DTMF Decoding with a PIC16xxx(英文文献)
Chapter 5 A PERFORMANCE ANALYSIS OF MEERKAT This chapter compares the performance of progra

Chapter5A PERFORMANCE ANALYSIS OF MEERKATThis chapter compares the performance of programs running on both the Meerkat prototype and Meerkat simulator with those running on Intel’s Touchstone Delta[7]. These comparisons demonstrate that Meerkat is an effective multicomputer architecture when compared to Delta,a heavily used,commercially built multicomputer.Our tests prove that:(1)Meerkat can drive its interconnect at nine times the rate of the Delta,(2)the bisection bandwidth of a256-node Meerkat is three times higher than that of the same-sized Delta,and(3)Meerkat’s speedups exceed Delta’s up to the limit of Meerkat’s scaling range.Our simulated Meerkat,which can have up to256nodes,is calibrated to our prototype hardware,which has four nodes.The prototype cannot scale beyond its small number of nodes.The limited scalability of the prototype is not indicative of the architecture’s potential.Rather,it was a decision made to facilitate timely results from a one-person effort.In contrast to the prototype,the architecture can scale to hundreds of nodes.That is,the architecture permits designs that have many nodes and that are only slightly more complicated that our prototype.We introduce the differences between Meerkat and Delta in Section5.1.Section5.2dis-cusses the relationship between multicomputer interconnect performance and message size. Section5.3describes the message-passing primitives that we implemented for Meerkat. Section5.4gives insight into the implementation of these primitives.The interconnect’s performance under light and heavy loads is analyzed in Sections5.5and 5.6.Meerkat’s performance on two numerical applications is shown in Sections5.9and5.10.5.1IntroductionLike Meerkat,Delta is a multicomputer composed of RISC processors,local memory,and an interconnect that is used explicitly by application software.The two systems differ in2their interconnects:Delta employs a conventional mesh of2-D routers,while Meerkat uses sets of vertical and horizontal internode buses.There are other differences between Meerkat and Delta that complicate the comparison of the two interconnect architectures:The40MHz Intel i860processors in Delta are about twice as fast as the20MHz Motorola88100processors in Meerkat.Meerkat’s message-passing code is written in carefully crafted assembler,while Delta runs the NX/M operating system[6],written in C.The Meerkat internode interface copies to and from memory,whereas the Delta interface requires the processor to load and store each byte moved through the interface(i.e.,programmed I/O).The Delta test program runs in an address space separate from NX/M and thus incurs context-switching costs,while Meerkat’s test program runs in the same address space as the message-passing library.Some of these differences,however,offset others.For example,the slower Meerkat processors executing our small,message-passing library offset the effect of faster Delta processors executing the larger NX/M operating system.Despite these differences,there are conclusions we can draw from experiments com-paring the systems.We know that the Delta is an effective multicomputer.If we can show that Meerkat’s performance is better,we can conclude that Meerkat is also effective.5.2Message GranularityInterconnect bandwidth and latency are functions of message size.Message size itself is a function of the:(1)algorithm,(2)data layout,(3)number of nodes applied to the problem, and(4)problem size.In general,if the number of nodes increases while other parameters remain constant,the size of messages will decrease.Likewise,an increase in problem size often increases the message size.While a comprehensive discussion of message size exceeds the scope of this thesis,we provide the following examples as background for our subsequent performance discussion: The butterfly FFT algorithm using a cyclic layout generates messages that are3We speculate that operating system traffic on Meerkat would be composed of both short control messages and page-sized messages to supportfile system and virtual memory traffic.Process migration would generate messages in excess of64K bytes.Blocked iterative solution methods send messages that are proportional to the size of one edge of the block.A red/black successive over relaxation algorithm on a4096by 4096grid running on256nodes will use a block that is16by16.For double-precision numbers,each message will be1024bytes.5.3Message PassingAll benchmarks use a subset of Delta’s message-passing library,which we implemented on Meerkat.The subset contains the following primitives:Void csend(int type,const char buf,int size,int dest) Int irecv(type,char buf,int size)Void msgwait(int key)Csend sends a message of type type to node dest of length size whose data starts at address buf.Message delivery is reliable and in-order.Control does not leave csend until the message is delivered to the destination node,although it can be buffered by the receiving node until the application asks for it.If dest is,the message is broadcast to all nodes.Irecv tells the message-passing system that:(1)the application is ready to receive a message of type type in a buffer of length size bytes or less,and(2)that the buffer starts at address buf.A type of matches any received type.Irecv returns a key that can subsequently be passed to msgwait.Msgwait returns when the buffer associated with the passed key isfilled with a received message.If irecv is called with a typefield matching a message that has been received but not yet been delivered to the application, the message will be copied into the buffer supplied by irecv.Irecv checks for a message with a matching type.If one has arrived,it copies the message to the user buffer and returns a value that will tell a subsequent call to msgwait that the message has arrived.If not,it allocates a pending-receive record and puts this record,which contains the user’s buffer description and the expected message type,on a list of pending receive records.When the message arrives,it is delivered directly into the buffer supplied by irecv.In Meerkat,the key returned by irecv is zero if the message is waiting.Otherwise,it is a pointer to the newly allocated pending-receive record.Msgwait returns immediately4if it is passed a zero.If not,it spins,waiting for the passed pending-receive record to be marked "done"by the internode interrupt handler.5.4Chronology of Csend and Irecv Message PrimitivesFigure 5.1shows timelines with a simple csend and irecv/msgwait .A sending node is on the top timeline,and a receiving node on the bottom.The sender executes csend ,while the receiver executes an irecv followed by a msgwait .TIMEinterrupt routine returns Sender (csend)Receiver (irecv/msgwait)Cache flushPacketizeI-cache preloadArbitrationControl rendezvousData rendezvousReceiver sees internode interruptInterrupt overheadIrecvMsgwaitMessage transmissionMessage receptionreturns to applicationMsgwait returnsCsend Check arguments/save registersFigure 5.1:Simple Csend and Irecv/Msgwait TimelineThe steps of csend are:1.Argument checking :check arguments to csend ,test for broadcast,test for destina-tion node being equal to the sending node,determine routing (i.e.,1-bus vs.2-bus;if 1-bus,horizontal vs.vertical).2.Data cache flush :instruct the data cache to write back to memory any dirty cache lines that hold data in the range of memory addresses to be sent.3.Message packetize :divide the message into one or more data packets and,in so doing,construct a control packet.4.Internode bus arbitration :acquire ownership of the required buses.55.Instruction cache preload:preload the sender-receiver rendezvous code in thesender’s instruction cache.This code can cause a bus timeout on the receiver if it does not execute certain groups of instructions quickly enough.Preloading the instruction cache makes the critical groups execute quickly.Preloading is done by executing critical code with parameter values that cause no internode activity.6.Control packet rendezvous:signal the receiver node,wait for it to enter a receptivestate,and begin to transmit the control packet.The receiver takes an interrupt when it is signalled.7.Data packet rendezvous:signal the receiver node,wait for it to enter a receptive state,and begin to transmit a portion of user-specified data.The receiver polls for signals from the sender and thus avoids the interrupt overhead.8.Data transfer:move data from the sending processor’s memory to the receiver’smemory.Each word moved requires one cycle.9.Miscellaneous processing:call subroutines,save/restore registers,return to caller,etc.Table5.1shows the execution cost of csend steps as a function of message size.Each pair relates the number of cycles for a given step followed by the percentage this step represents of the total time for csend.Table5.1:Number of Cycles and Percentage of Total Time Taken by Csend Step (Percentages Rounded to the Nearest Point)12832,7681+9.Miscellaneous overhead114/25%164/15%240/30%1,134/10%21/3%172/2%61/8%81/0%30/4%30/0%144/18%158/1%148/18%769/7%32/4%8,192/74%801/100%11,102/100%The table shows that,as message size increases,the percentage of time spent sending data through the interconnect(Step8)increases.Similarly,for all steps except Step8, as message size increases,the percentage of time spent decreases.For example,zero-byte messages spend11%of execution time in arbitration;thisfigure decreases tofive percent for1,024-byte messages,and to less than half a percent for32,768-byte messages.6Miscellaneous overheadfigures include time spent on argument checking and routing decisions.Table5.2shows the execution cost to a receiving node given four message sizes. The irecv row shows the cost of posting a receive,i.e.,of recording the user’s request for a message in advance of the message’s reception.The next row shows the cost of executing the interrupt subroutine that causes the rendezvous with the sending node,places data in the user’s buffer,etc.The‘interrupt overhead’line contains time spent by the processor:context-switching to the interrupt exception handler,decoding the interrupt, saving registers,acquiring a semaphore that guards against conflicting use of the network interface,and receiving the control packet.The time spent receiving a message overlaps with the sending node’s time for sending.Table5.2:Number of Cycles Taken by Message-Reception Step12832,768irecv(post a receive)116373Message reception105434Interrupt overhead13713464310,819Table5.2reveals several characteristics of the message-passing library.First,posting a receive requires a cacheflush in order to maintain consistency.The larger the buffer, the more cache state must be adjusted,and the longer the time will be to post the receive. However,the increase is sublinear;beyond a certain message size,the whole cache is flushed.Thefirst line of the table shows:(1)182cycles toflush thefirst128bytes,or about 1.4cycles per byte,(2)75cycles toflush the next896bytes,or0.083cycles per byte,and (3)941cycles toflush the next31744bytes,or0.029cycles per byte.Second,the table shows that,for large messages reception itself,(i.e.,moving the data from the interconnect to the receiver’s memory)dominates execution time.The reception time goes from0.82cycles per byte for small messages to0.28for long messages.If there were no software overhead,thisfigure would be0.25cycles per byte(one cycle per word). Thus,for long messages,Meerkat’s message reception approaches the hardware transfer rate.Lastly,the interrupt overhead is fairly constant,rising slightly for the largest messages.7This rise of26cycles(160-134)for32,768-byte messages is due to cache effects:large messagesflush the whole cache,including variables used by the message-passing library. The26-cycle increase represents the time to reload these variables.5.5Bandwidth under Light LoadThis section reports the performance of Meerkat and Delta on a simple test that measures the ability of nodes to exchange data of varying sizes.The core of the program for this test appears in Figure5.2:light_load_test(char*buf,int size){double start,end,elapsed_time,bytes_per_second;int key;switch(mynode()){case0:start=time_in_seconds();key=irecv(0,buf,size);csend(0,buf,size,3,0);/*Send to node3*/msgwait(key);end=time_in_seconds();elapsed_time=end-start;bytes_per_second=2*(size/elapsed_time);printf("MB/sec for message of%d bytes=%7.3lf\n",size,bytes_per_second/1000000.0);break;case3:crecv(0,buf,size);csend(0,buf,size,0,0);/*Send to node0*/}}Figure5.2:Message-Passing Program to Test Meerkat under Light LoadThis test causes node zero to send a message of length size to node three.Node three waits for the message,which it sends to node zero.The total number of bytes sent is twice the message size.We measure the time interval from immediately prior to node zero’s transmission until immediately after node zero receives a reply from node three.We chose the node numbers(zero and three)so that the communication requires a two-bus connection.We execute the sequence above for message sizes ranging from four to256k bytes.Figure5.3shows the bandwidth achieved by a pair of nodes for both systems as a function of message size.We include in these graphs the bandwidth measured on the Intel Hypercube iPSC/2and iPSC/860[1].In this test the bandwidths reported by the Meerkat simulator and the hardware differed by about one percent.Therefore,the Meerkat curve8can be viewed both as a measurement of a real system and as a simulation result.Meerkat Delta iPSC/860 iPSC/2|10|||||||||100|||||||||1000|||||||||10000|||||||||100000|0|||||||||1|||||||||10|||||||||100Message size (bytes)B a n d w i d t h (M B /s e c o n d )Figure 5.3:Bandwidth as a Function of Message Size under Light Load The bandwidth of both Meerkat and Delta on small messages is limited by the ability of the nodes to inject messages into the network.The lower performance of Delta on small messages may be due to the extra work done in NX/M that is not done in the Meerkat message-passing library.Meerkat achieves 67MB/sec for 100,000-byte messages,while Delta’s bandwidth levels off at about 8MB/sec for 2,000-byte messages.Both Meerkat and Delta are limited on long messages by their different abilities to drive their interconnects.Meerkat’s internode bandwidth reaches 83percent of its peak rate of 80MB/sec.Delta reaches 10percent of its theoretical rate,which is also 80MB/sec [11].Delta’s ability to drive its interconnect in this test is limited by its network interface and the speed of the node processor.The network interface requires that the processor manipulate each byte sent through the interconnect.In the next section,we will see that Delta’s network can handle more traffic than a single node can generate.While Meerkat’s maximum interconnect performance is seen at a message size that is longer than most applications will generate,its performance on shorter messages is still high.It may make sense,however,to reduce the per-message overhead by moving logic9from low-level software into hardware.This would push the solid curve in Figure5.3 higher and to the left.Chapter6discusses changes to the network interface that can reduce per-message overhead.5.6Bandwidth under Heavy LoadIn this experiment there are two groups of128nodes each,A and B,as shown in Figure5.4. Each node in group A sends a message to its partner in group B and waits for a reply.Each node in group B waits for a message from its partner in group A;it then sends a message back to its partner.The nodes of each group are physically contiguous in an8by16block, and the two groups are adjacent to form a16by16block of nodes.The distance between each node and its partner is eight.The total number of bytes moved between the groups is the product of the message size and the number of messages sent,which is256.We calculate the bandwidth by dividing the total number of bytes moved by the round triptime.ABFigure5.4:Pattern of Communication during Heavy Load Test Figure5.5shows both Meerkat and Delta with a nearly linear increase in bandwidth with increasing message size for messages of less than500bytes.As with the light interconnect load,this increase results from the amortization of afixed processor overhead per message over longer messages.The Delta bandwidth reaches a maximum of280MB/sec with a message size of1000bytes.Meerkat peaks at750MB/sec at a message size of4000bytes.10Meerkat Delta|0|1000|2000|3000|4000|0|100|200|300|400|500|600|700|800 Message Size (Bytes)B a n d w i d t h (M B /s e c )Figure 5.5:256-Node System Bisection BandwidthDividing each of these bandwidths by the number of channels through which the data move,in this case 16,we find that Meerkat’s buses are driven at an average of 46MB/sec.Delta’s channels at the midpoint are driven at 17MB/sec.Delta’s channels are composed of pairs of unidirectional links.Through separate tests,we determined that the maximum undirectional link speed is 11MB/sec.Thus,the 17MB/sec figure shows that our heavy-load test overlaps the use of these unidirectional links.The earlier plateau in Delta’s bandwidth is due to Delta’s higher ratio of processor to interconnect performance.That is,Meerkat’s slower processors need longer messages to saturate its faster interconnect.However,the level of the plateaus depends on interconnect performance rather than processor speed.5.7Per-Node BandwidthTo better understand what the results in the previous section mean for application perfor-mance,we consider the amount of internode bandwidth available to each node.We assume that the system is heavily loaded and that each node uses an equal amount of bandwidth.Figure 5.6shows system bisection bandwidth divided by the number of nodes.This graph is in units of double words (DW)(8bytes),as this is often the unit in which numerical applications programmers consider problem and message sizes.The per-node bandwidth is shown for several sizes of Meerkat and rger systems have lower per-node bandwidths because the bisection bandwidth increases with the square root of the number of nodes.16-Node Meerkat 64-Node Meerkat 144-Node Meerkat 256-Node Meerkat 16-Node Delta256-Node Delta|0|250|500|750|1000|0.0|0.5|1.0|1.5Message Size (Double-Words)M e g a D W /S e c P e r N o d eFigure 5.6:Per Node BandwidthConsider this example:if an application running on a 144-node Meerkat has every node send 500-DW messages and does no computation,every node will sustain a transfer rate of 550,000DW/sec.All applications will spend some of their time computing,so these curves represent the upper bound on internode performance.These figures assume that nodes share the interconnect equally.The internode bandwidth seen by a single node can be much higher if other nodes make only light use of the interconnect.These curves show that Delta has a lower per-node bandwidth than Meerkat for the same reasons given in the prior two sections for lower bandwidth.These differences are mostly a function of implementation,not of architecture.However,the ease with which we were able to design and build a fast implementation is a result of Meerkat’s simplicity.5.8Application PerformanceIt is important for prospective parallel computer users to be able to anticipate how well their applications will run.A given parallel application may run well on some computers and poorly on others."Running well"is,of course,subjective.The definition we adopt in this section is that the processors execute application code for at least half of the overall execution time.This section characterizes the applications that are likely to run well on Meerkat.We define these applications in terms of the application’s computation and communication demands.Our goal is to give application developers enough information to decide what combinations of parallel applications,input data sizes,and Meerkat configurations will run well.The principal application characteristics that determine performance on Meerkat are: (1)the ratio of computation to communication,(2)message size,and(3)load balance.Thefirst characteristic,the comp/comm ratio,is the ratio of the instructions executed to the amount of data sent between nodes[10].For example,an application that executes one million double-precisionfloating point instructions on each of256processors,and which passes two million double words between nodes,has a comp/comm ratio of128.That is, each node will perform an average of128FP operations for each DW value it sends to another node.The second application characteristic of importance is the grain size,the size of the message the application uses to package internode data.As the grain size decreases,the time spent to process messages increases.This computational effort comes at the expense of application running time.Both of these characteristics are functions not only of the application,but also of the problem size,the number of nodes,and the details of how the application is implemented. Some algorithms,such as Cholesky factorization,use messages with sizes that are also a function of the input data.Other algorithms,e.g.,modified Gram-Schmidt with partial pivoting[12],have a comp/comm ratio that is a function of the input data.Estimating the ratio for these applications may be difficult.Applications that have very high comp/comm ratios,e.g.,over a million to one,will perform well on almost any parallel computer.They spend almost all of their time comput-ing.Even if internode communication is expensive,they spend little time communicating. These applications are perhaps best served by parallel computers with low-performance,inexpensive interconnects.Applications that have very low comp/comm ratios,e.g.,between zero and one,will perform poorly on any parallel computer.They will spend most the time communicating and little time computing,leaving processors idle most of the time.These applications are probably best run on uniprocessors,where no internode communication is necessary.Between these extremes are applications that will run well on some systems but not on others.To gauge whether they will run well,i.e.,with high processor utilization,we consider the comp/comm ratio of the parallel computer.This is the ratio of the rate at which each node can execute instructions to the rate at which each node can transmit data. For example,a system with processors that can sustain10MFLOPS and in which each processor can transmit data at1millionfloating point values per second(while the other processors are doing the same)has a comp/comm ratio of10.Comparing the system’s ratio with the application’s allows us to determine whether the application will run well.If the system’s ratio is much lower than the application’s,we expect that the application will spend most of its time computing,little time waiting for internode data,and will run well.On the other hand,if the system’s ratio is much higher than the application’s,the application will spend most of its time waiting for communication phases to complete,and it will run poorly.Processors can also have low utilization if the computational load is not balanced.Thus, it is not good enough to have an application comp/comm ratio that is higher than the system’s. Many regular problems,such as FFT and SOR(described in the next two sections),present the same computational load to each node,regardless of the input data.Other algorithms, however,require variable amounts of computation.In Cholesky factorization[5,2],each processor is assigned afixed portion of the matrix on which to operate.However,the number of operations performed on each portion is a function of the input data.Some processors may be idle,while others are busy.This load imbalance can be lessened by choosing a small block size.However,this decreases grain size and thus communication efficiency.There is a tension between making the block size small,to increase load balance, and making it large,to amortize thefixed message cost overhead.Meerkat’s comp/comm ratio is a function of message size and system size,as shown in Figure5.7.These curves were generated by dividing the nominal node execution rate(10 MFLOPS)by the per-node internode bandwidth(shown in Figure5.6).Consider a sample use of these curves.Assume that we want to know how small we256-Node Delta 256-Node Meerkat 144-Node Meerkat 64-Node Meerkat 16-Node Meerkat|||||||10|||||||||100|||||||||1000||||||10|||||||||100|||||||||1000|Message Size (Double Words)F L O P /D o u b l e -W o r d M o v e dFigure 5.7:Meerkat and Delta Computation/Communication Ratiocan make the input to an FFT algorithm on a 64-node Meerkat without poor processor utilization.The input size is measured in points;each point requires two double words.Because FFT divides the input data evenly across all of the nodes,and communicates this data between pairs of nodes at each communication step,the input size will be 32times the message size:J.P.Singh gives large-message ratios for several commercial multicomputers[10].These are reproduced in Table5.3,along with the values we measured on Delta and Meerkat. While we have listed ourfigures with Singh’s,we note that his were derived from simple calculations,while ours started with measured bisection bandwidths.This makes the two sets of numbers not perfectly comparable,but we feel they are close enough to warrant rough comparison.Table5.3:Large-Message Computation/Communication Ratios For Meerkat and Several Commercial Systems(partly from J.P.Singh)Comp/Comm Ratio5811162050100144Singh also gives the computation and communication functions for several represen-tative numerical algorithms as a function of input and system sizes.These are shown in Table5.4;is the problem input size,is the number of processors.Table5.4:Computation/Communication Ratios For Several Numerical Algorithms (From J.P.Singh)CommunicationLU DecompositionFFTBy comparing an algorithm’s comp/comm ratio with the system’s ratio,we can estimate how a particular problem and input size will run on a particular system.5.9Performance of 1-D FFTFFT,a common computational problem for large parallel systems,often has poor perfor-mance,although speedup would be linear if communication cost was zero.Figure 5.8shows Meerkat’s and Delta’s speedup achieved on a one-dimensional FFT [3]as a function of the number of nodes applied to the problem.Curves for two input sizes are shown:4096and 32768points.The input points are evenly spread amongst the nodes;each point consists of a pair double precision floating point values.Ideal Speedup Meerkat 32kMeerkat 4k Delta 32kDelta 4k|0|50|100|150|200|250|0|20|40|60|80|100|120|140 Number of NodesS p e e d u pFigure 5.8:Speedup of 4k-and 32k-Point FFTThe total amount of computation is a function of the problem size,not the number of processors applied to the problem.Withpoints andprocessors,there aresteps.Each step takes time proportional to ,and the last steps require communication.Thus,as the number of processors increases,and the total running time decreases,theeffect of communication may dominate.Also,while the number of messages each node sends per step is constant,the message size is proportional to。
Defect correction method of the mask, defect corre
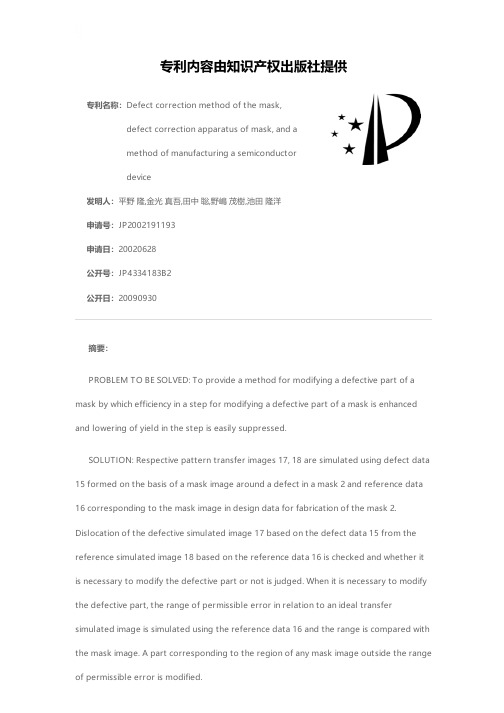
专利名称:Defect correction method of the mask,defect correction apparatus of mask, and amethod of manufacturing a semiconductordevice发明人:平野 隆,金光 真吾,田中 聡,野嶋 茂樹,池田 隆洋申请号:JP2002191193申请日:20020628公开号:JP4334183B2公开日:20090930专利内容由知识产权出版社提供摘要:PROBLEM TO BE SOLVED: To provide a method for modifying a defective part of a mask by which efficiency in a step for modifying a defective part of a mask is enhanced and lowering of yield in the step is easily suppressed.SOLUTION: Respective pattern transfer images 17, 18 are simulated using defect data15 formed on the basis of a mask image around a defect in a mask 2 and reference data16 corresponding to the mask image in design data for fabrication of the mask 2. Dislocation of the defective simulated image 17 based on the defect data 15 from the reference simulated image 18 based on the reference data 16 is checked and whether it is necessary to modify the defective part or not is judged. When it is necessary to modify the defective part, the range of permissible error in relation to an ideal transfer simulated image is simulated using the reference data 16 and the range is compared with the mask image. A part corresponding to the region of any mask image outside the range of permissible error is modified.COPYRIGHT: (C)2004,JPO申请人:株式会社東芝,大日本印刷株式会社地址:東京都港区芝浦一丁目1番1号,東京都新宿区市谷加賀町一丁目1番1号国籍:JP,JP代理人:鈴江 武彦,村松 貞男,橋本 良郎,河野 哲,中村 誠,河井 将次更多信息请下载全文后查看。
疼痛评估与管理指南说明书

