ABSTRACT On the Scalability of IEEE 802.11 Ad Hoc Networks
ieee control system letters评价

ieee control system letters评价IEEE Control Systems Letters (CSL) is a prestigious journal in the field of control systems. In this article, we will evaluate the significance and impact of IEEE CSL, its features, and the process of submitting a manuscript for publication.To begin with, IEEE CSL is a peer-reviewed journal that focuses on the rapid publication of high-quality research papers in the field of control systems. It is a relatively new journal, established in 2017, but it has quickly gained recognition and has become a valuable resource for researchers and practitioners in the control systems community.One of the key features of IEEE CSL is its rigorous peer-review process. All manuscripts submitted to the journal undergo a thorough evaluation by experts in the field. This ensures that only the highest-quality research is published, maintaining the journal's reputation for excellence. The review process is also known for its efficiency and quick turnaround time, allowing authors to disseminate their work faster compared to many other journals in the field.Another notable feature of IEEE CSL is its focus on short papers. The journal primarily publishes letters, which are typically concise and compact articles that present significant and novel findings. This format encourages authors to focus on the core ideas and contributions of their research, making the papers more readable and accessible to a broad audience.The importance of IEEE CSL cannot be overstated. As a publication of the prestigious Institute of Electrical and Electronics Engineers (IEEE), it provides a platform for researchers to showcase their work to a global audience. The journal's high impact factor and association with IEEE contribute to increased visibility and recognition for authors, leading to potential collaborations and career advancements.Now let us delve into the process of submitting a manuscript to IEEE CSL. The first step is to carefully read the guidelines and instructions for authors provided on the journal's website. It is crucial to ensure that the manuscript adheres to the prescribed format, including font size, margins, and reference style.Next, the authors need to prepare their manuscript, presentingtheir research findings concisely and clearly. As IEEE CSL focuses on letters, it is essential to emphasize the novelty and significance of the work in a concise manner. The abstract and introduction should clearly outline the problem addressed, the proposed approach, and the key results.Once the manuscript is prepared, it can be submitted through the IEEE CSL online manuscript submission system. The submission should include all the required documents, such as the cover letter, manuscript file, and any supplementary materials. Authors can track the progress of their submission through the system and receive updates on the review process.After the submission, the manuscript will undergo a rigorous peer-review process. Typically, this involves evaluation by at least two anonymous reviewers who provide constructive feedback on the strengths and weaknesses of the research. Authors are given the opportunity to revise their manuscript based on the reviewers' comments and submit a revised version.If the manuscript is accepted, it will be published in the next available issue of IEEE CSL. The authors will also have theopportunity to present their work at conferences and workshops associated with the journal, providing further exposure and networking opportunities.In conclusion, IEEE Control Systems Letters is a highly regarded journal in the field of control systems, offering a platform for rapid and high-quality dissemination of research. Its focus on short letters, along with its stringent peer-review process, ensures that only significant and novel contributions make it to publication. Submitting a manuscript to IEEE CSL requires careful adherence to guidelines and the presentation of concise and clear research findings. The journal's association with IEEE and its high impact factor contribute to its significance and impact in the control systems community.。
Ultra WideBand (UWB) 系统介绍

~172~Βιβλιοθήκη PPM + THSS
Str(t)
transmitting 0 pulse wtr(t)
Tc Tf Ts : data symbol time
t
Str(t)
transmitting 1
δ
δ Tc Tf
δ
δ t
Ts
codeword C = [1 0 0 2] , N h = 3 code period N p = 4 Ts = N s ⋅ T f i.e. , Ts = 4 ⋅ T f N s : number of pulses per data symbol T f ≥ N h ⋅ Tc i.e., T f = 3 ⋅ Tc
~171~
Impulse Radio UWB Techniques (1)
Time-Modulated (Hopping) UWB (TM(H)-UWB) — low duty cycle (Impulse radio) — data modulation by pulse position (time dithering) or signal polarity — multiaccess channelization by time coding (Time- Hopping, TH) — for precise location, tracking, radar sensing (through wall), data communications
校园网的规划与设计-毕业论文【范本模板】

校园网规划与设计摘要随着计算机、通信和多媒体技术的发展,使得网络上的应用更加丰富.同时在多媒体教育和管理等方面的需求,对校园网络也提出进一步的要求。
因此需要一个高速的、先进的、可扩展的校园计算机网络以适应当前网络技术发展的趋势并满足学校各方面应用的需要。
作为教育基石的学校,在培养先进的人才的同时,也迫切需要有高性能、高可靠性、扩展性好的网络解决方案。
本文阐述了校园网的应用特点,以及网络产品如何满足校园网用户的多方面需求.并对校园网建设提供一套大众化的方案:首先分析对象的现状及需求,再确定网络总体设计方案,进而分析结构化布线、网络技术选型、设备选型,设计网络拓扑结构并建设,最后对网络设备进行配置及包括IP子网划分和VLan配置.关键词:校园网、网络设备、协议Campus plan and designAbstractWith the computer, communications and multimedia technology, makes the network more extensive application. At the same time in multimedia education and management needs of the campus network is also further requirements。
Therefore need a high-speed, advanced and scalable campus computer network to adapt to current trends in the development of network technology and applications to meet the needs of all aspects of the school。
Schools as an educational foundation in training advanced talents, but also an urgent need for high performance, high reliability, scalability good networking solutions。
中英文论文写作(摘要)
1 基本特性 2 时态 3 语态 4 语法修辞 5 一个典型示例 6 化学常用句式
2 时态
以一般现在时为主, 也使用一般过去时和 现在完成时 从理论上讲: 说法一: 一般现在时
通过科 学实验取得的 研究结果、结 论,揭示自然 界的客观规律 一般过去时
Objective 动词不定式开头 To investigate … To study … To explore … To examine … To determine … To report … To review … 使用第一人称时,用凡指的we, the author, the authors ,不用I。 如: In this paper we conclude …
Result: The contents of the components of midecamyc A1 and leucomycin A6 was 30%~ 50% and 10%~20% respectively, the contents of the rest components w lower, different manufactures produces have differ components. Conclution: To revise the specificati meleumycin for quality control.
指示性文摘(indicative abstract)
This type of abstract is designed to ind the subject of a paper, making it easy fo potential readers to decide whether to r the paper.
IEEE8021aq(SPB)协议详解

Lui Simonetti & Gates Zeng
Where are we coming from ?
L2 Bridged Networks
L3 IP Routed Networks
L2 networks did not scale So L3 (IP) routing had to be
3. L2 OAM tool
2. Scalable Control Plane
– Availability of Link State Protocols such as: IS-IS & OSPF
– 802.1ag brings sophisticated OAM tools, which can complement and
2. Scalable Control Plane
– Availability of Link State Protocols such as: IS-IS & OSPF
3. IP OAM Tools
– ping, traceroute
4. IP Virtualization possible
– But requires BGP & MPLS for scalability
IEEE 802.1aq
1998 Virtual Lans (VLAN Tagging)
2005 Provider Bridging (QinQ)
2008
Provider Backbone Bridging (MacInMac)
2011 Shortest Path Bridging (SPBV & SPBM)
IEEE Computer Society (IEEE CS) 全文期刊(23种)列表及简介
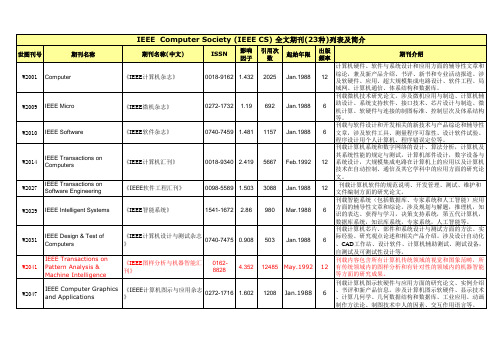
W2001
Computer
《IEEE计算机杂志》
0018-9162 1.432
Jan.1988
W2009
IEEE Micro
《IEEE微机杂志》
0272-1732
1.19
692
Jan.1988
6
W2010
IEEE Software
《IEEE软件杂志》
0740-7459 1.481
1157
Jan.1988
0098-5589 1.503
3088
Jan.1988
12
W2029
《IEEE智能系统》
1541-1672
2.86
980
Mar.1988
6
W2031
IEEE Design & Test of Computers IEEE Transactions on Pattern Analysis & Machine Intelligence
《IEEE移动计算汇刊》 《IEEE科学与工程计算杂志 》 《IEEE互联网计算杂志》 《IEEE多媒体杂志》
1536-1233 1521-9615 0.75 341 806 424
Jan.2002 Mar.1994 Jan.1997 Mar.1994
12 6 6 4
1089-7801 2.554 1070-986X 1.243
Mar.1995 Jan.1999 Jan.2003
6 6 6
W2128
《IEEE-ACM计算生物学与生 1545-5963 物信息学汇刊》
Jan.2004
4
IEEE Computer Society (IEEE CS) 全文期刊(23种)列表及简介
ieee conference on decision and control 检索

ieee conference on decision and control 检索IEEE conference on decision and control (CDC) is a prominent annual conference in the field of systems, control, and decision-making. Focusing on new theories, methodologies, and applications, CDC serves as a platform for researchers and practitioners to exchange ideas and present their latest findings. In this article, we will explore the significance of CDC, its history, and key topics covered in the conference.CDC has a long history dating back to 1962 when it was first held. Since then, it has grown into a prestigious conference attracting experts and professionals from academia, industry, and government organizations. The conference features a wide range of technical sessions, workshops, panel discussions, and keynote speeches by distinguished speakers. The topics covered in CDC are diverse and encompass various aspects of control and decision-making, including but not limited to:1. Control Theory: CDC provides a platform for discussing state-of-the-art control theory and its applications. Topics such as stability analysis, optimal control, robust control, adaptive control, and nonlinear control are frequently discussed in the conference.2. Decision Theory: Decision-making plays a crucial role in many fields such as finance, economics, and operations research. CDC explores decision models, algorithms, and methods for solving decision-making problems in uncertain and dynamic environments.3. System Identification and Estimation: Estimating system parameters and identifying system models are essential tasks incontrol systems. CDC focuses on techniques for system identification, parameter estimation, and model validation.4. Robotics and Automation: With advancements in robotics and automation, CDC features sessions and workshops dedicated to discussing topics related to autonomous systems, robot control, machine learning in robotics, and human-robot interaction.5. Networked Control Systems: Networked systems have become ubiquitous in various domains such as transportation, energy, and communication networks. CDC explores control methodologies for networked systems, including networked estimation, networked control, and distributed control.6. Game Theory and Multi-agent Systems: Game theory provides a mathematical framework for analyzing decision-making in multi-agent systems. CDC discusses game-theoretic approaches to system design, coordination, and cooperation in multi-agent systems.7. Cyber-Physical Systems (CPS): CDC addresses challenges and solutions related to integrating physical systems with computational elements. Topics include modeling and control of CPS, sensor networks, and real-time systems.In addition to the technical sessions, CDC also organizes tutorial sessions presented by experts in the field. These tutorials offer an opportunity for attendees to learn about the fundamentals and recent developments in specific areas of control and decision-making.CDC also hosts several competitions, such as the Student Best Paper Competition and the Student Poster Competition, to encourage young researchers to showcase their work and interact with peers and mentors.Apart from the technical program, CDC provides ample opportunities for networking and collaboration among participants. The conference attracts researchers, practitioners, and industry professionals from all over the world, providing a diverse and stimulating environment for knowledge sharing and collaboration. In conclusion, IEEE conference on decision and control (CDC) is a significant annual event in the field of systems, control, and decision-making. With its rich history and expansive technical program, CDC serves as a platform for researchers and practitioners to exchange ideas, present their latest findings, and foster collaboration in various areas of control and decision-making.。
abstract - LES摘要-莱斯

▪ In particular, by providing for traditionally language based capabilities like scope rules and exception handling.
N. Minsky, PUC Nov25/05
6
Potential Benefits of Laws, and their Pitfalls
➢ The benefits
▪ They could engender predictability—despite the openness and heterogeneity of the system at hand—thus simplifying it.
--rests on the following simple observations: ▪ In the absence of natural laws of software, we
need to formulate artificial laws, like we do for societies.
▪ Involves hierarchy of laws, and interoperability between them.
▪ Generalizing the concept of workflows ➢ Flexible regulation of dynamic coalitions
▪ As in grids, virtual enterprises, supply chains.
➢ How can one reason about such systems?
IEEE期刊论文翻译

