call flow
金融外汇买卖相关英语词汇翻译

金融外汇买卖相关英语词汇翻译金融外汇买卖相关英语词汇翻译Accepted 承兑Accrued interest累计利息advance 放款American style 美式选择权appreciation 升值Arbitrage 套利交易asset allocation 资产分配原则Asset swap 就持有的资产利息进行交换Asset/liability management 资产负债管理Assets liquidity 资产的流动性Assets safety 资产安全Assets yield 资产的获利性AT the money (ATM) 价平Auction 标售Authority letter 授权书Banker’s acceptance 银行承兑汇票Basis swap (floating -against floating IRS)Bear call spread 买权看空价差Bear put spread 卖权看空价差Bearer form 持有人形式best order 最佳价格交易指示单Bid rate 借入利率(或买入价格,汇率)Big figure 大数(交易时忽略不报的前几位数)Book entry form 无实体形式Break-even exchange rate 两平点汇率Bretton Woods system 布莱登国际货币制度Broken date 畸零天期(见Odd date)Bull call spread 买权看多价差Bull put spread 卖权看多价差Buy call 买入买权Buy or sell forward 买卖远期Buy or sell spot 买卖即期Buy put 买入卖权Buyer 买方Calendar spread 水平式价差策略Call option 买权Calling customer 询价者Calling party 询价者Cash flow book 现金流量登记薄Cash flow gap 现金流量缺口Cash flow gap 资金缺口Cash flow projection现金流量之预期Cash 当日交割CD(certificate of deposit) 存单Chain method 联算法Chief money dealer首席货币交易员Clearing house 清算所Commercial hedge 进出口商避险Commercial paper商业本票Commodity futures trading commission 美国期货交易委员会Competitive bid 竞标Contract date 定约日Contract limit 契约额度Contract risk 契约风险Counter party 交易对手Country limit 国家额度Coupon rate 票面利率Coupon swap (fixed-against floating IRS)Cover 补回,冲销covered interest arbitrage 无汇率波动风险的套利操作Credit risk 信用风险Cross hedge 交叉避险Cross rates 交叉汇率(通过第三种货币计算两种货币的汇率)Currency future 外汇期货Currency futures contracts 外汇期货契约Currency futures 外汇期货Current yield 当期收益率Cut off time 营业截止时间Day trading 当日冲销(使当日净部位为零)Dealer’s authority 交易权限Dealing day 交易日Dealing room 交易室Dealing ticket 交易单Delivery Date 交割日Direct quotation=price quotation直接报价Discount 贴水Dj index future 道·琼斯指数期货合约Draft 汇票Duration 存续期间Easy money 低价货币Effective interest rate 有效利率Engineered swap transaction操纵式换率交易(将买入卖出两个不同交易合并,使其具有换汇交易的效果)European currency unit(ECU)欧洲货币单位Exchange control system 外汇管制制度Exercise price 履约价格Expiry date 到期日Face value 面值(股票、票据上记载的名目价值)Firm market 行情坚挺的市场Firm order 确定指示单Fixed exchange rate system 固定汇率制定Fixed rate liability 利率固定负债Fixing date 指标利率定订基准日Flat yield curve 水平收益率曲线floating exchange 浮动汇率制度Floor broker 场内经纪商Floor trader 场内交易商Follow up action 动态策略Forward against forward远期对远期换汇交易Forward rate agreement(FRA)远期利率协定Forward rate 远期汇率Forward value date 远期外汇到期日FT-SE 100 Index Future 伦敦金融时报指数期货Futures 期货FX risk 汇率风险Gapping 期差操作General floating 普遍浮动Generic Swap 标准型的IRS 交易gold exchange standard金汇兑本位制度gold export point 黄金输出点Gold rush 黄金抢购风gold standard 金本位制度Government bonds 政府债券Group of Twenty 20国委员会Hang Seng Index 恒生估价指数Hedging interest rate risk规避利率波动风险Hit 询价者以bid rate 卖出被报价币给报价银行Holding position 持有部位If order 附条件交易指示单IMM 芝加哥国际货币市场In the money (ITM) 价内Index swap 利率交换indirect quotation=quantity quotation 间接报价Inter bank offer rates 银行同业拆放利率Interest rate futures 利率期货Interest rate parity theory 利率平价理论Interest rate return 报酬率Interest rate swaps(IRS)利率交换intermediary 中间人international payment system 国际支付制度Intra day limit 日间额度Intra-day trader日间交易者,短线交易员Intrinsic value 隐含价值Junior money dealer资浅货币交易员LIBOR 伦敦银行同业拆借利率LIFFE 伦敦国际金融期货交易所Line of credit 信用额度Line of limit 额度限制liquidity premium流通性风险补贴London inter bank bid rate (LIBID) 伦敦银行间存款利率Long butterfly call spread 买入碟式买权价差Long butterfly put spread 买入碟式卖权价差Long currency future contract 买入外汇期货契约Long Straddle 买入跨式部位,下跨式部位Long strangle 买入不同履约价格的跨式部位Margin call 追加保证金Margin trading 保证金交易Mark to market 调整至市场价Market order 市场价格指示单Mismatch gapping 到期缺口Money market swap IRS持有时间短于两年者Money position 货币部位long position 买超或长部位(借入的金额大于贷)Monthly limit 每月限额multiple currency reserve system多种货币准备制度Nasdaq Index Future 纳斯达克指数期货Near the money 价近Negative yield curve 负收益率曲线Negotiable certificate of deposit 可转让定期存单Net mismatch 净缺口Nikki index future 日经指数期货Nominal interest rate 名目利率Nominal Interest rate名目利率(票面或双方约定的利率,减通货膨胀等于实质利率)Non earning asset 非利率敏感资产Non profitable liability非利率敏感负债Non reference currency 报价币Notional amount 承作金额Odd date(Odd maturity)畸零天期,畸零期(FX交易非整周整月的日期,如10天,40天)Off-balance Sheet 表外交易工具(衍生性金融产品)Offer rate 贷放利率(或卖出价格,汇率)Offset 对冲,轧平Open spot net position 即期净部位Operation risk 作业风险Option date forward 任选交割日的远期汇率Option 选择权Options reserve 选择权保留额度Order 交易指示单Out of the money(OTM) 价外Outright forward 远期直接汇率Over the counter店头市场,柜台交易市场Overall limit 总合限额Overbought 买超Overnight(O/N) 当日交割之隔夜拆放Oversold 卖超Par 报价与被报价币的利率相同,换汇汇率为零。
【cisco】architecture wifi offload

White PaperArchitecture for Mobile Data Offload over Wi-Fi Access NetworksIntroductionMobile network traffic is growing exponentially, and service providers must manage their networks efficiently to meet consumer demand. The technology evolution of radio access networks is limited by the laws of physics, and significant growth in radio frequency (RF) efficiency can no longer be expected. Long-Term Evolution (LTE) radio access is reaching the limits of Shannon’s law, the spectrum available for mobile data applications is limited, and the only solution for increasing overall mobile network capacity is to increase the carrier-to-interference ratio while decreasing cell size and deploying small cell technologies. The most efficient way to use small cells is to position them in locations where significant amounts of data are generated (shopping malls, stadiums, university campuses, public transportation hubs, etc.) and where subscribers spend most of their time and therefore consume significant amounts of data (homes, offices, etc.). Wi-Fi, one of the small cell technologies, appeals to many operators as a cost-effective mean of offloading large amounts of mobile data traffic while delivering a variety of new services. It offers these features:● ● ● ●Widespread existing deployments Availability of user devices that support the technology Cost efficiency Capability to address new users and devices without mobile subscription (without a subscriber identity module [SIM])● ●Globally available spectrum capacity Standards availability for integration into mobile core networksThis document explores technical aspects of Wi-Fi offload architecture and its capabilities and integration into existing mobile networks to provide a viable and efficient way to offload subscriber traffic.Overview of Wi-Fi Offload ArchitectureThe Third-Generation Partnership Project (3GPP) standard differentiates two types of Wi-Fi access (also referred to as non-3GPP IP access):●Untrusted: Introduced in the early stages of the Wi-Fi specification in 3GPP Release 6 (2005), untrusted access includes any type of Wi-Fi access that either is not under control of the operator (public open hotspot, subscriber’s home WLAN, etc.) or that does not provide sufficient security (authentication, encryption, etc.).●Trusted: Trusted access generally refers to operator-built Wi-Fi access with over-the-air encryption and a secure authentication method. Trusted non-3GPP IP access was introduced only with the LTE standard in 3GPP Release 8 (2008). Although most of today’s offload designs are build on the trusted model, 3GPP does not currently offer guidance for integration with the 3G or 2G packet core. However, as discussed in this document, this type of access is natively integrated into LTE’s evolved packet core (EPC).© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 1 of 23Because most of today’s mobile networks are 3G based, a significant part of this document describes the possible methods of integrated trusted non-3GPP IP access into the 3G mobile packet core (MPC) together with its associated policy and charging control (PCC) architecture. Although the term “trusted non-3GPP IP access” is defined for EPC only, this document extends its definition in 3G contexts to describe Wi-Fi networks controlled by mobile operators. 3GPP 24.302 has the following definition: “For a trusted non-3GPP IP access network, the communication between the user equipment and the EPC is secure.” Thus, with the latest service provider Wi-Fi architectures encompassing Extensible Authentication Protocol (EAP) and IEEE 802.1X-based authentication, and with IEEE 802.11i-based RF encryption and optional use of control and provisioning of wireless access points and Datagram Transport Layer Security (DTLS) for secured user and control planes, all the elements exist for service provider Wi-Fi to be considered as trusted non-3GPP. After the 3G designs, this document describes the evolution of the architectures toward EPC integration as specified in 3GPP standards. Session mobility and, more generally, IP address persistence when moving between 3G, LTE, and Wi-Fi are also covered. The document also discusses the integration models for untrusted networks, although these are less commonly deployed in mobile networks. In the 3GPP specification, the Wi-Fi network is referred to as the Wi-Fi access network only. No details about the Wi-Fi network structure are specified. This document, however, separates the network into the access and gateway components. The Wi-Fi network infrastructure for mobile data offload consists of three parts:● ●Wi-Fi radio access network (Wi-Fi RAN) Wi-Fi access gateway (WAG) and Wi-Fi back-end systems (this document expands the definition from 3GPP TS 23.234 to refer also to non-3GPP WAG)●Packet core integration elements (multiple options)© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 2 of 23Figure 1 illustrates the architecture. It includes integration elements for 3G as well as LTE to show a summary of all designs built throughout this document.Figure 1. Wi-Fi Network ArchitectureIf the Wi-Fi network is used for mobile data offload, which is the topic of this document, it needs to take care of these tasks:● ●Authentication: To help ensure that only authorized subscribers can access the network PCC: For proper billing, quality of service (QoS), and policy enforcement for the traffic generated through Wi-Fi access, ideally compliant with 3GPP PCC●IP persistence: For service mobility between different access networks (3G to Wi-Fi, Wi-Fi to 3G, or across the Wi-Fi network)The following sections examine the details of each of these functions.AuthenticationTo control subscriber access to Wi-Fi networks, multiple authentication methods can be used. The choice of method is crucial to the usability of the network. The more transparent the authentication method is for the subscriber, the greater the likelihood that the subscriber will connect to the network. The authentication method also determines the subscriber and device types that can be addressed in a particular network (subscribers with or without SIM cards, the operator’s subscribers, visiting subscribers, etc.). In a typical modern Wi-Fi network, two types of authentication are available to address all possible subscribers and at the same time provide convenient access to the network for frequent Wi-Fi users. The first method, portalbased authentication, targets customers without a permanent contract with the operator (vouchers, time-limited© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 3 of 23access, SMS payments, etc.). Alternatively, EAP authentication provides transparent and easy access for the operator’s own subscribers with SIM cards or certificates.Portal-Based AuthenticationPortal-based authentication depends on Layer 3 connectivity to the network and HTTP communication before granting access to the subscriber. The Wireless Internet Service Provider Roaming (WISPr) standard also uses HTTP communication with the portal for automatic authentication, with the user device launching HTTP communication in the background without user intervention (Figure 2).Figure 2. Portal-Based Authentication ArchitectureThis method relies on the WAG in the Wi-Fi network, which blocks all IP communication for unknown (new) subscribers and redirects HTTP connections to a captive portal. The captive portal is responsible for requesting user credentials from the subscriber and triggering authentication, authorization, and accounting (AAA) to authenticate the subscriber. After successful login, the WAG will typically be signaled by the AAA server. From this moment, the subscriber is known in the AAA cache, and WAG allows the subscriber to send and receive data. Usually, the user’s IEEE 802.11 MAC address is also cached in the AAA server, together with the user data and granted service. If the subscriber leaves the Wi-Fi coverage area and then returns, the subscriber’s device will be recognized by the WAG based on the MAC address and automatically authenticated against the cached AAA record, so the subscriber is not repeatedly redirected to the portal after losing Wi-Fi coverage. This method of MAC address caching is also referred to as transparent automatic logon (TAL).© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 4 of 23A typical TAL attachment call flow is shown in Figure 3 for the case of a Layer 2 attached WAG.Figure 3. Typical Transparent Automatic Logon Call FlowEAP-Based AuthenticationEAP-based authentication uses EAP and IEEE 802.1x to provide Layer 2 authentication for subscribers accessing the network with EAP-capable devices. For actual authentication, multiple credentials can be used, depending on the capability of the device. Devices with SIM cards encapsulate the SIM application information exchange into the EAP message, and these are proxied by the AAA server to the home-location register (HLR) for authentication. EAP-SIM (RFC 4186) or EAP-Authentication and Key Agreement (EAP-AKA; RFC 4187) standards are used for the encapsulation, depending on the type of SIM card used and the HLR capabilities. Obviously, this method requires interconnection between the AAA server and the HLR or home-subscriber server (HSS). The architecture is shown in Figure 4.© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 5 of 23Figure 4.EAP-Based Authentication ArchitectureFor subscribers with non-SIM devices, the operator can distribute certificates for EAP-Transport Layer Security (EAP-TLS) or similar versions of EAP authentication. The typical call flow of EAP authentication (with HLR integration) is shown in Figure 5.Figure 5. Typical EAP Authentication Call Flow© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 6 of 23Note that EAP-based authentication offers a radio security advantage. Because the authentication is handled at Layer 2, EAP messages can be used to negotiate encryption keys for the IEEE 802.11i-based encryption of the radio interface. This approach provides much stronger security for radio communication compared to the unencrypted radio interface of portal-based authentication and is uniquely able to prevent simple MAC address spoofing attacks.Next Generation HotspotIn 2010, Cisco and industry leaders formed the Next Generation Hotspot Task Group in the Wireless Broadband Alliance (WBA). The goal was to rally the industry around a common set of Wi-Fi Alliance (WFA) standards called Hotspot 2.0 that would bring a 3G-like end-user experience to Wi-Fi authentication and roaming. The outcome of the Next Generation Hotspot Task Group is a set of operator guidelines and the Wi-Fi Certified Passpoint interoperability for operators and equipment vendors. The Cisco SP Wi-Fi solution features Next Generation Hotspot, enabling service providers to better manage and monetize their carrier-grade Wi-Fi networks. There are three main building blocks of the next-generation hotspot: IEEE 802.11u, Wi-Fi Protected Access 2 (WPA 2) Enterprise, and EAP-based authentication. For a detailed description of the initiative, see The Future of Hotspots: Making Wi-Fi as Secure and Easy to Use as Cellular.® ™program expected in 2012 from the Wi-Fi Alliance. The certification will help ensure authentication and roamingAuthentication SummaryBecause of the complementary functions of both authentication methods, mobile operators deploying Wi-Fi access networks usually implement both EAP and IEEE 802.1X authentication and portal-based authentication in their networks. Portal-based authentication is used to attract subscribers visiting the network who don’t yet have a relation to the operator. It allows typical public Wi-Fi use cases such as credit card payments, vouchers, and SMS passwords. In general, it enables generation of new revenue from Wi-Fi networks. EAP-based authentication targets primarily devices with the operator’s SIM card. It allows transparent authentication and secure communication without much interaction from the subscriber (only initial configuration of the service set ID (SSID) is needed when a device detects the Wi-Fi network for the first time). In real-life deployments, the introduction of EAP-SIM or EAP-AKA authentication leads to significantly better utilization of the network by subscribers and therefore enables much greater savings from offloading. With the introduction of Wi-Fi Certified Passpoint devices, operators will be able to simplify Wi-Fi network access even more. IEEE 802.11u devices do not need any intervention from the subscriber to connect to the Wi-Fi network (unlike traditional devices, which require SSID selection). Roaming agreements based on the Next Generation Hotspot recommendation (WLAN Roaming Inter-Exchange [WRIX]) enable user equipment with IEEE 802.11u support to choose the right SSID automatically, even in visited networks.Policy and Charging ControlAn important concern of mobile operators is the availability of similar or identical policy enforcement and charging rules for the subscriber, regardless of the RAN being used. Therefore, the design of PCC integration is a crucial part of Wi-Fi offload.© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 7 of 23Experience from live deployments shows that the most efficient approach to PCC integration is the reuse of the elements deployed for the 3GPP services. The actual integration option will depend on the PCC infrastructure implemented in the particular mobile operator network. If the operator uses a device with the standalone policy and charging enforcement function (PCEF), the WAG will be integrated as an additional gateway served by the PCEF. If the PCEF is integrated into the gateway General Packet Radio Service (GPRS) support node (GGSN), the WAG may emulate a serving GPRS support node (SGSN) and switch the Wi-Fi sessions to a GPRS Tunneling Protocol (GTP) tunnel to the traditional GGSN. The following sections discuss the details of these two options. Note that this document describes trusted non-3GPP access integration into 2G and 3G PCC. The 3GPP standard offers no guidance for this integration. Later this document explores standardized architecture for LTE integration and untrusted non-3GPP IP access integration.Standalone PCEFIn the standalone PCEF scenario, the WAG is set up to send user data traffic to the PCEF for PCC integration. At the same time, traffic that does not need policy control (traffic from visiting customers, wholesale traffic, onetime voucher users, etc.) is allowed to go directly to the Internet (Figure 6).Figure 6. Standalone PCEF ArchitectureBecause the PCEF needs to be able to correlate the user identity with the data flows passing the PCEF, a mechanism is needed that can synchronize the user identity with the IP address of the subscriber (so that individual data packets can be associated with the user data plan and processed accordingly). Commonly, the RADIUS proxy function on the PCEF is used to create user session information based on the attributes included in the accounting messages coming from the access gateway for a particular user. Figure 7 shows the typical call flow.© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 8 of 23Figure 7.Typical PCEF Authentication Call FlowIf this model is deployed, the operator needs to help ensure that all mandatory information needed by the PCEF is included in the RADIUS messages from the access gateway or proxied through AAA, where the necessary attributes are added to the message. In addition to the IP address of the subscriber session, information about the international mobile subscriber identity (IMSI), the mobile station international subscriber directory number (MSISDN), and the associated access point name (APN) is usually required.GTP to Traditional GGSNIf the PCEF is an integral part of the GGSN, the option of forcing Wi-Fi sessions into a GTP tunnel (packet data protocol [PDP] context) may provide the best solution for PCC integration. The traffic that does not belong to the mobile subscribers of the operator, and which therefore cannot be processed on the GGSN, is forwarded directly to the Internet (Figure 8).© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 9 of 23Figure 8.GTP-to-Traditional GGSN ArchitectureClearly, GTP support is required on the WAG for this deployment model. Also important to consider is the availability of the required attributes in the PDP context request, which are mandatory in the operator’s PCC system. Again, these attributes commonly include the IMSI, MSISDN, QoS profile, and APN. The call flow for this deployment model is shown in Figure 9.Figure 9. GTP-to-Traditional GGSN Call Flow© 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.Page 10 of 23Note that even though all sessions (3G and Wi-Fi) are anchored on the GGSN, this solution does not provide transparent handover of the IP sessions between the Wi-Fi and 3G radio networks. This limitation exists because the Wi-Fi and 3G PDP contexts are individual sessions, and the user device can open them simultaneously. Unfortunately, the 3GPP standard does not provide a mechanism to help ensure that the same GGSN is chosen for both of these PDP contexts, and therefore anchoring of the sessions on the same device cannot be achieved.PCC Integration ConsiderationsWhen performing PCC integration, note the following:●The options listed are valid and needed for 3G. As discussed later, LTE provides native integration into theEPC and therefore into the PCC●The critical element is the capability of the WAG to provide all necessary information for charging(specifically, some of these attributes are not part of EAP authentication and need to be retrievedseparately, if needed: for example, the MSISDN, the QoS profile, and optionally, the 3GPP chargingcharacteristics)●Usually, the PCEF does not handle traffic from users who are not mobile customers of the operator(non-SIM subscribers). This traffic is sent directly to the Internet. If these particular sessions need policy or charging functions, these are usually handled by the WAG and Wi-Fi back-end systems directlyLTEBefore describing the third function of the Wi-Fi offload architecture, session handover, this document examines the integration of PCC in an LTE scenario. This examination will help you later understand user session mobility and anchoring.3GPP TS 23.402 describes native integration of trusted and untrusted non-3GPP IP access networks into the EPC. The standard accepts that the Wi-Fi network is as valid an access network as any other 3GPP radio access network. This acceptance enables operators to use the standards-based EPC components for integration and therefore helps ensure a good level of interoperability between different access types.As mentioned earlier, this document concentrates first on the trusted part of the architecture. To force the Wi-Fi traffic to the EPC, two interfaces are defined, both of them terminating Wi-Fi sessions on the packet data network gateway (P-GW) as shown in Figure 10.Figure 10. 3GPP Architecture for Non-3GPP IP Access Integration into EPC, S2c OptionThe S2c interface is based on the Dual-Stack Mobile IP Version 6 (DSMIPv6) protocol and requires user equipment to support it. DSMIPv6 creates a tunneled connection between the user equipment and the P-GW, which is used to forward all traffic to and from the user equipment. The P-GW is responsible for assigning a virtual IP address to the tunnel during the setup process. This IP address is from the same IP pool that is used for LTE sessions. Because all traffic to and from the user equipment is sent through the tunnel, the P-GW has complete visibility of the user traffic and can apply PCC and other necessary functions to the traffic in the same manner as it does to the LTE sessions (Figure 11).Figure 11. 3GPP Architecture for Non-3GPP IP Access Integration into EPC, S2a OptionAnother option shown in Figure 11 is to choose the S2a interface for forwarding traffic from the Wi-Fi network to the EPC. This interface is based on the Proxy Mobile IPv6 (PMIPv6) protocol. As with S2c, the interface terminates on the P-GW and enables visibility into the user traffic. The difference is that the PMIPv6 protocol does not require any changes on the user equipment. The wireless access gateway (WAG) in the trusted non-3GPP IP access network provides the mobile IP functions transparently for the client. It creates the tunnel, requests the IP address from the P-GW, and then assigns this address to the Wi-Fi connection. In this way, the user equipment is assigned an IP address that is part of the P-GW pool, but it does not see the address as virtual but as a physical address directly on the Wi-Fi interface.Figure 12 shows an overview of LTE architecture. Again, in addition to tunneled traffic to the EPC, direct connection from the WAG to the Internet is enabled for users who are not mobile subscribers of the operator.Figure 12. LTE ArchitectureTwo methods of integration (S2a and S2c) have been used here, and each has different implications for the deployment. The S2c approach requires changes on the user equipment; therefore, it is considered client-based. This feature may not be trivial in a mobile network because of the need for client software for functions. The mobile operator must help ensure that large numbers of different handsets and operating systems can be addressed by the software, must keep the user equipment updated with new versions of software, and must motivate subscribers to use the client software. Figure 13 illustrates the attachment as defined by 3GPP. Phase A represents attachment to the Wi-Fi network. In phase B, the DSMIPv6 tunnel is opened to the P-GW; and in phase C, the session is signaled as the active one. Also illustrated is the establishment of policies for the session using the PCRF.Figure 13. S2c Network Attachment As Defined by 3GPPThe S2a approach eliminates the problem of the client software. The trade-off here is that the operator loses control of Wi-Fi activation and session handover on the user equipment. This loss of control may result in unexpected behavior of the user equipment during switchover from 3GPP access to Wi-Fi and back. Figure 14 shows the attachment as defined by 3GPP. The trusted non-3GPP IP access network represents the Wi-Fi network, with the WAG as part of this network. For a detailed description of the call flow, please refer to 3GPP TS 23.402.Figure 14. S2a Network Attachment As Defined by 3GPPInter-Radio HandoverBefore analyzing different methods of handover, it is important to understand the terms often used in this context. Specifically, you need to understand what session handover is and the types of handover that can be implemented depending on the requirements of the mobile operator.In mobile data networks, one of the most important procedures is handover - when a subscriber moves from one radio station to another. The handover procedure describes the behavior of the network when the subscriber switches from one radio type to another (for example, from 3G to Wi-Fi).Today, few handover types can be used. The one required in the operator’s network needs to balance the expectations of subscribers and the complexity of the architecture.