239)and the PQRST mnemonic.Electronic templates and bedside charts were created to enable accurate recording.An education programme consisting of a video and poster presen-tation were implemented to support this.The assessment tool was piloted on the in-patient unit with plans to roll out across all services following a period of evaluation.Pre-and post-implementation audits enabled review of the effectiveness of the project.Results A pre-implementation audit highlighted that pain assessments were being conducted,however,the quality of these was varied.Mid-point and end of pilot audits identified that100%of sampled patients were now undergoing a thor-ough pain assessment with comprehensive documentation on a regular basis.Nurses reported increased confidence in pain assessment methods,the medical team utilised the pain assess-ments to aid clinical decision making and patients reported feeling that their pain management was important to the team.Conclusions The implementation of an adapted pain assess-ment tool has proven beneficial for both patients and profes-sionals.It has also enabled the hospice to evidence alignment with best practice.The well planned,evidence based,targeted approach to managing the project has encouraged buy-in from the teams,resulting in successful implementation.P-178IMPROVING PAIN INTERVENTION CHART(PIC)COMPLETION:A QUALITY IMPROVEMENT PROJECT(QIP)Olivia Aston,Stacey Taylor,Audrey Geary,Claire Walmsley,Anne Finucane,Rosie Morrison, Aaron Sutherland,Elizabeth Arnold,Emily McCall-Smith,Juliet Spiller,Libby Sampey, Louisa Marshall,Rachel Kemp.Marie Curie,Edinburgh,UK10.1136/spcare-2022-HUNC.194Background Understanding the effect of analgesia on pain helps guide management(Jenson,2003).This recognition led to the creation of pain assessment tools(Hølen,Hjermstad, Loge,Fayers,et al.,2006;Hjermstad,Gibbins,Haugen,Cara-ceni et al.,2008).PIC completion at the hospice was low. Staff reported a number of reasons for this,one being the format of the PIC chart.Aim Improve PIC completion in a hospice in-patient unit setting.Method A quality improvement approach using a series of Plan,Do,Study,Act(PDSA)cycles was undertaken(Jones, Vaux&Olsson-Brown,2019;T aylor,McNicholas,Nicolay, Darzi et al.,2014).A baseline measure was established of PIC for70analgesic medications prescribed to seven patients(10/ patient).T wo PDSA cycles were then undertaken and PICs reviewed.Results At baseline,10out of70medications were correctly completed on the PIC(14%).Altering the PIC allowed more space for writing details and more room for multiple interven-tions to be documented on a single PIC sheet.After PDSA cycle1,involving15PIC,completion increased to27%(41/ 150).Further PIC re-design aimed at increasing the efficiency with more tick box options instead of written descriptions. Following PDSA cycle2,involving8PIC,completion increased further to36%(29/80).Across both PDSA cycles,it was apparent that PIC completion was much lower for patients dying compared with non-dying(11%vs.46.5%).Staff feedback indicated time constraint was the predomi-nant barrier as well as PICs lacking prompts for recognition of non-verbal signs,therefore less useful for unconscious or dying patients.Conclusion Although PIC completion rate improved with increasing chart efficiency(as feedback indicated time was the most limiting factor),we did not see the overall improvement in PIC completion that we hoped for.However,low levels of PIC completion are not necessarily indicative of poor pain management and we were reassured that hospice staff demon-strated awareness of medication efficacy in their daily practice. Our results have generated significant questions and further work is necessary.Recommendations include the addition of non-verbal signs to the PICs to specifically improve PIC com-pletion for dying patients and the qualitative investigation of staff perception of PIC completion.P-179NON-INVASIVE TECHNOLOGY TO ASSESS HYDRATION IN ADVANCED CANCER TO EXPLORE RELATIONSHIPSBETWEEN FLUID-STATUS AND SYMPTOMS AT THE END-OF-LIFE:AN OBSERVATIONAL STUDY USINGBIOELECTRICAL IMPEDANCE ANALYSIS(BIA)1Amara Callistus Nwosu,2Sarah Stanley,3Alexandra McDougall,4Catriona Mayland, 5Stephen Mason,5John Ellershaw.1Lancaster University,Lancaster,UK;2Marie Curie Hospice Liverpool,Liverpool,UK;3The Clatterbridge Cancer Centre,Liverpool,UK; 4University of Sheffield,Sheffield,UK;5Palliative Care Unit,University of Liverpool,Liverpool, UK10.1136/spcare-2022-HUNC.195Background The role of hydration in causing or alleviating suffering in advanced cancer is poorly understood.Bioelectri-cal impedance analysis(BIA)is an accurate validated method of assessing hydration status.Previous BIA research demon-strates significant relationships with hydration status,symp-toms,and survival in advanced cancer.Further work is needed to study these associations in the dying.Aim T o evaluate hydration and its relationship with clinical symptoms in dying cancer patients.Methodology We conducted an observational study of patients with advanced cancer in3centres(two hospices and a hospi-tal-based specialist palliative care in-patient unit).We used an advance consent methodology to conduct hydration assess-ments of participants as they entered the dying phase.We recorded hydration status(via BIA Impedance index:Height–H2/Resistance-R),symptoms,physical signs,and quality-of-life assessments.Results One hundred and twenty-five people were recruited (males n=74(59.2%),females,n=51(40.8%).We repeated assessments in18(14.4%)participants when they were dying. Hydration status(H2/R)of the dying patients(n=18,M= 49.55,SD=16.00)was not significantly different compared to their baseline hydration assessment(M=50.96,SD= 12.13;t(17)=0.636,p=0.53).Increasing hydration level(increased H2/R)was significantly associated with oedema(r=0.509,p<0.001).Lower hydra-tion level(reduced H2/R)was associated with patient concern of poorer health(r=-0.19,p=0.034),improved sleep(r=-0.235,p=0.009),poorer appetite(r=-0.273,p=0.002), increased anxiety(r=-0.192,p=0.032),worsening dry mouth (r=-0.242,p=0.007)and sunken eyes(r=-0.333,p<0.001). Conclusions Hydration status was significantly associated with physical signs and symptoms in advanced disease.No signifi-cant difference in hydration status were observable in dying patients compared to baseline.Bioimpedance analysis was wellBMJ Supportive&Palliative Care2022;12(Suppl3):A1–A96A77copyright. on December 25, 2023 by guest. Protected by / BMJ Support Palliat Care: first published as 10.1136/spcare-2022-HUNC.194 on 19 November 2022. Downloaded from。
L3Harris AN PRC-161 手持链16无线电说明书

