周黎安 - Default BEA WebLogic Server Web Server …
J2EE课程设计及项目实训教学——JBuilderX与Weblogic8的集成
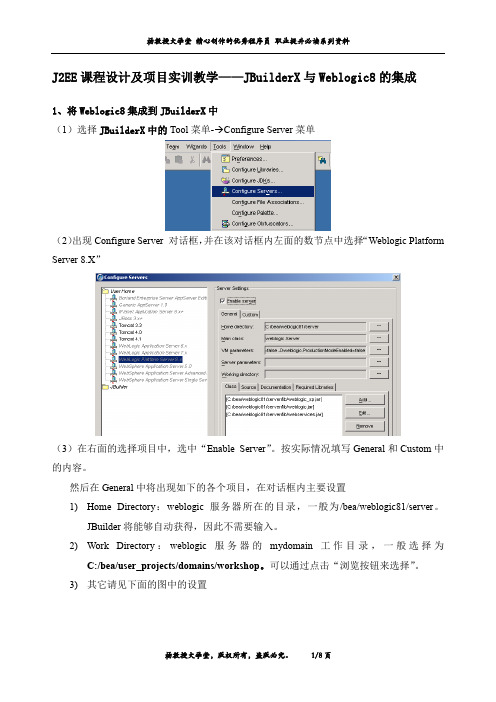
C:/bea/user_projects/domains/workshop。可以通过点击“浏览按钮来选择” 。
注意:
杨教授大学堂,版权所有,盗版必究。 2/8 页
杨教授大学堂 精心创作的优秀程序员 职业提升必读系列资料
1) 其中的 JDK 的目录位置要改变为实际的 Weblogic 下的 C:/bea/jdk142_04 目录 2) 选中“Add an Admin Console Item to The Tools Menu”项目,并定位 IE 浏览器的位 置 C:/Program Files/Internet Explorer/IEXPLORE.EXE,以后可以在 JBuilder 中启动 Weblogic 的管理控制台。 (5)最后点击“OK”按钮,完成两者的集成 此时将在 JBuilderX 中的 Tools 菜单中见到如下的项目,选择该菜单将启动 Weblogic 的管理控制台。
(3)在右面的选择项目中,选中“Enable Server” 。按实际情况填写 General 和 Custom 中 的内容。 然后在 General 中将出现如下的各个项目,在对话框内主要设置 1) Home Directory : weblogic 服务器所在的目录,一般为 /bea/weblogic81/server 。 JBuilder 将能够自动获得,因此不需要输入。 2) Work Directory : weblogic 服 务 器 的 mydomain 工 作 目 录 , 一 般 选 择 为 C:/bea/user_projects/domains/workshop。可以通过点击“浏览按钮来选择” 。 3) 其它请见下面的图中的设置
杨教授大学堂 精心创作的优秀程序员 职业提升必读系列资料
Weblogic_Server安装及使用

Weblogic Server 安装及使用目录一、Weblogic8.1 简介 (3)(一) 综述 (3)(二) BEA WebLogic Server 概述 (3)(三) BEA WebLogic Server 在企业中的角色 (3)(四) 为什么升级到BEA WEBLOGIC SERVER 8.1? (3)二、Weblogic 8.1.4的安装 (4)(一) Weblogic Platform 简单介绍 (4)(二) Weblogic8.1.4安装 (5)三、Weblogic 8.1.4的使用 (11)(一) 概念解释 (11)(二)后台EJB服务器在Weblogic8.1下的部署 (12)1. EJBDomain的建立 (12)2. 发布EJB Module (12)3. 建立一个JDBC Connection Pool (16)4. 建立一个JDBC Data Sources (21)5. 建立一个JMS Server (23)6. 配置Domain Credential (28)7. 配置系统运行必须的参数 (29)(三)受理服务器在Weblogic8.1下的部署 (30)1. SLDomain的建立 (30)2. 发布SLModule (30)四、实际演示 (31)一、Weblogic8.1 简介(一) 综述BEA WebLogic Server 在使应用服务器成为企业应用架构的基础方面继续处于领先地位。
作为BEA WebLogic Enterprise Platform 的基石,BEA WebLogic Server 为构建集成化的企业级应用提供了稳固的基础,它们以Internet 的容量和速度,在连网的企业之间共享信息、提交服务,实现协作自动化。
BEA WebLogic Server 的遵从J2EE 、面向服务的架构,以及丰富的工具集支持,便于实现业务逻辑、数据和表达的分离,提供开发和部署各种业务驱动应用所必需的底层核心功能。
64位weblogic安装部署以及常见问题解决

64位weblogic11g安装部署以及常见问题解决方案目录(一) 安装 (1)在Windows 64位操作系统安装Weblogic的注意事项 (3)(二) 部署运行 (3)1. 包引入错误 (3)2.乱码现象 (3)3.mime-typeType配置问题 (4)4.应用不存在 (4)5.ClassNotFoundException: org.hibernate.hql.ast.HqlToken (4)6.weblogic部署war包action不能访问问题解决方法[There is no Action mapped fornamespace / and action name] (5)ng.StackOverflowError (5)(一)安装我们在64位的服务器上为提高性能要安装64位的weblogic。
经常在网上看到有人问,weblogic有64位的么?weblogic需要破解么?weblogic有专门的64位版本,这里安装的是weblogic11g,也就是10.3.6版本,12c的版本安装应该类似。
weblogic从bea被oracle收购后,不需要破解,就只有授权。
什么意思呢?就是说从oracle官网上下载的weblogic 就是全功能版本,不管是集群还是其他,功能没有任何限制。
但是如果要用于商业环境,必须要向oracle买license,当然可以偷偷的用,那就是盗版,侵权,有一天oracle可以告的破产……。
1、下载64位weblogic,打下这个地址::// oracle/technetwork/middleware/ias/downloads/wls-main-097127.html,在这里可以看到除了mac os X操作系统外,其他系统的64位都是同一个版本,wls1036_generic.jar。
如下列图,weblogic的下载需要注册一个oracle官网的帐号。
2、下载64位JDK,我们下载的文件wls1036_generic.jar文件里面不包括JDK,如有可能, 请尽量在Windows/Linux平台下使用JRockit虚拟机,下载地址::// oracle/technetwork/middleware/jrockit/downloads/index.html。
Bea Weblogic Server V8.1Sp2在Windows Ser ver 2003中安装的步骤
Bea Weblogic Server的安装步骤目录1.weblogic主程序的安装2.说明环境:操作系统:Windows Server 2003 Enterprise Edition Sp1Weblogic server:weblogic Server 8.1 Sp2正文1.双击Weblogic Server的安装程序:2.准备工作结束后,出现具体版本号,然后跳过具体版本号,进入Weblogic Server V8.1 Sp2的安装引导界面,点击下一步:3.是否同意许可,选择是。
4.选择Bea主目录的安装路径5.点击下一步,选择安装的类型,这里选择完全:6.点击下一步,并选择成品安装目录7.点击下一步,开始安装。
8.安装完成后的成功页面,如下:如何需要安装XML Spy的可以把前面的方框勾上,点击完成就会开始安装XML Spy。
这里选择不安装。
说明:1、安装过程中,没有出现任何的错误信息,说明weblogic server成功安装。
2、在bea主目录下的文件夹代表的意思分别是:Ext_componets------------------配合weblogic server使用的组成部分,组件。
Jdk141_05-----------------------Sun Java 2 SDK的1.4.1版本,1.4.1指明安装在机器上的Sun SDK版本。
Jrockit81sp2_141_05------------Weglogic JRockit SDK.1.4.1指明了安装在机器上的版本。
Logs--------------------------------存放weblogic server使用过程中所产生的日志。
User_projects---------------------存放用户定义的用户工程。
Utils--------------------------------包含支持安装所有BEA Weblogic 品台产品的有用工具。
WebLogic-Web服务器安全配置基线要点

WebLogic Web服务器安全配置基线中国移动通信有限公司管理信息系统部2012年 04月版本版本控制信息更新日期更新人审批人V1.0200创V2.0更201备注:1.若此文档需要日后更新,请创建人填写版本控制表格,否则删除版本控制表格。
目录4 ......................................................................................................................................... 1章概述第41.1 ......................................................................................................................................... 目的4 ................................................................................................................................. 适用范围1.24 ................................................................................................................................. 1.3适用版本4 ......................................................................................................................................... 实施1.44 ................................................................................................................................. 1.5例外条款5 ............................................................................................................. 帐号管理、认证授权第2章5 ......................................................................................................................................... 帐号2.1系统启动帐号2.1.1.. (5)帐号锁定策略5................................................................................................................. 2.1.262.2 ......................................................................................................................................... 口令密码复杂度6 ..................................................................................................................... 2.2.17日志配置操作章......................................................................................................................... 第37日志配置................................................................................................................................. 3.1审核登录73.1.1.........................................................................................................................8 ................................................................................................................ IP4章协议安全配置第8.................................................................................................................................... 协议.IP4.1支持加密协议8................................................................................................................. 4.1.1数量限制应用服务器84.1.2......................................................................................... Socket禁用9................................................................................................ 