●Handover without IP address persistency (connectivity handover): When a subscriber connects to the Wi-Fiaccess network, the subscriber is authenticated transparently and is assigned a new IP address by theWi-Fi network. All new communications can use the new IP address as the source. All established TCP and UDP connections can, however, still continue over the 3G network. If the user equipment logicdisables the 3G interface, then these established sockets will need to be (automatically) reestablished over Wi-Fi, using the new IP address.●Handover with IP persistency (IP handover): When a subscriber connects to the Wi-Fi network, thesubscriber will be assigned the same IP address as he used on the 3G or LTE network. If the established TCP and UDP connections are bound to a physical interface (because of the TCP/IP stack implementation of the UE), they will need to be (automatically) reestablished using the new Wi-Fi interface, even though they will use the same IP address.●Session handover (transparent handover): This type of handover is similar to IP handover, but thehandover must occur in a time range that allows real-time media applications (voice over IP, streamingvideo, etc.) - for example, using established UDP sockets for media and TCP sockets for the control-plane protocol - to continue without interruption or user-experience degradation as the device switches between Wi-Fi and 3G cellular connectivity.Note that seamless handover can be achieved only with user equipment cooperation, which means that software updating (for client software) is needed on terminals. At minimum, this software needs to provide a virtual interface adapter, to mask the physical interface structure for TCP and UDP sockets. The challenges of client software have already been discussed above.3GPP defines handover mechanisms for trusted Wi-Fi only as part of the LTE architecture. For untrusted Wi-Fi, proposals exist for 3G and LTE. This document starts with a look at trusted non-3GPP IP access networks in LTE.S2a-Based Handover (Clientless)The advantage of PMIPv6 as protocol for the S2a interface is that the protocol is built for network-based IP mobility. Therefore, it can provide, without client involvement, handover of the IP address between different access types. In this design, the P-GW is responsible for anchoring the session, assigning the IP addresses, and switching the PMIPv6 or Ga TP tunnels between different access gateways in the event of handover. The access gateways must support the mobile access gateway (MAG) function to fulfill all mobile IP-related mobile-node functions.Figure 15 illustrates the handover call flow as defined in 3GPP TS 23.402. The trusted non-3GPP IP access element is equivalent to a WAG.Figure 15. Handover Call Flow As Defined in 3GPP TS 23.402Although S2a-based handover is clientless, recall that the problems with Wi-Fi-to-3GPP handover are the existence of two radio interfaces on the user equipment and the role of the user equipment as the handover decision point. Because of these two factors, the network can never ensure that the user equipment is using the proper interface.Note: The definition of what constitutes a proper interface can change on an operator-by-operator basis.Also, at the user equipment, the TCP/IP stack needs to be able to cope with two physical interfaces that may eventually have identical IP addresses. Additionally, in some TCP/IP stack implementations, application sockets may be bound to a physical interface. Therefore, when the user equipment or application switches between interfaces, the application connections must be dropped and may need to be reestablished from the new interface.Given all of these dependencies, the PMIPv6-based architecture cannot (without user equipment support) guarantee operation of a transparent handover function on all user equipment types. This situation can be improved if a properly designed connection manager (with virtual adapters) is installed on all user equipment.Cisco is actively working with chipset and handset vendors to support standardization and development of user equipment that meets the requirements for smooth clientless handover.S2c-Based Handover (Client-based)For the S2c interface, 3GPP reuses the IETF-defined DSMIPv6 protocol between the user equipment and theP-GW as the anchor point. When on the non-3GPP network, the user equipment builds the DSMIPv6 to the appropriate P-GW and is assigned a virtual IP address, which is then used for application communication.The same IP address will be assigned to the user equipment over a 3GPP access network in the event of handover. The 3GPP network is treated as the home network, and therefore the user equipment does not need to set up a DSMIPv6 tunnel on the 3GPP access network.Figure 16, from 3GPP TS 23.402, summarizes the call flow during handover from an LTE access network to aWi-Fi access network.。
SIPReasonHeader

SIPReasonHeaderSIP Reason HeaderOverviewThe Reason Header field for SIP is included in each of the following messages. (ITU-T Recommendation Q.850) ?BYECANCEL4xx, 5xx, and 6xx messagesUp till software 10.3.3 the IMG had the ability to propagate the Reason Header in each of the above messages from the TDM leg of the call to the SIP leg of the call. The Reason Header would indicate why a SIP request or response was issued. In software 10.5.0 the ability to propagate the Reason Header from the SIP leg of a call to the TDM side of the call was added. The Reason Header Field in each of the SIP messages is used primarily for debugging problems in a circuit. Clients and servers are free to ignore this header field as it has no impact on protocol processing. The Reason Header Field satisfies RFC 3326. The Reason Header field now gives the customer the ability to propagate cause code information from SIP to TDM and TDM to SIP without having to configure SIP-T.Call TracingSupport Personnel can enable Call Tracing on the IMG. Once this is accomplished all Reason Header information will be printed out for the following messages:BYECANCEL4xx, 5xx, and 6xx messagesNote: In case of multiple Reason Headers presented in the incoming SIP message, only the first Reason Header is decoded.Benefits:This feature is useful for debugging purpose, particularly if there is a call failure in SIP to SS7 traffic. Below are Call Flows and their corresponding Call Traces. Note that for reference the Reason Header field is shown in red.Implementation (Message propagates from TDM to SIP)CASE #1:Cause Number 1 (404 message)A call is generated from the SIP side to the IMG. The IMG then converts to an SS7 network and receives the IAM message. The SS7 leg sends a release with cause code of 1 (Unallocated Number). The IMG then would send a SIP 404 message with the cause code in the Reason Header indicating the problem is an Unallocated (unassigned) number. See Call Flow and Call Trace belowCall FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]SIP/2.0 404 Not Found Call processing releasedVia: SIP/2.0/UDP 10.129.39.123:5060;branch=z9hG4bK-d87543-672bb759901c9e2a-1--d87543-; rport;received=10.129.39.1 23Contact:Call-ID: 2b61265d2e589e06ZjIzZDY3ZjU4ODA3NmRhODdmNGI4Y2M0NGRmNTYyMTY.From: "Boston";tag=f818c458To: "508";tag=a94c095b773be1dd6e8d668a785a9c8449dcCSeq: 1 INVITEServer: Cantata-SIP/10.3.2.22 Boston 0Reason: Q.850 ;cause=1 ; text="Unallocated (unassigned) number"Content-Length: 0CASE #2:Cause Number 17 (486 message)A call is generated from the SIP side to the IMG. The IMG then converts to an SS7 network and receives the IAM message. The SS7 leg sends a release with cause code of 17 (User Busy). The IMG then would send a SIP 486 message with the cause code in the Reason Header indicating the problem is User Busy. See Call Flow and Call Trace below Call FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]SIP/2.0 486 Busy Here Call processing releasedVia: SIP/2.0/UDP 10.129.39.123:5060;branch=z9hG4bK-d87543-af44ae69a320e04a-1--d87543-; rport;received=10.129.39.1 23Contact:Call-ID: 1c214262d2299f3cZjIzZDY3ZjU4ODA3NmRhODdmNGI4Y2M0NGRmNTYyMTY.From: "Boston";tag=244d4425To: "508";tag=a94c095b773be1dd6e8d668a785a9c84c527CSeq: 1 INVITEServer: Cantata-SIP/10.3.2.22 Boston 0Reason: Q.850 ;cause=17 ; text="User busy"Content-Length: 0CASE #3Cause Number 16 (BYE message)A call is generated from the SS7 side to the IMG. The IMG then converts to a SIP network and receives the INVITE message. The SIP side then sends a 180 ringing response. The SIP side then sends a 200 OK message and the call gets connected. After a while the phone is hung up and the SS7 leg sends a RELEASE with cause code of 16 (Normal Clearing). The IMG then would send a SIP BYE message with the cause code in the Reason Header indicating the problem is a Normal Clearing. See Call Flow and Call Trace belowCall FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]BYEsip:***********.39.123:5060SIP/2.0Via:SIP/2.0/UDP10.129.39.59:5060;rport;branch=z9hG4bK-3a95-46623-19995-361Call-ID:***********************************.39.59CSeq: 2 BYEMax-Forwards: 70To: ;tag=8262313bFrom: ;tag=95ffcd055e0f78f7d5d397020e89288d2b07User-Agent: Cantata-SIP/10.3.2.22 Boston 0Reason: Q.850 ;cause=16 ; text="Normal call clearing"Content-Length: 0CASE #4:Cause Number 3 (404 message)If the user dials an incorrect number that is not in the route table the IMG will reject the call and send a 404 Not Found to the SIP side.Call FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]SIP/2.0 404 Not Found Call processing releasedVia: SIP/2.0/UDP 10.129.39.123:5060;branch=z9hG4bK-d87543-47486a49a1277175-1--d87543-; rport;received=10.129.39.123Contact:Call-ID: 3355d752f5739754ZjIzZDY3ZjU4ODA3NmRhODdmNGI4Y2M0NGRmNTYyMTY.From: "Boston";tag=2816b75aTo: "999";tag=a94c095b773be1dd6e8d668a785a9c84de15CSeq: 1 INVITEServer: Cantata-SIP/10.3.2.37 Boston 0Reason: Q.850 ;cause=3 ; text="No route to destination"Content-Length: 0CASE #5:Cause Number 1 (404 message)In case the user dials correct number but incoming translation table has wrong number, then IMG would reject the call and send a 404 Not Found to the SIP side.Call FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]SIP/2.0 404 Not Found Call processing releasedVia: SIP/2.0/UDP 10.129.39.123:5060;branch=z9hG4bK-d87543-47486a49a1277175-1--d87543-; rport;received=10.129.39.123Contact:Call-ID: 3355d752f5739754ZjIzZDY3ZjU4ODA3NmRhODdmNGI4Y2M0NGRmNTYyMTY.From: "Boston";tag=2816b75aTo: "999";tag=a94c095b773be1dd6e8d668a785a9c84de15CSeq: 1 INVITEServer: Cantata-SIP/10.3.2.37 Boston 0Reason: Q.850 ;cause=1 ; text="Unallocated (unassigned) number"Content-Length: 0Implementation (Message propagates from SIP to SIP)CASE #1:SIP to SIPIn the case of SIP to SIP traffic, the Reason header field is usually not needed in responses because the status code and the reason phrase already provide sufficient information,according to RFC 3326. However, the Reason Header is included for BYE, 4xx, 5xx, and 6xx. Please note that CANCEL message in the SIP to SIP traffic does not include the Reason header field.Call FlowCall Trace<--- [10.129.39.123, 5060 <- 10.129.39.59, 5060]BYEsip:***********.39.123:5060SIP/2.0Via:SIP/2.0/UDP10.129.39.59:5060;rport;branch=z9hG4bK-2701-1786-19997-394Call-ID:************************************.39.59CSeq: 2 BYEMax-Forwards: 70To: ;tag=d47d7510From: ;tag=95ffcd055e0f78f7d5d397020e89288d708eUser-Agent: Cantata-SIP/10.3.2.37 Boston 0Reason: SIP ;cause=16 ; text="Normal call clearing"Content-Length: 0CASE #2:487 MessageIn the case below, where SIP sends an INVITE message and then sends CANCEL, the IMG sends a 487 Request Terminated in response to the CANCEL message.Call FlowCall Trace<--- [10.129.39.123, 5070 <- 10.129.39.59, 5060]SIP/2.0 487 Request TerminatedVia: SIP/2.0/UDP10.129.39.123:5070;branch=z9hG4bK-675e-1160585843-19988-10-129-39-123;received=10.129.39.123 Contact:Call-ID:*************.39.123From: sipp ;tag=1To: sut ;tag=a94c095b773be1dd6e8d668a785a9c84e50dCSeq: 1 INVITEServer: Cantata-SIP/10.3.2.37 Boston 0Reason: SIP ;cause=487 ; text="Request Terminated"Content-Length: 0Implementation (Message propagates from SIP to TDM)CASE #1:Cause NumberA call is generated from SS7 protocol and sent to the IMG. IMG1 converts from SS7 to SIP. Call is then sent to IMG2 where it converts the SIP messaging back to SS7 and the call goes out of IMG2 using SS7 protocol. The call is then release by hanging phone up or any such normal call release scenario. Note the RELEASE message has the reason header information. Below is Call Flow.Call Trace<--- [10.129.45.107, 5060 <- 10.129.45.104, 5060]BYEsip:*****************.45.107:5060SIP/2.0\r\nVia: SIP/2.0/UDP 10.129.45.104:5060;rport;branch=z9hG4bK-149e-1196263031-19999-118\r\nCall-ID:***************************************.45.104\r\nCSeq: 2 BYE\r\nMax-Forwards: 0\r\nTo: ;tag=a94c095b773be1dd6e8d668a785a9c84089db2cd\r\n From: ;tag=95ffcd055e0f78f7d5d397020e89288d4e3f1b4c\r\nUser-Agent: Cantata-SIP/10.5.0.143 Boston 0\r\nReason: Q.850 ;cause=31 ;text="Normal, unspecified"\r\nContent-Length: 0\r\n\r\n。
Process Flow 说明

Process Flow 繪製時易發生之問題
1. 本流程的定義為Normal狀況時,即重覆運作而會發生者,(特例不需列入 流程中); 舉例如附件0(人力評估或設備評估等) 2. a. 流程圖上他單位的工作內容須明確說明(以動詞說明),舉例如附件 b. Control Point 表上之說明須明確包含File 的形式及傳遞的方式(必要 的需求才列,以動詞說明),舉例如附件0 3. Check Point 若未達到要求時,其Else 須能回饋到管理機制上(非只解決 此次事件,而是需杜絕此事件之再發生),舉例如附件0.6 4. a.Check Point (take)---本單位最晚何時取得他單位完成的結果才可以順 利完成下一動作 b. Control Point (Give)---本單位最快何時可將本動作完成轉他單位執行 5. 流程圖上之箭頭流向標註需明開:
以 1st 階先執行
Process Flow 展開說明 Process Flow 目的:
1. 明確定義各單位(甚至個人)工作內容及重點 2. 工作流程之合理化 3. 使每個單位(每個人)扮演好螺絲釘的角色,確保每個 單位(或人)都不出錯 4. 達到管理的目標---使事情一定會發生 5. 第一次就把事做對(做好FMEA)
6. 本單位任一動作之執行或完成而與他單位之 Input (Take) 或 Output Out (Give) 關係,例如附件 0 ( NB PD 原始版, In Out In ) 7. 流程圖中之動作或流程非憑空想像 (或僅以合理性推斷),需確知並確認 目前該流程之執行方式,若有不合理處可同時修改以達到合理化目的, 舉例如附件2(領料及秤重作業) 8. 他單位間之流程動作或他單位內部須執行之流程動作均不需列在流程 圖上.
