Statistical Mechanical Entropy of Two-Dimensional Black Holes
化学专业英语常用词4

Physical chemistry 物理化学Thermodynamics [,θɜːmə(u)dai'næmiks] n 热力学Kinetics [ki'netiks; kai-] n 动力学Quantum chemistry 量子化学Statistical mechanics 统计力学Mechanism ['mek(ə)niz(ə)m] n 机理Equilibrium of Heterogeneous SubstancesColloid and surface chemistry 胶体表面化学Quantum mechanics 量子力学Infrared spectroscopy 红外光谱Microwave spectroscopy 微波光谱EPR spectroscopy电子顺磁共振波谱法NMR spectroscopy 核磁共振谱Nuclear chemistry核化学Astrochemistry 天体化学Surface chemistry 表面化学Mechanical work 机械功Zero law of thermodynamics 热力学第零定律law of thermodynamics 热力学定律entropy ['entrəpi] n 熵system ['sistəm] n 系统surrounding [sə'raundiŋ] n 环境internal energy 内能thermodynamic potential 热力位(势)equilibrium [,iːkwi'libriəm; ,ekwi-] n 平衡spontaneous process 自发过程Zeroth law 第零定律Energy balance equation 能量守恒方程Legendre transformation勒让德变换Enthalpy ['enθ(ə)lpi; en'θælp i] n 焓Helmholtz energy 亥姆霍兹自由能Gibbs energy 吉布斯自由能Isolated system 孤立系统Adiabatic system 绝热系统Diathemic system 透热系统Closed system 封闭系统Open system 开放系统Thermodynamic equilibrium 热力学平衡Reversible process 可逆过程Definite state定态Intensive variable 强度变量Extensive variable 广度变量Equation of state 状态方程Thermodynamic process 热力学过程Isobaric [,aisə'bærik] adi 等压的Isochoric[,aisəu'kɔ:rik]/ isometric[aisə(u)'metrik]/ isovolumetric [,aisəu,vɔlju'metrik] adj 等容的Isothermal [,aisəu'θɜːməl] adj 等热的Adiabatic [,eidaiə'bætik; ,ædiə-] adj 绝热的Isentropic [,aisen'trɔpik] adj 等熵的Isenthalpic [,aisən'θælpik] adj等焓的Steady state 稳态Phase rule 相律Phase diagram 相图Phase [feiz] n 相Density ['densiti] n 密度Index of refraction 折射率Chemical composition 化学组成Plasma ['plæzmə] n 等离子体Polar ['pəulə] adj 极性的Non-polar 非极性的Phase transition 相转变Triple point 三线点Solidus 固相线Liquidus 液相线Critical point 临界点Supercritical fluid 超临界流体Non-azeotropic 非共沸的Binary phase diagram 二元相图Eutectic [juː'tektik] adj 低共熔的,共熔的n 共熔合金Peritectic [,perə'tektik] adj 包晶体的(转熔的)n 包晶Boiling point diagram 沸点图Chemical kenetics 化学动力学Reaction rate 反应速率Effect of various variables 各种变量的影响P181Re-arrangement of atom 原子重排Formation of intermediate 中间体的形成Law of mass action 质量作用定律Zero-order 零级First-oder 一级Second-order 二级Rate-determining step决速步Activation energy 活化能Arrhenius equation 阿伦尼乌斯方程Eyring equation 艾琳方程Physical state 物理状态Concentration [kɔns(ə)n'treiʃ(ə)n] n 浓度Catalyst ['kæt(ə)list] n 催化剂Autocatalysis [,ɔːtəukə'tælisis] n 自催化作用Enzyme ['enzaim] n 酶Michaelis-Menten kinetics 米夏埃利斯-门滕动力学Partial pressure 分压Electrochemistry [i,lektrəu'kemistri] n 电化学Electrolysis [,ilek'trɔlisis; ,el-] n 电解Electrochemical reaction 电化学反应Oxidation/reduction reaction 氧化/ 还原反应Electrochemical cell 电化学电池Galvanic cell 伽伐尼电池,原电池V oltaic cell 伏达电池Anode ['ænəud] n 阳极Cathode ['kæθəud] n 阴极Electrical battery 电池Primary battery 原电池,一次电池Secondary battery 蓄电池,充电电池Electroform [i'lektrəufɔːm] v 电铸Electroplate [i'lektrə(u)pleit; i,lektrə(u)'pleit] v 电镀Electrowinning [i,lektrəu'winiŋ] n 电解冶金法,电积金属法Electrorefine 电解精炼,电精制Corrosion [kə'rəuʒ(ə)n] n 腐蚀,锈蚀Passivation [pæsi'veiʃən] n 钝化Plate [pleit] v 电镀Cathodic protection 阴极保护Surface science 表面科学Surface chemistry 表面化学Surface physics 表面物理Surface engineering 表面工程Interface 界面Colloid science 胶体科学Adsorption [æd'sɔ:pʃən] n 吸附Chemisorption [kɛmi'zɔrpʃən] n 化学吸附Physisorption [,fizi'sɔ:pʃən] n 物理吸附Colloid chemistry 胶体化学Dispersed phase 分散相Continuous phase 连续相Aerosol ['eərəsɔl] n 气溶胶Emulsion [i'mʌlʃ(ə)n] n 乳液Foam [fəum] n 泡沫Dispersion [di'spɜːʃ(ə)n] n 分散体系Hydrosol ['haidrəusɔl] n 水溶胶Tyndall effect 丁达尔效应Stability of colloid system 胶体系统的稳定性Steric stabilization 位阻稳定Electrostatic stabilization 静电稳定作用Buoyancy ['bɔiənsi] n 浮力Floc [flɔk] n 絮状物Flocculant ['flɑkjələnt] n 絮凝剂Depletant n 耗尽剂Suspension [sə'spenʃ(ə)n] n 悬浮液Brownian force 布朗力Viscoelastic [,viskəui'læstik] n 粘弹性的Lattice ['lætis] n 点阵Pattern 图样,模,型式,图,特性,图案Unit cell 晶胞Lattice parameter 晶格参数Miller index notation 密勒指数Orthogonal [ɔː'θɔg(ə)n(ə)l] adj 正交的Optical property 光学性质Adsorption and reactivity 吸附和反应性Surface tension 表面张力Microstructural defect 微结构缺陷Cleavage ['kliːvidʒ] n 裂缝,分裂Plastic deformation 塑性变形Burgers vector 伯格斯矢量Inherent symmetry 固有对称性Two fold rotational symmetry 二重旋转对称Mirror plane symmetry镜面对称Translational symmetry 平移对称Compound symmetry 复合对称Cubic ['kjuːbik] adj 立方的Hexagonal [hek'sæɡənəl] adj 六方的Tetragonal [ti'træg(ə)n(ə)l] adj 四方的Rhombohedral [rɔmbəu'hi:drəl] adj 菱形的Orthorhombic [,ɔːθə(u)'rɔmbik] adj 正交晶的,斜方的Monoclinic [mɔnə(u)'klinik] adj 单斜的Triclinic [trai'klinik] adj 三斜的Bravais lattice 布拉维点阵Space lattice 空间点阵Quasicrystal ['kweizai'kristl] n 准晶体Point group / crystal class点群Reflection [ri'flekʃ(ə)n] n 反射Rotation [rə(u)'teiʃ(ə)n] n 旋转Inversion [in'vɜːʃ(ə)n] n 反衍Improper rotation 非正常旋转,反射旋转Rotation axe 旋转轴Reflection plane 反射面Center of symmetry 对称中心Symmetry element 对称元Space group 点群Pure translation 纯平移,纯平动Screw axe 螺旋轴Glide plane 滑动面。
材料科学与工程专业英语词汇
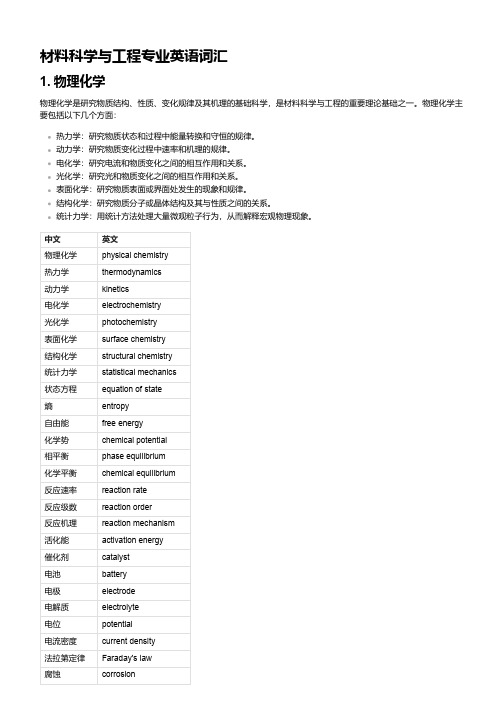
材料科学与工程专业英语词汇1. 物理化学物理化学是研究物质结构、性质、变化规律及其机理的基础科学,是材料科学与工程的重要理论基础之一。
物理化学主要包括以下几个方面:热力学:研究物质状态和过程中能量转换和守恒的规律。
动力学:研究物质变化过程中速率和机理的规律。
电化学:研究电流和物质变化之间的相互作用和关系。
光化学:研究光和物质变化之间的相互作用和关系。
表面化学:研究物质表面或界面处发生的现象和规律。
结构化学:研究物质分子或晶体结构及其与性质之间的关系。
统计力学:用统计方法处理大量微观粒子行为,从而解释宏观物理现象。
中文英文物理化学physical chemistry热力学thermodynamics动力学kinetics电化学electrochemistry光化学photochemistry表面化学surface chemistry结构化学structural chemistry统计力学statistical mechanics状态方程equation of state熵entropy自由能free energy化学势chemical potential相平衡phase equilibrium化学平衡chemical equilibrium反应速率reaction rate反应级数reaction order反应机理reaction mechanism活化能activation energy催化剂catalyst电池battery电极electrode电解质electrolyte电位potential电流密度current density法拉第定律Faraday's law腐蚀corrosion中文英文光敏材料photosensitive material光致变色photochromism光致发光photoluminescence光催化photocatalysis表面张力surface tension润湿wetting吸附adsorption膜membrane分子轨道理论molecular orbital theory晶体结构crystal structure点阵lattice空间群space group对称元素symmetry element对称操作symmetry operationX射线衍射X-ray diffraction2. 量子与统计力学量子与统计力学是物理学的两个重要分支,是材料科学与工程的重要理论基础之一。
用英语介绍爱因斯坦

Part 4
General Theory
4 of Relativity and Later Years
General Theory of Relativity and Later Years
In 1915, Einstein published his general theory of relativity, which explained gravitation as a consequence of the curvature of spacetime. The theory revolutionized our unde rstanding of gravity and marked a turning point in Einstein's career. The following year, he was awarded the Nobel Prize in Physics for his work on the photoelectric effect
答 辩 人 :XXX
Part 2
2
Studies and Work in Switzerland
and Germany
Studies and Work in Switzerland and Germany
In 1900, Einstein graduated from the University of Zurich with a teaching diploma in mathematics and physics. He began teaching mathematics and physics at a series of Swiss schools, including the Cantonal School i
纳斯别尔格公式英文

纳斯别尔格公式英文The Nasserberg Formula is a mathematical expression that has been widely used in various fields, particularly in the study of thermodynamics and statistical mechanics. This formula, named after the renowned physicist Gerhard Nasserberg, provides a relationship between the entropy of a system and its microstates. Understanding the Nasserberg Formula is crucial for comprehending the fundamental principles of thermodynamics and the behavior of complex systems.At its core, the Nasserberg Formula states that the entropy of a system is proportional to the natural logarithm of the number of accessible microstates. Mathematically, this can be expressed as S = k ln W, where S represents the entropy of the system, k is the Boltzmann constant, and W is the number of accessible microstates. This simple yet powerful equation has profound implications in our understanding of the physical world.One of the primary applications of the Nasserberg Formula is in the field of statistical mechanics, where it provides a bridge between themicroscopic behavior of individual particles and the macroscopic properties of a system. By considering the distribution of particles among the available microstates, we can derive important thermodynamic quantities such as temperature, pressure, and internal energy. This connection between the microscopic and macroscopic realms is a fundamental aspect of our understanding of the physical universe.Furthermore, the Nasserberg Formula has implications for our understanding of information theory and the nature of information itself. In this context, the entropy of a system can be interpreted as a measure of the uncertainty or information content of that system. This relationship between entropy and information has led to the development of fields such as information theory and communication theory, which have had a profound impact on our ability to store, transmit, and process information.One of the fascinating aspects of the Nasserberg Formula is its ability to describe the behavior of complex systems, such as those found in biology, ecology, and even social sciences. In these domains, the concept of entropy can be used to understand the organization and dynamics of complex systems, from the intricate networks of living organisms to the collective behavior of human societies. By analyzing the distribution of microstates in these systems, researchers can gain insights into their underlying principles and potentially predict theirfuture behavior.Moreover, the Nasserberg Formula has played a crucial role in the development of our understanding of the universe as a whole. In cosmology, the concept of entropy has been used to study the evolution of the universe, from the early stages of the Big Bang to the eventual fate of the cosmos. The Nasserberg Formula has provided a framework for understanding the arrow of time, the directionality of entropy, and the implications for the ultimate fate of the universe.In recent years, the Nasserberg Formula has also found applications in the realm of quantum mechanics and the study of quantum systems. In this context, the formula has been generalized to describe the entropy of quantum states, providing insights into the behavior of quantum systems and the nature of information at the quantum level.Despite its mathematical simplicity, the Nasserberg Formula has had far-reaching implications and has shaped our understanding of the physical world in profound ways. It continues to be a subject of active research and exploration, as scientists and researchers seek to push the boundaries of our knowledge and uncover the deeper mysteries of the universe.In conclusion, the Nasserberg Formula is a fundamental equation that has had a profound impact on our understanding of the physical world. From its applications in thermodynamics and statistical mechanics to its implications in information theory, cosmology, and quantum mechanics, this equation has proven to be a cornerstone of our scientific understanding. As we continue to explore the frontiers of knowledge, the Nasserberg Formula will undoubtedly continue to play a crucial role in shaping our understanding of the universe and the fundamental laws that govern it.。
熵的解释

