1.3.3显示配置信息 (5)1.3.4显示路由信息 (5)1.3.5显示端口信息 (5)1.3.6显示VLAN信息 (5)1.3.7显示HSRP运行状况 (5)1.3.8ping、telnet、traceroute (5)1.3.9用命令方式重新启动交换机 (5)2 CA TAL YST4506配置 (6)2.1 基本信息配置 (6)2.2 VLAN配置 (7)2.3 配置第三层接口 (7)2.4 配置HSRP (8)2.5 配置路由 (9)2.6 设置TRUNK及端口绑定 (9)2.6.1TRUNK配置 (9)2.6.2端口绑定 (10)3 CA TAL YST2950配置 (10)3.1 基本信息配置 (10)3.2 配置VLAN (11)3.3 分配管理IP (12)3.4 配置静态路由 (12)鸿联95呼叫中心网络核心设备由2台CATAL YST4506交换机构成,二层交换机CA TAL YST2950分别以双千兆链路连接核心交换机。
关于本文档中的LVAN划分及IP地址分配,请详见《VLAN规划表》及《IP地址分配表》。
本文档按实际配置需求进行部分举例说明(不是全部配置),维护人员参照此文档配置步骤及相应命令,进行参数设置。
1 交换机操作基础1.1 登录登录CATALYST交换机有多种方式,常用的方式为CONSOLE口登录及TELNET登录。
如果交换机第一次被使用,必须通过CONSOLE口登录才可以对交换机进行设置。
CATALYST交换机随机配备一条CONSOLE线及1个9针转接头,CONSOLE线两头为RJ-45接口,一头可接入交换机的CONSOLE端口,另一头可连接9针转接头,并与PC 的COM口连接。
Cisco-Catalyst-4500系列交换机配置手册

目录CISCO CATALYST 4500系列交换机功能应用与安全解决方案 (4)一、CISCO CATALYST 4500系列交换机概述 (4)1、功能概述 (4)2、技术融合 (4)3、最优控制 (4)4、集成永续性 (4)5、高级QOS (5)#6、可预测性能 (5)7、高级安全性能 (5)8、全面的管理 (5)9、可扩展架构 (5)10、延长了增加投资的时间。
(5)11、CISCO CATALYST 4500系列产品线 (5)12、设备通用架构 (6)13、CISCO CATALYST 4500系列交换机的特点 (6)。
(1)性能 (6)(2)端口密度 (6)(3)交换管理引擎冗余性 (6)(4)以太网电源(POE) (7)(5)高级安全特性 (7)(6)CISCO IOS软件网络服务 (7)(7)投资保护 (7)(8)功能透明的线卡 (7)>(9)到桌面的千兆位连接 (8)(10)基于硬件的组播 (8)(11)CISCO NETFLOW服务 (8)(12)到桌面的光纤连接 (8)14、CISCO CATALYST 4500系列的主要特性 (8)15、CISCO CATALYST 4500系列交换机的优点 (10)16、CISCO CATALYST 4500系列的应用 (10)(1)采用以太网骨干的多层交换企业网络 (10)'(2)中型企业和企业分支机构应用 (10)二、CISCO CATALYST 4500系列交换机的解决方案 (11)1、DHCP的解决方案: (11)(1)不用交换机的DHCP功能而是利用PC的DHCP功能 (11)(2)利用三层交换机自带的DHCP功能实现多VLAN的IP地址自动分配 (11)(3)三层交换机上实现跨VLAN 的DHCP配置(路由器+三层交换机).............................. . (12)(4)相关的DHCP调试命令: (13)(5)DHCP故障排错 (13)$2、ARP防护的解决方案 (14)(1)基于端口的MAC地址绑定 (14)(2)基于MAC地址的扩展访问列表 (14)(3)基于IP地址的MAC地址绑定 (15)(4)CISCO的DAI技术 (15)3、VLAN技术的解决方案 (17)(1)虚拟局域网络(VIRTUAL LANS)简介 (17)(2)虚拟网络的特性 (17)#(3)发展虚拟网络技术的主要动能有四个: (18)(4)VLAN划分的6种策略: (18)(5)使用VLAN具有以下优点: (19)(6)CATALYST 4500系列交换机虚拟子网VLAN的配置: (19)(7)CATALYST 4500交换机动态VLAN与VMPS的配置 (20)的介绍: (20)客户机的介绍: (21)客户机的配置: (22)¥数据库配置文件模板: (23)4、CATALYST 4500系列交换机NAT配置: (24)4500系列交换机NAT的支持 (24)、NAT概述 (24)、NAT原理及配置 (24)5、三层交换机的访问控制列表 (26)利用标准ACL控制网络访问 (26)利用扩展ACL控制网络访问 (26)/基于端口和VLAN的ACL访问控制 (27)6. VTP 技术 (27)7、CISCO 交换机的端口镜像的配置: (30)CISCO 4507R 端口镜像配置方法 (30)、CISCO 4506交换机镜像端口配置方法 (32)8、CISCO CATALYST交换机端口监听配置 (32)9、CISCO 4500交换机的负载均衡技术 (32)10.