密码学【英文精品】
密码学翻译1

在消息认真中键入Hash函数使用加密功能,如MD5或SHA哈沙为消息或认证成为一个标准的方法在许多互联网应用程序和协议。
虽然很容易实施,这些机制通常是基于特设技术,缺乏健全的安全分析我们提出新的、简单、实用的认证方案施工的基础,信息在加密的哈希函数。
我们的方案NMAC和HMAC ,被证明是安全的只要哈希函数有一些合理的潜在优势。
iloreover加密,我们的方案的安全紧密相关的哈希函数此外我们的计划是非常有效和实用的。
他们的表现是本质上说这的潜在的哈希函数,iloreover他们使用哈希函数(或其压缩作用)作为一个黑盒,以便得到更广泛的图书馆代码或硬件可以用来实现他们S一个简单的方法.1介绍摘要本文针对上海,authenticationand问题带到forenformation哈希函数,如使用密码的安全需求MD5the互联网。
哈希算法是密码学主要的一部分。
这是我们加密人员与泛滥的破解技术抗争的主力,我们知道他们最不喜欢就是密码图形。
一个hash算法提供了可变长度的输入字符串和固定长度的结果。
输入的很简便就是“hash”的意思,这个词不是人名的缩写。
你可以用hash来输入数据,固定长度的字符串允许我们使用hash值来引用实际字符串本身。
因为hash算法使用长的字符串,再变成一个短的。
不可避免有2个字符串通过hash 算法会得出一样的结果,这个在密码学中叫“碰撞”。
举个你可以明白hash值的例子,假如Jon Callas和Jane Cannoy他们名字的hash值都是JC。
碰撞是了解hash算法很重要的部分,我们将会在比特(bit)的单位上有更多的介绍。
尽管缩写是一个很简单描述原文的方式,缩写造成了密码学目的的hash算法的错误。
密码学的hash算法。
有很多用在加密技术中的属性。
●很难逆向运算hash算法。
据hash知识,没有一个好的办法找到hash值对应的那个字符串。
我们已经知道了hash算法会丢失数据,创造了一个简单的相对性。
密码学概览
for(int i=0;i<5;i++){ for(int j=0;j<5;j++){ mp.insert(pair<char,WordPos>{keys[i][j],WordPos{i,j}}); }
} mp.insert(pair<char,WordPos>{'J',mp['I']}); }
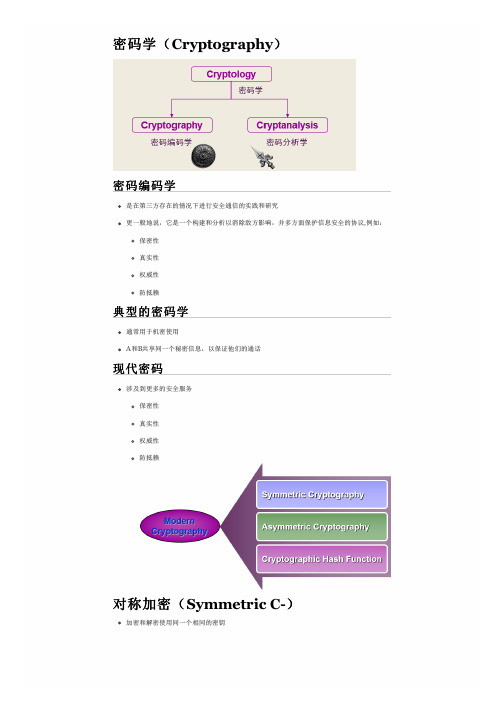
密码学(Cryptography)
密码编码学
是在第三方存在的情况下进行安全通信的实践和研究
更一般地说,它是一个构建和分析以消除敌方影响,并多方面保护信息安全的协议,例:
保密性 真实性 权威性 防抵赖
典型的密码学
通常用于机密使用
A和B共享同一个秘密信息,以保证他们的通话
现代密码
涉及到更多的安全服务 保密性 真实性 权威性 防抵赖
} string ErrorTextCipher_Encode(const string& p, const string& k,const char matrix[26][26]) {
string key = ""; string res = ""; ErrorTextCipher_KeyExpand(key, k, p.size()); for (int j = 0; j < p.size(); j++) {
}
for(int i=0;i<group.size();i+=2){ char p_1=group[i]; char p_2=group[i+1]; WordPos pos_1=mp[p_1]; WordPos pos_2=mp[p_2]; char c_1,c_2; if(pos_1.x==pos_2.x){ pos_1.x=(pos_1.x+1)%5; pos_2.x=(pos_2.x+1)%5; }else if(pos_1.y==pos_2.y){ pos_1.y=(pos_1.y+1)%5; pos_2.y=(pos_2.y+1)%5; }else{ swap(pos_1.x,pos_2.x); } c_1=PlayfairCipher_GetKeyChar(keys,pos_1); c_2=PlayfairCipher_GetKeyChar(keys,pos_2); res+=c_1; res+=c_2;
密码学