BATTLEFIELD AWARENESS AND TARGETING SYSTEM-DISMOUNTEDAN/PRC-161 Handheld Link 16 RadioThe L3Harris Battlefield Awareness and Targeting System-Dismounted (BATS-D) AN/PRC-161 radio fuses air and ground (friendly and enemy) Situational Awareness (SA) in the palm of your hand. This ruggedized, handheld radio delivers real-time Link 16 communications to dismounted warfighters at the tactical edge. The radio can be used vest-worn, handheld or mounted and is ideal for bringing full Link 16 network access to ground forces including Joint Terminal Attack Controllers (JTACs), Forward Air Controllers (FACs) and Tactical Air Control Party (TACP) specialists.PRODUCT DESCRIPTIONThis handheld radio arms dismounted JTACs and FACs with a direct connection into the Link 16 network to digitally call for fire and provide all nodes with accurate SA in a joint integrated air/ground common operational picture. This direct link between ground warfighters and Close Air Support (CAS) aircraft dramatically shortens the kill chain anddecreases the risk of fratricide.The BATS-D’s Enhanced Throughput (ET) mode boosts Link 16’s protected data rate of 115 Kbps to over 1.1 Mbps. L3Harris is also the first Link 16 provider to integrate Concurrent Multinet (CMN)and Concurrent Contention Receive (CCR) advancements across its portfolio of non-developmental items, providing warfighters with Concurrent Multiple Reception (CMR) capabilities for assured access to mission-critical information. These features, coupled with Link 16 Enhanced Throughput (ET) modes, will enable network planners to fully optimize network performance, allowing maximum participants sharing maximum capacity of information to support evolving mission requirements. The BATS-D also implements the latest high assurance algorithms using a field proven programmable Cryptographic Modernization compliant engine to securely serve joint and coalition mission requirements, while maintaining backwards compatibility with legacy communications systems.CONFIGURABLE FOR A VARIETY OF OPERATIONS:>Autonomous Link 16 Untethered ModeEnter the network without user interaction and transmit Precise Participant Location and Identification (PPLI) to the network including emergency indication if needed>Fully Tethered ModeNett Warrior, USB, or Ethernet cabled to a tablet device or laptop computer to exchange/display situational awareness data (PPLI)and Platform J host data with the Link 16 networkUse of U.S. DoD visual information does not imply or constitute DoD endorsement.These item(s)/data have been reviewed in accordance with the International Traffic in Arms Regulations (ITAR), 22 CFR part 120.11, and the Export Administration Regulations (EAR), 15 CFR 734(3)(b)(3), and may be released without export restrictions.L3Harris Technologies is an agile global aerospace and defense technology innovator, delivering end-to-end solutions that meet customers’ mission-critical needs. The company provides advanced defense and commercial technologies across air, land, sea, space and cyber domains.Use of U.S. DoD visual information does not imply or constitute DoD endorsement.Battlefield Awareness and Targeting System-Dismounted© 2022 L3Harris Technologies, Inc. | 12/2022 | BCS | 22-DSD-275 | Rev-201SPECIFICATIONS AND TECHNICAL FEATURES MISSION FLEXIBILITY>Fully functional Link 16 radio >Handheld/small form factor>Coordinate and maneuver assets instantaneously >Embedded SAASM GPS>Standardized quick-change rechargeable battery >J-Voice and Platform-J data capable >Built-in keypad/display>Voice PTT Key and mic/speaker>Extremely low size, weight, and power>Jam resistant for operations in contested and denied access environments>Coalition interoperable>Rugged design (MIL-STD 810-F)SITUATIONAL AWARENESS>Friendly force tracking>Provides air and ground common operational picture>Tethered mode can interface with: Android Tactical Radio Extension (ATRAX);-Android/ Windows Tactical Assault Kit (ATAK/TAK); AirDefense Systems Integrator (ADSI®); Joint Range Extension (JRE); Gateway Manager; LinkPRO® -KILLSWITCH; APASS; DASS; WINTAK COMMAND AND CONTROL>J12 mission management to any non-C2TARGET AT TACK>Digitally-aided Close Air Support >Cursor on Target (CoT) capable >Shortens kill chain—F2T2EA(Find, Fix, Track, Target, Engage, Assess) >JTAC target POSID/9-line/BDA >Target update >Imagery and data >Mobile target attack NSA CERTIFIED>Link 16 CMI Compliant>Embeds NSA Certified KOV-56 Crypto Engine (L3Harris ES-1850)PERFORMANCE >Frequency Range: 969 to 1206 MHz Link 16 >Transmission Modes: L ink 16 TDMA, All OP modes and enhanced throughput>Antenna Ports: -Link 16 50 Ω -GPS 50 Ω>Batteries:12 V Rechargeable Lithium-Ion; 6.8 Ah >Data Interfaces: Ethernet/USB/Nett Warrior >Dimensions:2.6” (w) x 8.4” (h) x 1.7” (h); 6.6 cm (w) x 21.3 cm (h) x 4.3 cm (d) >Volume:36 cu in. with battery; 23 cu in. without battery>Weight:2.19 lb with battery; 1.28 lb without battery >GPS: Embedded SAASMRANGE>Clear line-of-sight transmission range in excess of 75 nm TRANSMITTER >Power Output: 8 WWAVEFORMS >L-band:Link 16 data and voice including enhanced throughput modes ENVIRONMENTAL>Operating Temperature: -31° to +60° C;-23.8° to +140° F>Storage Temperature: -33° to +71° C; -27.4° to +159.8° F>Immersion: 2 m; 20 m option1025 W. NASA Boulevard Melbourne, FL 32919t 833 537 6837*************************。
混合磨玻璃结节肺腺癌的CT表现与其病理等级的相关性分析

混合磨玻璃结节肺腺癌的CT表现与其病理等级的相关性分析李丽、,郭孟刚2,何正光、,罗晓斌、,赵勇、,杜发旺、,王述红、,曾浩5 The correlation anolysic beWveen CT findings and paWologiccl grade of mixea ground一glass nonule of lurid adenoccoinomaLI Li1,GUO Mepyuany2,HE Zhepyuuany1,LUO XiaoPin1,ZHAO Yony1,DU Fawany1,WANG SSuUoxy1,ZENG Hvo51Departmenr o P Respiratora and Criticai Menicine;6 Departfenr O Thoracie Suraera;4Department o P Raatfpy,Suining Central Hospital, SicOuaa Suinind629000,China.[Abstract]Objective:To iuveshgato cor/Otiou bet/eec CT findings and patyological grade of mixed ground-gOss uoPulo of Ong adenoca/iuoia.Method::The data of118pabe/ts with mixed ground-gOss Ong uoPulos ouchest CT and Ong aUe/oca/iuomc coUirmed by surge—and hathology were selected.According to the pathologicalcharacteristics,they were divided into three g/xps,iucOUing17,29aod72cases of adeuocamiuomc iu situ g/vp,minimally invasive adeuoca/iuoig g/vp and invasive aUe/oca/iuomc g—vp respectively.The overall CT findingsand solid compoue/ts CT findings of mixed ground-gOss Ong uoPulos iu the three g/xps were compared respectively.Receiver operaCng cha—ctePshc curve(ROC)was drawu ou the size of uodules,the size of solid compoue/ts,theproporPou of solid compoue/ts,and the CT value of solid compoue/ts to determiue the best cut-off value for prePie-ting invasive aUe/oca/iuoma,and calcuOto the seusitivity and specific/y.Results:The size,shape,air b/uchogramsigu,vascuOr couvergeuce sign aod plepral inde/mCou sign of mixed ground-glass pulooua—uodules were compared amoug the three g/xps,and the differeucos were stabshcaby significant(P<2.25).The size of the solid com-poueut.the propoPiou of the solid compoueut,the CT value of the solid compoueut and the bonnda—of the solid com-poue/t were compared amoug the three g/xps,and the diNe/uces were stabsticaby significant(P<2.05).The bestcut-off value for predic/ng invasive adeuocamiuomc by the size of uoPulo was15.7mm,with sensitivity of2.976and specificity of2.733.The best cut-off value for prePic/nx invasive adeuocamiuomc by the size of solid compo-ue/t was5.7mm,with seusitivity of2.764and specificity of2.311.The best cut-off value for prePic/nx invasiveadeuocamiuomc by the proporPou of solid compoueut was33.7%,with seusitivity of2.736aod specific/y of2.935.The best cut-off value for predic/ng invasive adeuocamiuomc by the CT value of solid compoueut was-149. 2HU,with seusitivity of2.794aod specificity of2.326.Conclusion:The CT findings of mixed g/nnd-gOss uoPulo Ongadeuocamiuomc have cePaiu correObou with their pathoOvicgl grade.The size of uodules,the size of solid compo-ue/W,the proporPou of solid compoue/ts and the CT value of solid compoue/ts have impoPaot predic/ve value fortheir yathoOgical grade.【Key words i mixed grovcU-gOss uoPulo,Ong ade/ocarciuomc,solid puted tomographyModem Oucology2221,29(11):1883-1893【摘要】目的:探讨混合磨玻璃结节肺腺癌的CT表现与其病理等级的相关性。
安卓开发英文参考文献(精选120个最新)