双机热备HSRP (34)<三、CATALYST 4500系列交换机的安全策略 (36)(一) 三层交换机网络服务的安全策略 (36)(二)三层交换机访问控制的安全策略 (38)(三)三层交换机其他安全配置 (38)(1)及时的升级和修补IOS软件。
思科4506配置手册

系统状态:绿色(正常)/红色(故障)
交换机负载利用率:总交换使用率在1%到100%之间
控制端口:RJ-45凹式端口
重启(交换机隐含保护)
管理端口:10/100BASE-TX(RJ-45凹式)数据终端设备(DTE);绿色(工作正常)/橙色(禁用)/关闭(没有连接)
其它功能:
支持以下的GBIC模块:
{{fastethernet | gigabitethernet }
slot/interface - interface}]
进入组配置状态
Step 3
可以使用平时的端口配置命令进行配置
Step 4
end
退回
Step 5
show interfaces[interface-id]
验证配置
Step 6
copy running-config startup-config
SNMP v1、v2和v3检测,提供全面的带内管理功能
基于命令行界面(CLI)的管理控制台,提供详细的带外管理
远程监控(RMON)软件代理,可以支持四个RMON群组(历史、统计、警报和事件),从而可以增强对流量的管理、监控和分析
利用一个Cisco SwitchProbeAnalyzer(交换端口分析器[SPAN]端口支持所有九个RMON群组,这个端口可以通过一个单一的网络分析器或者RMON探测器对一个端口、一组端口或者整个交换机进行流量监控)
基于完整的第3/4层报头(只限于IP)进行分类和标记
基于完整的第3/4层报头(只限于IP)制定输入和输出策略
能够集中或者单独在出口或者入口分别配置1024种监管器
整形和共享输出队列管理
细微的QoS功能不会影响正常的交换性能
思科4506配置手册

4506交换机(IOS版)简明配置维护手册2003-10目录说明 (3)产品特性 (3)配置端口 (5)配置一组端口 (5)配置二层端口 (7)配置端口速率及双工模式 (8)端口描述 (8)配置三层口 (10)监控及维护端口 (12)监控端口和控制器的状态 (12)刷新、重置端口及计数器 (13)关闭和打开端口 (14)配置VLAN (15)理解VLAN (15)可支持的VLAN (15)配置正常范围的VLAN (16)生成、修改以太网VLAN (16)删除VLAN (18)将端口分配给一个VLAN (18)配置VLAN Trunks (19)使用STP实现负载均衡 (22)配置EtherChannel (27)三层以太通道配置 (27)三层物理端口配置 (28)二层以太通道配置 (29)配置以太通道负载均衡 (31)配置SPAN (32)理解SPAN (32)SPAN会话 (33)目标端口 (33)源端口 (33)流量类型 (33)基于VLAN的SPAN (33)SPAN流量 (34)配置SPAN (34)指定源 (34)指定目标 (35)监视一个trunk接口上的源VLAN (35)说明本手册只包括日常使用的有关命令及特性,其它未涉及的命令及特性请参考英文的详细配置手册。
产品特性Cisco Catalyst 4506将非阻塞的第2/3/4层交换与增强的控制结合在一起,从而让企业和城域以太网用户在部署基于互联网的应用时具有业务灵活性。
作为Cisco A VVID(融合语音、视频和集成数据的网络体系架构)的一个关键性组件,Cisco Catalyst 4500利用智能化的网络服务,将控制从网络骨干扩展到了网络边缘,这些服务包括先进的服务质量(QoS)、可扩展的性能、全面的安全性和简便的管理功能。