s_18_216_306_126_144_198_198_216___0__54__72_342_126_144_324__36_252__54__72
X- X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y- Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Scytale
Grille密码
VIC密码 (一种复杂的手工密码,在五十年代早期被至少一名苏联间谍使用过,在当时是十分安全的)
对传统密码学的攻击
频率分析
重合指数
希尔
希尔密码(Hill Password)是运用基本矩阵论原理的替换密码,由Lester S. Hill在1929年发明。
每个字母当作26进制数字:A=0, B=1, C=2... 一串字母当成n维向量,跟一个n×n的矩阵相乘,再将得出的结果模26。
注意用作加密的矩阵(即密匙)在<math>\mathbb_^n</math>必须是可逆的,否则就不可能译码。只有矩阵的行列式和26互质,才是可逆的。
三、Hill cipher(希尔密码)
d__3__36__51__21__24__33__33__36___0___9__12__57__21__24__54___6__52____48___0__12__16__76__28__32__72___8__56__12__16
m_12_144_204__84__96_132_132_144___0__36__48_228__84__96_216__24_168__36__48
简述密码学

简述密码学密码学历和密码系统种类密码学(Cryptology)一字源自希腊文"krypto's"及"logos"两字,直译即为"隐藏"及"讯息"之意。
密码学的起源可能要追溯到人类刚刚出现,并且尝试去学习如何通信的时候。
他们不得不去寻找方法确保他们的通信的机密。
但是最先有意识的使用一些技术的方法来加密信息的可能是公元六年前的古希腊人。
他们使用的是一根叫scytale 的棍子。
送信人先绕棍子卷一张纸条,然后把要写的信息打纵写在上面,接着打开纸送给收信人。
如果不知道棍子的宽度(这里作为密匙)是不可能解密里面的内容的。
后来,罗马的军队用凯撒密码(三个字母表轮换)进行通信。
恺撒密码是公元前50年古罗马恺撒用过的密码,加密方法是把a变成D,b变成E,c换成F,依次类推,z换成C。
这样明文和密文的字母就建立一一对应的关系。
在随后的19个世纪里面,主要是发明一些更加高明的加密技术,这些技术的安全性通常依赖于用户赋予它们多大的信任程度。
在19世纪Kerchoffs写下了现代密码学的原理。
其中一个的原理提到:加密体系的安全性并不依赖于加密的方法本身,而是依赖于所使用的密匙。
.在二次大战中,密码更是扮演一个举足轻重的角色,许多人认为同盟国之所以能打赢这场战争完全归功于二次大战时所发明的破译密文数字式计算器破解德日密码。
破译密文数字式计算器又名图灵机,是数学家图灵所发明的。
公元1949年,Shannon提出第一篇讨论密码系统通讯理论之论文,近代密码学可说是滥觞于斯。
直至公元1975年,Diffie与Hellman提出公开金匙密码系统之观念,近代密码学之研究方向,正式脱离秘密金匙密码系统之窠臼,蓬勃发展,至今已近二十年。
发展至今,已有二大类的密码系统。
第一类为对称金钥(Symmetric Key),第二类为非对称金钥(Public Key)。
密码学原理及应用——摩斯密码