4.1.3Send Server Header01章设备其他配置操作............................................................................................................... 第501安全管理............................................................................................................................... 5.1定时登出0....................................................................................................................... 5.1.11更改默认端口01* ............................................................................................................. 5.1.2错误页面处理............................................................................................................... 115.1.3目录列表访问限制....................................................................................................... 115.1.42 ........................................................................................................................... 6第章评审与修订1第1章概述1.1 目的本文档规定了中国移动通信有限公司管理信息系统部门所维护管理的WebLogic Web服务器应当遵循的安全性设置标准,本文档旨在指导系统管理人员进行WebLogic Web服务器的安全配置。
Weblogic8.1缺省应用配置

Weblogic8.1缺省应用配置Weblogic8.1缺省应用配置在Weblogic7中,要配置某个应用作为缺省应用(Default Web Application)的话,只需要在控制台(Console)界面上进行设置即可。
但Weblogic8.1的控制台里面似乎找不到这个选项了。
直接修改config.xml也无法达到目的。
要配置Weblogic8.1的缺省应用,需要为相应的Web Application的WEB-INF目录下加上相应的配置文件信息。
1、对于以ear形式发布的web application,在application.xml 中加入:<web><web-uri>yourAppName</web-uri><context-root>/</context-root></web>2、对于以目录形式发布的web application,可以在weblogic.xml里面配置:<!DOCTYPE weblogic-web-app PUBLIC "-//BEA Systems, Inc.//DTD Web Application 8.1//EN" "/servers/wls810/dtd/weblogic810-web-jar.dtd"><weblogic-web-app><container-descriptor><index-directory-enabled>true</index-directory-enabled> </container-descriptor><context-root>/</context-root></weblogic-web-app>注意:application.xml里面的配置将会覆盖掉weblogic.xml的配置信息(Note that the application.xml context-root takes precedent over the weblogic.xml value.)bea关于default web application的说明:Designating a Default Web ApplicationThe default Web Application is presented to clients who do not specify a URI (or specify "/" as the URI). To deploy a Web Application as a default Web Application, set the value of the context-root element to "/" in its deployment descriptor.You can specify the context-root element in the weblogic.xml deployment descriptor for Web Applications that are packaged as a .war archive or exploded .war directory. If you package the Web Application as part of an Enterprise Application (.ear archive or exploded .ear), specify the context-root in application.xml. Note that the application.xml context-root takes precedent over the weblogic.xml value.Deploy the application using the instructions in Deploying a New Web Application.To deploy a Web Application as part of an .ear archive or exploded .ear, see Deploying WebLogic Server Applications.。
WebLogic Server 配置步骤全攻略

BMS系统环境配置步骤1.1安装与初始化webservice在WebLogic安装及初始化双击weblogic安装程序>点击下一步>创建新的bea路径>点击自定义安装>去掉额外的功能>去掉默认勾选>点击下一步.>点击下一步.>点击下一步.>点击下一步.>去掉默认勾选项,点击完成1.2新建域>点击开始菜单> 所有程序>选择Oracle WebLogic>选择WebLogic Server 10gR3>选择Tools>点击Configuration Wizard 进入配置向导>点击下一步>点击下一步>输入用户密码>定制其它设置选项,选择yes,点击Next>点击下一步>配置端口号:1348,点击下一步>点击下一步>点击下一步>点击下一步>设置域的名称:bdms_domain,点击create>勾选Start Admin Server,点击Done。
结束安装并启动webLogic>在弹出框中输入用户名密码,启动weblogic服务1.3 建立数据源>启动weblogic服务后,打开web,地址栏输入http://localhost:1348/console进入如下页面,输入用户名密码登陆>点击Lock&Edit,选择DataSource>点击New按钮>点击Next>输入数据源连接参数>测试当前配置>测试数据连接,显示为如下成功提示信息后,点击next>勾选你要部署的服务,点击结束Finish>激活更改,完成数据源建立步骤1.4发布应用>点击“锁定并编辑”(Lock&Edit)>点击“部署”(deployments)>点击“安装”(install)>选择项目发布路径,并选择要发布的项目,点击下一步>点击下一步:>点击finish结束>点击激活更改按钮>选择bms,点击启动,选择为所有请求,完成部署。
WebLogic 简介及安装与配置指南

WebLogic 简介及安装与配置指南- ---------------------------------------------------------------------------------一、BEA Weblogic简介:BEA WebLogic PlatformTM 7.0是BEA公司一套基于J2EE功能强大的电子商务套件,提供了许多功能强大的中间件以方便编程人员编写的JSP、SERVLET等电子商务应用,可以为企业提供一个完整的商务应用解决方案。
BEA WebLogic PlatformTM 7.0通过一个统一的、简便的和可扩展的构建体系,让企业能够提高生产力和降低成本。
BEA WebLogic Platform 7.0包含BEA产品中所特有的应用基础结构技术,其中包括BEA WebLogic ServerTM、BEA WebLogic PortalTM和BEA WebLogic IntegrationTM。
这些技术与BEA WebLogic WorkshopTM结合起来,为应用开发、部署和管理提供了单一的、统一的、易用的基础结构平台。
BEA WebLogic Platform 7.0 提供:? 统一性融开发、门户和集成框架入一体的集成服务器为全面满足企业的应用需求,提供了单一的解决方案。
这个平台减少了产品学习、集成、支持和维护的工作量,从而可以降低企业成本,满足业务需求,并充分发挥已有基础结构资产的效益? 简便性通过简化应用开发、部署和管理,提高了生产效率。
其集成的开发框架让开发人员(不仅仅是J2EE专家)快速开发和部署企业级Web Service应用。
简便的部署和管理将降低维护的要求,从而降低应用维护成本,并让企业专注于业务目标的实现,而不是技术的管理。
? 可扩展性开放的可扩展性使BEA WebLogic Platform 7.0成为最好的选择,并让企业充分发挥已有和将来投资的效益。
Weblogic安装和配置

11.向服务器分配计算机,我这里为一个管理服务器AdminServer 和一个被管服务器myserver1 ,分别点击所侧这两个服务器,点击向右的箭头,选择完成后,点击“下一步”。
12.数据库(JDBC)选项选择否,点击“下一步”。
13.消息传递(JMS)选项选择否,点击“下一步”。
14.选择控制台的用户名、密码,我这里为weblogic/weblogic ,点击“下一步”。
startManagedWebLogic.cmd "myserver1" "http://10.2.18.203:8001" 按回车。
6.稍等片刻,当控制台出现<Server started in running mode>,说明被管服务器启动正常。
7.回控制台察看服务器状态,此时AdminServer 、myserver1 的状态为running ,启动完毕。
二.安装过程。
本次安装是在windows环境下安装,整个过程比较简单,大部分只需要按照默认的设置即可,步骤如下:
1) 双击 platform815_zh_CN_win32.exe 开始安装,出现欢迎界面,点击下一步。
2) BEA许可条款,选择“是”,单击下一步。
7) 最后把选择运行Quickstart选择去掉,点击安装完成。
三.配置过程。
安装完成之后,配置过程比较重要,要实现规划好,我这次只在一台计算机上配置,即主管服务器和被管服务器在一台机子上,还可以配置集群,这在以后的文章中再写,此配置过程,没有涉及到JDBC、JMS|,以及各种应用的部署,其过程基本如下:
5)关键任务可靠性
其容错、系统管理和安全性能已经在全球数以千记的关键任务环境中得以验证。
BEA WebLogic 服务器版本 6.1 管理指南及 BEA WebLogic Express

Server ™B E A W e b L o g i c S e r v e r V e r s i o n 6.1D o c u m e n t D a t e : J u n e 24, 2002BEA WebLogic Administration Guide and BEA WebLogic Express™CopyrightCopyright © 2002 BEA Systems, Inc. All Rights Reserved.Restricted Rights LegendThis software and documentation is subject to and made available only pursuant to the terms of the BEA Systems License Agreement and may be used or copied only in accordance with the terms of that agreement. It is against the law to copy the software except as specifically allowed in the agreement. This document may not, in whole or in part, be copied photocopied, reproduced, translated, or reduced to any electronic medium or machine readable form without prior consent, in writing, from BEA Systems, Inc.Use, duplication or disclosure by the U.S. Government is subject to restrictions set forth in the BEA Systems License Agreement and in subparagraph (c)(1) of the Commercial Computer Software-Restricted Rights Clause at FAR 52.227-19; subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013, subparagraph (d) of the Commercial Computer Software--Licensing clause