熵概念辨析EntropyCao Zexian中国科学院物理研究所内容提要¾热力学基础知识回顾¾Emergent Phenomenon¾Entropy和熵的字面意思¾熵概念-伤脑筋¾Entropy的数学表达¾Entropy 概念上的伟大成果量子力学的诞生;光子的极化态自旋薛定谔方程的推导;信息论¾Entropy作为过程的判据?¾结束语热力学是怎样的一门学问?我在德国Kaiserslautern大学机械系一间实验室的窗框上读到过这样的一段话,大意是:“热力学是这样的一门课:你学第一遍的时候觉得它挺难,糊里糊涂理不清个头绪,于是,你决定学第二遍;第二遍你觉得好像明白了点什么,这激励你去学第三遍;第三遍你发现好像又糊涂了,于是你只好学第四遍。
等到第四遍,well, 你已经习惯了你弄不懂热力学这个事实了。
”但我们必须理解热力学,因为:¾热力学是真实的。
Nothing in life is certain except death, taxes and the second law of thermodynamics. -Seth Lloyd¾热力学就在身边。
In this house, we obey the laws of thermodynamics! -Dan Castellaneta¾热力学是必备知识。
知冷知热是确立配偶人选的基本判据。
-曹则贤P. W. Anderson: More is different曹则贤,熵非商:the myth of Entropy,《物理》第九期,Entropy的字面意思Tropy的字面意思tropik<tropicus< Gr tropikos,belonging to a turn(of the sun at the solstices)Tropic of Cancer(北回归线)Tropic of Capricorn (南回归线))Heliotropism: 向日性。
熵

熵的由来物理学中,熵有两个定义——热力学定义和统计力学定义。
熵最初是从热力学角度定义的。
19世纪50年代,克劳修斯(...R J E C lausius)编造了一个新名词:entropy,它来自希腊词“trope”,意为“转变,变换”。
为了与能量(energy)相对应,克劳修斯在“trope”上加了一个前缀“en”。
在克劳修斯看来,“energy”和“entropy”这两个概念有某种相似性。
前者从正面量度运动转化的能力;后者从反面量度运动不能转化的能力,即运动丧失转化能力的程度,表述能量的可转换能力(活力)丧失的程度,或能量僵化(蜕化)的程度(尽管能量总体是守恒的)。
例如,你用20元人民币购得一袋大米,你的价值总量(能量)不变,但一袋大米在市场上的再交换能力(活力)低于20元人民币。
这种消费使其熵(经济)增大。
按当初的设计,活力越丧失,能量越僵化,熵越大。
热力学第一定律描述了自然界中各种形式的能量转换过程中量的守恒,并未指出不同形式能量的本质的差异。
而热力学第二定律告诉我们,能量之间的品质是有差别的:有序运动的能量可以通过做功完全转变成无序运动的能量;而无序运动的能量不能完全转变成有序运动的能量(效率为100%的热机是不能实现的)。
或者说,有序运动的能量转化为其他形式的能量的能力强,能被充分利用来做功,品质较高;而无序运动的能量转化能力弱,做功能力差,品质较低。
根据热力学第二定律,高品质的能量转换为低品质的能量的过程是不可逆的。
高品质的能量转换为低品质的能量后,就有一部分不能再做功了。
我们把这样的过程称为能量的退化,通过物理学知识可以证明:退化的能量与系统的熵增成正比。
于是,我们可以说:熵是能量不可用程度的度量。
“熵”的中文译名是我国物理学家胡刚复教授确定的。
他于1923年5月为德国物理学家普朗克作《热力学第二定律及熵之观念》讲学时做翻译,把“entropy”译为“熵”。
它是热量变化与温度之比(商),又与热学有关,就加了个“火”字旁,定名为熵。
化工热力学专业词汇中英文对照表
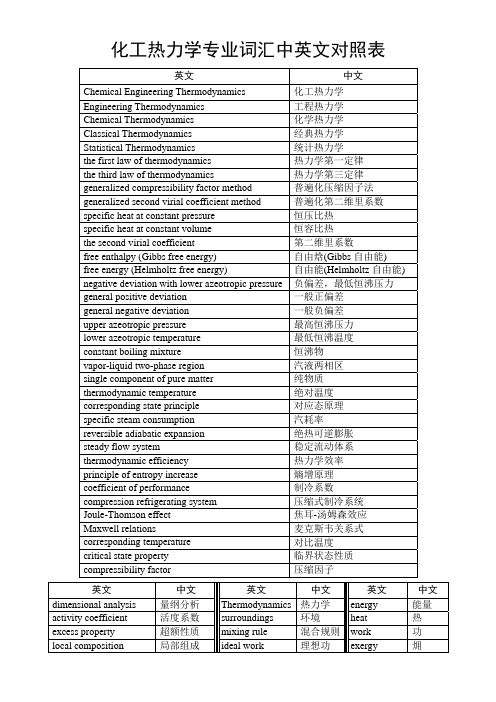
化工热力学专业词汇中英文对照表英文 中文Chemical Engineering Thermodynamics化工热力学Engineering Thermodynamics 工程热力学Chemical Thermodynamics 化学热力学Classical Thermodynamics 经典热力学Statistical Thermodynamics 统计热力学the first law of thermodynamics 热力学第一定律the third law of thermodynamics 热力学第三定律generalized compressibility factor method 普遍化压缩因子法generalized second virial coefficient method 普遍化第二维里系数specific heat at constant pressure 恒压比热specific heat at constant volume 恒容比热the second virial coefficient 第二维里系数free enthalpy (Gibbs free energy) 自由焓(Gibbs自由能)free energy (Helmholtz free energy) 自由能(Helmholtz自由能)negative deviation with lower azeotropic pressure负偏差,最低恒沸压力general positive deviation 一般正偏差general negative deviation 一般负偏差upper azeotropic pressure 最高恒沸压力lower azeotropic temperature 最低恒沸温度constant boiling mixture 恒沸物vapor-liquid two-phase region 汽液两相区single component of pure matter 纯物质thermodynamic temperature 绝对温度corresponding state principle 对应态原理specific steam consumption 汽耗率reversible adiabatic expansion 绝热可逆膨胀steady flow system 稳定流动体系thermodynamic efficiency 热力学效率principle of entropy increase 熵增原理coefficient of performance 制冷系数compression refrigerating system 压缩式制冷系统Joule-Thomson effect 焦耳-汤姆森效应Maxwell relations 麦克斯韦关系式corresponding temperature 对比温度critical state property 临界状态性质compressibility factor 压缩因子英文 中文 英文 中文 英文 中文 dimensional analysis 量纲分析Thermodynamics热力学energy 能量activity coefficient 活度系数surroundings 环境heat 热excess property 超额性质mixing rule 混合规则work 功local composition 局部组成ideal work 理想功exergy 㶲phase equilibrium 相平衡 actualwork 实际功process 过程flash evaporation 闪蒸phase diagram 相图cycle 循环system 孤立体系path 路径degrees centigrade 摄氏温度 isolatedazeotropic point 恒沸点throttle valve 节流阀compression 压缩irreversible process 不可逆过程Carnot Cycle 卡诺循环refrigeration 制冷heating heat pump 供热热泵open system 开放体系heat pump 热泵forward circulation 正向循环function of state 状态函数pressure 压力throttling expansion 节流膨胀reverse cycle 逆向循环property 性质supercritical fluid 超临界流体Rankine Cycle 朗肯循环fugacity 逸度superheated steam 过热蒸汽supercritical 超临界entropy 熵reversible process 可逆过程heat pump cycle 热泵循环triple point 三相点regenerative cycle 回热循环closed system 封闭体系system 体系equilibrium constant 平衡常数booster pump 增压泵 dryness 干度degree of freedom 自由度partial pressure 分压enthalpy 焓equation of state 状态方程concentration 浓度gas 气体equilibrium state 平衡状态mole fraction 摩尔分数steam 汽体intensive property 强度性质working medium工质temperature 温度extensive property 广度性质air-conditioner 空调机expansion 膨胀relative volatility 相对挥发度eccentric factor 偏心因子valume 体积process parameter 过程变量gas constant 气体常数phase rule 相律inversion temperature 转变温度internal energy 内能liquid 液体overcooled liquid 过冷液体inversion curve 转变曲线refrigerator 冰箱cycle 再热循环turbine 透平机isothermal process 等温过程 reheatedchemical potential 化学势reduced pressure对比压力interface 分界面partial molar property 偏摩尔性质regular solution 正规溶液mixture 混合物criteria for equilibrium 平衡判据athermal solution无热溶液dew point 露点nonideal solution非理想溶液evaporator 蒸发器critical point 临界点ideal dilute solution 理想稀溶液refrigerator 制冷机bubble point 泡点vapor-liquid equilibrium汽液平衡reversible-work 可逆功condenser冷凝器spontaneous process 自发过程isobaric process 等压过程shaft work 轴功isentropic process 等熵过程isometric process等容过程flow work 流动功isenthalpic process 等焓过程residual property剩余性质lost work 损失功。
基于支持向量机的弗兰克-赫兹实验曲线拟合

本期推荐本栏目责任编辑:王力基于支持向量机的弗兰克-赫兹实验曲线拟合周祉煜1,孟倩2(1.河北师范大学物理学院,河北石家庄050024;2.江苏师范大学计算机科学与技术学院,江苏徐州221116)摘要:弗兰克-赫兹实验是“近代物理实验”中的重要实验之一,数据量大且数据处理复杂。
支持向量机是一种广泛应用于函数逼近、模式识别、回归等领域的机器学习算法。
本文将支持向量机算法应用于弗兰克-赫兹实验数据的拟合,过程简单,在python 环境下验证该方法拟合精度高,效果好。
支持向量机算法还可应用于其他的物理实验曲线拟合。
关键词:支持向量机;曲线拟合;弗兰克-赫兹实验;Python 中图分类号:TP18文献标识码:A文章编号:1009-3044(2021)13-0001-02开放科学(资源服务)标识码(OSID ):Curve Fitting of Frank Hertz Experiment Based on Support Vector Machine ZHOU Zhi-yu 1,MENG Qian 2(1.Hebei Normal University,College of physics.,Shijiazhuang 050024,China;2.School of Computer Science and technology,Jiang⁃su Normal University,Xuzhou 221116,China)Abstract:Frank-Hertz experiment is a classical experiment in modern physics experiments.It has a large amount of experimental data and a complicated data processing process.Support Vector Machine is a machine learning algorithm which widely used in function approximation,pattern recognition,regression and other fields.In this paper,support vector machine is used to do curve fitting for the experimental data of Frank-Hertz experiment.The process is simple,and the method is verified to have high curve fit⁃ting accuracy and good effect in python environment.SVM can also be applied to curve fitting in other physics experiments.Key words:support vector machine,curve fitting,Frank Hertz experiment ,python 1998年,Vapnik V N.等人[1]提出了一种新型的基于小样本和统计学习理论的机器学习方法-支持向量机(Support Vector Machine,SVM),该方法可以从有限的训练样本出发寻找“最优函数规律”,使它能够对未知输出作尽可能准确的预测,可应用于函数逼近、模式识别、回归等领域。
薛定谔—麦克斯韦尔方程径向解的存在性和多重性(英文)

In 1887, the German physicist Erwin Schrödinger proposed a radial solution to the Maxwell-Schrödinger equation. This equation describes the behavior of an electron in an atom and is used to calculate its energy levels. The radial solution was found to be valid for all values of angular momentum quantum number l, which means that it can describe any type of atomic orbital.The existence and multiplicity of this radial solution has been studied extensively since then. It has been shown that there are infinitely many solutions for each value of l, with each one corresponding to a different energy level. Furthermore, these solutions can be divided into two categories: bound states and scattering states. Bound states have negative energies and correspond to electrons that are trapped within the atom; scattering states have positive energies and correspond to electrons that escape from the atom after being excited by external radiation or collisions with other particles.The existence and multiplicity of these solutions is important because they provide insight into how atoms interact with their environment through electromagnetic radiation or collisions with other particles. They also help us understand why certain elements form molecules when combined together, as well as why some elements remain stable while others decay over time due to radioactive processes such as alpha decay or beta decay.。
《概率论与数理统计》基本名词中英文对照表