密码学原理及应用——摩斯密码English Answer.Cryptography: Principles and Applications.Morse Code.Morse code is a simple method of encoding text into a series of short and long signals. It was invented in the 1830s by Samuel Morse and has been widely used for communication over long distances.Morse code is based on assigning a unique sequence of dots and dashes to each letter of the alphabet. The length of the dots and dashes is determined by the frequency of the letters in the English language. For example, theletter "E" is represented by a single dot, while the letter "Z" is represented by four dashes.To encode a message using Morse code, each letter isconverted into its corresponding sequence of dots and dashes. These dots and dashes are then transmitted over a communication channel, such as a telegraph wire or a radio wave.To decode a Morse code message, the receiver must know the sequence of dots and dashes that corresponds to each letter of the alphabet. The receiver can then use this knowledge to decode the message.Morse code is a simple and effective method of encoding text. It is easy to learn and use, and it can be used to transmit messages over long distances.Applications of Morse Code.Morse code has been used for a wide variety of applications, including:Communication over telegraph wires.Communication over radio waves.Communication in emergencies.Communication with ships and aircraft.Communication with the deaf and hard of hearing.Morse code is still used today, although it has been largely replaced by other methods of communication, such as telephony and email. However, Morse code remains a valuable tool for communication in emergencies and for communication with the deaf and hard of hearing.中文回答:密码学原理及应用——摩斯密码。
《密码学基本概念》PPT课件

19
精选PPT
六、密码学的理论基础
⑴ 商农信息论
①从信息在信道传输中可能受到攻击,引入密码理论;
②提出以扩散和混淆两种基本方法设计密码;
③阐明了密码系统,完善保密,理论保密和实际保密 等概念。
⑵ 计算复杂性理论
①密码的安全性以计算复杂度来度量;
②现代密码往往建立在一个数学难题之上,而难是计 算复杂度的概念;
③商用密码: 用于保护国家和事企业单位的非机密的敏感信息。
④个人密码: 用于保护个人的隐私信息。
前三种密码均由国家密码管理局统一管理!
3
精选PPT
二、密码的基本思想
伪装信息,使未授权者不能理解它的真实含义。
所谓伪装就是对信息进行一组可逆的数学变换。 伪装前的原始信息称为明文, 伪装后的信息称 为密文,伪装的过程称为加密。去掉伪装还原 明文的过程成为解密。加密在加密密钥的控制 下进行。解密在解密密钥的控制下进行。用于 加密的一组数学变换称为加密算法。用于解密 的一组数学变换称为解密算法。
②研究密码破译的科学称为密码分析学 (Cryptanalysis),
③而密码编制学和密码分析学共同组成 密码学(Cryptology)。
14
精选PPT
密码分析
①如果能够根据密文系统地确定出明文或密钥, 或者能够根据明文-密文对系统地确定出密钥,
则我们说这个密码是可破译的。
②一个密码,如果无论密码分析者截获了多少 密文和用什么方法进行攻击都不能被攻破,则 称为是绝对不可破译的。
12
精选PPT
• DNA密码
• DNA密码基于生物学中的某种困难问题。
• 由于DNA密码的安全不依赖于计算困难问 题,所以不管未来的电子计算机、量子计 算机和DNA计算机具有多么强大的计算能 力,DNA密码对于它们的计算攻击都是免 疫的 。
现代密码学【英文】

New Directions in Cryptography
W.Diffie & M.E.Hellman
Probabilistic Encryption
S.Goldwasser & S.Micali
By 1976...
Practically – Computers and “Private key security” exist (DES), and are becoming more and more applicable. Theoretically –
By 1976... (biographical details)
In 1972, Whitfiled Diffie, an AI graduate student, developes more than an interest in cryptography.
In 1974, at the age of 30, he phones Martin Hellman, assistant professor in Stanford, to discuss issues in crypto. They begin collaborating.
1. NO definitions, notations, claims, proofs etc.
2. HOWEVER: clever ideas, clever insights!
3. Practicality. Historical survey.
So, what do we have in “conventional cryptographic system” (block or stream)?
密码学-2

