ISSUE Emulation of DS1 circuits over ATM networks
数字电子技术加英文注释
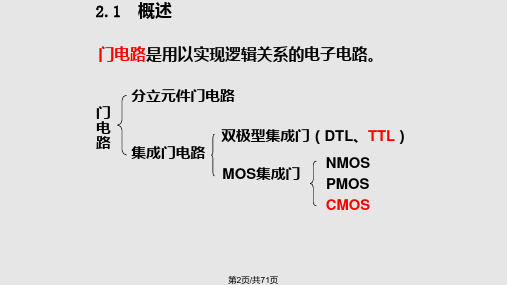
2.1 概述
二、逻辑电平 Vcc
Logic Levels
The voltages used to represent a 1 and a 0 are called logic levels.
Vo
实际开关为晶体二极管、三极
VI
管以及场效应管等电子器件
S
VI控制开关S的断、通情况。 S断开,VO为高电平;S接通,VO为低电平。
④74LS:低功耗肖特基系列;74LS系列成为功耗延迟积较小的系列。74LS系列 产品具有最佳的综合性能,是TTL集成电路的主流,是应用最广的系列。
⑤74AS:先进肖特基系列;
④74ALS:先进低功耗肖特基系列。
第24页/共71页
2.4 TTL集成门电路
74LS系列常用芯片
VCC 3A 3B 3Y 4A 4B 4Y
Implement inverter with BJT
+VCC Rc iC
Rb b
c uo
ui
iB
利用二极管的压降为0.7Ve,保证
输入电压在1V以下时,开关电路
可三靠极地管截开止关。 电路
输入为低,输出为高; A
输入为高,输出为低。
0
1
A(V) Y(V) <0.8 5 >2 0.2
YA
Y
A
1
Y
1
0
②外加反向电压,二极管截止。
门坎电压Uth 硅 PN 结伏安特性
iD(mA)
0.7V
uD(V)
第8页/共71页
2.2 半导体二极管和三极管的开关特性
二、二极管开关特性
D uI
Vcc R
uo
利用二极管的单向导电性,相当 于一个受外加电压极性控制的开关。
DesignWare ARC EM Overlay Management Unit Datashee

DESIGNWARE IP DATASHEETThe DesignWare ® ARC ® EM Overlay Management Unit (OMU) option enables address translation and access permission validation with minimal power and area overhead while boosting the ability to run larger and more data intensive operations, such as those increasingly prevalent within AIoT, storage and wireless baseband applications, on an ARC EM processor. This hardware-based Overlay Management Unit provides support for virtual memory addressing with a Translation Lookaside Buffer (TLB) for address translation and protection of 4KB, 8KB or 16KB memory pages. In addition, fixed mappings of untranslated memory are supported, enabling the system to achieve increased performance over a large code base residing in a slow secondary storage memory, with the option to be paged in as needed into faster small on-chip page RAM (PRAM) in an efficient way. This is particularly suited for operating environments in which virtual address aliasing is avoided in software.In systems that run all code as a single process (single PID), using a large virtual address space with a one-to-one correspondence between the virtual address and a large selected area of secondary storage space (such as flash memory or DRAM), the address-translation facility of the Overlay Management Unit can be used to detect when a section (or one or more pages) of code is resident in the PRAM and provide the physical address to the page in the PRAM. Virtual address spacePhysical address space Figure 1: Virtual to Physical Address TranslationHighlights• Lightweight hardware-based memorymanagement unit (MMU) enablingaddress translation and accesspermission validation• Fully associative Instruction andData µTLBs• Configurable joint TLB depth of 64, 128 or256 entries• Common address space forinstruction and data• Independent rd/wr/execute flags for user/kernel modes per page• Optimized TLB programming withsoftware managed JTLB and hardwareassisted replacement policy• 32-bit unified instruction/dataaddress space–2GB virtual translated addressspace, mapping to 4GB physicaladdress space• Configurable page size: 4 KB, 8 KB, 16 KB• Per page cache control• Optional ECC for JTLB RAMsTarget Applications• AIoT• Storage• Wireless• NetworkingARC Overlay Management Unit forMemory ModelThe EM processor supports virtual memory addressing when the Overlay Management Unit is present. If the Overlay Management Unit is not present or if it is present but disabled, all the virtual addresses are mapped directly to physical addresses. By default, the Overlay Management Unit is disabled after reset. Note that the data uncached region is always active even if the Overlay Management Unit is disabled.The Overlay Management Unit features a TLB for address translation and protection of 4 KB, 8 KB or 16 KB memory pages, and fixed mappings of an untranslated memory. The upper half of the untranslated memory section is uncached for I/O uses while the lower half of the untranslated memory is cached for a system kernel.With the Overlay Management Unit option enabled, the ARC EM cache-based cores define a common address space for both instruction and data accesses in which the memory translation and protection systems can be arranged to provide separate, non-overlapping protected regions of memory for instruction and data access within a common address space. The programming interface to the Overlay Management Unit is independent of the configuration of the TLB in terms of the associativity of number of entries (Figure 2).Virtual address space Physical address space in secondary storagePhysical address space in on-chip page RAM Figure 2: Memory Address Mapping with Overlay Management ComponentsPage Table LookupThe system management or micro-kernel software tracks the mapping of pages from the program store in the level-3 memory to smaller level-2 memory. The number of entries used/required for this varies based on the Overlay Management Unit page size and the size of the level-2 memory. The Overlay Management Unit acts as a software-controlled cache into this page table, performs hardware address translation, and checks access permissions (Figure 3).Two levels of cache are provided:• The first level consists of micro TLBs (or μTLBs). These are very small, fully associative caches into the second level of the OLM cache. They allow for single-cycle translation and permission checking in the processor pipeline. The μTLBs are updated automatically from the second level of the cache.• The second level of the cache is called the joint TLB (JTLB). This consists of a larger, RAM-based 4-way set-associative TLB. The JTLB is loaded by special kernel mode handlers known as TLB miss handlers.• The final level of the hierarchy is the main page table itself. This contains the complete details of each page mapped for use by kernel or user tasks. The μTLBs, JTLB, and miss handlers combine to implement cached access into the OS page table.Figure 3: Overlay Manager Table StructureTranslation Lookaside BuffersTo provide fast translation from virtual to physical memory addresses the Overlay Management Unit contains Translation Lookaside Buffers (TLBs). The TLB architecture of the ARC EM’s Overlay Management Unit can be thought of as a two level cache for page descriptors: “micro-TLBs” for instruction and data (μITLB & μDTLB) as level one, and the “Joint” (J-TLB) as level two. The μITLB and μDTLB contain copies of the content in the joint TLB. The μTLBs may have descriptors not contained in the joint TLB. In addition to providing address translation, the TLB system also provides cache control and memory protection features for individual pages. The ARC EM implementation features a system configured as follows:• The μITLB and μDTLB are fully associative and physically located alongside the instruction cache and data cache respectively, where they perform single-cycle virtual to physical address translation and permission checking. The μITLB and μDTLB are hardware managed. On a μITLB (or μDTLB) page miss, the hardware fetches the missing page mapping from the JTLB.• The JTLB consists of a four-way set associative Joint Translation Lookaside Buffer with 64, 128 or 256 entries and is software managed. On a joint TLB page miss, special kernel-mode TLB miss handlers fetch the missing page descriptor from memory and store it in the JTLB, as well as swapping in the required contents from the main memory store into the level-2 memory. No part of the Overlay Management Unit has direct access to the main memory. The JTLB is filled by software through an auxiliary register interface.DocumentationThe following documentation is available for the DesignWare ARC Overlay Management Unit Option for ARC EM:• ARCv2 ISA Programmers Reference Manual• ARC EM Databook• DesignWare ARC EM Integration GuideTesting, Compliance, and QualityVerification of the ARC EM Overlay Management Unit follows a bottom-up verification methodology from block-level through system-level. Each functional block within the product follows a functional, coverage-driven test plan. The plan includes testing for ARCv2 ISA compliance as well as state- and control-specific coverage points that have been exercised using constrained pseudo-random environments and a random instruction sequence generatorARC EM ProcessorsThe ARC EM processors, built on the ARCv2 instruction set architecture (ISA) are designed to meet the needs of next-generation system-on-chip (SoC) applications and enable the development of a full range of 32-bit processor cores – from low-end, extremely power-efficient embedded cores to very high-performance host solutions that are binary compatible and designed with common pipeline elements. ARC EM processors can be precisely targeted to meet the specific performance and power requirements for each instance on a SoC, while offering the same software programmer’s model to simplify program development and task partitioning.©2021 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks isavailable at /copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners.。
NORMA 4000 5000 Power Analyzer 用户说明手册说明书

Since some countries or states do not allow limitation of the term of an implied warranty, or exclusion or limitation of incidental or consequential damages, the limitations and exclusions of this warranty may not apply to every buyer. If any provision of this Warranty is held invalid or unenforceable by a court or other decision-maker of competent jurisdiction, such holding will not affect the validity or enforceability of any other provision.
BEGRENZTE GEWÄHRLEISTUNG UND HAFTUNGSBESCHRÄNKUNG
Fluke gewährleistet, daß jedes Fluke-Produkt unter normalem Gebrauch und Service frei von Material- und Fertigungsdefekten ist. Die Garantiedauer beträgt 2 Jahre ab Versanddatum. Die Garantiedauer für Teile, Produktreparaturen und Service beträgt 90 Tage. Diese Garantie wird ausschließlich dem Erster
调试单体设备英语作文

调试单体设备英语作文Title: Debugging Monolithic Devices。
Debugging monolithic devices is a crucial aspect of ensuring their optimal functionality and performance. In this essay, we will explore the process of debugging monolithic devices, highlighting the challenges involved and the strategies employed to overcome them.Firstly, it is important to understand what monolithic devices are. Monolithic devices refer to integrated circuits or systems where most, if not all, components are fabricated onto a single substrate or chip. These devices are commonly found in various applications, including microprocessors, memory chips, and sensors.One of the primary challenges in debugging monolithic devices is the complexity of their internal structure. Unlike modular devices where components can be easily isolated and tested individually, monolithic devicespresent a more intricate system where a fault in one component can affect the functionality of the entire device. Therefore, pinpointing the root cause of a problem requires meticulous analysis and testing.To effectively debug monolithic devices, engineers employ a variety of techniques and tools. One commonly used method is the use of built-in self-test (BIST) circuits. These circuits are integrated into the device during the fabrication process and allow for automated testing of various components. By activating the BIST circuits, engineers can quickly identify faulty components or connections within the device.In addition to BIST circuits, engineers also utilize external testing equipment such as oscilloscopes, logic analyzers, and probe stations. These tools enable engineers to perform detailed measurements and observations of the device under test, helping to identify anomalies and irregularities.Furthermore, advanced diagnostic techniques such asfault simulation and emulation are employed to simulatereal-world operating conditions and identify potentialfailure scenarios. By subjecting the device to simulated stress conditions, engineers can uncover latent defects and weaknesses that may not be apparent during normal operation.Despite the availability of sophisticated tools and techniques, debugging monolithic devices remains a challenging task due to the inherent complexity of these systems. Often, the process involves a combination of theoretical analysis, empirical testing, and creative problem-solving.Moreover, the miniaturization of modern monolithic devices presents additional challenges in debugging. As components shrink in size, the spacing between them decreases, making it more difficult to access and probe individual elements. This necessitates the development of specialized testing methodologies and equipment capable of handling miniature components.In conclusion, debugging monolithic devices is acomplex and challenging process that requires a combination of expertise, creativity, and advanced tools. By employing a systematic approach and leveraging the available resources, engineers can effectively identify and resolve issues, ensuring the reliability and performance of monolithic devices in various applications.。
数字电子技术专业英语词汇表