《概率论与数理统计》基本名词中英文对照表英文中文Probability theory 概率论mathematical statistics 数理统计deterministic phenomenon 确定性现象random phenomenon 随机现象sample space 样本空间random occurrence 随机事件fundamental event 基本事件certain event 必然事件impossible event 不可能事件random test 随机试验incompatible events 互不相容事件frequency 频率classical probabilistic model 古典概型geometric probability 几何概率conditional probability 条件概率multiplication theorem 乘法定理Bayes’s formula 贝叶斯公式Prior probability 先验概率Posterior probability 后验概率Independent events 相互独立事件Bernoulli trials 贝努利试验random variable 随机变量probability distribution 概率分布distribution function 分布函数discrete random variable 离散随机变量distribution law 分布律hypergeometric distribution 超几何分布random sampling model 随机抽样模型binomial distribution 二项分布Poisson distribution 泊松分布geometric distribution 几何分布probability density 概率密度continuous random variable 连续随机变量uniformly distribution 均匀分布exponential distribution 指数分布numerical character 数字特征mathematical expectation 数学期望variance 方差moment 矩central moment 中心矩n—dimensional random variable n—维随机变量two-dimensional random variable 二维离散随机变量joint probability distribution 联合概率分布joint distribution law 联合分布律joint distribution function 联合分布函数boundary distribution law 边缘分布律boundary distribution function 边缘分布函数exponential distribution 二维指数分布continuous random variable 二维连续随机变量joint probability density 联合概率密度boundary probability density 边缘概率密度conditional distribution 条件分布conditional distribution law 条件分布律conditional probability density 条件概率密度covariance 协方差dependency coefficient 相关系数normal distribution 正态分布limit theorem 极限定理standard normal distribution 标准正态分布logarithmic normal distribution 对数正态分布covariance matrix 协方差矩阵central limit theorem 中心极限定理Chebyshev’s inequality 切比雪夫不等式B ernoulli’s law of large numbers 贝努利大数定律statistics 统计量simple random sample 简单随机样本sample distribution function 样本分布函数sample mean 样本均值sample variance 样本方差sample standard deviation 样本标准差sample covariance 样本协方差sample correlation coefficient 样本相关系数order statistics 顺序统计量sample median 样本中位数sample fractiles 样本极差sampling distribution 抽样分布parameter estimation 参数估计estimator 估计量estimate value 估计值unbiased estimator 无偏估计unbiassedness 无偏性biased error 偏差mean square error 均方误差relative efficient 相对有效性minimum variance 最小方差asymptotic unbiased estimator 渐近无偏估计量uniformly estimator 一致性估计量moment method of estimation 矩法估计maximum likelihood method of estimation 极大似然估计法likelihood function 似然函数maximum likelihood estimator 极大似然估计值interval estimation 区间估计hypothesis testing 假设检验statistical hypothesis 统计假设simple hypothesis 简单假设composite hypothesis 复合假设rejection region 拒绝域acceptance domain 接受域test statistics 检验统计量linear regression analysis 线性回归分析。
新编化学化工专业英语

前几课翻译链接:/s/1o6qiyuQLesson 10 ThermodynamicsThermodynamics is the physics of energy, heat, work, entropy and the spontaneity of processes. Thermodynamics is closely related to statistical mechanics from which many thermodynamic relationships can be derived.热力学是物理能量,热,工作过程,熵和自发性。
热力学是密切相关的统计力学,热力学关系可以推导出。
While dealing with processes in which systems exchange matter or energy, classical thermodynamics is not concerned with the rate at which such processes take place, termed kinetics. For this reason, the use of the term “thermodynamics”usually refers to equilibrium thermodynamics. In this connection, a central concept in thermodynamics is that of quasistatic processes, which are idealized, “infinitely slow”processes. Time-dependent thermodynamic processes are studied by non-equilibrium thermodynamics.在处理中,系统交换物质或能量的过程,经典热力学不关心这些过程发生的速率,称为动力学。
Thermal Time Scales in a Color Glass Condensate

a r X i v :h e p -p h /0505199v 1 23 M a y 2005Thermal Time Scales in a Color Glass CondensateV.Parihar and A.WidomPhysics Department,Northeastern University,Boston MA 02115,USAY.N.SrivastavaPhysics Department &INFN,University of Perugia,Perugia,ITIn a model of relativistic heavy ion collisions wherein the unconfined quark-gluon plasma is con-densed into glass,we derive the Vogel-Fulcher-Tammann cooling law.This law is well known to hold true in condensed matter glasses.The high energy plasma is initially created in a very hot negative temperature state and cools down to the Hagedorn glass temperature at an ever decreas-ing rate.The cooling rate is largely determined by the QCD string tension derived from hadronic Regge trajectories.The ultimately slow relaxation time is a defining characteristic of a color glass condensate.PACS numbers:25.75.-q,25.75.Nq,24.85.+p,12.38.MhI.INTRODUCTIONThere has been considerable recent interest[1,2,3,4,5]in measurements of a possible quark-gluon plasma whose properties may be probed by relativistic heavy ion colli-sions (RHIC).Central to the study of a possible uncon-fined color plasma is the time scale required to form this thermodynamic fluid phase.The central question con-cerns how the phase formation time compares with the collision time of the heavy ion probes.The apparent experimentally observed suppression of heavy quark particle production has led to the notion that thermal formation times may be longer than might be at first expected.The notion of an unconfined color fluid plasma was,for some RHIC energies,replaced by the notion of a color glass condensate[6,7,8,9,10,11,12,13](CGC).In simple terms,thermal relaxation times in glasses are much longer than thermal relaxation times in fluids.If the thermal relaxation times were not much shorter than the RHIC collision times,then the observed heavy quark suppression becomes understandable.The thermal relaxation time in condensed matter glasses follows a well known and long established law due to Vogel[14],Fulcher[15]and Tammann[16](VFT).The thermal relaxation time depends on temperature accord-ing to the VFT rule[17]τ≈τ∞expΦ3¯hcσ2 II.PERTURBATION THEORETICAL QCDRecall the running coupling constant in QED,i.e.α(Q2)=e2π ∞0 ℑmε(−ν−i0+)ν.(5)For time-like wave vectors,the vacuum is dissipative ℑmε(−ν−i0+)≥0ifν=−Q2>0.(6) Among the processes contributing to the dissipative vac-uum Eq.(6)are the creation out of the vacuum of charged particle anti-particle pairs produced by incident electro-magnetic radiation.From Eqs.(5)and(6),it follows that for some space-like Q2>0,the real dielectric response will vanish.This constitutes the Landau ghost problem of QED.In particlular,the potential energy between two static charges,z1e and z2e is determined by the dielectric screening function e2→e2/ε(Q2)as discussed in stan-dard works on quantum electrodynamics[22];V(r)= z1z2e2π ∞0sin(Qr)dQ4π¯h cεs(Q2),(8) whereinεs(Q2)=−Q2ν+Q2 dνπ=−g24π 113n f(10)wherein N c is the number of colors and n f is the number offlavors.Note the conditionℑmεs(−ν−i0+)≤0(color amplifier),(11) which implies that the perturbation theory vacuum is in reality an excited QCD state which decays into the true vacuum[18].Unlike the perturbation theory QED vacuum which requires external radiation energy to pro-duce particle pairs,the perturbation theory QCD vac-uum spontaneously decays into the true vacuum radiat-ing bursts of hadrons.The excited state QCD perturba-tion theory vacuum is similar to an excited amplifying LASER material with inverted excitation energy levels. The Laser material spontaneously decays into the true ground state radiating a photon pulse.Amplifying me-dia may be described by a negative temperature.Ini-tial high energy particles blast the true vacuum into a QCD perturbation theory vacuum at negative tempera-ture.The resulting system then cools to the true vacuum radiating hadrons.When a very hot negative tempera-ture cools down the temperature keeps going down.The temperature goes down through T=−∞then appearing at T=+∞further cooling through decreasing positive temperatures.From Eqs.(9)and(11)it follows for space-like wave vectors thatεs(Q2)>0so there are no QCD Landau ghosts.The quark potentials are described in terms of the color screening functionV s(r)=ηab t1a t2b g2π ∞0sin(Qr)dQπ ∞0sin(Qr)QdQ2=limQ→0εs(Q2)2=−1ν2>0,(14) onefinds via Eqs.(13)and(14)thatlimr→∞χ′′s(r)=− 2L 2.(15) The central result of this section is a confining linear potentialV s(r)=−ηab t1a t2bσr as r→∞,(16) with a“string tension”σ= g23III.QCD STRINGSThe QCD string may be physically pictured as follows[23]:(i)Between two quarks with color charges t 1a g and t 2b g is a string.(ii)Inside the string is a gluon condensate electric fieldE =4πL 2.(18)(iii)The tension in the string isσ=g E .(19)(iv)Let us suppose two virtually zero mass quarks movewith light speed c on the ends of a linear string which extends along the straight line segment −a <r <a .In rigid body rotation|v |a (speed),Mc 2= a −aσdr 1−|v /c |2,=πσa,J =12c,J =M 2c 32πσ.(21)From experimental linear Regge trajectories¯h cσ≈0.18GeV 2.(22)The question arises as to the nature of quark-antiquark pair creation,i.e.jet production,in a scattering experiment wherein the incoming particles supply the en-ergy to create the gluon condensate within the string as well as supplying the quark pair energy (mc 2per quark).Quark motion along the string obeys Newton’s law for the rate of change of momentumdp¯h |mc 2|2δ(2cp ).(25)From the viewpoint of QCD string fragmentation,the probability that the string dissociates may be writtend 2P =dpdr drdt =dpdpdp,d 2P2π¯hexp − ¯νdp2π¯he −m2c 3/¯h g E=σ2πcσ=J.(28)In the quantum theory of the Boson (gluon)string,J hasthe spectrumJ =¯h NwhereN =0,1,2,3,....(29)If there are n k,j =0,1,2,3,....string excitations with polarization j each carrying angular momentum ¯h k with k =1,2,3,....,thenN =2j =1∞ k =1kn kj .(30)Eq.(30)gives rise to a statistical mechanical entropyproblem which involves analytical number theory.How many different ways Ωcan you form the integer N out of the smaller integers {n kj }?From the asymptotic solution[24]of an earlier and similar partitioning prob-lem,the solution to the QCD excitation string partition-ing problem was found[25].In the large N →∞limit,ln Ω(N )≈2π 3+ln (6N )−7/4√4 along with Eqs.(28),(29)and(31)wefind the Hagedornstring entropySk B T g −7k B T g +˜Sk B =13 .(33)The Hagedorn glass temperature isk B T g= 4π≈207MeV(34)where Eq.(22)has been invoked.The thermal equations of state for a hot string now follow from1∂E1T g−7k Bk B =7T−T g−7(T−Tg) +S∞(T>T g),S∞=limT→∞S(T)S∞2 1+ln2π2 +1Ωi=exp S f−S ik B (T>T g),τ=τ∞ T−T g k B(T−T g) (38)Eq.(38)is consistent with the VFT asymptotic Eq.(1) withΦ=7k B T g5[6]M.Gyulassy and L.McLerran,Nucl.Phys.A750,30(2005).[7]Dmitri Kharzeev and Kirill Tuchin,Nucl.Phys.A753,316(2005).[8]E.Iancu and R.Venugopalan in QGP3,R.Hwa andX.-N.Wang Editors,World Scientific,Singapore(2004).[9]J.Jalilian-Marian,Mod.Phys.Lett.A19,1251(2004).[10]Raju Venugopalan,hep-ph/0412396(2004).[11]E.Iancu,A.Leonidov,and L.McLerran,hep-ph/0202270(2002).[12]Raju Venugopalan,Comments Nucl.Part.Phys.22,113(1997).[13]A.Ayala,J.Jalilian-Marian,L.McLerran and R.Venu-gopalan,Phys.Rev.D52,2935(1995).[14]H.Vogel,Phys.Z.22,645(1921).[15]G.S.Fulcher,J.Am.Chem.Soc.8,339(1925);J.Am.Chem.Soc.8,789,(1925).[16]G.Tammann and W.Hesse,Z.Anorg.Allg.Chem.156,245(1926).[17]H.Tanaka,Phys.Rev.Lett.90,055701(2003).[18]Y.Srivastava,S.Pacetti,G.Pancheri and A.Widom,“Dispersive techniques forαs,R had and instability of the perturbative vacuum”,Invited talk at the conference “e+e−physics at intermediate energies workshop”,eConf C010430T19(2001).[19]ndau,in Neils Bohr and the Development ofPhysics,W.Pauli Editor,Pergamon Press,London (1955).[20]S.Sivasubramanian,Y.Srivastava and A.Widom,Mod.Phys.Lett.B161201(2002).[21]R.Hagedorn,Nuovo Cim.Suppl.3,147(1965)[22]V.B.Berestetskii, E.M.Lifshitz and L.P.Pitaevskii,Quantum Electrodynamics,§114,Butterworth-Heinemann,Oxford(1997).[23]Y.Srivastava and A.Widom,Phys.Rev.D6*******(2001).[24]G.H.Hardy and S.Ramanujan Proc.London Math.Soc.17,75(1918)[25]K.Huang and S.Weinberg,Phys.Rev.Lett.25,895(1970).。
研究和分析文本信息隐藏工具(IJCNIS-V5-N12-6)