at NASA FAR supplement 16-52.227-86; or their equivalent.Information in this document is subject to change without notice and does not represent a commitment on the part of BEA Systems. THE SOFTWARE AND DOCUMENTATION ARE PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND INCLUDING WITHOUT LIMITATION, ANY WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. FURTHER, BEA Systems DOES NOT WARRANT, GUARANTEE, OR MAKE ANY REPRESENTATIONS REGARDING THE USE, OR THE RESULTS OF THE USE, OF THE SOFTWARE OR WRITTEN MATERIAL IN TERMS OF CORRECTNESS, ACCURACY, RELIABILITY, OR OTHERWISE.Trademarks or Service MarksBEA, WebLogic, Tuxedo, and Jolt are registered trademarks of BEA Systems, Inc. How Business BecomesE-Business, BEA WebLogic E-Business Platform, BEA Builder, BEA Manager, BEA eLink, BEA WebLogic Commerce Server, BEA WebLogic Personalization Server, BEA WebLogic Process Integrator, BEA WebLogic Collaborate, BEA WebLogic Enterprise, and BEA WebLogic Server are trademarks of BEA Systems, Inc.All other product names may be trademarks of the respective companies with which they are associated.BEA WebLogic Server Administration GuideDocument Date Software VersionJune 24, 2002BEA WebLogic Server Version 6.1ContentsAbout This DocumentAudience (xxiii)e-docs Web Site (xxiii)How to Print the Document (xxiii)Contact Us! (xxiv)Documentation Conventions (xxiv)1.Overview of WebLogic Server ManagementDomains, the Administration Server and Managed Servers.............................1-2Administration Console.....................................................................................1-4Run-time and Configuration Objects.................................................................1-6Central Point of Access to Log Messages.........................................................1-7Creating a New Domain....................................................................................1-82.Starting and Stopping WebLogic ServersWebLogic Administration Server and WebLogic Managed Servers................2-1 Startup Messages........................................................................................2-2Failover Considerations for the Administration Server.............................2-3 Starting the WebLogic Administration Server..................................................2-3 Use of Passwords When Starting the WebLogic Server............................2-4Starting the WebLogic Administration Server from the Start Menu.........2-4Starting and Stopping the WebLogic Server as a Windows Service.........2-5Starting the WebLogic Administration Server from the Command Line..2-6Setting the Classpath Option.............................................................2-10A Server’s Root Directory................................................................2-11Starting the Administration Server Using a Script...................................2-12Restarting the Administration Server when Managed Servers are Running....WebLogic Server Administration Guide iii2-13Restarting the Administration Server on the Same Machine............2-14Restarting the Administration Server on Another Machine..............2-14Server Startup Process..............................................................................2-15 Adding a WebLogic Managed Server to the Domain.....................................2-16Starting a WebLogic Managed Server.............................................................2-17Informational Thread Dumps When Starting Clusters......................2-19Starting the WebLogic Managed Servers Using Scripts..........................2-20 Stopping WebLogic Servers from the Administration Console......................2-21Shutting Down a Server from the Command Line...................................2-21 Setting Up a WebLogic Server Instance as a Windows Service.....................2-22Setting Up Windows Services: Main Steps..............................................2-23Specifying the Name of the Server Instance and the Windows Service..2-23Specifying the Location of the Administration Server......................2-24Require Managed Servers to Start After the Administration Server.2-25Enabling Graceful Shutdowns from the Windows Control Panel.....2-27Redirecting Standard Out and Standard Error to a File....................2-28Adding Classes to the Classpath.......................................................2-31Run the Installation Script.................................................................2-32Removing WebLogic Server as a Windows Service................................2-33Changing Passwords for a Server Installed as a Windows Service..........2-33 Registering Startup and Shutdown Classes.....................................................2-343.Node ManagerOverview of Node Manager..............................................................................3-1Node Manager Logs...................................................................................3-2 Setting Up Node Manager.................................................................................3-4Setting Up Node Manager for Secure Socket Layer Protocol....................3-5Step 1: Obtain a Digital Certificate and Private Key..........................3-6Step 2: Converting a WebLogic-Style Private Key............................3-7Step 3: Merging the Certificates into a Single Certificate File...........3-7Setting Up the Administration Server to Use Node Manager....................3-8Step 1: Create a Configuration Entry for the Machine........................3-8Step 2: Configure Node Manager on Each Machine...........................3-8 iv WebLogic Server Administration GuideStep 3: Configure Startup Information for Managed Servers.............3-9 Platform Support for Node Manager...............................................................3-11 Starting the Node Manager from the Command Line.....................................3-11 Setting Up the Environment.....................................................................3-12 Setting the Environment Variables on Windows..............................3-12Setting the Environment Variables on UNIX...................................3-12 Setting the Classpath................................................................................3-13Starting the Node