Process Flow 觀念及繪製方式
JAVA整理复习题含答案教学文案

J A V A整理复习题含答案1.已知:int a =8,b=6; 则:表达式++a-b++的值为(4)2.已知:boolean b1=true,b2; 则:表达式! b1 && b2 ||b2的值为(false)3.已知:double x=8.5,y=5.8; 则:表达式x++>y--值为(True )4.已知:int a[ ]={2,4,6,8}; 则:表达式(a[0]+=a[1])+ ++a[2]值为(12)5.执行int x, a = 2, b = 3, c = 4; x = ++a + b++ + c++; 结果是(x=12)6.Java中的显式类型转换既能(从低类型向高类型转换)也能从高类型向低类型转换,而隐式类型转换只有前者。
7.执行下列程序代码的输出结果是(10,11,11)。
int a = 10; int i, j; i = ++a; j = a--;System.out.printf("%d,%d,%d", a, i, j);8.执行完boolean x=false; boolean y=true; boolean z=(x&&y)&&(!y) ; intf=z==false?1:2; 这段代码后,z与f的值分别是(False )和(1)9.类是一组具有相同(属性)和(行为)的对象的抽象。
(实例)是由某个特定的类所描述的一个个具体的对象10.(NEW )是一个特殊的方法,用于创建一个类的实例11.(静态)方法不能直接访问其所属类的(实例)变量和(实例)方法,只可直接访问其所属类的(静态成员)变量和(静态成员)方法12.(类)变量在内存中只有一个拷贝,被该类的所有对象共享;每当创建一个实例,就会为(实例)变量分配一次内存,(实例)变量可以在内存中有多个拷贝,互不影响。
13.Java使用固定于首行的(Package)语句来创建包。
kotlin callbackflow用法

CallbackFlow是Kotlin中一种常用的异步编程方式,它结合了Kotlin协程和Flow API,可以方便地处理异步操作和数据流。
下面是一个使用CallbackFlow的示例:kotlinimport kotlinx.coroutines.*import kotlinx.coroutines.flow.*// 定义一个异步函数,返回一个CallbackFlow<Int>fun asyncFunction(): CallbackFlow<Int> = flow {// 模拟异步操作delay(1000)emit(1)delay(1000)emit(2)delay(1000)emit(3)}// 调用异步函数,并处理返回的CallbackFlow<Int>launch {asyncFunction().collect { value ->println("Received value: $value")}}在上面的示例中,我们定义了一个异步函数asyncFunction(),它返回一个CallbackFlow<Int>。
在函数内部,我们使用flow代码块来定义一个Flow对象,并在其中执行异步操作。
通过emit()方法,我们可以向Flow中发送数据。
在这个例子中,我们发送了三个整数1、2和3。
在主线程中,我们调用asyncFunction()函数并使用collect方法来处理返回的CallbackFlow。
collect方法会订阅Flow并接收其中的数据。
在这个例子中,我们简单地打印接收到的值。
需要注意的是,由于Kotlin协程是异步的,因此在调用asyncFunction()函数时,我们使用launch函数来启动一个新的协程。
这样,主线程不会被阻塞,可以继续执行其他任务。
callflow
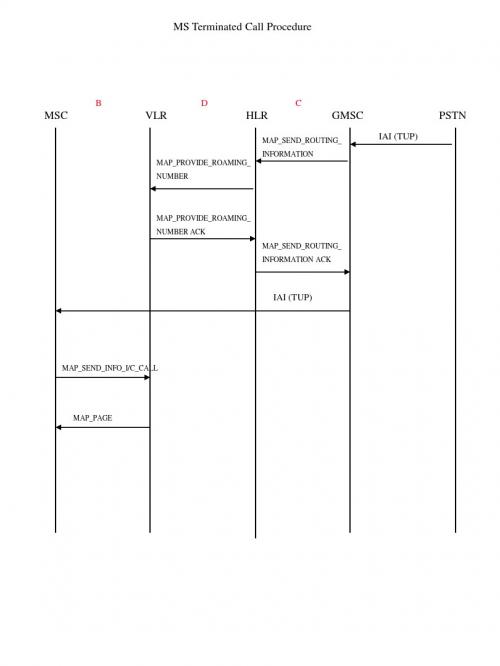
T9103 +
QUEUING(DT1)
BSSMAP
Channel Activation ACK T9103 -
DATA REQ <ASSIGN CMD>
RR(SDCCH)
ASSIGN CMD RELEASE REQ (local end)
RR(FACCH)
(L2 - SABM) EST IND
RR(FACCH)
CBK(TUP)
RELEASE(DT1) DATA REQ RELEASE <REL> T308 + DTAP-CC
CC(FACCH)
CLF(TUP)
RELEASE COM DATA IND <RELASE COM> RELEASE COM(DT1) T308 DTAP-CC CLF(TUP)
CC(FACCH)
DTAP-MM
MAP_AUTHENTICATE ACK MAP_SET_CIPHERING_MODE MAP_PROCESS_ACCESS_REQ_ACK
CM SERVICE ACCEPT(DT1) CM SERVICE ACCEPT(DT1) DTAP
RR(SDCCH)
CM SERVICE ACCEPT(DT1) CIPHER MOD CMD(DT1) ENCR CMD
MS
Um
BTS
MSC
E
GMSC
CLF(TUP)
PSTN
CLF(TUP)
DISCONNECT(DT1) DATA REQ <DISC> T305 + DTAP-CC
CC(FACCH)
DISCONNECT
CC(FACCH)
National Instruments TestStand序列编辑器用户手册说明书
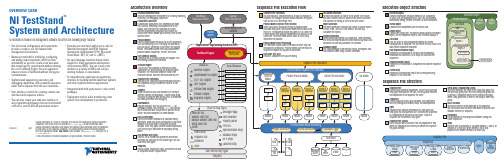
Execution Object StructureExecution ObjectContains information TestStand needs to run a sequence, its steps, and any subsequences it calls. You can suspend,interactively debug, resume, terminate, or abort executions.Thread ObjectRepresents an independent path of control flow.Report ObjectContains the report text. The process model updates the Report object, and the sequence editor or user interface displays it.Call StackLists the chain of active sequences waiting for nestedsubsequences to complete. The first item in the call stack is the most-nested sequence invocation.Root SequenceContext ObjectRepresents the execution of the least-nested sequence invocation that contains a list of steps and calls to other sequences.SequenceContext ObjectRepresents the execution of a sequence that another sequence called.Current StepRepresents the executing step of the currently executingsequence in the call stack.Architecture OverviewTestStand Sequence EditorTestStand development environment for creating, modifying,executing, and debugging sequences.Custom User InterfacesCustomizable applications that, depending on mode,edit, execute, and debug test sequences on a test station. User interfaces are available in several different programming languages and include fullsource code, which allows you to modify them to meet specific needs.Process ModelsDefine the operations that occur for all test sequences,such as identifying the UUT, notifying the operator of pass/fail status, generating a test report, and logging results. TestStand includes three fully customizable process models: Sequential, Parallel, and er Interface ControlsA powerful set of ActiveX controls and support APIs for creating custom user interfaces.TestStand EngineA set of DLLs that provides an extensive ActiveX Automation API for controlling and interacting with TestStand. The TestStand Sequence Editor, User Interface Controls, and user interfaces use this API.Sequence File ExecutionsCreated by the TestStand Engine when you execute a test sequence using the sequence editor or a user interface.AdaptersAllow TestStand to call code modules in a variety of different formats and languages. Adapters also allow TestStand to integrate with various ADEs to streamline test code generation and debugging.Code ModulesProgram modules, such as LabVIEW VIs (.vi ) or Windows Dynamic Link Libraries (.dll ), that contain one or more functions that perform a specific test or action. TestStand adapters call code modules. Built-In Step TypesDefine the standard behaviors for common testing operations. Some step types use adapters to call code modules that return data to TestStand for furtheranalysis. Other step types perform standard operations,such as calling an executable or displaying dialog boxes.User-Defined Step TypesDefine a set of custom step properties and default behaviors for each step of that custom type. You can also define data types.TemplatesCreate custom sequences, steps, and variables to use as templates to build sequence files.OVERVIEW CARDNI TestStandTMSystem and ArchitectureNI TestStand is flexible test management software that offers the following major features:•Out-of-the-box configuration and components provide a ready-to-run, full-featured test management environment.•Numerous methods for modifying, configuring,and adding new components, which provide extensibility so you can create a test executive that meets specific requirements without altering the core TestStand Engine. You can upgrade to newer versions of TestStand without losing your customizations.•Sophisticated sequencing, execution, anddebugging capabilities, and a powerful sequence editor that is separate from the user interfaces.•User interface controls for creating custom user interfaces and sequence editors.•You can also create your own user interface in any programming language that can host ActiveX controls or control ActiveX automation servers.•Example user interfaces with source code for National Instruments LabVIEW, National Instruments LabWindows ™/CVI ™, Microsoft Visual Basic .NET, C#, and C++ (MFC).•An open language interface that provides support for many application development environments (ADEs). You can create code modules in a variety of ADEs and call pre-existing modules or executables.• A comprehensive application programminginterface for building multithreaded test systems and other sophisticated test applications.•Integration with third-party source code control packages.•Deployment tools to aid in transferring a test system from development to production.TestStand Sequence EditorCode ModulesResultsResultsResultsResultsResultsResultsResultsResultsCustom User InterfacesUser Interface (UI)ControlsApplication Programming Interface (API) TestStand EngineSequence File ExecutionsUser-Defined Step TypesSequence File ExecutionsNo ModelTest Socket 0Execution UUTUUTUUTTest Socket 1Execution UUTUUT TestSocket nExecution UUTUUTUUT UUT UUTUUTUUTUUTProcess Model Result ProcessingSchema DefinitionsDatabase LoggerReport GeneratorADO/ODBCThread Object 0Thread Object n Sequence File GlobalsStepsMain Step GroupStepsCleanup Step GroupParametersSequencesLocal VariablesAdapters.VI.DLL, .OBJ, .LIB, .C.DLL .DLL, .EXE .DLL, .EXE.PRG .SEQLabVIEW Adapter LabWindows/CVI Adapter C/C++ DLL Adapter .NET Adapter ActiveX/COM Adapter HTBasic Adapter Sequence AdapterTypesSequence FileParallel Process ModelBatch Process ModelSequential Process ModelProcess Model Sequence File ExecutionTestSocket nExecution Test Socket 1Execution TestSocket 0Execution Oracle . . .SQL ServerReport ObjectExecution ObjectCall StackRootSequenceContextObject 0SequenceContextObject 1SequenceContextObject nStep Object 0Step Object n. . .Current StepMicrosoft Access Process Models. ... ..XMLHTMLASCII-Text. . .Sequence File Execution FlowSequence File ExecutionsYou can execute a sequence directly, or you can execute a sequence file through a process model Execution entry point,such as Test UUTs and Single Pass.Process Model Sequence File ExecutionWhen you start an execution through a process modelExecution entry point, the process model defines how to test the UUTs. The Sequential model tests one UUT at a time. The Parallel model tests multiple independent test sockets at the same time. The Batch model tests a batch of UUTs using dependent test sockets.Process Model Result ProcessingThe TestStand Engine collects the results of each step that executes into a result list. Process models use the result list to generate reports and log data to databases. Unit Under Test (UUT)Device or component that you are testing.Test Socket ExecutionFor each test socket, or fixture, in the system, the Parallel and Batch models launch a separate test socket execution that controls the testing of UUTs in that test socket.Report GeneratorThe report generator traverses test results to create reports in XML, HTML, and ASCII-text formats. You can fully customize the reports.Schema DefinitionsSchema definitions define SQL statements, table definitions,and TestStand expressions that define how to log results to a database. You can fully customize the schemas.Database LoggerThe database logger traverses test results and exports data into database tables using schema definitions.Sequence File StructureSequence FileContains any number of sequences, a set of data types and step types the sequence file uses, and any global variables that sequences in the sequence file share.SequencesContain groups of steps, local variables, and parameters used for passing data between steps and subsequences.TypesSequence files contain definitions of all data types and step types that its sequences use. Variables and properties in a sequence are instances of data types. Steps in a sequence are instances of step types.Sequence File GlobalsStore data you want to access from any sequence or step within the sequence file in which you define the sequence file global variable.Setup, Main, Cleanup Step GroupsTestStand executes the steps in the Setup step group first,the Main step group next, and the Cleanup step group last.By default, a sequence moves to the Cleanup step group when a step generates an error in the Setup or Main step group.Local VariablesStore data relevant to the execution of the sequence. You can access local variables from within steps and code modules defined in a sequence.ParametersUse parameters to exchange data between calling and called sequences.StepsPerform built-in operations or call code modules. A step is an instance of a step type, which defines a set of step properties and default behaviors for each step.373457B-01 Apr07. . .. . .. . .National Instruments, NI, , NI TestStand, and LabVIEW are trademarks of National Instruments Corporation. Refer to the Terms of Use section on /legal for more information aboutNational Instruments trademarks. Other product and company names mentioned herein are trademarks or trade names of their respective companies. For patents covering National Instruments products,refer to the appropriate location: Help»Patents in your software, the patents.txt file on your CD, or /patents .