I. J. Computer Network and Information Security, 2013, 12, 45-52Published Online October 2013 in MECS (/)DOI: 10.5815/ijcnis.2013.12.06Study and Analysis of Text Steganography ToolsIndradip BanerjeeDepartment of Computer Science & Engineering, National Institute of Technology,Durgapur, West Bengal, India.ibanerjee2001@Souvik BhattacharyyaDepartment Computer Science & Engineering,University Institute of Technology,Burdwan University, Burdwan, Indiasouvikbha@Gautam SanyalDepartment of Computer Science & Engineering, National Institute of Technology,Durgapur, West Bengal, India.nitgsanyal@Abstract — “Maintain the security of the secret information”, this words has been a great challenge inour day to day life. Sender can send messages regularly through a communication channel like Internet, drawsthe attention of third parties, hackers and crackers, perhaps causing attempts to break and expose the unusual messages. Steganography is a gifted region which is used for secured data transmission over any public media. Wide quantity of research work has been established by different researchers on steganography. Steganalysis is an art and science of detecting messages hidden using steganography. Some research work has also been remarked in the field of Steganalysis also. In this contribution, we have gone through steganalysis attack of some established text steganography tools.Index Term— Text Steganography, Text Steganalysis, Security, Cover Text, Stego TextI.I NTRODUC TIONInformation hiding is the ability to prevent or hidden certain aspects from being accessible to others excluding authentic user. It has many sub disciplines. One of the most important sub disciplines is steganography [1] which is derived from a work by Johannes Trithemus (1462-1516) entitled "Steganographia" and comes from the Greek language defined as "covered writing" [2]. It is an ancient art of hiding information in ways a message i s hidden in an innocent-looking cover media so that will not arouse an eavesdropper’s suspicion. Steganography diverges from cryptography in the sense that where cryptography focuses on keeping the contents of a message secret by encryption technique, steganography focuses on keeping the presence of a message secret [3], [4].Another form of information hiding is digital watermarking, which is the process that embeds data called a watermark, tag or label into a multimedia object such that watermark can be detected or extracted later to make an assertion about the object. The object may be an image, audio, video or text only [5], [6]. A hidden channel could be defined as a communications channel that transfers some kind of information using a method originally not intended to transfer this kind of information. Observers are unaware that a covert message is being communicated. Only the sender and recipient of the message notice it. Steganography works have been carried out on different media like images, video clips, text, music and sound [7], [4].In Image Steganography method the secret message is embedded into an image as noi se to it, which is nearly impossible to differentiate by human eyes [8], [9], [10]. In video steganography, same method may be used to embed a message [11], [12]. Audio steganography embeds the message into a cover audio file as noise at a frequency out of human hearing range [10]. One major category, perhaps the most difficult kind of steganography is text teganography or linguistic steganography because due to the lack of redundant information in a text compared to an image or audio. The text steganography is a method of using written natural language to conceal a secret message as defined by Chapman et al. [13].Figure 1: Types of Steganography46Study and Analysis of Text Steganography ToolsTEXT STEGANOGRAPHYThe affluence of electronic documented information available in the world as well as the exertion of serious linguistic analysis makes this an interesting medium for steganographic information hiding. Moreover the Text is one of the ancient media used in steganography. Letters, books and telegrams hide secret messages within their texts in earlier time i.e. before the electronic age comes. Text steganography refers to the hiding of information within text i.e. character-based messages. There are three basic categories of text steganography (Fig. 1) maintained here: format-based methods, random and statistical generation and linguistic methods.[14]i. Format-based methods [14]:This methods use the physical formatting of text as a space in which to hide information. Format-based methods usually modify existing text for hiding the steganographic text. Insertion of spaces or non-displayed characters, careful errors tinny throughout the text and resizing of fonts are some of the many format-based methods used in text steganography.ii. Random and statistical generation method [14]: This avoid comparison with a known plaintext, steganographers often resort to generating their own cover texts. Character sequences method hide the information within character sequences.iii. Linguistic methods [14]:The affluence of electronic documented information available in the world as well as the exertion of serious linguistic analysis makes this an interesting medium for steganographic information hiding.In case of text steganography, firstly, a secret message will be covered up in a cover-text by applying an embedding algorithm to produce a stego-text. The stego-text will then be transmitted by a communication channel to a receiver.TEXT STEGANALYS ISThe usage of text media, as a cover channel for secret communication, has drawn more attention [15]. This attention in turn creates increasing concerns on text steganalysis. At present, it is harder to find secret messages in texts compared with other types of multimedia files, such as image, video and audio [16-21]. In general, text steganalysis exploits the fact that embedding information usually changes some statistical properties of stego texts; therefore it is vital to perceive the modifications of stego texts. Previous work on text steganalysis could be roughly classified into three categories: format- based [22, 23], invisible character-based [24-26] and linguistics, respectively. Different from the former two categories, linguistic steganalysi s attempts to detect covert messages in natural language texts. In the case of linguistic steganography, lexical, syntactic, or semantic properties of texts are manipulated to conceal information while their meanings are preserved as much as possible[27].Due to the diversity of syntax and the polysemia of semantics in natural language, it is difficult to observe the alterations in stego texts. So far, many linguistic steganalysis methods have been proposed. In these methods, special features are designed to extend semantic or syntactical changes of stego texts. For example, Z.L. Chen [28] et al. designed the N-window mutual information matrix as the detection feature to detect semantic steganagraphy algorithms. Furthermore, they used the word entropy and the change of the word location as the semantic features [29, 30], which improved the detection rates of their methods. Similarly, C.M. Taskiran et al [31] used the probabilistic context-free grammar to design the special features in order to attack on syntax steganography algorithms. In the work mentioned above, designed features strongly affect the final performances and they can merely reveal local properties of texts. Consequently, when the size of a text is large enough, differences between Natural texts (NTs) and Stego texts (STs) are evident, thus the detection performances of the mentioned methods are acceptable. Whereas, when the sizes of texts become small, the detection rates decrease dramatically and cannot be satisfied for applications. In addition, some steganographic tool s have been improved in the aspectsof semantic and syntax for better camouflage [32]. Therefore, linguistic steganalysi s still needs further research to resolve these problems. Some more work on Text Steganalysi s has been discussed below.A. Linguistic Steganalysis Based on Meta Features and Immune Mechanism [33]: Linguistic steganalysi s depends on efficient detection features due to the diversity of syntax and the polysemia of semantics in natural language processing. This paper presents a novel linguistics steganalysis approach based on Meta features and immune clone mechanism. Firstly, Meta features are used to represent texts. Then immune clone mechanism is exploited to select appropriate features so as to constitute effective detectors. Our approach employed Meta features as detection features, which is an opposite view from the previous literatures. Moreover, the immune training process consi sts of two phases which can identify respectively two kinds of stego texts. The constituted detectors have the capableof blind steganalysis to a certain extent. Experiments show that the proposed approach gets better performance than typical existing methods, especially in detecting short texts. When sizes of texts are confined to 3kB, detection accuracies have exceeded 95.B. Research on Steganalysis for Text Steganography Based on Font Format [34]: In the research area of text steganography, algorithms based on font format have advantages of great capacity, good imperceptibility and wide application range. However, little work on steganalysis for such algorithms has been reported in the literature. Based on the fact that the statistic features of font format will be changed after using font-format-based steganographic algorithms, we present a novel Support Vector Machine-based steganalysis algorithm to detect whether hidden information exists or not. This algorithm can not only effectively detect the existence of hidden information,but also estimate the hidden information length according to variations of font attribute value. As shown by experimental results, the detection accuracy of our algorithm reaches as high as 99.3 percent when the hidden information length is at least 16 bits.The dimensionality of data from text file is normally huge; it is unrealistic to use the data directly for steganalysis. A feasible approach is to extract certain amount of data from the text and use them to represent the text itself for steganalysis. The features for steganalysis should reflect minor distortions associated with data hiding.Moments based FeatureTo construct the features of both cover and stego or suspicious text several moments of the series has been computed. In mathematics, a moment is, loosely speaking, a quantitative measure of the shape of a set of points. The "second moment", for example, is widely used and measures the "width" of a set of points in one dimension or in higher dimensions measures the shape of a cloud of points as it could be fit by an ellipsoid. Other moments describe other aspects of a distribution such as how the distribution is skewed from its mean, or peaked. There are two ways of viewing moments [35], one based on statistics and one based on arbitrary functions such as f (x ) or f (x , y ).Statistical view: Moments are the statistical expectation of certain power functions of a random variable. The most common moment is the mean which is just the expected value of a random variable as given in 1.∫∞∞−==dx x xf X E )(][µ(1)where f (x ) is the probability density function of continuous random variable X . More generally, moments of order p = 0, 1, 2, … can be calculated as m p = E[X p ].These are sometimes referred to as the raw moments. There are other kinds of moments that are often useful. One of these is the central moments])[(p p X E µµ−=. The best knowncentral moment is the second, which is known as the variance, given in 2.21222)()(µµσ−=−=∫m dx x f x(2)Two less common statistical measures, skewness and kurtosis, are based on the third and fourth central moments. Moments are easily extended to two or more dimensions as shown in 3.∫∫==dxdy y x f y x Y X E m qp q p pq ),(][ (3)Here f (x , y ) is the joint pdf.Estimation: However, moments are easy to estimate from a set of measurements, x i . The p -th moment is estimated as given in 4 and 5.∑−=Ni p ip xNm 11 (4)(Often 1/N is left out of the definition) and the p -th central moment is estimated as∑−=ip ip x xN)(1µ(5)x is the average of the measurements, which is theusual estimate of the mean. The second central moment gives the variance of a set of data 22µ=s . For multidimensional distributions, the first and second order moments give estimates of the mean vector and covariance matrix. The order of moments in two dimensions is given by p +q , so for moments above 0, there is more than one of a given order. For example, m 20, m 11, and m 02are the three moments of order 2.Non-statistical view: This view is not based on probability and expected values, but most of the same ideas still hold. For any arbitrary function f (x ), one may compute moments using the equation 6 or for a 2-D function using 7.∫∞∞−=dx x f xm pp )((6)∫∫=dxdy y x f y x m q p pq ),((7)Notice now that to find the mean value of f (x ), one must use m 1/m 0, since f (x ) is not normalized to area 1 like the pdf. Likewise, for higher order moments it is common to normalize these moments by dividing by m 0(or m 00). This allows one to compute moments which depend only on the shape and not the magnitude of f (x ). The result of normalizing moments gives measures which contain information about the shape or distribution (not probability dist.) of f (x ).Digital approximation: For digitized data, we must replace the integral with a summation over the domain covered by the data. The 2-D approximation is written in 8.