Manager......................................................................3-13 Command-Line Arguments...............................................................3-13Classpath Option...............................................................................3-15 Starting the Node Manager Using Start Scripts..............................................3-16 Remote Starting and Killing of Managed Servers...........................................3-16 The Distinction Between Stopping and Killing a Managed Server.........3-17Starting and Killing Domains and Clusters..............................................3-18 Setting Up Node Manager as a Windows Service...........................................3-18 Removing Node Manager as a Windows Service....................................3-194.Configuring WebLogic Servers and ClustersOverview of Server and Cluster Configuration.................................................4-1 Role of the Administration Server.....................................................................4-2 Starting the Administration Console.................................................................4-4 How Dynamic Configuration Works.................................................................4-5 Planning a Cluster Configuration......................................................................4-6 Server Configuration Tasks...............................................................................4-7 Cluster Configuration Tasks............................................................................4-105.Monitoring a WebLogic Server DomainOverview of Monitoring....................................................................................5-1 Monitoring Servers............................................................................................5-2 Performance........................................................................................5-3Server Security....................................................................................5-3JMS.....................................................................................................5-3JTA......................................................................................................5-3 Monitoring JDBC Connection Pools.................................................................5-4WebLogic Server Administration Guide ving Log Messages to Manage WebLogic ServersOverview of Logging Subsystem......................................................................6-1Local Server Log Files......................................................................................6-4Client Logging............................................................................................6-6Log File Format..........................................................................................6-6 Message Attributes............................................................................................6-7Message Catalog................................................................................................6-8Message Severity...............................................................................................6-9Debug Messages.......................................................................................6-10 Browsing Log Files.........................................................................................6-10Viewing the Logs.....................................................................................6-10 Creating Domain Log Filters...........................................................................6-117.Deploying ApplicationsSupported Formats for Deployment..................................................................7-1Using the Administration Console to Deploy Applications..............................7-2Step 1: Configure and Deploy the Application..........................................7-2Step 2: Deploying Application Components..............................................7-3Deploying Web Application Components..........................................7-3Deploying EJB Components...............................................................7-4Deploying Resource Adapter Components.........................................7-5Deployment Order......................................................................................7-6 Updating Deployed Applications at Startup......................................................7-6Forcing Application Update at Startup.......................................................7-7 Auto-Deployment..............................................................................................7-7Enabling or Disabling Auto-Deployment...................................................7-8Auto-Deployment of Applications in Expanded Directory Format...........7-9Undeployment or Redeployment of Auto-Deployed Applications............7-9Redeployment of Applications Auto-Deployed in Exploded Format......7-108.Configuring WebLogic Server Web ComponentsOverview...........................................................................................................8-2HTTP Parameters..............................................................................................8-2Configuring the Listen Port...............................................................................8-5 vi WebLogic Server Administration GuideWeb Applications..............................................................................................8-5 Web Applications and Clustering..............................................................8-6Designating a Default Web Application....................................................8-6 Configuring Virtual Hosting..............................................................................8-8 Virtual Hosting and the Default Web Application.....................................8-8Setting Up a Virtual Host...........................................................................8-9 How WebLogic Server Resolves HTTP Requests..........................................8-11 Setting Up HTTP Access Logs........................................................................8-14 Log Rotation.............................................................................................8-14Setting Up HTTP Access