© 2003–2007 National Instruments Corporation. All rights reserved.Printed in Ireland.StepsSetup Step GroupTemplatesFlow Control Sequence Call Statement LabelMessage Popup Call Executable Property Loader FTP FilesSynchronization Steps Database Steps IVI-C Steps LabVIEW UtilityPass/Fail Test Numeric Limit Test Multiple Numeric Limit Test String Value Test Action Built-In Step TypesYou can use the fully customizable TestStand developmentenvironment to create, modify, execute, and debug sequences. You can also use the sequence editor to modify step types and process models. You can customize the environment by docking, auto-hiding, and floating panes to optimize your development tasks. TheDevelopment EnvironmentOVERVIEW CARD NI TestStand TMSystem and ArchitectureTestStand includes separate user interface applications developed in LabVIEW, LabWindows/CVI, Microsoft Visual Basic .NET,C#, and C++ (MFC). Because TestStand includes the source code for each user interface, you can fully customize the userinterfaces. You can also create your own user interface using any programming language that can host ActiveX controls orcontrol ActiveX automation servers. With the user interfaces in operator mode, you can start multiple concurrent executions, set breakpoints, and single-step. In editor mode, you can modify sequences, display sequence variables, sequence parameters,step properties, and so on.TestStand Sequence Editor Overview User Interface OverviewPrinted DocumentationNI TestStand Quick Start GuideUse this document for system requirements andinstallation instructions. This document also contains information about the different TestStand licensing options.NI TestStand Release NotesUse this document to learn about new features and upgrade information.Using TestStandUse this manual to familiarize yourself with the TestStand environment and the basic features you use to build and run test sequences.Using LabVIEW with TestStandUse this manual in conjunction with the Using TestStand manual to learn how to use LabVIEW with ing LabWindows/CVI with TestStandUse this manual in conjunction with the Using TestStand manual to learn how to use LabWindows/CVI with TestStand.NI TestStand Reference ManualUse this manual to learn about TestStand concepts,architecture, and features.Online HelpNI TestStand HelpUse this help file to learn more about the TestStand environment and the TestStand User Interface Controls and Engine APIs. The NI TestStand Help also includes basic information about using an ActiveX automation server.NI TestStand VIs and Functions HelpUse this help file to learn more about TestStand-specific VIs and functions. This help file is accessible only from LabVIEW.Cards and PostersNI TestStand User Interface Controls Reference Poster Use this poster to learn about the controls available for writing custom user interfaces for TestStand.NI TestStand API Reference PosterUse this poster as an overview of the TestStand API. This poster lists the properties, objects, methods, and APIinheritance of the TestStand API.L i s t B a r Lists the currentlyopen sequence files and executions.S e q u e n c e F i l e W i n d o wE x e c u t i o n V i e wR e p o r t V i e wS e q u e n c e V i e wLists steps in the sequence and step group for the sequence file you select in the list bar.Displays the threads,call stack, and steps for the execution you select.Displays the report for the execution you select.Displays sequences and other items in a sequence Displays the threads,call stack, and stepsthat an execution runs.When executioncompletes, displays thereport for theexecution.User Manager WindowAdministers groups, users,login names, pass-words, and privi-leges.UsersDisplays users for the test station. Output Pane Displays output messages that expressions and code modules post to theTestStand Engine.Call Stack Pane Displays the nested sequence invocations for the thread you select.sequence editor provides familiar LabVIEW, LabWindows/CVI, and Microsoft Visual Studio .NET debugging tools, including breakpoints, single-stepping, stepping into or over function calls, tracing, a Variables pane, and a Watch View pane. In the TestStand Sequence Editor, you can start multiple concurrent executions, execute multiple instances of the same sequence, and execute different sequences at the same time. Separate Execution windows display each execution. In trace mode, the Execution window displays the steps in the currently executing sequence. When you suspend an execution, the Execution window displays the next step to execute and provides single-stepping options.Templates List Organizes custom sequences, steps,and variables you can use as templates for building sequence files.Step Settings PaneSpecifies the settings for the step, such as code module parameters, switching, flow control, and post actions.Variables Pane Displays the variables andproperties, including the values, that steps can access at run time.StepPerforms built-in operations or calls code modules.ProjectOrganizes sequence files and code module files in folders.Workspace PaneManages projects for source code control (SCC) integration and deployment. TestStand inte-grates with third-party SCC pack-ages to add files, obtain the lat-est versions of files, and check files in and out.Watch View Pane Monitors the values of specifiedvariables, properties,and expressions during an execution.Threads Pane Contains a list of threads in the current execution.Insertion Palette Displays step types and templates you can insert into sequence files.GroupsDisplays groups that users belong to.。
PF3WB PF3WC PF3WS PF3WR数字流量开关-多功能型说明书
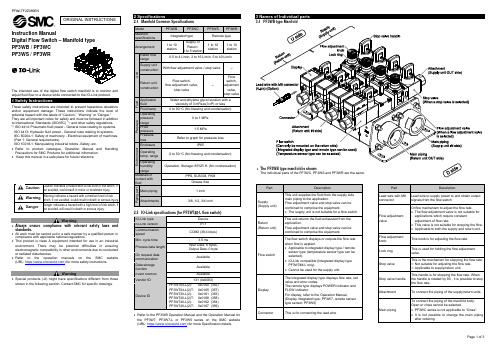
Page 1 of 3Instruction ManualDigital Flow Switch – Manifold type PF3WB / PF3WC PF3WS / PF3WRThe intended use of thedigital flow switch manifoldis to monitor and adjust fluid flow to a device while connected to the IO-Link protocol.These safety instructions are intended to prevent hazardous situations and/or equipment damage. These instructions indicate the level of potential hazard with the labels of “Caution,” “Warning” or “Danger.”They are all important notes for safety and must be followed in addition to International Standards (ISO/IEC) *1), and other safety regulations. *1)ISO 4414: Pneumatic fluid power - General rules relating to systems. ISO 4413: Hydraulic fluid power - General rules relating to systems.IEC 60204-1: Safety of machinery - Electrical equipment of machines. (Part 1: General requirements)ISO 10218-1: Manipulating industrial robots -Safety. etc.• Refer to product catalogue, Operation Manual and Handling Precautions for SMC Products for additional information. • Keep this manual in a safe place for future reference.CautionCaution indicates a hazard with a low level of risk which, ifnot avoided, could result in minor or moderate injury.WarningWarning indicates a hazard with a medium level of riskwhich, if not avoided, could result in death or serious injury.DangerDanger indicates a hazard with a high level of risk which, ifnot avoided, will result in death or serious injury.Warning• Always ensure compliance with relevant safety laws and standards.• All work must be carried out in a safe manner by a qualified person in compliance with applicable national regulations.• This product is class A equipment intended for use in an industrial environment. There may be potential difficulties in ensuring electromagnetic compatibility in other environments due to conducted or radiated disturbances.• Refer to the operation manuals on the SMC website (URL: https:// ) for more safety instructions.Warning• Special products (-X) might have specifications different from those shown in the following section. Contact SMC for specific drawings.2 Specifications2.1 Manifold Common Specifications2.2 IO-Link specifications (for PF3W7##-L flow switch)• Refer to the PF3WB Operation Manual and the Operation Manual for the PF3W7, PF3W7-L or PF3W5 series on the SMC website (URL: https:// ) for more Specification details.3.1 PF3WB type ManifoldPart DescriptionSupply(Supply unit)This unit supplies the fluid from the supply side main piping to the application.Flow adjustment valve and stop valve can be combined to comprise the equipment.• The supply unit is not suitable for a flow switch. Return(Return unit)This unit returns the fluid exhausted from the application.Flow adjustment valve and stop valve can be combined to comprise the equipment.Flow switch The flow switch displays or outputs the flow rate when flow is applied.• Applicable to integrated display type / remote sensor type (temperature sensor type can be selected).• IO-Link compatible (Integrated display type PF3W7##-L only).• Cannot be used for the supply unit.Display The integrated display type displays flow rate, set value and error codes.The remote type displays POWER indicator and FLOW indicator.For display, refer to the Operation Manual.(Display integrated type: PF3W7, remote sensor type sensor: PF3W5)Connector This is for connecting the lead wire.PartDescriptionLead wire with M8 connectorLead wire to supply power to and obtain output signals from the flow switchFlow adjustment valveOrifice mechanism to adjust the flow rate.• The flow adjustment valve is not suitable for applications which require constant adjustment of flow rate.• This valve is not suitable for stopping the flow. • Applicable to both the supply and return unit. Flow adjustment knob This knob is for adjusting the flow rate. Lock ringThis is used for holding the flow adjustment valve.Stop valveThis is the mechanism for stopping the flow rate. ∗: Not suitable for adjusting the flow rate. ∗: Applicable to supply/return unit.Stop valve handleThis handle is for stopping the flow rate. When the handle is rotated by 90°, it is possible to stop the flow rate.AttachmentTo connect the piping of the supply/return units. Main pipingTo connect the piping of the manifold body. Open or close cannot be selected.• PF3WC series is not applicable to “Close”. • It is not possible to change the main piping after ordering.ORIGINAL INSTRUCTIONSModel PF3WBPF3WCPF3WSPF3WRManifold specifications Integrated type Remote type Arrangement 1 to 10 stationSupply or Return: 1 to 5 station1 to 10 station1 to 10 stationU n i t Rated flow range 0.5 to 4 L/min, 2 to 16 L/min, 5 to 40 L/min Supply unit construction With flow adjustment valve / stop valve- Return unit construction Flow switch,flow adjustment valve,stop valve-Flow switch, adjustment valve, stop valveF l u i d Applicable fluid Water and ethylene glycol solution with aviscosity of 3 mPa •s(3 cP) or less Fluid temp. 0 to 90 o C (No freezing and condensation)P r e s s u r e Operating pressure range 0 to 1 MPa Proof pressure 1.5 MPaPressure loss Refer to graph for pressure lossE n v i r o n m e n tEnclosure IP65Operating temp. range 0 to 50 oC (No freezing and condensation)Operating humidity range Operation, Storage: 85%R.H. (No condensation)Materials in contact with fluidPPS, SUS304, FKMGrease free P i p i n g p o r tMain piping 1 inch Attachments 3/8, 1/2, 3/4 inch•The PF3WB type manifold is shown .The individual parts of the PF3WC, PF3WS and PF3WR are the same.4.1 InstallationWarning•Do not install the product unless the safety instructions havebeen read and understood.•Use the product within the specified operating pressure andtemperature range.•Tighten to the specified tightening torque.If the tightening torque is exceeded the mounting screws, brackets andthe product can be broken. Insufficient torque can cause displacementof the product from its correct position.•Do not drop, hit or apply excessive shock to the product.Otherwise damage to the internal parts can result, causing malfunction.•Do not pull the lead wire forcefully, and do not lift the product bypulling the lead wire (tensile force 49 N or less).4.2 EnvironmentWarning•Do not use in an environment where corrosive gases, chemicals, saltwater or steam are present.•Do not use in an explosive atmosphere.•Do not expose to direct sunlight. Use a suitable protective cover.•Do not install in a location subject to vibration or impact in excess ofthe product’s specifications.•Do not mount in a location exposed to radiant heat that would result intemperatures in excess of the product’s specifications.•Do not use the product in places where there are cyclic temperaturechanges.Heat cycles other than ordinary changes in temperature can adverselyaffect the inside of the product.4.3 Mounting•Never mount the product in a location where it will be used as a support.•Mount the product so that the fluid flows in the direction indicated bythe arrow on the product label or on the product body.•Check the flow characteristics data for pressure loss and the straightinlet pipe length effect on accuracy, to determine inlet pipingrequirements.•Do not sharply reduce the piping size.•The monitor with integrated display can be rotated. It can be set at 90ointervals clock and anticlockwise, and also at 45o and 225o clockwise.Rotating the display with excessive force will damage the end stop.•When a stop valve is mounted, rotate the monitor after closing the stopvalve handle.Rotating the monitor with excessive force with the stop valve open, themonitor and stop valve will interfere with each other, causing damage(refer to the figure below).4.4 Direct mounting (PF3W704 / 720 / 740)•When mounting the product, mount it to a panel with screws(equivalent to M6) using the mounting holes provided.•Mounting plate thickness should be approximately 3 mm.•Screws and nuts must be prepared by the user.The PF3WB uses 6 mounting screws, and the PF3WC, PF3WS and4.5 PipingCaution•Before connecting piping make sure to clean up chips, cutting oil, dustetc.•When installing piping or fittings, ensure sealant material does notenter inside the port.•Eliminate any dust left in the piping using an air blow before connectingthe piping to the product.•Ensure there is no leakage after piping.•When connecting piping to the product, hold the piping with a wrenchon the metal part of the piping (piping attachment) and main port of themain piping, which is integrated into the piping.•Using a spanner on other parts may damage the product.In particular, do not let the spanner come into contact with the M8connector. The connector can be easily damaged.After hand tightening, apply a spanner of the correct size to thespanner flats on the product, and tighten it for 2 to 3 rotations, to thetightening torque shown in the table below.If the tightening torque is exceeded, the product can be damaged. Ifthe correct tightening torque is not applied, the fittings may becomeloose.Nominal Thread size Tightening torque Width across flatsRc (NPT) 3/8 15 to 20 N•m 20.9 mmRc (NPT) 1/2 20 to 25 N•m 23.9 mmRc (NPT) 3/4 28 to 30 N•m 29.9 mmRc (NPT) 1 36 to 38 N•m 41.0 mm4.6 WiringCaution•Do not perform wiring while the power is on.•Confirm proper insulation of wiring.Poor insulation (interference from another circuit, poor insulationbetween terminals, etc.) can lead to excess voltage or current beingapplied to the product, causing damage.