期刊论文翻译一:一种纳米级的辐射加固CMOS锁存器设计和性能分析文章英文名称:Design and Performance Evaluation of Radiation Hardened Latches for Nanoscale CMOS作者:Sheng Lin, Yong-Bin Kim, and Fabrizio Lombardi第一作者单位:Electrical and Computer Engineering Department, Northeastern University, Boston, United States原文出版出处:IEEE Transactions on Very Large Scale Integration (VLSI) Systems, v 19, n 7, p 1315-1319, July 2011摘要:深亚微米/纳米CMOS电路对外部辐射现象更敏感,有可能导致所谓的软错误的发生。
因此,在纳米级的电路设计中电路的软错误容忍度是有严格要求的。
由于传统的容错方法,在电力方面、面积和性能方面耗费大量的成本,存储单元的低功耗加固设计发展(如插销和存储器)越来越重要。
本文提出三个新加固设计的CMOS锁存器,工艺尺寸为32纳米,这些电路是基于施密特触发器的,而第三个电路采用了在反馈回路级联配置。
级联ST锁存器的临界电荷比传统的锁存器高112%,而面积增加只有10%。
一种锁存器新型的设计指标(QPAR)去测试总体设计效果,包括面积、性能、功耗和抗软错误。
(QPAR)表明,设计的级联ST锁存器与现有的加固设计方法相比实现多达36%的改进。
蒙特卡罗分析了本文中加固锁存器对电压、温度(PVT)的变化曲线。
关键词:电路可靠性,加固锁存器,纳米CMOS工艺,抗辐射加固,稳健设计。
一、简介INTRODUCTION由于纳米技术从探索到工业实践发展迅速,纳米电路的操作已被广泛地进行了分析。
ieee transaction under review

ieee transaction under reviewTitle: An Effective Approach for Intrusion Detection in Wireless Sensor Networks: A Survey and ReviewAbstract:With the growing usage of Wireless Sensor Networks (WSNs) in various applications, security has become a paramount concern. Intrusion detection systems (IDSs) are widely employed to detect and mitigate security threats in WSNs. This paper presents a comprehensive survey of recent advancements in intrusion detection techniques for WSNs. We categorize the existing approaches based on detection models, clustering algorithms, and data aggregation techniques. Furthermore, we discuss the challenges and limitations associated with current solutions and propose potential directions for future research. The effectiveness of these approaches is assessed through extensive experiments using real-world datasets. Our findings provide valuable insights for researchers and practitioners who are interested in developing robust intrusion detection systems for WSNs.1. IntroductionWireless Sensor Networks (WSNs) consist of a large number of low-cost and small-sized sensor nodes that collaboratively monitor and collect data from a physical environment. Due to their widespread deployment in critical applications, such as environmental monitoring, healthcare, and military operations, WSNs are vulnerable to various security threats, including node compromise, message tampering, and denial of service (DoS) attacks. Intrusion detection systems (IDSs) play a crucial role in detecting and mitigating such threats. In this paper, we aim toprovide a comprehensive survey of intrusion detection techniques for WSNs, highlighting their strengths and limitations.2. Review MethodologyWe reviewed a wide range of research papers and publications from prestigious IEEE journals and conferences to identify relevant studies on WSN intrusion detection. The selected papers were analyzed and categorized based on the detection models, clustering algorithms, and data aggregation techniques adopted. 3. Detection ModelsDifferent models have been proposed for detecting intrusions in WSNs, including anomaly-based, signature-based, and hybrid models. Anomaly-based IDSs detect deviations from baseline behavior, while signature-based IDSs match observed patterns against known attack signatures. Hybrid IDSs combine the strengths of both approaches to achieve higher detection accuracy. This section provides a detailed analysis of these models, comparing their advantages and disadvantages.4. Clustering AlgorithmsClustering algorithms are widely used in IDSs to group sensor nodes based on their similarity to identify anomalies. We review several popular clustering algorithms, including k-means, hierarchical clustering, and fuzzy clustering, with a focus on their suitability for WSNs. The impact of different clustering parameters on detection accuracy and energy consumption is discussed. We also present a comparative analysis of these algorithms based on experimental results.5. Data Aggregation TechniquesData aggregation techniques play a crucial role in reducing transmission overhead and energy consumption in WSNs. However, they can also introduce vulnerabilities and enable attacks. This section reviews various data aggregation techniques, such as spatial and temporal aggregation, and discuss their implications for intrusion detection. We highlight the trade-off between energy efficiency and security, providing insights into the selection of appropriate data aggregation techniques for different scenarios.6. Challenges and Future DirectionsDespite the advancements in intrusion detection techniques for WSNs, several challenges remain, including resource constraints, scalability, and resilience to sophisticated attacks. This section discusses these challenges and proposes potential solutions and future research directions. We emphasize the need for the development of lightweight and distributed IDSs that can effectively detect and prevent attacks while meeting the resource constraints of WSNs.7. Experimental EvaluationTo evaluate the effectiveness of different intrusion detection approaches, we conducted extensive experiments using real-world datasets. We compare the detection accuracy, false alarm rate, and energy consumption of different models, clustering algorithms, and data aggregation techniques. The experimental results provide insights into the performance of these approaches and enable us to identify the most effective combinations for practical deployment.8. ConclusionThis paper provides a comprehensive survey and review of recent advancements in intrusion detection techniques for WSNs. We categorize and analyze the existing approaches based on detection models, clustering algorithms, and data aggregation techniques. The challenges and limitations associated with current solutions are discussed, and potential directions for future research are proposed. Our evaluation results using real-world datasets provide valuable insights for researchers and practitioners working on robust intrusion detection systems for WSNs.。
计算机领域等级会议

顶级会议,在美国召开
IC设计领域
29
IEEEVLSITestSymposium
一级会议,在美国召开
测试领域
30
IEEE/ACMDesign,AutomationandTest inEurope
一级会议,在欧洲召开
设计与测试领域
31
IEEEAsianTestSymposium
一级会议,在亚洲召开
测试领域
无线网络领域新兴得重要国际会议,内容侧重于adhoc网络。
生灭过程——精选推荐

⽣灭过程基于⽣灭过程的机群系统⾼可⽤性分析与设计*⾼⽂祝明发(中国科学院计算技术研究所国家智能计算机研究开发中⼼,北京,100080,)摘要随着机群中结点数⽬的增加,系统失效的概率也将增⼤。
为保证超级服务器提供连续不间断的服务,要求系统具有⾼可⽤性。
本⽂在对机群系统的运⾏特性进⾏分析的基础上,运⽤马⽒过程描述了机群系统中的⾼可⽤性(High Availability),并从理论上建⽴了基于⽣灭过程的机群⾼可⽤模型。
⽂中在给出机群⾼可⽤管理软件结构的基础上,设计了⼀种基于集中式结构的主副容错协议;通过可⽤度的分析结果得出:机群⾼可⽤系统采⽤了可修复性技术后,只要有⼀个HA结点能正常⼯作,该系统是“可⽤”的。
关键词机群系统,⾼可⽤性,可扩展性,⽣灭过程中图法分类号TP338.6; TP3161引⾔机群是⼀组物理上通过⾼速互连⽹连接在⼀起的计算机集合,通过附加的机群系统软件,互相协作,作为⼀个整体对外提供服务,其中每个计算机称为⼀个结点。
机群系统的优点是可扩展性好。
但随着机群系统规模的增⼤,结点数⽬的增多,机群系统整体的可靠性会相应降低。
因此提⾼机群系统可⽤性的软件将成为机群操作系统中必不可少的部分。
基于UNIX的⾼可⽤机群系统⾸先出现于80年代末期,随后,各主要UNIX⼚家纷纷推出⾃⼰的⾼可⽤系统,如IBM HACMP, Sun Solitice, HP service Guard等[1][2][3]。
⽽微软也于1997年推出了Windows NT上的Wolfpack机群软件[4]。
直到90年代后期,⼤部分的系统只⽀持2~4个结点和1~2个关键应⽤。
随着Internet使⽤的迅猛发展,应⽤软件对服务器的性能要求⼜有了进⼀步的提⾼。
⾼性能计算机引⼊事物处理领域已成必然,⽽其可扩展性和⾼可⽤性,即能⽀持⼏⼗甚⾄⼏百的可扩展的⾼可⽤系统,将成为近年来的研究热点。
本⽂的研究即为机群系统中的⾼可⽤性。
第2部分建⽴基于⽣灭过程的多机⾼可⽤模型,为设计机群的⾼可⽤软件提供了理论基础。
毕业设计的英文翻译----开放式控制器体系结构 - 过去,现在和未来