密钥量为 ( q! ) n
5、换位密码 (这里换位被看作一种多表代替密码!)
n X n Y n Zq ,
K 为 {1,2,, n} 上的全体置换的全体, 对任意明文 m (m1 , m2 ,, mn ) X n,k K, c E(m) (m (1) , m ( 2) ,, m ( n ) ) k
Z5
+ 0 1 2 3 0 0 1 2 3 1 1 2 3 4 2 2 3 4 0 3 3 4 0 1 4 4 0 1 2 * 1 1 1
* Z5
2 2
3 3
4 4
2
3 4
2
3 4
4
1 3
1
4 2
3
2 1
4
4
0
1
2
3
对于英文字母表 q=26
字母 数字
Z 26 {0, 1, 2,, 25}
f
c Ek (m) (m k ) mod q m Dk (c) (c k ) mod q
加法密码的密钥量为q 。 移位密码,凯撒密码体制
2、 乘法密码 X Y Z q , K Z q *, m X , k K ,
c Ek (m) km mod q, m k c mod q
密钥量为 (q )! 当q为素数时
n
A
D
B
E
R
P-1
b r e a d
* 求逆时需要重新排序!
(4 5 1 3 2) (3 5 4 1 2)
代替:字母表上的置换表。 (substitution) 换位:明文字母上的置换。(直接称为置换permutation) 混淆和扩散 S 盒和 P 盒
信息安全工程师教程内1.5节专业英语翻译

Cryptography is the practice and study of hiding information. In modern times, cryptography is considered a branch of both mathematics and computer science, and is affiliated closely with information theory,computer security, and engineering. Cryptography is used in applications present in technologically advanced societies; examples include the security of ATM cards, computer passwords,and electronic commerce, which all depend on cryptography.密码学是信息隐藏的实践与研究。
现代密码学被认为是数学和计算机科学的一个分支,它与信息论、计算机安全和工程密切相关。
密码技术被应用于技术先进的社会中,例如A TM卡、计算机密码和电子商务的安全,这些都依赖于密码学。
(1 )TerminologyUntil modem times, cryptography referred almost exclusively to encryption, the process of converting ordinary information (plaintext) into unintelligible gibberish (i.e., ciphertext). Decryption is the reverse, moving from unintelligible ciphertext to plaintext. A cipher (or cypher) is a pair of algorithms which creates the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and, in each instance, by a key. This is a secret parameter (ideal以known only to the communicants) for a specific message exchange context. Keys are important, as ciphers without variable keys are trivially breakable and therefore less than useful for most purposes. Historically, ciphers were often used directly for encryption or decryption, without additional procedures such as authentication or integrity checks.直到近代,加密提到几乎完全加密,普通的转换过程的信息(明文)到不知所云胡言乱语(即密文)。
密码学 入门(一)

Introduction
Pillars of Cryptology
9 / 27
Cryptology is Interdisciplinary
Computer Science
M
at he er ing
m
at ine
ics
ec El tr( on a )ic ng lE
Introduction
Pillars of Cryptology
2
Classical Cryptography One Time Pad
Introduction
Practicalities of Cryptography A
4 / 27
Introduction
This course will be about the science of cryptology. We focus on the basics for simplicity and to display the way modern cryptology works. Definitions Reductions (aka security proofs) Constructions We will concentrate on cryptology relevant to secure communication between two parties.
Hi Hello Bye
Anna Bye Bob
Introduction
Paradigms of Cryptology
12 / 27
Secure Communication
Confidentiality, integrity, authenticity
密码学的基础知识英文翻译