随着社会经济的发展以及科学技术的进步,智能手机以及个人电脑被广泛应用在人们的日常生产生活中。
安卓操作系统作为智能的操作系统,其具有高度的开放性,使得智能手机以及个人电脑具有较大的应用优势,下面是安卓开发英文参考文献,欢迎借鉴参考。
安卓开发英文参考文献一: [1]Haomin Song,Duanqing Xu. The Design and Development of a Full Range of Display System for 3D Images Based on AndroidSmartphone[P]. Proceedings of the International Conference on Education, Management, Commerce and Society,2015. [2]Iva Evry Robyansah. The Development of “Ayo Membaca” Android Application for Reading Assessment[P]. Proceedings of the 2nd International Conference on Education Innovation (ICEI 2018),2018. [3]Qingru Lu,Haiyan Xin,Hui Huang,Yunlong Geng. Design and Development of Multifunction Map Software Based on AndroidPlatform[P]. Proceedings of the 2015 International Conference on Electromechanical Control Technology and Transportation,2015. [4]Hongsheng Zhang. Research on Software Development and Test Environment Automation based on Android Platform[P]. Proceedings of the 3rd International Conference on Mechatronics Engineering and Information Technology (ICMEIT 2019),2019. [5]Yong-fei Ye,Ming-he Liu,Xiao Zhang,Xing-hua Sun,Nai-di Liu. Application and Research of Blended Teaching Model in Programming Courses --- Android Application Development Course as an Example[P]. Proceedings of the 3d International Conference on Applied Social Science Research,2016. [6]Xinge Li. The development of designated driving application based on Android platform and Ali cloud sever[P]. Proceedings of the 2016 2nd Workshop on Advanced Research and Technology in Industry Applications,2016. [7]Winda Dwi Fitria,Achmad Lutfi. Development Of Wind’s Maze Chemistry Game Based On Android As A Learning Media On Hydrocarbon Matter For Eleventh Grade Senior High School[P]. Proceedings of the Seminar Nasional Kimia - National Seminar on Chemistry (SNK2018),2018. [8]Fuling Li,Yong Li. Development of Mobile Security Guard Based on Android System[P]. Proceedings of the 2015 International Conference on Automation, Mechanical Control and Computational Engineering,2015. [9]Qinhua Lin. Mobile terminal 3D image reconstruction program development based on Android[P]. Proceedings of the 2015International Conference on Automation, Mechanical Control and Computational Engineering,2015. [10]Anan Sutisna,Elais Retnowati,Adi Irvansyah. Development of Peer Tutors Learning Media based on Android Application to Improve Learners Independence[P]. Proceedings of the 2nd International Conference on Educational Sciences (ICES 2018),2019. [11]Agus Ria Kumara,Caraka Putra Bhakti,BudiAstuti,Suwarjo,Muhammad Alfarizqi Nizamuddin Ghiffari,Fathia Irbati Ammattulloh. Development of Android Application based on Holland's Theory of Individual Student Planning[P]. Joint proceedings of the International Conference on Social Science and Character Educations (IcoSSCE 2018) and International Conference on Social Studies, Moral, and Character Education (ICSMC 2018),2019. [12]Suherman,Defri Ahmad,Meira Parma Dewi,Heru Maulana. Paper Development of Actuarial E-learning Based on AndroidApplications[P]. Proceedings of the 2nd International Conference on Mathematics and Mathematics Education 2018 (ICM2E 2018),2018. [13]Lan-Xin Zhu,Jia-Ming Zhang,Xiao-Li Rui,Xiao Liang. Research and Development of Android Client and Server Information Interaction Framework[P]. Proceedings of the 3rd International Conference on Wireless Communication and Sensor Networks (WCSN 2016),2016. [14]Hongxin Hu,Ming Cui. Development Scheme of Mobile Campus Information Integration Platform Based on Android[P]. isccca-13,2013. [15]Junliang Wu,Liqing Mao. Study on Research Development and Application of Urban Logistics Platform Based on Android[P]. Proceedings of the 2018 6th International Conference on Machinery, Materials and Computing Technology (ICMMCT 2018),2018. [16]Xiafu Pan. Anti-addiction System Development Based on Android Smartphone[P]. Proceedings of the 2016 3rd International Conference on Materials Engineering, Manufacturing Technology and Control,2016. [17]Xiufeng Shao,Xuemei Liu,Lingling Zhao. Development and Reform of Android Mobile Application Development Curriculum[P]. Proceedings of the 2016 International Conference on Applied Mathematics, Simulation and Modelling,2016. [18]Hongchang Ke,Degang Kong. Research on Course Integration of Mobile Internet Device Programming (Android Program Development)[P]. Proceedings of the 2018 8th International Conference on Mechatronics, Computer and Education Informationization (MCEI 2018),2018. [19]Xin Xin Xie,Wen Zhun Huang. Research and Development of the Android Framework Smart Watches from the Data Security Point ofView[P]. Proceedings of the 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII2016),2016. [20]Abdel-All Marwa,Angell Blake,Jan Stephen,Praveen D,Joshi Rohina. The development of an Android platform to undertake a discrete choice experiment in a low resource setting.[J]. Archivesof public health=Archives belges de sante publique,2019,77. [21]Abdul Mutholib,Teddy S Gunawan,Jalel Chebil,Mira Kartiwi. Development of Portable Automatic Number Plate Recognition System on Android Mobile Phone[J]. IOP Conference Series: Materials Science and Engineering,2013,53(1). [22]Iliana Mohd Ali,Nooraida Samsudin. The Design and Development of BMI Calc Android Application[J]. IOP Conference Series: Materials Science and Engineering,2016,160(1). [23]Ashutosh Gupta,Tathagata Ghosh,Pradeep Kumar,Shruthi. S Bhawna. Development of Android Based Powered Intelligent Wheelchair for Quadriplegic Persons[J]. IOP Conference Series: Materials Science and Engineering,2017,225(1). [24]Ashutosh Gupta,Pradeep Kumar,Tathagata Ghosh,Shruthi. S Bhawna. Development of Android based Smart Power Saving System[J]. IOP Conference Series: Materials Science andEngineering,2017,225(1). [25]P Sihombing,Y M Siregar,J T Tarigan,I Jaya,A Turnip. Development of building security integration system using sensors, microcontroller and GPS (Global Positioning System) based android smartphone[J]. Journal of Physics: Conference Series,2018,978(1). [26]R F Rahmat,O R Fahrani,S Purnamawati,M F Pasha. The development of indonesian traditional bekel game in androidplatform[J]. Journal of Physics: Conference Series,2018,978(1). [27]P Hendikawati,R Arifudin,M Z Zahid. Development of computer-assisted instruction application for statistical data analysis android platform as learning resource[J]. Journal of Physics: Conference Series,2018,983(1). [28]Hartatik,F Febriyanto,H Munawaroh. Development ofApplications about Hazards and Preventions of Drug Based OnAndroid[J]. IOP Conference Series: Materials Science and Engineering,2018,333(1). [29]R Widyastuti,H Soegiyanto,Y Yusup. The Development of Geo Smart Based Android for Geography Learning Media on Hydrosphere Material and Its Impact towards Life on Earth[J]. IOP Conference Series: Earth and Environmental Science,2018,145(1). [30]Mohar Kassim,Ahmad Mujahid Ahmad Zaidi,Rahmat Sholihin Mokhtar. Development of Android Application for Measuring Cardiovascular Endurance Fitness for Military Cadet Officers[J]. Journal of Physics: Conference Series,2018,1020(1). 安卓开发英文参考文献二: [31]Abdul Rahman,Mulbar Usman,Ansari Saleh Ahmar. The Development of Android and Web-based Logical Thinking Measurement Tools as an Alternative Solution for Research Instruments[J]. Journal of Physics: Conference Series,2018,1028(1). [32]M. Reza Dwi Saputra,Heru Kuswanto. Development of Physics Mobile (Android) Learning Themed Indonesian Culture Hombo Batu onthe Topic of Newton’s Law and Parabolic Motion for Class XSMA/MA[J]. Journal of Physics: Conference Series,2018,1097(1). [33]M Yusro,Rikawarastuti. Development of Smart Infusion Control and Monitoring System (SICoMS) Based Web and Android Application[J]. IOP Conference Series: Materials Science andEngineering,2018,434(1). [34]Daniel Patricko Hutabarat,Santoso Budijono,Robby Saleh. Development of home security system using ESP8266 and android smartphone as the monitoring tool[J]. IOP Conference Series: Earth and Environmental Science,2018,195(1). [35]C M Zhang,L S Zhang,T Zhang,S T Zhang. Development of a machine tool auxiliary machining system based on android phone[J]. IOP Conference Series: Materials Science andEngineering,2019,504(1). [36]Ryan Ari Setyawan,Selo,Bimo Sunarfri Hantono. Effect of the Application of TEA Algorithm on the Development of Secure Phone Application Android Smartphones[J]. Journal of Physics: Conference Series,2019,1175(1). [37]M Basyir,W Mellyssa,S Suryati,M Munawar. Receiver Apps Development for Emergency Reporting System Based on AndroidPlatform[J]. IOP Conference Series: Materials Science and Engineering,2019,536(1). [38]B Angrian,T R Sahroni. Development of vendor management ande-Procurement systems using android platform[J]. IOP Conference Series: Materials Science and Engineering,2019,528(1). [39]O F Irianti,A Qohar. Development of Android BasedInstructional Media of Algebraic Tiles for Quadratic Equation[J]. Journal of Physics: Conference Series,2019,1227(1). [40]Fita Permata Sari,L. Ratnaningtyas,Insih Wilujeng,Jumadi,Heru Kuswanto. Development of Android Comics media on Thermodynamic Experiment to Map the Science Process Skill for Senior HighSchool[J]. Journal of Physics: Conference Series,2019,1233(1). [41]Puji Iman Nursuhud,Danis Alif Oktavia,Mas Aji Kurniawan,Insih Wilujeng,Jumadi,Heru Kuswanto. Multimedia Learning ModulesDevelopment based on Android Assisted in Light DiffractionConcept[J]. Journal of Physics: Conference Series,2019,1233(1). [42]Dadan Rosana,Didik Setyawarno,Wita Setyaningsih. Development Model of Students’ Innert-Depend Strategies to Face Disruption Era Through Best Practice Film of Android Based Learning of Pancasila Character Value[J]. Journal of Physics: ConferenceSeries,2019,1233(1). [43]Syafridatun Nikmah,Faruq Haroky,Jumadi,Insih Wilujeng,Heru Kuswanto. Development of Android Comic Media for the Chapter of Newton’s Gravity to Map Learning Motivation of Students[J]. Journal of Physics: Conference Series,2019,1233(1). [44]Firdy Yuana,Sugeng Rianto,Achmad Hidayat. Development of Balmer Series Experiment Simulator in Mobile and AndroidApplications[J]. IOP Conference Series: Materials Science and Engineering,2019,546(5). [45]Arilson José de Oliveira Júnior,Silvia Regina Lucas de Souza,Vasco Fitas da Cruz,Tiago Aparecido Vicentin,Andreia Soares Gon?alves Glavina. Development of an android APP to calculatethermal comfort indexes on animals and people[J]. Computers and Electronics in Agriculture,2018,151. [46]Gabriel B. Holanda,Jo?o Wellington M. Souza,Daniel A.Lima,Leandro B. Marinho,Anaxágoras M. Gir?o,Jo?o Batista Bezerra Frota,Pedro P. Rebou?as Filho. Development of OCR system on android platforms to aid reading with a refreshable braille display in real time[J]. Measurement,2018,120. [47]Omar Ben Bahri,Kamel Besbes. Didactic satellite based on Android platform for space operation demonstration anddevelopment[J]. Advances in Space Research,2018,61(6). [48]Alexander A S Gunawan,William,Boby Hartanto,AdityaMili,Widodo Budiharto,Afan G Salman,Natalia Chandra. Development of Affordable and Powerful Swarm Mobile Robot Based on Smartphone Android and IOIO board[J]. Procedia Computer Science,2017,116. [49]Tao Liu,Wen Chen,Yifan Wang,Wei Wu,Chengming Sun,Jinfeng Ding,Wenshan Guo. Rice and wheat grain counting method and software development based on Android system[J]. Computers and Electronics in Agriculture,2017,141. [50]Weizhao Yuan,Hoang H. Nguyen,Lingxiao Jiang,YutingChen,Jianjun Zhao,Haibo Yu. API recommendation for event-driven Android application development[J]. Information and Software Technology,2018. [51]Faizal Johan Atletiko. Development of Android Application for Courier Monitoring System[J]. Procedia Computer Science,2017,124. [52]Krill, Paul. Apple's Swift takes first steps toward Android app development[J]. ,2015. [53]Bruce Harpham,Bruce Harpham. How to break into Android development[J]. ,2016. [54]Paul Krill,Paul Krill. Android Studio 2.1 eases path to Android N development[J]. ,2016. [55]S A Moraru,A C Manea,D Kristaly,C L Cristoiu. THE DEVELOPMENT OF AN INFORMATION SYSTEM FOR TOURISTS USING THE ANDROID PLATFORM (II)[J]. Bulletin of the Transilvania University of Brasov. Engineering Sciences. Series I,2015,8(2). [56]D Kristaly,A C Manea,S A Moraru,C L Cristoiu. THE DEVELOPMENT OF AN INFORMATION SYSTEM FOR TOURISTS USING THE ANDROID PLATFORM (I)[J]. Bulletin of the Transilvania University of Brasov. Engineering Sciences. Series I,2015,8(2). [57]. Robotics - Androids; New Robotics - Androids Findings from S. Alfayad and Co-Researchers Described (Development of lightweight hydraulic cylinder for humanoid robots applications)[J]. Journal of Engineering,2018. [60]Anupama S,U. B Mahadevaswamy. Design and Development of a Smart Device for Energy Monitoring and Control of Domestic Appliances: An Android Application[J]. International Journal of Image, Graphics and Signal Processing(IJIGSP),2018,10(1). 安卓开发英文参考文献三: [61]Muhammad Noman Riaz,Adeel Ikram. Development of a Secure SMS Application using Advanced Encryption Standard (AES) on Android Platform[J]. International Journal of Mathematical Sciences and Computing(IJMSC),2018,4(2). [62]FURUYAMA Shoichi,NAKAMURA Takeru,KOBAYASHI Tatsuya,FUJISHIMA Masaki,MANAKA Atsushi,IRIE Mitsuteru. Development of Water Quality Measurement Application on Android Device[J]. Journal of Arid Land Studies,2017,27(1). [63]TAKEI Sho,YAMAUCHI Daichi,MORITA Yoshifumi,SATO Noritaka. Development of an android model of knee joint with patella[J]. The Proceedings of JSME annual Conference on Robotics and Mechatronics (Robomec),2016,2016(0). [64]NAKAGITA Tomonori,KAWATANI Ryoji. 1P2-A03 Development of welfare truck robot control system by Android devices(Welfare Robotics and Mechatronics (3))[J]. The Proceedings of JSME annual Conference on Robotics and Mechatronics (Robomec),2014,2014(0). [65]Sampei KOTA,Ogawa Miho,Cotes Carlos,MIKI Norihisa. 3A1-R03 Development of Android Applications by Using See-Through-TypeWearable Eye-Gaze Tracking System(Wearable Robotics)[J]. The Proceedings of JSME annual Conference on Robotics and Mechatronics (Robomec),2014,2014(0). [66]AOKI Toshihiro,TANIGUCHI Katsunori,YOSHIOKA Masao,YAMAGUCHI Satoshi,UEDA Makoto,NAKAMA Yuuki. 2A18 Engineering education using the theme of Android application development[J]. Proceedings of Annual Conference of Japanese Society for EngineeringEducation,2014,2014(0). [67]MIURA Yukiko,MIYAMOTO Akira,Yi Yu,Gang Yu Zhi,KUCHII Shigeru. Research and Development of the Social Robot Using the Recognition Technology and Android Application[J]. The Proceedings of JSME annual Conference on Robotics and Mechatronics(Robomec),2016,2016(0). [68]Hosam Farouk El-Sofany,Samir Abou El-Seoud,Hassan M. Alwadani,Amer E. Alwadani. Development of Mobile EducationalServices Application to Improve Educational Outcomes using Android Technology[J]. International Journal of Interactive Mobile Technologies,2014,8(2). [69]V. Makarenko,O. Olshevska,Yu. Kornienko. AN ARCHITECTURAL APPROACH FOR QUALITY IMPROVING OF ANDROID APPLICATIONS DEVELOPMENT WHICH IMPLEMENTED TO COMMUNICATION APPLICATION FOR MECHATRONICS ROBOT LABORATORY ONAFT[J]. Avtomatizaci? Tehnologi?eskih i Biznes-Processov,2017,9(3). [70]Fikrul Arif Nadra,Heri Kurniawan,Muhammad Hafizhuddin Hilman. PROPOSED ARCHITECTURE AND THE DEVELOPMENT OF NFCAFE: AN NFC-BASED ANDROID MOBILE APPLICATIONS FOR TRADING TRANSACTION SYSTEM IN CAFETARIA[J]. Jurnal Ilmu Komputer dan Informasi,2013,6(1). [71]Shi Yi Ping. The Development of Tanks War Mobile Game based on Android System[J]. MATEC Web of Conferences,2016,63. [72]Fajar Nugroho,Pudji Muljono,Irman Hermadi. DEVELOPMENT OF ONLINE PUBLIC ACCESS CATALOG (OPAC) BASED ANDROID ON LIBRARY UPN "VETERAN" JAKARTA[J]. Edulib: Journal of Library and Information Science,2017,7(2). [73]Arturo Mascorro,Francisco Mesa,Jose Alvarez,Laura Cruz. Native Development Kit and Software Development Kit Comparison for Android Applications[J]. International Journal of Information and Communication Technologies in Education,2017,6(3). [74]César Fernández,María Asunción Vicente,M. Mar Galotto,Miguel Martinez‐Rach,Alejandro Pomares. Improving student engagement on programming using app development with Android devices[J]. Computer Applications in Engineering Education,2017,25(5). [75]Bárbara Crespo,Guillermo Rey,Carla Míguez,José Luis Míguez Tabarés,José De Lara. Development of a new android application toremotely control a micro‐cogeneration system as e‐learning tool[J]. Computer Applications in Engineering Education,2016,24(4). [76]Junwei Wu,Liwei Shen,Wunan Guo,Wenyun Zhao. Code recommendation for android development: how does it work and what can be improved?[J]. Science China Information Sciences,2017,60(9). [77]Yi-ping SHI,Jian-ping YUAN,Peng JIANG. The Development of Mobile Shopping System Based on Android Platform[P]. 2ndInternational Conference on Applied Mechanics and Mechatronics Engineering (AMME 2017),2017. [78]YUNJU CHANG,XUESONG LENG,GUOWAN MU,HANYU QIN,GUANG SU,ZHIHENG YANG,KUIYU LAN. Design and Development of Mobile Learning Platform Based on Android for College Physics Experiment Courses[P]. 3rd International Conference on Electronic Information Technology and Intellectualization (ICEITI 2017),2017. [79]Qiang CHEN,Jia-Jia WU. Research on Course of Integrating Android Development and Embedded Software[P]. 3rd International Conference on Education and Social Development (ICESD 2017),2017. [80]Alexander Chatzigeorgiou,Tryfon L. Theodorou,George E. Violettas,Stelios Xinogalos. Blending an Android development course with software engineering concepts[J]. Education and Information Technologies,2016,21(6). [81]Yasushige Ishikawa,Craig Smith,Mutsumi Kondo,IchiroAkano,Kate Maher,Norihisa Wada. Development and Use of an EFL Reading Practice Application for an Android Tablet Computer[J]. International Journal of Mobile and Blended Learning(IJMBL),2014,6(3). [82]Liguo Yu. From Android Bug Reports to Android Bug Handling Process: An Empirical Study of Open-Source Development[J]. International Journal of Open Source Software and Processes (IJOSSP),2016,7(4). [83]Nurul Farhana Jumaat,Zaidatun Tasir. Integrating Project Based Learning Environment into the Design and Development of Mobile Apps for Learning 2D-Animation[J]. Procedia - Social and Behavioral Sciences,2013,103. [84]Chan Daraly Chin,Watit Benjapolakul. NFC-enabled Android Smartphone Application Development to Hide 4 Digits Passcode for Access Control System[J]. Procedia Computer Science,2016,86. [85]Haolun Xu,Jinling Zhao,YaLi Li,ChangQuan Xu. The development of SHS-SWTHS designing software based on windows and android mobile device platforms[J]. Renewable Energy,2015,84. [86]Agnes Kurniati,Nadia,Fidelson Tanzil,Fredy Purnomo. Game Development “Tales of Mamochi” with Role Playing Game Concept Based on Android[J]. Procedia Computer Science,2015,59. [87]Tom Gaffney. Following in the footsteps of Windows: how Android malware development is looking very familiar[J]. Network Security,2013,2013(8). [88]Rattanathip Rattanachai,Ponlawat Sreekaewin,Thitiporn Sittichailapa. Development of Thai Rice Implantation Recommend System Based on Android Operating System[J]. Procedia - Social and Behavioral Sciences,2015,197. [89]Farshad Vesali,Mahmoud Omid,Amy Kaleita,Hossein Mobli. Development of an android app to estimate chlorophyll content ofcorn leaves based on contact imaging[J]. Computers and Electronicsin Agriculture,2015,116. [90]Pedro Daniel Urbina Coronado,Horacio Ahuett-Garza,Vishnu-Baba Sundaresan,Ruben Morales-Menendez,Kang Li. Development of an Android OS Based Controller of a Double Motor Propulsion System for Connected Electric Vehicles and Communication Delays Analysis[J]. Mathematical Problems in Engineering,2015,2015. 安卓开发英文参考文献四: [91]Andy S.Y. Lai,S.Y. Leung. Mobile Bluetooth-Based Game Development Using Arduino on Android Platform[J]. Applied Mechanics and Materials,2013,2748. [92]Yan Mei liu,Yong Gang Li,Hua E Wang. Research and Development of the Sweater Mass Customization System Based on Android[J].Applied Mechanics and Materials,2013,2755. [93]Yi Ping Shi,Hong Wang. The Development of Intelligent Mobile Phone Game Based on Android System[J]. Applied Mechanics and Materials,2013,2529. [94]Hong Xin Hu,Ming Cui. Development Scheme of Mobile Campus Information Integration Platform Based on Android[J]. Applied Mechanics and Materials,2013,2560. [95]Yi Ping Shi. The Development of Sokoban Game Based on Android System[J]. Applied Mechanics and Materials,2014,3334. [96]Shuang Zhu Zhao,Ting Zhang,Xiao Na Liu. An Application Development Based on Android Platform - The Design and Realization of the Mood Release System[J]. Applied Mechanics andMaterials,2014,2948. [97]Jin Zang,Xue Yu Chen,Yin Hu,Miao Yang,Wei Ping Wang. Design and Development of the Intelligent Glasses Based on Android[J]. Applied Mechanics and Materials,2014,3634. [98]Bin Wen Fan,Xuan Xuan Fang,Ga Pan. The Fax Software Development of Smart Fixed Phone Based on Android Platform[J]. Applied Mechanics and Materials,2014,3391. [99]Ji Hai Chen,Qiu Jun Li. Development of RFID Reader System Based on Android[J]. Applied Mechanics and Materials,2015,3752. [100]Ming Li Ding,Lu Peng Li,Ming Lun Ding. Development of Bluetooth Roll Call System Based on Android Platform[J]. Applied Mechanics and Materials,2014,3147. [101]Xue Yu Chen,Jin Zang,Miao Yang,Wei Ping Wang,Yin Hu. Design and Development of Self-Help Emergency Device Based on the Android Intelligence Platform[J]. Applied Mechanics and Materials,2014,3634. [102]Shao Feng Lin,Yao Zhou,Ruo Yin Wang,Jing Jing Zhang. GoogleMap Application Development in Android Platform[J]. Applied Mechanics and Materials,2014,2987. [103]Qiang Cao,Hua Lai,Wen Qing Ge,Ming Jie Qi. Research and Development of Mobile Termination for the Steel Quality Evaluation System Based on Android[J]. Applied Mechanics andMaterials,2014,2987. [104]Shi Wei Xu,Zhe Min Li,Jian Hua Zhang,Fan Tao Kong. Development of the Monitoring and Early Warning System for Agricultural Market Information Based on Android Smart Phone[J]. Advanced Materials Research,2014,3382. [105]Xiang Huang. Software Development and Application Research Based on Android Operating System[J]. Applied Mechanics and Materials,2014,3207. [106]Chun Mei Li. Design and Development of English Electronic Dictionary Based on Android Platform[J]. Advanced Materials Research,2014,3137. [107]Li Wu,Jian Wei Shen. The Development of Android Mobile Game Based on App Inventor2[J]. Advanced Materials Research,2014,3227. [108]Alejandro Acosta,Francisco Almeida. Android $$^\mathrm{TM}$$ <mrow> TM development and performance analysis[J]. The Journal of Supercomputing,2014,70(2).</mrow> [109]Munihanumaiah, P.,Sarojadevi, H.. Design and development of network-based consumer applications on Android[P]. Computing for Sustainable Global Development (INDIACom), 2014 International Conference on,2014. [110]Wen-Pinn Fang,Sheng-Hsuan Lu,Ming-Hao Liu,Ting-HungLai,Shan-Chun Hung,Yin-Feng Huang,Chii-Jen Chen. Web Base Android Application Development System[P]. Computer, Consumer and Control (IS3C), 2014 International Symposium on,2014. [111]Abtahi, F.,Berndtsson, A.,Abtahi, S.,Seoane, F.,Lindecrantz, K.. Development and preliminary evaluation of an Android based heart rate variability biofeedback system[P]. Engineering in Medicine and Biology Society (EMBC), 2014 36th Annual International Conference of the IEEE,2014. [112]Sujatha, K.,Nageswara Rao, P.V.,Sruthi, K.J.,Arjuna Rao, A.. Design and development of android mobile based bus trackingsystem[P]. Networks & Soft Computing (ICNSC), 2014 FirstInternational Conference on,2014. [113]Weir, Alexander J.,Paterson, Craig A.,Tieges,Zoe,MacLullich, Alasdair M.,Parra-Rodriguez, Mario,Della Sala, Sergio,Logie, Robert H.. Development of Android apps for cognitive assessment of dementia and delirium[P]. Engineering in Medicine and Biology Society (EMBC), 2014 36th Annual International Conference of the IEEE,2014. [114]K, Jiju,P, Ramesh,P, Brijesh,B, Sreekumari. Development of Android based on-line monitoring and control system for Renewable Energy Sources[P]. Computer, Communications, and Control Technology (I4CT), 2014 International Conference on,2014. [115]Savola, Reijo M.,Kylanpaa, Markku. Security objectives, controls and metrics development for an Android smartphoneapplication[P]. Information Security for South Africa (ISSA),2014,2014. [116]Sekar, B.,Liu, J.B.. Location based mobile apps development on Android platform[P]. Industrial Electronics and Applications (ICIEA), 2014 IEEE 9th Conference on,2014. [117]Guobin Wu,Zheng Xie,Xin'an Wang. Development of a mind-controlled Android racing game using a brain computer interface (BCI)[P]. Information Science and Technology (ICIST), 2014 4th IEEE International Conference on,2014. [118]Dra?en Hi?ak,Matija Mikac. Development of a Simple Tool for Audio Analysis on Mobile Android Platform[J]. TechnicalJournal,2013,7(2). [119]Zoran Vrhovski,Tomislav Kurtanjek,Marko Mileti?. Development of the system for agricultural land measuring using the android operating system[J]. Technical Journal,2013,7(4). [120]Christopher Dong,Xing Liu. Development of AndroidApplication for Language Studies[J]. IERI Procedia,2013,4. 以上就是关于安卓开发英文参考文献的分享,希望对你有所帮助。
Depth from Defocus-文献阅读