第2层特性•第2层硬件数据包转发率可达48Mpps•第2层交换端口和VLAN中继•IEEE 802.1Q VLAN封装•ISL VLAN封装(不包括WS-X4418-GB 和WS-X4412-2GB-T 中的阻塞端口)•动态中继协议(DTP)•VLAN中继协议(VTP)和VTP域•每个交换机支持4096个VLAN(将来的软件版本)•每个VLAN的生成树(PVST)和PVST+•STP PortFast和PortFast防护措施•STP UplinkFast和BackboneFast•STP根段防护措施•Cisco搜索协议•IGMP侦听v1和v2•在线路卡中集成Cisco以太通道、快速以太通道、千兆位以太通道技术•端口集中协议(PAgP)•单向链路检测(UDLD)和主动型UDLD第3层特性•IP Cisco快速传送(CEF)路由速度可达48Mpps•静态IP路由•IP路由协议(内部网关路由协议[IGRP]、增强型IGRP[EIGRP]、开放式最短路径优先[OSPF]、路由信息协议[RIP]、RIP2)•边界网关协议[BGP4]和多播边界网关协议[MBGP]•热待机路由协议(HSRP)•IGMP v1、v2和v3•IP多播路由协议(距离向量多播路由协议[DVMRP]、PIM、SSM)•多播源发现协议(MSDP)•Cisco群组多播协议(CGMP)服务器•完全支持互联网控制消息协议(ICMP)•ICMP路由器发现协议先进的服务质量和成熟流量管理•针对每个端口的QoS配置•硬件上支持每个端口四个队列•严格优先级排序•IP DSCP和IP 优先权•基于IP服务类型(ToS)或者DSCP进行分类和标记•基于完整的第3/4层报头(只限于IP)进行分类和标记•基于完整的第3/4层报头(只限于IP)制定输入和输出策略•能够集中或者单独在出口或者入口分别配置1024种监管器•整形和共享输出队列管理•细微的QoS功能不会影响正常的交换性能扩展性能•64Gbps交换矩阵•第2层硬件数据包转发率可达48Mpps•第3层IP Cisco 快速转发路由速率可达48Mpps•第4层(TCP/UDP)基于硬件的过滤速率可达48Mpps•实现先进的第3/4层服务不会造成任何性能上的损失•持续以每秒1000台主机的速度进行基于软件的查询•支持32768个MAC地址•在路由表(由单点播送和多播共享)中支持131072个记录•可以扩展到2000个虚拟端口(VLAN端口)•利用Cisco千兆位以太通道技术,可以汇聚高达16Gbps的带宽•基于硬件的多播管理•基于硬件的ACL简便的可管理性•只需一个控制台端口和IP地址,来管理系统中的所有功能•软件配置管理,包括本地和远程的存储•可选的闪存卡,可以用于存储软件影像,进行备份和方便的软件升级•通过CiscoWorks Windows网络管理软件,对每个端口、每个交换机进行管理,为Cisco的路由器、交换机和集线器提供一个统一的管理接口•SNMP v1、v2和v3检测,提供全面的带内管理功能•基于命令行界面(CLI)的管理控制台,提供详细的带外管理•远程监控(RMON)软件代理,可以支持四个RMON群组(历史、统计、警报和事件),从而可以增强对流量的管理、监控和分析•利用一个Cisco SwitchProbe Analyzer(交换端口分析器[SPAN]端口支持所有九个RMON群组,这个端口可以通过一个单一的网络分析器或者RMON探测器对一个端口、一组端口或者整个交换机进行流量监控)•分析支持,包括入口、出口和VLAN SPAN全面的安全性•TACACS+和RADIUS,它们可以对交换机进行集中控制,并防止未经授权的用户更改配置•在所有端口上的标准和扩展ACL•在所有端口上(没有性能损失)采用路由器访问控制列表(RACL)•专用VLAN(PVLAN),可以在一个交换机的两个端口之间提供安全性和独立性指示灯和端口规格•系统状态:绿色(正常)/红色(故障)•交换机负载利用率:总交换使用率在1%到100%之间•控制端口:RJ-45凹式端口•重启(交换机隐含保护)•管理端口:10/100BASE-TX(RJ-45凹式)数据终端设备(DTE);绿色(工作正常)/橙色(禁用)/关闭(没有连接)其它功能:支持以下的GBIC模块:•1000BASE-SX GBIC: 光纤最长1804 feet (550 m)•1000BASE-LX/LH GBIC: 光纤最长32,808 feet (6 miles or 10 km)•1000BASE-ZX GBIC: 光纤最长328,084 feet (62 miles or 100 km)配置端口配置一组端口当使用interface range命令时有如下的规则:•有效的组范围:o vlan从1 到4094o fastethernet槽位/{first port} - {last port}o gigabitethernet槽位/{first port} - {last port}•端口号之间需要加入空格,如:interface range fastethernet 2/1 –5是有效的,而interface range fastethernet 2/1-5是无效的.•interface range命令只能配置已经存在的interface vlan•所有在同一组的端口必须是相同类别的。