Open Controller Architecture - Past, Present and FutureGunter Pritschow (Co-ordinator), Yusuf Altintas, Francesco Jovane, Yoram Koren, Mamoru Mitsuishi, Shozo Takata, Hendrik van Brussel, Manfred Weck, Kazuo YamazakiAbstractOpen Control Systems are the key enabler for the realization of modular and re-configurable manufacturing systems. The large number of special purpose machines and the high level of automation have led to an increasing importance of open control systems based on vendor neutral standards. This paper gives an overview on the past, present and future of Open Controller Architecture. After reflecting on the different criteria, categories and characteristics of open controllers in general, the CNC products in the market are evaluated and an overview on the world-wide research activities in Europe, North America and Japan is given. Subsequently the efforts to harmonize the different results are described in order to establish a common world-wide standard in the future. Due to the “mix-and-match’’ nature of open controllers concentrated attention must be paid to testing mechanisms in the form of conformance and interoperability tests.Keywords: Open architecture control, CNC, Machine tool1 INTRODUCTIONOpen Architecture Control (OAC) is a well known term in the field of machine control. Since the early nineties several initiatives world-wide have worked on concepts for enabling control vendors, machine tool builders and end-users to benefit more from flexible and agile production facilities. The main aim was the easy implementation and integration of customer-specific controls by means of open interfaces and configuration methods in a vendor-neutral, standardized environment [13][19].The availability and broad acceptance of such systems result in reduced costs and increased flexibility. Software can be reused and user-specific algorithms or applications can be integrated. Users can design their controls according to a given configuration. This trend was forced both by the increasing number of special purpose machines with a high level of automation and the increasing development costs for software (Figure 1).Figure 1: CNC Hardware and software -Actual trend existingIn the past the CNC market was dominated by heterogeneous, device-oriented systems with proprietary hardware and software components. The tight coupling of application software, system software and hardware led to very complex and inflexible systems. Great efforts were made to maintain and further develop the products according to new market requirements. Modern CNC approaches, which comprise extensive functionality to achieve a high quality and flexibility of machining results combined with a reduced processing time, favor PC- based solutions with a homogenous, standardized environment (Figure 2). The structure is software- oriented and configurable due to defined interfaces and software platforms. Open control interfaces are necessary for continuously integrating new advanced functionality into control systems and are important for creating re-configurable manufacturing units [17]. Unbundling hardware and software allows profiting from the short innovation cycles of the semiconductor industry and information technology. With the possibility for reusing software components, the performance of the overall system increases simply by upgrading the hardware platform.Figure 2: PC-based, software-oriented Control SystemsThere are a lot of benefits for suppliers and users of open control systems (Figure 3) [7]. CNC designers and academics benefit from a high degree of openness coveringalso the internal interfaces of the CNC. For CNC users the external openness is much more important. It provides the methods and utilities for integrating user-specific applications into existing controls and for adapting to user-specific requirements, e.g. adaptable user interfaces or collection of machine and production data. The external openness is mainly based on the internal openness but has functional or performance Iimitations .2 STATE OF THE ART2.1 Control Systems and their interfacesControls are highly sophisticated systems due to very strict requirements regarding real-time and reliability. For controlling the complexity of these systems hardware and software interfaces are an essential means. The interfaces of control systems can be divided into two groups-external and internal interfaces (Figure4).External InterfacesThese interfaces connect the control system to superior units, to subordinate units and to the user. They can be divided into programming interfaces and communication interfaces. NC and PLC programming interfaces are harmonized by national or international standards, such as RS-274, DIN 66025 or IEC 61131-3. Communication interfaces are also strongly influenced by standards. Fieldbus systems like SERCOS, Profibus or DeviceNet are used as the interface to drives and 110s. LAN (Local Area Network) networks mainly based on Ethernet and TCP/lP do reflect the interfaces to superior systems.Internal InterfacesInternal interfaces are used for interaction and data- exchange between components that build up the control- system core. An important criterion in this area is the support of real-time mechanisms. To achieve a re-configurable and adaptable control the internal architecture of the control system is based on a platform concept. The main aims are to hide the hardware-specific details from the software components and to establish a defined but flexible way of communication between the software components. An application programming interface(API) ensures these requirements. The whole functionality of a control system is subdivided into several encapsulated, modular software components interacting via the defined API.2.2 Hardware and software structure of control systemsFigure 5 shows different variants for the hardware structures of control systems. Variant a) shows an analog drives interface with position controller in the control system core. Each module of this structure uses its own processor which leads to a large variety of vendor-specific hardware. Combining modules leads to a significant reduction of the number of processors. Variant b) shows intelligent digital drives with integrated control functionality, which result from higher capacity, miniaturization and higher performance of the processors. Variant c) shows a PC-based single processor solution with a real-time extension of the operating system. All control-functions run as software tasks in the PC-based real-time environment.2.3 Market overviewThe controls available in the market provide different levels of openness according to the criteria shown in Figure 6. An important criterion is the use of a standardized computing platform (i.e. hardware, operating system and middleware) as an environment to execute the HMI and CNC software. Besides this, the connectivity of the CNC to upper and lower factory levels must be guaranteed. Application Programming Interfaces (API) are used to integrate third party software in the CNC products. Al though most of today’s controls offer openness concerning the operator-related control functions (Human-Machine Interface, HMI) only few controls allow users to modify their low-level control algorithms to influence the machine-related control functions.Figure 7 gives an overview of the characteristics of today’s control s ystems regarding the degree of openness.Although many control systems provide open interfaces for software integration (e.g. OPC) there is still no common definition of data which is passed back and forth via the programming interface. Therefore, the control systems available on the market today do not implicitly support “plug-and-play” features. To improve this situation, the fieldbus systems can serve as a role model (see Figure 8). The variety of different fieldbus systems has led to the broad consensus that harmonizing the application-oriented interfaces is desirable in order to hide the plurality and the complexity of the systems from the user. Most fieldbus organizations are already using so-called device profiles in order to support the interchangeability of the devices of different vendors.For example, the SERCOS interface standard (IEC61491) for the cyclic and deterministic communication between CNC and drives has defined the semantics forapprox. 400 parameters describing drive and control functions which are used by the devices of different vendors.3 DEFINITIONS AND CATEGORIES OF OPENNESS3.1 DefinitionsThe “Technical Committee of Open Systems” of IEEE defines an open system as follows: “An open system provides capabilities that enable properly implemented applications to run on a variety of platforms from multiple vendors, interoperate with other system applications and present a consistent style of interaction with the user” (IEEE 1003.0).To estimate the openness of a controller the following criteria can be applied (Figure 9):Portability. Application modules (AM) can be used on different platforms without any changes, while maintaining their capabilities.Extendibility. A varying number of AM can run on a platform without any conflicts.Inferoperability. AM work together in a consistent manner and can interchange data in a defined way.Scalability. Depending on the requirements of the user, functionality of the AM and performance and size of the hardware can be adapted.To fulfill the requirements of the IEEE-definition and these criteria of openness, an open control system must be:vendor neutral. This guarantees independence of single proprietary interests.consensus-driven. It is controlled by a group of vendors and users (usually in the form of a user group or an interested group).standards-based. This ensures a wide distribution in the form of standards (national/international standards or de-facto standards).freely available. It is free of charge to any interested party.3.2 Categories of Open Control SystemsIf we speak of openness in control systems, the following categories can be identified (Figure 10):Open HMl: The openness is restricted to the non-real-time part of the control system. Adaptations can be made in user oriented applications.Kernel with restricted openness: The control kernel has a fixed topology, but offers interfaces to insert user-specific filters even for real-time functions.Open Control System: The topology of the control kernel depends on the process. It offers interchangeability, scalability, portability and interoperability.Open control systems that are available today mostly offer the possibility for modifications in the non-real-time part in a fixed software topology. They lack the necessary flexibility and are not based on vendor-neutral standards.3.3 RequirementsA vendor-neutral open control system can only be realized if the control functionality is subdivided in functional units and if well-defined interfaces between these units are specified (Figure 11). Therefore modularity can be identified as the key for an open system architecture. In determining the module complexity there is an obvious trade-off between the degree of openness and the cost of integration [6]. Smaller modules provide a higher level of openness and more options, but increase the complexity and integration costs. Furthermore such a low level of granularity can lead to much higher demands for resources and it may even deteriorate the real-time performance of the overall system.Combining modules in the manner of “mix-and-match’’ requires a comprehensive set of standard Application Programming Interfaces (APIs). For vendor-neutral open control systems the interfaces need to be standardized and broadly accepted. Due to the complexity of such modular systems the definition of a system architecture is recommendable and helpful. This leads to the introduction of so-called system platforms (Figure 12). These platforms encapsulate the specifics of a computing system by absorbing the characteristics of hardware, operating system and communication. The availability of such middleware systems facilitates the easy porting of application software and also the interoperability of application modules even in distributed heterogeneous environments.Due to the possibility to “mix-and-match’’ modules via standardized interfaces the quality of the overall system is determined by the degree of the interoperability between the single modules (see Section 5).4 SYSTEMS ON THE WAY TO THE MARKET4.1 Major international activitiesOSEC (Japan)The OSE (Open System Environment for Manufacturing) consortium was established in December 1994. Three project phases were carried out until March 1999 [1][2][3]. The OSEC Architecture was intended to provide end users, machine makers, control vendors, software vendors, system integrators, etc. a standard platform for industrial machine controllers, with which they can add their own unique values to the industrial machines, and hence promote the technical and commercial development of the industrial machines. The OSEC API is defined in the form of an interface protocol, which is used to exchange messages among controller software components representing the functionality and the real- time cycle. Each functional block can be encapsulated as an object so it is not necessary to deal with how a functional block processes messages to it at architecture level (Figure 13). Although the structure of functional blocks can be defined uniquely by the OSEC architecture from a logical point of view, the system is neither determined nor limited at its implementation phase because there are so many options for implementations. These options may include system contrivances such as device driver, interprocess communication, installation mechanisms such as static library and DLL, hardware factors like selection of controller card, and implementations of software modules added for execution control and/or monitoring of various software. In other words, the implementation model to realize the architecture model is not limited to a particular model. In this way, it is assured to incorporate various ideas in the implementation model depending on the system size or its hardware implementation and/or utilization.JOP (Japan)In parallel to the OSE consortium activities, MSTC formed the Open-Controller Technical Committee (OC- TC) from 1996 to 2000, under the umbrella of JOP (Japanese Open Promotion Group). The objectives of OC-TC were to provide the opportunities for various companies to discuss and work together on the standardization of open controller technologies. The OC- TC was also expected to act as liaison between domestic and international activities in this field. OC-TC was participated by approximately 50 members, which included major Japanese controller vendors, machine tool builders, integrators, users, and academics. Some of the members represented the other groups concerning open controllers such as the OSE consortium and the FA Intranet Promotion Group .One of the working groups was engaged in developing a standard API for interfacing between NC and PC-based HMI. It should be also effective for the communication between NC and an upper level management controller. The work was carried out based on the proposals from the major controller vendors and that from the OSE consortium. The developed specifications were named PAPI and released July, 1999 [4] [5]. PAPI was approved as a JIS (Japan Industrial Standard) technical report and published in October, 2000. To demonstrate the effectiveness of the specifications developed by OC-TC, in Nagoya in October 1999, two CNCs manufactured by different vendors were connected to a Windows NT machine in which the same HMI systems developed by the University of Tokyo were implemented (Figure 14). Since any specific controller architecture is not assumed, PAPI can be implemented in various types of existing CNC systems, such as PC + proprietary NC, PC + NC board, and Software NC on PC+110 board. The HMI system communicates with the CNCs via PAPI which is a function-oriented software library in the programming language C. The PAPI interface is neutralizing the vendor-specific interface by mapping the PAPI calls to the vendor-specific API and protocol.OMAC (USA)The Open Modular Architecture Controllers (OMAC) Users Group is an industry forum to advance the state of controller technology [l0]. An effort was undertaken within OMAC to define API specification for eventual submittal to an established standards body. The OMAC API adopted a component-based approach to achieve plug-and-play modularization, using interface classes to specify the API [11]. For distributed communication, component-based technology uses proxy agents to handle method invocations that cross process boundaries. OMAC API contains diffe rent “sizes” and “types” of reusab le plug-and-play components - component, module, and task - each with a unique Finite State Machine (FSM) model so that component collaboration is performed in a known manner. The term component applies to reusable pieces of software that serves as a building block within an application while the term module refers to a container of components. Tasks are components used to encapsulate programmable functional behavior consisting of a series of steps that run to completion, including support for starting, stopping, restarting, halting, and resuming, and may be run multiple times while a controller is running. Tasks can be used to build controller programs consisting of a series of Transient Tasks, with ability to restart and navigate, or as standalone Resident Tasks to handle specialized controller requirements, (e.g., axis homing or ESTOP).To integrate components, a framework is necessary to formalize the collaborations and other life cycle aspects in which components operate. The OMAC API uses Microsoft Component Object Model (COM) as the initial framework in which to develop components, with the expected benefit that control vendors could then concentrate on application-specific improvements that define their strategic market-share - as opposed to spending valuable programming resources reinventing and maintaining software “plumbing.”The primary problem with COM framework, specifically under the Windows 2000 operating system, is the lack of hard, real-time preemptive scheduling, but third party extensions to Windows 2000 can be used to overcome this requirement.Figure 15 illustrates a sketch of OMAC API controller functionality. The HMI module is responsible for human interaction with a controller including presenting data, handing commands, and monitoring events and in the OMAC API “mirrors” the actual controller with references to all the major modules and components via proxy agents. The Task Coordinator module is responsible for sequencing operations and coordinating the various modules in the system based on programmable Tasks. The Task Coordinator can be considered the highest level Finite State Machine in the controller. A Task Generator module translates an application-specific control program (e.g., RS 274 part program) into a series of application-neutral Transient Tasks. The Axis Group module is responsible for coordinating the motions of individual axes, transforming an incoming motion segment specification into a sequence of equi-time- spaced setpoints for the coordinated axes. The Axis module is responsible for servo control of axis motion, transforming incoming motion setpoints into setpoints for the corresponding actuators 10 points. The Control Law component is responsible for servo control loop calculations to reach specified setpoints. OSACA (Europe)In Europe the ESPRIT project OSACA (Open System Architecture for Controls within Automation Systems) was initiated in 1992 with the aim to unite European interests and to create a vendor-neutral standard for open control systems[9][16].It was supported by major European control vendor and machine tool builders. OSACA reached a mature state already in April 1996 having at its disposal a stable set of specifications and a tested pool for system software. Based on these results, several application-oriented projects were carried out. In 1988 two pilot demonstrators in the automotive industry proved the interoperability of OSACA-compliant controllers and applications. The OSACA association eth currently 35 members from all over the word is the lasting organization to keep and maintain the OSACA-related specifications.The basic technical approach of the OSACA architecture is the hierarchical decomposition of control functionality into so-called functional units (Figure 16).For each of these functional units (e.g. motion control, motion control manager, axescontrol, logic control, etc.) the interfaces are specified by applying object-oriented information models. This technique is similar to the approach of MAP/MMS but with a limited and manageable number of object classes.The data interface consists of several variable objects that support the read and/or write access to data structure(data flow).The data can be of a simple type or of a complex type(array, structure, union).By using formal templates(Figure17) all the characteristics of a single interface object are specified. These elements cover the name (e.g, “mc-active-feed-override”), the type (e.g. UNS32: 32-bit unsigned value), the scaling (e.g. 0.l%),the range and the access rights (read only, to all the major modules and components via proxy write only, read/write) of the data. An additional description is to avoid misinterpretations of the use of the data. The process interface consists of several process objects that are used to describe the dynamic behavior (control flow) of the application modules by means of finite state machine (FSM). The state machines are described by static states, dynamic states and transitions to change the states of a given state-machine. The transitions can handle input and output parameters to pass data between application modules via the communication platform. The formal template for such process interfaces consists of an unambiguous description and the following attributes: list of static states (identifier, list of possible transitions), list of dynamic states (identifier) and a list of transitions (input parameters, output parameters, return codes). The process interface can also be used to activate application-specific functions in form of procedure calls. The interoperability of distributed application modules is supported by an infrastructure (so-called OSACA platform) which comprises client-server principles, synchronous and asynchronous calls and event handling via any underlying communication protocol and media (e.g. by using the TCP/lP protocol). A dedicated configuration runtime system is handling the system’s startup and shutdown. Besides, it also allows an easy reconfiguration of the system.开放式控制器体系结构- 过去,现在和未来摘要开放式控制系统是用于模块化和可重新配置制造系统实现的关键推动者。
IEEE-805-1984.pdf

