A FRAMEWORK FOR MINIMIZING LATENCY IN CDN USING URL REQUEST ROUTING APPROACH Abstract
人工智能的好处英语作文

Artificial Intelligence, or AI, has become a significant part of our lives, transforming various industries and daily activities. Here are some of the key benefits of AI:1. Efficiency and Productivity: AI systems can perform tasks much faster than humans, without the need for breaks, leading to increased efficiency and productivity in various sectors such as manufacturing, data processing, and customer service.2. Accuracy: AI algorithms are designed to minimize errors. They can analyze large datasets and identify patterns with a high degree of accuracy, which is particularly useful in fields like finance, healthcare, and scientific research.3. Personalization: AI can tailor experiences to individual preferences, making services more personalized and userfriendly. For example, online shopping platforms use AI to recommend products based on a users browsing and purchase history.4. Innovation: AI is a catalyst for innovation. It enables the development of new technologies and solutions to complex problems, from selfdriving cars to advanced medical treatments.5. Accessibility: AI technologies, such as voice assistants and translation services, make information and communication more accessible to people with disabilities.6. Cost Reduction: By automating repetitive tasks, AI can reduce labor costs and help businesses operate more economically.7. Enhanced Decision Making: AI can process and analyze vast amounts of data to provide insights that inform better decisionmaking in business and governance.8. Predictive Capabilities: AI systems can predict trends and outcomes based on historical data, which is invaluable for planning and risk management.9. Improved Safety: In industries such as aviation and transportation, AI systems can monitor and control processes to reduce the risk of accidents.10. Educational Advancements: AI can provide personalized learning experiences for students, adapting to their pace and style of learning, and offering resources that suit their needs.11. Healthcare Advancements: AI is revolutionizing healthcare by assisting in diagnosis, treatment planning, and patient monitoring, leading to better patient outcomes.12. Environmental Benefits: AI can optimize energy usage, predict environmental changes, and support sustainable practices, contributing to a healthier planet.In conclusion, the benefits of AI are vast and multifaceted, touching every aspect of modern life and offering solutions to some of the worlds most pressing challenges. As AI continues to evolve, its potential to improve our lives is limitless.。
英语作文-集成电路设计行业的最新技术与应用案例分享

英语作文-集成电路设计行业的最新技术与应用案例分享In recent years, the field of integrated circuit (IC) design has witnessed remarkable advancements driven by cutting-edge technologies and innovative applications. This rapid evolution is not only shaping the future of electronics but also revolutionizing various industries reliant on semiconductor devices. In this article, we explore some of the latest trends and case studies that highlight the transformative impact of these advancements.One of the key areas experiencing significant breakthroughs is the development of System-on-Chip (SoC) designs. SoC integrates multiple functionalities previously handled by separate ICs into a single chip, enhancing efficiency, reducing power consumption, and minimizing physical footprint. This consolidation is pivotal in mobile devices, IoT applications, and automotive electronics, where compactness and energy efficiency are critical.Moreover, the rise of artificial intelligence (AI) and machine learning (ML) has spurred demand for specialized ICs optimized for neural network computations. Graphics Processing Units (GPUs) and Tensor Processing Units (TPUs) are prime examples of ICs tailored to accelerate complex AI algorithms, enabling advancements in autonomous vehicles, natural language processing, and computer vision.In parallel, the evolution of semiconductor manufacturing processes has been instrumental. The transition to smaller nodes, such as 7nm and beyond, enhances transistor density and performance while reducing power consumption. This trend not only supports the development of faster and more energy-efficient ICs but also enables the integration of advanced features like high-speed interfaces, secure hardware enclaves, and advanced signal processing capabilities.Furthermore, the proliferation of 5G technology has catalyzed innovations in RF (Radio Frequency) IC design. ICs capable of handling high-frequency signals withminimal latency are crucial for 5G infrastructure and mobile devices. These advancements are pivotal in enabling faster data rates, lower latency, and robust connectivity, thereby facilitating the widespread adoption of 5G across various sectors including telecommunications, healthcare, and smart cities.Another noteworthy trend is the growing emphasis on security in IC design. With the increasing connectivity of devices and the rise of cyber threats, there is a critical need for ICs that incorporate robust security features. Hardware-based security solutions such as Trusted Execution Environments (TEEs) and secure boot mechanisms are becoming standard in modern IC designs to safeguard sensitive data and protect against malicious attacks.Moreover, the convergence of IC design with advanced packaging technologies is opening new avenues for innovation. 