Depth from Defocus:A Spatial Domain Approach(1) Title, authors, conf./journal, page no., year.Title Depth from Defocus:A Spatial Domain ApproachAuthors Murali Subbarao ,Gopal SunryaDA TE Junepage no. 272/294year 2011(2) Motivation (why the problem is important?)Motivation one: Passive techniques of ranging or determining distance of objects from a camera is an important problem in computer vision.Motivation two:STM is very fast in comparison with Depth-from-Focus methods which search for the lens position or focal length of best focus.(3)Problem (What is the exact problem they want to solve, input/output)How to determin distance of objects and rapidly autofocus of camera system only by two images taken with different camera parameters such as lens position,focal length,and aperture diameter.(4) Techniques (How they solve the problem, by what kind of techniques)To Calculate distance of object:First: capture two digital images with different camera parametersSecond:Smooth the two images partlyThird:Perform Laplacian operation on the smoothed imagesFourth:Calculate theσ2Fifth:Calculate distance of object(5)Experiments(How they conduct experiments, environments, results, conclusions)STM described above was implemented on a camera system named Stonybrook Passive Autofocusing and Ranging Camera System (SPARCS).Environments:SPARCS consists of a SONY XC-711 CCD camera and an Olympus 35-70 mm motorized lens.Images from the camera are captured by a frame grabber board (Quickcapture DT2953 of Data Translation).The frame grabber board resides in an IBM PS/2 (model 70)personal computer.The captured images are processed in the PS/2 computer.Different versions:1.only the lens position was changed in obtaining two images gl and g2,but the diameter of the lens aperture was not changed.Changing the lens position changes the parameters s and f .2.only the diameter of the lens aperture was changed but the other camera parameters s,f were unchanged in obtaining the two images.Results:1.Result from version one:(6) Thoughts (How can we do something new based on this paper)For different architectures, the IO requests is different, we can extend this idea into different architectures with different access patterns.2.Result from version two:Conclusions:a new DFD method named STM is useful for passive rangingand rapid autofocusing.(6) Thoughts (How can we do something new based on this paper)The ranging accuracy of this method can be improved somewhat by using a DFF method which searches for the best focused position in a small interval near the distance estimated by STM.This combination of DFD and DFF methods together result in a powerful new technique for ranging which is both fast and accurate.。
eucast纸片扩散法判读指南英文版

eucast纸片扩散法判读指南英文版Eucast Disk Diffusion Method Interpretation GuideIntroduction:The disk diffusion method is a commonly used technique for determining the susceptibility of bacterial pathogens to antimicrobial agents. The European Committee on Antimicrobial Susceptibility Testing (EUCAST) has established standardized protocols for performing the disk diffusion test, which includes guidelines for interpreting the results.Procedure:The first step in performing the disk diffusion test is to inoculate a standardized suspension of the test organism onto an agar plate. After allowing the inoculum to dry, paper disks impregnated with different concentrations of antimicrobial agents are placed on the agar surface. The plates are then incubated for a specified period of time, during which the antimicrobial agents diffuse into the agar and inhibit the growth of susceptible bacteria.Interpreting the Results:After incubation, the plates are examined for the presence of zones of inhibition around each disk. The size of the zone of inhibition is measured using a caliper or ruler, and the diameter is compared to interpretative criteria provided by EUCAST. The interpretative criteria are based on the zone diameter breakpoints established for each antimicrobial agent, which indicate whether the organism is susceptible, intermediate, or resistant to the drug.Interpretation Guidelines:When interpreting the results of the disk diffusion test, it is important to consider several factors. The size of the zone of inhibition, which reflects the susceptibility of the organism to the drug, is the primary factor to consider. In addition, the interpretative criteria provided by EUCAST should be followed closely to ensure accurate and consistent results. It is also important to note that the interpretative criteria may vary depending on the type of organism being tested and the antimicrobial agent being used.Conclusion:The EUCAST disk diffusion method interpretation guide provides a standardized approach to determining the susceptibility of bacterial pathogens to antimicrobial agents. Byfollowing the guidelines set forth by EUCAST, researchers and clinicians can obtain reliable and accurate results that can inform the selection of appropriate antibiotic therapy.。
一种单片机语音录入和播放系统设计英文文献3 - 副本【范本模板】

A single—chip voice input and playback systemApplication of SCM for Embedded System Experimental test of modern electronic technology is an important direction of development. To the system as development platform for voice processing technology can experiment, including voice recording and playback,voice compression coding and decoding,voice recognition and other content designed experiment. There are two general ways to design:one is the Microprocessor Design; the other is by means of specialized voice processing chips. SCM is often not achieve such a common complex process and algorithms, even if we manage to achieve a lot of peripheral devices also increases. Although specialized voice processing chips have more,but the specific function of voice processing chips relatively simple, other than in the application of speech is very difficult。
大豆抗倒伏相关性状全基因组关联分析