Recognized as an American National Standard (ANSI)IEEE Std 805-1984 IEEE Recommended Practice for System Identification in Nuclear Power Plants and Related FacilitiesSponsorPower Generation Committeeof theIEEE Power Engineering SocietyApproved June 23, 1983IEEE Standards BoardApproved November 15, 1984American National Standards Institute© Copyright 1984 byThe Institute of Electrical and Electronics Engineers, Inc345 East 47th Street, New York, NY 10017, USANo part of this publication may be reproduced in any form, in an electronic retrieval system or otherwise, without the prior written permission of the publisher.IEEE Standards documents are developed within the Technical committees of the IEEE Societies and the Standards Coordinating Committees of the IEEE Standards Board. Members of the committees serve voluntarily and without compensation. They are not necessarily members of the Institute. The standards developed within IEEE represent a consensus of the broad expertise on the subject within the Institute as well as those activities outside of IEEE which have expressed an interest in participating in the development of the standard.Use of an IEEE Standard is wholly voluntary. The existence of an IEEE Standard does not imply that there are no other ways to produce, test, measure, purchase, market, or provide other goods and services related to the scope of the IEEE Standard. Furthermore, the viewpoint expressed at the time a standard is approved and issued is subject to change brought about through developments in the state of the art and comments received from users of the standard. Every IEEE Standard is subjected to review at least once every five years for revision or reaffirmation. When a document is more than five years old, and has not been reaffirmed, it is reasonable to conclude that its contents, although still of some value, do not wholly reflect the present state of the art. Users are cautioned to check to determine that they have the latest edition of any IEEE Standard.Comments for revision of IEEE Standards are welcome from any interested party, regardless of membership affiliation with IEEE. Suggestions for changes in documents should be in the form of a proposed change of text, together with appropriate supporting comments.Interpretations: Occasionally questions may arise regarding the meaning of portions of standards as they relate to specific applications. When the need for interpretations is brought to the attention of IEEE, the Institute will initiate action to prepare appropriate responses. Since IEEE Standards represent a consensus of all concerned interests, it is important to ensure that any interpretation has also received the concurrence of a balance of interests. For this reason IEEE and the members of its technical committees are not able to provide an instant response to interpretation requests except in those cases where the matter has previously received formal consideration.Comments on standards and requests for interpretations should be addressed to:Secretary, IEEE Standards Board345 East 47th StreetNew York, NY 10017USAForeword(This Foreword is not a part of IEEE Std 805-1984, IEEE Recommended Practice for System Identification in Nuclear Power Plants and Related Facilities.)In April 1979, the Working Group on Unique Identification in Power Plants of the Station Design Subcommittee was formed and charged with the task of producing a series of recommended practices for unique identification in power plants. Later, realizing that this concept provided the same benefits to other types of facilities, the title was extended to include and related facilities.This series of recommended practices, entitled the Energy Industry Identification Systems (ELIS), provides a single source of unique identification of systems, structures, and components for all types of power generation and related facilities with provision for the inclusion of currently established plant system identifier codes. Using this series of recommended practices, which includes principles, a table of component function identifier codes, implementation instructions, and system descriptions for the various types of power plants and related facilities, a user can correlate a system, structure, or component with another organization for purposes of reporting, comparison, or general communication. Numerous economic, safety, and convenience benefits can be derived from this concept. IEEE Std 805 deals with system descriptions and system codes for nuclear power plant systems.The purpose of this working group was to generate an industry-wide language of communication which users could employ at the interface of their organizations and which would not require them to change a viable identification concept which they were using internally. In the event that the users do not have a viable identification concept of their own, they may choose to employ this concept for their internal applications since it has been successfully applied by several utilities and architect/engineering firms.If conflicts with other standards are discovered, they will be handled in a revision.This recommended practice was prepared by the Working Group for Unique Identification in Power Plants and Related Facilities, Station Design Subcommittee of the Power Generation Committee.At the time this recommended practice was approved, the members of the working group were:J. L. Parris, ChairO. M. Anderson Alex Barlas M. R. Belew V. T. Carlson L.T. Gordon D.T. HallF. J. Hebdon W. C. Henry P. J. HoeflerF. H. HoernschmeyerS. JordanJ. R. KoupalS. MukhoR. D. NalvenD. A. NormanF. M. PattersonR. W. RohwederC. O. RemineM. H. RothsteinP. D. Sierer, JrR. L. SimardG. E. SimoneauxF. W. SloatJ. G. StaudtAt the time the IEEE Standards Board approved this standard on June 23, 1983 it had the following members:James H. Beall, ChairEdward Chelotti, Vice ChairSava I. Sherr, SecretaryJ. J. Archambault John T. Boettger J. V. Bonucchi Rene Castenschiold Edward J. Cohen Len S. CoreyDonald C. FleckensteinJay ForsterDonald H. HeirmanIrvin N. HowellJoseph L. Koepfinger*Irving KolodnyGeorge KonomosR. F. LawrenceJohn E. MayDonald T. Michael* John P. Riganati Frank L. Rose Robert W. SeelbachJay A. StewartClifford O. SwansonRobert E. WeilerW. B. WilkensCharles J. Wylie*Member emeritusAt the time this recommended practice was approved, the members of the Power Generation Committee were:R. Zwigler, ChairD. Diamant, Vice ChairR. W. Cantrell, SecretaryJ. C. Appiarius W. W. Avril M. S. Baldwin J. H. BellackI. B. Berezowski G. BermanG. C. BoyleF. L. Brennan P.G. Brown E. F. ChelottiH. E. Church, Jr C. H. Clarridge R. S. Coleman R. E. CottaM. L. Crenshaw R. S. DarkeP. Davidson A. C. Dolbec G. R. Engman W. H. Esselman V. F. Estcourt T. F. Faulkner W. M. Fenner A. H. FerberD. I. GordenR. D. HandelJ. J. HeagertyM. E. JackowskiE. F. KaprielianF. E. KeayP. R. LandrieuS. LawP. LewisH. E. LokayG. L. LuriJ. T. MadillJ. D. MatherO. S. MazzoniA. J. McElroyT. M. McMahonJ. L. MillsW.S. MorganP. A. NevinsS. NikolokockosJ. T. NikolasR. E. PennJ. D. PlaxcoR. J. ReimanF. D. RobbinsD. E. RobertsW.J. RomRg ScottJ. J. SeibertM. N. SprouseA. J. SpurginR. B. SquiresJ. V. StephensG. I. StillmanJ. E. Stoner, JrV. C. SulzbergerS. TjepkemaR. H. WaltmanE. J. WarcholM. WarrenK. L. WestJ. P. WhooleyR. F. WilletC. J. WylieT. D. YounkinsComments, suggestions, and requests for interpretation may be addressed to: SecretaryIEEE Standards BoardThe Institute of Electrical and Electronic Engineers, Inc.345 East 47th StreetNew York, NY 10017CLAUSE P AGE1. Scope and Purpose (1)2. Discussion (1)3. References (2)4. Conventions (8)5. System Descriptions (14)IEEE Recommended Practice for System Identification in Nuclear Power Plants and Related Facilities1. Scope and Purpose1.1 ScopeThis recommended practice provides a single source of nuclear power plant system descriptions which, along with related recommended practices concerning unique identification principles and definitions, component function identifiers, and implementation instructions, makes up a concept for uniquely identifying systems, structures, and components of light water nuclear power plant projects (electric power generating stations) and related facilities. Fossil, hydro, and other types of power plants are not included in this edition.1.2 PurposeThe purpose of this series of recommended practices is to present a common language of communication which will permit a user to correlate a system, structure, or component with another organization for the purposes of reporting, comparison, or general communication. It does not require a using organization to change its own internal identification concept, but if the organization chooses to do so it has only to transcode at the interface from their internal language to this common language concept.The user may choose to adopt this concept for internal organizational use. It represents the accumulated practice of the industry assimilated into one set of practices. A significant feature of this concept is that the unique identification code identifies the function at the component level and not the hardware itself.2. DiscussionThe system descriptions concentrate on system function and include such internal details as is necessary to clearly support the system function description. They are not intended to serve as design input. System diagrams also show connections with major interfacing systems, and major components in these interfacing systems, where appropriate to enhance communication of the system function. The system description grouping, as indicated by the first character ofIEEE Std 805-1984IEEE RECOMMENDED PRACTICE FOR SYSTEM IDENTIFICA TION the two-alpha-character code, is designed to favor the convenience of plant operation rather than plant design and construction.The system descriptions and diagrams represent typical systems and are not intended for design purposes. When a system function can be accomplished by significantly different system internal designs, the system description includes a brief identification of major design alternatives to serve as an aid for correlating plant specific system designs with this classification concept. The differences among PWR system nomenclature and system designs were not included in this classification concept because of the functional similarity among the different PWR designs, A single set of system nomenclature and system boundaries has been defined for all PWR designs.The major differences between PWR and BWR system nomenclature and system internal designs have been preserved in that separate system descriptions and diagrams are provided, where appropriate.The symbols used in the system diagrams were selected to represent accepted practice as much as possible.3. ReferencesWhen the following standards referred to in this recommended practice are superseded by a revision, the latest revision shall apply.[1] ANSI/IEEE Std 100-1977, IEEE Standard Dictionary of Electrical and Electronics Terms.[2] IEEE Std 803-1983, IEEE Recommended Practice for Unique Identification in Power Plants and Related Facilities—Principles and Definitions.[3] IEEE Std 803A-1983, IEEE Recommended Practice for Unique Identification in Power Plants and Related Facilities—Component Function Identifiers.[4] IEEE Std 804-1983, IEEE Recommended Practice for Unique Identification in Power Plants and Related Facilities—Implementation.Table 1—EIIS System List—Alphabetical by System CodeA — Primary Heat Source Systems GroupAA Control Rod Drive System (BWR)Fig 2 AA Control Rod Drive System (PWR)Fig 3 AB Reactor Coolant System (PWR)Fig 4 AC Reactor Core SystemAD Reactor Recirculation System (BWR)Fig 5B — Engineered Safety Systems GroupBA Auxiliary/Emergency Feedwater System (PWR)BB Containment Combustible Gas Control SystemBC Containment Ice Condenser System (PWR) Refrigeration Subsystem Fig 8 BC Containment Ice Condenser System (PWR) Ice Condenser Subsystem Fig 9 BD Containment Leakage Control SystemBE Containment Spray System (PWR)Fig 10 BF Containment Vacuum Relief SystemIN NUCLEAR POWER PLANTS AND RELA TED FACILITIES IEEE Std 805-1984Table 1—EIIS System List—Alphabetical by System Code (Continued)BG High-Pressure Core Spray System (BWR)Fig 11 BH Emergency/Standby Gas Treatment System Fig 12 BI Essential Service Water System Fig 13 BJ High-Preseure Coolant Injection System (BWR)Fig 14 BK Containment Fan Cooling System (PWR)Fig 15 BL Isolation Condenser System (BWR)Fig 16 BM Low Pressure Core Spray System (BWR)Fig 17 BN Reactor Core Isolation Cooling System (BWR)Fig 18 BO Residual Heat Removal/Low Pressure Coolant Injection System (BWR)Fig 19 BP Residual Heat Removal/Low Pressure Safety Injection System (PWR)Fig 20 BQ High Pressure Safety Injection System (PWR)Fig 21 BR Standby Liquid Control System (BWR)Fig 22 BS Ultimate Heat Sink SystemBT Suppression Pool Makeup System (BWR)Fig 23C — Reactor Auxiliaries Systems GroupCA Boron Recycle System (PWR)Fig 24 CB Chemical and Volume Control/Makeup and Purification System (PWR)Fig 25(a) and (b) CC Closed/Component Cooling Water System Fig 26 CD Control Rod Drive Cooling System (PWR)Fig 27 CE Reactor Water Cleanup System (BWR)Fig 28 CF Reactor Services SystemCG Suppression Pool Purification System (BWR)Fig 29D — Fuel Management Systems GroupDA Fuel Pool Cooling and Purification SystemDB Nuclear Fuel Services SystemDC Diesel Fuel Oil System Fig 30 DR Fuel Oil Receiving Storage, and Transfer System Fig 31 DF Nuclear Fuel Transfer SystemE — Electrical Power Systems GroupEA Medium-Voltage Power System (601V through 35 kV)Fig 32 EB Medium-Voltage Power System—Class 1E Fig 33 EC Low-Voltage Power System (600V and less)Fig 34 ED Low-Voltage Power System—Class 1E Fig 35 EE Instrument and Uninterruptible Power System Fig 36 EF Instrument and Uninterruptible Power System—Class 1E Fig 37 E1DC Power System Fig 38 EJ DC Power System—Class 1E Fig 39 EK Emergency Onsite Power Supply System Fig 40 EL Main Generator Output Power System Fig 41F — Electrical Support Systems GroupFA Cable Raceway SystemIEEE Std 805-1984IEEE RECOMMENDED PRACTICE FOR SYSTEM IDENTIFICA TIONTable 1—EIIS System List—Alphabetical by System Code (Continued)FB Cathodic Protection SystemFC Grounding and Lightning Protection SystemFD Heat Tracing SystemFE Heat Tracing System—Class 1EFF Normal AC Lighting SystemFG Standby AC Lighting SystemFH Emergency DC Lighting SystemFI Communications SystemFJ Station Generation Telemetering SystemFK Switchyard SystemI — Instrumentation and Monitoring Systems GroupIA Security SystemIB Annunciator SystemIC Fire Detection SystemID Computer SystemIG Incore/Excore Monitoring SystemIH Core Vibration Monitoring SystemII Loose Parts Monitoring SystemIJ Leak Monitoring SystemIK Containment Environmental Monitoring System Fig 42 IL Radiation Monitoring SystemIM Temperature Monitoring SystemIN Seismic Monitoring SystemIO Performance Monitoring SystemIP Pest Accident Monitoring SystemIQ Sequence of Events Monitoring SystemIR Television SystemIS Environmental/Meteorological Monitoring System (Ex PLT)IT Main Turbine Instrumentation SystemIU Display Control SystemIV Vibration Monitoring SystemJ — Protection and Control Systems GroupJA Integrated Control SystemJB Feedwater/Steam Generator Water Level Control SystemJC Plant Protection SystemJD Reactor Power Control SystemJE Engineered Safety Features Actuation SystemJG Solid State Control System/Auxiliary Logic Control SystemJI Turbine Steam Bypass Control System Turbine Supervisory Control SystemJK Feedwater Pump Turbine Instrumentation and Control SystemJL Panels SystemJM Containment Isolation Control SystemK — Water, Chemical, and Drainage Systems GroupKA Condensate Storage and Transfer System Fig 43 KB Turbine Building Closed Cooling Water System Fig 44 KC Demineralized Water Storage and Transfer System Fig 45 KD Condensate and Feedwater Chemistry Control SystemKE Heat Rejection System Fig 46 KF Heat Rejection Chemical Treatment SystemKG Nonessential Service Water System Fig 47 KH Water Filtration System Fig 48 KI Raw Water Makeup SystemKJ Makeup Demineralizer System Fig 49 KK Potable Water Distribution System Fig 50 KL Removable Chemical Cleaning SystemKM Chilled Water SystemKN Sampling and Water Quality System Fig 51 KO Gland Seal Water Supply System Fig 52 KP Fire Protection System (Water)Fig 53 KQ Fire Protection System (Chemical)L — Service Auxiliaries Systems GroupLA Diesel Lube Oil SystemLB Diesel Cooling Water SystemLC Diesel Generator Starting Air System Fig 54 LD Instrument Air Supply SystemLE Essential Air SystemLF Service Air System Fig 55 LG Welding Gas SystemLH Breathing Air SystemLJ Hydrogen Supply SystemLK Nitrogen Supply System Fig 56 LL Lube Oil SystemLM Lube Oil Storage and Transfer System Fig 57 LN Insulating Oil System Fig 58 LP Laboratory Gas SystemLQ Laboratory Equipment SystemLR Material and Equipment Handling SystemLS Plant Shop SystemLT Record Storage SystemLU Yard Handling and Maintenance SystemLV Plant Hot Water SystemLW Carbon Dioxide (CO2) Supply SystemM — Site Facility Buildings and Structures GroupMA Administration BuildingMB Industrial/Sanitary Waste Treatment BuildingMC Maintenance and Warehouse BuildingMD Makeup Water Intake StructureMF Service BuildingMG Wastewater Outfall StructureMH Water Treatment BuildingMJ Visitors CenterMK Essential Service Water Pump BuildingN — Power Generation Buildings and Structures GroupNA Control Building/Control ComplexNB Emergency Onsite Power Supply BuildingNC Emergency Operations Facility (Offsite)ND Fuel BuildingNE Radwaste BuildingNF Auxiliary BuildingNG Reactor Building (BWR)NH Reactor Containment BuildingNM Turbine BuildingNN Circulating Water StructuresS — Steam Cycle Systems GroupSA Auxiliary Steam System Fig 59 SB Main/Reheat Steam System Fig 60 SD Condensate System Fig 61 SE Steam Extraction System Fig 62 SF Condensate Demineralizer System Fig 63 SG Condenser System Fig 64 SH Condenser Vacuum System Fig 65 SI Condenser Tube Cleaning System Fig 66 SJ Feedwater System Fig 67 SK Feedwater Pump Injection and Miscellaneous System Fig 68 SL Feedwater Pump Turbine Lube Oil System Fig 69 SM LP Heater Drains and Vents System Fig 70 SN HP Heater and MSR Drains and Vents System Fig 71T — Power Conversion Systems GroupTA Main Turbine System Fig 72 TB Main Generator SystemTC Turbine Steam Seal System Fig 73 TD Turbine Lube Oil System Fig 74TE Miscellaneous Turbine Vents SystemTF Turbine Drains and Miscellaneous Piping SystemTG Main Turbine Control Fluid System Fig 75 TH Main Generator Gas Purge SystemTI Main Generator Seal Oil SystemTJ Main Generator Stator Cooling System Fig 76 TK Main Generater Hydrogen Cooling System Fig 77 TL Main Generator Excitation SystemU — Site Facility Environmental Control Systems GroupUA Pumping Station Environmental Control SystemUB Water Treatment Building Environmental Control SystemUC Service Building Environmental Control SystemUD Administration Building Environmental Control SystemUE Security Building Environmental Control SystemUF Technical Support Center Environmental Control SystemUG Emergency Operations Facility Environmental Control SystemUH Visitors Center Environmental Control SystemV — Power Generation Buildings Environmental Control Systems GroupVA Reactor Building Environmental Control SystemVB Drywell Environmental Control System (BWR)VC Shield Annulus Return and Exhaust SystemVE Access Corridors Environmental Control SystemVF Auxiliary Building Environmental Control SystemVG Fuel Building Environmental Control SystemVH Radwaste Building Environmental Control SystemVI Control Building/Control Complex Environmental Control SystemVJ Emergency Onsite Power Supply Building Environmental Control SystemVK Turbine Building Environmental Control SystemVL Plant Exhaust SystemW — Waste Management Systems GroupWA Cask Decontamination System Fig 78 WB Solid Waste Management SystemWD Liquid Waste Management SystemWE Gaseous Waste Management System (PWR)Fig 79 WF Offgas System (BWR)Fig 80 WG Sanitary Waste Processing System Fig 81 WH Wastewater Disposal System Fig 82 WI Steam Generator Blowdown System (PWR)Fig 83 WJ Sludge Waste Dewatering SystemWK Equipment and Floor Drain System4. ConventionsThe sequence identifier associated with a specific piece of equipment is assigned at the discretion of the organization applying the code. However, if the intent of the recommended practice is to be achieved, there must be uniformity in the assignment of system designators and function identifiers. To achieve this uniformity in the assignment of system identifiers, the following conventions regarding system cognizance should be followed:1)Heat Exchangers. Heat exchangers are considered to be located in the system in which they perform a heatingor cooling function in support of plant power production. Heat exchangers which provide both a heatings and cooling function (for example, Condensate blowdown cooler) are assigned to the system which, under normal plant conditions, operates at the higher temperature.2)Instruments. Sensors are assigned to the system in which they sense. Actuators are assigned to the system inwhich the actuation takes place.3)Circuit Breakers. Where circuit breakers control specific equipment, the circuit breaker is assigned to thesystem in which the equipment is assigned. Where circuit breakers control the distribution of electrical power they are assigned to that electrical distribution system.4)Valves. Valves are assigned to the system in which they control fluid flow.5)Transformers. Transformers are assigned to the lower voltage system.Table 2—EIIS System List—Alphabetical by System TitleVE Access Corridors Environmental Control SystemMA Administration BuildingUD Administration Building Environmental Control SystemIB Annunciator SystemNF Auxiliary BuildingVF Auxiliary Building Environmental Control SystemBA Auxiliary/Emergency Feedwater System (PWR)Fig 6 SA Auxiliary Steam System Fig 59 CA Boron Recycle System (PWR)Fig 24 LH Breathing Air SystemFA Cable Raceway SystemLW Carbon Dioxide (CO2) Supply SystemWA Cask Decontamination System Fig 78 FB Cathodic Protection SystemCB Chemical and Volume Control/Makeup and Purification System (WR)Fig 25(a) and (b) KM Chilled Water SystemNN Circulating Water StructuresCC Closed/Component Cooling Water System Fig 26 FI Communications SystemID Computer SystemKD Condensate and Feedwater Chemistry Control SystemSF Condensate Demineraliser System Fig 63 KA Condensate Storage and Transfer System Fig 43 SD Condensate System Fig 61 SG Condenser System Fig 64SI Condenser Tube Cleaning System Fig 66 SH Condenser Vacuum System Fig 65 BB Containment Combustible Gas Control System Fig 7 IK Containment Environmental Monitoring System Fig 42 BK Containment Fan Cooling System (PWR)Fig 15 BC Containment Ice Condenser System (PWR) Refrigeration System Fig 8 BC Containment Ice Condenser System (PWR) Ice Condenser Subsystem Fig 9 JM Containment Isolation Control SystemBD Containment Leakage Control SystemBE Containment Spray System (PWR)Fig 10 BF Containment Vacuum Relief SystemNA Control Building/Control ComplexVI Control Building/Control Complex Environmental Control SystemCD Control Rod Drive Cooling System (PWR)Fig 27 AA Control Rod Drive System (BWR)Fig 2 AA Control Rod Drive System (PWR)Fig 3 IH Core Vibration Monitoring SystemEI DC Power System Fig 38 EJ DC Power System—Class 1E Fig 39 KC Demineralised Water Storage and Transfer System Fig 45 LB Diesel Cooling Water SystemDC Diesel Fuel Oil System Fig 30 LC Diesel Generator Starting Air System Fig 54 LA Diesel Lube Oil SystemIU Display Control System (DCS)VB Drywell Environmental Control System (BWR)FH Emergency DC Lighting SystemNB Emergency Onsite Power Supply BuildingVJ Emergency Onsite Power Supply Building Environmental Control SystemEK Emergency Onsite Power Supply System Fig 40 UG Emergency Operations Facility Environmental Control SystemNC Emergency Operations Facility (Offsite)BH Emergency/Standby Gas Treatment System Fig 12 JE Engineered Safety Features Actuation SystemIS Environmental/Meteorological Monitoring System (Ex PLT)WK Equipment and Floor Drain SystemLE Essential Air SystemMK Essential Service Water Pump BuildingBI Essential Service Water System Fig 13 SK Feedwater Pump Injection and Miscellaneous System Fig 68 JK Feedwater Pump Turbine Instrumentation and Control SystemSL Feedwater Pump Turbine Lube Oil System Fig 69 JB Feedwater/Steam Generator Water Level Control SystemSJ Feedwater System Fig 67 IC Fire Detection SystemKQ Fire Protection System (Chemical)KP Fire Protection System (Water)Fig 53 ND Fuel BuildingVG Fuel Building Environmental Control SystemDE Fuel Oil Receiving, Storage, and Transfer System Fig 31 DA Fuel Pool Cooling and Purification SystemWE Gaseous Waste Management System (PWR)Fig 79 KO Gland Seal Water Supply System Fig 52 FC Grounding and Lightning Protection SystemSN HP Heater and MSR Drains and Vents System Fig 71 KF Heat Rejection Chemical Treatment System Fig 47 KE Heat Rejection System Fig 46 FD Heat Tracing SystemFE Heat Tracing System—Class 1EBJ High Pressure Coolant Injection System (BWR)Fig 14 BG High Pressure Core Spray System (BWR)Fig 11 BQ High Pressure Safety Injection System (PWR)Fig 21 LJ Hydrogen Supply SystemIG Incore/Excore Monitoring SystemMB Industrial/Sanitary Waste Treatment BuildingLD Instrument Air Supply SystemEE Instrument and Uninterruptible Power System Fig 36 EF Instrument and Uninterruptible Power System—Class 1E Fig 37 LN Insulating Oil System Fig 58 JA Integrated Control SystemBL Isolation Condenser System (BWR)Fig 16 SM LP Heater Drains and Vents System Fig 70 LQ Laboratory Equipment SystemLP Laboratory Gas SystemIJ Leak Monitoring SystemWD Liquid Waste Management SystemII Loose Parts Monitoring SystemBM Low Pressure Core Spray System (BWR)Fig 17 EC Low-Voltage Power System (600 V and less)Fig 34 ED Low-Voltage Power System—Class 1E Fig 35 LM Lube Oil Storage and Transfer System Fig 57 LL Lube Oil SystemTL Main Generator Excitation SystemTH Main Generater Gas Purge SystemTK Main Generator Hydrogen Cooling System Fig 77 EL Main Generator Output Power System Fig 41 TI Main Generator Seal Oil SystemTJ Main Generator Stator Cooling System Fig 76 TB Main Generator SystemSB Main/Reheat Steam System Fig 60 TG Main Turbine Control Fluid System Fig 75 IT Main Turbine Instrumentation SystemTA Main Turbine System Fig 72 MC Maintenance and Warehouse BuildingKJ Makeup Demineralizer System Fig 49 MD Makeup Water Intake StructureLR Material and Equipment Handling SystemEA Medium-Voltage Power System (601 V through 35 kV)Fig 32 EB Medium-Voltage Power System—Class 1E Fig 33 TE Miscellaneous Turbine Vents SystemLK Nitrogen Supply System Fig 56 KG Nonessential Service Water SystemFF Normal AC Lighting SystemDB Nuclear Fuel Services SystemDF Nuclear Fuel Transfer SystemWF Offgas System (BWR)Fig 80 JL Panels SystemIO Performance Monitoring SystemVL Plant Exhaust SystemLV Plant Hot Water SystemJC Plant Protection SystemLS Plant Shop SystemIP Post Accident Monitoring SystemKK Potable Water Distribution System Fig 50 UA Pumping Station Environmental Control SystemIL Radiation Monitoring SystemNE Radwaste BuildingVH Radwaste Building Environmental Control SystemKI Raw Water Makeup SystemNG Reactor Building (BWR)VA Reactor Building Environmental Control SystemNH Reactor Containment BuildingAB Reactor Coolant System (PWR)Fig 4。
基于ND 芯片的脊髓电刺激器的设计