•Do not route wires and cables together with power or high voltagecables.Otherwise the product can malfunction due to interference of noise andsurge voltage from power and high voltage cables to the signal line.Route the wires (piping) of the product separately from power or highvoltage cables.•Keep wiring as short as possible to prevent interference fromelectromagnetic noise and surge voltage.Do not use a cable longer than 30 m. (IO-Link compatible device: 20m or less).•Ensure that the FG terminal is connected to ground when using acommercially available switch-mode power supply.•When an analogue output is used, install a noise filter (line noise filter,ferrite element, etc.) between the switch-mode power supply and thisproduct.4.7 Connector Wiring5 SettingsRefer to the Operation manuals on the SMC website(URL: https://) for the following Settings:Flow switch Setting and Function setting•Integrated display type: PF3W7•Integrated display type (IO-Link compatible): PF3W7-L•Remote type sensor: PF3W56.1 General MaintenanceCaution•Not following proper maintenance procedures could cause the productto malfunction and lead to equipment damage.•If handled improperly, compressed air can be dangerous.•Maintenance of pneumatic systems should be performed only byqualified personnel.•Before performing maintenance, turn off the power supply and be sureto cut off the supply pressure. Confirm that the air is released toatmosphere.•After installation and maintenance, apply operating pressure andpower to the equipment and perform appropriate functional andleakage tests to make sure the equipment is installed correctly.•If any electrical connections are disturbed during maintenance, ensurethey are reconnected correctly and safety checks are carried out asrequired to ensure continued compliance with applicable nationalregulations.•Do not make any modification to the product.•Do not disassemble the product, unless required by installation ormaintenance instructions.•How to reset the product after a power cut or when the power hasbeen unexpectedly removedWhen the flow switch is the integrated display type, the settings of theproduct are retained from before the power cut or de-energizing.The output condition also recovers to that before the power cut or de-energizing, but may change depending on the operating environment.Therefore, check the safety of the whole system before operating theproduct.7 Troubleshooting7.1 Error indication (PF3W7 Integrated display type)When using PF3W7 integrated display or PF3W5 remote sensorWhen PF3W7-L (IO-Link) is used in SIO modeNo. Name Wire colour Function1 DC(+) Brown 12 to 24 VDC2 N.C./ OUT2 White N.C. / Switch output 2 (SIO)3 DC(-) Blue 0 V4 OUT1 Black Switch output 1 (SIO)When PF3W7-L (IO-Link) is used as IO-Link deviceNo. Name Wire colour Function1 L+ Brown 18 to 30 VDC2 N.C./ OUT2 White N.C. / Switch output 2 (SIO)3 L-Blue 0 V4 C/Q BlackIO-Link data /Switch output 1 (SIO)∗: Wire colours are for the lead wire included with the PF3W7 series.Page 3 of 37.2 Error indication (PF3W5 Remote sensor type) If the error cannot be reset after the above measures are taken, or errors other than the above are displayed, please contact SMC.Refer to the Operation manual on the SMC website (URL: https:// ) for more detailed information about Troubleshooting.8 How to OrderRefer to the operation manual or catalogue on the SMC website (URL: https:// ) for How to order information.9 Outline Dimensions (mm)Refer to the Operation manual on the SMC website (URL: https:// ) for outline and mounting dimensions for the PF3WB, PF3WC, PF3WS and PF3WR.10.1 Limited warranty and Disclaimer/Compliance Requirements Refer to Handling Precautions for SMC Products.11 Product disposalThis product should not be disposed of as municipal waste. Check your local regulations and guidelines to dispose of this product correctly, in order to reduce the impact on human health and the environment.12 ContactsRefer to or www.smc.eu for your local distributor / importer.URL: https:// (Global) https:// (Europe) SMC Corporation, 4-14-1, Sotokanda, Chiyoda-ku, Tokyo 101-0021, Japan Specifications are subject to change without prior notice from the manufacturer. © 2021 SMC Corporation All Rights Reserved. Template DKP50047-F-085M。
工作流管理系统FlowStep的

增加支持的任务类型
原有的六种任务类型(Script,Query , Or,Call,Condition,Input) 增加And,Nothing,Show,Insert, Delete,Update类型任务 开发相应的And,Nothing,Show ,Insert, Delete,Update类型工作流引擎
工作流管理系统的主要产品
IBM的工作流产品 Flowmark 的应用 IBM 的 MQSeries WorkFlow Action Technologies 公司的 Metro FileNet 公司的 Visual WorkFlo JetForm 公司的 InTempo
目前的工作基础
已经完成的部分
企业经营过程定义
“一个经营过程是为了实现企业某个经营目标 的一个过程,它在部分或者全部组织机构和人 员的参与下,利用企业资源(包括所需的处理 设备、通信设备、计算机硬件、软件等等), 按照预先确定的规则,在参与者和组织机构之 间进行文档、信息、任务的传递和处理(包括 经营决策),从而实现预定的经营目标。”
企业经营过程描述
这个经营过程要做什么?即其目的或想 达到的目标是什么? 这个经营过程是如何完成的,有那些任 务并经过那些步骤完成? 这个经营过程有谁参与完成,有那些部 门参与?(人) 这个经营过程用了那些方式或手段来完 成?(物)
工作流的基本概念
工作流是一类能够完全或者部分自动执 行的经营过程,它根据一系列过程规则, 文档、信息或任务能够在不同的执行者 之间进行传递与执行。 在实际情况中可以更广泛地把凡是由计 算机软件系统(工作流管理系统)控制 其执行的过程都称为工作流。
FlowStep外部逻辑 FlowStep外部逻辑
为企业自主开发任务提供接口 属于一类特殊任务(Custom),由专门 的引擎解释执行 支持分布式 与任务模块无关
Think-in-OD

objective – The more labor , the quicker responder
theory is very important !
Avaya – Proprietary. Use pursuant to your signed agreement or Avaya policy.
7
Voice Browser vs. Internet Browser
VoiceXML/ CCXML browsers
AMS/MPP
Voice Browser
Web Server
<xml> <root> </root>
</xml>
VXML Files
Internet Explorer
Avaya – Proprietary. Use pursuant to your signed agreement or Avaya policy.
Experience Portal
applications
Call Flow
Prompt
Connectors
Grammar
Navigator
Outline
Avaya – Proprietary. Use pursuant to your signed agreement or Avaya policy.
Customer
Avaya – Proprietary. Use pursuant to your signed agreement or Avaya policy.
卡梅伦液压数据手册(第 20 版)说明书
iv
⌂
CONTENTS OF SECTION 1
☰ Hydraulics
⌂ Cameron Hydraulic Data ☰
Introduction. . . . . . . . . . . . . ................................................................ 1-3 Liquids. . . . . . . . . . . . . . . . . . . ...................................... .......................... 1-3
4
Viscosity etc.
Steam data....................................................................................................................................................................................... 6
1 Liquid Flow.............................................................................. 1-4
Viscosity. . . . . . . . . . . . . . . . . ...................................... .......................... 1-5 Pumping. . . . . . . . . . . . . . . . . ...................................... .......................... 1-6 Volume-System Head Calculations-Suction Head. ........................... 1-6, 1-7 Suction Lift-Total Discharge Head-Velocity Head............................. 1-7, 1-8 Total Sys. Head-Pump Head-Pressure-Spec. Gravity. ...................... 1-9, 1-10 Net Positive Suction Head. .......................................................... 1-11 NPSH-Suction Head-Life; Examples:....................... ............... 1-11 to 1-16 NPSH-Hydrocarbon Corrections.................................................... 1-16 NPSH-Reciprocating Pumps. ....................................................... 1-17 Acceleration Head-Reciprocating Pumps. ........................................ 1-18 Entrance Losses-Specific Speed. .................................................. 1-19 Specific Speed-Impeller. .................................... ........................ 1-19 Specific Speed-Suction...................................... ................. 1-20, 1-21 Submergence.. . . . . . . . . ....................................... ................. 1-21, 1-22 Intake Design-Vertical Wet Pit Pumps....................................... 1-22, 1-27 Work Performed in Pumping. ............................... ........................ 1-27 Temperature Rise. . . . . . . ...................................... ........................ 1-28 Characteristic Curves. . ...................................... ........................ 1-29 Affinity Laws-Stepping Curves. ..................................................... 1-30 System Curves.. . . . . . . . ....................................... ........................ 1-31 Parallel and Series Operation. .............................. ................. 1-32, 1-33 Water Hammer. . . . . . . . . . ...................................... ........................ 1-34 Reciprocating Pumps-Performance. ............................................... 1-35 Recip. Pumps-Pulsation Analysis & System Piping...................... 1-36 to 1-45 Pump Drivers-Speed Torque Curves. ....................................... 1-45, 1-46 Engine Drivers-Impeller Profiles. ................................................... 1-47 Hydraulic Institute Charts.................................... ............... 1-48 to 1-52 Bibliography.. . . . . . . . . . . . ...................................... ........................ 1-53
曼斯特拉姆多口值阀用户手册说明书

RMULTI-PORT VALVE USER MANUALFor CMP# 27518-204-000FILTER PUMP►TOP►THROUGH FILTER ►BOTTOM►POOL RETURN For normal filter action and vacuuming pool through filter.BACKWASH PUMP►BOTTOM►THROUGH FILTER►TOP►WASTE For cleaning filter by reversing flow.RINSE PUMP►TOP►THROUGH FILTER►BOTTOM►WASTEFor start-up cleaning and resetting filter bed after backwashing.WASTE PUMP►WASTEFor vacuuming directly to waste, lowering pool level or draining pool.CLOSED NO FLOW. DO NOT USE WHEN PUMP IS IN OPERATION For shutting off all flow to filter and pool.RECIRCULATEPUMP►POOL RETURNFor circulating water without going through filter.Valve Setting Water Flow Path ; Setting FunctionPRODUCT INFORMATIONThis multi-port valve is a replacement for Hayward SP071621 Vari-Flo Control Valve and it is used for Hayward Pro-Series Sand Filters such as S220T/T2, S244T/T2, S270T/T2, S310T2 and S360T2. It features an easy-to-use lever action handle that lets you dial up to six valve/filter functions- filter, backwash, waste, rinse, closed, or recirculate. Theports are 2” FPT fittings.*Hayward is a registered trademark of Hayward IndustriesINSTALLATION & SERVICE INSTRUCTIONS• Confirm correct valve is being used for your filter type and model.• To install valve to filter, clamp valve on top of filter and connect pump, return, and waste lines by following the markings of the ports. Use Teflon pipe tape to connect pipe fittings. DO NOT OVER TIGHTEN PIPE FITTINGS.• VALVE TOP IS UNDER SPRING LOAD. To open top half and service valve, evenly and alternately loosen cover screws.• To disassemble valve and replace parts, set handle in the position between any two settings. Tap out handle pin and remove cover screws.• To re-assemble the top half, ensure bottom gasket and diverter sealing surface are clean. Place diverter on a smooth and firm surface. Assemble parts on shaft by following Figure A.Make sure the pointer on handle and the arrow on diverter point to same direction. Press down the cover using clamps by depressing heavy-duty spring and secure handle with pin.• To re-assemble the top half to valve bottom, tighten cover screws evenly and alternately. DO NOT OVERTIGHTEN THE SCREWS.• WINTERIZATION: To winterize, drain the pump and filter per manufacturer’s instructions. Press down on the valve handle and rotate to a position that is between any two settings.1Handle 12Dowel Pin13Plastic Washer 14Top Cover15Top Cover O-ring 16Spring Washer 17Heavy Duty Spring 18Diverter Washer 19Diverter O-ring 110Diverter 1Item QTY Item Description Figure A: Top Half Assy Components0313 sbFor the full list of replacement parts of this unit, please check our catalog or our website at .CUSTOM MOLDED PRODUCTS, INC | 800-733-9060 | NEWNAN, GEORGIA 30265 | Complete Top Half Assy 27518-204-100(includes 1-10)。
金融术语中英对照(附中文释义)

金融术语中英对照(附中文释义)American Style Option:美式选择权自选择权契约成立之日起,至到期日之前,买方可以在此期间以事先约定的价格,随时要求选择权的卖方履行契约。
亦即,要求选择权的卖方依契约条件买入或卖出交易标的物。
Appreciation: 升值在外汇市场中,升值使指一个货币相对于另一个货币的价值增加。
Arbitrage: 套利在金融市场从事交易时,利用市场的失衡状况来进行交易,以获取利润的操作方式。
其主要操作方法有两种:一为利用同一产品,在不同市场的价格差异;一为利用在同一市场中各种产品的价格差异来操作。
不论是采用何种方法来进行套利交易,其产品或市场的风险程度必须是相等的。
Asset Allocation: 资产分配原则基于风险分散原则,资金经理在评估其资金需求,经营绩效与风险程度之后,将所持有的资产分散投资于各类型的金融产品中。
如股票、外汇、债券、贵金属、房地产、放款、定存等项,以求得收益与风险均衡的最适当资产组合(Optimum Assets Components).Asset/Liability Management(ALM): 资产负债管理由于金融机构的资产为各种放款及投资,而负债主要为各种存款,费用收入、或投资人委托之资金。
因此资产负债管理的目的,即在于使银行以有限的资金,在兼顾安全性(Safty)、流动性(Liquidity)、获利性(Profitability)及分散性(Diversification)的情况下,进行最适当的资产与负债的分配(Asset Allocation)。
At The Money: 评价选择权交易中,履行价格等于远期价格时称之为评价。
Bear Market: 空头市场(熊市)在金融市场中,若投资人认为交易标的物价格会下降,便会进行卖出该交易标的物的操作策略。
因交易者在卖出补回前,其手中并未持有任何交易标的物,故称为:“空头”。
所谓空头市场就是代表大部分的市场参与者皆不看好后市的一种市场状态。
LTE Call Flow_解读

Step 18-20
Step 18. The eNodeB sends the RRC Connection Reconfiguration message including the EPS Radio Bearer Identity to the UE, Attach Accept message will be sent along to UE. Step 19. The UE sends the RRC Connection Reconfiguration Complete message to the eNodeB. Step 20. The eNodeB sends the Initial Context Response messageep1. UE initiates attach procedure by transmitting an attach request to eNodeB. Step 2. eNodeB derives MME from RRC parameters carrying old GUMMEI & indicated Selected Network. Step 3. If UE identifies itself with GUTI and MME changed since detach, MME uses the GUTI received from UE to derive the old MME/SGSN Address & send request to old MME/SGSN for IMSI.