数字电子技术专业词汇表此专业词汇表由中山大学微电子2加2专业10级全体同学于2011年春协作查找和翻译而成ABEL一种逻辑电路设计语言Absolute value绝对值abstraction抽象academic学术的,理论的accommodate容纳acquisition获得物acronym首字母略缩词activate使活动actuator促动器addend加数adder加法器additional附加的adhering粘附的adjacency邻接物adnauseum令人作呕的advantage优势aforethought预谋alarm警告albeit虽然algebra代数algebraic代数的algorithm算法aligned对齐的alphabet字母表alphabetic照字母次序的alphanumeric字母数字的ambient周围ambiguity歧义性ambiguous引起歧义的AMI传号交替反转码amiss出差错的amplifier放大器amplitude幅度analog模拟analogous类似的anode阳极anthologies精选的appealing有魅力的append附加applicable合适的application应用appropriate恰当的aptly适当地arbitrary任意的arc电弧architecture架构archive存档arcs弧光灯arithmetic算术array数组arrow箭头artifact人工制品ascend上升ascending上升的ASIC专用集成电路assemble装配assembly装配线assert断言asserted生效的assign分配assignment分配assumption假设asterisk星号asymmetrical不对称的asynchronous异步的attenuated衰减的attenuator衰减器attic阁楼attribute属性automatic自动的automatically自动地auxiliary辅助的axiom原理balanced code平衡码bandwidth带宽barrel shifter柱式位移器base基极behavioral行为的benchmark基准bidirctional双向的binary二进制的binary digit二进制数字binomial二项式的bipolar双极的biquinary二五混合进制的bistable双稳态的bit位bit vectors位向量bitwise按位计算block阻塞;阻止;限制blow熔断boolean布尔数学体系的boolean-expression布尔表达式boost提升borrow借位bounce弹回bracket括号内的brute-force暴力bubble气泡buffer缓冲器bug故障bundling集束Bypass旁路cable电缆cache快速缓存CAD计算机辅助设计CAE计算机辅助工程cajole诱使capability能力capable能胜任的capacitance电容capacitive电容性的capacitor电容器capture占领carburetor化油器,汽化器carry进位cascade级联cascading级联catalog目录catchy易记住的categorize分类cathode负极causality因果性ceiling顶函数centerpoint中点character字符characteristic特性charge充电checksum校验和chunk相当大的数量circuitry电路的circuits电路circular环形的circumstance条件citation引用clause条款cleanup清理整顿clock时钟clockwise顺时针方向的closure封闭coaxial同轴的code编码codeword码字coding编码coefficient系数coil线圈collapse倒塌collector集电极colon列column列combinational联合的commercial商业的commutativity交换性compact紧凑的comparison比较compatibility兼容性compatible兼容的compilation编著compile编译compiler编译器complement补complementary互补的complexity复杂性complicated复杂的component成员;成分comprehensive广泛的compromise折中computation计算compute计算comsumption功率消耗concatenate连结concatenation连结conceivably令人信服的conceive构思,以为concept概念conceptual观念的,概念的concise简明的concurrent同时发生的configuration配置,构造conjure用魔术变出consecutive连续的consensus一致conservative保守的consistency一致性consistent一致的constant常数的constraint约束construct构成consume消费consumption消费contemplate深思熟虑contextual前后关系的contiguous连续的continuously连续的control logic控制逻辑controller控制器convention惯例conversely相反地convert转变converter转换器co-opted协同优化correction-factor校正因子correspond对应corresponding对应的corrupt败坏cosmic宇宙的cosmic ray宇宙射线counter计数器counterclockwise逆时针方向的counterpart与另一方相当的事物couple耦合,一对coverage覆盖范围CPLD复杂可编程逻辑器件crank柄criteria判断标准critical决定性的crosshatch画出交叉线阴影crosspoint相交点crosstalk色度亮度干扰crucial决定性的crystalline晶态的cumulative累积的curricula课程customization专用化customize定制cut off截断cycle周期cylinder圆柱daisy菊花daisy chain串级链database资料库dataflow数据流data-transmission数据传输DC balanced直流平衡deactivate使无效debounce去除抖动debug调试decade十年decibel分贝decimal十进制的declaration宣布decode解码decoder解码器decompose分解decomposed分解了的decomposition分解decoupling去耦合dedicate奉献deduce推断deem认为default默认值defect缺点definite明确的definition定义delay延迟deleterious有害的delve钻研demonstrate展示demultiplexer信号分离器denote表示density密度depicte描写derivation推导derivative导数derive导出derived导出descend下降descending下行的detect探测detector检测器deterministically确定地diagram图表dicey不确定的dictate支配difference差Differential差分dim昏暗的dimension纬度diminish减小DIP package双列直插封装diphase code二相编码directive指令disabled使失效discard丢弃discharge释放电荷discipline纪律discontinuity不连续discrete离散的disk磁盘,光盘disparity不平衡性disposition处置disregard忽视dissipate损耗dissipation损耗distinct不同的distortion扭曲disturbance干扰dividend被除数documentation文档纪录domain范围dominant占优势的dominate主导DPLL数字锁相环drain漏极dramatically戏剧地dual二重的duality二元性的duel斗争,抗争duplicate复制duration持续的时间dutifully忠实地;忠贞地dye染色dynamic动态edge边缘edge-trigger边缘触发electromechanical机电的elegance优雅的element元件,基础elevator电梯eliminate消除elimination消除embed嵌入embody体现emitter射极emphatically强调地emulate模仿encode编码encompass围绕encompassing围绕encounter冲突encyclopedic百科传书的end-around首尾循环entidy实体enumerate列举enumerated列举ephemeral短暂的equation方程式equilibrium平衡equivalence等同equivalent相当于erasable可擦除的erasable可消除的erase清除erroneous错误的error-detecting检错esoteric神秘的essence本质essential本质上essentially根本上estimate估计ethernet以太网event事件evident明显的exceed超越excess额外的excess-3余3excessive过度的excitation激发exclusive排外的execute执行exhaustive详尽的,彻底的expansion展式explanatory解释的explicit清楚的exploit开发exponentially以指数方式extension扩展external外部的extract提取eyestrain眼睛疲劳fabric构造fabricate建造fabrication建造fanout扇出fascinate使着迷feasibility可行性feasible可行的feature特征feedback反馈feedback回馈fiber-optic光纤的figure象征finite有限的finite field有限域finite-memory有限存储器fixed固定的flag标记flexibility灵活性flip翻转flip-flop触发器fluid流体;流动的flux磁通font字体foolproof万无一失的foregoing前面提到的foreseeable能预测的forestall预先阻止formula公式formulate表达formulate用公式表示formulation用公式表示formule公式fortuitous偶然发生的FPGA现场可编程逻辑阵列fraction分数frill褶边function功能,函数functionality功能fundamental基本的furthermore此外fuse熔丝fuse blown保险丝熔断garage车库gear传动装置generality一般性generalize推广generate产生generation产生,代generator发生器generic通用genuine真实的geometry几何学geopolitical地理政治学的geopolitics地缘政治学glance一瞥glitch短时脉冲波global全局的graph图表graphcially用图表表示的graphical绘画的Gray code格雷码guarantee保证halve二等分hamming哈明hardware硬件havoc毁坏hazard冒险HDL硬件描述语言heir后人hence因此hermetically密封地hexadecimal十六进制的hierarchical分层的hierarchy层次结构high-order高位的hint暗示holography全息术hook钩住horizontal水平的house收藏hydraulic液压的hype大肆宣传hypothetical假设的hysteresis滞后作用IC集成电路idempotency幂等identical同一的Identifier标识符idle空闲的illuminate照亮illustrate阐明immune免于……的immunity免疫力impedance阻抗imperfection缺点implement执行,手段implementation执行implicant蕴含项Implication暗指implicitly含蓄地;暗中地impose强加inadvertently无意地;不经意地incandescent白炽inclination趋向inclined倾向于incompatible不相容的inconsistency不一致性inconsistent不一致的incorporate加上increment增长incrementer增量器indecipherable难辨认的indeterminate不确定的Index指标indicate指示indicative标示的,指示的indicator指示器indice指数indistinguishable不易察觉的individual单个的induction归纳法Infinite无限的Infinitesimally极小地inherent固有的Inhibit抑制;禁止INIT初始化initial初始的initialization初始化initialize初始化innocuous-looking看似乏味的innovation革新insanely疯狂地insightful富有洞察力的inspection检查instantaneously瞬时地instantiate举例说明instantiation实例化instructive教育性的instrument仪器insulate使隔绝insulating绝缘的intact完好的integer整数integration完成intensity亮度,强度interchange交替变化interchangeable可互换的interconnect互相连接interconnection互连interface接口Interfacing接口intermediate中间的intermittent间歇的intermix混合internal内部的interoperability互用性,协同工作的能力interpret解释interpretation解释intersection交点intimidate威吓intriguing吸引人的intuitive直觉的intuitively直觉地,直观地invalid无效的inverse相反的inversion反转invert倒置inverter反相器invoke引起irrelevant不相关的isolation隔离itemized详细列举的iterative迭代的jitter紧张不安judiciously明智的jumble混乱的juxtaposition并列Karnaugh卡诺Karnaugh map卡诺图knob球形柄label标签lag落后于;延迟latch锁存器latch up闩锁launch发起layout布局,版面设计leakage漏leftmost最左边的legend图例legible清楚的Legitimate合法的legitimate合理的legitimately正当合理的library文库likewise同样的linear线型的linearly呈直线的literal文字的lithium锂logic逻辑lookup查找lowercase小写字母的LSI大规模集成macro宏macrocell宏单元magnetic磁的magnetization磁化magnitude幅度maintain维持maintainability可维护性的maintenance维护malice恶意Manchester code曼彻斯特编码mandatory强制的,义务的manifest显然的manipulate操作manipulation操作manual手工的manufactory工厂manufacturability可生产性manufacture制造manufacturer制造商map映射margin容限marginal在页边的matrix矩阵maximize增至最大限度maximum极大,最大限度MCM多次接触混相Mealy米里型状况mechanical机械的,固定的mechanism机制,原理media介质medium手段megohm百万欧姆merge使合并merit长处messier混乱的metastability亚稳定性metastable亚稳的methodology一套方法microampere微安microprocessor微处理器migrate移往mil千分之一military军事的mimic毫米波单片集成电路minimal最小的minimize减至最小minimizer最小化器minterm最小项minuend被减数misleading误导的mismatch使配合不当mnemonic记忆的moderate适度的moderate中等的moderate-speed中等速度modify修改modular模的modulo以…为模molecular分子的molecule分子momentary短暂的monolithic整体的;庞大的MSI中规模集成multibit多位multichip多片状multiphase多相multiple复合的multiplexer多路复用器multiplicand被乘数multiplicant被乘数multiplication乘法multiplier乘数multiply相乘multisource多源mutual相互的NAND gate与非门nanosecond纳秒narrative叙述negate求反negation否定negative logic负逻辑negligible可忽略的negotiate谈判,商议nerd讨厌的人nested嵌套的nesting嵌套nibble半字节noise margin噪声容限nomenclature术语nominal名义上的noncritical非关键的noncrystalline非晶体的nondeterministically非确定地nonideal非理想的noninverting同相nonlogic非逻辑nonnumeric非数值的nonoverlap不重合nontrivial重要的nonvolatile非挥发性的nonzero非零的NOR或非notation符号notion概念notwithstanding尽管noxious有害的;有毒的NRE负阻元件NRZ不归零逢1翻转制obsolescence废弃obsolete淘汰obtain获得, occasional不经常的octal八进制的omit省略,忽略open-drain漏极开路operand操作数operation操作optimal最佳的optimization优化optimize使最优化optional可选择的orientation定位oriented面向……的original原件oscillate震荡oscillator震荡器outcome结果outline提纲overall总体的overflow溢出overflow溢出overlay覆盖overly过度的overridden无效的overstress过应力package封装pad焊盘painstaking勤勉的pairwise成对地panel平板、控电板paradigm范例parallel平行的parameter参数,参量parenthesen括号parenthesize加括号parity奇偶校验parlance说法partial部分的partial product部分积partition分割partitioned分段的patent专利pattern模式PCB印刷电路板perform执行perfume香料peril危机periodic周期性的periphery边缘Perl一种CGI脚本语言permanent永久的,固定的persistent不断的pertain关于,perverse错误的pessimistic悲观的phase阶段philosopher哲人philosophy哲学pictorial绘画的;形象化的pin引脚pin number引脚号pinout引出线pipeline流水线pit凹陷pitfall缺陷pixel像素PLA可编程逻辑阵列PLD可编程逻辑器件pneumatic气动pointy-haired秃头polarity极polymer聚合体portion部分portray画像postpone延迟postulate假设potential有可能的potentially潜在地,可能地precede在之前,先于precedence优先权preceding前述的precise精确的precomputed预先计算的predecessor前身predefined预先确定predetermined先已决定的prefix前缀preliminary初步的premise前提preponderance优先preset预置prime基本的primitive原始的probing探测procedural程序上的procedure程序proceed前进,进行programmable可编程的propagate传播propagation传播property特性proportional比例的proportionally按比例pros and cons赞成和反对的理由protocol条款,协议prototype雏形,蓝本provision供应prudent谨慎的pseudo假的pseudorandom伪随机的pulse脉搏;脉冲pump泵punctuation标点符号puncture穿孔purist纯化论者pushbuttons按键PWB线路板quad四倍的quadruple四倍的quartz石英quiescent静态的quote引述;举证;报价quotient商quotient商,商数radically根本地,本质上radices根,基数radix基数rail轨random随意的Range范围规格rating标称值rationale基本原理readability可读性reciprocal互惠的Recommended值得推荐的Reconvened再聚会;再集会rectangle矩形recursively回归地,递归地redeeming补偿的redefined重新定义的redo改装redraw重画reduced约简的redundant多余的reference参考refinement提纯reflected反射reg寄存器regardless不顾regenerate使再生regenerative恢复的register寄存器reinforce加强relay中转relay logic继电器逻辑remainder余数replica复制品replicate复制representation表示法representative代表reprogrammability可重复编程request要求reserved保留的reset重置resistive抵抗性的resistor电阻器respectively分别地restrict受限制的restriction约束retard阻碍retrieve检索reveal显示revenue收入reverse反转Reverse-polarity逆极性;逆偏振revise修改revolution革命rightmost最右边的ripple波纹ripple adder行波加法器robust强健的robustness鲁棒性rollover翻转rotary旋转的rotation旋转roughly大致row一行RZ归零制salient显著的sanity明智satisfy令人满意的saturate浸湿scale规模scan扫描scenario局面schematic原理图scheme计划scope范围sector部门segment部分selectively选择性的self-complementing自补码semantics语义学semicolon分号semiconductor半导体seminumerical半数值的sensitivity敏感度sensor感应器separate使分离sequence顺序,序列sequential时序的,相继的serially连续的shift移位shifter转换机构shortcut捷径shrapnel榴弹shuffle弄混;乱堆sign符号signal信号signed-magnitude符号量值significant重要的silver-halide卤化银simple-minded头脑简单的simplify简化simulate仿真simulation仿真simulator仿真器simultaneous同时的sink使下沉sketch画图skew偏斜slant倾斜的slash斜杠SMT表面装配技术sneak path潜通路Snext综合近端串扰socket插口solder焊接solely唯一地sophisticate复杂的sourcing供应sparsest稀疏的spec规格specification规格specified指定的specify指定sponsor赞助商sponsored赞助的sprinkled点缀Sreg状态寄存器SSI指令基本格式stabilize使稳固static静态stereo立体声stimulate刺激storage贮藏straightforward直接的strategy策略stray杂散的stream流stream流structural结构化的structure结构stubborn顽固的subarray子阵列subcube子集subdirectory子目录subexpression子表达式subrange子范围subroutine子程序subscript下标符号subsection分段subsequent随后的subset子集subsidiary附属的substantial实际的substitute替换substituting取代subsystem子系统subtle细微的subtlety微妙subtract减subtraction减法subtractor减法器subtrahend减数subtype子类型successive连续的sufficient足够的suffix下标summarize总结superset扩展集supplant取代suppression抑制susceptible易受影响的swallow吞swap交换switching-algebra开关代数symmetric对称的symmetry对称性synchronize使同步synchronizer同步器synchronous同步的syndrome典型表现synopsys电子设计软件商名syntactical语法的syntax语法synthesis综合synthesize综合synthesized合成的synthesizer合成器table图表tabular列成表格的tabulated制成表的Tailored定做的tedious单调的tedium沉闷telecommunication电信template模版temporarily暂时地tempt使想要tentacle触角terminal终点termination终止Test试验test bench测试台text文本textual文本的theorem定理theoretical理论的threshold阈值thru-hole通孔tick时钟跳动timescale时间标尺toggle跳转tolerant忍受的topology拓扑,布局track记录track路径trademark商标transceiver收发器transcribing抄写transfer迁移transform转换,改变transformer-coupled变压器耦合transient瞬态的transistor晶体管transition转变transmission传送transmit传输transparent透明的transponder收发机transpose移项treatise专著treelike树状tricky难处理的trigger触发trivial琐细的truncate截短truth table真值表trvial没价值不重要的TTL晶体管-晶体管逻辑(电路) turn-the-crank实现tweak调整tweaking补偿ultraviolet紫外线unambiguous不含糊的uncompressed无压缩的unconstrained不受拘束的underscore强调undetectable不可探测性undue过度的unidirectional单向的unique唯一的unprimed未装填的unsigned无符号的unspecified非特指的unwieldy笨重的upgrade升级、提高品质uppercase大写字母的valid有效的vaporize使蒸发variables变量variation变化vector矢量vendor卖主verbal言语的Verification确认verify证实verilog一种逻辑电路设计语言versa电磁阀versatile多用途的version版本versus对vertical垂直的VHDL一种逻辑电路设计语言vice versa反之亦然victim牺牲者vinyl乙烯树脂violate违反visualize在脑中使形象化visually视觉上VLSI超大规模集成电路volatile易变的wafer晶片waveform波形weighted code加权码weird离奇的wire电线withstand承受wrapper包装wreak诉诸XOR异或yield产出。
Memristor based memory The sneak paths problem and solutions