3D IC integration and heterogeneous integration techniques enable the stacking of multiple IC layers or diverse technologies within a single package. This approach enhances performance, reduces interconnect lengths, and addresses thermal management challenges, thereby advancing the capabilities of ICs in high-performance computing, data centers, and edge computing applications.In conclusion, the field of integrated circuit design continues to evolve rapidly, driven by technological advancements and diverse applications. From SoC designs and AI-optimized ICs to advanced manufacturing processes and secure IoT solutions, each innovation contributes to pushing the boundaries of what is possible in electronics and beyond. As these trends unfold, they promise to reshape industries, enhance user experiences, and pave the way for a more connected and intelligent future.。
以科技为主题英语作文200词

以科技为主题的英语作文,每篇不少于200个单词。
篇1.The Influence of Artificial IntelligenceArtificial intelligence (AI) has become one of the most significant technological advancements in recent years. It has permeated various aspects of our lives, from daily household appliances to complex industrial systems.In the medical field, AI can assist doctors in diagnosing diseases more accurately. For example, it can analyze a large number of medical images such as X -rays and MRIs in a short time, helping to identify early - stage tumors or other abnormalities that might be overlooked by human eyes. In transportation, self - driving cars based on AI technology are being developed. These vehicles have the potential to reduce traffic accidents caused by human errors, such as fatigue driving or distracted driving.However, the development of AI also brings some challenges. One of the concerns is the potential loss of jobs. As machines become more intelligent and capable of handling tasks that were previously done by humans, many people may find themselves unemployed. Another issue is the ethical dilemma. For instance, if an AI - controlled system makes a decision that causes harm, it's difficult to determine who should be held responsible.Despite these problems, the potential benefits of AI are enormous. We should work on maximizing its advantages while minimizing the negative impacts through proper regulations and ethical considerations.篇2.The Importance of 5G Technology5G technology has emerged as a revolutionary force in the telecommunications industry. It offers speeds that are several times faster than 4G, enabling seamless and instant data transfer.In the entertainment industry, 5G allows for high - quality streaming of videos and online gaming without any lag. Users can enjoy immersive experiences such as virtual reality (VR) and augmented reality (AR) games more smoothly. For example, in a VR concert, the high - speed 5G connection ensures that the visual and auditory effects are transmitted in real -time, making the user feel as if they are actually at the concert venue.In the business world, 5G facilitates better communication between different branches of a company. Video conferencing becomes more stable and clear, enabling employees to collaborate effectively regardless of their geographical locations. It also enables the Internet of Things (IoT) to reach new heights. More devices can be connected to the networksimultaneously, improving the efficiency of smart factories, where machines can communicate with each other to optimize production processes.Moreover, 5G has the potential to transform the healthcare sector. Remote surgeries can be performed with greater precision as the low -latency connection ensures that the surgeon's movements are accurately replicated by the robotic surgical instruments. In conclusion, 5G technology is set to reshape our lives and drive innovation in countless industries.