探索与创基于ND芯片的脊髓电刺激器的设计冯超1马早2(1.西部机场集团有限公司机场建设指挥部陕西西安712035;2.西安咸阳国际机场股份有限公司陕西西安712035)摘要:本设计在介绍复杂疼痛治疗原理的“闸门学说”基础上,采用国产ND芯片,单片机等电路设计制作了脊髓电刺激器,实现了刺激阻抗测量,可编程多波形刺激信号的输出,可编程刺激通道的选择和休眠唤醒的工作方式;采用精细加工技术和热成型技术设计制作了刺激电极;这些设计具有体积小,耗电量低,可靠性高的特点。
经对样机的测试,所设计的刺激器符合要求。
关键词:SCS神经病理性疼痛刺激电极神经调节单片机中图分类号:TN911.7文献标识码:A文章编号:1674-098X(2021)10(a)-0181-03 Design of Spinal Cord Electrical Stimulator Based on ND ChipFENG Chao1MA Zao2(1.Airport Construction Headquarters of Western Airport Group Co.,Ltd.,Xi'an,Shaanxi Province,712035China;2.Xi'an Xianyang International Airport Co.,Ltd.,Xi'an,Shaanxi Province,712035China) Abstract:On the basis of introducing the"gate theory"of complex pain treatment principle,this design uses domestic ND chip,single chip microcomputer and other circuits to design and manufacture spinal cord electric stimulator.The measurement of stimulation impedance,the output of programmable multi waveform stimulation signal,the selection of programmable stimulation channel and the working mode of sleep wake-up are realized.The stimulation electrode is designed and fabricated by fine machining technology and thermoforming technology.These designs have the characteristics of small volume,low power consumption and high reliability.Through the test of the prototype,the designed stimulator meets the requirements.Key Words:SCS;Neuropathic pain;Stimulating electrode;Neuromodulation;Single chip1背景神经病理性疼痛(Neuropathic Pain,NP)是由躯体感觉神经系统的损伤及疾病所导致的疼痛,以痛觉过敏、痛觉超敏、自发性疼痛和感觉异常等为主要表现,这类疼痛多数是由不同的疾病和损害引起的综合征,疼痛的机理复杂,导致临床上这类病人的治疗不充分完善,严重影响了生活质量,给病人带来了更大的痛苦和经济负担。
ieee iscas best paper 价值