Cisco思科路由器配置手册
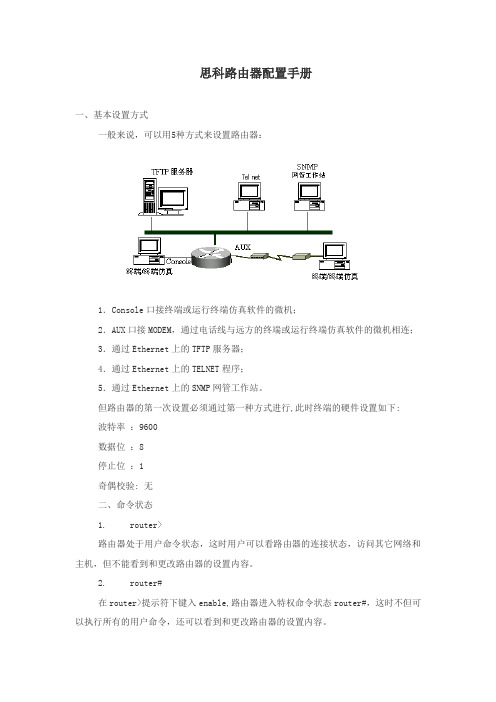
思科路由器配置手册一、基本设置方式一般来说,可以用5种方式来设置路由器:1.Console口接终端或运行终端仿真软件的微机;2.AUX口接MODEM,通过电话线与远方的终端或运行终端仿真软件的微机相连;3.通过Ethernet上的TFTP服务器;4.通过Ethernet上的TELNET程序;5.通过Ethernet上的SNMP网管工作站。
但路由器的第一次设置必须通过第一种方式进行,此时终端的硬件设置如下:波特率:9600数据位:8停止位:1奇偶校验: 无二、命令状态1. router>路由器处于用户命令状态,这时用户可以看路由器的连接状态,访问其它网络和主机,但不能看到和更改路由器的设置内容。
2. router#在router>提示符下键入enable,路由器进入特权命令状态router#,这时不但可以执行所有的用户命令,还可以看到和更改路由器的设置内容。
3. router(config)#在router#提示符下键入configure terminal,出现提示符router(config)#,此时路由器处于全局设置状态,这时可以设置路由器的全局参数。
4. router(config-if)#; router(config-line)#; router(config-router)#;…路由器处于局部设置状态,这时可以设置路由器某个局部的参数。
5. >路由器处于RXBOOT状态,在开机后60秒内按ctrl-break可进入此状态,这时路由器不能完成正常的功能,只能进行软件升级和手工引导。
6. 设置对话状态这是一台新路由器开机时自动进入的状态,在特权命令状态使用SETUP命令也可进入此状态,这时可通过对话方式对路由器进行设置。
三、设置对话过程显示提示信息全局参数的设置接口参数的设置显示结果利用设置对话过程可以避免手工输入命令的烦琐,但它还不能完全代替手工设置,一些特殊的设置还必须通过手工输入的方式完成。
分部网络设备基本配置(第六组+3月16日)

安博实训平台资源网络工程路由交换方向XXX网络项目基本配置安博教育集团一 网络描述二 基本配置2.1交换机Cisco WS-C4506 Cisco WS-C3750 Cisco WS-C2960 2.2.1 基本配置 2.2.1.1 设备访问首先使用随设备附带的配置Console 线缆,分别连接管理工作站的Com 端口和交换机的Console 端口;启动Windows 操作系统下的超级终端,配置参数如下;2.2.1.2 设备名称Router>enRouter#conf tRouter(config)#hostname DL-R-0012.2.1.3 设备口令设置远程访问用户口令DL-S-01(config)#line vty 0 4DL-S-01(config-line)#loginDL-S-01(config-line)#password liuzuDL-S-01(config-line)#exit2.2.1.4设置特权用户口令DL-S-01(config)#enable password liuzu2.2.1.5关闭DNS查找功能(默认时打开)DL-S-01(config)#no ip domain-lookup2.2.1.6启用logging synchronous 阻止控制台信息覆盖命令行上的输入DL-S-01(config)# line console 0DL-S-01(config-line)# logging synchronous2.2.1.7将exec-timeout设置为0 0 为控制台连接设置以秒或分钟的超时DL-S-01(config)#line con 0DL-S-01(config-line)#exec-t 0 02.2.1.8配置console口访问不需要密码DL-S-01(config)#line con 02.2.1.9IP地址配置DL-R-001DL-R-001(config)#int f0/0DL-R-001(config-if)#ip add 192.168.2.113 255.255.255.252 DL-R-001(config-if)#no shDL-R-001(config-if)#exitDL-R-001(config)#int f0/1DL-R-001(config-if)#ip add 192.168.2.117 255.255.255.252 DL-R-001(config-if)#no