LTE Call FLow
LTE Call Flow
Concept
UE: User Equipment, like mobile handsets eNB: Evolved Node B, the hardware connected to the mobile phone network MME: Mobility Management Entity SGW: Serving Gateway, routes and forwards user data packets PGW: Packet Date Network Gateway, provides connectivity from the UE to external packet data networks by being the point of exit and entry of traffic for the UE HSS: Home Subscriber Server
Platform2配置说明_V1.0

Platform2框架开发配置说明Service定义说明<services><part-define/> ......全局部件定义(用于全局引用)<group-define/> ......全局部件组定义(用于全局引用)<service> ......服务定义,id属性即为功能码<part-define/> ......局部部件定义(用于本服务引用)<group-define/> ...... 局部部件组定义(用于本服务引用)<flowId/> ......产生执行序列的元素id,根据此id分发流程<flow> ......某一流程的定义<part/> ......执行部件<ref/> ......对“执行部件定义”、“执行部件组定义”的引用<condition/>......条件执行序列<call/> ......子服务调用</flow></service></services>Platform2框架中元素间的关系【元素】【包含】<services/> 0...n个<part-define/>0...n个<group-define/>0...n个<service/><part-define/> 0...n个<param/><group-define/> 0...n个<part/>0...n个<ref/>0...n个<condition/>0...n个<call/>part/ref/condition至少要有一个<service/> 0...n个<part-define/>0...n个<group-define/>1个<flowId/>1...n个<flow/><flowId/> 无<flow/> 0...n个<part/>0...n个<ref/>0...n个<condition/>0...n个<call/><condition/>0...n个<part/>0...n个<ref/>0...n个<condition/>0...n个<call/>part/ref/condition至少要有一个<call/> 无<part/> 0...n个<param/><param/> 无<ref/> 无Platform2框架中元素的属性<services/> 无<part-define/> name(必)/class(必)/desc(非必,默认=null)<group-define/> id(必)<service/> id(必)/open(非必,默认=true) 【约束:id由英文字母大小写、数字、下划线组成,且大小写不敏感】<part/> name(必)/class(必)/desc(非必,默认=null)<param/> name(必)/value(必)<ref/> name(非必,默认=被引用对象的name属性)/ref(必)<condition/> id(必)/cond(非必,默认=null)/class(非必,实现Cond接口,默认=null)【约束:cond与class不能同时配置且必选一,class需要实现com.umpay.platform2.service.cond.Cond接口】<call/> id(必)【约束:id是存在的service元素的id】<flow/> id(必)/open(非必,默认=true)/accessTypes(非必,默认=所有接入方式)<flowId/> depends(非必,默认=null)/separator(非必,默认=,)/class(非必,默认=null)/desc(非必,默认=null)【约束:depends与class不能同时配置且必选一;当depends 配置了才能配置separator;class需要实现com.umpay.platform2.service.ID接口】关于ref的使用说明概念本地-- <service/> 的孩子元素被称为“service服务的本地元素”,简称“本地”,亦称“局部”全局-- <services/>的孩子元素被称为“service服务的全局元素”,简称“全局”使用说明<ref/>元素引用的元素有两种:<part-define/>和<group-define/><part-define/>分“本地部件定义(localPartDef)”、“全局部件定义(globalPartDef)”两种。
2G3G Call flow&location update

"Location Update" for "Upgraded Sub" in "UMTS Coverage“
"Location Update" for "New Sub" in "GSM Coverage“ "Location Update" for "New Sub" in "UMTS Coverage“
"Incoming Call" for "Upgraded Sub" in "GSM Coverage“
"Incoming Call" for "Upgrader Sub" in "UMTS Coverage“ "Incoming Call" for "New Sub" in "GSM Coverage“ "Incoming Call" for "New Sub" in "UMTS Coverage“ "Outgoing Call" for "Upgraded Sub" in "GSM Coverage“ "Outgoing Call" for "Upgarded Sub" in "UMTS Coverage“ "Outgoing Call" for "New Sub" in "GSM Coverage" "Outgoing Call" for "New Sub" in "UMTS Covera
DeviceMaster Nserial Device Driver for eCos说明书

DeviceMaster® Nserial Device DriverThis document describes the nserial device driver for eCos. The driver provides a high-level API that user applications can use to access the DeviceMaster serial ports.The nserial driver is based on the eCos 1.3.1 serial driver. The following enhancements have been made to the 1.3.1 serial driver:•Non-blocking read/write•Semi-blocking read•Modem control/status line support•Error count query•Buffer status query•Arbitrary baud rate•Flow control enhancementsIf you are unfamiliar with the eCos I/O device API, see the eCos Reference Manual, Part IV: I/O Package (Device Drivers).nserial APIThe nserial API consists of the five standard eCos system calls:•cyg_io_lookup()•cyg_io_read()•cyg_io_write()•cyg_io_get_config()•cyg_io_set_config()If you are unfamiliar with these calls please see the "User API" section of the eCos Reference Manual, Part IV: I/O Package (Device Drivers).cyg_io_lookup()The device names supported by the nserial driver are "/dev/ser0" through "/dev/ser31" (assuming a 32-port device).cyg_io_read()Reads may be blocking, non-blocking, or semi-blocking.blocking The default state for a serial port is blocking reads. If N bytes are requested in the call to cyg_io_read(), the call will not return until N bytes have been transfered to the user’sbuffer. The call will wait indefinitely for the requested number of bytes.non-blocking The call to cyg_io_read() will return immediately. If less than the requested number of bytes is available, the returned length will reflect the number of bytes actually transferred,and the status will return -EAGAIN.semi-blocking The call to cyg_io_read() will return as soon as some data has been transferred. If no data is available, it will block indefinitely until at least one byte of data is available. If less thanthe requested number of bytes is read, the returned length will reflect the number of bytesactually transferred, and the status will return -EAGAIN.The low-level UART driver in the 4/8/16/32 port DeviceMaster transfers data every 10ms, soa loop containing a semi-blocking cyg_io_read() call will execute once every 10ms whiledata is being received, and block indefinitely if no data is being received.Other UART drivers may transfer data based on a FIFO full trigger rather than on a fixedtime period. For example a loop containing a semi-blocking cyg_io_read() call mightexecute once for every 64 receive bytes.cyg_io_write()Writes may be blocking or non-blocking. There is no semi-blocking mode for write operations.Blocking The call to cyg_io_write() will return as soon as all requested data has been transferred to the transmit buffer.If there is insufficient room in the buffer, the call will block indefinitely until room becomesavailable.non-blocking The call to cyg_io_write() will return immediately. If there was insufficient room in the transmit buffer for the requested number of bytes, the length will reflect the actual numberof bytes transferred, and the status will return -EAGAIN.cyg_io_get_config()The following keys are supported for the cyg_io_get_config() call:CYG_IO_GET_CONFIG_SERIAL_INFOGets the current configuration of the serial port. The structure in which data is returned is: typedef struct {cyg_serial_baud_rate_t baud;cyg_serial_stop_bits_t stop;cyg_serial_parity_t parity;cyg_serial_word_length_t word_length;cyg_uint32 flags;cyg_uint8 rxflow_xon_char;cyg_uint8 rxflow_xoff_char;cyg_uint8 txflow_xon_char;cyg_uint8 txflow_xoff_char;cyg_uint8 interface_mode;cyg_uint32 read_timeout;cyg_uint32 write_timeout;cyg_uint32 inter_char_timeout;cyg_serial_modem_callback_t *modem_callback;void *modem_callback_data;cyg_serial_rx_callback_t *rx_callback;void *rx_callback_data;cyg_uint8 eol1;cyg_uint8 eol2;} cyg_serial_info_t;The fields are defined as follows:baud The current baud rate. This might be one of the enumerated constant values defined in serialio.h such as CYGNUM_SERIAL_BAUD_9600 or it may be the actual baud rate(e.g. the integer value 9600).If the numerical value is less than 50, it is assumed to be an enum constant. If it is 50or larger, it is assumed to be the actual baud rate.stop One of the enumerated constant values defined in serialio.h:CYGNUM_SERIAL_STOP_1CYGNUM_SERIAL_STOP_1_5CYGNUM_SERIAL_STOP_2parity One of the enumerated constant values defined in serialio.h:CYGNUM_SERIAL_PARITY_NONECYGNUM_SERIAL_PARITY_EVENCYGNUM_SERIAL_PARITY_ODDCYGNUM_SERIAL_PARITY_MARKCYGNUM_SERIAL_PARITY_SPACENote:Not all UART types support mark and space parity. The DeviceMaster 4/8/16/32-port hardware only supports none/even/odd.word_length One of the enumerated constant values defined in serialio.h:CYGNUM_SERIAL_WORD_LENGTH_5CYGNUM_SERIAL_WORD_LENGTH_6CYGNUM_SERIAL_WORD_LENGTH_7CYGNUM_SERIAL_WORD_LENGTH_8Note:Not all UART types support 5 and 6 bit word lengths. The DeviceMaster 4/8/16/32-port hardware only supports 7 and 8 bit word lengths.flags Bit map of binary option flags:CYG_SERIAL_FLAGS_RTSCTS enables RTS/CTS hardware flow control. Equivalentto setting both of RTS_RX_FLOW and CTS_TXFLOW.CYG_SERIAL_FLAGS_RTS_RXFLOWEnables hardware RTS flow control for transmitter.CYG_SERIAL_FLAGS_CTS_TXFLOWEnables hardware CTS flow control for receiver.CYG_SERIAL_FLAGS_XONXOFF_RXFLOWEnables Xon/Xoff flow control of receive data stream.CYG_SERIAL_FLAGS_XONXOFF_TXFLOWEnables Xon/Xoff flow control of transmit data stream.CYG_SERIAL_FLAGS_RTS_TOGGLEEnables automatic control of RTS for half-duplex communications. RTS is asserted whiledata is being transmitted and de-asserted when no data is being transmitted. This modeshould be enabled when using the port in RS-485 mode or when using an external half-duplex RS-232 device such as a Bell-202 modem or an RS-232/485 converter.CYG_SERIAL_FLAGS_EN_LOOPBACKEnables hardware loopback of transmit data to receive data.CYG_SERIAL_FLAGS_IGN_NULLSCauses null receive bytes to be discarded.CYG_SERIAL_FLAGS_RD_NONBLOCKenables non-blocking read mode.CYG_SERIAL_FLAGS_RD_SEMIBLOCKEnables semi-blocking read mode.CYG_SERIAL_FLAGS_WR_NONBLOCKEnables non-blocking write mode.rxflow_xoff_char The character transmitted when the receive buffer is nearly full and the driver wishes the remote device to stop sending.rxflow_xon_char The character transmitted when the receive buffer empties and an Xoff haspreviously been sent to stop the remote device from sending.txflow_xoff_char Receipt of this character will cause the driver to stop sending data until the Xon character is received.txflow_xon_char Receipt of this character will cause the driver to resume sending data.interface mode#define RS232_MODE 0x00#define RS422_MODE 0x08#define RS485_MODE 0x10CYG_IO_GET_CONFIG_SERIAL_OUTPUT_DRAINBlocks until all buffered write data has been sent.CYG_IO_GET_CONFIG_SERIAL_INPUT_FLUSHDiscards all buffered but unread receive data.CYG_IO_GET_CONFIG_SERIAL_OUTPUT_FLUSHDiscards all buffered but unsent write data.CYG_IO_GET_CONFIG_SERIAL_ABORTTBDCYG_IO_GET_CONFIG_SERIAL_TX_STOPStop sending data, but do not discard buffered write data.CYG_IO_GET_CONFIG_SERIAL_TX_STARTStart sending buffered write data.CYG_IO_GET_CONFIG_SERIAL_BUFFER_INFOGets the current status of the read and write buffers. The structure in which data is returned is: typedef struct {cyg_int32 rx_bufsize;cyg_int32 rx_count;cyg_int32 tx_bufsize;cyg_int32 tx_count;} cyg_serial_buf_info_t;These values do not include any data buffered in the UART. Only data immediately accessible tocyg_io_read() and buffer space immediately usable by cyg_io_write() is reported.CYG_IO_GET_CONFIG_SERIAL_MODEMGets the current state of the modem control and status lines. Data is returned as an unsigned int bitmap with masks defined in serialio.h:CYG_SERIAL_MODEM_CTSCYG_SERIAL_MODEM_DSRCYG_SERIAL_MODEM_RICYG_SERIAL_MODEM_CDCYG_SERIAL_MODEM_CTS_DELTACYG_SERIAL_MODEM_DSR_DELTACYG_SERIAL_MODEM_RI_DELTACYG_SERIAL_MODEM_CD_DELTACYG_SERIAL_MODEM_DTRCYG_SERIAL_MODEM_RTSCYG_SERIAL_MODEM_FLOWTXOFFCYG_IO_GET_CONFIG_SERIAL_ERRORSGets the count of various types of serial errors. The structure in which data is returned is: typedef struct {unsigned rxOverflow;unsigned rxParity;unsigned rxFraming;unsigned rxBreak;unsigned fifo;} cyg_serial_error_count_t;CYG_IO_GET_CONFIG_SERIAL_CLRERRSResets the error counts to zero.CYG_IO_GET_CONFIG_SERIAL_BREAKONEnables the "send break" feature of the UART. This will cause a space to be sent continuously until the BREAKOFF key is invoked.CYG_IO_GET_CONFIG_SERIAL_BREAKOFFDisables the "send break" feature of the UART. This returns the UART to normal data transmission mode.CYG_IO_GET_CONFIG_TX_OVERRIDEClears any xoff condition that may have been set by receipt of an Xoff character while Xon/Xoff transmit flow control is enabled.cyg_io_set_config()The following keys are supported for the cyg_io_set_config() call:•CYG_IO_SET_CONFIG_SERIAL_INFO•CYG_IO_SET_CONFIG_SERIAL_WRITE_PRIORITY_BYTE•CYG_IO_SET_CONFIG_SERIAL_MODEMExample ProgramThe following example program uses the nserial driver API to echo received data on all 16 ports of a DeviceMaster 16-port platform.