ieee iscas best paper 价值IEEE ISCAS Best Paper (IEEE ISCAS最佳论文) - 价值及其重要性引言:IEEE国际电子电气工程师协会国际混合信号电路及系统研讨会(International Symposium on Circuits and Systems, ISCAS)是世界上最大的关于电子电气工程的学术研讨会之一。
每年在世界各地举办的ISCAS都会评选出该年度最佳论文。
本文将探讨IEEE ISCAS最佳论文的价值及其重要性,以及该奖项背后的影响和意义。
一、IEEE ISCAS最佳论文的价值及意义(The value and significance of IEEE ISCAS Best Paper)ISCAS最佳论文奖项的价值在于其对学术界的认可和鼓励。
这个奖项代表了对出色研究的肯定,同时也鼓励研究者在该领域继续深入研究。
ISCAS 研讨会是该领域内与会者进行交流和分享最新研究成果的重要平台,因此ISCAS最佳论文的评选也反映了该领域的学术水平和创新程度。
ISCAS最佳论文的获奖者不仅能够在全球范围内获得广泛的关注和赞誉,还可以受益于与其他领域内顶尖专家的合作和互动。
此外,这一荣誉也为研究者争取到更多的研究资金和项目支持提供了有力的证明。
二、ISCAS最佳论文的评选标准(Selection criteria for IEEE ISCAS BestPaper)ISCAS最佳论文的评选并非简单的奖励高被引用论文或高影响因子期刊发表的论文,而是根据一系列严格的标准和流程进行评审。
首先,论文的创新性是评判的重要因素。
ISCAS最佳论文必须提出具有独特见解和创新思路的研究内容,并在该领域带来突破性进展。
其次,论文的方法和技术应当是具有实际可行性和重现性的,并且能够为该领域提供实质性的解决方案。
此外,ISCAS最佳论文还要求论文的写作质量、实验数据的可信性和结果的解释透明度等方面达到一定水平。
基于双谱的射频指纹提取方法

第19卷 第1期 太赫兹科学与电子信息学报Vo1.19,No.1 2021年2月 Journal of Terahertz Science and Electronic Information Technology Feb.,2021文章编号:2095-4980(2021)01-0107-05基于双谱的射频指纹提取方法贾济铖,齐琳(哈尔滨工程大学信息通信工程学院,黑龙江哈尔滨 150001)摘 要:研究了基于通信辐射源射频指纹(RFF)的同类型设备分类识别理论,通过提取通信信号的围线积分双谱值来作为设备个体识别的特征向量,使用支持向量机(SVM)分类器进行识别。
构建辐射源识别系统,并使用实测信号进行仿真测试。
结果显示该方法具有稳定的识别效果,且在信噪比(SNR)为-22 dB时,系统可以达到接近90%的分类识别准确度。
这说明本文提出的基于双谱的RFF提取方法有效。
关键词:物理层安全;射频指纹;围线积分双谱;个体识别中图分类号:TN918文献标志码:A doi:10.11805/TKYDA2019291RF fingerprint extraction method based on bispectrumJIA Jicheng,QI Lin(College of Information and Communication Engineering,Harbin Engineering University,Harbin Helongjiang 150001,China)Abstract:The classification and recognition theories of the same type of equipment based on the Radio Frequency Fingerprint(RFF) of the communication radiation source are studied. The integralbispectrum values of the communication signal are extracted as the feature vector of the device, and theSupport Vector Machine(SVM) classifier is used for identification. After constructing a radiation sourceidentification system, the measured signals are used for simulation testing. The simulation results show astable recognition effect by using the proposed method, and the system can achieve nearly 90%classification recognition accuracy when the Signal to Noise Ratio(SNR) is -22 dB. This result validatesthe effectiveness of bispectrum-based RF fingerprint extraction method.Keywords:physical layer security;Radio Frequency Fingerprint(RFF);contour integral bispectrum;individual identification物联网及5G的快速发展,使彼此链接的无线设备越来越多,同时也带来了一系列监管与安全的难题。
思美特控制系统(En)

IPCRF/IPCRF2The IPST series of wireless touchpanels are based on the leading radio frequency technologies and wireless communication encoding methods. They are flexible and reliable, and are not limited to direction, obstacle or distance (freedom of movement within 300 feet).MPDA-100/200Prozessor Intel XScale PXA270 32 MB ROM 64/128 MB RAMDisplay 3.5" TFTWireless Connectivity IrDA, IEEE 802.11b Li-ion batteryApplication programming: Support control flow visual development software with strong functionTouch control terminalIPIO-1/2Dimmer channel: Four-channel independent dimmer module Input power: 220V for a single channel, 1800W, the total power less than 3600W Network input: Four-digit dedicated network connecting terminal Cover: Dark gray and white metallic over Installation mode: Embedded or wall-mounted Relay: Eight independent relay control Power of a single channel: 20A, 277VAC Local input: 8-digit local input Network input: Four-digit dedicated network connecting terminal Power: 24VDC network power supply Dimensions: 38.10cm*20.32cm*6.35cm(H W D)Weight: 7.2 pounds / 3.3Kg IPCLI-4IPPCI-8Main Controller Control equipment around The SMARTISYS IPIO series of interface computers are the most common devices with universal interfaces among the control systems. They are applicable to situations where the infra-red and relay interfaces need expansion. They can also be employed in a third-party control system, serving as an interface device.SMARTISYS Control System SMARTISYS Control System。
联合TDOA改进算法和卡尔曼滤波的UWB室内定位研究