密码学的基础知识在公钥加密系统中,为了保障加密操作的便捷,产生了密钥技术.目前, 公钥加密系统都使用两个不同的密钥,其中一个密钥是私有的,另一个是公有的.根据不同的应用要求,发送方可使用其私钥或者接收方的公钥或同时使用二者来执行密码加密功能。
密钥体制的应用一般可分为三类; (1)加密/解密:发送方用接收方的公钥对消息加密; (2) 数字签名:发送方用自己的私钥对消息“签名”,可以对整条消息或者对消息的一个小的数据块来产生,接受方利用公钥验证数据源; (3) 密钥交换:通信双方交换会话密钥,一般都要借用通信第三方的私钥。
非对称加密算法进行数字签名时使用两个密钥:公开密钥(public key)和私有密钥(private key),分别用于对数据的加密和解密,即如果使用公开密钥对数据进行加密,只有用对应的私有密钥才能进行解密;如果用私有密钥对数据进行加密,则只有用对应的公开密钥才能解密。
任何拥有发送方公开密钥的人都可以通过密钥验证明文来源的正确性。
由于发送方私有密钥的保密性,使得接收方可以根据验证结果来拒收该报文,也能使其他人无法伪造报文。
密钥密钥是一个数值,它和加密算法一起生成特别的密文。
密钥本质上是非常非常大的数。
密钥的尺寸用位(bit)来衡量,1024 位密钥代表的数是非常巨大的. 在公开密钥加密方法中,密钥的尺寸越大,密文就越安全. 然而,公钥的尺寸和传统加密方法中密钥的尺寸是不相关的.传统 80 位密钥的强度等同于 1024 位的公钥,传统 128 位密钥的强度等同于 3000 位的公钥。
在同种加密算法中,密钥越大越安全。
但是传统方法和公开密钥方法所用的加密算法不一样,因此它们的密钥尺寸不能直接比较公钥和私钥是算术相关的,仅凭公钥推算出私钥是非常困难的。
然而如果有足够的时间和计算能力,总是可能导出私钥的。
这使得选择合适尺寸的密钥变得非常重要。
为了安全需要足够大的密钥,为了速度有要足够小的密钥。
1密码学

分组密码(block cipher):将明文分成固定 长度的组,用同一密钥和算法对每一块加 密,输出也是固定长度的密文。 流密码(stream cipher):又称序列密码,每 次加密一位或一字节的明文。
12
密码算法的分类
按照密钥使用方法分
对称密码算法(symmetric cipher):又称传 统密码算法(conventional cipher)或秘密密 钥算法、单密钥算法。 非对称密钥算法(asymmetric cipher),又 称公开密钥算法(public-Key cipher) 。
加密算法;要解密的密文;分析者任选明文,并 用(与待解密文)同一密钥加密的密文;分析者有 目的选择密文,并用(与待解密文)同一密钥解密 的对于明文 传统密码体制基于加密信息的攻击类型
密码的安全性考虑
无条件安全(Unconditionally secure)
无论破译者有多少密文,他也无法解出对应的明文, 即使他解出了,他也无法验证结果的正确性. 一次一密 破译密码的代价超出密文信息的价值 破译密码的时间超出密文信息的有效生命期
(transposition):明文的字母保持相同,但打 乱排列的顺序。
31
替换密码
简单替换密码(simple substitution cipher),又 称单字母密码(monoalphabetic cipher)
明文的一个字符用相应的一个密文字符替换,而 且密文所用的字符与一般的明文所用字符属同一 语言系统。 明文中的字符映射到密文空间的字符还依赖于它 在上下文中的位臵。
加密算法(encryption algorithm).
区块链中的密码学的英语作文