∑∑∑∑−−−−==M i Nj q p M i N j q jp ij i pq j i j i f y x y x f m 1111),(),((8)If f (x , y ) is a binary matrix function of an object, the area is m 00, the x and y centroids are 9 and 10.0010/m m x =(9)0001/m m y = (10)To implement the attack of text Steganography we use some stego text from some available steganography tools which are discussed below.SNOW DOS 32 [37]: The encoding system used by snow depend on the fact that spaces and tabs (known as whitespace ), when appearing at the end of lines, are invisible when presented in pretty well all text viewing programs. This allows messages to be hidden in ASCII text without affecting the text's visual representation. And since trailing spaces and tabs occasionally occur naturally, their existence should not be sufficient to immediately alert an observer who stumbles across them.wbS tego4.3open [36]: This module of steganography has been published under the GNU General Public License (GPL). wbStego uses a custom mechanism for localization. All information is stored in the data file, which consists of a number of blocks, all introduced by a 3 byte header specifying the size of the block. The file is a terminated by 3 bytes set to 0, i.e. a block header without data block.In this paper, we have analyzed the text steganalysi s by the help of statistical moment’s technique using two of steganography tools. After wide research on steganography by author’s previous work [11], [12], [13], [14], [15], [16], [17], [18], [33], [34], author is going to start work on the analysis part of text steganography.This paper is organized into the following sections. Section II describes the proposed model. Analyses of the results are in section III. The last section descries the concluded part of the work.II. P ROPOSED M ODELText steganalysis, at all this paper exactly deals with, uses two steganography tools (SNOW DOS 32 and wbStego4.3open). We have selected a cover and then create stego text by inserting various length of secret message. After that find out the moments up to 10 orders and observed that wbStego4.3open is better than SNOW DOS 32 at the side of embedding capacity.Figure 4: 2nd Order Moment values of SNOW & wbStego4.3open.Here we have observed that the value of moment in various length has changes. Simultaniously it also occurs in between 2nd order moment to 10th order moment which is furnished in Figure 2 and Figure 3 of SNOW DOS 32 and wbStego4.3 open steganography softwares.A. Solution MethodologyThe proposed system involves two software windows i.e. SNOW DOS 32 and wbStego4.3open. The user will be someone who is aware with the process of information hiding and will have adequate knowledge of steganography systems. The user first selects the plain text message from a file or enters text in specified area of software, another text to be used as the carrier (cover text). Then every tool will hide the message in the selected cover text and will procedure the stego text. Then create stego in various length of message and find out the moments which are shown in Fig. 2 and 3. After the comparison in between these values it has been observed that the system wbStego4.3open has minimum changes found for each order of moment (Fig. 4, Fig. 5), whereas the SNOW DOS 32 graph is decreasing for increase of embedding capacity.III.E XPERIMENTAL R ESULTSThe steganalyzer has been designed based on a training set and using various text steganographic tools. The steganographic tools used here SNOW DOS 32 & wbStego4.3open. In the experiments one cover and 30 input message were used for training and 20 cover text for testing. These experiments are performed using a large data set of text document obtained from publicly available websites. The data set i s categorized with respect to different features of the text to determine their potential impact on steganalysis performance. Fig.6 and Fig.7 shows that the graphical representation of 2nd Order Moment of SNOW DOS 32 and wbStego4.3open. Here it has been observe that the graph SNOW is decreasing for high embedding where as the wbStego graph is increasing for high embedding. So it has proved that the performance and capasity of wbStego is better than SNOW.IV.C ONCLUSIONSIn this paper, text based steganalysi s techniques of some module is tested based on moments and other similarity measure feature to evaluate what is the best. The plane text has been selected as an estimate of the cover-object. Next step is to use stati stical, invariant and other similarity measure features to measure the distortion and to determine the presence of hidden information in a text. Results from moments with numerous text series showed that the proposed steganalysis algorithm provides significantly better analysi s rates than existing ones. The author’s future goal is to compare these tool s with author’s own generic module of steganography.Figure 5: 7th Order Moment values of SNOW &wbStego4.3open.Figure 6: 2nd Order Moment graph of wbStego4.3open.Figure 7: 2nd Order Moment graph of SNOW.R EFERENCES[1]Fabien A.P. Petitcolas, Ross J. Anderson, MarkusG. Kuhn: Information Hiding—A Survey,Proceedings of the IEEE, Vol. 87, No. 7, July1999, pp. 1062-1078, ISSN 0018-9219.[2]K. Bennett. Linguistic steganography: Survey,analysis, and robustness concerns for hiding information in text. Purdue University, CERIASTech. Report, 2004.[3]Ross J. Anderson. and Fabien A.P.Petitcolas. Onthe limits of steganography. IEEE Journal onSelected Areas in Communications (J-SA C),Special Issue on Copyright and Privacy Protection,16:474–481, 1998.[4]JHP Eloff T Mrkel and MS Olivier. An overviewof image steganography. In Proceedings of thefifth annual Information Security South AfricaConference, South Africa, 2005.[5]S.P.Mohanty. Digital watermarking: A tutorialreview. International Journal of Digital Evidence,Fall 2003, 2003.[6]N.F.Johnson. and S. Jajodia. Steganography:seeing the unseen. IEEE Computer, 16:26–34,1998.[7]Kran Bailey Kevin Curran. An evaluation of imagebased steganography methods. InternationalJournal of Digital Evidence,Fall 2003, 2003.[8] D. Kahn. The codebreakers - the comprehensivehistory of secret communication from ancient times to the internet. Scribner, 1996.[9]Z. Duric N. F. Johnson and S. Jajodia. Informationhiding: Steganography and digital watermarking -attacks and countermeasures. Kluwer Academic,2001.[10]S. Low N.F. Maxemchuk J.T. Brassil and L.O.Gorman. Electronic marking and identificationtechniques to discourage document copying. IEEEJournal on Selected Areas in Communications,13:1495–1504, 1995.[11]G. Doerr and J.L. Dugelay. Security pitfalls offramebyframe approaches to video watermarking.IEEE Transactions on Signal Processing, Supplement on Secure Media., 52:2955–2964,2004.[12]G. Doerr and J.L. Dugelay. A guide tour of videowatermarking. Signal Processing: ImageCommunication., 18:263–282, 2003.[13]Kran Bailey Kevin Curran. An evaluation of imagebased steganography methods. 1999.[14]Krista Bennett (2004). " Linguistic Steganography:Survey, Analysis, and Robustness Concerns forHiding Information in Text". CERIAS TR 2004-13.[15]F.A.P. Petitcolas, R.J. Anderson, M.G. Kuhn,“Information hiding - a survey”, Proceedings ofthe IEEE, Vol.87, No.7, pp.1062–1078, 1999. [16]C. Kraetzer, J. Dittmann, “Pros and cons ofmelcepstrum based audio steganalysis using SVMclassification”, The 9th International Workshop onInformation Hiding, Saint Malo, France, pp.359–377, 2007.[17]M.E. Choubassi, P. Moulin, “Noniterativealgorithms for sensitivity analysis attacks”, IEEETransactions on Information Forensics and Security, Vol.2, No.3, pp.113–126, 2007.[18]O.H. Kocal, E. Avcibas, “Chaotic-type features forspeech steganalysis”, IEEE Transactions on Information Forensics and Security, Vol.3, No.4,pp.651–661, 2008.[19]Z.J. Wu, Y. Hu, X.X. Niu, H.X. Duan, X. Li,“Information hiding technique based speech securecommunication over PSTN”, Chinese Journal ofElectronics, Vol.15, No.1, pp.108–112, 2009. [20]H. Shan, K. Darko, “An estimation attack oncontent-based video fingerprinting”, Transactionson Data Hiding and Multimedia Security II,Vol.4499, No.2007, pp.35–47, 2007.[21]R. Bohme, “Weighted stego-image steganalysi sfor JPEG covers”, The 10th International Workshop on Information Hiding, Santa Barbara,California, USA, pp.178–194, 2008.[22]L.J. Li, L.S. Huang, X.X. Zhao, W. Yang, Z.L.Chen, “A statistical attack on a kind of word-shifttext-steganography”, The 4th International Conference on Intelligent Information Hiding andMultimedia Signal Processing, Harbin, China,pp.1503–1507, 2008.[23]L.Y. Xiang, X.M. Sun, G. Luo, C. Gan, “Researchon steganalysis for text steganography based onfont format”, The 3rd International Symposium onInformation Assurance and Security, Manchester,United Kingdom, pp.490–495, 2007.[24]J.W. Huang, X.M. Sun, H. Huang, G. Luo,“Detection of hidden information in webpagesbased on randomness”, The 3rd InternationalSymposium on Information Assurance andSecurity, Manchester, United kingdom, pp.447–452, 2007.[25]H.J. Huang, X.M. Sun, Z.H. Li, G. Sun,“Detection of steganographic information in tagsof webpage”, The 2nd International Conference onScalable Information Systems, Brussels, Belgium,pp.325–328, 2007.[26]H.J. Huang, S.H. Zhong, X.M. Sun, “Steganalysisof information hidden in webpage based onhigher-order statistics”, Proceedings of theInternational Symposium on Electronic Commerceand Security, ISECS 2008, Guangzhou, China,pp.957–960, 2008.[27]M. Chapman, G.I. Davida, M. Rennhard, “Apractical and effective approach to large scaleautomated linguistic steganography”, The 4thInternational Conference on Information andCommunications Security, Venice, Italy, pp.156–165, 2007.[28]Z.L. Chen, L.S. Huang, Z.Z. Yu, W. Yang, L.J. Li,X.L. Zheng, X.X. Zhao, “Linguistic steganographydetection using statistical characteristics ofcorrelations between words”, The 11thInternational Workshop on Information Hiding,Darmstadt, Germany, pp.224–235, 2008.[29]Z.L. Chen, L.S. Huang, Z.S. Yu, X.X. Zhao, X.L.Zheng, “Effective linguistic steganographydetection”, The 8th IEEE International Conferenceon Computer and Information TechnologyWorkshops, Sydney, Australia, pp.224–229, 2008. [30]Z.L. Chen, L.S. Huang, Z.S. Yu, L.J. Li, W. Yang,“A statistical algorithm for linguisticsteganography detection based on distribution ofwords”, The 3rd International Conference onAvailability, Security, and Reliability, Barcelona,Spain, pp.558–563, 2008.[31]C.M. Taskiran, U. Topkara, M. Topkara, E.J. Delp,“Attacks on lexical natural languagesteganography systems”, Proceedings of SPIEInternational Society for Optical Engineering,Society of Photo-Optical InstrumentationEngineers, San Jose, USA, pp.97–105, 2006.[32]K. Bennett, “Linguistic steganography: Survey,analysis, and robustness concerns for hidinginformation in text”, Purdue University, Indiana,USA, 2004.[33]YA NG Hao and CAO Xianbin “ LinguisticSteganalysis Based on Meta Features and ImmuneMechanism “Chinese Journal of Electronics,Vol.19, No.4, Oct. 2010[34]Lingyun Xiang, Xingming Sun, Gang Luo, CanGan. “Research on Steganalysis for TextSteganography Based on Font Format”, The ThirdInternational Symposium on InformationAssurance and Security (IAS 2007), Manchester, United Kingdom , August 2007. [35] MOMENTS IN IMA GE PROCESSING Bob Bailey Nov. 2002 [36] Available online: http://home.tele2.at/wbailer/wbstego/wbs4devdoc .html [37] Available online: .au/snow/ [38] Indradip Banerjee, Souvik Bhattacharyya and Gautam Sanyal. “Novel text steganography through special code generation.” In Proceedings of International Conference on Systemics,Cybernetics and Informatics (ICSCI-2011), Hyderabad,India., Jan 5-8, 2011. [39] Indradip Banerjee, Souvik Bhattacharyya and Gautam Sanyal. “The text steganography using article mapping technique(AMT) and SSCE”. Journal of Global Research in Computer Science, 2, April 2011. [40] Souvik Bhattacharyya, Indradip Banerjee and Gautam Sanyal. Design and implementation of a secure text based steganography model. In 9th annual Conference on Security and Management (SAM) under The 2010 World Congress in Computer Science,Computer Engineering and Applied Computing(WorldComp 2010), Las Vegas,USA, July 12-15,2010. [41] Souvik Bhattacharyya, Indradip Banerjee and Gautam Sanyal. Implementation of a novel text based steganography model. In National Conference on Computing and Systems (NACCS), Dept. of Computer Science, The University of Burdwan, Burdwan,India., Jan 29, 2010. [42] Souvik Bhattacharyya, Indradip Banerjee and Gautam Sanyal. A novel approach of secure text based steganography model using word mapping method(WMM). International Journal of Computer and Information Engineering 4:2 2010 - World Academy of Science, Engineering and Technology (WASET), 4:96103, Spring 2010. [43] Souvik Bhattacharyya, Indradip Banerjee, Arka Prokash Mazumdar and Gautam Sanyal. Text steganography using formatting character spacing. IJICS, 13, Decembar, 2010. [44] Souvik Bhattacharyya, Indradip Banerjee and Gautam Sanyal. A survey of steganography and steganalysi s technique in image, text, audio and video as cover carrier. Journal of Global Research in Computer Science, 2, April 2011. [45] Indradip Banerjee, Souvik Bhattacharyya and Gautam Sanyal. An Approach of Quantum Steganography through Special SSCE Code. International Journal of Computer and Information Engineering - World Academy of Science, Engineering and Technology (WASET), Issue 0080:2011, Article 175, Page: 939-946. [46] Indradip Banerjee, Souvik Bhattacharyya and Gautam Sanyal. Text Steganography through Quantum Approach. In Journal on Wireless Networks And Computational Intelligence, Communications in Computer and Information Science, 2012, Volume 292, Part 7, 632-643, DOI:10.1007/978-3-642-31686-9_74 Springer-Verlag Berlin Heidelberg 2012.[47] Indradip Banerjee, Souvik Bhattacharyya and Gautam Sanyal. "A Procedure of Text Steganography Using Indian Regional Language"Journal on "I. J. Computer Network and Information Security, 2012, v. 8, p. 65-73"Published Online August 2012 in MECS.Indradip Banerjee is a Research Scholar at National Institute ofTechnology, Durgapur, West Bengal, India. He received his MCA degree from IGNOU in 2009, PGDCA from IGNOU in 2008, MMM from Annamalai University in 2005 andBCA (Hons.) from The University of Burdwan in 2003. He is pursuing his PhD. in Engineering at Computer Science and Engineering Department, National Institute of Technology, Durgapur, West Bengal, India. His areas of interest are Steganography, Cryptography, Text Steganography, Image Steganography, Quantum Steganography and Steganalysis. He has published 16 research papers inInternational and National Journal s / Conferences. Souvik Bhattacharyya received his B.E. degree in Computer Science and Technology from B.E. College, Shibpur, India and M.Techdegree in Computer Science and Engineering from National Institute of Technology, Durgapur, India. Currently he is working as an Assistant Professor and In-Charge in Computer Science and Engineering Department at University Institute of Technology, The University of Burdwan. His areas ofinterest are Natural Language Processing, Network Security and Image Processing. He has published nearly 65 papers in International and National Journals / Conferences.Gautam Sanyal has received his B.E and M.Tech degree National Institute of Technology (NIT), Durgapur, India. He has receivedPh.D (Engg.) from Jadavpur University, Kolkata, India, in the area of Robot Vision. He possesses an experience of more than 25 years in the field of teaching and research. He has published nearly 150 papers in International and National Journals / Conferences. Two Ph.Ds (Engg) have already beenawarded under his guidance. At present he is guidingsix Ph.Ds scholars in the field of Steganography,。
制冷与空调专业英语词汇