Memristor-based Memory:The Sneak Paths Problem and Solutions Mohammed Affan Zidan a,Hossam Aly Hassan Fahmy b,Muhammad Mustafa Hussain a,Khaled Nabil Salama aa Electrical Engineering,King Abdullah University of Science and Technology(KAUST),Thuwal23955-6900,Saudi Arabiab Electronics and Communication Department,Faculty of Engineering,Cairo University,Cairo,EgyptAbstractIn this paper,we investigate the read operation of memristor-based memories.We analyze the sneak paths problem and provide a noise margin metric to compare the various solutions proposed in the literature.We also analyze the power consumption associated with these solutions.Moreover,we study the effect of the aspect ratio of the memory array on the sneak paths.Finally,we introduce a new technique for solving the sneak paths problem by gating the memory cell using a three-terminal memistor device. Keywords:Nanotechnology,Memory,Memory Array,Memristor,Sneak Paths1.IntroductionMemristors(memory resistors)offer a promising alternative to conventional memory devices.According to the Interna-tional Technology Road-map for Semiconductors(ITRS),cur-rent memory technologies(DRAM,SRAM,and NAND Flash) will soon be facing design challenges related to their contin-ued scaling-down[1].Memristors are considered to be a very good candidate for future memory devices when compared to other emerging technologies such as Magnetoresistive RAM (MRAM)and Phase Change RAM(PCM/PCRAM)[2].The main advantage these emerging technologies share is the prop-erty of retaining data after bias removal.Moreover,memristor-based memories have many unique advantages including very high density compared to other memory technologies and hard disk drives.The memristor is a nonlinear resistor which changes its state relative to the net charge(or net electricflux)passing through its two terminals.It saves its state after an electrical bias is removed.The memristor(M),which was described by Chua in1971[3],is generally thought of as the fourth of the two-terminal basic passive elements,alongside the resistor(R),ca-pacitor(C),and inductor(L).Thefirst reported passive imple-mentation of the memristor was the TiO2-based device intro-duced by HP in2008[4].Recently,devices based on different materials have been introduced[5–9].In addition,several mod-els for memristors has been introduced[10–16].Since thefirst reported use of the memristor,it received a significant of at-tention in the research community.In addition to be used as a memory element[2,17–26],the memristor has found many applications in oscillators[27–30],logic and arithmetic cir-cuits[31,32],programmable analog circuits[33,34],and in modeling and emulation of natural phenomena[35,36].Email addresses:mohammed.zidan@.sa(Mohammed Affan Zidan),hfahmy@(Hossam Aly Hassan Fahmy), muhammadmustafa.hussain@.sa(Muhammad Mustafa Hussain),khaled.salama@.sa(Khaled Nabil Salama)One of the main challenges facing the memristor at the circuit and architecture level is the sneak paths problem.In this paper we introduce a new way to analyze the sneak paths using nor-malized noise margins.Our analysis is based on simulations for different memory array sizes,data sets,and architectures using the models presented in[17].Moreover,we study the effect of the aspect ratio of the memory array on the sneak paths.Finally, a new method is introduce for solving the sneak paths based on a new gating technique by using three-terminal memistor device as a gate for the memristor memory cell.The following section discusses the main concept of the memristor-based memory.The Section3describes the sneak paths analysis,and Section4summarized the main solutions for the sneak paths that have been described in the literature. Then,the new proposed solution is given in Section5.2.Memristor-Based MemoryMemristor-based memories are fabricated as a high-density crossbar architecture.Memristor devices are located at each intersection between two bars,as shown in Fig.1.Typical memristor-based memories do not use transistors for cell gat-ing.The advantage of these devices is that they have a retain-able memory and a very high density compared to otherstorage Figure1:A simple memristor-based memory array showing how a memristor device is located at the intersection between two bars of the array.纵横比Table1:Detailed comparison between memristor-based memory,traditional memories,and other emerging memories according to the2011ITRS report[1].The abbreviations used are:T–transistor,C–capacitor,R–resistor,and D–diode.The bold font indicates the best value per row.Traditional Memories Other Emerging Technologies Redox DRAM SRAM NOR Flash NAND Flash FeRAM MRAM PCRAM Including Memristor Cell Element1T1C6T1T1T1T1C1(2)T1R1T(D)1R(1D)(1T)1R Feature Size(nm)36-6545902218065459 Density(Gbit/cm2)0.8-130.4 1.2520.14 1.212154-309 Read Time(ns)2-100.215100453512<50 Write Time(ns)2-100.210710665351000.3 Retention Time4-64ms N/A10years10years10years>10years>10years>10yearssystems.Table1shows a detailed comparison between memristor-based memory,traditional memories,and other emerging mem-ories.The memristor memory is4x as dense as the hard disk drive(HDD)[37],and23x as dense as DRAM.As a result, memristor-based memories are a good candidate for replacing both the permanent and running storages,therefore approaching the ideal model of having oneflat memory instead of memory hierarchy.The current reading and writing speeds are slower than DRAM and SRAM,but are very fast compared toflash memories,as shown in Table1.These numbers show that mem-ristors could easily replaceflash memories,while further speed enhancement is required for replacing CMOS memories.HP Labs are currently reporting a fast switching time of less than 2ns[38].Recently,Elpida Memory Inc.,reported the develop-ment of a high-speed non-volatile resistance memory[39].It is to be noted that any resistor with a hysteresis curve is consid-ered a memristor[40].HP Labs expects to come up with their memristor-based memory chip replacingflash and solid-state drives(SSD)in2013[41].2.1.Writing OperationData are stored in the memristor in the form of its resistance value,where each of the limiting resistances R o f f and R on are assigned to the two Boolean values‘0’and‘1’.R o f f and R on are the maximum and minimum resistances of the device,respec-tively.Writing one of these values is simply done by passing current through the cell of interest until the memristor’s resis-tance saturates.The saturation value(R on or R o f f)depends on the direction of the writing current.Even this simple writing operation could consume considerable of energy,depending on the values of the memristor’s resistances.2.2.Reading OperationWhile writing to the memristor is a straightforward opera-tion,reading is more challenging.In the memristor memory array,we are trying to sense a cell resistance merged in a com-plete resistive structure.This could be compared to the problem offinding a needle in a haystack.Moreover,the reading oper-ation itself could be destructive to the cell data,depending onthe device properties.2.3.Multilevel MemoryMultilevel memory is one promising application for the memristor ing such a technique would enormously increase the density of memristor-based memory,but wouldalso reduce the noise margin significantly.The current pro-posed techniques for building binary memristor-based memorysuffer from many problems that could be fatal for the multi-level memory.Some researchers believe1M is insufficient forbuilding multilevel memory,and that1M1T(one memristor andone transistor)or1M1D(one memristor and one diode)areneeded[42].We believe that addressing the current challengesfacing the binary memristor-based memory will directly solvethe multilevel memory problems.3.Sneak Paths AnalysisSneak paths are undesired paths for current,parallel to the intended path.The source of the sneak paths is the fact thatthe crossbar architecture is based on the memristor as the only memory element,without gating.Fig.2a shows an array witha simple voltage divider and its equivalent circuit.Thefigureshows the ideal case in which the currentflows from the sourceto the ground passing through only the desired cell at the inter-section between the activated column and row.Unfortunatelythis is not the real case as shown in Fig.2b.The currentflowsthrough many sneak paths beside the desired one.These pathsact as an unknown parallel resistance to the desired cell resis-tance as shown in Fig.2b.What makes the sneak paths problemharder to solve is the fact that the paths depend on the contentof the memory.This is due to the fact that the current will sneakwith more intensity through the paths with smaller resistance,which is memory content dependent.The added resistance of the sneak paths significantly narrowsthe noise margin and reduces the maximum possible size of a memristor array.To study the effect of the sneak paths on thenoise margin,we simulate memristor-based memory arrays of漏电流路径更趋向于电阻小的通路,所以漏电流依赖于存储的内容V (a)R M R SP(b)Figure 2:The reading current path through a memristor memory array and the equivalent circuit for (a)the ideal case where the current flows only through the target cell and (b)an example of a real case where current sneaks through di fferent undesired paths.The green lines show the desired path and the red ones show the e ffective sneak paths.di fferent sizes and with di fferent data sets.The sets are selected to reflect both the worst and best cases for the memory content.The worst case for the sneak paths is a memory full of “ones”since the e ffect of the sneak paths becomes more dominant as their resistance decreases.On the other hand the “all zeros”case is the best case condition since all the sneak paths are made of R o f f resistances in series.In addition tothe previouscases,checkered casestypical of real data and interleaved rows (or columns)are also used.These cases are considered as normal test cases since ones and zeros are present in equal numbers and are uniformly distributed.The simulation result is independent of the location of the cell in the array if we neglect the rows’and columns’pad resistances.We can interpret the array as a complete sphere,since connecting the terminals of each row or column will not introduce any change to the equivalent circuit as shown in Fig.3.Hence all the cell locations are equivalent from the sneak paths point of view.All the simulations werewhere a and k x are constants.The reported feasible values in [17]for the constants are a =3−1and k on =10−8A and k o f f =10−11A for the ON and OFF states of the device respec-tively.In conventional CMOS circuits,there are two regions defined for accepted values of ONEs and ZEROs [43],as shown in Fig.4.For typical CMOS circuits,the prefect ONE has the value of V OH =V dd and the perfect ZERO is V OL =GND .However,the circuit can tolerate shift in values of the input of the value detected for ONE or ZERO noise.For a given ence between voltages values representing ONE and ZERO at the target cell is a perfect measure for the sneak-path e ffect.We define a total noise margin as the region between the ON (2)the such V ol cir-and 忆阻器的位置对漏电影响不大To study the effect of the array size on the sneak-paths we de-fined a normalized value,where the∆is compared to its best case,as:∆′=∆Array∆Device(3)where∆Device is the case of one device used(the best case)while ∆Array is for the array case.∆Array is highly dependent on the data stored in the memory as shown later.3.1.Floating ArrayThe basic structure for a memory array is to leave the un-used array terminalsfloating.Simulation results for thefloat-ing memristor array are shown in Fig.5a.Thefigure shows∆′versus the array size for four different data sets.The simula-tions show that the noise margins of both the“all ones”and the “interleaved”cases almost vanish at a very small array size of 4kbit.At the array size of16kbit,∆′reaches a negligible value of0.00145and0.00323for the“all ones”and the“interleaved”cases respectively.This shows how the sneak paths affect the noise margins and consequently limit the maximum capacity of the array.On the other hand,the noise margin for the best case condition is almost unaffected by the array size.The reason for this is that the large R o f f/R on(k o f f/k on)ratio of103makes sneak paths of resistances R o f f in series ineffective.3.2.Grounded ArrayGrounding the unselected rows and columns might be con-sidered as a mean of preventing sneak paths.In[20]the equiv-alent circuits for all the possibilities of grounding thefloating terminals are given.None of the four possibilities of:1)float-ing rows and columns,2)floating rows and grounded columns, 3)grounded rows andfloating columns,and4)grounded rows and columns,could solve the sneak paths problem.The idea behind grounding thefloating terminals is to provide paths for the sneaking current to the ground rather than the sense cir-cuit.However,part of the current will stillfind its path to the ground through the load resistance.Effectively grounding rows or columns or both will move part of the unknown resistance of the sneak paths so that it is parallel to the total resistance of the equivalent circuit instead of R M,which does not solve the problem.While grounding the array’sfloating terminals does not solve the sneak paths problem,it does marginally improve the noise margin.Fig.5b-d shows the simulation results for∆′versus the array size for the grounded terminals cases.For the grounded rows and columns case,the simulations show that the noise margin still vanishes as the array size increases but at a slower rate than in thefloating terminals case.At an array size of 16kbit,∆′reaches a negligible values of0.052and0.096for the “all ones”and the“interleaved”cases respectively,but on the other hand these values are higher than for thefloating terminals case.The two cases of grounding either columns or rows showslightly better results.This is due to fact that grounding both rows and columns at the same time is equivalent to short circuit any element not in the selected row or column.Since each of Figure5:Noise margins(∆′)versus the array size containing four different data sets.Figure 6:Power consumption versus array size plotted logarith-mically for the cases of grounded and floating array terminals.The dotted line shows the ideal case without the sneak paths e ffect.these unselected elements two terminals will be connected to ground.Therefore,the total resistance of the sneak-path will be less than the case of grounding either rows or columns sepa-rately.The main disadvantage of the grounded technique is the huge power consumption for the reading operation compared to the floating terminals case.Fig.6shows a logarithmic plot of the average power consumption for the cases of floating and grounded terminals.The figure shows the enormous increase in power consumption for the grounded terminals case com-pared to the floating terminals case.Fig.7shows that the in-crease in power consumption is much more than the increase in noise margin.At an array size of 16kbit,an averagepower of 12.77µW is consumed in the grounded terminals case,com-pared to 48.88nW in the case of floating terminals,i.e.power grounded terminals solution impractical.Also,at large array sizes,the improvement in the noise margin is impractical since the margin almost vanishes.4.Sneak Paths SolutionsIn this section the main solutions proposed in the literature for the sneak paths are discussed.4.1.Multistage ReadingThis method was introduced in [17]by the HP Labs team.Their technique attempts to overcome the sneak paths problem using a straightforward,but long,algorithm.The reading pro-cedure is given as:1)perform current measurement for the tar-get cell,2)put the target cell in the OFF state,and perform current measurement for the target cell,3)put the target cell in the ON state,and perform current measurement for the target cell,4)compare the measured currents to determine the state of the cell,and 5)return the memory cell to its (assumed)original state.This sensing algorithm requires a large amount of time and also a large sensing circuit (three sample-and-hold circuits,a voltage comparator,voltage divider,and the control circuit).This technique will also be ine fficient for the narrow noise mar-gins at large array sizes,since the e ffect of sneak paths will dominate and the resistance value of the target cell will be neg-ligible.According to the simulations shown in Fig.5a,∆′could be as low as 0.00145for an array size of only 4kbit.4.2.Unfolded ArchitectureThis solution is presented in [20],and is based on having a separate column for each memristor,as shown in Fig.8.While this solution eliminates the sneak paths problem,it enormously reduces the memory density.The decreased density can be de-(4)and will also much less4.3.Diode GatingOne of the proposed solutions for the sneak paths is to add a diode to each memory cell[20],producing a new cell of one diode and one memristor(1D1M),as shown in Fig.9.Such a strategy would eliminate sneak paths.According to[44], adding diodes to the array will increase the delay of the sys-tem by adding capacitive loads and diode threshold voltages will decrease the output swing.However,the major problem facing such a strategy is that it will block the writing process in the native array structure,since writing to a memristor requires two different polarities.In[45]a3D array structure is provided to enable the write operation with a diode present.In this tech-nique,each cell will contain one programming element,two diodes,and four connecting crossbars.While this technique al-lows the write operation,it consumes more area per cell.In addition,the3D alignment for four bars may reduce the array density significantly.Finally,it is not clear that the new struc-ture containing four bars will still eliminate the sneak paths. 4.4.Transistor GatingUsing large transistors for gating the memristor will solve the sneak paths problem.On the other hand this method will ruin the high memristor-memory density,since the gating tran-sistor’s size is much larger than that of the memristor.Although using small devices will reduce the sneak paths it will not elim-inate it.This is due to the fact that the recently introduced small transistors are consider to act as leaky valves.Moreover,these devices with relatively high OFF current will increase the static power component significantly.Finally,it should be mentioned that one of the major issue of using transistor gating is its limi-tation to the3D stacking of memristor arrays.In[46]an array of one transistor and one memristor(1T1M)is reported.They report a gating transistor of10µm channel length and200µm channel width.Moreover,two wires are required for driving each cell;one for the transistor and one for the memristor.plimentary MemristorsIn this technique two complimentary memristors are used a the memory cell,so that their total resistance are always“R on+Figure9:Simple memory array with1D1M used for each mem-ory cell.R o f f”,as introduced in[47].Having always a high resistancecell reduces the sneak-path current significantly.In this methodONE is distinguished from the ZERO by the orientation of thedesired cell,{R on,R o f f}or{R o f f,R on}.Therefore,a complex reading technique is required.Moreover,the system will nottake full advantage of having high R o f f/R on device.ing Memristors NonlinearityThe voltage drop on the desired cell is higher than any of thesneak-path elements,since the shortest sneak-path will containat least three series memristors.In[48],a high nonlinear deviceis reported,such that I(V/2)≈I(V)/100at V≈1V.This veryuseful property will significantly reduce the sneak paths currentrelative to the desired cell current,and will consistently reducethe sneak-path effect by a high factor.This solution also willnot be practical for large memory array.4.7.AC SenseInstead of using regular DC signal an AC signal is used forsensing the data stored in the desired cell,as introduced in[49].This technique uses load capacitance at the input of the senseamplifier to implement a low passfilter,as shown in Fig.10.The response of thefilter is mainly based on the resistive valueof the desired cell.However,this method adds extra complex-ity for the memory system,since AC input and sensing are re-quired.Moreover,this method will not be as effective for largearrays.Figure10:Simple memory array showing the added columncapacitors for the AC sense.5.Array Aspect RatioIn this section we study the effect of the aspect ratio on theperformance of memristor array.Non-unity aspect ratio couldbe thought of as a helping method towards a sneak-paths freememory.The aspect ratio of an array is defined as its numberof columns to the number of rows.Normal square arrays haveaspect ratios of unity.The aspect ratio of the memory array isone of the main parameters which could be used to limit theeffect of the sneak paths.A memory with one row or one col-umn will not suffer from sneak paths at all,since there will beonly one path for the current as shown in Fig.11.As the aspectratio approaches unity,the possibilities for sneak paths increaseand∆′decreases.An unbalanced aspect ratio structure could123123构成低通滤波器be fabricated in a square area by folding the array in a zigzag shape.However,the main cost of using an aspect ratio other than one is the increase in the required area for selection and sensing circuitry.This area could be given as:Sense Circuit Area =√S [θ√A +ρ√A ](5)6.Gating Using Three-Terminal Memistor Device Memristors can be considered better gates compared to tran-sistors or diodes,since they can be characterized by having very high OFF resistance with much smaller area.In [17],memristor devices are reported to have R o f f =1G Ω.Moreover,memris-tors are not intruder species to the memory array,compared to and diodes.However,it is not possible to write on ei-the gate memristor or the data memristor separately,given with high ON /OFF ratios of more than one hundred.trying to introduce extra rows or columns to enable sep-writing will return us to the initial point,where the sneak are dominant.The three-terminal memistor device captures both of the of the memristor and transistor as a gate device.device was introduced prior to the memristor in 1960by [50].The memistor is a three-terminal device whereDesired CellData Device ON Memistor13:Structure of the proposed memristor gated array,an example of selected of selected cell is shown.the resistance between two terminals is controlled using the third one,in the same analogy of transistor but with a mem-ory effect.In other words,the resistance of the device is con-trolled by time integral of the current on the third terminal and not the instantaneous current as the case of transistor,as stated be in[50,51].This means that there is no need to keep an ac-tive bias on the third terminal to keep the device ON(or OFF). The memistor will retain is ON or OFF state after removing the bias from the third terminal.One of the advantages of this bias-less switching is the very low static power consumed.Memis-tors can inherent the high ON/OFF ratio and small footprint of memristors and the high controllability of transistor by having a third terminal.Fig.13shows the structure of the memistor gated array,where each memory cell is gated with a memis-tor device.Extra columns are required for programming the memistor gate.It is a assumed that the memistor has the same ON/OFF values of the data cell.At the desired cell the gate de-vice is turned ON and all the other gates are turned OFF,which is how the desired cell is selected.Therefore,all the sneak paths will contain at least three series high resistances.This will shift the operation of the memory to work equivalently to the best case scenario,where all the sneak paths are made of OFF de-vices.All the unselected cells will have a total resistance higher than R o f f.The resistance of the selected cell,with open gate, will depend mainly on the data device resistance.This resis-tance willbe either2R on or R o f f+R on,with a very high ON/OFF ratio.Our proposed method has a major advantage over the complementary memristors technique that the desired cell has much higher ratio between its ON and OFF states.In comple-mentary structures the total resistance is always(R on+R o f f),in all of the cases.Based on that,our proposed solution has higher average signal to noise ratio.Moreover,the R o f f/R on ratio of the device is directly reflected on desired cell state values. Fig.14show the noise margins for the proposed technique and the normal array withfloating terminals versus the array size for the worst case data set“all ones”.It appears clearly that the memistor gating has a significant impact on the sneak pathsFigure14:Noise margins(∆′)versus the array size for the normal array withfloating terminals and the new introduced memistor gated array for“All Ones”data set.Also the ratio be-tween the two results are shown in green color on the secondary axis.Figure15:Average power consumption versus the array size for the normal array withfloating terminals and the new introduced memistor gated array for“All Ones”data set.effect,where the worst case of the memistor gating is almost as the best case of the normal array withfloating terminals.For 16Kbit array the memristor gating architecture noise margins is 619.5x compared to the normal array withfloating terminals.In the same direction,the worst case power consumption is signif-icantly decreased as shown in Fig.15.For the worst case with the memoryfilled with“all ones”,average power consumption was reduced more thanfive time for an array size of16kbit. This ratio increases as the array size increases.Finally,in worth mentioning that while miniaturizing the three-terminal memis-tor as a single device did not pass the same long path as the two-terminal memristor,we believe that its great advantages as a gating device will motivate the fabrication community for cre-ating better memistor devices.7.ConclusionWe reviewed the main introduced solutions for the memris-tors sneak-paths problem.We proposed a new technique for an-alyzing the sneak paths problem facing memristor-based mem-ory arrays.The new analysis is accompanied by simulations on Cadence Virtuoso6for different memory array sizes,data sets,and architectures.We also studied the memory array as-pect ratio effect on the sneak paths.Finally,we introduced an new solution for the problem based on using the three-terminal memistor device.AcknowledgmentsThe authors would like to thank Dr.Amro Elshurafa for his reviews and valuable suggestions.References[1]International technology roadmap for semiconductors.URL /[2]O.Kavehei,S.Al-Sarawi,K.Cho,K.Eshraghian, D.Abbott,Ananalytical approach for memristive nanoarchitectures,Arxiv preprint arXiv:1106.2927.[3]L.Chua,Memristor-the missing circuit element,IEEE Transactions onCircuit Theory18(5)(1971)507–519.[4] D.B.Strukov,G.S.Snider,D.R.Stewart,R.S.Williams,The missingmemristor found,Nature435(2008)80–83.[5] A.Zakhidov,B.Jung,J.Slinker,H.Abru˜n a,G.Malliaras,A light-emitting memristor,Organic Electronics11(1)(2010)150–153.[6]S.Jo,K.Kim,W.Lu,High-density crossbar arrays based on a si memris-tive system,Nano letters9(2)(2009)870–874.[7]N.Gergel-Hackett, B.Hamadani, B.Dunlap,J.Suehle, C.Richter,C.Hacker,D.Gundlach,Aflexible solution-processed memristor,IEEEElectron Device Letters30(7)(2009)706–708.[8]R.Waser,Resistive non-volatile memory devices,Microelectronic Engi-neering86(7-9)(2009)1925–1928.[9]T.Kim,E.Jang,N.Lee,D.Choi,K.Lee,J.Jang,J.Choi,S.Moon,J.Cheon,Nanoparticle assemblies as memristors,Nano letters9(6) (2009)2229–2233.[10]Z.Biolek,D.Biolek,V.Biolkova,SPICE model of memristor with non-linear dopant drift,Radioengineering18(2)(2009)210–214.[11]J.Valsa,D.Biolek,Z.Biolek,An analogue model of the memristor,Inter-national Journal of Numerical Modelling:Electronic Networks,Devices and Fields24(4)(2011)400–408.[12] A.G.Radwan,M.A.Zidan,K.N.Salama,HP memristor mathematicalmodel for periodic signals and DC,in:IEEE International Midwest Sym-posium on Circuits and Systems(MWSCAS’10),2010,pp.861–864. [13] A.G.Radwan,M.A.Zidan,K.N.Salama,On the mathematical model-ing of memristors,in:IEEE International Conference on Microelectronics (ICM’10),2010,pp.284–287.[14]H.Abdalla,M.Pickett,SPICE modeling of memristors,in:IEEE In-ternational Symposium on Circuits and Systems(ISCAS’11),2011,pp.1832–1835.[15]S.Kvatinsky,E.Friedman,A.Kolodny,U.Weiser,Team:Thresholdadaptive memristor model,Submitted to IEEE Transactions on Circuits and Systems I:Regular Papers,(also CCIT Technical Report#804). [16]T.Prodromakis,B.Peh,C.Papavassiliou,C.Toumazou,A versatile mem-ristor model with nonlinear dopant kinetics,IEEE transactions on electron devices58(9)(2011)3099–3105.[17]P.V ontobel,W.Robinett,P.Kuekes,D.Stewart,J.Straznicky,R.Stan-ley Williams,Writing to and reading from a nano-scale crossbar memory based on memristors,Nanotechnology20(2009)425204.[18]Y.Ho,G.Huang,P.Li,Dynamical properties and design analysis for non-volatile memristor memories,IEEE Transactions on Circuits and Systems I:Regular Papers58(4)(2011)724–736.[19]K.-H.Jo,C.-M.Jung,K.-S.Min,S.-M.Kang,Self-adaptive write circuitfor low-power and variation-tolerant memristors,IEEE Transactions on Nanotechnology9(6)(2010)675–678.[20]H.Manem,G.Rose,X.He,W.Wang,Design considerations for variationtolerant multilevel cmos/nano memristor memory,in:Proceedings of the 20th symposium on Great lakes symposium on VLSI,2010,pp.287–292.[21]Y.Pershin,M.Di Ventra,Experimental demonstration of associativememory with memristive neural networks,Neural Networks23(7)(2010) 881–886.[22]K.Eshraghian,K.Cho,O.Kavehei,S.Kang,D.Abbott,S.Kang,Mem-ristor MOS content addressable memory(MCAM):Hybrid architecture for future high performance search engines,IEEE Transactions on Very Large Scale Integration(VLSI)Systems(99)(2010)1–11.[23] D.Niu,Y.Chen,Y.Xie,Low-power dual-element memristor based mem-ory design,in:The16th ACM/IEEE international symposium on Low power electronics and design,2010,pp.25–30.[24]Y.V.Pershin,M.D.Ventra,Experimental demonstration of associativememory with memristive neural networks,Neural Networks23(7)(2010) 881–886.[25]P.O.V ontobel,W.Robinett,P.J.Kuekes,D.R.Stewart,J.Straznicky,R.S.Williams,Writing to and reading from a nano-scale crossbar mem-ory based on memristors,Nanotechnology20(42)(2009)425204. [26]G.Huang,Y.Ho,P.Li,Memristor system properties and its design ap-plications to circuits such as nonvolatile memristor memories,in:In-ternational Conference on Communications,Circuits and Systems(IC-CCAS’10),2010,pp.805–810.[27] A.Talukdar, A.G.Radwan,K.N.Salama,Generalized model formemristor-based wien family oscillators,Microelectronics Journal42(9) (2011)1032–1038.[28] A.Talukdar,A.G.Radwan,K.N.Salama,Non linear dynamics of mem-ristor based3rd order oscillatory system,Microelectronics Journal43(3) (2012)169–175.[29]M.A.Zidan,H.Omran,A.G.Radwan,K.N.Salama,Memristor-basedreactance-less oscillator,Electronics Letters47(22)(2011)1220–1221.[30]M.Itoh,L.Chua,Memristor oscillators,Int.J.Bifurcation and Chaos18(11)(2008)3183–3206.[31]W.Robinett,M.Pickett,J.Borghetti,Q.Xia,G.Snider,G.Medeiros-Ribeiro,R.Williams,A memristor-based nonvolatile latch circuit,Nan-otechnology21(2010)235203.[32] F.Merrikh-Bayat,S.Shouraki,Memristor-based circuits for performingbasic arithmetic operations,Procedia Computer Science3(2011)128–132.[33]S.Shin,K.Kim,S.-M.Kang,Memristor applications for programmableanalog ics,IEEE Transactions on Nanotechnology10(2)(2011)266–274.[34]Y.Pershin,M.Di Ventra,Practical approach to programmable analogcircuits with memristors,IEEE Transactions on Circuits and Systems I: Regular Papers57(8)(2010)1857–1864.[35]Y.V.Pershin, Fontaine,M.Di Ventra,Memristive model of amoebalearning,Physical Review E80(2)(2009)021926.[36]S.Jo,T.Chang,I.Ebong,B.Bhadviya,P.Mazumder,W.Lu,Nanoscalememristor device as synapse in neuromorphic systems,Nano letters10(4) (2010)1297–1301.[37]M.Kryder,C.Kim,After hard drives-what comes next?,IEEE Transac-tions on Magnetics45(10)(2009)3406–3413.[38] F.Miao,J.P.Strachan,J.J.Yang,M.-X.Zhang,I.Goldfarb,A.C.Tor-rezan,P.Eschbach,R.D.Kelley,G.Medeiros-Ribeiro,R.S.Williams, Anatomy of a nanoscale conduction channel reveals the mechanism of a high-performance memristor,Advanced Materials23(2011)5633–5640.[39]Elpida Memory develops resistance RAM prototype.URL /en/news/2012/01-24r.html [40]L.Chua,Resistance switching memories are memristors,Applied PhysicsA:Materials Science&Processing102(4)(2011)765–783.[41] D.Manners,IEF2011:HP to replaceflash and SSD in2013,ElectronicsWeekly(2011).[42]G.Rose,Overview:Memristive devices,circuits and systems,in:IEEEInternational Symposium on Circuits and Systems(ISCAS’10),2010,pp.1955–1958.[43]S.-M.Kang,Y.Leblebici,CMOS Digital Integrated Circuits Analysis&Design,McGraw-Hill,2007.[44]W.Fei,H.Yu,W.Zhang,K.Yeo,Design exploration of hybrid cmos andmemristor circuit by new modified nodal analysis,IEEE Transactions on Very Large Scale Integration(VLSI)Systems(99)(2011)1–15.[45] B.Mouttet,Programmable crossbar signal processor,US Patent7,302,513(2007).[46]S.Kim,H.Jeong,S.Kim,S.Choi,K.Lee,Flexible memristive memoryarray on plastic substrates,Nano Letters11(12)(2011)5438–5442. [47] C.Jung,J.Choi,K.Min,Two-step write scheme for reducing sneak-path leakage in complementary memristor array,IEEE Transactions on Nanotechnology11(3)(2012)611–618.[48]J.J.Yang,M.-X.Zhang,M.D.Pickett,F.Miao,J.P.Strachan,W.-D.Li,W.Yi,D.A.A.Ohlberg,B.J.Choi,W.Wu,J.H.Nickel,G.Medeiros-Ribeiro,R.S.Williams,Engineering nonlinearity into memristors for passive crossbar applications,Applied Physics Letters100(11)(2012) 113501.[49]M.Qureshi,W.Yi,G.Medeiros-Ribeiro,R.Williams,AC sense tech-nique for memristor crossbar,Electronics letters48(13)(2012)757–758.[50] B.Widrow,Adaptive“adaline”neuron using chemical“memistors”,Tech.rep.,Stanford University(1960).[51]H.Kim,S.Adhikari,Memistor is not memristor,IEEE Circuits and Sys-tems Magazine12(1)(2012)75–78.。
电力职称英语试题及答案