区块链中的密码学的英语作文The cryptography applied in the blockchain mainly includes the following aspects:digital abstractBlockchain is essentially a distributed data storage method. Each data block is linked by a digital summary. For example, each block in Bitcoin contains the summary value of its previous block. Therefore, the digital digest is the most widely used cryptography technology in the blockchain, and it is also one of the core technologies of the blockchain.The digital digest algorithms commonly used in the blockchain are SHA-256 and RIPEMD160, among which SHA256 is the main digest algorithm used to construct the blockchain. For example, in Bitcoin, SHA256 is mainly used to complete the calculation of PoW (proof of work), that is, mining; in the HyperLedger-Fabric blockchain platform, it is mainlyused to detect unauthorized modification of data and identify the signer and non-repudiation. In addition to its own data, each block in the blockchain also contains the digital summary value of the previous block data, and points to the previous block through a pointer. Such a list structure establishes the entire chain.If the attacker tampers with the value of a certain block (such as the Kth block), then the saved H(K) of the K+1 block is inconsistent with the value calculated by the K digest. The attacker can modify K+1 in order to cover up the tampering. The value of H(K) in the block, but the H(K+1) of the K+2 block is inconsistent with the calculation result of the K+1 block summary, and the attacker has to continue to modify the H(K+1) value...to By analogy, in theory, the attacker must modify all node data on the blockchain starting from block K+1 to avoid being discovered, which is simply not feasible in practice, and some special node data cannot be modified. This is how the blockchainensures that data is tamper-proof.Merkle treeA Merkle tree, which is a binary or multi-fork tree based on numerical summaries. The bottommost node of the Merkle tree includes the block data and its digital summary value, and the nodes at other layers contain the summary value of the combined data of the two sub-nodes in the lower layer. An example of its structure is as follows.The characteristic of the Merkle tree is that the data changes of the underlying nodes can be transmitted layer by layer to the uppermost nodes; conversely, the changes of the data of the underlying nodes can be monitored through the uppermost nodes. Taking advantage of this feature, using the Merkle tree in the blockchain can achieve fast comparison of data and fast positioning of nodes without downloading the entire data on the chain. Simple Payment Verification(SPV) in Bitcoin is a typical application based on Merkle tree.digital signatureBlockchain uses digital signatures to confirm the identity of transactors. For example, in a cryptocurrency transaction, the initiator of the transaction digitally signs the transaction information and submits the signature result to the miner. The miner verifies the signature with the public key of the signing user. If the verification is passed, the transaction information is recorded and the transaction is completed. The digital signature algorithms used in the blockchain are all based on ECC, such as the secp256k1 elliptic curve cryptographic algorithm used in Bitcoin.Symmetric encryptionThere are also application scenarios involving the use of symmetric encryption in the blockchain. Forexample, the official Bitcoin client uses AES (symmetric block cipher algorithm) to encrypt wallet files to ensure the security of the client's private key.HMACHMAC is the abbreviation of Hash-based Message Authentication Code, translated into Chinese is Hash-based message authentication code. Its predecessor is MAC (Message Authentication Code). In fact, the HMAC operation is somewhat similar to the digital signature. The digital signature uses the private key to asymmetrically encrypt the digital abstract, while the HMAC uses the negotiated key to symmetrically encrypt the digital abstract (knowing this, the process of HMAC does not need to be described again) . Therefore, HMAC can be regarded as an enhanced version of the digital summary, and the purpose is to protect the integrity of the data. As mentioned earlier, the digital abstract plays an extremely important role in the blockchain, so it is necessary to add another layer of encryption to theabstract to prevent it from "streaking" and make it more reliable.homomorphic encryptionHomomorphic encryption is actually not a new technology, it existed before the blockchain. Homomorphic encryption means that the encrypted data continues to maintain the computing characteristics and functions of the plaintext data before encryption. As a simple example, for the following formula:1+2=3Suppose we encrypt 1 and 2 respectively to get two ciphertexts (hexadecimal representation):1-------->0x8CBD412-------->0x1EF9B7Then add the two encrypted results to get the sum:0x8CBD41+0x1EF9B7=0xABB6F8Now to decrypt this sum, according to the previous encryption method, it is impossible for us to decrypt 3 anyway. But if it is homomorphic encryption, the sum of the encrypted results of 1 and 2 should also be 3 after decryption, that is, although the data is encrypted, its computing characteristics are still maintained, which is the so-called "homomorphic". It can be expressed by the following formula, E represents the homomorphic encryption algorithm, F represents the data operation, a, b, c are the plaintext data involved in the operation:F(E(a),E(b),E(c))=E(F(a,b,c))In the decentralized structure of the blockchain, many important and sensitive data may need to be processed on third-party nodes, so the data needs to be processed in an encrypted state. This is whathomomorphic encryption does in blockchains.。
密码学