联合TDOA改进算法和卡尔曼滤波的UWB室内定位研究张桀;沈重【摘要】随着“互联网+”的提出以及物联网技术的不断发展,各行业对人员、货物等进行定位的场景在不断增多;与此同时,安防监控、航空航天、无人工业化操作、海域勘探、数字化旅游等新兴领域对室内定位系统的需求也在日益增强。
针对不同需求,学术界和工业界开发了多种定位技术,它们在定位适用性、定位精度等方面存在较大的差异。
相比其他定位方式,超宽带(UWB)定位技术在精确度、实时性能和数据可扩展方面具有独特的优势,通过改进基于到达时间差(TDOA)的算法,降低了时钟同步的难度,联合卡尔曼滤波进一步消除了传输过程中的误差干扰,最终使得室内定位更加精确。
%With the presentation of ″Internet+″ and continuous development of Internet of Things technology,the scenesto locate the staff and goods are increasing. At the same time,the demands of emerging fields(such as securitymonitoring,aero⁃space,unmanned industrialization operation,seas exploration,digital tourism)for indoor positioning are growing. To satisfydif⁃ferent requirements,various positioning technologies were developedby the academia and industry,but they have great dif⁃ferences in the aspects of positioning applicability,positioning accuracy,etc. In comparison with other positioning methods,the UWB(ultra wideband)positioning technology has the unique advantages in positioning accuracy,real⁃time performance and data scalability. In this paper,the algorithm based on TDOA (time difference of arrival) was improved to reduce the difficulty of clock synchronization,and in combination with Kalman filtering,the errorinterference in transmission process was eliminated. The method can make the indoor positioning more accurately.【期刊名称】《现代电子技术》【年(卷),期】2016(039)013【总页数】5页(P1-5)【关键词】到达时间差;卡尔曼滤波;超宽带;室内定位【作者】张桀;沈重【作者单位】海南大学信息科学技术学院,海南海口 570228;海南大学信息科学技术学院,海南海口 570228【正文语种】中文【中图分类】TN911-34全球定位系统(Global Positioning System,GPS)是室外定位的通用解决方案,在无辅助的情况下定位精度一般为10 m以上。
英国《科学文摘》(ScienceAbstracts精品PPT课件