电力职称英语试题及答案一、选择题(每题2分,共20分)1. The primary function of a transformer is to:A. Convert voltage levelsB. Amplify electrical signalsC. Rectify alternating currentD. Filter electrical noise答案:A2. In an electric power system, the term "load" refers to:A. The source of electrical powerB. The electrical equipment that consumes powerC. The transmission lines that carry powerD. The protective devices for circuits答案:B3. Which of the following is not a type of electrical fault?A. Short circuitB. OverloadC. Ground faultD. Surge protection答案:D4. The unit of electrical power is the:A. VoltB. AmpereC. WattD. Ohm答案:C5. The purpose of a circuit breaker is to:A. Provide a path for excess currentB. Maintain a constant voltage levelC. Protect the circuit from overcurrentD. Convert AC to DC答案:C二、填空题(每题1分,共10分)6. The three main components of an electric power system are the _______, transmission, and distribution.答案:generation7. The SI unit for electrical resistance is the _______.答案:ohm8. In a parallel circuit, the total resistance is always_______ than any individual resistance.答案:lower9. The process of converting mechanical energy intoelectrical energy is known as _______.答案:generation10. A fuse is a type of protective device that operates by_______ when the current exceeds a safe level.答案:melting三、简答题(每题5分,共30分)11. Explain the difference between AC and DC power systems. 答案:AC (Alternating Current) power systems use a current that regularly reverses direction, while DC (Direct Current) power systems use a current that flows in one direction only.12. What is the significance of Ohm's Law in electrical engineering?答案:Ohm's Law is fundamental in electrical engineering asit relates the voltage (V), current (I), and resistance (R) in a simple electrical circuit, expressed as V = IR, allowing for calculations of these quantities.13. Describe the role of a generator in an electric power system.答案:A generator is a device that converts mechanical energy into electrical energy, serving as the primary source of power in an electric power system.14. What are the functions of a capacitor in an electrical circuit?答案:A capacitor in an electrical circuit can store energy, filter signals, and block direct current while allowing alternating current to pass.四、计算题(每题5分,共20分)15. Calculate the total resistance in a circuit with two resistors in parallel, where R1 = 100 ohms and R2 = 200 ohms.答案:\( R_{total} = \frac{R1 \times R2}{R1 + R2} = \frac{100 \times 200}{300} = \frac{20000}{300} = 66.67 \) ohms16. If a 12-volt battery is connected to a 3-ohm resistor, what is the current flowing through the resistor?答案:\( I = \frac{V}{R} = \frac{12}{3} = 4 \) amperes17. What is the power consumed by a 5-ohm resistor with a current of 2 amperes flowing through it?答案:\( P = I^2 \times R = 2^2 \times 5 = 4 \times 5 = 20 \) watts18. If a 240-volt AC motor draws a current of 5 amperes, what is the apparent power?答案:\( S = V \times I = 240 \times 5 = 1200 \) volt-amperes五、论述题(每题10分,共20分)19. Discuss the importance of energy efficiency in power systems and how it can be achieved.答案:Energy efficiency is crucial in power systems as it reduces energy consumption, lowers operational costs, and decreases environmental impact. It can be achieved through various means such as using high-efficiency equipment, optimizing system operations, and implementing demand-side management strategies.20. Explain the concept of smart grids and their advantages over traditional power systems.答案:Smart grids are advanced power systems that use digital technology and automation to improve the efficiency, reliability, and sustainability of electricity production anddistribution. They offer numerous advantages over traditional systems, including better demand response, enhanced grid stability, and the ability to integrate renewable energy sources more effectively.。
乔布斯传读后感

2020.07.22 Book Reivew Vicky书名:Steve Jobs by Walter Isaacson (作者)阅读时间:=2020.05.26-07.06 哈哈哈,一个半月的时间才读完。
亚马逊电子图书精华帖!!!!【原文摘录】1.He was not a model boss or human being, tidily packaged for emulation.他不是一位模范老总或者模范个人,可以让人争相模范的那种。
Driven by demons, he could drive those around him to fury and despair.被恶魔驱使,他能使周围的人陷入愤怒和绝望。
But his personality and passions and products were all interrelated, just as Apple’s hardware and software tended to be, as if part of an integrated system.但是他的性格、激情和产品都是相通的,就像是苹果的软硬件相互关联,合为整体一样。
His tale is thus both instructive and cautionary, filled with lessons about innovation, character, leadership, and values.因此,关于他的人生充满了创新、性格、领导力和价值,既有教育意义,也有警示作用。
2.He was proud that his father never adopted a servile attitude or slick style that may have made him a better salesman.令他自豪的是,他的父亲没有为了成为一个更好的销售员而变得卑躬屈膝或者油腔滑调。
Digital filters

Digital filtersThese days it is increasingly common for signal processing such as digital filtering to be done by a microprocessor with appropriate software instead of an analogue electronic circuit. There are a number of reasons for this:♦analogue components are variable and their parameters tend to drift with time. A microprocessor always performs exactly the same way♦the microprocessor can be reprogrammed to incorporate new and improved features.An analogue circuit would have to be rebuilt♦many applications already have a microprocessor in them — it makes sense to minimise the analogue part of the circuit and do as much processing as possible in software♦some processing tasks cannot be done in an analogue circuitWe’ll look at a particular example of di gital signal processing — the low passfilter.Analogue approachThe classic RC filter shown in Figure 1 is an example of a low pass filter. The break frequency is 1/2πRC. Signals of frequency below this are unaffected, while signals of higher frequency are attenuated, as shown in Figure 2.R and C are chosen to give a break frequency ofSoftware approachA digital filter can achieve the same effect. We need some kind of microprocessor, anA/D converter, and a D/A converter. Many real life applications have these anyway, so there is no additional cost.It turns out that low pass filtering can be done remarkably easily. One method is to generate an output that is just a weighted sum of the input and the previous output, ie: Output = A * previous output + B * input(Proving this formula isn’t so easy.)The constants A and B are given by:RC t e A / ∆−= B = 1-Awhere ∆t is the time taken to process each sample, and R and C are the values that would have been used in the analogue circuit.We can show that this method gives similar results with a couple of spreadsheets. Suppose we apply a 1-Volt step input to both circuits. The output should start off at 0V and get closer and closer to 1V without ever getting there.In spreadsheet 1, the capacitor voltage is calculated every 1ms for an RC filter withR=10k Ωand C=1 µF. The formula required is:) ( / RC to e 1 E V −−=R = 10000C = 0.000001time (ms) Vout0 0.0001 0.0952 0.1813 0.2954 0.330(Rows missed out to save space)17 0.81718 0.83519 0.85020 0.865Spreadsheet 1 — Analogue filterIn spreadsheet 2, the output is predicted for a digital filter doing one calculation every millisecond. Constants A and B are calculated from R and C using the formulas above. R = 10000 A = 0.948374C = 0.000001 B = 0.091625time (ms) Vin Vout0 1 0.0001 1 0.0952 1 0.1813 1 0.2594 1 0.330(Row s missed out to save space)17 1 0.87718 1 0.83519 1 0.85020 1 0.865Spreadsheet 2 — Digital filterYou’ll see that both methods give results that are exactly the same. This may lead you to think that digital filters are perfect. Sadly, this isn’t the case. Firstly, t he analogue version gives an output that is continuously changing, while the digital version has an output that only changes once a millisecond in this case. (See graphs 1 and 2.) Secondly, we haven’t attempted to calculate the frequency response for the digital filter. This requires much more complex maths, and turns out to have some imperfections. Finally, if we are going to the trouble of building a circuit with a microprocessor in it, we could design a much more sophisticated filter than this.However, this example does show that digital signal processing can be used as an alternative to an analogue filter.Typical applicationTwo further applications of digital filtering are —(find examples yourself on the internet. Describe the applications in around 100–200 words each, and quote the sources and web addresses you referred to.)。
PI2211-00-QAIG;PI2211-EVAL1;中文规格书,Datasheet资料
Description:
The PI2211 hot swap controller and circuit breaker ensures safe system operation during circuit card insertion by limiting the start-up or in-rush current to the load and eliminating the electrical disturbance or possible voltage sag imposed on a backplane power supply. During steady state operation, the PI2211 acts as a circuit breaker disconnecting from the backplane power source if a overcurrent condition arises. The PI2211 uses an external N-channel MOSFET and employs the MOSFET’s transient thermal characteristics (supplied by the MOSFET supplier) to ensure operation within the MOSFET’s dynamic safe operating area (SOA). The PI2211, with True-SOA™, continuously monitors MOSFET power to calculate the MOSFET junction temperature rise and determines proper operation regardless of load conditions. The PI2211 limits the MOSFET junction temperature rise to a maximum of 60°C preventing overheating (hot spotting) by cycling the MOSFET on/off and allowing it to cool for a period determined by the programmed MOSFET package thermal properties. Emulation and protection based on the specific MOSFET’s transient thermal performance optimizes the safe operating limits and allows designers to take advantage of the latest power MOSFET technologies. During a circuit breaker fault, the PI2211 internal GlitchCatcher™ circuit acts as an active snubber, passing inductive bus energy through the MOSFET mitigating the need for additional BUS input transient protection and protects against MOSFET avalanching.
机电专业英语试题及答案