密码学综述姓名:陶佳杰学号:10053430 专业名称:网络工程2014年3月2日密码学的发展前言密码学(在西欧语文中,源于希腊语kryptós“隐藏的”,和gráphein“书写”)是研究如何隐密地传递信息的学科。
在现代特别指对信息以及其传输的数学性研究,常被认为是数学和计算机科学的分支,和信息论也密切相关。
著名的密码学者Ron Rivest解释道:“密码学是关于如何在敌人存在的环境中通讯”,自工程学的角度,这相当于密码学与纯数学的异同。
密码学是信息安全等相关议题,如认证、访问控制的核心。
密码学的首要目的是隐藏信息的涵义,并不是隐藏信息的存在。
密码学也促进了计算机科学,特别是在于电脑与网络安全所使用的技术,如访问控制与信息的机密性。
密码学已被应用在日常生活:包括自动柜员机的芯片卡、电脑使用者存取密码、电子商务等等。
密码是通信双方按约定的法则进行信息特殊变换的一种重要保密手段。
依照这些法则,变明文为密文,称为加密变换;变密文为明文,称为脱密变换。
密码在早期仅对文字或数码进行加、脱密变换,随着通信技术的发展,对语音、图像、数据等都可实施加、脱密变换。
文献研究密码学的产生密码学在公元前400多年就早已经产生了,正如《破译者》一书中所说“人类使用密码的历史几乎与使用文字的时间一样长”。
密码学的起源的确要追溯到人类刚刚出现,并且尝试去学习如何通信的时候,为了确保他们的通信的机密,最先是有意识的使用一些简单的方法来加密信息,通过一些(密码)象形文字相互传达信息。
接着由于文字的出现和使用,确保通信的机密性就成为一种艺术,古代发明了不少加密信息和传达信息的方法。
例如我国古代的烽火就是一种传递军情的方法,再如古代的兵符就是用来传达信息的密令。
就连闯荡江湖的侠士,都有秘密的黑道行话,更何况是那些不堪忍受压迫义士在秘密起义前进行地下联络的暗语,这都促进了密码学的发展。
事实上,密码学真正成为科学是在19世纪末和20世纪初期,由于军事、数学、通讯等相关技术的发展,特别是两次世界大战中对军事信息保密传递和破获敌方信息的需求,密码学得到了空前的发展,并广泛的用于军事情报部门的决策。
密码学 加密方式 fernet

密码学加密方式 fernet英文回答:Fernet is a symmetric encryption algorithm thatprovides secure and authenticated encryption. It is part of the cryptography library in Python and is widely used for encrypting data. Fernet uses symmetric keys, which meansthat the same key is used for both encryption and decryption.To use Fernet, you first need to generate a key. This key should be kept secret and should not be shared with anyone. Once you have the key, you can use it to encryptand decrypt your data. The encryption process involves converting the data into a binary format and then applying the Fernet encryption algorithm using the key. The resultis a ciphertext, which is the encrypted version of the data.One of the advantages of using Fernet is that it provides both encryption and authentication. This meansthat not only is the data encrypted, but it is also protected against tampering. Fernet uses a message authentication code (MAC) to ensure the integrity of the encrypted data. This MAC is generated using a separate key, which is derived from the original key. By including the MAC in the ciphertext, Fernet ensures that the data has not been modified since it was encrypted.Fernet also provides a simple and easy-to-use interface for encryption and decryption. In Python, you can use the `cryptography` library to generate a Fernet key and perform encryption and decryption operations. Here is an example of how to use Fernet in Python:from cryptography.fernet import Fernet.# Generate a key.key = Fernet.generate_key()。
密码学 vigenere密码

.063
0.14 0.12 0.1 0.08 0.06 0.04 0.02 0 a b c
.091
.028
.010
.023
.001
.020
.001
字母的标准频率
d
e
f
g
h
i
j
k
l
m
n
o
p
q
r
s
t
u
v
w
x
y
z
vigenere密文如下:
VVHQWVVRHMUSGJGTHKIHTSSEJCHLSFCBGVWC RLRYQTFSVGAHWKCUHWAUGLQHNSLRLJSHBLTS PISPRDXLJSVEEGHLQWKASSKUWEPWQTWVSPG OELKCQYFNSVWLJSNIQKGNRGYBWLWGOVIOKH KAZKQKXZGYHCECMEIUJOQKWFWVEFQHKIJRCL RLKBIENQFRJLJSDHGRHLSFQTWLAUQRHWDMW LGUSGIKKFLRYVCWVSPGPMLKASSJVOQXEGGVE YGGZMLJCXXLJSVPAIVWIKVRDRYGFRJLJSLVEGG VEYGGEIAPUUISFPBTGNWWMUCZRVTWGLRWUG UMNCZVILE 问题:假设密钥长度为5,如何确定密钥?
字母的标准频率
m
n
o
p
q
r
s
t
uLeabharlann vwxy
z
可猜测密钥的第5位为s
确定密钥的数学描述
例:分析密文件vvhq.text
假 设 密 钥 长 度 为 l , 我 们 将 密 文 分 成 l组 .
密码学【英文精品】120页PPT