篇3.The Development of Space TechnologySpace technology has always been a fascinating and challenging area of human exploration. Over the years, remarkable progress has been made in this field.One of the main achievements is the development of more advanced rockets. These rockets are capable of carrying heavier payloads into space. For instance, the SpaceX Falcon Heavy can lift a significant amount of satellites or even spacecraft for deep -space exploration. With these powerful rockets, we have been able to launch more communication satellites, which have improved global communication systems, enabling us to have better access to information from around the world.Space exploration missions have also expanded our understanding of the universe. The Mars rovers have sent back valuable data about the Martian environment, including information about its soil, atmosphere, and possible signs of past life. These missions not only satisfy our curiosity about the solar system but also provide crucial information for potential future human habitation on other planets.In addition, space technology has led to the development of satellite -based Earth observation systems. These systems can monitor weather patterns, natural disasters such as hurricanes and wildfires, and changes in the Earth's climate. This data is essential for disaster prevention and mitigation strategies as well as for scientific research on climate change. Overall, space technology continues to push the boundaries of human knowledge and capabilities.篇4.The Role of Biotechnology in Modern SocietyBiotechnology has witnessed rapid development in the modern era and has had a profound impact on our lives.In the field of medicine, biotechnology has led to the development of innovative drugs. For example, monoclonal antibodies are a type of biotech -derived medicine that can target specific disease -causing molecules in the body. These drugs have shown remarkable efficacy intreating various cancers and autoimmune diseases. Gene therapy is another exciting area. Scientists are working on modifying or replacing faulty genes to treat genetic disorders. In some cases, this approach has the potential to cure diseases that were previously considered incurable.In agriculture, biotechnology has improved crop yields and quality. Genetically modified (GM) crops are engineered to be more resistant to pests, diseases, and environmental stresses. For instance, some GM corn varieties can produce their own insect - repelling proteins, reducing the need for chemical pesticides. This not only increases food production but also has environmental benefits as it decreases the use of harmful chemicals.Biotechnology also plays a role in environmental protection. Microorganisms can be engineered to break down pollutants more efficiently. For example, certain bacteria can be used to clean up oil spills or treat wastewater. However, like any technology, biotechnology also raises some concerns, such as potential risks to the environment and human health associated with GM organisms. But with proper regulation and research, biotechnology can bring more benefits to society.篇5.The Impact of Quantum TechnologyQuantum technology is an emerging field that holds great promisefor the future. It is based on the principles of quantum mechanics, which are very different from classical physics.In computing, quantum computers have the potential to revolutionize the way we process information. Unlike traditional computers that use bits to represent data as either 0 or 1, quantum computers use qubits. Qubits can exist in multiple states simultaneously, allowing for exponentially faster processing of complex problems. For example, quantum computers can be used to solve optimization problems in logistics and finance much more quickly. They can analyze vast amounts of data in a short time, which is crucial for fields such as weather forecasting and drug discovery.In communication, quantum encryption offers an unprecedented level of security. The principles of quantum mechanics ensure that any attempt to intercept the communication will be detected. This is because the act of observing a quantum state changes it. Quantum key distribution systems are being developed to protect sensitive information, such as in government and military communications.However, quantum technology also presents challenges. Building and maintaining stable quantum systems is extremely difficult due to the delicate nature of quantum states. But with continuous research and development, quantum technology is likely to bring about a new era of technological innovation.作文中文翻译:篇1. 人工智能的影响人工智能(AI)已成为近年来最重要的技术进步之一。
FortiGate企业防火墙解决方案介绍说明书

HighlightsValidatedSecurityUniversal PlatformSupportOne NetworkOSSingle Paneof GlassPerformanceFortiGate appliances, interconnectedwith the Fortinet Security Fabric,form the backbone of theFortinet Enterprise Solution/sfDATA SHEETFortiGate/FortiWiFi® 30E Unified Threat Management Distributed Enterprise FirewallDATA SHEET: FortiGate/FortiWiFi 30EHARDWAREInstall in Minutes with FortiExplorerThe FortiExplorer wizard enables easy setup and configuration coupled with easy-to-follow instructions. FortiExplorer runs on popular mobile devices like Android and iOS. Using FortiExplorer is as simple as starting the application and connecting to the appropriate USB port on the FortiGate. By using FortiExplorer, you can be up and running and protected in minutes.Wireless and 3G/4G WAN ExtensionsThe FortiGate supports