机电专业英语试题及答案一、选择题(每题2分,共10分)1. Which of the following is not a type of electrical machine?A. GeneratorB. TransformerC. PumpD. Motor答案:C2. The unit of electrical power is:A. VoltB. AmpereC. WattD. Ohm答案:C3. In an electrical circuit, what does the term "resistance" refer to?A. The ability of a material to conduct electricityB. The ability of a material to resist heatC. The ability of a material to resist electricityD. The ability of a material to resist light答案:C4. What is the function of a relay in an electrical system?A. To amplify signalsB. To switch circuits on or offC. To measure currentD. To convert AC to DC答案:B5. What does the acronym PLC stand for in industrial automation?A. Power Line CommunicationB. Personal Learning ComputerC. Programmable Logic ControllerD. Public Limited Company答案:C二、填空题(每题2分,共10分)1. The three main components of an electric motor are the stator, the rotor, and the ________.答案:bearings2. The process of converting mechanical energy intoelectrical energy is known as ________.答案:generation3. A ________ circuit is a closed loop through which electric current flows.答案:closed4. The unit of electrical resistance is the ________.答案:ohm5. In a hydraulic system, a ________ is used to convert fluid power into mechanical power.答案:actuator三、简答题(每题5分,共20分)1. Explain the difference between AC and DC current.答案:AC (Alternating Current) is an electric current whose direction and magnitude change periodically, while DC (Direct Current) is an electric current that flows in a constant direction.2. What are the main components of a typical electrical power distribution system?答案:The main components include power generation, transmission lines, substations, distribution lines, and end-user equipment.3. Describe the function of a capacitor in an electrical circuit.答案:A capacitor in an electrical circuit stores electrical energy in an electric field. It can smooth out voltage fluctuations, filter out noise, and provide a stable voltage supply.4. What are the advantages of using a programmable logic controller (PLC) in industrial automation?答案:PLCs are advantageous due to their reliability, flexibility, ease of programming, and ability to handle multiple inputs and outputs, making them ideal for complex control systems in industrial automation.四、翻译题(每题5分,共20分)1. 将下列句子翻译成英文:“电机的效率是指电机输出的机械功率与输入的电功率之比。
VQD1000-TF2Z545EN 4口气阀系列说明书
Instruction Manual 4 Port Solenoid ValveSeries VQD1000The intended use of this valve is to control the movement of an actuator.1 Safety InstructionsThese safety instructions are intended to prevent hazardous situations and/or equipment damage. These instructions indicate the level of potential hazard with the labels of “Caution,” “Warning” or “Danger.” They are all important notes for safety and must be followed in addition to International Standards (ISO/IEC) *1), and other safety regulations. *1)ISO 4414: Pneumatic fluid power - General rules relating to systems. ISO 4413: Hydraulic fluid power - General rules relating to systems.IEC 60204-1: Safety of machinery - Electrical equipment of machines. (Part 1: General requirements)ISO 10218-1: Robots and robotic devices - Safety requirements for industrial robots - Part 1: Robots.• Refer to product catalogue, Operation Manual and Handling Precautions for SMC Products for additional information. • Keep this manual in a safe place for future reference.CautionCaution indicates a hazard with a low level of risk which, if not avoided, could result in minor or moderate injury.WarningWarning indicates a hazard with a medium level of riskwhich, if not avoided, could result in death or serious injury.DangerDanger indicates a hazard with a high level of risk which, ifnot avoided, will result in death or serious injury.Warning• Always ensure compliance with relevant safety laws and standards.• All work must be carried out in a safe manner by a qualified person in compliance with applicable national regulations.• If this equipment is used in a manner not specified by the manufacturer, the protection provided by the equipment may be impaired.Caution• The product is provided for use in manufacturing industries only. Do not use in residential premises.2 Specifications2.1 Valve specifications TypeStandard single Large-flow single Large- flow latchingFluid Air Operating pressure range [MPa] 0 (Vacuum: -101.2 kPa) to 0.7 Ambient and fluid temperature [°C] -10 to 50 (no freezing) Flow characteristics Refer to catalogue Response time [ms] Refer to catalogue Duty cycle Contact SMC Min. operating frequency 1 cycle / 30 days Max. operating frequency [Hz] Contact SMC Manual override Non-locking push type Locking Lubrication Not required Impact / Vibration resistance [m/s 2]Note 1)150/30 Enclosure (based on IEC60529) IP402 Specifications - continuedMounting orientation Unrestricted WeightRefer to catalogueTable 1.Note 1) Impact resistance: No malfunction occurred when it was tested with a droptester in the axial direction and at right angles to the main valve and armature; in both energized and de-energised states and for every time in each condition. (Values at the initial period).Vibration resistance: No malfunction occurred in a one-sweep test between 45 and 2000 Hz. Tests are performed at both energized and de-energized states in the axial direction and at right angles to the main valve and armature. (Values at the initial period).2.2 Solenoid specifications Type Standard single Large-flow single Large-flowlatchingCoil rated voltage [VDC] 12, 24 24 Electrical entry L/M plug connector Coil insulation class Class B or equivalentAllowable voltage fluctuation-10% to +10% of rated voltage Power consumption [W] Note 1) 2 3.2 (Inrush) 1 (Holding)2Surge voltage suppressor Varistor Diode Varistor Indicator light LEDTable 2.Note 1) Refer to catalogue for energy saving type power waveform.2.3 Pneumatic symbolSingle type Latching typeFigure 1. Pneumatic symbol2.4 Special productsWarningSpecial products (-X) might have specifications different from those shown in this section. Contact SMC for specific drawings.3 Installation3.1 InstallationWarning• Do not install the product unless the safety instructions have been read and understood. 3.2 EnvironmentWarning• Do not use in an environment where corrosive gases, chemicals, salt water or steam are present.• Do not use in an explosive atmosphere.• Do not expose to direct sunlight. Use a suitable protective cover.• Do not install in a location subject to vibration or impact in excess of the product’s specifications .• Do not mount in a location exposed to radiant heat that would result in temperatures in excess of the product’s specifications. 3.3 PipingCaution• Before connecting piping make sure to clean up chips, cutting oil, dust etc.• When installing piping or fittings, ensure sealant material does not enter inside the port. When using seal tape, leave 1 thread exposed on the end of the pipe/fitting.• Tighten fittings to the specified tightening torque. Port Thread Tightening torque [N·m]1(P), 3(R) M5 1 to 1.5 2(B), 4(A)P(1), R(3) (Manifold)1/83 to 5Table 4.3 Installation - continued3.4 LubricationCaution• SMC products have been lubricated for life at manufacture, and do not require lubrication in service.• If a lubricant is used in the system, refer to catalogue for details. 3.5 Air supplyWarning• Use clean air. If the compressed air supply includes chemicals, synthetic materials (including organic solvents), salinity, corrosive gas etc., it can lead to damage or malfunction.Caution• Install an air filter upstream of the valve. Select an air filter with afiltration size of 5 μm or smaller. 3.6 Manual overrideWarning• Regardless of an electric signal for the valve, the manual override is used for switching the main valve. Since connected equipment will operate when the manual override is activated, confirm that conditions are safe prior to activation.• Locked manual overrides might prevent the valve responding to being electrically de-energised or cause unexpected movement in the equipment.• Refer to the catalogue for details of manual override operation. 3.7 MountingCaution• Ensure gaskets are in good condition, not deformed and are dust and debris free.• When mounting valves ensure gaskets are present, aligned and securely in place and tighten the mounting screws to a torque of 0.18 to 0.25 N∙m.• When piping and mounting valves, clamp the body part in place to avoid applying force to the coil. If you apply force over 120 N to coil, connection pins deform, which may cause malfunction. (Latching: 50N or more).Figure 2.3.8 Electrical circuitsCautionFigure 3. Single type (Standard: 2W)Figure 4. Single type (Large flow: 3.2 W)Effective energizing time for the energy saving type is between 15 to 25 ms at 24 VDC. Refer to catalogue for electrical power waveform.3 Installation - continuedFigure 5. Latching solenoid typeFigure 6. Positive commonFigure 7. Negative common3.9 Electrical connectorsCautionFigure 8. How to use plug connectorPull lead wire with gently, otherwise it may cause contact failure ordisconnection.Refer to catalogue for guidance on how to use plug connector. 3.10 Residual voltageCaution• If a varistor voltage suppressor is used, the suppressor arrests the back EMF voltage from the coil to a level in proportion to the rated voltage.• Ensure the transient voltage is within the specification of the host controller.• Contact SMC for the varistor residual voltage.• In the case of a diode, the residual voltage is approximately 1 V.• Valve response time is dependent on surge suppression method selected.ORIGINAL INSTRUCTIONSFittingCoilPin BodyLEDSOL.Red (+/-)Black (-/+)V a r i s t o rRed (+)Black (-)E n e r g y s a v i n g I CDiode SOL.SOL.LEDA (-) SetC (+) COMV a r i s t o rS i m u l t a n e o u s e n e r g i s a t i o n p r o t e c t i o n c i r c u i tB (-) ResetS i m u l t a n e o u s e n e r g i s a t i o n p r o t e c t i o n c i r c u i tS i m u l t a n e o u s e n e r g i s a t i o n p r o t e c t i o n c i r c u i tBlack (-) A-ONRed (+) COMWhite (-) B-ONRed (+) A-ONBlack (-) COMWhite (+) B-ONSOL.SOL.CoverGroove PinConnectorLeverLeverConnectorL plug connector M plug connector Base mounted Body ported Base mounted Body ported AC3 Installation - continued3.11 Countermeasure for surge voltageCaution•At times of sudden interruption of the power supply, the energy stored in a large inductive device may cause non-polar type valves in a de-energised state to switch.•When installing a breaker circuit to isolate the power, consider a valve with polarity (with polarity protection diode), or install a surge absorption diode across the output of the breaker.3.12 Extended period of continuous energizationWarning•If a valve will be continuously energized for an extended period of time, or is mounted in a control panel, the temperature of the valve will increase due to the heat generated by the coil assembly. This will likely adversely affect the performance of the valve and any nearby peripheral equipment. Therefore, if the valve is to be energized for periods of longer than 30 minutes at a time or if during the hours of operation the energized period per day is longer than the de-energized period, we advise using a direct operated continuous duty type valve such as the VK series or the VT series, or consider use of the latching type for which continuous energization is not required.•Coil temperature may get high due to ambient temperature or energizing duration. Do not touch the valve by hand directly. When there is such a dangerous case to be touched by hands directly, install a protective cover.•The latching type should not be energized over 30 seconds. Ensure the de-energised period is longer than the energised time (both A andB should be turned off.) before the next operation.3.13 Effect of back pressure when using a manifoldWarningUse caution when valves are used on a manifold, because an actuator may malfunction due to back-pressure.3.14 Latching typeCaution•Use in a circuit that does not have simultaneous energization of A-ON and B-ON signals.•The minimum energization time required for self-holding is 50 ms. •Although there is no problem for normal operations and environments. please consult SMC when operating in an environment with vibration (10G or more) or strong magnetic fields.•When there is the magnetic body at the valve side, it may cause malfunction. Allow a space over 10 mm between the valve and magnetic body.•Even though this valve is held on to B-ON position (passage: P → B), it may switch to the set position during transportation or due to impact when mounting valves, etc. Therefore, check the initial position by means of power supply or manual override prior to use.Energisation Passage Light colourA-ON (Set) A(-) C(+)Black RedP→A(B→R)RedB-ON (Reset) B(-) C(+)White RedP→B(A→R)GreenTable 5.Note) For positive common.4 How to OrderRefer to catalogue for ‘How to Order’.5 Outline DimensionsRefer to catalogue for outline dimensions.6 Maintenance6.1 General maintenanceCaution•Not following proper maintenance procedures could cause the product to malfunction and lead to equipment damage.•If handled improperly, compressed air can be dangerous. •Maintenance of pneumatic systems should be performed only by qualified personnel. 6 Maintenance - continued•Before performing maintenance, turn off the power supply and be sureto cut off the supply pressure. Confirm that the air is released toatmosphere.•After installation and maintenance, apply operating pressure andpower to the equipment and perform appropriate functional andleakage tests to make sure the equipment is installed correctly.•If any electrical connections are disturbed during maintenance, ensurethey are reconnected correctly and safety checks are carried out asrequired to ensure continued compliance with applicable nationalregulations.•Do not make any modification to the product.•Do not disassemble the product, unless required by installation ormaintenance instructions.6.2 MountingCautionRefer to 3.7 Mounting for guidance on how to mount valve to base.6.3 Maintainable partsCautionRefer to catalogue for how to order manifold accessories, sub-plates orelectrical connector assemblies.7 Limitations of Use7.1 Limited warranty and disclaimer/compliance requirementsCautionRefer to Handling Precautions for SMC Products.7.2 Effect of energy loss on valve switchingWarningSingle type Latching type Note)Air supply present,electrical supply cutValve spoolreturns to OFFposition by springforce.Valve spool holds position untilreset signal is sent (B-ON), spoolthen returns to OFF position byspring force.Electrical supplypresent, air supply cutValve operation is not dependent on presence of airsupply. Spool position/movement is unaffected byloss of air supply.Note) Refer to 3.14 and catalogue for Latching type operation guidance.7.3 Holding of pressureWarningSince valves are subject to air leakage, they cannot be used forapplications such as holding pressure (including vacuum) in a system.7.4 Cannot be used as an emergency shut-off valveWarningThis product is not designed for safety applications such as anemergency shut-off valve. If the valves are used in this type of system,other reliable safety assurance measures should be adopted.7.5 Leakage voltageCautionEnsure that any leakage voltage caused by the leakage current when theswitching element is OFF causes ≤ 2% of the rated voltage across thevalve.7.6 Low temperature operationCautionUnless otherwise indicated in the specifications for each valve, operationis possible to -10˚C, but appropriate measures should be taken to avoidsolidification or freezing of drainage and moisture, etc.7 Limitations of Use - continued7.7 Vacuum applications and use as a 3 port valve.Caution•Use a VQD(1/2)(2/3/5)1(V/W) valve for vacuum applications.•Connect the vacuum source to the 3(R) port.•Refer to catalogue for diagram.•Air pressure cannot be applied to the 3(R) port.•When used as a 3 port valve, conversion from N.O. to N.C. and viceversa is possible by plugging either port 4(A) or 2(B).•The valve cannot be used as a 2 port valve.8 Product DisposalThis product shall not be disposed of as municipal waste. Check yourlocal regulations and guidelines to dispose this product correctly, in orderto reduce the impact on human health and the environment.9 ContactsRefer to or www.smc.eu for your localdistributor/importer.URL : https:// (Global) https:// www.smc.eu (Europe)SMC Corporation, 4-14-1, Sotokanda, Chiyoda-ku, Tokyo 101-0021, JapanSpecifications are subject to change without prior notice from the manufacturer.© 2022SMC Corporation All Rights Reserved.Template DKP50047-F-085M。
数字集成电路--电路、系统与设计(第二版)课后练习题 第六章 CMOS组合逻辑门的设计-Chapter 6 Designing
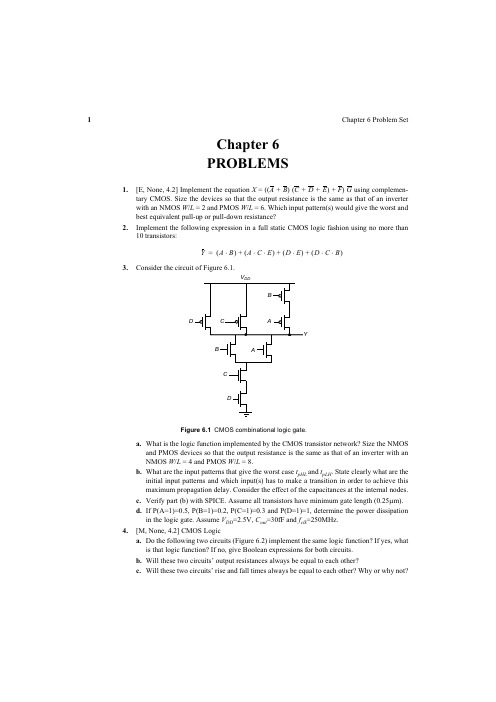
4
Chapter 6 Problem Set
VDD F G
A B
A
A B
A
Figure 6.6 Two-input complex logic gate.
11.
Design and simulate a circuit that generates an optimal differential signal as shown in Figure 6.7. Make sure the rise and fall times are equal.
2
VDD E 6 A A 6 B 6 C 6 D 6 F A B C D 4 4 4 4 E 1 A B C D E 4 4 4 4 E 1 6 F 6 B 6 C 6 D
Chapter 6 Problem SetVDD 6Circ来自it ACircuit B
Figure 6.2 Two static CMOS gates.
Digital Integrated Circuits - 2nd Ed
3
2.5 V
PMOS
M2 W/L = 0.5μm/0.25μm Vout Vin M1 W/L = 4μm/0.25μm NMOS Figure 6.4 Pseudo-NMOS inverter.
a. What is the output voltage if only one input is high? If all four inputs are high? b. What is the average static power consumption if, at any time, each input turns on with an (independent) probability of 0.5? 0.1? c. Compare your analytically obtained results to a SPICE simulation.
Tube-Tech CL 1B压力器说明书