制冷与空调专业英语词汇初级词汇环境surroundings热库hot source热源heat source冷源heat sink , cold source焓enthalpy熵entropy功work热量heat能量守恒energy conservation 理想气体idea gas真实气体actual gas沸点boiling point凝结condensation沸腾boiling池内沸腾pool boiling膜态沸腾film boiling相变change of phase压缩compression膨胀expansion节流throttling潜热latent heat显热sensible heat制冷refrigeration氟利昂11 freon 11氟利昂12 freon 12氟利昂13 freon 13氟利昂14 freon 14氟利昂22 freon 22制冷剂refrigerant氨ammonia二氧化碳carbon dioxide二氧化硫sculpture dioxide甲烷methane乙烷ethane丙烷propane乙烯ethylene稳态Steady state非稳态unsteady state传热学heat transfer传热heat transmission 换热heat exchange热流heat flow吸收率absorptive反射率reflectivity熔化fusion熔点melting point升华sublimation三相点triple point临界状态critical state临界温度critical temperature临界压力critical pressure凝固solidification凝固点solidification point沸点boiling point凝结condensation摄氏温度centigrade scale放气管air bleeder散气式通风air blow aeration鼓风机air blower吹气,空气吹污air blowing吹气管air blowpipe压缩空气瓶air bottle空气室air box空气制动器air brake排气孔air bleed hole空气室air barrel湿蒸气wet vapor过热superheat过热蒸气superheated vapor过热度degree of superheat过冷sub cooling过冷液体sub cooled liquid气-液混合物liquid-vapor mixture 干度quality冷凝点condensation point冷凝液condensate共沸混合物isentropic mixture共沸性zoetrope共沸点isentropic point辐射radiation核态沸腾nucleate boiling对流沸腾convective boiling膜状凝结film condensation珠状凝结drop condensation饱和状态saturation state饱和温度saturation temperature饱和压力saturation pressure饱和液体saturation liquid饱和蒸气saturation vapor饱和蒸气压saturated vapor pressure 过饱和supersaturating过饱和蒸气supersaturated vapor热力过程thermodynamic process等温过程isothermal process等压过程isobaric process等容过程isochoric process绝热过程adiabatic process绝热指数adiabatic exponent多变过程polytrophic process多变指数polytrophic exponent等焓过程isenthalpic process等熵过程isentropic process可压缩性compressibility热流量heat flow rate热流密度density of heat flow rate温度场temperature field导热heat conduction导热系数thermal conductivity热扩散系数thermal diffusivity对流换热convective heat transfer自然对流free convection强制对流forced convection等焓膨胀isenthalpic expansion热阻thermal resistance接触热阻thermal contact resistance 热滞后thermal lag传质mass transfer分子扩散molecule diffusion对流扩散convective diffusion绝热膨胀adiabatic expansion多变膨胀polytropic expansion节流膨胀throttling expansion 等焓节流isenthalpic throttling热力循环thermodynamic cycle工质working substance热机循环engine cycle制冷循环refrigeration cycle可逆循环reverse cycle卡诺循环Carnot cycle逆卡诺循环reverse Carnot cycle朗肯循环Rankine cycle斯特林循环Stirling cycle空气制冷循环air refrigeration池内沸腾pool boiling膜态沸腾film boiling核态沸腾nucleate boiling对流沸腾convective boiling膜状凝结film condensation珠状凝结drop condensation绝热压缩adiabatic compression多变压缩polytropic compression压缩指数compression exponent冰熔当量ice melting equivalent理论功率idea power指示功率indicated power指示效率indicated efficiency轴功率shaft horse power机械效率mechanical efficiency总效率Overall efficiency制冷系数coefficient of performance 空调负荷air conditioning load气流组织air distribution气流组织air distribution空气处理单元air handling unit风淋室air shower制冷工程refrigeration engineering 制冷工作者refrigerationist制冷工程师refrigeration engineer 制冷技术员refrigeration technician 制冷技工refrigeration mechanic 辐射换热radiation heat transfer对流放热系数the convective coefficient of heat transfer热力学thermodynamics统计热力学statistical thermodynamic 热力学系统thermodynamic system 孤立系isolated system热力学平衡状态thermodynamicequilibrium state 制冷剂循环量circulating mass ofrefrigerant可逆过程reversible process不可逆过程irreversible process热力学第一定律first law ofthermodynamics热力学第二定律Second law ofthermodynamics热力学第三定律third law ofthermodynamics零定律zero principle内能internal energy理想气体状态方程idea gas stateequation理想气体常数perfect gas constant 压缩性系数coefficient ofcompressibility压力-比容图pressure and specificvolume diagram温度-熵图temperature - entropydiagram双级压缩制冷循环two-stage compression refrigeration cycle氨双级压缩制冷循环ammoniatwo-stage compression refrigeration cycle氟利昂双级压缩制冷循环freontwo-stage compression refrigeration cycle覆叠式制冷循环cascade refrigeration 辐射换热系数radiation heat transfer coefficient传热系数the coefficient of heat transfer 平壁传热heat transfer through a plate 圆管传热heat transfer through a tube 肋壁传热heat transfer through a fin wall吸收式制冷循环absorption refrigeration cycle蒸气压缩制冷循环vapor compression refrigeration cycle液态制冷剂过冷循环liquid refrigerat subcooled cycle蒸气过热循环vapor supor superheated cycle混合制冷剂制冷循环mixture cycle焦耳-汤姆逊效应Joule Thomson effect焦耳-汤姆逊系数Joule Thomson coefficient蒸气喷射制冷循环vapor jet refrigeration cycle制冷剂循环容积circulating volume of refrigerant单位压缩功compress work per mass 热力完善度thermodynamic perfect degree制冷安装技工refirgeration installation mechanic制冷维修技工refrigeration serviceman 单位轴功率制冷量refrigreation effect per shaft horse-power运转工况下的制冷量rating under working conditions产冷量refrigerating capacity制冷量refrigerating effect单位制冷量refrigerating capacity per weighing单位容积制冷量refrigerating capacity per unit of swept volume容积效率V olumetric efficiency冷凝热量condenser heat过冷热量heat of subcooling标准制冷量Standard rating直接回水系统direct return system。
identical objects翻译