Logs by Using the Administration Console....8-15Common Log Format...............................................................................8-16Setting Up HTTP Access Logs by Using Extended Log Format.............8-17 Creating the Fields Directive............................................................8-18Supported Field identifiers................................................................8-18Creating Custom Field Identifiers.....................................................8-20 Preventing POST Denial-of-Service Attacks..................................................8-24 Setting Up WebLogic Server for HTTP Tunneling........................................8-25 Configuring the HTTP Tunneling Connection.........................................8-25Connecting to WebLogic Server from the Client.....................................8-26 Using Native I/O for Serving Static Files (Windows Only)............................8-279.Proxying Requests to Another HTTP ServerOverview...........................................................................................................9-1 New Version of the HttpProxyServlet...............................................................9-2 Setting Up a Proxy to a Secondary HTTP Server.............................................9-2 Sample Deployment Descriptor for the Proxy Servlet......................................9-410.Proxying Requests to a WebLogic ClusterOverview.........................................................................................................10-1 New Version of the HttpClusterServlet...........................................................10-2 Setting Up the HttpClusterServlet...................................................................10-2 Sample Deployment Descriptors ....................................................................10-4 web.xml for HttpClusterServlet SP02......................................................10-5web.xml for Deprecated HttpClusterServlet............................................10-6Proxy Servlet Deployment Parameters....................................................10-7WebLogic Server Administration Guide viiSyntax................................................................................................10-7Cluster Configuration and Proxy Plug-ins.............................................10-13 Verifying Your Configuration.......................................................................10-1311.Installing and Configuring the Apache HTTP Server Plug-InOverview.........................................................................................................11-2Keep-Alive Connections in Apache Version 1.3.x..................................11-2Keep-Alive Connections in Apache Version 2.x.....................................11-3Proxying Requests....................................................................................11-3 Certifications...................................................................................................11-3Installing the Apache HTTP Server Plug-In....................................................11-4Installing as a Dynamic Shared Object....................................................11-4Installing as a Statically Linked Module..................................................11-9 Configuring the Apache HTTP Server Plug-In.............................................11-10Editing the httpd.conf File......................................................................11-11Notes on Editing the httpd.conf File.......................................................11-13 Using SSL with the Apache Plug-In..............................................................11-14Configuring SSL Between the Apache HTTP Server Plug-In and WebLogicServer..............................................................................................11-15Issues with SSL-Apache Configuration.................................................11-15Specifying Trust of the WL-Proxy-Client-Cert Header.........................11-16 Connection Errors and Clustering Failover...................................................11-18Connection Failures................................................................................11-18Failover with a Single, Non-Clustered WebLogic Server......................11-18The Dynamic Server List........................................................................11-19Failover, Cookies, and HTTP Sessions..................................................11-19 Template for the httpd.conf File....................................................................11-21Sample Configuration Files...........................................................................11-21Example Using WebLogic Clusters.......................................................11-22Example Using Multiple WebLogic Clusters.........................................11-22Example Without WebLogic Clusters....................................................11-22Example Configuring IP-Based Virtual Hosting....................................11-23Example Configuring Name-Based Virtual Hosting With a Single IP Address11-2312.Installing and Configuring the Microsoft Internetviii WebLogic Server Administration GuideInformation Server (ISAPI) Plug-InOverview of the Microsoft Internet Information Server Plug-In....................12-2 Connection Pooling and Keep-Alive........................................................12-2Proxying Requests....................................................................................12-3 Platform Support.............................................................................................12-3 Installing the Microsoft Internet Information Server Plug-In.........................12-3 Proxying Multiple Virtual Websites from IIS.................................................12-7 Creating ACLs through IIS.............................................................................12-8 Sample iisproxy.ini File ..................................................................................12-9 Using SSL with the Microsoft Internet Information Server Plug-In...............12-9 Configuring SSL....................................................................................12-10Specifying Trust of the WL-Proxy-Client-Cert