TUBE-TECH CL1BCompressorDESCRIPTION.The TUBE-TECH compressor CL1B differs from many other compressors,in that the gain-reduction element is made from a non-semiconductor element,which in itself has a very low harmonic distortion and none of the non-linearity problems involved when using most semiconductor elements.Furthermore there is no long-term degradation of the element thus giving it almost infinite life.This element is placed after the input-transformer of the compressor and followed by an all tube-based amplifier with a gain of-∞dB to+30dB.Thus the signal is not fed through any semiconductor circuitry on its way to the output.The amplifier consists of two tubes(valves)in push-pull configuration(one ECC83as thepre-amp and phase splitter,and one ECC82as the output stage),and an output transformer. The power supply for the pre-amp and phase splitter are stabilized and the heaters of both tubes(valves)are fed with a stabilized DC voltage.The whole amplifier(including input and output transformer)and the power supplies are placed on one PC-board.Both input and output are balanced(600Ω)and fully floating.The in/out key switches the compressor in and out without clicks.THE SIDECHAIN:The side chain is the only part of the compressor that contains semiconductors.They are used for three reasons:First they do not affect the sound reproduction,second they have a high slew rate,which is of importance for the performance of the compressor and third they don't take up much room.It contains two J-FET quad op-amps,one npn-transistor and one FET-transistor,which handles the signal for the gain-reduction element.The compressor contains two time constants circuits:1.Fixed attack and release times2.Variable attack and release timesThe attack/release select switch makes it possible to use these two circuits separately or combine their functions.This gives a feature not normally obtained in other compressors:In the combined(fix./man.)state the attack-and release controls makes it possible toobtain a complex release-time slope.(See page4)(980112)COMPRESSOR INTERCONNECTION:The side chain sockets for interconnection of several compressors are located on the rear panel.A switch(BUS SELECT)on the front selects which compressors are interconnected,and on which bus they are connected.If you e.g.have10compressors in a rack,you can select compressor1,5,7and8on bus1,and compressor2,3,6and9on bus2,leaving compressor4 and6in the off position.Compressors1,5,7,8are now interconnected and all four will perform the exact same compression.This applies to compressor2,3,6and9as pressor4and6are independent.The interconnection implies,that the unit,which performs the most compression,is controlling the others.To choose which one you want to control,select the attack/release time,the threshold and the ratio on that unit,and turn the threshold fully counter clockwise on the reminding compressors. It is of course possible to have all the interconnected compressors control each other simultaneously.NB:Remember to set the ratio control and the gain control in the same position on the "slaves".Otherwise the stereo image could be shifted during compression.Theattack/release-control on the slaves will have no effect.The input/output capability of the side chain-circuit allows up to ten compressors to be linked together.They are connected in parallel with a standard1/4"stereo jack/-jack cord(tip:bus1,ring:bus 2).The two jack socket on the rear panel is connected in parallel and both are input/output.(980112)CONTROLS:GAIN:The gain control is used to"make up"for the gain loss,which takes place when the unit is compressing.It is placed after the gain-reduction circuitand therefore has no influence on the threshold setting.The gain-control iscontinuously variable from off to+30dB.RATIO:The ratio control varies the ratio by which the input signal is compressed.If the ratio selected is to2:1,and the input signal increases10dB,theoutput signal is only increased by5db.The ratio control is continuouslyvariable from2:1to10:1.THRESHOLD:The threshold is the point where the compressor begins its action.It isdefined as the point where the gain is reduced by1dB.The threshold is continuously variable from+20dBU to-40dBU. METER:The VU-meter switch has three positions:1.Input The meter is reading the level at the input socket.pressionThe VU-meter is reading gain reduction.Its rest position is"0VU",and the amount ofcompression is shown as a decreasing deflection indB.3.Output The VU-meter is reading the level at the output socket."0VU"is equivalent to+4dBU.NB:Leave the meter switch in position compression as it mightintroduce distortion if left in the input or output position.IN/OUT:This leverswitch switches the compressor in and out of the signal path.The out position bypasses the entire compressor.ATTACK:The attack control chooses how fast/slow the compressor responds to an increase in the input signal.The attack control is continuously variable from0.5to300milliseconds. RELEASE:The release control chooses how fast/slow the compressor responds to a decrease in the input signal.The release control is continuously variable from0,05to10seconds.(980112)ATTACK/RELEASE SELECT:This switch selects how the compressor reacts to an increase(attack)ordecrease(release)of the input signal.There are three settings of the switch:1.Fixed.Attack time:1msecRelease time:50msec2.Manual.Attack time:from0.5msec to300msecRelease time:from0.05sec to10sec3.Fix/man.This setting combines the release times of fixed and manualmode.The attack time is as in the fixed mode.The fix/man mode always has a fast attack,but it is possible to obtain a release time depending on the input signal,e.g.get a fast release when the peak disappears,then superseded shortly thereafter by the release time selected by the release control.From the time the peak disappears,until the selected release time takes over,is dependent upon the setting of the attack control.That is,the attack control changes function from a pure attack control,to a control of delay with the same time range.The more CW the attack control is turned,the longer time before the release controltakes over.The more CCW the attack control is turned,the shorter time before the release control takes over.This function is valid only if the time of the peak is shorter than the setting of the attack control. If the peak of the program is longer than the setting of the attack control,or if the attack control has reached the full CCW position,it will respond as in the manual mode.The fix/man mode acts as an automatic release function with a constant fast attack time and fast release time for short peaks and a longer release times for longer peaks.This setting is mainly intended for use on program material(overall compression).BUS SELECT:Interconnects several compressors on bus1or bus2.If the compressor is left in the off position,it works entirely independently.(980112)SUGGESTED APPLICATIONSOFTUBE-TECH COMPRESSOR CL1BIn the following,you will find suggestions on various applications of the TUBE-TECH compressorCL1B.They are given as a convenient guide to enable you to familiarise yourself with the different aspects of using the compressor.We have not mentioned specific settings of gain and threshold as they are dependent upon input levels.Instead we have specified how much compression in dB,we feel,is needed for the various examples.OVERALL COMPRESSION:FINAL MIXCOMPRESSION NEEDED:3-4dBAttack/release select:Fix/manAttack:2o'clockRelease:10o'clockRatio:9o'clockSTANDARD COMPRESSION:BASS,PIANO,GUITAR,KEYBOARDS AND VOCALSCOMPRESSION NEEDED:4-5dBAttack/release select:ManualAttack:2o'clockRelease:10o'clockRatio:10-2o'clockHEAVY COMPRESSION ON INSTRUMENTS:LINE GUITAR AND PIANOCOMPRESSION NEEDED:10dBAttack/release select:ManualAttack:7o'clockRelease:1o'clockRatio:3o'clockCOMPRESSION OF DRUMS:SNARE AND BASS DRUMCOMPRESSION NEEDED:2-3dBAttack/release select:FixedRatio:9-12o'clock(980112)ADJUSTMENT PROCEDURE:CAUTION:Before making any adjustment let the unit heat-up at least15min.Observe that the offset-voltage measured at the side chain jack socket,when the THRESHOLD is off,is not greater than+/-15mV DC in both position"fixed"and "manual".(tip is bus1and ring is bus2).If the voltage exceeds this value,replace either IC1or IC2.THE GRE SHALL BE MARKED BETWEEN1.225-1.285ADJUSTMENT OF BASIC GAIN:1)Apply a signal of1kHz,-30,0dBU into the input of the compressor.2)Turn the GAIN-control fully clockwise.3)Set the RATIO-control at2:14)Adjust the pre-set GAIN(located on amp/psu PCB)to an output-reading of0,0dBU.ADJUSTMENT OF COMPRESSION TRACKING:1)Turn the THRESHOLD-control fully counter-clockwise.2)Set the RATIO-control at2:1.3)Set the BUS-select-switch at1.4)Apply a signal of1kHz,0,0dBU into the input of the compressor.5)Adjust the GAIN-control to an output-reading of0,0dBU.6)Apply a DC-voltage of+250,0mV into the side chain jack socket(tip)and observe thatthe output level has dropped to-10,0dB.7)If this is not the case,adjust the level with P2(P1)*,to obtain a drop of exactly-10,0dB. *The trimpots in parenthesis refers to PCB870316-0,1,2(980810)ADJUSTMENT OF THE VU METER READING"COMPRESSION":1)Turn the THRESHOLD-control fully counter-clockwise.2)Switch the METER-selector to Compression.3)Set the RATIO-control at2:14)Apply a signal of1kHz,0,0dBU into the input of the compressor.5)Adjust the GAIN-control to an output-reading of0,0dBU.6)Adjust P4(P2)*until the meter is reading0VU.7)Apply a DC-voltage of+250,0mV into the side chain jack socket and observe that theoutput level has dropped to-10,0dBU.If this is not the case,adjust the compressiontracking(see above)8Adjust P3until the meter is reading-10,0VU.9)Remove the DC-voltage from the side chain jack socket.10)Repeat step6-9.NB:The VU-meter accuracy should be within+/-0,5dB when reading compression. ADJUSTMENT OF THE RELEASE CONTROL:1)Set the METER switch in position compression.2)Set the attack/release SELECT switch in position manual.3)Apply a signal of1kHz,0,0dBU into the input of the compressor.4)Adjust the THRESHOLD-control to a reading of-10VU of the VU-meter5)Set the ATTACK-control at fast.6)Set the RELEASE-control at slow.7)Switch off the1kHz and observe that the VU meter moves to0VU in approx.10sec.8)If this is not the case,adjust P1(P5)*,to obtain a release time of approximately10sec. *The trimpots in parenthesis refers to PCB870316-0,1,2(950119)Over view of the sidechain PCBPCB870316-0,1,2P2P3P1P50VU-10VU-10dB Rel.10Sec.PCB870316-3P4P3P2P10VU-10VU-10dB Rel10Sec.101115TECHNICAL SPECIFICATIONS CL1B:Input impedance:600OhmsOutput impedance:<60OhmsFrequency-response:5Hz-25kHz+0.5/-3dB Distortion THD@40Hz:0dBU:<0,15%10dBU:<0,15%maximum output(1%THD):+26,0dBUmaximum input(1%THD):+21,0dBUNoise Rg=200Ohm:Output Gain0dB+30dB Unweighted-85,0dBU-75,0dBUCCIR468-3-75,0dBU-65,0dBUCMRR@10KHz<-60dBGain:off to+30dBCompressorRatio:2:1to10:1Threshold:off to-40dBUAttack:0,5mS to300mSRelease:0,05S to10STracking between interconnected compressors:(0to30dB compression):<+/-1dBTubesECC821ECC831DimensionsHeight:3units132m m/5,2”Width:483m m/19”Depth:170m m/6,7”WeightNet:4,1Kg/9,0lbsShipping:5,9Kg/13,0lbsPower requirements@115V/230V AC,50-60Hz30-40WAll specifications at RL=600Lydkraft reserves the right to alter specifications without prior notice(051018jgp)。
电力系统潮流计算软件设计外文原文及中文翻译

电力系统潮流计算软件设计外文原文及中文翻译外文原文及中文翻译Modelling and Analysis of Electric Power SystemsPower Flow Analysis Fault AnalysisPower Systems Dynamics and StabilityPrefaceIn the lectures three main topics are covered,i.e.Power flow an analysisFault current calculationsPower systems dynamics and stabilityIn Part I of these notes the two first items are covered,while Part II givesAn introduction to dynamics and stability in power systems. In appendices brief overviews of phase-shifting transformers and power system protections are given.The notes start with a derivation and discussion of the models of the most common power system components to be used in the power flow analysis.A derivation of the power ?ow equations based on physical considerations is then given.The resulting non-linear equations are for realistic power systems of very large dimension and they have to be solved numerically.The most commonly used techniques for solving these equations are reviewed.The role of power flow analysis in power system planning,operation,and analysis is discussed.The next topic covered in these lecture notes is fault current calculations in power systems.A systematic approach to calculate fault currents in meshed,large power systems will be derived.The needed models will be given and the assumptions made when formulating these models discussed.It will be demonstrated thatalgebraic models can be used to calculate the dimensioning fault currents in a power system,and the mathematical analysis has similarities with the power ?ow analysis,soitis natural to put these two items in Part I of the notes.In Part II the dynamic behaviour of the power system during and after disturbances(faults) will be studied.The concept of power system stability isde?ned,and different types of pow er system in stabilities are discussed.While the phenomena in Part I could be studied by algebraic equations,the description of the power system dynamics requires models based on differential equations.These lecture notes provide only a basic introduction to the topics above.To facilitate for readers who want to get a deeper knowledge of and insight into these problems,bibliographies are given in the text.Part IStatic Analysis1 IntroductionThis chapter gives a motivation why an algebraic model can be used to de scribe the power system in steady state.It is also motivated why an algebraic approach can be used to calculate fault currents in a power system.A power system is predominantly in steady state operation or in a state that could with sufficient accuracy be regarded as steady state.In a power system there are always small load changes,switching actions,and other transients occurring so that in a strict mathematical sense most of the variables are varying with thetime.However,these variations are most of the time so small that an algebraic,i.e.not time varying model of the power systemis justified.A short circuit in a power system is clearly not a steady state condition.Such an event can start a variety of different dynamic phenomena in the system,and to study these dynamic models are needed.However,when it comes to calculate the fault current sin the system,steady state(static) model swith appropriate parameter values can be used.A fault current consists of two components,a transient part,and a steady state part,but since the transient part can be estimated from the steady state one,fault current analysis is commonly restricted to the calculation of the steady state fault currents.1.1 Power Flow AnalysisIt is of utmost importance to be able to calculate the voltages and currents that different parts of the power system are exposed to.This is essential not only in order to design the different power system components such asgenerators,lines,transformers,shunt elements,etc.so that these can withstand the stresses they are exposed to during steady state operation without any risk of damages.Furthermore,for an economical operation of the system the losses should be kept at a low value taking various constraint into account,and the risk that the system enters into unstable modes of operation must be supervised.In order to do this in a satisfactory way the state of the system,i.e.all(complex) voltages of all nodes in the system,must be known.With these known,all currents,and hence all active and reactive power flows can be calculated,and other relevant quantities can be calculated in the system.Generally the power ?ow,or load ?ow,problem is formulated as a nonlinear set of equationsf (x, u, p)=0(1.1)wheref is an n-dimensional(non-linear)functionx is an n-dimensional vector containing the state variables,or states,ascomponents.These are the unknown voltage magnitudes and voltage angles of nodes in the systemu is a vector with(known) control outputs,e.g.voltages at generators with voltage controlp is a vector with the parameters of the network components,e.g.line reactances and resistancesThe power flow problem consists in formulating the equations f in eq.(1.1) and then solving these with respect to x.This will be the subject dealt with in the first part of these lectures.A necessary condition for eq.(1.1) to have a physically meaningful solution is that f and x have the same dimension,i.e.that we have the same number of unknowns as equations.But in the general case there is no unique solution,and there are also cases when no solution exists.If the states x are known,all other system quantities of interest can be calculated from these and the known quantities,i.e. u and p.System quantities of interest are active and reactive power flows through lines and transformers,reactive power generation from synchronous machines,active and reactive power consumption by voltage dependent loads, etc.As mentioned above,the functions f are non-linear,which makes the equations harder to solve.For the solution of the equations,the linearizationy X Xf ?= (1.2)is quite often used and solved.These equations give also very useful information about the system.The Jacobian matrix Xf ?? whose elements are given by j iij X f X f ??=??)((1.3)can be used form any useful computations,and it is an important indicator of the system conditions.This will also be elaborate on.1.2 Fault Current AnalysisIn the lectures Elektrische Energiesysteme it was studied how to calculate fault currents,e.g.short circuit currents,for simple systems.This analysis will now be extended to deal with realistic systems including several generators,lines,loads,and other system components.Generators(synchronous machines) are important system components when calculating fault currents and their model will be elaborated on and discussed.1.3 LiteratureThe material presented in these lectures constitutes only an introduction to thesubject.Further studies can be recommended in the following text books:1. Power Systems Analysis,second edition,by Artur R.Bergen and VijayVittal.(Prentice Hall Inc.,2000,ISBN0-13-691990-1,619pages)2. Computational Methods for Large Sparse Power Systems,An object oriented approach,by S.A.Soma,S.A.Khaparde,Shubba Pandit(Kluwer Academic Publishers, 2002, ISBN0-7923-7591-2, 333pages)2 Net work ModelsIn this chapter models of the most common net work elements suitable for power flow analysis are derived.These models will be used in the subsequent chapters when formulating the power flow problem.All analysis in the engineering sciences starts with the formulation of appropriate models.A model,and in power system analysis we almost invariably then mean a mathematical model,is a set of equations or relations,which appropriately describes the interactions between different quantities in the time frame studied and with the desired accuracy of a physical or engineered component or system.Hence,depending on the purpose of the analysis different models of the same physical system or components might be valid.It is recalled that the general model of a transmission line was given by the telegraph equation,which is a partial differential equation, and by assuming stationary sinusoidal conditions the long line equations, ordinary differential equations,were obtained.By solving these equations and restricting the interest to the conditions at the ends of the lines,the lumped-circuit line models (π-models) were obtained,which is an algebraic model.This gives us three different models each valid for different purposes.In principle,the complete telegraph equations could be used when studying the steady state conditions at the network nodes.The solution would then include the initial switching transients along the lines,and the steady state solution would then be the solution after the transients have decayed. However, such a solution would contain a lot more information than wanted and,furthermore,it would require a lot of computational effort.An algebraic formulation with the lumped-circuit line model would give the same result with a much simpler model ata lower computational cost.In the above example it is quite obvious which model is the appropriate one,but in many engineering studies these lection of the“correct”model is often the most difficult part of the study.It is good engineering practice to use as simple models as possible, but of course not too simple.If too complicated models are used, the analysis and computations would be unnecessarily cumbersome.Furthermore,generally more complicated models need more parameters for their definition,and to get reliable values of these requires often extensive work.i i+diu+du C ’dx G ’dxR ’dx L ’dx u dxFigure2.1. Equivalent circuit of a line element of length dx In the subsequent sections algebraic models of the most common power system components suitable for power flow calculations will be derived.If not explicitly stated,symmetrical three-phase conditions are assumed in the following.2.1 Lines and CablesThe equ ivalent π-model of a transmission line section was derived in the lectures Elektrische Energie System, 35-505.The general distributed model is characterized by the series parametersR′=series resistance/km per phase(?/km)X′=series reactance/km per phase(?/km)and the shunt parametersB′=shunt susceptance/km per phase(siemens/km)G′=shunt conductance/km per phase(siemens/km )As depicted in Figure2.1.The parameters above are specific for the line or cable configuration and are dependent onconductors and geometrical arrangements.From the circuit in Figure2.1the telegraph equation is derived,and from this the lumped-circuit line model for symmetrical steady state conditions,Figure2.2.This model is frequently referred to as the π-model,and it is characterized by the parameters)(Ω=+=impedance series jX R km km km Z )(siemens admittance shuntjB G Y sh km sh km sh km =+= I mk Z km y sh km y sh mkI kmkmFigure2.2. Lumped-circuit model(π-model)of a transmission line betweennodes k and m.Note. In the following most analysis will be made in the p.u.system.Forimpedances and admittances,capital letters indicate that the quantity is expressed in ohms or siemens,and lower case letters that they are expressed in p.u.Note.In these lecture notes complex quantities are not explicitly marked asunder lined.This means that instead of writing km Z we will write km Z when this quantity is complex. However,it should be clear from the context if a quantity is real or complex.Furthermore,we will not always use specific type settings for vectors.Quite often vectors will be denoted by bold face type setting,but not always.It should also be clear from the context if a quantity is a vector or a scalar.When formulating the net work equations the nodeadmittance matrix will be used and the series admittance of the line model is neededkm km 1-km km jb g z y +== (2.1)With22km r g km km kmx r +=(2.2)and 22km x -b km km kmx r += (2.3)For actual transmission lines the series reactance km x and the series resistance km r are both positive,and consequently km g is positive and km b is negative.The shunt susceptance sh y km and the shunt conductance sh g km are both positive for real line sections.In many cases the value of sh g km is so small that it could be neglected.The complex currents km I and mk I in Figure2.2 can be expressed as functions of the complex voltages at the branch terminal nodes k and m:k sh km m k km km E y E E y I +-=)( (2.4)m k m mk )(E y E E y I sh km km +-=(2.5)Where the complex voltages arek j k k e θU E = (2.6)k j k k e θU E =(2.7) This can also be written in matrix form as))(()(m k sh km km km km sh km km mk km E E y y y -y -y y I I ++=(2.8) As seen the matrix on the right hand side of eq.(2.8)is symmetric and thediagonal elements are equal.This reflects that the lines andcables are symmetrical elements.2.2 TransformersWe will start with a simplified model of a transformer where we neglect the magnetizing current and the no-load losses .In this case the transformer can be modelled by an ideal transformer with turns ratio km t in series with a series impedance km z which represents resistive(load-dependent)losses and the leakage reactance,see Figure2.3.Depending on if km t is real ornon-real(complex)the transformer is in-phase or phase-shifting.p k mU m ej θm I km I mkU kej θk U p e j θp Z km 1:t km p k mU m ej θm I km I mkU kej θk U p e j θp Z km t km :1Figure2.3. Transformer model with complex ratio kmj km km e a t ?=(km -j 1-km km e a t ?=) mp k U m ej θm I km I mk U kej θk U p e j θp Z km a km :1Figure2.4. In-phase transformer model 2.2.1In-Phase TransformersFigure2.4shows an in-phase transformer model indicating the voltage at the internal –non-physical –node p.In this model the ideal voltage magnitude ratio(turns ratio)iskm k p(2.9) Since θk = θp ,this is also the ratio between the complex voltages at nodes k and p, km j k j p k pa e U e U E E k p ==θθ(2.10)There are no power losses(neither active nor reactive)in the idealtransformer(the k-p part of the model),which yields0I E I E *mk p *km k =+(2.11) Then applying eqs.(2.9)and(2.10)giveskm mk km mk km -a I I -I I ==(2.12)A B Ck m I mk I kmFigure2.5. Equivalent π-model for in-phase transformerwhich means that the complex currents km I and mk I are out of phase by 180since km a ∈ R.Figure2.5 represents the equivalent π-model for thein-phase transformer in Figure2.4.Parameters A, B,and C of this model can be obtained by identifying the coefficients of the expressions for the complex currents km I and mk I associated with the models of Figures2.4 and 2.5.Figure2.4 givesm km km k km 2km p m km km km E y a E y a E -E y -a I )()()(+==(2.13)m km k km km p m km mk E y E y a -E -E y I )()()(+== (2.14)or in matrix form ))(()(m k km km km km km km2km mk km E E y y a -y a -y a I I =As seen the matrix on the right hand side of eq.(2.15) is symmetric,but thediagonal elements are not equal when 1a 2km ≠.Figure2.5 provides now the following:m k km E A -E A -I )()(+=(2.16)m k mk E C A E A -I )()(++=(2.17)or in matrix form))(()(m k mk km E E C A A -A -B A I I ++= (2.18)Identifying the matrix elements from the matrices in eqs.(2.15) and (2.18) yieldskm km y a A = (2.19)km km km y 1-a a B )(= (2.20)km km )y a -(1C =(2.21) 2.2.2 Phase-Shifting TransformersPhase-shifting transformers,such as the one represented in Figure2.6,are used to control active power flows;the control variable is the phase angle and the controlled quantity can be,among other possibilities,the active power flow in the branch where the shifter is placed.In Appendix A the physical design of phase-shifting transformer is described. A phase-shifting transformer affects both the phase and magnitude of the complex voltages k E and p E ,without changing their ratio,i.e., km j km km k p e a t E E ?== (2.22)Thus, km k p ?θθ+=and k km p U a U =,using eqs. (2.11) and (2.22)km j -km *km mkkm e -a -t I I ?==I km m U m ej θm I mk pkU k ej θk Z km 1:a kme j φkmkm k p ?θθ+=k km p U a U = Figure2.6. Phase-shifting transformer with km j km km e a t ?=As with in-phase transformers,the complex currentskm I and mk I can be expressed in terms of complex voltages at the phase-shifting transformer terminals:m km *km k km 2km p m km *km km E y t -E y a E -E y -t I )()()(+== (2.24)m km k km km p m km mk E y E y t -E -E y I )()()(+==(2.25)Or in matrix form))(()(m k km km km km *km km 2km mk km E E y y t -y t -y a I I =(2.26) As seen this matrix is not symmetric if km t is non-real,and the diagonal matrixelements are not equal if 1a 2km ≠.There is no way to determine parameters A, B,and Cof the equivalent π-model from these equations,since the coefficient km *km y t - ofEm in eq.(2.24)differs from km km y t -in eq.(2.25),as long as there is non zero phase shift,i.e. km t ?R.A phase-shifting transformer can thus not be represented by a π-model.2.2.3Unified Branch ModelThe expressions for the complex currents km I and mk I for both transformersand shifters derived above depend on the side where the tap is located;i.e., they are not symmetrical.It is how ever possible to develop unified complex expressions which can be used for lines,transformers,and phase-shifters, regardless of the side on which the tap is located(or even in the case when there are taps on both sides of thedevice).Consider initially the model in Figure2.8 in which shunt elements have beentemporarily ignored and km j km km e a t ?= and m k j mk mk e a t ?=。
理性使用数字技术作文