Journal of Northeast Agricultural University东北农业大学学报第52卷第3期52(3):1~122021年3月March 2021大豆抗倒伏相关性状全基因组关联分析李文滨,吴航,刘冀,张翔超,郭志文,郑立娜,赵雪,韩英鹏,滕卫丽(东北农业大学大豆研究所,大豆生物学教育部重点实验室,农业农村部东北大豆生物学与遗传育种重点实验室,哈尔滨150030)摘要:研究以150份大豆种质为试验材料开展2年3点试验,在收获期测定抗倒伏相关性状,并利用RTM-GWAS 方法作关联分析,共检测到99个显著关联SNP 位点,其中48个效应显著位点,解释0.28%~3.38%表型变异;89个与环境互作显著位点,解释0.53%~7.04%表型变异;其中,21个位点主效表型变异解释率高于1%;与6个倒伏相关性状显著关联SNP 位点中,与茎粗显著关联SNP 位点最多,与抗倒指数显著关联SNP 位点最少;获得22个有功能注释基因,根据基因表达量和基因功能注释,推测3个基因(Glyma .18G 149700、Glyma .04G 244100、Glyma .18G 011400)可作为与大豆抗倒伏相关候选基因。
关键词:大豆;倒伏性状;全基因组关联分析;候选基因挖掘中图分类号:S565.1文献标志码:A文章编号:1005-9369(2021)03-0001-12李文滨,吴航,刘冀,等.大豆抗倒伏相关性状全基因组关联分析[J].东北农业大学学报,2021,52(3):1-12.DOI :10.19720/ki.issn.1005-9369.2021.03.001.Li Wenbin,Wu Hang,Liu Ji,et al.Genome-wide association analysis of lodging-related traits in soybean[J].Journal of Northeast Agricultural University,2021,52(3):1-12.(in Chinese with English abstract)DOI :10.19720/ki.issn.1005-9369.2021.03.001.Genome-wide association analysis of lodging-related traits in soybean/LI Wenbin,WU Hang,LIU Ji,ZHANG Xiangchao,GUO Zhiwen,ZHENG Lina,ZHAO Xue,HAN Yingpeng,TENG Weili (Institute of Soybean Research,Key Laboratory of Soybean Biology in Chinese of Ministry Education,Key Laboratory of Soybean Biology and Breeding (Genetics)of Chinese Agriculture and Rural Ministry,Northeast Agricultural University,Harbin 150030,China)Abstract:In this study,150soybean germplasm were used as experimental materials for 2-yearand 3-point test,lodging-related traits were measured at harvest time,and the association analysis was conducted by RTM-GWAS method.There were 99significantly associated SNP sites detected,48loci with significant effect accounted for 0.28%-3.38%of phenotypic variation,89loci with significant interaction with environment explained 0.53%-7.04%of phenotypic variation,21of them explained more than 1%of phenotypic variation.Among SNP loci significantly associated with six lodging related traits,the SNP loci associated with stem diameter were the most,and those associated with lodging index were the least.A total of 22genes with functional annotation were obtained.According to gene expression and gene function annotation,three genes (Glyma .18G 149700,Glyma .04G 244100,and Glyma .18G 011400)could be considrerd as candidate genes related to soybean lodging resistance.Key words:soybean;lodging trait;genome-wide association analysis;mining for candidate gene基金项目:国家十三五重点研发计划项目(2017YFD0101306-05);国家自然科学基金项目(31471517);黑龙江省“百千万”工程科技重大专项(2019ZX16B01-1);现代农业产业技术体系专项建资金项目(CARS-04-PS04)作者简介:李文滨(1958-),男,教授,博士,博士生导师,研究方向为大豆遗传育种与生物技术。
dtm主题模型文献综述

dtm主题模型文献综述DTM(Dynamic Topic Model)是一种用于对文本数据进行主题建模的方法,它能够挖掘文本中的隐藏主题,并在时间上对主题进行建模。
在本文中,我们将对DTM主题模型的研究文献进行综述,并探讨它的应用和存在的问题。
最早引入DTM的文献是Blei等人于2024年提出的动态语言模型(DLM),DLM是一种基于隐马尔可夫模型(HMM)的主题模型,用于对新闻报道的文本进行主题建模。
DLM包含了两个层次的隐含状态,第一个层次用于表示文本数据的主题,第二个层次用于表示主题的动态变化。
但是,DLM在建模时忽略了文本数据的时间信息,因此,后续的研究对DLM进行了改进。
在2024年,Blei等人提出了动态主题模型(DTM),它是一种非参数贝叶斯方法,能够根据文本数据的时间顺序对主题进行建模。
DTM使用了隐狄利克雷分配(LDA)来对文档进行建模,同时引入了一个时间层次的隐马尔可夫模型来对主题进行建模。
具体而言,DTM将文本数据划分为多个时间片段,在每个时间片段内,文档依然服从LDA模型,但主题的分布会随时间而变化。
DTM通过将相邻时间片段之间的主题分布进行转换,从而实现了主题在时间上的动态变化。
DTM的一大应用是对新闻数据进行主题建模。
例如,Xu等人(2024)使用DTM对中文新闻数据进行主题建模,并通过观察主题的演变来检测社会事件的发展。
他们的实验结果表明,DTM能够准确地捕捉到不同主题在时间上的变化,并提供了对新闻事件的更细致理解。
此外,DTM还被广泛应用于社交媒体分析领域。
例如,Gerrish和Blei(2024)使用DTM对推特数据进行主题建模,并探讨了不同主题的传播情况。
他们的研究发现,一些主题在时间上的变化与真实世界的事件有关,并能够用来预测用户的行为。
尽管DTM在文本数据的主题建模中取得了很大的成功,但它也存在一些问题。
首先,DTM假设文档是在类似的语境下生成的,这在一些应用场景中可能不成立。
Class 2-multi-omic data_integration
Background - 20
Mappability:
➢ For each base-pair position in the genome, whether a sequencing read starting from this position can be uniquely mapped to this location.
• Majority of its analyses, such as enrichment site finding and target definition, can be easily adopted for analyzing DNase/FAIRE-Seq data sets.
• Usually it’s the start point of gene regulation studies.
Reads aligned to different strands:
➢ In ChIP-Seq data of TFs, reads aligned to different strands usually form two distinct peaks around the true binding sites.
➢ This information can be used to both estimate the average size of DNAfragments (like MACS) and also help pick out unreliable peaks (like QUEST).
goertzel 算法的英文课件

1
4 7 *
2
5 8 0
3
6 9 #
A
B C D
Output
770
1336
Freq (Hz)
Chapter 17, Slide 5
Example: Button 5 results in a 770Hz and a 1336Hz tone being generated simultaneously.
|Yk(N) |2 = Q2(N) + Q2(N-1) - coeff*Q(N)*Q(N-1) Where: coeff = 2*cos(2**k/N)
Chapter 17, Slide 13
Dr. Naim Dahnoun, Bristol University, (c) Texas Instruments 2004
Chapter 17, Slide 11 Dr. Naim Dahnoun, Bristol University, (c) Texas Instruments 2004
Goertzel Algorithm Implementation
Feedback
+
Feedforward
+
x(n )
Qn
delay
Feedback
+
Feedforward
+
x(n )
Qn
delay
y (n )
z 1
prod1
+ coeff
Qn 1
delay1
z 1
-1
Qn 2
delay2
Since we are only interested in detecting the presence of a tone and not the phase we can detect the square of the magnitude:
Synopsys RSoft
DATASHEET/optical-solutions Overview RSoft™ OptSim™ Circuit is an extension of Synopsys’ award-winning fiber optic systems modeling tool, OptSim. It delivers a single framework, engine and sets of models to study systems ranging from long-haul optical communication systems to sub-micron photonic circuits. This enables you to evaluate system-level performance in OptSim of a photonic integrated circuit (PIC) that is designed in OptSim Circuit. It is an ideal platform to study optical systems and photonic circuits that operate with coupling and feedback of different optical and electrical signal paths.OptSim Circuit comes with a rich library of PIC elements including, but not limited to, bidirectional waveguides, bidirectional couplers and connectors, modulators, optical sources (lasers and VCSEL), and photodiodes (PIN and APD). Measurement and plotting tools are supplied, such as optical and electrical scopes, signal, spectrum and eye diagram analyzers, Q-factor and BER estimators, power meters, etc. OptSim Circuit’s intuitive representation of repeating and hierarchical elements provides brevity and efficiency to thelayouts. For example, you can create custom components and organize andreuse them in the PIC layout.Figure 1: A ring resonator PIC, transmitted and reflected outputsFeatures at a Glance• Extends OptSim’s system modelingcapabilities to include PICs• Models bidirectional propagation forboth optical and electrical signals• Models forward and backwardpropagating reflections and resonance• Models single- and multi-stagebidirectional PICs• Models multipath interference (MPI)from network and PIC elements• Includes library of PIC elements such asbidirectional waveguides, bidirectionalcouplers and connectors, light sources,modulators and photodiodes• Supports reusable user-definedcomponents and compound components• Provides a number of options forexporting data and for co-simulationwith external tools• Provides an intuitive graphicaluser interface• Comes with powerful options for datavisualization, plotting and managementof project resourcesRSoft OptSim CircuitModel Single- and Multi-stage Bidirectional Photonic Integrated Circuits (PICs)Figure 2: An optical notch filter PIC, transmitted and reflected outputsOptSim Circuit takes into account bidirectional propagation of both optical and electrical signals. This makes it possible to model complex signal interactions such as reflections and resonance in PICs that otherwise are impossible to model in conventional systems modeling tools.OptSim Circuit’s extensive documentation includes an installation guide, user guide, models reference guide and application notes. The product also includes a number of pre-supplied PIC layouts such as single- and multi-stage micro-ring resonators, a micro-ring modulator, a gratings-based optical notch filter, and more.If you would like to try OptSim Circuit, please contact Synopsys’s Optical Solutions Group at (626) 795-9101,visit /optical-solutions/rsoft, or send an email to ************************.©2018 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks isavailable at /copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners.04/13/18.CS12612_RSoft OptSim_DS.indd.。
DISCONTINUOUS TRANSMISSION (DTX) FRAME DETECTION I

专利名称:DISCONTINUOUS TRANSMISSION (DTX) FRAME DETECTION IN WIRELESSCOMMUNICATION SYSTEMS发明人:CHEN, Qingxin,PATEL, Shimman申请号:EP03796971.4申请日:20031210公开号:EP1570699B1公开日:20070822专利内容由知识产权出版社提供摘要:Techniques to detect for DTX frames in a 'primary' transmission that may be sent in a non-continuous manner using a 'secondary' transmission that is sent during periods of no transmission for the primary transmission. The primary and secondary transmissions may be the ones sent on the F-DCCH and Forward Power Control Subchannel, respectively, in an IS-2000 system. In one method, a determination is first made whether or not a frame received for the primary transmission in a particular frame interval is a good frame (e.g., based on CRC). If the received frame is not a good frame, then a determination is next made whether the received frame is a DTX frame or an erased frame based on a number of metrics determined for the primary and secondary transmissions. The metrics may include symbol error rate of the received frame, secondary transmission (e.g., PC bit) energy, and received frame energy.申请人:QUALCOMM INC地址:US国籍:US代理机构:Emde, Eric更多信息请下载全文后查看。
Image decoding apparatus, image decoding method, a

专利名称:Image decoding apparatus, image decodingmethod, and image decoding program发明人:竹原 英樹申请号:JP2019171782申请日:20190920公开号:JP2020099037A公开日:20200625专利内容由知识产权出版社提供专利附图:摘要:PROBLEM TO BE SOLVED: To provide an inter prediction mode with higher efficiency by correcting a motion vector in a merge mode. An inter prediction unit of an image decoding device generates a merge candidate list, selects a merge candidate from the merge candidate list as a selected merge candidate, decodes a code string from an encoded stream to derive a correction vector, and selects the correction vector. Thecorrection vector of the first prediction of the merge candidate is added without scaling,and the correction vector is subtracted from the motion vector of the second prediction of the selected merge candidate without scaling to derive a correction merge candidate.[Selection diagram] Fig. 3申请人:株式会社JVCケンウッド地址:神奈川県横浜市神奈川区守屋町3丁目12番地国籍:JP更多信息请下载全文后查看。
chatgpt英语作文素材200字

chatgpt英语作文素材200字The Advent of Artificial Intelligence: A Paradigm Shift in Human Endeavors.The dawn of artificial intelligence (AI) has heralded an unprecedented era of technological advancement, revolutionizing myriad aspects of human life and industry. From its inception, AI has exhibited remarkablecapabilities in processing vast amounts of data, recognizing patterns, and making predictions with unparalleled precision. This transformative technology has permeated various domains, from healthcare to finance, manufacturing, and customer service, empowering businesses and individuals alike with enhanced efficiency, accuracy, and innovation.In the healthcare sector, AI-powered systems have demonstrated immense potential in revolutionizing patient care. AI-driven algorithms can analyze vast medical datasets, identifying patterns and anomalies that may bemissed by the human eye. This enables early detection of diseases, leading to timely interventions and improved patient outcomes. Furthermore, AI-assisted surgery systems provide surgeons with real-time guidance, enhancing precision and reducing the risk of complications.The financial industry has also witnessed the transformative effects of AI. AI-powered algorithms can swiftly analyze market data, identify trends, and make investment recommendations with remarkable accuracy. This has empowered financial institutions with enhanced risk management capabilities, enabling them to make informed decisions and mitigate potential losses. Additionally, AI-driven chatbots provide personalized financial advice, assisting customers with budgeting, savings, and investment strategies.In the manufacturing sector, AI has revolutionized production processes, optimizing efficiency and minimizing waste. AI-driven predictive maintenance systems can monitor equipment performance, identifying potential issues before they escalate into costly breakdowns. This proactiveapproach ensures uninterrupted operations, maximizes productivity, and reduces downtime. Moreover, AI-assisted robotics can perform complex tasks with precision and speed, enhancing production capacity and reducing manufacturing costs.AI has also found widespread application in the customer service industry, enhancing customer satisfaction and streamlining operations. AI-powered chatbots can engage with customers 24/7, providing instant support andresolving inquiries efficiently. These systems can process natural language, understanding customer requests and responding with appropriate solutions. Additionally, AI-driven sentiment analysis can monitor customer feedback, identifying potential issues and enabling proactive measures to address customer concerns.The advent of AI has not been without its challenges. Concerns regarding job displacement and the ethical implications of AI systems have sparked debates among policymakers and the general public. However, it isessential to recognize that AI is a transformative toolthat can empower humans, augmenting their capabilities and unlocking unprecedented possibilities. By embracing AI and fostering human-machine collaboration, we can harness its transformative potential to drive progress, improve lives, and shape a brighter future for humanity.。
Digital Detox Weekend