26、机遇对于有准备的头脑有特别的 亲和力 。 27、自信是人格的核心。
28、目标的坚定是性格中最必要的力 量泉源 之一, 也是成 功的利 器之一 。没有 它,天 才也会 在矛盾 无定的 迷径中 ,徒劳 无功。- -查士 德斐尔 爵士。 29、困难就是机遇。--温斯顿.丘吉 尔。 30、我奋斗,所以我快乐。--格林。——华盛顿 17、一个人即使已登上顶峰,也仍要自强不息。——罗素·贝克 18、最大的挑战和突破在于用人,而用人最大的突破在于信任人。——马云 19、自己活着,就是为了使别人过得更美好。——雷锋 20、要掌握书,莫被书掌握;要为生而读,莫为读而生。——布尔沃
END
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
JLM 20060107 22:16
3
Communications Engineers Coat of Arms
The Source Sender: Alice Plaintext (P)
Compress
(to save space)
Encrypt
(for confidentiality)
Encode
• Symmetric Key cryptographic algorithms use a secret known to the authorized parties called a “key”. Encryption and Decryption use the same key.
– The transformations are simple and fast enough for practical use and implementation. – “Keyspace” large enough to protect against exhaustive search. – The encryption algorithm must be efficiently invertible. – Two major types: Stream ciphers and Block ciphers
JLM 200hedule
Date 1 1/3 Topic Practical Aspects of Cryptography Lecturer Josh
2
3 4 5 6 7 8 9 10
1/10
1/17 1/24 1/31 2/7 2/14 2/21 3/1 3/8
Webpage: /education/courses/csep590/06wi/
Recommended texts:
Stinson, Cryptography, Theory and Practice. 2nd Edition, CRC Press, 2002. Menezes, vanOrtshot, Vanstone. Handbook of Applied Cryptography. Ferguson and Schneier, Practical Cryptography.
Symmetric Key Ciphers and Hashes
Public Key Ciphers Cryptographic Protocols I Cryptographic Protocols II Security of Block Ciphers AES and Cryptographic Hashes Trust, PKI, Key Management [Last HW Assignment) Random Numbers/Elliptic Curve Crypto Three topics: Elections, ITAR/Politics, Side Channels/Timing Attacks, DRM, BigNum Implementation
Portions © 2004-2005, John Manferdelli.
This material is provided without warranty of any kind including, without limitation, warranty of non-infringement or suitability for any purpose. This material is not guaranteed to be error free and is intended for instructional use only.
(to correct errors)
Noisy insecure channel
Noisy insecure channel
The Sink Receiver:Bob
Decode
(to correct errors)
Decrypt
(for confidentiality)
Decompress
(to save space)
JLM 20060107 22:16 5
Why go Ugly?
Algorithm
RSA-1024 Encrypt RSA-1024 Decrypt
AES-128 RC4 DES
Speed
.32 ms/op (128B), 384 KB/sec 10.32 ms/op (128B), 13 KB/sec
Plaintext (P)
JLM 20060107 22:16
4
Symmetric Encryption
Plaintext (P) Key (k) Encrypt Ek(P) Ciphertext (C) Ciphertext (C) Key (k) Decrypt Dk(P)
Plaintext (P)
John
Josh Brian Brian John John Brian Josh All
JLM 20060107 22:16
2
Symmetric Key Cryptography and Cryptographic Hashes - I
John Manferdelli
jlm@ jmanfer@
University of Washington CSEP 590TU – Practical Aspects of Modern Cryptography
Instructors: Josh Benaloh, Brian LaMacchia, John Manferdelli Tuesdays: 6:30-9:30, Allen Center 305