理性使用数字技术作文英文回答:The advent of digital technologies has revolutionized our lives, providing us with unprecedented access to information, communication, and entertainment. While these technologies offer numerous benefits, it is crucial to use them rationally to maximize their positive impact and minimize potential risks.First and foremost, it is important to approach digital technologies with a critical mindset. We must be mindful of the information we consume and the sources from which it comes. With the proliferation of fake news and misinformation, it is more important than ever to verify information before sharing or believing it. This involves checking multiple sources, considering the credibility of authors, and being aware of our own biases.Furthermore, we should be mindful of the amount of timewe spend using digital devices. Excessive screen time can lead to a variety of health issues, including eye strain, sleep problems, and social isolation. It is essential to set limits on our digital usage and make sure to engage in other activities that promote our physical and mental well-being.Another important aspect of rational digital use is protecting our privacy and personal data. Digital technologies collect vast amounts of information about our online activities, which can be used for various purposes, including targeted advertising, surveillance, and even discrimination. We should take steps to protect our privacy by using strong passwords, being cautious about the information we share online, and using privacy-enhancing tools.In the workplace, it is essential to use digital technologies effectively and efficiently. This involves understanding the capabilities of various tools and software, as well as managing our time wisely to avoid burnout. It is also important to maintain a healthy work-life balance and avoid excessive use of digitaltechnologies outside of work hours.Finally, we must consider the ethical implications of digital technologies. These technologies have the potential to be used for both good and evil, and it is up to us to ensure that they are used in a responsible and ethical manner. This includes using digital technologies to promote social justice, fight discrimination, and address environmental challenges.中文回答:理性使用数字技术。
Narda Remote Spectrum Analyzer和IDA Series技术指南说明书

TN_IDA_1068_E_IQ data 1 / 8 Subject to changeFigure 1: Basic setup for a communications system See last page for abbreviationsCommunicationschannel Modulator DemodulatorTransmitterReceiverCapturing IQ data with NRA and IDAA brief theoretical outline with practical examplesWith the Scope/IQ option, the NRA and IDA instruments allow you to generate IQ data from the received data and display, demodulate, and store them, and transmit them block by block or as a continuous stream via a remote interface. What, though, is the significance of this I/Q data? What are they used for? And, how are they obtained using NRA and IDA?Communications systemsTo transmit data wirelessly it must be modulated onto a suitable, usually high frequency, carrier signal. This gives a basic setup as shown in figure 1. The demodulator must perform exactly the opposite function to the modulator. The receiver must also be able to cope with the impairments to the modulated signal that are added as it passes through the communications channel.The type of modulation has to be suitable for the signal content and the communications channel. Various techniques are used to transmit different signals together through the same medium and then separate them again, e.g.:▪ Frequency multiplex,▪ Time multiplex and / or▪Code multiplexThe following types of modulation are commonly used for sinusoidal carriers: ▪ AM, FM, PM, (angle modulation) for analog signals ▪ASK, FSK, PSK, APSK, QAM for digital signalsIf a prominent but unknown signal in the spectrum is to be classified or even its message content reconstructed, various parameters such as1981TN_IDA_1068_E_IQ_data 2 / 8 Subject to changeFigure 3: Basic representation of an IQ based communications installation Figure 2: Representation of an IQ data pair in thecomplex planeQ(I, Q) M φIIQ modulator Communications- IQ demodulator channelcos(ωτt + φτ) cos(ωνt + φν)Modulator Demodulator-sin(ωτt + φτ) -sin(ωνt + φν)Complex base band signal Real Complex base band signal band pass signalTransmitter Receiverthe type of modulation need to be determined before a matching receiver can be produced for the unknown transmitter. This is not possible “on the fly”, so the NRA and IDA provide facilities for recording the unknown signal in the form of IQ data so that it can subsequently be subjected to a more precise investigation.IQ dataGenerally speaking, the IQ data consists of pairs of data describing an instantaneous time signal in the complex plane, as shown in figure 2.“I” stands for the in phase component, which has a phase angle of 0°relative to the converted carrier, and which therefore forms the real component in the complex plane. In contrast, “Q” is the quadrature component, which is phase shifted by 90° relative to the carrier, thus forming the imaginary component.The values for an IQ data pair describe the instantaneous amplitude M and the phase angle φ of a signal. Changes in the time signal are reflected as a shift in the IQ data point in the complex plane.TN_IDA_1068_E_IQ_data 3 / 8 Subject to changeFigure 4: Spectrum and IQ data.– Top: The entire spectrum,– Center: Spectrum of signal converted to the baseband,– Bottom: A time section of the signal converted to thebase band expressed as IQ data.PSignal under considerationf ν fP0 fBase band Time 'I' 'Q'0.00E+000.00208341 -0.00078946 5.00E-08 0.00243203 -0.00051186 1.00E-07 0.00280739 -0.0002444 1.50E-07 0.00316431 2.40E-05 2.00E-07 0.00353968 0.00029236 2.50E-07 0.00384864 0.000530313.00E-07 0.00414745 0.000764563.50E-07 0.00442414 0.000975764.00E-07 0.00461874 0.001151 4.50E-07 0.00479581 0.001281045.00E-07 0.00490279 0.00140462 5.50E-07 0.00493231 0.001462726.00E-07 0.00490372 0.001510686.50E-07 0.0048161 0.00151898The IQ data find application in the transmitters and receivers in communications installations. They are also suitable for recording signals from the communications channel itself.From the point of view of a basic communications installation – as depicted in figure 3 – the IQ data appear before conversion from the base band into the actual transmission band in the transmitter and after conversion from the transmission band to the base band in the receiver.The payload signal or data stream is fed to the IQ modulator in thetransmitter in the form of IQ data. The IQ modulator limits the bandwidth of the signal and converts it into the transmission frequency band. After addition of the I and Q components, the real, band-limited signal can be transmitted in a radio channel.The received signal together with any captured interference is converted back to the base band again and band limited by the IQ demodulator inthe receiver, so that the original payload signal or data stream together with the interference is available at the output of the IQ demodulator as IQ data.The signal can be captured by the NRA and IDA during transmissionover the radio channel. In this case, the instrument takes over the role ofa receiver that can store IQ data. The IQ data represent a specificsection of the spectrum in the time domain shifted into the base band,as depicted clearly in figure 4.Signals that have known modulation, such as AM or FM, can often be directly demodulated by the IDA and output to a loudspeaker orheadphones. Experts can discern other types of modulation by thesound after AM or FM demodulation.The IDA can also demodulate a UMTS or LTE signal and determinecertain parameters of the transmitted signal. Things are more difficult if the modulation of the signal is unknown. The modulation type needs to be identified, and the characteristic of thematching receive filter, the exact carrier frequency, the phase, and theline digit rate all need to be determined. NRA and IDA can save the corresponding section from the spectrum in the form of IQ data for thispurpose for subsequent processing or export to another device over aninterface.TN_IDA_1068_E_IQ_data 4 / 8 Subject to changeFigure 5: Simplified block diagram of NRA and IDA for recovering the IQ data. From the A/D converter onwards, it corresponds to the receiver structure shown in figure 3Table 1: IQ data handling facilities of NRA and IDA cos(ωνt + φν)A Dcos(ω0t)-sin(ωνt + φν)Recovering the IQ data: How it is done in NRA and IDANRA and IDA combine analog and digital techniques for signal analysis: a classic heterodyne receiver for pre-selection is followed by a digital analyzer for fine selection and further processing. To help you understand IQ data recovery, the block diagram can be simplified as follows:Following pre-selection, frequency conversion, and A/D conversion, the received signal is mixed down to a base band and split into its in phase and quadrature components in the process. The subsequent filters limit the bandwidth. It should be noted here that the frequency of the IQ demodulator can only be roughly selected because the exact signal frequency is unknown; the phase is initially arbitrary. Generally, too, the selection filter does not correspond to that used in the correct receiver, as the filter parameters are also not known at this point in time. The parameter settings merely serve to allow the part of the spectrum of interest to be saved as IQ data.There are basically two modes for storing the IQ data: block mode and streaming mode.A maximum 250,000 points per block are available in block mode . The maximum bandwidth here is 32 MHz. NRA and IDA capture the datablock by block, i.e. take sections from the time signal. Time gaps in therecording thus occur between the blocks. The advantage of block modeis the high bandwidth.In streaming mode , the NRA captures the data continuously and outputs them without interruption via one of the interfaces. The maximum bandwidth is 400 kHz. The advantage of streaming mode is that the data are without time interruptions. The limitation of the bandwidth to 400 kHz is a disadvantage.D i s p l a yD e m o d u l a t eS t o r e i n t e r n a l l y / S D c a r dB l o c k m o d eS t r e a m i n g m o d eIDA • • •1) •– NRA 2)– – ••1)Export using IDA-Tools or on SD card 2)With NRA demo programTN_IDA_1068_E_IQ_data 5 / 8Subject to changeFigure 6: The signal spectrum (zoom display)Figure 7: The IQ data of the signal shown graphicallyversus timeExample 1: IQ data captured with IDAIn this example, the signal is a 16QAM signal; this is in fact not known at the start of the measurement.The signal can be seen in Spectrum mode (figure 6). The center frequency and bandwidth must be entered to tune the IDA to the signal. The center frequency, which is used to mix the signal down to the base band, does not necessarily correspond exactly to the carrier frequency, as this is not directly discernible from the signal itself. This has to be corrected later by calculation.AM or FM demodulation can be tried in order to find out more about the signal type. If this does not give a clear indication, switch from Spectrum to Scope mode using Extras > Go to. The IDA uses the same settings made in Spectrum mode for this.The Time Span and Channel Bandwidth (CBW) settings need to be made, depending on whether you want to view or store the signal. The CBW has to be set such that the Nyquist-Shannon sampling theorem is at least fulfilled if the signal is to be displayed and further processed. This means that the CBW must be at least twice the signal bandwidth. Since the selection filter of the IDA limits the signal bandwidth, it is a good idea to select a more generous CBW than this, otherwise the edges of the selection filter in the IDA (used to capture the data) and those of the actual receive filter (in the emulated receiver) will overlap in the subsequent emulation of the actual receiver.The IDA can display the IQ data directly as a graph versus time(figure 7). They can be transferred to an SD card, read out using the IDA-Tools software and exported, or accessed directly via one of the available remote interfaces for further processing using a PC.TN_IDA_1068_E_IQ_data 6 / 8 Subject to changeFigure 8: IQ data, transmitted as a block or as a streamExample 2: IQ data captured with NRAA 16QAM signal is also used here as an example of how the IQ data are captured using the NRA.Transfer of the data to a PC can be done in block mode using the “Scope-Demo” demo program or by direct access through a remote interface. The NRA sends the data over the remote interface following a request.To get started quickly, it is a good idea to use the demo programs. You can set up the NRA directly from the “Scope-Demo” program and export the IQ data blocks as .csv or .wav files. To help you get started with programming, as well as referring to the Command Reference Guide , you can activate the Communication Log, which records all the commands sent from the demo program to the NRA. Once you have set the parameters and recalled the data with the demo, you can read out the commands needed for this from the log file. Communication can then take place using these commands with a terminal program. You can then integrate the entire communication and evaluation into your own application. You can see from figure 8 that each IQ block must be requested individually by the PC in block mode.In streaming mode , the NRA communicates with the PC via a remote link and sends the IQ data as a stream over a stream link. Both links are via a single physical interface. Once started, the NRA transmits IQ data continuously over the stream link. Figure 8 shows that the PC sends commands to the NRA over the remote link and the NRA also uses this link to send responses to these commands to the PC. The NRA starts to stream the IQ data over the stream link following the Start command and continues until it receives the Stop command from the PC.Communication and evaluation of the data typically takes place directly from a client specific application.Regardless of whether block or streaming mode is used, mainstream software such as RadioInspector or the Satellite Link Planner from Inradios can be used to transfer the IQ data to the PC and evaluate them from within the software.PCUSB/LANNRABlock modePC get IQ data NRAreturn IQ block 1get IQ datareturn IQ block 2Streaming modePC start IQ stream NRA OKIQ data IQ data IQ data IQ datastop IQ stream OKRemote link Stream linkTN_IDA_1068_E_IQ_data 7 / 8 Subject to changeFigure 10: 16QAM constellation diagramFigure 9: Vector diagram after clock recovery andphase correction Example 3: Evaluation by constellation diagramThe data captured from example 1 or 2 can now be analyzed on the PC, for example by generating a constellation diagram.The sample points are shown as a vector diagram in figure 9. The values are scaled by level; the carrier frequency and phase are already recovered, which can be seen from the square appearance of the vector diagram (correct carrier frequency) which is aligned parallel to the axes (correct phase). A receive filter matching the transmit filter has been used.Despite the oversampling, which is not synchronized with the line digit rate, the aggregation at 16 points expected from a 16QAM signal can already be seen.Figure 10 shows only those values that correspond to the line digit rate and which form the constellation diagram. It should be noted that you cannot discern which of the four states (0°, 90°, 180° or 270°)corresponds to the actual phase. This information can be obtained, for example, by synchronization to IQ sequences known to the receiver that are intended for this purpose. If this information is also known, the states of the transmitted symbols can be reconstructed form the chronological sequence.SummaryThis Technical Note gives a brief overview of what IQ data are, where they find application, and how the NRA and IDA instruments can record these data. It also gives an example of how a constellation diagram can be generated from the recorded IQ data.NRA and IDA provide the functions needed for receiving and capturing IQ data.The real challenge in practical application is usually determining the type of an unknown signal source. The recorded IQ data allow com-prehensive analysis and further processing of the information at any future time.TN_IDA_1068_E_IQ_data 8 / 8 Subject to changeNarda Safety Test Solutions GmbH Sandwiesenstrasse 772793 Pfullingen, Germany Phone: +49 7121-97 32-0 Fax: +49 7121-97 32-790E-Mail:***************************www.narda-sts.de Narda Safety Test Solutions435 Moreland RoadHauppauge, NY 11788, USA Phone: +1 631 231-1700 Fax: +1 631 231-1711E-Mail:******************* Narda Safety Test Solutions Srl Via Leonardo da Vinci, 21/23 20090 Segrate (Milano) - Italy Phone: +39 02 269987 1 Fax: +39 02 269987 00E-mail:********************www.narda-sts.it© 2013 Narda Safety Test Solutions GmbH® The n ame and logo are registered trademarks of Narda Safety Test Solutions GmbH and L-3 Communications Holdings, Inc. – Trade names are the trademarks of their respective owners.AbbreviationsAM Amplitude modulation FM Frequency modulation PM Phase modulation (Frequency and phase modulation are forms of angle modulation) ASK Amplitude shift keying FSK Frequency shift keying PSK Phase shift keying APSK Asymmetric phase shift keying QAM Quadrature amplitude modulation NRA Narda Remote Spectrum Analyzer IDA Interference and Direction AnalyzerLinksNRA data sheetNRA operating manualNRA Command Reference Guide (extract)IDA data sheetIDA operating manual www.narda-sts.de。
KL2408 8通道数字输出模块说明书