Header.........................12-11 Proxying Servlets from IIS to WebLogic Server..........................................12-12 Testing the Installation..................................................................................12-13 Connection Errors and Clustering Failover...................................................12-14 Connection Failures................................................................................12-14Failover with a Single, Non-Clustered WebLogic Server......................12-14The Dynamic Server List.......................................................................12-15Failover, Cookies, and HTTP Sessions..................................................12-15 13. Installing and Configuring the Netscape Enterprise Server Plug-In (NSAPI)Overview of the Netscape Enterprise Server Plug-In......................................13-2 Connection Pooling and Keep-Alive........................................................13-2Proxying Requests....................................................................................13-3 Certifications...................................................................................................13-3 Installing and Configuring the Netscape Enterprise Server Plug-In...............13-3 Modifying the obj.conf File.............................................................................13-5 Using SSL with the NSAPI Plug-In................................................................13-9 Configuring SSL....................................................................................13-10Specifying Trust of the WL-Proxy-Client-Cert Header.........................13-11 Connection Errors and Clustering Failover...................................................13-12 Connection Failures................................................................................13-12Failover with a Single, Non-Clustered WebLogic Server......................13-12The Dynamic Server List.......................................................................13-13WebLogic Server Administration Guide ixFailover, Cookies, and HTTP Sessions..................................................13-13 Failover Behavior When Using Firewalls and Load Directors ....................13-15Sample obj.conf File (Not Using a WebLogic Cluster)................................13-16Sample obj.conf File (Using a WebLogic Cluster).......................................13-1814.Managing SecuritySteps for Configuring Security........................................................................14-2Changing the System Password.......................................................................14-3Specifying a Security Realm...........................................................................14-5Configuring the File Realm......................................................................14-5Configuring the Caching Realm...............................................................14-7Configuring the LDAP Security Realm.................................................14-12Restrictions When Using the LDAP Security Realm......................14-14Locating Users and Groups in the LDAP Directory.......................14-15Configuring an LDAP Realm V1....................................................14-15Configuring an LDAP Realm V2....................................................14-20Supported LDAP Server Templates................................................14-22Using Microsoft Active Directory with WebLogic Server.............14-25Configuring the Windows NT Security Realm......................................14-26Configuring the UNIX Security Realm..................................................14-30Configuring the RDBMS Security Realm..............................................14-33Installing a Custom Security Realm.......................................................14-37Migrating Security Realms.....................................................................14-38 Defining Users...............................................................................................14-39Defining Groups............................................................................................14-42Defining ACLs..............................................................................................14-43Configuring the SSL Protocol.......................................................................14-46Obtaining a Private Key and Digital Certificate.....................................14-47Storing Private Keys and Digital Certificates........................................14-50Defining Trusted Certificate Authorities................................................14-51Defining Attributes for the SSL Protocol...............................................14-52Using PKCS#7 Files...............................................................................14-57Modifying Parameters for SSL Session Caching...................................14-58 Configuring Mutual Authentication..............................................................14-59Configuring RMI over IIOP with SSL..........................................................14-59 x WebLogic Server Administration GuideProtecting Passwords.....................................................................................14-60 Installing an Audit Provider..........................................................................14-63 Installing a Connection Filter........................................................................14-64 Setting Up the Java Security Manager..........................................................14-64 Modifying the weblogic.policy File for Third Party or User-Written Classes........14-67Using the Recording Security Manager Utility.............................................14-68 Configuring Security Context Propagation...................................................14-68 SSL Certificate Validation............................................................................14-73 Installation Instructions..........................................................................14-73Controlling the Level of Certificate Validation.....................................14-76Checking Certificate Chains...................................................................14-78Troubleshooting