shDL-R-001(config-if)#exitDL-S-01DL-S-01(config)#int f0/6DL-S-01(config-if)#no swDL-S-01(config-if)#no switchportDL-S-01(config-if)#ip add 192.168.2.114 255.255.255.252 DL-S-01(config-if)#no shDL-S-01(config-if)#exitDL-S-01(config)#DL-S-02DL-S-02(config)#int f0/1DL-S-02(config-if)#no swDL-S-02(config-if)#no switchportDL-S-02(config-if)#ip add 192.168.2.118 255.255.255.252 DL-S-02(config-if)#no shDL-S-02(config-if)#exitDL-S-02(config)#2.2.1.10启用SSH并测试DL-R-001(config)#ip domain-naDL-R-001(config)#ip domain-name DL-R-001(config)#cryDL-R-001(config)#crypto keyDL-R-001(config)#crypto key genDL-R-001(config)#crypto key generate rsDL-R-001(config)#crypto key generate rsaDL-R-001(config)#username liuzuDL-R-001(config)#username liuzu passDL-R-001(config)#username liuzu password 123456 DL-R-001(config)#line vtDL-R-001(config)#line vty 0 15DL-R-001(config-line)#loginDL-R-001(config-line)#login loDL-R-001(config-line)#login localDL-R-001(config-line)#DL-S-01(config)#line vtyDL-S-01(config)#line vty 0 15DL-S-01(config-line)#logDL-S-01(config-line)#loginDL-S-01(config-line)#login loDL-S-01(config-line)#login localDL-S-01(config-line)#endDL-S-01#ssh ?-l Log in using this user name-v Specify SSH Protocol VersionDL-S-01#ssh -l liuzu 192.168.2.113OpenPassword:Password:DL-R-001>三检查设备的连通性3.1 show cdp neighbors命令的使用3.2 ping命令的使用。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
4506交换机(IOS版)简明配置维护手册2003-10目录说明 (3)产品特性 (3)配置端口 (5)配置一组端口 (5)配置二层端口 (7)配置端口速率及双工模式 (8)端口描述 (8)配置三层口 (10)监控及维护端口 (12)监控端口和控制器的状态 (12)刷新、重置端口及计数器 (13)关闭和打开端口 (14)配置VLAN (15)理解VLAN (15)可支持的VLAN (15)配置正常范围的VLAN (16)生成、修改以太网VLAN (16)删除VLAN (18)将端口分配给一个VLAN (18)配置VLAN Trunks (19)使用STP实现负载均衡 (22)配置EtherChannel (27)三层以太通道配置 (27)三层物理端口配置 (28)二层以太通道配置 (29)配置以太通道负载均衡 (31)配置SPAN (32)理解SPAN (32)SPAN会话 (33)目标端口 (33)源端口 (33)流量类型 (33)基于VLAN的SPAN (33)SPAN流量 (34)配置SPAN (34)指定源 (34)指定目标 (35)监视一个trunk接口上的源VLAN (35)说明本手册只包括日常使用的有关命令及特性,其它未涉及的命令及特性请参考英文的详细配置手册。
产品特性Cisco Catalyst 4506将非阻塞的第2/3/4层交换与增强的控制结合在一起,从而让企业和城域以太网用户在部署基于互联网的应用时具有业务灵活性。