Signal LED 2Signal LED 1 Output 1Output 3Output 5Output 7 KL2408 | 8-channel digital output terminal 24 V DCT he KL2408 digital output terminal connects the binary control signals from the automation unit on to the actuators at the process level with electrical isolation. It is protected against reverse polarity connection and handles load currents with outputs that are protected against overload and short-circuit. T he Bus Terminal contains eight channels which indicate their signal state by means of light emitting diodes. It is particularly suitable for space-saving use in control cabinets. The connection technology is optimised for single-ended inputs. All components have to use the same reference point as the KL2408. The power contacts are looped through. The outputs are supplied by the 24 V power contact.KL2408 | KS2408Connection technology1-wire Number of outputs8Nominal voltage24 V DC (-15 %/+20 %)Load typeohmic, inductive, lamp load Max. output current0.5 A (short-circuit proof) per channel Short-circuit current< 2 A Breaking energy< 150 mJ/channel Reverse voltage protectionyes Electrical isolation500 V (K-bus/field potential)Current consumption power contactstyp. 60 mA + load Current consumption K-bustyp. 18 mA Bit width in the process image8 outputs Configurationno address or configuration setting Weightapprox. 70 g Operating/storage temperature-25…+60 °C/-40…+85 °C Relative humidity95 %, no condensation Vibration/shock resistanceconforms to EN 60068-2-6/EN 60068-2-27EMC immunity/emissionconforms to EN 61000-6-2/EN 61000-6-4Protect. class/installation pos.IP 20/variable Pluggable wiringfor all KSxxxx Bus Terminals Approvals/markingsCE, UL, ATEX, GL, IECEx Ex-Marking II 3 G Ex nA IIC T4 Gc Ex nA IIC T4 Gc Ex tc IIIC T135 °C DcSignal LED 8Signal LED 6Signal LED 4Signal LED 7 Signal LED 5 Signal LED 3 Power contact +24 VPower contact 0 V Output 2Output 4Output 6Output 8Top view Contact assemblyKL2408BECKHOFF New Automation Technology We reserve the right to make technical changes.。
unable to converge during transient analysis

unable to converge during transient analysisThere are several reasons why a transient analysis may not converge:1. Initial conditions: The initial conditions provided for the circuit may be incorrect or impossible, leading to convergence issues. Double-check that the initial conditions are accurate.2. Time step size: The time step size chosen for the transient analysis may be too large. A large time step can cause instability in the circuit simulation and prevent convergence. Try reducing the time step size and see if convergence improves.3. Circuit complexity: Highly complex circuits with many interconnected components and nonlinear elements can be more challenging to converge during transient analysis. Simplifying or partitioning the circuit can help improve convergence.4. Incorrect component models: The models used for the circuit components may not accurately represent their behavior, leading to convergence issues. Check that you are using the correct models for all components in the circuit.5. Convergence criteria: The convergence criteria set for the transient analysis may be too strict or too lenient. Adjusting the convergence tolerance or max iteration settings may help achieve convergence.6. Initial guess: The initial guess provided for the circuit voltages and currents may be far from the final solution, causingconvergence difficulties. Providing a better initial guess can aid in achieving convergence.7. Simulator limitations: The circuit simulator being used may have limitations or known issues that can affect convergence. Check the documentation or forums for any known convergence problems with the specific simulator being used.If none of the above solutions work, it may be necessary to seek help from a simulation expert or consult the circuit simulator's support team for further assistance.。
电子阀门产品说明书

2.1 Valve Specifications((Note)Impact resistance:No malfunction when tested with a drop tester inthe axial direction and at a right angle to the mainvalve and armature, one time each in bothenergized and de-energized status. (initial value)Vibration resistance:No malfunction when tested with one sweep of 8.3to 2000Hz in the axial direction and at a right angleto the main valve and armature, one time each inboth energized and de-energized states.(initial valve)Solenoid SpecificationNote:The following voltage range must be kept for T type (with power savingcircuit) as voltage drop may occur due to the internal circuit.24VDC: -5~+10%12VDC: -6~+10%2.2 Circuit Symbolsnot switch.(Note) This circuit shows 2 position double, 3 position, 4 position dual 3-port valve(Note) This circuit shows 2 position double, 3 position, 4 position dual 3-port valveup to 9 stations. The valves are connected in order of 1 2 3 4 so thatthere will be no extra terminal.Light/surge voltage suppressorNon-polar typeWhen the solenoid valve has no polarity.With power savingPower consumption is decreased by 1/3 (SJ3!60T) by reducing the wattagerequired to hold the valve in an energized state. (Effective energizing time is over62ms at 24VDC.)How to use plug connectorsWhen attaching and detaching a connector, first shut off the electric power and the airsupply. Also, crimp the lead wires and sockets securely.1.Attaching and detaching connectorsAttachingHold the lever and connector unit between your fingers and insert straight ontothe pins of the solenoid valve so that the lever's pawl is pushed into the grooveand locks.DetachingRemove the pawl from the groove by pushing the lever downward with yourthumb, and pull the connector straight out.SJ2000-TFM84Installation and Maintenance ManualSJ2000/3000 Cassette TypeManifold Solenoid ValvesX2.Crimping of lead wires and socketsStrip 3.2 to 3.7mm at the end of the lead wires, insert the ends of the corewires evenly into the sockets, and then crimp with a crimping tool. When this is done, take care that the coverings of the lead wires do not enter the core wire crimping area.(crimping tool: model no. DXT170-75-1)3.Attaching and detaching lead wires with sockets AttachingInsert the sockets into the square holes of the connector (with (+), (-)indication), and continue to push the sockets all the way in until they lock by hooking into the seats in the connector . (When they are pushed in, their hooks open and they are locked automatically.) Then confirm that they are locked bypulling lightly on the lead wires.DetachingTo detach a socket from a connector , pull out the lead wire while pressing the socket's hook with a stick having a thin tip (about 1mm). If the socket will be used again, first spread the hook outward.CAUTION:SMC products have been lubricated for life at manufacture, and do not require lubrication in service.If a lubricant is used in the system, use turbine oil Class 1(no additive), ISO VG32.Once lubricant is used in the system, lubrication must be continued because theoriginal lubricant applied during manufacturing will be washed away.4SETTINGS AND PROGRAMMING CAUTION:Manual switch operationWhen the valve is operated manually, move the switch to the position where the letters A and B becomes visible. [Manual switch freed condition (refer to below).]If the valve is operated manually with the switch locked, the switch may break or airleakage may occur . Therefore, be sure to free the manual switch before operation.After manual operation, re-lock the switch. (The manual switch cannot be operated ifpush and turn locking slotted manual override [D type] is locked.)WARNING:Manual override operationUse extreme CAUTION when operating the manual override as connected equipmentwill commence operation. Ensure all safety measures are in place. Non locking push typePress in direction specified with an arrow.Push-turn locking slotted typePush and rotate in direction specified with an arrow (90° clockwise).If not rotated, can be used in the same way as non-locking push type.With D type, use a precision driver (flat blade) and rotate lightly. [Torque: Less than 0.1Nm] When D type is locked, be sure to push before rotating. Rotating withoutpush-ing may break manual override and cause failure such as air leakage.CAUTION:Light IndicationWhen equipped with indicator light and surge voltage suppressor , the light window turns orange when solenoid A is energized, and green when solenoid B is energized.WARNING:When the valve is turned off by operating a switch, be sure to move it to the lock position. Turning off in the improper position may cause connected equipment to start.5MAINTENANCE WARNING:Not following proper procedures could cause the product to malfunction and could lead to damage to the equipment or machine.If handled improperly, compressed air can be dangerous. Assembly, handling and repair of pneumatic system should be performed by qualified personnel only. Drain: remove condensate from the filter bowl on a regular basis.Before removing the positioner for maintenance or replacing unit parts after installation, make sure the supply pressure is shut off and all residual air pressure is released from piping.Shut-down before maintenance: before attempting any kind of maintenancemake sure the supply pressure is shut off and all residual air pressure is released from the system to be worked on.Start-up after maintenance: apply operating pressure and power to theequipment and check for proper operation and possible air leaks. If operation is abnormal, please verify product set-up parameters. Do not make any modification to the productDo not disassemble the product, unless required by installation or maintenance instructions.CAUTION:Changing the connector entry directionWhen changing the connector entry direction, move the switch on the top of theconnector block to the FREE position and then rotate the connector . Be sure to return the switch to the LOCK position before connecting the connector . (If the switch cannot be slid smoothly, move the connector slightly.)Forcible operation of the connector in the LOCK position or allowing the connector to move in the FREE position may break the connector block or lead wire respectively.CAUTION:Fitting Assembly replacementBy replacing a valve's fitting assembly, it is possible to change the connection diameter of the 4(A), 2(B), 1(P) and 3/5(E) ports.When replacing, pull out the fitting assembly after removing the clip with a flat head screwdriver . To mount a new fitting assembly, insert in place and reinsert the clip.Note 1, When changing the connection diameters for port 1(P) and 3/5(E), indicateon the manifold specification sheet.Note 2,Be careful to avoid damage or contamination of O-rings, as this can causeair leakage.Note 3,When removing a straight type fitting assembly from the valve, afterremoving the clip, connect a tube or plug (KJP-02, KQ2P-!!) to the One-touch fitting and pull it out by holding the tube (or plug).If the fitting assembly is pulled out by holding its release button (resin part),the release bushing may be damaged.Note 4,Be sure to shut off the power and air supplies before disassembly.Furthermore, since air may remain inside the actuator , piping and manifold,confirm that the air is completely exhausted before performing any work.Note 5,When inserting tubing into an elbow type fitting assembly, insert the tubingwhile holding the elbow fitting assembly body with your hand. If the tubing is inserted without holding the elbow, excessive force can be applied to the valve and fitting assembly, causing air leakage or damage.CAUTION:Plug-in manifold station expansion1.Loosen screws a fixed to DIN rail (2pcs at one side)2.Slide the valve and valve lock switch of each block to which the station is to be added in the direction toward the coil and release the linkage. (If the linkage of the blocks is released without the valve lock switch released firmly, a hook of the valve locking switch might deform or break.)3.Mount added valve or SUP ./EXH. block assembly on DIN rail.4.The valves and block assembly can be linked and remounted to the DIN railexcept for EX180 series. (In the case of EX180 series, the connector block needs to be mounted independently beforehand. After that, other valves and block assembly can be mounted linked.5.Link the valve and each block by pressing and pushing down the valve locking switch in the direction toward the cylinder port.Tighten the screws a to fix on DIN rail.6.To improve sealing performance, hold the end block by hand lightly after fixing the connector block and tighten fixing screws.Connector block assembly for D-sub and flat ribbon cable, End block assembly M3: 0.6NmConnector block assembly for serial M4: 1.4Nm 10LIMITATIONS OF USECAUTION:1.If 10 stations or less are made into 11 stations or more, add SUP ./EXH.block assembly.2.Be sure to shut off the power and air supplies before disassembly. Furthermore,since air may remain inside the actuator , piping and manifold, confirm that the air is completely exhausted before performing any work.3.When disassembly and assembly are performed, air leakage may result ifconnections between blocks and tightening of the end block's holding screw, is inadequate. Before supplying air , confirm that there are no gaps, etc. between blocks, and that manifold blocks are securely fastened to the DIN rail. Then supply air and confirm that there is no air leakage before operating.6LIMITATIONS OF USE WARNING:Do not exceed any of the specifications laid out in section 2 of this document or the specific product catalogue.1.Voltage LeakageWhen C-R device (surge voltage suppressor) Is used for the protection of switching device, note that the voltage leakage will be increased by passingvoltage leakage through C-R device. Suppressor residual voltage leakage should be as follows: DC coil: 3% or less of rated voltage.2.Drive the solenoid valve for AC with SSR or triac output. Leak current:When C-R device (surge voltage suppressor) Is used for the protection of switching device, note that the voltage leakage will be increased by passing voltage leakage through C-R device. Suppressor residual voltage leakage should be as follows: DC coil: 3% or less of rated voltage. Minimum load capacity (minimum load current)When valve's consumption current is less than minimum load capacity of output element, or when the margin is small, output element sometimes can not change itself. Please consult SMC.3.Surge voltage suppressorIf a surge protection circuit contains non-ordinary diodes such as Zener diodes or ZNRs, a residual voltage that is in proportion to the protective elements and the rated voltage will remain, Therefore, give consideration to surge voltage protection of the controller . In the case of diodes, the residual voltage is approximately 1V .4.Use in low temperature environmentsValve use in possible to temperature extremes to -10 C. Take appropriate measures to avoid freezing of drainage, moisture etc. 5.Mounting direction.All mounting postures are available7EUROPEAN CONTACT LIST7.1 SMC CorporationCountry Telephone Country Telephone Austria (43) 2262-62 280Italy(39) 02-92711 Belgium(32) 3-355 1464 Netherlands (31) 20-531 8888 Czech Republic (420) 5-414 24611 Norway (47) 67 12 90 20 Denmark (45) 70 25 29 00 Poland (48) 22-548 50 85 Finland (358) 9-859 580 Portugal (351) 22 610 89 22France (33) 1-64 76 1000 Spain (34) 945-18 4100 Germany (49) 6103 4020 Sweden (46) 8 603 12 00 Greece (30) 1- 342 6076 Switzerland (41) 52-396 3131 Hungary (36) 23 511 390 Turkey(90) 212 221 1512 Ireland(353) 1-403 9000United Kingdom(44) 1908-56 38887.2 WebsitesSMC Corporation SMC EuropeSJ2000*-TFJ0003。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
T1X1.3/97-037
NOTICE
The proposals in this submission have been formulated to assist A TIS subcommittee T1X1. This document is offered to the subcommittee as a basis for discussion and is not a binding proposal on Northern Telecom. The requirements are subject to change in form and numerical value after more study. Northern Telecom specifically reserves the right to add to, or amend the statements made herein. Nothing contained herein shall be construed as conferring by implication, estoppel or otherwise any license or right under any patent, whether or not the use of any information herein necessarily employs an invention of any existing or later issued patent.
T1X1.3/97-037
This page intentionally left blank.
T1X1.3/97-037
T1X1.3/97-037
T1X1.3/97-037 3.Test Results
This section summarizes measurements of DS1 wander for both the SRTS and adaptive clocking mechanisms.
Time Interval Error
DS1 phase variation was measured using an SJ300 Jitter and Wander Analyzer. Figure 3 com-pares the time-interval-error of the SRTS and adaptive clocking mechanisms. Note that this fig-ure superimposes two 10-second intervals from two separate 15000-second tests. The figure illustrates the characteristic breathing effects of the SRTS and adaptive clocking mechanisms under ideal conditions as the terminating AAL1 reconstitutes the DS1 signal received by the originating AAL1.
Figure3TIE Comparison
The breathing effect of the adaptive clocking mechanism has a lower frequency but higher amplitude than the SRTS mechanism.
MTIE
Figure 4 compares the MTIE of the SRTS and adaptive clocking mechanisms.
T1X1.3/97-037
Figure4MTIE Comparison
The figure shows the following:
•for both SRTS and adaptive clocking, the MTIE is well within the T1.101 requirements for public network DS1 timing signals
•for both SRTS and adaptive clocking, the MTIE is well within the T1.403 and G.824 require-ments for private network DS1s
•the SRTS mechanism creates less wander than adaptive clocking, but not remarkably less TDEV
Figure 5 compares the TDEV of the SRTS and adaptive clocking mechanisms.
T1X1.3/97-037 Figure5TDEV Comparison
The higher frequency wander of the SRTS mechanism is apparent in the TDEV graph of Figure 5.
Also, it should be noted, that both the SRTS and adaptive clock mechanisms are well below the T1.101 TDEV requirements for public network DS1 timing signal interfaces.
Input Frequency Offset Tolerance
In this test, the frequency of the input DS1 signal was increased beyond 1.544 MHz until loss-of-sync or loss-of-frame was detected on the output DS1. Both the SRTS and adaptive clocking mechanisms withstood frequency offsets of 300 Hz (200ppm). Neither mechanism could toler-ate an offset of 400 Hz.
Input Phase Transient Tolerance
The reactions of the SRTS and adaptive clocking mechanisms to an input phase ramp were also measured. The results are shown in Figures 6 and 7. The phase of the input DS1 was changed by offsetting its frequency by 4.6 ppm for 1 second.
T1X1.3/97-037
Figure6SRTS Step Response
Figure7Adaptive Clock Step Response
Both the SRTS and adaptive clocking mechanisms reacted well to the input phase change, i.e. tracked without loss of data. The SRTS algorithm appears to have a wider bandwidth than the adaptive algorithm.
T1X1.3/97-037 4.Conclusions & Next Steps
Conclusions
This paper has shown the following for the ideal case:
•the SRTS mechanism creates less wander than the adaptive clocking mechanism in this design
•the wander performance of the SRTS and the example adaptive clocking mechanisms are adequate for asynchronous circuit transport in an ideal environment
•the phase characteristics in these conditions are a function of the equipment design, rather than the clock transport mechanism
Next Steps
The following activities should be pursued to develop a better understanding of the performance of the SRTS and adaptive clocking mechanisms:
•explore wander-CDV relationship for adaptive clocking
•measure jitter performance of SRTS and adaptive clocking
•repeat wander and jitter tests with other A TM access devices
•test robustness of SRTS and adaptive clocking during network fault conditions, e.g. fre-quency offsets or lost cells
T1X1.3/97-037。