identical objects翻译identical objects的中文翻译为“相同的物体”,它指的是在某个集合中,所有的对象具有相同的性质与特征。
在数学、物理、统计学等领域,identical objects通常被用来研究各种问题,比如组合数学、熵、热力学等等。
以下是五条双语例句:1. The model assumed that all particles in the system were identical objects.模型假设系统中的所有粒子都是相同的。
2. In combinatorics, the problem of counting the number of ways to arrange identical objects is known as a permutation.在组合数学中,计算排列相同对象的方式的问题被称为排列。
3. The concept of identical objects plays a fundamental role in the study of entropy in statistical mechanics.相同物体的概念在统计力学中的熵的研究中起着基础性的作用。
4. The identification of identical objects is sometimes a challenging problem in computer vision.在计算机视觉中,确定相同物体的身份是有时候具有挑战性的问题。
5. The principle of indistinguishability states that identical objects cannot be distinguished from each other, even in theory.不可分辨性原则表明,相同的物体即使在理论上也不能被区分开来。
水溶液中蛋白质的热力学性质

D O I :10.3969/j.i s s n .1001-5337.2021.1.072 *收稿日期:2020-08-24基金项目:国家自然科学基金(11675090);山东省高等教育教学改革项目(10446201605);鲁东大学大学生创新创业训练计划项目.通信作者:孔祥木,男,1963-,博士,教授;研究方向:统计物理与复杂系统;E -m a i l :k o n gx m 668@163.c o m.水溶液中蛋白质的热力学性质*张秀颖①, 张盼盼①, 王 杰②, 徐玉良①, 孔祥木①(①鲁东大学物理与光电工程学院,264025;②海军航空大学,265401,山东省烟台市) 摘要:采用偶极子溶剂模型,应用平均场理论研究了水溶液中蛋白质系统的热力学性质.计算了系统的配分函数,得到了水分子的平均偶极矩㊁系统自由能㊁熵和热容量的解析表达式,讨论了它们随温度的变化规律.研究发现,平均偶极矩随温度的升高线性减小;蛋白质的熵随温度的升高逐渐增大;相同温度时,恒定电场下的热容值要大于恒定偶极矩下的热容值,恒定电场热容和恒定偶极矩热容随温度的变化规律也不相同,恒定电场热容在变性点具有极大值.关键词:蛋白质;平均场理论;平均偶极矩;熵;热容中图分类号:O 414.2 文献标识码:A 文章编号:1001-5337(2021)01-0072-040 引 言蛋白质是构成生物最基本的生物高分子,由二十多种大小和电荷有很大差异并且侧链基团极性不同的氨基酸脱水缩合组成,在所有生物的生命体内起着不可或缺的作用.氨基酸和肽链还未折叠形成蛋白质时的状态就是我们所说的蛋白质的展开状态的一种;而另一种蛋白质的展开,就是蛋白质变性.十多年来,人们对蛋白质体系在水溶液中的热力学性质进行了研究.P r i v a l o v 等人先后在实验上测定了不同种类蛋白质的热容㊁吉布斯函数和焓等热力学量[1,2].H a y n i e 和F r e i r e 用D S C 方法测定了蛋白质在折叠/伸展转变时的焓变[3].O y l u m l u o gl u 用巨正则系综理论计算了水溶液中蛋白质M b,L y s ,C y t ,R n s 的熵㊁焓㊁热容以及吉布斯函数随温度的变化,并与P r i v a l o v 等的实验数据进行了对照,发现理论值与实验值符合得很好[4-6].热容是表征化学变化非常重要的热力学量,熵也是重要的热力学函数.通过对相关热力学函数的研究,我们可以更深入地理解蛋白质的折叠态与伸展态[7].2002年B a k k 等人采用正则系统的方法研究了水溶液中蛋白质的热容(电场恒定),讨论了热容随温度的变化[8].本文采用W a r s h e l 和L e v i t t 提出的偶极子溶剂模型[9],用统计物理中的正则系综理论研究蛋白质水溶液系统的热力学性质.以M b ,L ys ,C yt ,R n s 4种蛋白质为例,讨论平均偶极矩㊁熵和热容量随温度的变化特性.1 偶极子溶剂模型及配分函数我们考虑水溶液中的蛋白质系统.按照F r a n k和E v a n s 提出的模型,可以将蛋白质周围的水看作像冰一样的刚性有序结构[10,11].将水分子看成经典电偶极子,类似于蛋白质给它加了一个外电场ε⇀,电偶极矩s ⇀在蛋白质周围有序排列.在电场ε⇀的作用下电偶极矩s ⇀具有能量E =-ε⇀㊃s ⇀,为了计算简单令s ⇀=1,则有E =-εc o s θ,(1)其中θ是电场ε⇀与偶极矩s ⇀之间的夹角.方程(1)是B a k k 和H o ye 在研究中用到的水合作用模型[12,13].在蛋白质折叠过程中,最先提出把溶剂水当做偶极子处理的是W a r s h e l 和L e v i t t [9],后来R u s s e l 和W a r s h e l [14]以及A v b e l j [15]也在处理蛋白质问题的过程中应用了这一模型.在一对水分子i 和j 之间存在着相互作用,其相互作用能为E i j =-J i j ㊃s ⇀i ㊃s ⇀j ,(2)其中J i j 是耦合常数,s ⇀i 和s ⇀j 分别是水分子i 和j第47卷 第1期2021年1月 曲阜师范大学学报J o u r n a l o f Q u f u N o r m a l U n i v e r s i t yV o l .47 N o .1J a n .2021的偶极矩.在平均场理论中[16],等式(2)中的相互作用类似于在方程(1)中加在ε上的附加电场,最终获得等效电场εe .把等式(1)和(2)联立可以得到E e θ()=εec o s θ+12b m 2,(3)其中εe =ε+b m ,b =ðj J i j ,m =<c o s θ>是平均偶极矩.在等式(3)中12b m 2来源于对相互作用重复计算的消除[17,18].设每个蛋白质分子周围都有N 个水分子,考虑系统处在平衡态的情况.在正则系综中此系统的配分函数可写为Z =ʏ2π0d φʏπd θs i n θe x p -βE e θ()()[]N=Z e e x p -βb m 22æèçöø÷éëêêùûúúN,(4)其中Z e =4πs i n h (εe )βεe .(5)2 蛋白质的热力学性质2.1 平均偶极矩按照正则系综理论,利用配分函数(4)式可得到平均偶极矩[8]m =c o t h εe k T æèçöø÷-k T εe,(6)上式也可以写为m =c o t h εe R T æèçöø÷-R T εe.(7)在(7)式中,我们把玻尔兹曼常数k 用气体常数R 代换,相应的ε与b 变成每摩尔的能量.对比m 的表达式(6)和(7)可以看出m 的数值并没改变,只是研究对象由一个蛋白质分子变为一摩尔蛋白质.图1给出了M b ,L y s ,C yt ,R n s 等4种蛋白质系统的平均偶极矩m 随温度T 的变化关系,参数ε,b 和N的取值列于表1中[8].可以看出,平均偶极矩随温度呈近似线性递减变化,即随着温度的升高c o s θ的平均值越来越小,说明水分子在蛋白质周围变得越来越杂乱无章.为了分析平均偶极矩随温度的变化规律,我们对图1中的计算结果进行了线性拟合,得到了平均偶极矩随温度的变化关系M (M b ,L y s ,C yt )=1.152-0.0016T ,(8)M (R n s )=1.150-0.0015T .(9)其中(8)式对应于蛋白质M b ,L y s 和C yt ,(9)式对应于蛋白质R n s .线性拟合的结果也画在了图1中,可以看出根据(7)式计算结果基本上是线性变化的.图1 平均偶极矩随温度的变化曲线其中实心圆是根据(7)式计算的结果,实线是线性拟合结果:(a )蛋白质M b ,L y s ,C yt ;(b )蛋白质R n s .表1 不同蛋白质对应的参数蛋白质ε(k J /m o l )b (k J /m o l)NT tM b2.058.21240301L y s 2.058.2800298C yt 2.058.2740302R n s 2.009.05003202.2 熵在正则系综中一摩尔蛋白质熵的表达式可写为S =R l n Z -β∂l n Z ∂βæèçöø÷+S 0,(10)其中S 0为积分常数.把配分函数表达式(4)代入(10)式得到S =N R (A +B +C )+S 0,(11)这里A =-12βε2e (-2b 2m 2β-2βε2-b (1+4m βε)+2βεe (b +b 2m 2β+2b m βε+βε2)c o t h (βεe ), B =-b β2ε2e c o t h (βεe )2, C =l n4πs i n h βεe ()βεe æèçöø÷-b β21εe β-c o t h βεe ()æèçöø÷2.这里同样把玻尔兹曼常数k 用气体常数R 代换,以便使ε和b 表示每摩尔的量.具体求得M b ,L y s ,C yt ,R n s 4种蛋白质在给定温度下的熵值,从而可37第1期 张秀颖,等:水溶液中蛋白质的热力学性质以给出熵增(取变性点的熵为零)随温度的变化曲线,如图2所示参数ε,b ,N 的取值同m 的计算相同.可以看出,熵增随温度的升高而增大,说明系统的混乱程度增加,或者说水分子在蛋白质周围的排列随温度增加变得无序,与平均偶极矩曲线得出的结论一致;曲线与T 轴交点对应蛋白质的变性温度,每种蛋白质各不相同.图2 熵增随温度的变化曲线(变性点的熵设为0)2.3 热容首先考虑系统在ε恒定时的热容,根据热力学第一定律,有C ε=d Q d T æèçöø÷ε=∂U ∂T æèçöø÷ε,(12)由内能与配分函数的关系可以得出U =-∂∂βl n Z ,进一步有C ε=-NHR T 2βI +J (),(13)其中H =ε2e (1+2b 2m 2β2+4b m β2ε+2β2ε2-c o s h (2βεe )),I =2b 3m 2β2-βε2-b 2m β(m -4βε)+b (1-2m βε+2β2ε2),J =(b 2m 2β+βε2+b (2m β-1))c o s h (2βεe ).为了更直观地看出热容随温度的变化规律,我们计算了4种蛋白质M b ,L y s ,C y t ,R n s 的热容曲线(图3:参数ε,b 和N 的取值同熵的计算相同).可以看出,所得结果与B a k k 等的结果基本一致[8].这4种蛋白质的热容虽然各不相等,但它们随温度的变化趋势是一样的,并且变化趋势与实验结果一致[4-6,19].从图3还可以看出,热容曲线存在一极大值,与图2比较可以看出,极大值点处温度大致对应着变性温度.这说明,每种蛋白质的变性温度不同,但是其在自然状态下的热容值都小于变性状态的热容值.下面讨论偶极矩m 恒定下的热容,根据熵与恒偶极矩热容的关系C m =T ∂S ∂T æèçöø÷m,(14)可以得到C m =N R T 2R 2T 2-ε2ec s c h εe R T æèçöø÷2æèçöø÷.(15)同样可以画出C m 随温度的变化曲线,如图4所示,可以看出恒偶极矩热容随温度升高而减小.比较可知,恒定电场下的热容在变性点温度存在一峰值,而恒偶极矩热容呈现单调递减的规律,并且一般情况下恒偶极矩热容要小于电场恒定时的热容.图3 恒定电场热容随温度的变化曲线图4 恒定偶极矩热容随温度的变化曲线3 小 结本文采用偶极子溶剂模型,把蛋白质体系看成一个正则系综,利用平均场理论,研究了水溶液中蛋白质系统中的平均偶极矩㊁自由能㊁熵和热容量随温度的变化.结果表明,不同种类的蛋白质具有不同的熵增和热容量,但它们随温度的变化趋势是相同的.随着温度的升高,熵逐渐增大.研究还发现,系统的恒定电场热容量在变性点具有极大值.参考文献:[1]M a k h a t a d z e GI ,P r i v a l o vP L .H e a tc a p a c i t y of p r o -t e i n s :Ⅰ.P a r t i a lm o l a r h e a t c a p a c i t y o f i n d i v i d u a l a m i n o a c i d r e s i d u e s i n a q u e o u s s o l u t i o n :H yd r a t i o nef f e c t [J ].J M o l B i o l ,1990,213(2):375.47 曲阜师范大学学报(自然科学版) 2021年[2]M a k h a t a d z e GI ,P r i v a l o vP L .H e a tc a p a c i t y of p r o -t e i n s :Ⅱ.P a r t i a l m o l a rh e a tc a p a c i t y o ft h eu n f o l d e d p o l y p e p t i d e c h a i no f p r o t e i n s :P r o t e i nu n f o l d i ng ef f e c t s [J ].JM o l B i o l ,1990,213(2):385.[3]H a y n i eD T ,F r e i r eE .E s t i m a t i o no f t h e f o l d i n g/u n f o l -d i n g e n e r g e t i c so fm a r g i n a l l y s t a b l e p r o t e i n su s i n g di f -f e r e n t i a l s c a n n i n g c a l o r i m e t r y [J ].A n a lB i o c h e m ,1994,216(1):33.[4]O y l u m l u o g l u G ,B üy ük k ıl ıçF ,D e m i r h a nD.I n v e s t i ga -t i o no fh y d r a t i o ne f f e c to f t h e p r o t e i n sb yp h e n o m e n o -l o g ic a l t h e r m o s t a t i s t i c a lm e t h od s [J ].P h y s i c aA ,2006,361(1):255.[5]O y l u m l u o g l u G ,B üy ük k ıl ıçF ,D e m i r h a nD.I n v e s t i ga -t i o no f h e a t c a p a c i t i e s o f p r o t e i n sb y s t a t i s t ic a lm e c h a n i -c a lm e t h od s [J ].P h y s i c aA ,2007,375(2):577.[6]O y l u m l u o g l uG ,B üyük k ıl ıçF ,D e m i r h a nD.At h e r m o -s t a t i s t i c a l a p p r o a c h t o p r o t e i n s t r u c t u r e s [J ].P h ys i c aA ,2008,387(7):1577.[7]黄克逊.统计物理和蛋白质折叠讲义[M ].上海:复旦大学出版社,2006.95.[8]B a k kA ,H o y e JS ,H a n s e nA.S p e c i f i ch e a tu p o na qu e -o u su n f o l d i n g o ft h e p r o t e i ni n t e r i o r :at h e o r e t i c a la p -p r o a c h [J ].P h y s i c aA ,2002,304(3-4):355.[9]W a r s h e lA ,L e v i t tM.T h e o r e t i c a l s t u d i e s o f e n z ym i c r e -a c t i o n s :d i e l e c t r i c ,e l e c t r o s t a t i c a n ds t e r i c s t a b i l i z a t i o no ft h e c a r b o n i u mi o n i n t h e r e a c t i o no f l y s o z y m e [J ].JM o l B i o l ,1976,103(2):227.[10]F r a n k H S ,E v a n s M W.F r e ev o l u m ea n de n t r o p y in c o n d e n s e ds y s t e m s Ⅲ.E n t r o p y i nb i n a r y l i qu i d m i x -t u r e s ;p a r t i a lm o l a le n t r o p y ind i l u t es o l u t i o n s ;s t r u c -t u r e a n d t h e r m o d y n a m i c s i na q u e o u s e l e c t r o l y t e s [J ].J C h e m P h ys ,1945,13(11):507.[11]S h i n o d aK .C h a r a c t e r i s t i c p r o p e r t y i na qu e o u ss o l u t i o n s :e f f e c t o f i c e b e r g f o r m a t i o n o fw a t e r s u r r o u n d i n g s o l u t e o n t h e s o l u b i l i t y (o rc m c )a n di t s p e c u l i a rt e m p e r a t u r ed e -pe n d e n c e [J ].A d vC o l l o i d I n t e rf a c e S c i ,1992(41):81.[12]B a k k A ,H o y eJS .M i c r o s c o p i ca r gu m e n t f o rt h ea -n o m a l o u s h y d r a t i o nh e a t c a p a c i t y i n c r e m e n t u p o ns o l -v a t i o no fa p o l a rs u b s t a n c e s [J ].P h y s i c a A ,2002,303(3-4):286.[13]B a k k A.T w o -s t a t e p r o t e i n m o d e lw i t h w a t e r i n t e r a c -t i o n s :i n f l u e n c e o f t e m p e r a t u r e o n t h e i n t r i n s i c v i s c o s i t y o fm y o g l o b i n [J ].P h ysR e vE ,2001,63(6):061906.[14]R u s s e l lS T ,W a r s h e lA.C a l c u l a t i o n so fe l e c t r o s t a t i ce n e r g i e s i n p r o t e i n s .T h ee n e r g e t i c sof I o n i z e dg r o u ps i nb o v i n e p a n e a t i ct r y p s i ni n h i b i t o r [J ].J M o lB i o l ,1985,185(2):389.[15]A v b e l j F .A m i n oa c i dc o n f o r m a t i o n a l p r e f e r e n c e sa n d s o l v a t i o no f p o l a r b a c k b o n e a t o m s i n p e pt i d e s a n d p r o -t e i n s [J ].JM o l B i o l ,2000,300(5):1335.[16]M a SK.S t a t i s t i c a lm e c h a n i c s [M ].P h i l a d e l p h i a :W o r l d S c i e n t i f i c ,1985.458.[17]B a k kA ,H o y e JS ,H a n s e nA.H e a t c a p a c i t y o f p r o t e i n f o l d i n g [J ].B i o p h y s J ,2001,81(2):710.[18]H o y e JS ,S t e l lG.S t a t i s t i c a lm e c h a n i c so f p o l a r f l u i d s i ne l e c t r i c f i e l d s [J ].JC h e m P h y s ,1980,72(3):1957.[19]P r i v a l o vPL ,M a k h a t a d z eGI .C o n t r i b u t i o no fh yd r a -t i o na n dn o n -c o v a le n t i n t e r a c t i o n s t ot h eh e a t c a p a c i t y ef f e c t o n p r o t e i nu n f o l d i ng [J ].J M o lB i o l ,1992,224(3):715.T h e r m o d y n a m i c p r o pe r t i e s of p r o t e i n s i nw a t e r Z HA N G X i u y i ng ①, Z HA N GP a n p a n ①, WA N GJ i e ②, X UY u l i a n g ①, K O N G X i a n gm u ①(①S c h o o l o f P h y s i c s a n dO p t o e l e c t r o n i cE n g i n e e r i n g ,L u d o n g U n i v e r s i t y,264025;②N a v a lA v i a t i o nU n i v e r s i t y ,265401,Y a n t a i ,S h a n d o n g,P R C )A b s t r a c t :T h e t h e r m o d y n a m i c p r o p e r t i e s o f p r o t e i n s y s t e mi nw a t e r a r e s t u d i e db y u s i n g d i po l e s o l v e n t m o d e l a n dm e a n f i e l d t h e o r y .T h e p a r t i t i o n f u n c t i o no f t h e s y s t e mi s c a l c u l a t e d ,a n d t h e e x pr e s s i o n s o f t h e a v e r a g e d i p o l em o m e n t ,f r e e e n e r g y ,e n t r o p y a n dh e a t c a p a c i t y o f t h e s ys t e ma r eo b t a i n e d .M e a n w h i l e ,w e a l s od i s c u s s t h e i r v a r i a t i o n sw i t h t e m p e r a t u r e .T h e r e s u l t s s h o wt h a t t h e a v e r a g e d i po l em o m e n t d e c r e a s e s l i n e a r l y w i t h t h e i n c r e a s eo f t e m p e r a t u r e ;t h ee n t r o p y o f p r o t e i n s i n c r e a s e g r a d u a l l y w i t ht h e i n c r e a s eo f t e m p e r a t u r e ;a t t h e s a m e t e m p e r a t u r e ,t h e h e a t c a p a c i t y at c o n s t a n t e l e c t r i c f i e l d i s g r e a t e r t h a n t h a t a t c o n -s t a n t d i p o l em o m e n t ,a n d t h e v a r i a t i o n l a w w i t h t e m p e r a t u r eo f b o t hh e a t c a p a c i t i e s i s a l s od i f f e r e n t .T h e h e a t c a p a c i t y a t c o n s t a n t e l e c t r i c f i e l dh a s am a x i m u ma t t h e d e n a t u r a t i o n p o i n t .K e y wo r d s :p r o t e i n ;m e a n f i e l d t h e o r y ;a v e r a g e d i p o l em o m e n t ;e n t r o p y ;h e a t c a p a c i t y 57第1期 张秀颖,等:水溶液中蛋白质的热力学性质。
关于熵焓的书籍