作为Cisco A VVID(融合语音、视频和集成数据的网络体系架构)的一个关键性组件,Cisco Catalyst 4500利用智能化的网络服务,将控制从网络骨干扩展到了网络边缘,这些服务包括先进的服务质量(QoS)、可扩展的性能、全面的安全性和简便的管理功能。
第2层特性•第2层硬件数据包转发率可达48Mpps•第2层交换端口和VLAN中继•IEEE 802.1Q VLAN封装•ISL VLAN封装(不包括WS-X4418-GB 和WS-X4412-2GB-T 中的阻塞端口)•动态中继协议(DTP)•VLAN中继协议(VTP)和VTP域•每个交换机支持4096个VLAN(将来的软件版本)•每个VLAN的生成树(PVST)和PVST+•STP PortFast和PortFast防护措施•STP UplinkFast和BackboneFast•STP根段防护措施•Cisco搜索协议•IGMP侦听v1和v2•在线路卡中集成Cisco以太通道、快速以太通道、千兆位以太通道技术•端口集中协议(PAgP)•单向链路检测(UDLD)和主动型UDLD第3层特性•IP Cisco快速传送(CEF)路由速度可达48Mpps•静态IP路由•IP路由协议(内部网关路由协议[IGRP]、增强型IGRP[EIGRP]、开放式最短路径优先[OSPF]、路由信息协议[RIP]、RIP2)•边界网关协议[BGP4]和多播边界网关协议[MBGP]•热待机路由协议(HSRP)•IGMP v1、v2和v3•IP多播路由协议(距离向量多播路由协议[DVMRP]、PIM、SSM)•多播源发现协议(MSDP)•Cisco群组多播协议(CGMP)服务器•完全支持互联网控制消息协议(ICMP)•ICMP路由器发现协议先进的服务质量和成熟流量管理•针对每个端口的QoS配置•硬件上支持每个端口四个队列•严格优先级排序•IP DSCP和IP 优先权•基于IP服务类型(ToS)或者DSCP进行分类和标记•基于完整的第3/4层报头(只限于IP)进行分类和标记•基于完整的第3/4层报头(只限于IP)制定输入和输出策略•能够集中或者单独在出口或者入口分别配置1024种监管器•整形和共享输出队列管理•细微的QoS功能不会影响正常的交换性能扩展性能•64Gbps交换矩阵•第2层硬件数据包转发率可达48Mpps•第3层IP Cisco 快速转发路由速率可达48Mpps•第4层(TCP/UDP)基于硬件的过滤速率可达48Mpps•实现先进的第3/4层服务不会造成任何性能上的损失•持续以每秒1000台主机的速度进行基于软件的查询•支持32768个MAC地址•在路由表(由单点播送和多播共享)中支持131072个记录•可以扩展到2000个虚拟端口(VLAN端口)•利用Cisco千兆位以太通道技术,可以汇聚高达16Gbps的带宽•基于硬件的多播管理•基于硬件的ACL简便的可管理性•只需一个控制台端口和IP地址,来管理系统中的所有功能•软件配置管理,包括本地和远程的存储•可选的闪存卡,可以用于存储软件影像,进行备份和方便的软件升级•通过CiscoWorks Windows网络管理软件,对每个端口、每个交换机进行管理,为Cisco的路由器、交换机和集线器提供一个统一的管理接口•SNMP v1、v2和v3检测,提供全面的带内管理功能•基于命令行界面(CLI)的管理控制台,提供详细的带外管理•远程监控(RMON)软件代理,可以支持四个RMON群组(历史、统计、警报和事件),从而可以增强对流量的管理、监控和分析•利用一个Cisco SwitchProbe Analyzer(交换端口分析器[SPAN]端口支持所有九个RMON群组,这个端口可以通过一个单一的网络分析器或者RMON探测器对一个端口、一组端口或者整个交换机进行流量监控)•分析支持,包括入口、出口和VLAN SPAN全面的安全性•TACACS+和RADIUS,它们可以对交换机进行集中控制,并防止未经授权的用户更改配置•在所有端口上的标准和扩展ACL•在所有端口上(没有性能损失)采用路由器访问控制列表(RACL)•专用VLAN(PVLAN),可以在一个交换机的两个端口之间提供安全性和独立性指示灯和端口规格•系统状态:绿色(正常)/红色(故障)•交换机负载利用率:总交换使用率在1%到100%之间•控制端口:RJ-45凹式端口•重启(交换机隐含保护)•管理端口:10/100BASE-TX(RJ-45凹式)数据终端设备(DTE);绿色(工作正常)/橙色(禁用)/关闭(没有连接)其它功能:支持以下的GBIC模块:•1000BASE-SX GBIC: 光纤最长1804 feet (550 m)•1000BASE-LX/LH GBIC: 光纤最长32,808 feet (6 miles or 10 km)•1000BASE-ZX GBIC: 光纤最长328,084 feet (62 miles or 100 km)配置端口配置一组端口当使用interface range命令时有如下的规则:•有效的组范围:o vlan从1 到4094o fastethernet槽位/{first port} - {last port}o gigabitethernet槽位/{first port} - {last port}•端口号之间需要加入空格,如:interface range fastethernet 2/1 –5是有效的,而interface range fastethernet 2/1-5是无效的.•interface range命令只能配置已经存在的interface vlan•所有在同一组的端口必须是相同类别的。
见以下例子:4506# configure terminal4506(config)# interface range fastethernet2/1 - 54506(config-if-range)# no shutdown4506(config-if-range)#*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to up*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet2/2, changed state to up*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet2/3, changed state to up*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet2/4, changed state to up*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet2/5, changed state to up*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet2/05, changed state to up*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet2/3, changedstate to up*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet2/4, changedstate to up以下的例子显示使用逗号来配置不同类型端口的组:4506# configure terminal4506(config)# interface range fastethernet2/1 – 3, gigabitethernet3/1 - 24506(config-if-range)# no shutdown4506(config-if-range)#*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to up*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet2/2, changed state to up*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet2/3, changed state to up*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface GigabitEthernet3/1, changed state to up *Oct 6 08:29:28: %LINK-3-UPDOWN: Interface GigabitEthernet3/2, changed state to up *Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/ 1, changed state to up*Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/ 2, changed state to up*Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/ 3, changed state to up配置二层端口4506的所有端口缺省的端口都是二层口,如果此端口已经配置成三层端口的话,则需要用switchport来使其成为二层端口。