分类表及目次(Classification and
Contents)
6000 COMPUTER SOFTWARE 1612
6100 SOFTWARE TECHNIQUES
AND SYSTEMS
1612
6110 Systems analysis and programming
1613
6130B Graphics techniques 1630
《科学文摘》包括5个分辑: A:Physical Abstracts (PA)物理文摘
B:Electrical
and
Electronics
bstracts(EEA) 电气与电子学文摘
C:Computer
and
control
Abstracts(CCA) 计算机与控制文摘
D:Information
Technology
科学文摘网络版——INSPEC概况
INSPEC的英文全称为Information Service in Physics、ElectroTechnology、Computer and Control,即英国IEE的物理、电子电 气、计算机与控制及信息科学文摘的 缩写。
现在ISI与IEE合作将INSPEC数据内容 建立在ISI Web of Knowledge平台上
设立:化学物质索引、数值索引、 天文学对象索引
点击此处选择其他数据库
点击数据 库的名称
浏览辅助索引
受控词索引(叙词表)
选择刊名的首字母
点击“ADD”将感兴 趣的来源刊添加到 下面的检索框中
期刊细节
点击“OK”将选中 的刊物添加到检索 项中去
刊物详细信息
检索示例
确定检索字段
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
On the Scalability of IEEE802.11Ad Hoc NetworksLifei Huang huang.343@T en-Hwang Lailai@The Ohio State University Department of Computer and Information Science2015Neil AvenueColumbus,OH43210-1277ABSTRACTThe IEEE802.11standards support the peer-to-peer mode In-dependent Basic Service Set(IBSS),which is an ad hoc net-work with all its stations within each other’s transmission range.In an IBSS,it is important that all stations are syn-chronized to a common clock.Synchronization is necessary for frequency hopping spread spectrum(FHSS)to ensure that all stations“hop”at the same time;it is also necessary for both FHSS and direct sequence spread spectrum(DSSS)to perform power management.This paper evaluates the syn-chronization mechanism,which is a distributed algorithm, specified in the IEEE802.11standards.By both analysis and simulation,it is shown that when the number of stations in an IBSS is not very small,there is a non-negligible probabil-ity that stations may get out of synchronization.The more stations,the higher probability of asynchronism.Thus,the current IEEE802.11’s synchronization mechanism does not scale;it cannot support a large-scale ad hoc network.To alle-viate the asynchronism problem,this paper proposes a simple modification to the current synchronization algorithm.The modified algorithm is shown to work well for large ad hoc networks.Categories and Subject DescriptorsC.2.2[Computer-Communication Networks]:Network Pro-tocolsGeneral TermsAlgorithms,performanceKeywordsIEEE802.11,ad hoc networks,scalability,clock synchroniza-tionPermission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.MOBIHOC’02,June9-11,2002,EPFL Lausanne,Switzerland. Copyright2002ACM1-58113-501-7/02/0006...$5.00.1.INTRODUCTIONThe IEEE802.11standards[4]are widely used for wire-less LAN(WLAN).They support two types of WLAN:one in infrastructure mode and the other in ad hoc mode.In the infrastructure mode,a station serves as the access point and communications can only take place between the access point and the other members of the basic service set(BSS).When the infrastructure does not exist or does not work,the ad hoc mode is useful.In the IEEE802.11standards[4],an ad-hoc network is called an Independent Basic Service Set(IBSS),in which all of the stations are within each other’s transmission range.Performance analysis of IEEE802.11WLAN has been re-ported in[2,1,7,10].Reference[2]evaluates the per-formance of the Distributed Coordination Function(DCF)of IEEE802.11standards and proposes an adaptive contention window protocol to replace the exponential backoff protocol. In[1]and[10],the saturation throughput of DCF is analyzed using different techniques.The effect of network size and traffic patterns on the capacity of ad hoc wireless networks is examined in[7],where the locality of traffic is shown to be a key factor of scalability of ad hoc networks.All the above works are focused on the IEEE802.11MAC protocol.However,the scalability issue has not been fully studied.Envision that in a classroom or in an auditorium, more than100students turn on their laptops to form an IBSS. Will the ad hoc network work properly?This question is not trivial.In this paper we will study the scalability of IEEE 802.11ad hoc networks from the viewpoint of clock synchro-nization.To the best of our knowledge,this paper is thefirst to report such a study.In an IEEE802.11WLAN,each station maintains a clock or timer.(A clock is called a timer in[4];therefore,we use timer and clock interchangeably in this paper.)Clock synchro-nization is needed for power management,synchronization of frequency hopping,and coordination of Point Coordina-tion Function(PCF).In power management each station uses its clock to determine the beginning and the end of the ad hoc traffic indication(ATIM)window.In FHSS,each station deter-mines when to“hop”to a new channel according to its timer. Finally,in an IEEE802.11infrastructure network that uses PCF,the timer is used to predict the start of a super frame.In order to synchronize the clocks,IEEE802.11specifies the timing synchronization function(TSF).TSF is easy for in-frastructure networks.The access point periodically broad-casts a beacon frame that contains the timing information,DSSSaCWmin31aSlotTime20sMore precisely,the timestamp is equal to the value of theTSF timer at the time thefirst bit of the timestamp is transmit-ted to the physical layer plus the transmitting station’s delaythrough its physical layer from the MAC-PHY interface to itsinterface with the wireless medium.This detail is not impor-tant for our analysis.Actually,the receiving station will adjust the timestamp byadding an amount equal to the delay through the physicallayer,and the adjusted value of the timestamp is used for syn-chronization.This detail is not important for our analysis.2.2Related WorkIEEE802.11’s timing synchronization function is similar to the method proposed by Lamport[6].With this method,it is shown in[6]that given the clock accuracy,link delay and network diameter,and assuming that a timestamp is sent suc-cessfully along each link at a constant frequency,the timing values of the entire network are guaranteed to be accurate to an established bound.The assumption of successful transmis-sion of timestamp at a constant frequency is essential for the validity of the bound.This assumption does not hold for the TSF of the IEEE802.11IBSS.A different synchronization method called reference broad-cast synchronization(RBS)is presented in[3]for broadcast networks,especially for wireless ad hoc networks.A refer-ence broadcast or beacon does not contain an explicit times-tamp;instead,receivers use its arrival time as a point of refer-ence for comparing their clocks.RBS uses nontrivial statistics methods such as regression to estimate the phase offset and clock skew of any two nodes.Mills[8]proposes a Network Time Protocol(NTP)to syn-chronize clocks and coordinate time distribution in the Inter-net system.NTP cannot be used for sparse ad hoc networks which can be partitioned.To deal with partitioning in sparse ad hoc networks,a time synchronism algorithm is proposed in[9].At the other end of the spectrum of ad hoc networks in terms of station population,when there are a large number of stations in an ad hoc network,as to be seen in this paper, the stations are likely to be out of synchronization.3.ANALYSIS OF BEACON CONTENTION As mentioned in the preceding section,at the beginning of each beacon interval,all stations in an IBSS contend with each other to send beacon frames.There are two possible out-comes of each beacon contention:at least one beacon frame is transmitted successfully or no beacon frame is transmitted successfully.For our analysis,successful transmission is de-fined as follows.Definition A beacon transmission is considered successful if it encounters no collision.Thus,for ease of analysis,our model assumes no transmis-sion error.This assumption is not undesirable as our analysis is intended to point out the asynchronism problem with the IEEE802.11’s TSF scheme.If transmission error is taken into account,the asynchronism problem will just be even more severe.For an arbitrary station,there are three possible out-comes to’s beacon contention in each beacon period:1.Station does not transmit any beacon because it re-ceives a beacon before its random delay expires.2.Station transmits a beacon which collides with otherbeacons.3.Station transmits a beacon successfully.Wefirst analyze the probability that at least one station suc-cessfully transmits a beacon in a given beacon interval,and then we calculate the probability that a particular station suc-ceeds in beacon transmission during a given beacon interval. Suppose there are stations.Denote the beacon generation window by,which consists of slots numbered0through.Let be the probability that at least one of the stations succeeds in beacon transmission during a beacon interval.The event,,that there is a successful bea-con transmission in window consists of three disjoint sub-events:There is no beacon transmission in slot0,but there is a successful transmission in window.There is a successful beacon transmission in slot0.There are unsuccessful(collided)beacon transmissions in slot0,but at least one successful beacon transmission in slot1through slot.Thus,Prob()Prob()+Prob()+Prob()(1) Prob()and Prob()can be easily calculated as follows.Prob()(2) The boundary condition for is. To compute,recall that each beacon typically has a length of multiple,say,slots.If there is a beacon collision in slot0,the collided beacons will occupy all the slots from 0to and,as a result,there will be no successful beacon transmission before slot.Thus,for and,we have the following formula for.Figure 2:Explanation for p(n,W)0.10.20.30.40.50.60.70.80.9120406080100120140p (n ,W )Number of StationsAnalysis W=30Analysis W=62Simulation W=30Simulation W=62Figure 3:p(n,W)with b=11points on the curves are generated by simulation.As can be seen,the analysis results coincide with the simulation results very well.The figure shows that given ,is lower than 50%when .That means in half of the bea-con intervals,no beacon frames are transmitted successfully .As to be seen in the next section,this may cause some stations to become out of synchronization.Now we analyze ,the probability that a particular station,say ,successfully sends a beacon in a given beacon interval.Let denote the conditional probability that station successfully transmits a beacon given that it is scheduled to transmit in slot .Then we have the following equation:is the probability that is scheduled to transmitat slot .To compute ,note that Prob(a)Prob(b c d)Prob(e (b c d)),where a,b,c,d,e refer to the following events,respectively .(Figure 4helps explain these events.)(a)All other stations are scheduled to transmit after slot .The probability of this event isTherefore,forand,satisfies the fol-lowing recurrence:(5)The boundary condition for is and.Using Eqs.(4)and (5),the function is plotted in Fig.5for various values of ;in this figure,the value of is assumed to be 11.It is important to notice that the value ofis not sensitive to .The simulation results againmatch with our analysis.4.ANALYSIS OF ASYNCHRONISMClock synchronization is important for power management in both DSSS and FHSS as well as for the synchronization of hopping sequence in FHSS.If the clocks of two stations are so badly out of synchronization that either power management or FHSS can not work properly ,the two stations are said to be out of synchronization.If there are pairs of stations out of synchronization in an IBSS,the network is said to be in hazardous asynchronism .In this section,we will show that asynchronism may occur under the IEEE 802.11timing syn-chronization function (TSF).For simplicity ,we will often omit the adjective “hazardous”when referring to hazardous asyn-chronism.Let be the maximum clock difference tolerable by power management and FHSS.Definition Two clocks are out of synchronization if their times are different by more than .Two stations are out of synchronization if their clocks are out of synchronization.00.10.20.30.40.50.60.70.80.910510152025p 1(n ,W )Number of StationsAnalysis, W=30Simulation, W=30Analysis, W=62Simulation, W=62Figure 5:(n,W)with b=11Assume that the clocks in an IBSS are all different in speed (or accuracy).Thus,there is a unique fastest station ,whose clock is fastest in the system.We are particularly interested in two conditions of asynchronism:Fastest-station asynchronism —This refers to a situa-tion where the clock of the fastest station is ahead of the clocks of all other stations by more than units of time.Fastest-station asynchronism may occur in an IBSS because under the IEEE 802.11timing synchro-nization function,stations can only set their timers for-ward and never backward.Slower clocks synchronize with faster clocks,but faster clocks do not synchronize themselves with slower clocks.Thus,if the fastest sta-tion fails to transmit beacons for too many beacon inter-vals,its clock will be ahead of all other clocks by more than .Global asynchronism —Given a value between one and one hundred,percent global asynchronism (or simply percent asynchronism)refers to the situation that at least percent of the pairs of stations are out of synchronization.For each of these two types of asynchronism,we are inter-ested in the following questions:How often may asynchronism occur in an IBSS?Once asynchronism occurs,how long does it last?4.1Fastest-Station AsynchronismLet be the length of a beacon interval,and let denote the difference in clock accuracy between the fastest station and the second fastest station.Once the stations have been synchronized,if the fastest node fails to transmit a beacon in each of,let as in Eq.(4).Once an incident of fastest-node asynchronism occurs,it lasts at least for one beacon interval.After one interval,with prob-ability the condition of asynchronism continues to hold for at least additional beacon intervals.Thus,the ex-pected lasting time of fastest-node asynchronism,in terms of number of beacon intervals,is:(8)We have derived a formula for ,and for the case of fastest-node ing these formulae,we will compute in a later section ,and for various values of and .4.2Global AsynchronismGlobal asynchronism is much harder to analyze.Given a value between zero and one hundred,let be the dura-tion of a continuous percent asynchronism period,and let be the length between two consecutive periods of percent asynchronism.We are interested in the expected length of and that of .Two clocks may get out of synchronization because their accuracies are different.Let be the value such that per-cent of the pairs of stations differ by or more in clock accuracy;in other words,:at least percent of the pairs of clocks differ by in their accuracy. Define-asynchronism as a situation where every two stations whose clocks differ in accuracy by or more with each other are out of synchronization.Let be the duration of a-asynchronism period,and let be the length between two consecutive periods of-asynchronism.For simplicity,we write as in the rest of this section.Apparently,if the IBSS is in-asynchronism then it is in percent asynchronism.Therefore,and.If we know how to compute and ,then we have a lower bound on and an upper bound on.Since our purpose here is to point out poten-tial global asynchronism problems of the IEEE802.11timing synchronization function,a lower bound on and an up-per bound on will serve the purpose. Unfortunately,and are still difficult to com-pute.So,we instead compute a lower bound on and an upper bound on,which will still serve our purpose. As in the analysis of fastest-station asynchronism,let be the number of stations;,the beacon contention window size;and,the length of each beacon interval.Observe that after the stations have been synchronized,if no node suc-ceeds in beacon transmission in each of(9)Similarly,replacing the in Eq.(7)by as in Eq.(2)yields an upper bound on and:(10)Define the global asynchronism time ratio,denoted by, to be the percentage of time in which the system is in global asynchronism.From Eqs.(7)and(6),it follows thatValueWBeacon lengthPropagation delay Transmission error rateaBeaconPeriodClock accuracy501001502002503003504006080100120140160180I n t e r -a s y n c h r o n i s m T i m e (s )Number of StationsAnalysis, W=30, d=0.01%Method 1, W=30, d=0.01%Method 2, W=30, d=0.01%Figure 7:Inter-global-asynchronism time of IEEE 802.11show by both analysis and simulation that global asynchro-nism is not unusual in an FHSS system.For the length of a beacon interval,s,two clocks with a difference of in accuracy will drift away from each other by s.Thus,with s,and s,we have5010015020025030035040051015202530I n t e r -a s y n c h r o n i s m T i m e (s )Number of StationsAnalysis, W=30, d=0.005%Analysis, W=62, d=0.005%Analysis, W=30, d=0.003%Simulation, W=30, d=0.003%Figure 9:Inter-fastest-node-asynchronism time of IEEE 802.115101520253005101520253035404550A s y n c h r o n i s m R a t i o (%)Number of StationsAnalysis, W=30, d=0.003%Simulation, W=30, d=0.003%Figure 10:Fastest-node asynchronism time ratio of IEEE802.11node asynchronism occurs when the fastest station can not successfully transmit beacon frames for a number of consecu-tive beacon periods.Since this probability is much larger than the probability that no station at all successfully sends a bea-con frame for the same number of beacon intervals,fastest-node asynchronism is more likely to occur than global asyn-chronism.This phenomenon can be observed by comparing Figure 7to Figure 9.The fastest-node asynchronism time ratio when is given in Figure 10,from which we observe that the fastest sta-tion is out of synchronization with all other stations for 10%of the time even for an IBSS of just 30stations.With a net-work of 50stations,it is under fastest station asynchronism for 30%of the time.Next,we examine fastest-node asynchronism by simula-tion,assuming that all the clocks are uniformly distributed in accuracy between and .This time we are interested in the number of stations with which the fastest station is out of synchronization.The results are shown in Fig.11,where the -axis is the average percentage of stations with which the fastest station is out of synchronization.The5101520253035404550102030405060708090100A s y n c h r o n o u s C h a n n e l R a t i o (%)Number of StationsSimulation, W=30Simulation, W=62Figure 11:Average fastest-node asynchronous channel ra-tio of IEEE 802.11problem of asynchronism is more severe for FHSS ()than for DSSS ().In an FHSS system of 40stations,the fastest station is,at any time instance,out of synchroniza-tion with,on average,10%of the stations.When the IBSS size is 80,the fastest station would have hard time commu-nicating with 45%of the stations.For ,the fastest station would have synchronization problems with almost ev-ery other station.DSSS systems are not immune to the prob-lem.For ,the fastest station is,on average,out of synchronization with 15%of stations at any moment.The fastest-node asynchronism is a real problem for DSSS as well as for FHSS.6.A SCALABLE CLOCK SYNCHRONIZA-TION PROCEDUREWe have seen clock asynchronism problems that may arise when scaling up an IBSS.Now let us turn to the question of fixing it.If stations were allowed to set their timers both forward and backward in the process of synchronization,then there would be no fastest-node asynchronism but just global asynchronism problem,which could be alleviated by enlarging the beacon contention window size .A value of 62for ,as used in DSSS,could practically allow an IBSS of size 200.If a fixed large window size is not desirable,a simple scheme allowing the window size to dynamically change has been observed to perform very well.This result is not reported in this paper due to space limit.Now ,suppose we must keep intact the IEEE 802.11TSF’s provision of moving forward only .Since the stations can only set their timers forward,why not give the faster stations a higher priority to send beacon frames?Based on this idea,we propose an adaptive timing synchronization procedure (ATSP)that can considerably alleviate both the problem of fastest-node asynchronism and that of global asynchronism.We as-sign to each station an integer that determines how of-ten each station shall participate in beacon contention.That is,station contends for beacon transmission once every beacon periods.Therefore,smaller the value of ,higher the station’s chance of beacon transmission.Let the maxi-mum possible value of be .Let be a counter atstation that counts beacon periods.The proposed clock syn-chronization algorithm is described in the following.It is a simple modification to the current IEEE802.11TSF,and can be easily implemented.ATSP:Adaptive Timing Synchronization Procedure1.Initially,for each station,let be a random numberbetween1and and let.2.In each beacon interval,station participates in beaconcontention iff.3.Whenever station receives a beacon with a timing valuelater than its own,the station sets its timer to this value, increases by1if,and sets.4.If station does not receive any beacon frame with atiming value later than its own for consecutive beacon intervals,it decrements by1if, and sets.5.At the end of a beacon interval,each station increasesits by1.With ATSP,once the clocks have been synchronized,the fastest station will not receive a timing value greater than its own;its-value will gradually decrease to1and stay there. The other stations will gradually increase their-values until they reach.Define a stable state to be one in which the fastest station’s-value has reached1and the other stations have reached.Once the IBSS reaches a stable state, the fastest station has a very high probability of successfully sending a beacon and thereby synchronizing all the other sta-tions.In the above analysis,we implicitly assume,for ease of presentation,that there is only one fastest station.This as-sumption is not essential.If there are multiple fastest stations, ATSP will still works well.To testify the performance of ATSP,we did a couple of sim-ulations assuming a static IBSS adopting the parameter used in Section5.For global asynchronism,we adopted=0.01% and=23;and chose10for.For different values of ,we ran simulation for20times,each for20minutes of simulated time.Not a single incident of global asynchro-nism was observed.We also ran simulation for fastest-station asynchronism,with and with completely ran-domized clocks,and once again observed not a single case of asynchronism.Then we evaluated the performance of ATSP for a dynamic IBSS.In ATSP the fastest station is,to some extent,in charge of timing synchronization.Should the fastest station leave the IBSS because of mobility or other reasons,the formerly sec-ond fastest node will become the fastest.Suppose its index is .Since is decreased by one in every beacon inter-vals,it takes station at most beacon intervals to reduce to1.For example,if,the time will be at most 1000.1s=10seconds.Note that restabilization does not mean asynchronism;during restabilization,there may or may not be any incidence of asynchronism.In order to understand the probability of asynchronism in the process of restabiliza-tion,we let the fastest station leave and return to the IBSS once every six minutes.That is,it alternately leaves the IBSS for three minutes and returns for the next three minutes.As expected,no asynchronism was caused by a fastest node joining the IBSS.On the other hand,in the restabilization,number of stations350Global asyn.,=0.01%1 Fastest-station asyn.,=0.003%0 Fastest-station asyn.,randomized0sion range.An interesting question is whether802.11can be used to implement multi-hop ad hoc networks,assuming that each station has been enhanced with routing capability.We are currently investigating this problem and will report our results in a future paper.8.REFERENCES[1]G.Bianchi.Performance analysis of the IEEE802.11distributed coordination function.IEEE Journal onSelected Areas in Communications,18(3):535–547,2000.[2]G.Bianchi,L.Fratta,and M.Oliveri.Performanceevaluation and enhancement of the CSNA/CA MACprotocol for802.11wireless LANs.In Proc.PIMRC1996,pages392–396.[3]J.Elson,L Girod and D.Estrin.Fine-grained networktime synchronization using reference broadcasts.Submitted for review,February2002./Publications/Publications.html.[4]IEEE Std802.11.Wireless LAN Medium Access Control(MAC)and Physical Layer(PHY)specification,1999edition edition.[5]IEEE Std802.11b.Higher-Speed Physical LayerExtension in the2.4GHz Band,1999edition edition. [6]mport.Time,clocks and the ordering of events indistributed munications of the ACM,21(7):558–565,1978.[7]J.Li,C.Blake,D.S.J.D.Couto,H.I.Lee,andR.Morris.Capacity of ad hoc wireless networks.InProc.7th ACM International Conference on MobileComputing and Networking,2001.[8]ls.Internet time synchronization:the networktime protocol.In Global States and Time in DistributedSystems.IEEE Computer Society Press,1994.[9]K.R¨o mer and E.Zurich.Time synchronization in adhoc networks.In Proceedings of MobiHoc2001.[10]Y.C.Tay and K.C.Chua.A capacity analysis for theIEEE802.11MAC protocol.ACM/Baltzer WirelessNetworks,7(2):159–171,2001.。