Problems with Certificates..........................................14-7915.Managing TransactionsOverview of Transaction Management...........................................................15-1 Configuring Transactions................................................................................15-2 Additional Attributes for Managing Transactions...........................................15-4 Monitoring and Logging Transactions............................................................15-6 Moving a Server to Another Machine.............................................................15-716.Managing JDBC ConnectivityOverview of JDBC Administration.................................................................16-1 About the Administrative Console ..........................................................16-2About the Command-Line Interface........................................................16-2About the JDBC API................................................................................16-2Related Information..................................................................................16-3 Administration and Management......................................................16-3JDBC and WebLogic jDrivers..........................................................16-3Transactions (JTA)..........................................................................16-4 JDBC Components—Connection Pools, Data Sources, and MultiPools........16-4 Connection Pools......................................................................................16-5MultiPools................................................................................................16-6Data Sources.............................................................................................16-6 JDBC Configuration Guidelines for Connection Pools, MultiPools and DataSources..............................................................................................16-7。
应用beaweblogic系列培训

应用beaweblogic系列培训BeaWeblogic是Java EE平台上著名的应用服务器。
在现代企业级应用程序的开发中,使用BeaWeblogic为核心是一种常见的选择。
但是,这个强大的服务器平台是很复杂的,需要深入的知识和技能来掌握。
因此,对于开发人员和企业级应用程序开发者来说,BeaWeblogic应用程序开发的培训非常必要。
在这篇文章中,我们将探讨为什么应该参加BeaWeblogic培训和受训者能够获得哪些好处。
为什么要参加BeaWeblogic系列培训BeaWeblogic培训的基本原则是提高企业应用程序开发者的技能和知识,让他们更好地管理应用服务器。
下面是一些原因,说明为什么参加BeaWeblogic系列培训非常必要。
1. 深入了解BeaWeblogic的特点和功能BeaWeblogic是一款功能强大的应用服务器,它提供了很多高级特性,如JMS、JDBCconnection pool、容器、EJB Container等。
通过参加BeaWeblogic系列培训,学员不仅可以深入了解BeaWeblogic的特点,也可以了解它的高级功能,包括如何有效地使用它来增强应用程序。
此外,将了解BeaWeblogic提供的时下最流行的功能,如记录解析、管理控制、监控和负载平衡等。
2. 理解如何与BeaWeblogic交互在开发应用程序时,与BeaWeblogic交互是必须的。
参加BeaWeblogic系列培训,您将学习如何通过应用程序与BeaWeblogic进行交互。
课程还将使学员能够通过软件开发工具与BeaWeblogic盘旋起舞,支持数据存储,Web服务,安全性和其他重要的功能。
3. 提高应用程序的处理能力和可靠性学习BeaWeblogic培训的另一个主要优点是,可以提高应用程序的处理能力和可靠性。
在课程中将演示如何使用BeaWeblogic的内置工具来评估应用程序性能,并深入了解如何通过应用程序和BeaWeblogic的集成来实现微调和优化。
WebLogic Server 9.0

WebLogic Server 9.0
佚名
【期刊名称】《开放系统世界》
【年(卷),期】2005(000)010
【摘要】8月9日,BEA WebLogic Server 9.0全面上市。
BEA公司产品执行副总裁黄卫文(WaiWong)表示:“WebLogic Server9.0将使用户在转向SOA的同时,能够继续在复杂的异构环境中实现提高效率、降低IT成本和零宕机这些核心目标。
”
【总页数】1页(P41)
【正文语种】中文
【中图分类】TP393.4
【相关文献】
1.Weblogic 9.0下JDBC数据源的配置 [J], 邓建华
2.WebLogic SIP Server 2.2加速通信服务 [J],
3.基于WebLogic Server实现跨域启用集中式身份验证SOA [J], 谢辉;鲁士文
4.数据库连接池技术及其在Weblogic Server中的配置 [J], 王飞
5.基于JAAS安全机制在WebLogic Server中的实现 [J], 盛兴;朱威
因版权原因,仅展示原文概要,查看原文内容请购买。
BEAWebLogicServer系统维护及问题解决最佳实践试题

BEA WebLogic Server 系统维护及问题解决最佳实践试题姓名:Email:考试时间:120分钟试题类型:选择题 36题和论述题 2 题1.以下哪种JAVA平台适用于企业级的大型分布式网络应用?A. J2MEB. J2SE2.以下哪项不属于J2EE的标准组件?A. JSPB. ServletC. EJBD. ASP3.WebLogic 中的服务器(Server)包括管理服务器(Admin Server)和被管服务器(Managed Server),它是:A.支持多线程,能横跨多个JAVA虚拟机(JVM)执行的类的实例。
B.支持多线程,执行在单一JAVA虚拟机(JVM)中的类的实例。
C.单线程,能横跨多个JAVA虚拟机(JVM)执行的类的实例。
D.单线程,执行在单一JAVA虚拟机(JVM)中的类的实例。
4.关于WebLogic的Domain和ServerA.Domain是weblogic server管理的一个逻辑单元,至少包含一个ServerB.在创建server和使用server的时候需要先创建domainC.每个domain都包括一个文件,在domain的根目录下。
D.Domain不能跨越多个物理主机,只能在配置在一个物理主机上5.Domain的主要配置信息存放在以下哪个文件中?A. B. C. D.6.以下哪种WebLogicA. GUI方式B. Silent方式C. Console方式7.生产模式(Production Mode)A. 使用WebLogic Console方式B. 命令行方式C. 自动部署方式8.下面关于WebLogic ConsoleA.基于主控Server(Admin Server)的web应用的监控工具B.可以用来部署、配置应用和ServerC.可以管理多个Server和ClusterD.可以管理多个Domain9.在如下4类日志级别中,那种级别是最高和最严重的?A. INFOB. ALERTC. ERRORD. WARNING10.A. 管理B. 配置C. 监控D. 部署应用11.WebLogic Console可以监控:( 多选 )A. Server的状态B. Server的内存使用情况C. Server的CPU使用情况D. Server的执行队列情况12.外来服务请求通过如下哪种正确路线得到服务的?A.→ Socket Thread → Execute Queue → Execute ThreadB.→ Socket Thread → Execute Thread → Execute QueueC.→ Execute Queue → Socket Thread → Execute ThreadD.→ Execute Thread → Execute Queue → Socket Thread13.进行Thread Dump操作的方法有:( 多选 )A. kill -3 pid 操作系统命令方式( Unix ) B Ctrl + Break 组合键方式 ( Windows )C. kill -9 pid 操作系统命令方式( Unix )D. 的THREAD_DUMP命令方式14.Thread Dump操作的作用是A. 收集server的日志信息B. 备份server的日志信息C. 导出JVM执行堆栈中的线程信息D. 导出JAVA进程的本地堆栈信息15.A. JVM读取classesB. 一个新的socket连接建立C. 一个新的HTTP浏览器连接到服务器D. JVM新建一个java线程16.当too many open file信息出现时,应该:(多选)A.定期的监控进程打开的文件和网络连接数B.根据实际情况需要,适当的增加操作系统的文件打开数的limit值,继续监控C.检查应用代码是否存在没有正常关闭的文件D.如存在大量处在TIME_WAIT状态的connections,适当降低网络的TIME_WAIT等待时间17.关于WebLogic Server JDBC connection poolA.与数据库预先建好连接,是一个 ready-to-use 的poolB.应用必须通过DataSource来访问connection poolC.一个connection pool只能用于一个applicationD.Connection pool中的连接可以被共享和重用18.有一个系统,客户反映提交的请求很长时间无法响应,查看server的日志文件后,发现存在无法获得数据库连接的错误信息,而当时的CPU和I/O资源都很空闲。
Bea Web应用服务器重整电子商务

Bea Web应用服务器重整电子商务
初蒙
【期刊名称】《互联网周刊》
【年(卷),期】2001(000)031
【摘要】在应用服务器市场,BEAWebLogic Server 6.1正在以简练、有力的Web Services,重新定义并变革电子业务,让企业内外的应用系统和流程可通过Internet 实现无缝集成。
BEA WebLogic Server 6.1能够自动生成代码,将新的和已有的Java应用集成于Web Services,同时,它还提供了基于标准的应用集
【总页数】1页(P)
【作者】初蒙
【作者单位】本刊记者
【正文语种】中文
【中图分类】F713.36
【相关文献】
1.Web应用服务器中实体BEAN的性能优化策略 [J], 杨波;张文博;范国闯;陈宁江
2.新一代Web 应用服务器 BEA WebLogic研究与开发指南 [J], 时亚弘;周铭
3.新一代Web应用服务器软件-WebSphere应用服务器探析 [J], 韩德志;耿红琴
4.BEA WebLogic应用服务器实现Internet自助服务系统 [J],
5.BEA WebLogic应用服务器为Internet金融服务 [J],
因版权原因,仅展示原文概要,查看原文内容请购买。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
中文论文
[30]. “资源错配与政治周期”(与赵鹰妍、李力雄合作),《金融研究》2013 年第 3 期 [29]. “行政发包制与雇佣制:以清代海关治理为例”(与王娟合作),载入《国家建设与政
府行为》(周雪光、刘世定、折晓叶主编),中国社会科学出版社,2012 年 [28]. "税收努力、征税机构与税收增长之谜" (与刘冲、厉行合作),《经济学》(季刊)2011
[11]. “Intra-Industry Knowledge Spillovers from Foreign Direct Investment in R&D: Evidence from China’s ‘Silicon Valley’” (with Yasuyuki Todo and Weiying Zhang), Review of Development Economics 15(3), 569-585, 2011.