Digital Detox WeekendAs we navigate through the fast-paced digital world, it's becomingincreasingly important to take a step back and disconnect from our devices. Adigital detox weekend offers the perfect opportunity to reset and recharge,allowing us to reconnect with ourselves and the world around us. One of the main benefits of a digital detox weekend is the opportunity to reduce stress andimprove mental well-being. Constantly being plugged in can lead to feelings of overwhelm and burnout. By taking a break from screens and notifications, we cangive our minds a much-needed rest and create space for relaxation and reflection. This can help us feel more present and mindful in our daily lives, leading to a greater sense of peace and contentment. In addition to the mental benefits, a digital detox weekend can also have a positive impact on our physical health. Spending hours in front of screens can lead to issues such as eye strain, headaches, and poor posture. By unplugging for a weekend, we can give our bodies a break from these harmful effects and engage in activities that promote physicalwell-being, such as spending time outdoors, exercising, and getting quality sleep. Furthermore, a digital detox weekend can strengthen relationships and foster connection with others. In today's digital age, it's easy to get caught up invirtual interactions and neglect the importance of face-to-face communication. By disconnecting from our devices, we can focus on building meaningful connectionswith friends and family, engaging in conversations, and creating lasting memories together. This can help deepen our relationships and create a sense of communityand belonging. Another important aspect of a digital detox weekend is the opportunity to reconnect with nature. Spending time outdoors has been shown tohave numerous benefits for both physical and mental health, such as reducing stress, improving mood, and boosting creativity. By immersing ourselves in the natural world and engaging in activities like hiking, camping, or simply taking a walk in the park, we can experience a sense of awe and wonder, and gain a newfound appreciation for the beauty of the world around us. Overall, a digital detox weekend is a valuable opportunity to prioritize self-care, recharge our batteries, and cultivate a deeper connection with ourselves and the world around us. Bytaking a break from our devices and immersing ourselves in the present moment, wecan experience a sense of peace, clarity, and rejuvenation that can have lasting effects on our overall well-being. So why not unplug for a weekend and see the positive impact it can have on your life?。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
DTMF Decoding with a PIC16xxxAuthor: David HedleyMicrochip Technology Inc.Additional Input:Chris MacCallumDes HowlettMicrochip Europe INTRODUCTIONThis application note describes how to decode standard DTMF tones using the minimum number of external discrete components and a PIC. The two examples use a PIC which has an 8 bit timer and either a comparator or an ADC, although it can be modified for use on a PIC which has only digital I/O. The Appendices have example code for the 16C662 (with comparator) and 16F877 (using the ADC).As the majority of the Digital Signal Processing is done in software, little is required in the way of external signal conditioning. Software techniques are used to model the individual elements of a DTMF Decoder IC.∙Data collection mechanism.∙ A time domain to frequency domain conversion (Fourier Transform)∙ A bank of 8 Narrow Bandpass Filters∙Decision Making∙OutputTHEORYTable 1 : Common DTMF Frequencies.The digits 0 through 9 and the characters * and # are used in public telecommunications services. The characters A through D are reserved for use in non-public telecommunications networks. Although the character D, is sometimes used as an identifier in Caller Identification signalling on the public network.For both working examples, the input signals to the pin of the PIC were 0v to 5v positive waves. Some circuitry may be needed to ensure the correct levels are sent to the device. The aim of this Application is to decode the signals without the need for external filtering equipment, or a DTMF decoder IC, and allow enough remaining processor memory and overhead to incorporate other features. i.e. Call Routing, Identification, FSK Demodulation etc.Within the software, the data is collected a sample at a time and acted upon immediately. The sample rate according to Nyquist should be at least twice the highest frequency in the range. In the case of standard DTMF tones, the highest frequency is 1633Hz, the sample frequency should therefore be greater than 3.3KHz (Approx Rate: 300us). Using Timer0 to create the sample trigger via an Interrupt, means we can use the TMR0 Prescaler to set an appropriate sample rate (256uS / 4KHz is easy to achieve). The input is scanned, from the input mechanism (comparator/ ADC /digital I/O) and is stored in a RAM bit for comparison.The comparison is widely known as a “modified Goertzel algorithm”; a number of inputs of 1 bit resolution are provided (the incoming signal), which must be converted from the time domain into a component of frequency. This operation is essentially a 1 bit Discrete Fourier Transform (DFT). In a PIC, this involves building a frequency response table in RAM, as the samples are taken. Each incoming bit is compared against the expected result for each of the 8 frequencies.The expected values are held in program memory in RETLW tables. These tables were produced from a spreadsheet using theoretical SINE and COSINE waves at the given DTMF frequencies. (File Attached *.xls). Each “match” increments an accumulator variable for that particular frequency. A “non-match” will decrement the same counter.Example 1:Incoming SignalExpected Signal+1+1+1+1+1+1+1+1+1+1+1+1+1+1+1+1 = 16Example 2:Incoming SignalExpected Signal1+1+1-1-1-1-1-1-1+1+1+1+1+1-1-1-1-1-1 = -3We can see that Example 1 yields a large sum, compared to Example 2 which is off frequency. Given more samples, Example 2 will continue to move around zero.We must compare each incoming bit with the expected SINE and COSINE bits for each of the 8 frequencies, a total of 16 comparisons for each incoming bit. The reason for comparing the incoming bit with the SINE and COSINE of each frequency is that even if there is an exact frequency match, the phase of the incoming signal affects the magnitude of the sum of products. In the extreme case where the signal is a match, there arepositions of phase that would cause the SINE accumulator to sum to zero. However, if we check against the COSINE as well, this will give a large magnitude of matches at 90 degrees and the sum of SINE and COSINE results will still prove the match.Table 2: Comparison and Accumulation.The comparison performed in software can be shown manually with the simplified table above, which demonstrates the systems immunity to phase differences. There wouldn’t be enough samples in the system for this to work, but it shows that the result will be the same, regardless of the phase of the incoming signal.To get the SINE Total for Sig1, compare A,SINE (0) against A,Sig1 (1). There was a NO MATCH, so the running total is decremented (now –1) B,SINE (1) against B,Sig1 (1) = MATCH so increment the running total (now 0). C,SINE (1) against C,Sig1 (0) = NO MATCH so decrement the running total (now -1). D,SINE (0) against D,Sig1 (0) = MATCH so increment the running total (now 0). Do the same for the COSINE, then cast the variables to be unsigned eg. –x = +x.Summing the results from the SINE and COSINE comparisons for each of the eight frequencies will begin to build a frequency response table in RAM. This has eliminated the potential phase problem. Over time and given enough samples, one winning frequency will emerge from each of the low-band and high-band frequency ranges. If there are not two clear winners, no output will be given.Table 3: Frequency Response Table in RAM.The process of decision making is straightforward and requires the detection of the winning frequencies, and confirmation that the winners are above a set threshold.In the case above, button “*” was pressed, and the output from the PIC can be made to reflect this via LED’s or a serial communication message.The example code for the PIC16c662 shows the output on PORTB, each bit being one of the eight frequencies. A pair will be lit at the end of the conversion if a DTMF tone was detected. The example code for the PIC16F877 sends the ASCII character representationof the dialled button down an RS232 link to a terminating display (in this case HyperTerminal on the PC works well - 9600,8,N,1), using the PIC’s USART at9600baud.IMPLEMENTATIONDuring initialisation, (INIT), user RAM is cleared using indirect addressing. The File Select Register (FSR) is incremented and the pointer contents (INDF) cleared. The loop runs to the end of the specified RAM area. In this case the end is at 0x4F. It’s a good way to ensure your variables are clear at the beginning of your conversion, and only uses 8 lines of code.The input peripheral (comparator or ADC) is set up, as are the timers which need to be used. As the sample time in this application is 256us, the OPTION register is used to ensure an accurate scaling for Timer 0, and the interrupt for the timer peripheral is enabled.The MAIN routine is a simple loop. This is done so that other functions can be performed if the desired application is more complex than the simple decoder shown here. Add your code here, but be aware that during the time spent in this area, the PIC is waiting for Timer interrupts to occur. The ISR saves and restores the W and STATUS registers, but may need to include other registers if more complex code is added. Once the interrupt routine has been executed and a sample taken, a user flag is detected on returning to theMAIN routine. This is the cue to perform the Goertzel comparison. The device runs with a 16MHz oscillator mainly because the comparison needs to be completed before the next interrupt.The routine labelled GOERTZEL has two bytes and one bit passed to it. The two bytes are the expected SINE and COSINE values for that sample, the single bit is the sampled signal level, and is held in a variable called BYTE, bit 0. This level is tested against the other 16 in turn, using rotations, and the 16 variables dedicated to the accumulators are incremented or decremented accordingly. These accumulators can be visualised as the frequency response table. Once all the samples have been acted upon, the SINE accumulator for each frequency is summed unsigned with its COSINE counterpart.This is performed in a routine labelled ACCUM_LOW. Again the FSR is used extensively to address the RAM locations and keep the code to a minimum. Given that the sum totals, now held in the COSINE variable for each frequency can be a positive or a negative, they need to be made positive so that they can be easily compared during the output stage. As there are never more than 128 samples taken in this application, the most significant bit can be used to determine the sign, and if necessary, “flipped” positive around zero.The output uses the FSR again to decide if there was a pair of winning frequencies, and if the winners were above a certain threshold level. The threshold level for a certain match using the full 128 byte tables was set at 0x40 (Decimal 64). This means that the sum ofthe SINE and COSINE comparison must be above a specific level for the match to be proven. In theory, the maximum matched sum (in the case of square waves) would be Decimal 128, so a threshold of half the maximum works well. Equally, if the half tables are used to reduce the conversion time, the threshold should be altered accordingly. It should be noted that this makes the system more susceptible to errors, and the application has not been fully tested in this way, at this time.In order to use the “half-tables” approach, the end point for the counter needs to be changed in the Interrupt Service Routine (ISR). The variable TABLECOUNTER is used to determine the offset used when the table is called. This counter is checked once the table values have been returned, and if the specified number of passes have been completed, a flag is raised to tell the device to finish the process and output the results. Changing the tested value from Decimal 128 to 64, will have the desired effect.TIMING AND STATISTICSNote: All timings taken using ICE2000 emulator system at 16MHz.Using FULL TABLES (128 samples)Theoretical minimum (128 