熵(entropy)和焓(enthalpy)是热力学领域中的重要概念,它们用于描述热力学系统的状态和性质。
以下是一些建议的关于熵和焓的书籍,这些书籍涵盖了这两个概念以及它们在物理、化学等领域中的应用:1.《热力学与统计物理学》(Thermodynamics and Statistical Mechanics)作者:RichardFitzpatrick•这本书是一本面向研究生水平的教材,涵盖了热力学和统计物理学的基本原理,包括对熵和焓的详细讲解。
2.《热力学与热工学》(Thermodynamics: An Engineering Approach)作者:Yunus A.Cengel, Michael A. Boles•这是一本广泛用于工程热力学课程的教材,介绍了熵、焓以及它们在工程应用中的重要性。
3.《化学工程热力学》(Introduction to Chemical Engineering Thermodynamics)作者:Joseph M. Smith, Hendrick C. Van Ness, Michael M. Abbott•这本书专注于化学工程中的热力学,对熵和焓进行了深入的讲解,并提供了实际应用的例子。
4.《现代工程热力学》(Modern Engineering Thermodynamics)作者:Robert T. Balmer•这本书介绍了现代工程热力学的基本概念,包括对熵和焓的理解,以及它们在工程应用中的使用。
5.《热力学和统计物理学的奇迹》(The Miracles of Reversible Entropy)作者:DilipKondepudi•本书提供了关于熵和可逆过程的更深入的理论讨论,适合那些对热力学基础和统计物理学感兴趣的读者。
6.《化学热力学基础》(Physical Chemistry: A Molecular Approach)作者:Donald A.McQuarrie, John D. Simon•这本化学热力学教材包含了关于熵和焓等热力学概念的详细讲解,适用于学习化学热力学的学生。
工程热力学专业英语词汇

工程热力学专业英语词汇一些工程热力学的专业英语词汇Heat pump(热泵)Heat source(热源)Heat(enthalpy) of formation(生成热(生成焓))Heat(热)Helmholtz function(亥姆霍兹函数)Hess’law(赫斯定律)Humidity(湿度)Ideal gas equation of state(理想气体状态方程)Inequality of Clausius(克劳修斯不等式)Intensive quantity(强度量)Internal combustion engine(内燃机)Internal energy(热力学能(内能))Inversion curve(转变曲线)Inversion temperature(转回温度)Irreversible cycle(不可逆循环)Irreversible process(不可逆过程)Isentropic compressibility(绝热压缩系数)Isentropic process(定熵过程)Isobaric process(定压过程)Isolated system(孤立系)Isometric process(定容过程)Isothermal compressibility(定温压缩系数)Isothermal process(定温过程)Joule,J.P.(焦耳)Joule-Thomson effect(焦耳-汤普逊效应)Kelvin, L.(开尔文)Kinetic energy(动能)Kirchhoff’s law(基尔霍夫定律)Latent heat(潜热)Law of corresponding states(对应态定律)Law of partial volume(分体积定律)Le Chatelier’s princip le(吕-查德里原理)Local velocity of sound(当地声速)Lost of available energy(有效能耗散)Mach number(马赫数)Mass flow rate(质量流量)Maximum work from chemical reaction(反应最大功)Maxwell relations(麦克斯韦关系)Mayer’s formula(迈耶公式)Mechanical equilibrium(力平衡)Mixture of gases(混合气体)Moist air(湿空气)Moisture content(含湿量)Molar specific heat(摩尔热容)Nernst heat theorem(奈斯特热定理)Nozzle(喷管)One dimensional flow(一维流动)Open system(开口系)Otto cycle(奥托循环)Parameter of state(状态参数)Perfect gas(理想气体)Perfect gas(理想气体)Perpetual-motion engine of the second kind(第二类永动机)Perpetual-motion engine(永动机)Phase(相)Polytropic process(多变过程)Potential energy(位能)Power cycle(动力循环)Pressure(压力)Principle of increase of entropy(熵增原理)Process(过程)Psychrometric chart(湿空气焓-湿图)Pure substance(纯物质)Push work(推挤功)Quality of vapor-liquid mixture, Dryness(干度)Quantity of refrigeration(制冷量)Quasi-equilibrium process(准平衡过程)Quasi-static process(准静态过程)Rankine cycle(朗肯循环)Ratio of pressure of cycle(循环增压比)Real gas(实际气体)Reduced parameter(对比参数)Refrigerant(制冷剂)Refrigeration cycle(制冷循环)Refrigerator(制冷机)Regenerative cycle(回一些工程热力学的专业英语词汇热循环)Reheated cycle(再热循环)Relative humidity(相对湿度)Reversed Carnot cycle(逆卡诺循环)Reversed cycle(逆循环)Reversible cycle(可逆循环)Reversible process(可逆过程)Saturated air(饱和空气)Saturated vapor(饱和蒸汽)Saturated water(饱和水)Saturation pressure(饱和压力)Saturation temperature(饱和温度)Second law of thermodynamics(热力学第二定律)Simple compressible system(简单可压缩系)Sink(冷源)Specific heat at constant pressure(比定压热容)Specific heat at constant volume(比定容热容)Specific heat(比热容)Specific humidity(绝对湿度)Specific volume(比体积)Stagnation enthalpy(滞止焓)Standard atmosphere(标准大气压)Standard enthalpy of formation(标准生成焓)Standard state(标准状况)State postulate(状态公理)State(状态)Statistical thermodynamics(统计热力学)Steady flow(稳定流动)Steam(水蒸气)Subsonic(亚声速)Superheated steam(过热蒸汽)Supersonic(超声速)Technical work(技术功)Temperature scale(温度标尺)Temperature(温度)Theoretical flame temperature(理想燃烧温度)Thermal coefficient(热系数)Thermal efficiency(热效率)Thermal equilibrium(热平衡)Thermodynamic Probability(热力学概率)Thermodynamic system(热力学系统)Thermodynamic temperature scale(热力学温标)Thermodynamics(热力学)Third law of thermodynamics(热力学第三定律)Throttling(节流)Triple point(三相点)Unavailable energy(无效能)Universal gas constant(通用气体常数)Vacuum(真空度)Van der Waals’equation(范德瓦尔方程)Velocity of sound(声速)Virial equation of state(维里状态方程)Wet saturated steam(湿饱和蒸汽)Wet-Bulb temperature(湿球温度)Work(功)Working substance(工质)Zeroth law of thermodynamics(热力学第零定律)。
基于最大相关峭度解卷积的滚动轴承故障诊断方法

基于最大相关峭度解卷积的滚动轴承故障诊断方法摘要:滚动轴承健康状态会影响到整个机械系统,因此需要对其进行故障诊断。
提出一种基于最大相关峭度解卷积的滚动轴承故障诊断方法,首先通过相关峭度来衡量周期性和脉冲性,区分故障信号与噪声,其次以相关峭度最大为目标函数对测量进行进行解卷积提升周期性脉冲,再通过Hilbert包络解调得到包络信号,最后通过包络信号频谱判断滚动轴承故障情况。
关键词:最大相关峭度解卷积,Hilbert变换,滚动轴承,故障诊断中图分类号:TH133.331.引言滚动轴承作为最重要的机器零部件之一,已广泛运用于海洋船舶、航空航天等机械设备当中。
但是滚动轴承长期运行在高负载、变转速的恶劣环境中,极易发生故障,近45%至55%的旋转机械故障是由滚动轴承造成的[1],由此可见对滚动轴承故障进行准确诊断至关重要。
滚动轴承故障诊断是通过检测、隔离和识别来确定损坏状态的过程,早期诊断方法常常是使用一些统计参数对滚动轴承的故障情况进行判断[2]。
但是仅仅使用统计参数无法显示信号频率中包含的信息,随着快速傅里叶变换等快速计算频谱方法以及计算机算力的提升,谱方法被广泛运用于滚动轴承故障诊断当中。
之后研究人员使用了一系列的信号处理方法,其中包括经验模态分解、经验小波分解、变分模态分解等方法对信号进行降噪处理后再对信号进行谱分析,提升了信号的故障检测能力[3]。
但仅通过对信号进行降噪处理没有考虑到传递路径的影响限制了最终检测的能力,本文提出一种基于最大相关峭度解卷积的滚动轴承故障诊断方法,以相关峭度为目标函数对信号进行解卷积处理,补偿传递函数,提升信号的周期性脉冲,再通过Hilbert解调提取处理后信号的包络,最后通过频谱分析确定滚动轴承故障情况。
1.方法原理卷积问题是对一个已知输入信号和系统求解输出。
系统的输出需要考虑系统的记忆,可以表示为:(1)也就是说系统的输出是系统的输入经过一个FIR滤波器作用所得。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
ant under SU (2) gauge transformations. The gauge transformations generate spacetime diffeomorphisms 5, and since some diffeomorphisms shift the loca-
PITHA - 96/22 UNB Technical Report 96-01
1 Introduction
Although the final word has certainly not been written, several calculations have been performed which relate the Bekenstein-Hawking thermodynamic entropy 1 to the degeneracy of microscopic states. For Carlip 2 and Balachandran and his group 3, the microstates originate from treating the event horizon as the boundary of the spacetime. In particular, degrees of freedom which are pure gauge in the interior of spacetime become dynamical on the boundary.
3 Quantum Mechanics on the Boundary of Spacetime
As discussed above, we choose φ =
φ¯ to be:
φ¯
=
√ M
T3,
where
T3
is the
constant diagonal 2 × 2 su(2) matrix. This is a so√lution of the equations of motion on the boundary ∂M, in the limit as x0 → M ℓ.
1
the mass of the black hole is quantized. The resulting degeneracy of quantum states on the boundary is proportional to t√he square root of the black hole mass, and hence the entropy is given by log M .
In this talk, we apply Carlip’s program to an even lower dimensional black hole – namely that occurring as a solution of the ‘constant curvature’ (CC) theory of gravity in two-dimensional spacetime with a cosmological constant.4 The field equations for this theory include R = 2k, for Ricci scalar R and cosmological constant k = 0. We work with a closely related BF type topological gauge theory.5 We will show that when the latter theory is constructed on a manifold with a boundary that corresponds to the bifurcation two-sphere of a black hole of fixed mass M , and provided the gauge group is analytically continued to SU (2) (or, equivalently, if we consider the Euclidean CC-model,) the surface term gives rise to a non-trivial mechanical system equivalent to two harmonic oscillators with fixed energy. This system can be quantized only if
Fredericton, New Brunswick E3B 5A3 Canada
G. Kunstatter Dept. of Physics and Winnipeg Institute of Theoretical Physics, University of
Winnipeg Winnipeg, Manitoba R3B 2E9 Canada
surface term is required in Eq.(1), if the spacetime is a manifold-with-boundary such that the field φ is fixed on the boundary.
We will henceforth suppose that the spacetime metric given by the dyad ea has positive-definite signature and that k is positive. Thus the appropriate gauge group is SU (2). The black holes are to be identified with the manifoldwith-boundary M with interior the spherical cap and with boundary ∂M the embedded circle. The metric is given locally by
T.Strobl Institut fu¨r Theoretische Physik, RWTH-Aachen Sommerfeldstr. 26-28, D52056 Aachen, Germany
We calculate the statistical mechanical entropy associated with boundary terms in the two-dimensional Euclidean black holes in deSitter gravity.
with the isometry group of the on-shell metric. The equivalence with the CC gravity model is achieved by the identification A = AiTi = eaTa + ωT3, where a, b, .. = 1, 2 and ea, ω are Zweibein and spin connection, respectively. The
ds2 = M − x2/ℓ2 dθ2 + M − x2/ℓ2 −1 dx2,
(2)
where M is an invariant dimensionless parameter defined by M = T rφ2 ≡ φaφa + φ3φ3, which may be identified with the mass of the black hole. This is the dimensionally reduced Euclideani√zed BTZ black hole.6 The boundary in these coordinates is given by x = x0 > M ℓ.
arXiv:gr-qc/9607055v2 14 Mar 1997
STATISTICAL MECHANICAL ENTROPY OF TWO-DIMENSIONAL BLACK HOLES
J. Gegenberg Dept. of Mathematics and Statistics, University of New Brunswick
2 The 2-D Gravity Model The CC theory is closely related to a gauge theory 5
S[φ, A] = T r φF (A) − T r φA ,
(1)
M
∂M
where F (A) = dA+A∧A is the curvature of A, a Lie-algebra valued connection on a principal bundle over M and φ is a scalar field over M which also takes its values in the same Lie algebra. In order to describe the Euclidean CC theory with cosmological constant k, the appropriate Lie algebra is so(2, 1) for negative cosmological constant and su(2) for positive k, while for the Minkowskian theory it is so(2, 1) irrespective of the sign of k.5 The gauge grou = g−1A¯g + g−1dg.