年第 2 期 [15].“信誉的价值:以网上拍卖交易为例”(与张维迎、顾全林、沈懿合作),《经济研究》
版发表于 Frontiers of Economics in China 2009, 4(3): 425-448) [24]. “宗族制度、商人信仰与商帮治理:关于明清时期徽商与晋商的比较研究”(与蔡洪滨、
吴意云合作)《管理世界》2008 年第 8 期 (摘要收录于《高等学校文科学术文摘,2008 年第 6 期,44-45 页) [23]. “信誉与管制的互补与替代:基于网上交易数据的实证研究”(与杨居正、张维迎合作) 《管理世界》2008 年第 7 期 [22]. “企业信息化投资的绩效及其影响因素:基于浙江企业的经验证据”(与汪淼军、张维 迎合作)《中国社会科学》2007 年第 6 期 [21].“中国地方官员的晋升锦标赛模式研究” 《经济研究》2007 年第 7 期 (本文收录《中 国社会学文选》(应星、周飞舟、渠敬东编,中国人民大学出版社 2011 年版),2011 年获得北京大学第 11 届人文社会科学研究优秀成果一等奖) [20]. “企业生产率的代际效应和年龄效应”(与张维迎、顾全林、汪淼军合作)《经济学》 (季刊)2007 年第 6 卷第 4 期 [19]. “信息化、组织行为与组织绩效:基于浙江企业的实证研究”(与汪淼军、张维迎合作)
[10]. “FDI Spillovers in an Emerging Market: The Role of Foreign Firms’ Country Origin Diversity and Domestic Firms’ Absorptive Capacity” (with Yan Zhang, Haiyang Li and Yu Li), Strategic Management Journal 31: 969–989, 2010.
《管理世界》2007 年第 4 期 [18]. “中国轿车行业的合谋与价格战”(与王皓合作),《金融研究》2007 年第 2 期 [17].“地区放权与经济效率:以计划单列为例”(与史宇鹏合作)《经济研究》2007 年第 1
期 [16].“中国上市公司外部审计的选择及其治理效应”(与王鹏合作),《中国会计评论》2006
[9]. “Income and Consumption Inequality in Urban China: 1992-2003” (with Hongbin
Cai and Yuyu Chen), Economic Development and Cultural Change 58 (3): 385-413, 2010, lead article. [8]. “Incentives, Equality, and Contract Renegotiations: Theory and Evidence in the Chinese Banking Industry” (with Hongbin Cai and Hongbin Li), Journal of Industrial Economics 58(1): 156-189, 2010. [7]. "Political Connections, Financing and Firm Performance: Evidence from Chinese Private Entrepreneurs" (with Hongbin Li, Lingsheng Meng, and Qian Wang), Journal of Development Economics 87: 283-299, 2008. One of the Most Cited Journal of Development Economics Articles since 2007 with the rank of the 13th out of Top 25, 2012 [6]. "The Long-Term Health and Economic Consequences of the 1959-61 Famine in China" (with Yuyu Chen), Journal of Health Economics 26: 659-681, 2007, lead article. One of the Most Cited Journal of Health Economics Articles since 2007 with the rank of the 11th out of Top 25, 2012 [5] “Incentive Contracts and Bank Performance: Evidence from the Banking Industry in Rural China" (with Hongbin Li and Scott Rozelle), Economics of Transition 15(1): 109-124, 2007. [4] "Relative Performance Evaluation and the Turnover of Provincial Leaders in China" (with Ye Chen and Hongbin Li), Economics Letters 88: 421-425, 2005. [3] “Political Turnover and Economic Performance: The Incentive Role of Personnel Control in China” (with Hongbin Li), Journal of Public Economics 89:1743-1762, 2005. Reprinted in "Governing Rapid Growth in China: Equity and Institutions", edited by Ravi Kanbur and Xiaobo Zhang, 2009, London and New York: Routledge. One of the Most Cited Journal of Public Economics Articles since 2005 with the rank of the 3rd out of Top 10, 2010 [2] "Parental Childcare and Children’s Educational Attainment: Evidence from China" (with Hongbin Li, Xianguo Yao, and Junsheng Zhang), Applied Economics, 37 (18): 2067-2076, 2005. [1] “How Prudent Are Community Representative Consumers?” (with Yuyu Chen) Topics in Macroeconomics: Vol. 3: No. 1, Article 4. 2003.
发表论文:
英文论文
[13] "Family Ties and Organizational Design: Evidence from Chinese Private Firms" (with Hongbin Cai, Hongbin Li and Albert Park), Review of Economics and Statistics 95(3): 850-867, 2013.
行政和社会职务: 2006 年 8 月 2011 年 1 月,北京大学光华管理学院应用经济系副主任 2011 年 1 月至今,北京大学光华管理学院应用经济系主任 2006 年 10 月至今,北京大学莫里斯经济政策研究所,副所长
主要教学课程: 中级和高级微观经济学 微观计量经济学应用 激励与组织专题
研究方向: 政治经济学 产业组织 经济转型与发展
年第 11 卷第 1 期 [27]. “官员晋升竞争与边界效应:以省区交界地带的经济发展为例”(与陶婧合作),《金融研
究》2011 年第 3 期 [26]. “企业规模对职工工资的影响:来自中国竞争性劳动力市场的证据”(与陈凌、李宏彬
和熊艳艳合作),《金融研究》2010 年第 2 期 [25]. “政府规模、市场化与地区腐败”(与陶婧合作)《经济研究》2009 年第 1 期 (英文
China”(与陈玉宇合作)获全国高等学校科学研究优秀成果奖(人文社会科学)二等奖, 2009 年 8. 第五届“厉以宁教学奖”,2011 年 9. 论文“中国地方官员的晋升锦标赛模式研究”获得北京大学第 11 届人文社会科学研究 优秀成果一等奖,2011 年 10. 专著《转型中的地方政府:官员激励与治理》获第六届全国高等学校科学研究优秀成果 奖(人文社会科学)二等奖,2013 年