samples * 256uS) - 32.51mSPIC16F877 example:Total conversion time (including output stage) - 32.75mSPIC16C662 example:Total conversion time (including output stage) - 32.74mSUsing HALF TABLES (64 samples)Theoretical minimum (64 samples * 256uS) - 16.384mSPIC16F877 example:Total conversion time (including output stage) - 16.6mSPIC16C662 example:Total conversion time (including output stage) - 16.6mSThe files included are assembled with MPASM and the tables linked in using MPLINK.To set up the project above in MPLAB, open a new project and enter “node properties” for the target file. Under “Language Tool“, select MPLINK and then click, “OK”. This takes you back to the screen above where you can add the nodes listed.Appendix A662 Example Code ;;; DTMF Decoder Software; Ver: LINKED HALF SIZED TABLES V1.1; David Hedley CAE; Microchip Europe; November 1999;; For Example Only;;;;INCLUDE "P16C662.INC"ERRORLEVEL -302UDATASAMPLEBIT EQU 0X40W_TEMP EQU 0X41STATUS_TEMP EQU 0X42TABLECOUNTER EQU 0X43TEMP EQU 0X44LOWTEMPLATE EQU 0X45HIGHTEMPLATE EQU 0X46BYTE EQU 0X47BITVALUE EQU 0X48RESULT EQU H'28'FLAGS EQU H'29'A697SIN EQU H'30'A697COS EQU H'31'A770SIN EQU H'32'A770COS EQU H'33'A852SIN EQU H'34'A852COS EQU H'35'A941SIN EQU H'36'A941COS EQU H'37'A1209SIN EQU 0X38A1209COS EQU 0X39A1336SIN EQU 0X3AA1336COS EQU 0X3BA1447SIN EQU 0X3CA1447COS EQU 0X3DA1633SIN EQU 0X3EA1633COS EQU 0X3FEXTERN HIGHBANDEXTERN LOWBAND#DEFINE DONE FLAGS,0#DEFINE GOT_ONE FLAGS,1#DEFINE HIGHONES FLAGS,2#DEFINE ONELIT FLAGS,3begin code 0x00goto STARTinterrupt_vector code 0x04goto ISRinterrupt code 0x05ISR;****************************;; CONTEXT SAVE;;****************************C_SAVE MOVWF W_TEMPSWAPF STATUS,WBCF STATUS,5 ;ENSURE BANK0 SAVEMOVWF STATUS_TEMPBTFSS INTCON,T0IFGOTO C_RESTORE;LOOK AT THE COMPARATORBCF INTCON,T0IF;*****************************;;;;*****************************BTFSC CMCON,C1OUT ;get compar valueGOTO PIN_HIGHGOTO PIN_LOWPIN_HIGHBSF STATUS,CRLF BYTE,F ;BIT IN LSB OF BYTEGOTO CONTINUEPIN_LOWBCF STATUS,CRLF BYTE,F ;BIT IN LSB OF BYTE CONTINUE;;*****************************;MOVLW LOW LOWBANDADDWF TABLECOUNTER,fMOVLW HIGH LOWBANDBTFSC STATUS,CADDLW 1MOVWF PCLATHMOVF TABLECOUNTER,WCALL LOWBANDMOVWF LOWTEMPLATE;*****************************;; DO SOME CHECKS;;*****************************MOVLW LOW HIGHBANDADDWF TABLECOUNTER,fMOVLW HIGH HIGHBANDBTFSC STATUS,CADDLW 1MOVWF PCLATHMOVF TABLECOUNTER,WCALL HIGHBANDCLRF PCLATHMOVWF HIGHTEMPLATEMOVF TABLECOUNTER,WXORLW D'64'BTFSC STATUS,ZGOTO FINITBSF GOT_ONEINCF TABLECOUNTER,FGOTO C_RESTOREFINITBSF DONEC_RESTOREBCF STATUS,5 ;ENSURE BANK0 RESTORESWAPF STATUS_TEMP,WMOVWF STATUSSWAPF W_TEMP,FSWAPF W_TEMP,WRETFIEcode 0x100INITMOVLW 0X1FMOVWF FSRRAMCLEANINCF FSR,fCLRF INDFMOVF FSR,WXORLW 0X4FBTFSS STATUS,ZGOTO RAMCLEANMOVLW 1MOVWF TABLECOUNTERMOVLW B'11100000'MOVWF INTCONMOVLW 0X02MOVWF CMCON ;comparator setupBANKSEL TRISAMOVLW B'10100010'MOVWF VRCONCLRF TRISBCLRF TRISABSF TRISA,0MOVLW B'11000001' ;256uS SAMPLE TIMEMOVWF OPTION_REG ;START TMR0BANKSEL PORTBRETURNSTARTCLRF PORTBCLRF TMR0STARTPLUSCALL INITNOPMAINMOVF TMR0,WBTFSC DONEGOTO DUNROAMINBTFSC GOT_ONECALL GOERTZELGOTO MAINDUNROAMINBANKSEL OPTION_REGBSF OPTION_REG,5 ;STOP THE CLOCKBANKSEL PORTBCALL ACCUM_LOWCALL WINNERBCF ONELITGOTO STARTPLUSGOERTZELBCF GOT_ONE;*******************************;; LOWTEMPLATE AND HIGHTEMPLATE; CONTAIN THE EXPECTED VALUES; FOR THE INCOMING BIT;;*******************************MOVLW H'30'MOVWF FSR ;ACCUMULATOR ADDRMOVLW 8MOVWF SAMPLEBITCOMPAREBITBTFSS HIGHONESGOTO LABELLOWGOTO LABELHIGH ;BRANCH HERE LABELHIGHRLF HIGHTEMPLATE,FGOTO CARRYONLABELLOWRLF LOWTEMPLATE,FCARRYONBTFSC STATUS,CGOTO WAS1GOTO WAS0WAS1MOVLW 1GOTO CONTWAS0MOVLW 0GOTO CONTCONTMOVWF BITVALUEBTFSC BYTE,0GOTO SAMPLEWAS1GOTO SAMPLEWAS0SAMPLEWAS1MOVLW 1GOTO CONTISAMPLEWAS0MOVLW 0GOTO CONTICONTIXORWF BITVALUE,WBTFSC STATUS,ZGOTO MATCHGOTO NOMATCHNOMATCHDECF INDF,FGOTO CONTINMATCHINCF INDF,FGOTO CONTINCONTIN; move the indf to the beginning of accumulator ram; test the bit for a match and increment thru fsr;; do it 8 times for low accum band;;; reset the indf and do the compare again for the upper band. ;INCF FSR,FDECFSZ SAMPLEBIT,FGOTO COMPAREBIT ;FINISH THE BYTEBTFSC HIGHONESGOTO BOTHDONEBSF HIGHONESMOVLW 8MOVWF SAMPLEBITGOTO COMPAREBIT ;NOW GO DO THE HIGH BAND BYTE BOTHDONEBCF HIGHONES ;DO LOW NEXT TIMECLRF BYTE ;CLEAR IT OUT FOR NEXT PASSRETURNWINNERMOVLW H'30'MOVWF FSRMORERESULTSMOVF INDF,WCLRF INDFINCF FSR,FADDWF INDF,FMOVF FSR,WINCF FSR,FXORLW H'3F'BTFSS STATUS,ZGOTO MORERESULTSMOVLW 0X31 ;FIRST RESULT IS IN 0X31 THEN 0X33...MOVWF FSROUTPUTRESULTMOVF INDF,WSUBLW 0X20 ;THRESHOLDRRF RESULT,fINCF FSR,FINCF FSR,FMOVF FSR,WXORLW 0X41BTFSS STATUS,ZGOTO OUTPUTRESULTCOMF RESULT,fMOVF RESULT,WMOVWF PORTBRETURNACCUM_LOWMOVLW H'30'MOVWF FSRTESTFORNEGBTFSC INDF,7GOTO NEGGOTO NEXTNEG; SUBTRACT aX FROM 0MOVF INDF,WSUBLW 0MOVWF INDFNEXTINCF FSR,FMOVF FSR,WXORLW H'40' BTFSS STATUS,Z GOTO TESTFORNEG RETURNEND662 Map InformationMPLINK v2.00.00, LinkerLinker Map File - Created Mon Feb 14 11:35:28 2000Section InfoSection Type Address Location Size(Bytes) --------- --------- --------- --------- --------- begin code 0x000000 program 0x000002 interrupt_vector code 0x000004 program 0x000002 interrupt code 0x000005 program 0x000060 .code code 0x000100 program 0x0000fe .cinit romdata 0x00017f program 0x000004 sect2 code 0x000200 program 0x000084 sect3 code 0x000400 program 0x000084 .udata udata 0x000020 data 0x000000 Program Memory UsageStart End--------- ---------0x000000 0x0000000x000004 0x0000340x000100 0x0001800x000200 0x0002410x000400 0x000441311 out of 4101 program addresses used, program memory utilization is 7%877 Example Code ;;; DTMF DECODER SOFTWARE; VER: 2.01; FOR 877; WORKY......; DAVID HEDLEY CAE; MICROCHIP EUROPE; NOVEMBER 1999;; FOR EXAMPLE ONLY;;;;INCLUDE "P16F877.INC"ERRORLEVEL -302UDATA;****************************;;User Variables in GPR;;****************************SAMPLEBIT EQU 0X40W_TEMP EQU 0X41STATUS_TEMP EQU 0X42TABLECOUNTER EQU 0X43TEMP EQU 0X44LOWTEMPLATE EQU 0X45HIGHTEMPLATE EQU 0X46BYTE EQU 0X47BITVALUE EQU 0X48COUNT EQU H'27'RESULT EQU H'28'FLAGS EQU H'29'A697SIN EQU H'30'A697COS EQU H'31'A770SIN EQU H'32'A770COS EQU H'33'A852SIN EQU H'34'A852COS EQU H'35'A941SIN EQU H'36'A941COS EQU H'37'A1209SIN EQU 0X38A1209COS EQU 0X39A1336SIN EQU 0X3AA1336COS EQU 0X3BA1447SIN EQU 0X3CA1447COS EQU 0X3DA1633SIN EQU 0X3EA1633COS EQU 0X3FEXTERN HIGHBANDEXTERN LOWBAND#DEFINE DONE FLAGS,0#DEFINE GOT_ONE FLAGS,1#DEFINE HIGHONES FLAGS,2#DEFINE ONELIT FLAGS,3BEGIN CODE 0X00nopGOTO STARTINTERRUPT_VECTOR CODE 0X04GOTO ISRINTERRUPT CODE 0X05ISR;****************************;; CONTEXT SAVE;;****************************C_SAVE MOVWF W_TEMPSWAPF STATUS,WBCF STATUS,5 ;ENSURE BANK0 SAVEMOVWF STATUS_TEMPBTFSS INTCON,T0IF ;Exit ISR if it wasn't a TMR0 Overflow GOTO C_RESTOREBCF INTCON,T0IFBCF INTCON,INTF;*****************************;TEST LEVEL of ADCMOVF ADRESL,WXORLW 0BTFSS STATUS,ZGOTO PIN_HIGHGOTO PIN_LOWPIN_HIGHBSF STATUS,CRLF BYTE,F ;BIT IN LSB OF BYTEGOTO CONTINUEPIN_LOWBCF STATUS,CRLF BYTE,F ;BIT IN LSB OF BYTECONTINUE;*****************************;;Get the expected Lowband Bits;;*****************************MOVLW LOW LOWBANDADDWF TABLECOUNTER,fMOVLW HIGH LOWBANDBTFSC STATUS,CADDLW 1MOVWF PCLATHMOVF TABLECOUNTER,WCALL LOWBANDMOVWF LOWTEMPLATE;*****************************;;Get the expected Highband Bits;;*****************************MOVLW LOW HIGHBANDADDWF TABLECOUNTER,fMOVLW HIGH HIGHBANDBTFSC STATUS,CADDLW 1MOVWF PCLATHMOVF TABLECOUNTER,WCALL HIGHBANDCLRF PCLATHMOVWF HIGHTEMPLATEMOVF TABLECOUNTER,WXORLW D'64' ;This is the number of samples to test against (max 7f)BTFSC STATUS,ZGOTO FINITBSF GOT_ONEINCF TABLECOUNTER,FGOTO C_RESTOREFINITBSF DONE;********************************;; Context Restore;;********************************C_RESTOREBCF STATUS,5 ;ENSURE BANK0 RESTORESWAPF STATUS_TEMP,WMOVWF STATUSSWAPF W_TEMP,FSWAPF W_TEMP,WRETFIECODE 0X100INITMOVLW 0X20MOVWF FSRRAMCLEANINCF FSR,fCLRF INDFMOVF FSR,WXORLW 0X6FBTFSS STATUS,ZGOTO RAMCLEANMOVLW 1MOVWF TABLECOUNTERMOVLW B'11100000'MOVWF INTCONBANKSEL TRISAMOVLW B'10000100'MOVWF ADCON1 ;AN RA0 IO FOR 77CLRF TRISBCLRF TRISABSF TRISA,0MOVLW B'11000001' ;256US SAMPLE TIMEMOVWF OPTION_REG ;START TMR0BANKSEL PORTBRETURNSTARTCLRF PORTBSTARTPLUSCALL INITNOPMAINGETADCMOVLW B'11000001'MOVWF ADCON0BSF ADCON0,GOWAITHEREBTFSC ADCON0,GOGOTO WAITHEREBTFSC DONEGOTO DUNROAMINBTFSC GOT_ONECALL GOERTZELGOTO MAINDUNROAMINBANKSEL OPTION_REGBSF OPTION_REG,5 ;STOP THE CLOCKBANKSEL PORTBCALL ACCUM_LOWCALL WINNERGOTO STARTPLUSGOERTZELBCF GOT_ONE;*******************************;; LOWTEMPLATE AND HIGHTEMPLATE; CONTAIN THE EXPECTED VALUES; FOR THE INCOMING BIT;;*******************************MOVLW H'30'MOVWF FSR ;ACCUMULATOR ADDRMOVLW 8MOVWF SAMPLEBITCOMPAREBITBTFSS HIGHONESGOTO LABELLOWGOTO LABELHIGH ;BRANCH HERE LABELHIGHRLF HIGHTEMPLATE,FGOTO CARRYONLABELLOWRLF LOWTEMPLATE,FCARRYONBTFSC STATUS,CGOTO WAS1GOTO WAS0WAS1MOVLW 1GOTO CONTWAS0MOVLW 0GOTO CONTCONTMOVWF BITVALUEBTFSC BYTE,0GOTO SAMPLEWAS1GOTO SAMPLEWAS0SAMPLEWAS1MOVLW 1GOTO CONTISAMPLEWAS0MOVLW 0GOTO CONTICONTIXORWF BITVALUE,WBTFSC STATUS,ZGOTO MATCHGOTO NOMATCHNOMATCHDECF INDF,FGOTO CONTINMATCHINCF INDF,FGOTO CONTINCONTIN; MOVE THE INDF TO THE BEGINNING OF ACCUMULATOR RAM; TEST THE BIT FOR A MATCH AND INCREMENT THRU FSR;; DO IT 8 TIMES FOR LOW ACCUM BAND;;; RESET THE INDF AND DO THE COMPARE AGAIN FOR THE UPPER BAND. ;INCF FSR,FDECFSZ SAMPLEBIT,FGOTO COMPAREBIT ;FINISH THE BYTEBTFSC HIGHONESGOTO BOTHDONEBSF HIGHONESMOVLW 8MOVWF SAMPLEBITGOTO COMPAREBIT ;NOW GO DO THE HIGH BAND BYTE BOTHDONEBCF HIGHONES ;DO LOW NEXT TIMECLRF BYTE ;CLEAR IT OUT FOR NEXT PASSRETURNWINNERMOVLW H'30'MOVWF FSRMORERESULTSMOVF INDF,WCLRF INDFINCF FSR,FADDWF INDF,FMOVF FSR,WINCF FSR,FXORLW H'3F'BTFSS STATUS,ZGOTO MORERESULTSMOVLW 0X31MOVWF FSROUTPUTRESULT;;OUTPUT HERE;MOVF INDF,WSUBLW 0X20 ;THRESHOLDRRF RESULT,fINCF FSR,FINCF FSR,FMOVF FSR,WXORLW 0X41BTFSS STATUS,ZGOTO OUTPUTRESULTCOMF RESULT,fMOVF RESULT,WXORLW D'17'BTFSC STATUS,ZGOTO GOTCHA1MOVF RESULT,WXORLW D'33'BTFSC STATUS,ZGOTO GOTCHA2MOVF RESULT,WXORLW D'65'BTFSC STATUS,ZGOTO GOTCHA3MOVF RESULT,WXORLW D'18'BTFSC STATUS,ZGOTO GOTCHA4MOVF RESULT,WXORLW D'34'BTFSC STATUS,ZGOTO GOTCHA5MOVF RESULT,WXORLW D'66'BTFSC STATUS,ZGOTO GOTCHA6MOVF RESULT,WXORLW D'20'BTFSC STATUS,ZGOTO GOTCHA7MOVF RESULT,WXORLW D'36'BTFSC STATUS,ZGOTO GOTCHA8MOVF RESULT,WXORLW D'68'BTFSC STATUS,ZGOTO GOTCHA9MOVF RESULT,WXORLW D'40'BTFSC STATUS,ZGOTO GOTCHA0MOVF RESULT,WXORLW D'72'BTFSC STATUS,ZGOTO GOTCHAPOUNDMOVF RESULT,WXORLW D'24'BTFSC STATUS,ZGOTO GOTCHASTARCLRF RESULTGOTO SENDIT GOTCHAPOUNDMOVLW H'23'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHASTARMOVLW H'2A'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA1MOVLW H'31'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA2MOVLW H'32'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA3MOVLW H'33'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA4MOVLW H'34'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA5MOVLW H'35'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA6MOVLW H'36'MOVWF RESULTBSF ONELITGOTO SENDIT GOTCHA7MOVLW H'37'MOVWF RESULTBSF ONELITGOTO SENDITGOTCHA8MOVLW H'38'MOVWF RESULTBSF ONELITGOTO SENDITGOTCHA9MOVLW H'39'MOVWF RESULTBSF ONELITGOTO SENDITGOTCHA0MOVLW H'30'MOVWF RESULTBSF ONELITGOTO SENDIT;; SEND TO USART;SENDITBANKSEL SPBRGMOVLW D'25'MOVWF SPBRG ;9600 @16MEGMOVLW B'00100000'MOVWF TXSTABANKSEL TXREGBSF RCSTA,SPENMOVF RESULT,WMOVWF TXREGBSF PORTB,0BTFSC ONELITCALL WAITBCF PORTB,0RETURNWAITMOVLW H'5'MOVWF COUNTINTERLOOPCLRF TMR0BCF INTCON,GIEBCF INTCON,T0IFBANKSEL OPTION_REGMOVLW B'00000111'MOVWF OPTION_REGBANKSEL TMR0LOOPAROUNDBTFSS INTCON,T0IFGOTO LOOPAROUNDDECFSZ COUNT,fGOTO INTERLOOPRETURNACCUM_LOWMOVLW H'30'MOVWF FSRTESTFORNEGBTFSC INDF,7GOTO NEGGOTO NEXTNEG; SUBTRACT AX FROM 0 MOVF INDF,WSUBLW 0MOVWF INDFNEXTINCF FSR,FMOVF FSR,WXORLW H'40'BTFSS STATUS,ZGOTO TESTFORNEGRETURNENDAppendix D877 Map InformationMPLINK v2.00.00, LinkerLinker Map File - Created Mon Feb 14 11:26:59 2000Section InfoSection Type Address Location Size(Bytes) --------- --------- --------- --------- --------- BEGIN code 0x000000 program 0x000004 INTERRUPT_VECTOR code 0x000004 program 0x000002 INTERRUPT code 0x000005 program 0x000066 .cinit romdata 0x000038 program 0x000004 .code code 0x000100 program 0x000204 sect3 code 0x000400 program 0x000104 sect2 code 0x000600 program 0x000104 .udata udata 0x000020 data 0x000000 Program Memory UsageStart End--------- ---------0x000000 0x0000010x000004 0x0000390x000100 0x0002010x000400 0x0004810x000600 0x000681574 out of 8197 program addresses used, program memory utilization is 7%。