#include <cyg/kernel/kapi.h>#include <cyg/error/codes.h>io.h and serialio.h declare the nserial driver API:#include <cyg/io/io.h>#include <cyg/io/serialio.h>#include <stdio.h>#include <stdlib.h>The nserial driver does _not_ know about the selectible hardware interface feature of the DeviceMaster. That is handled below:// macros to set hardware interface type#define InterfaceSelect232 (0<<3)#define InterfaceSelect422 (1<<3)#define InterfaceSelect485 (2<<3)#define InterfaceSelect232i (3<<3)(Use 232i mode when you want to use the RTS toggle feature with an RS-232 interface.)The following is used to insure that output from different calls to diag_printf_m() don’t get interlaced in the diag UART output data stream. The diag_printf() function is a very low level, busy-wait, non-buffered, non-atomic output routine:// Stuff to implement atomic diagnostic message output// printf routine that prints messages to KS32C5000 UARTextern void diag_printf(const char *fmt, ...);// atomic diag_printf operation -- only use in running tasks,// not in initialization code, DSR or ISR code.#define UseDiagPrintfMutex 1#if UseDiagPrintfMutexstatic cyg_mutex_t dpMutex;#define diag_printf_m(fmt, args...) \do { \cyg_mutex_lock(&dpMutex); \diag_printf(fmt, ##args); \cyg_mutex_unlock(&dpMutex); \} while (0)#define diag_init() cyg_mutex_init(&dpMutex)#define diag_lock() cyg_mutex_lock(&dpMutex)#define diag_unlock() cyg_mutex_unlock(&dpMutex)#else#define diag_printf_m(fmt, args...) diag_printf(fmt, ##args)#define diag_init() /* noop */#define diag_lock() /* noop */#define diag_unlock() /* noop */#endiftypedef unsigned char tStack[4096];#define NumPorts 16We use one thread per serial port plus an additional "background" thread that reports statistics. Each thread needs a stack, a thread object, and a thread handle:cyg_thread echoThread[NumPorts], backgroundThread;tStack echoStack[NumPorts], backgroundStack;cyg_handle_t echoHandle[NumPorts], backgroundHandle;cyg_thread_entry_t echoTask, backgroundTask;// Here is where user execution startsvoid cyg_user_start(void){int i;diag_printf("Entering cyg_user_start() function\n");diag_init();For each of the serial ports, create and initialize a thread whose entry point is the "echoTask" function:for (i=0; i<NumPorts; ++i){setInterfaceType(i,InterfaceSelect232);cyg_thread_create(4, echoTask, i,"echo thread", echoStack[i], sizeof echoStack[i],&echoHandle[i],&echoThread[i]);cyg_thread_resume(echoHandle[i]);}Create and initialize the background thread:cyg_thread_create(5, backgroundTask, (cyg_addrword_t) -1,"background thread", backgroundStack, sizeof backgroundStack,&backgroundHandle,&backgroundThread);cyg_thread_resume(backgroundHandle);// returning from this function starts scheduler}void done(void){for (;;);}/* per-port count of bytes echoed */unsigned totalBytes[NumPorts];/* this is a simple thread that echos data on a serial port */void echoTask(cyg_addrword_t data){unsigned char buf[512];int portNum = (int)data;cyg_uint32 len;Cyg_ErrNo status;cyg_io_handle_t ioHandle;cyg_serial_info_t serConfig;char devName[32];diag_printf_m("%d: Beginning execution\n",portNum);The nserial device names are "/dev/ser0" through "/dev/ser15". The "data" parameter to the echoTask tells us which port to handle.sprintf(devName,"/dev/ser%d",portNum);status = cyg_io_lookup(devName, &ioHandle);if (status != ENOERR){diag_printf_m("%d: ERROR, cyg_io_lookup returned %d:%s\n",portNum,status,strerror(status));done();}Use cyg_io_get_config() to read the current serial port configuration structure:len = sizeof serConfig;status = cyg_io_get_config(ioHandle, CYG_IO_GET_CONFIG_SERIAL_INFO, &serConfig, &len);if (status != ENOERR){diag_printf_m("%d: ERROR, cyg_io_get_config returned %d:%s\n",portNum,status,strerror(status));done();}Modify the port config structure to reflect the confguration we want: 38400,8,n,1 with no flow control:serConfig.flags &= ~CYG_SERIAL_FLAGS_RTSCTS;serConfig.flags &= ~CYG_SERIAL_FLAGS_XONXOFF_RXFLOW;serConfig.flags &= ~CYG_SERIAL_FLAGS_XONXOFF_TXFLOW;serConfig.flags = CYG_SERIAL_FLAGS_RD_SEMIBLOCK;serConfig.baud = 38400;serConfig.stop = CYGNUM_SERIAL_STOP_1;serConfig.parity = CYGNUM_SERIAL_PARITY_NONE;serConfig.word_length = CYGNUM_SERIAL_WORD_LENGTH_8;serConfig.interface_mode = InterfaceSelect232;Use cyg_io_set_config() to "write" the configuration back to the serial port:len = sizeof serConfig;status = cyg_io_set_config(ioHandle, CYG_IO_SET_CONFIG_SERIAL_INFO,&serConfig, &len);if (status != ENOERR){diag_printf_m("%d: ERROR, cyg_io_get_config returned %d:%s\n",portNum,status,strerror(status));done();}Now just sit in a loop waiting for data to arrive and writing it back out when it does. We’ve placed the port in semi-blocking read mode, so calls to cyg_io_read() won’t return until we’ve got data, but it won’t wait for our buffer to be full, so remember to check the returned read length:for (;;){len = sizeof buf;status = cyg_io_read(ioHandle, buf, &len);// diag_printf_m("%d[%d]\n",portNum,len);// semi-blocking read shouldn’t return with len of 0,// but let’s check just the sameif (len == 0)continue;totalBytes[data] += len;if (status != ENOERR && status != -EAGAIN){diag_printf("%d: ERROR, cyg_io_read returned %d:%s\n",portNum,status,strerror(status));done();}status = cyg_io_write(ioHandle, buf, &len);if (status != ENOERR){diag_printf("%d: ERROR, cyg_io_write returned %d:%s\n",portNum,status,strerror(status));done();}}}Background task prints out status message once per second that contains the total bytes echoed on each port and the number of idle-loops/sec reported by eCos (a rough measure of CPU utilization):// idle thread loop count provided by eCosextern volatile unsigned idle_thread_loops;void backgroundTask(cyg_addrword_t data){int i;unsigned lastIdleThreadLoops, thisIdleThreadLoops;lastIdleThreadLoops = idle_thread_loops;while (1){cyg_thread_delay(100); // 1 secondthisIdleThreadLoops = idle_thread_loops;diag_lock();diag_printf("Bytes transfered: ");for (i=0; i<NumPorts; ++i)diag_printf("%d ",totalBytes[i]);diag_printf(" -- Idle Loops/Sec:%d\n",thisIdleThreadLoops - lastIdleThreadLoops);diag_unlock();lastIdleThreadLoops = thisIdleThreadLoops;}}Trademark NoticesComtrol and DeviceMaster are trademarks of Comtrol Corporation. Other product names mentioned herein may be trademarks and/or registered trademarks of their respective owners.Second Edition, June 25, 2004Copyright © 2001 - 2004. Comtrol Corporation.All Rights Reserved.Comtrol Corporation makes no representations or warranties with regard to the contents of this document or to the suitability of the Comtrol product for any particular purpose. Specifications subject to change without notice. Some software or features may not be available at the time of publication. Contact your reseller for current product information.Document Number: 2000241 Rev. B。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
MS Terminated Call Procedure Continue 6 (Mobile Release First) MS Um BTS Abis BSC A MSC
E
GMSC
PSTN
CC(FACCH)
DISCONNECT DATA IND <DISC> DISCONNECT(DT1) DTAP-CC CBK(TUP)
MS
Um interface
BTS
Abis interface
BSC
A interface MSC
B interface VLR
RR(RACH)
Channel Request T3120 + Channel Required
Channel Activation
Channel Activation ACK
BSSMAP
Paging
MS Terminated Call Procedure Continue 2 Um interface MS BTS Abis interface BSC A interface MSC B interface VLR
MAP_PROCESS_ACCESS_REQ
MAP_AUTHENTICATE AUTH REQUEST (DT1) DATA REQ<AUTH> AUTH REQUEST (CKSN, RAND) T3260 +
RR(AGCH) T3120 -
Paging RESP (L2-SABM)
RR(SDCCH)
EST IND(Paging Resp) T3101 L2 - UA Paging Resp CR(COMPL - L3 - INFO) (CKSN,MS ID,CGI,CLrk2) CC T3113 -
RR(SDCCH)
Um interface MS BTS
ALERTING
Abis interface BSC
A interface
E interface MSC GMSC
PSTN
CC(FACCH)
DATA IND <ALERT> ALERTING (DT1) T310 T301 + DTAP-CC ACM(TUP)
CC(FACCH)
DTAP-MM
MAP_AUTHENTICATE ACK
MAP_SET_CIPHERING_MODE CIPHER MOD CMD(DT1) ENCR CMD
BSSMAP
(algo nb,key)
RR(SDCCH)
CIPHER MOD CMD
RR(SDCCH)
CIPHER MOD COM DATA IND <CIPH MOD COM> CIPHER MOD COM(DT1)
MS
Um
BTS
MSC
E
GMSC
CLF(TUP)
PSTN
CLF(TUP)
DISCONNECT(DT1) DATA REQ <DISC> T305 + DTAP-CC
CC(FACCH)
DISCONNECT
CC(FACCH)
RELEASE DATA IND <REL> RELEASE(DT1) T305 DTAP-CC RLG(TUP)
RR(FACCH)
RR(FACCH)
(L2 - UA)
REL IND T3109 T3111 + RF CHAN REL T3111 RF CHAN REL ACK <RLSD> <RLC> CLEAR COM(DT1) TNT3 -
BSSMAP
Radio-resource release
Mobile - Originating Call Procedure
BSSMAP
MAP_PROCESS_ACCESS_REQ_ACK
MAP_FORWARD_NEW_TMSI TMSI REAL CMD (DT1) DATA REQ
DTAP-MM
(new TMSI,LAI)
MM(SDCCH) MM(SDCCH)
TMSI REAL CMD TMSI REAL COM
<TMSI REAL CMD>
B interface VLR
AUTH REQUEST (DT1) DATA REQ<AUTH> AUTH REQUEST (CKSN, RAND) T3260 +
DTAP-MM
MM(SDCCH)
AUTH RESPONSE
MM(SDCCH)
DATA IND<AUTH> AUTH RESPONSE (DT1) T3260 (SRES)
Paging(UDT)
BSSMAP
RR(PCH)
(IMSI/TMSI) Channel Request
RR(RACH) T3120 +
Channel Required
Channel Activation
Channel Activation ACK
Immediate Assign Command T3101 + (L2 - UI) Immediate Assignment
(L2 - UA)
RR(FACCH)
ASSIGN COM DATA IND <ASSIGN COM> ASSIGN COM(DT1) TNT2 -
BSSMAP
RF CHAN REL (SDCCH) RF CHAN REL ACK
CC
Radio-resource assignment
MS Terminated Call Procedure Continue 5
CLEAR CMD(DT1) TNT3 + CHAN REL T3109 + <CHAN REL> DEACT SACCH DEACT SACCH ACK DATA REQ
BSSMAP
RR(FACCH)
RLG(TUP)
RR(FACCH)
(L2 - DISC)
RR(FACCH)
(L2 - UA) REL IND
RELEASE COM(DT1) DATA REQ RELEASE COM <RELASE COM>
DTAP-CC
RLG(TUP)
CC(FACCH)
CLEAR CMD(DT1) TNT3 + DATA REQ CHAN REL T3109 + <CHAN REL>
BSSMAP
RR(FACCH)
DEACT SACCH (L2 - DISC) DEACT SACCH ACK
DTAP-MM
(new TMSI,LAI)
MM(SDCCH) MM(SDCCH)
TMSI REAL CMD
<TMSI REAL CMD>
TMSI REAL COM DATA IND <TMSI REAL COM> TMSI REAL COM (DT1)
DTAP-MM
MAP_FORWARD_NEW_TMSI ACK
Immediate Assign Command T3101 + (L2 - UI) Immediate Assignment
RR(AGCH)
T3120 -
(SDCCH ID)
RR(SDCCH)
CM SERV REQ (L2-SABM) T303 + EST IND<CM SERV REQ> T3101 CR(COMPL - L3 - INFO) <CM SERV REQ> (CKSN,MS ID,SER type,CLmk)
CBK(TUP)
RELEASE(DT1) DATA REQ RELEASE <REL> T308 + DTAP-CC
CC(FACCH)
CLF(TUP)
RELEASE COM DATA IND <RELASE COM> RELEASE COM(DT1) T308 DTAP-CC CLF(TUP)
CC(FACCH)
CONNECT
T313 + ACM(TUP) DATA IND <CONNECT> CONNECT (DT1) T301 ANC(TUP)
DTAP-CC
CONNECT ACK (DT1) DTAP-CC
ANC(TUP)
DATA REQ <CONNECT ACK>
CC(FACCH)
CONNECT ACK T313 -
DATA IND <TMSI REAL COM>
TMSI REAL COM (DT1)
DTAP-MM
MAP_FORWARD_NEW_TMSI ACK
Mobile - Originating Call Procedure Continue2
Um interface MS BTS
Abis interface BSC
MS Terminated Call Procedure
B
D
C
MSC
VLR
HLR
GMSC
IAI (TUP)
PSTN
MAP_SEND_ROUTING_ INFORMATION MAP_PROVIDE_ROAMING_ NUMBER
MAP_PROVIDE_ROAMING_ NUMBER ACK MAP_SEND_ROUTING_ INFORMATION ACK
A interface MSC
T9103 +
QUEUING(DT1)
BSSMAP
Channel Activation ACK T9103 -