external 3G/4G modems that allow additional or redundant WAN connectivity for maximum reliability. The FortiGate can also operate as a wireless access point controller to further extend wireless capabilities.Compact and Reliable Form FactorDesigned for small environments, you can simply place the FortiGate/FortiWiFi 30E on a desktop. It is small, lightweight yet highly reliable with superior MTBF (Mean Time Between Failure), minimizing the chance of a network disruption.Superior Wireless CoverageA built-in dual-band, dual-stream access point with internal antennas is integrated on the FortiWiFi 30E and provides speedy 802.11n coverage on both 2.4 GHz and 5 GHz bands. The dual- band chipset addresses the PCI-DSS compliance requirement for rogue AP wireless scanning, providing maximum protection for regulated environments.Interfaces1. USB Port2. Console Port3. 1x GE RJ45 WAN Port4. 4x GE RJ45 Switch PortsFortiGate 30EFortiWiFi 30EInterfaces1. USB Port2. Console Port3. 1x GE RJ45 WAN Port4. 4x GE RJ45 Switch PortsSERVICESFortiGuard ™ Security ServicesFortiGuard Labs offers real-time intelligence on the threat landscape, delivering comprehensive security updates across the full range of Fortinet’s solutions. Comprised of security threat researchers, engineers, and forensic specialists, the team collaborates with the world’s leading threat monitoring organizations, other network and security vendors, as well as law enforcement agencies:§Real-time Updates — 24x7x365 Global Operations research security intelligence, distributed via Fortinet Distributed Network to all Fortinet platforms.§Security Research — FortiGuard Labs have discovered over 170 unique zero-day vulnerabilities to date, totaling millions of automated signature updates monthly.§Validated Security Intelligence — Based on FortiGuard intelligence, Fortinet’s network security platform is tested and validated by the world’s leading third-party testing labs and customers globally.FortiCare ™ Support ServicesOur FortiCare customer support team provides global technical support for all Fortinet products. With support staff in the Americas, Europe, Middle East and Asia, FortiCare offers services to meet the needs of enterprises of all sizes:§Enhanced Support — For customers who need support during local business hours only.§Comprehensive Support — For customers who need around-the-clock mission critical support, including advanced exchange hardware replacement.§Advanced Services — For global or regional customers who need an assigned Technical Account Manager, enhanced service level agreements, extended software support, priority escalation, on-site visits and more.§Professional Services — For customers with more complex security implementations that require architecture and design services, implementation and deployment services, operational services and more.Enterprise BundleFortiGuard Labs delivers a number of security intelligence services to augment the FortiGate firewall platform. You can easily optimize the protection capabilities of your FortiGate with the FortiGuard Enterprise Bundle. This bundle contains the full set of FortiGuard security services plus FortiCare service and support offering the most flexibility and broadest range of protection all in one package.For more information, please refer to the FortiOS data sheet available at filter web traffic based on millions of real-time URL ratings. §Detect, contain and block advanced attacks automatically in minutes with integrated advanced threat protection framework. §Solve your networking needs with extensive routing, switching, WiFi, LAN and WAN capabilities.§Activate all the ASIC-boosted capabilities you need on the fastest firewall platform available.GLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 905 rue Albert Einstein Valbonne 06560Alpes-Maritimes, France Tel: +33.4.8987.0500APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6395.2788LATIN AMERICA SALES OFFICE Sawgrass Lakes Center13450 W. Sunrise Blvd., Suite 430 Sunrise, FL 33323United StatesTel: +1.954.368.9990Copyright© 2016 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary and may be significantly less effective than the metrics stated herein. Network variables, different network environments and other conditions may negatively affect performance results and other metrics stated herein. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet and any such commitment shall be limited by the disclaimers in this paragraph and other limitations in the written contract. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests, and in no event will Fortinet be responsible for events or issues that are outside of its reasonable control. Notwithstanding anything to the contrary, Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.DATA SHEET: FortiGate/FortiWiFi30EFirewall Latency (64 byte UDP packets)130 μs Firewall Throughput (Packets Per Second)180 Kpps Concurrent Sessions (TCP)900,000New Sessions/Second (TCP)15,000Firewall Policies5,000IPsec VPN Throughput (512 byte packets)75 Mbps Gateway-to-Gateway IPsec VPN Tunnels 200Client-to-Gateway IPsec VPN Tunnels 250SSL-VPN Throughput35 Mbps Concurrent SSL-VPN Users (Recommended Maximum)80IPS Throughput (HTTP / Enterprise Mix) 1600 / 240 Mbps SSL Inspection Throughput 2200 Mbps Application Control Throughput 3300 Mbps NGFW Throughput 4200 Mbps Threat Protection Throughput 5150 Mbps CAPWAP Throughput6950 Mbps Virtual Domains (Default / Maximum)5 / 5Maximum Number of FortiAPs (Total / Tunnel Mode) 2 / 2Maximum Number of FortiTokens20Maximum Number of Registered FortiClients 200High Availability ConfigurationsActive/Active, Active/Passive, ClusteringSPECIFICATIONSORDER INFORMATIONNote: A ll performance values are “up to” and vary depending on system configuration. IPsec VPN performance is based on512 byte UDP packets using AES-256+SHA1. 1. IPS performance is measured using 1 Mbyte HTTP and Enterprise Traffic Mix. 2. SSL Inspection is measured with IPS enabled and HTTP traffic, using TLS v1.2 with AES256-SHA. 3. Application Control performance is measured with 64 Kbytes HTTP traffic. 4. NGFW performance is measured with IPS and Application Control enabled, based on Enterprise Traffic Mix. 5. Threat Protection performance is measured with IPS and Application Control and Malware protection enabled, based on Enterprise Traffic Mix. 6. CAPWAP performance is based on 1444 byte UDP packets.。
无人驾驶英语作文80词

无人驾驶英语作文1Unmanned driving is a revolutionary technology that is transforming the way we travel. The basic principle of unmanned driving lies in the combination of various advanced technologies, such as sensors and algorithms.Sensors play a crucial role. They include cameras, lidar, and radar, which constantly collect information about the surrounding environment. These sensors can detect obstacles, other vehicles, pedestrians, and road signs. The collected data is then processed by complex algorithms. These algorithms analyze the information and make decisions on how the vehicle should move, accelerate, brake, or change lanes.Let's take some mainstream car brands as examples. Tesla's Autopilot system allows for semi-autonomous driving on highways. It can maintain a safe distance from the vehicle in front, adjust speed automatically, and even change lanes when the driver gives the command. Another example is Waymo, which has been testing fully autonomous vehicles in specific areas. Their technology enables the vehicle to navigate through complex urban environments.In conclusion, unmanned driving holds great promise for improving road safety and increasing travel efficiency. However, there are stillchallenges to be overcome, such as ensuring the reliability of the technology and addressing legal and ethical issues. But with continuous advancements, we can expect unmanned driving to become more common in the future.2Unmanned driving, a revolutionary technology that holds great promise for the future of transportation, also brings along numerous challenges. One of the most significant issues is determining legal liability in case of accidents. For instance, if an unmanned vehicle collides with another vehicle or causes harm to pedestrians, it is often difficult to attribute responsibility clearly. Is it the fault of the vehicle's manufacturer, the software developers, or some other party?Another complex problem is the moral dilemma. Imagine a situation where an unmanned vehicle has to make a split-second decision to avoid an accident. It might have to choose between hitting a group of pedestrians or swerving into a barrier, potentially causing harm to the passengers. How should such decisions be programmed and who decides the ethical guidelines?There have been several controversial incidents related to unmanned driving. In one case, an unmanned car failed to recognize a pedestrian crossing the road and resulted in a serious accident. This raised questions about the reliability and effectiveness of the vehicle's sensors andalgorithms.To address these challenges, clear and comprehensive laws and regulations need to be established. Manufacturers and developers should be held accountable for the safety and performance of their products. Advanced technologies such as better sensors, improved algorithms, and enhanced machine learning capabilities should be employed to improve the decision-making ability of unmanned vehicles. Moreover, public awareness and education about unmanned driving are crucial to ensure acceptance and understanding of this technology.In conclusion, while unmanned driving offers exciting possibilities, it is essential to overcome the challenges through a combination of legal measures, technological advancements, and public engagement. Only then can we fully realize the benefits of this transformative technology.3Unmanned driving is set to revolutionize transportation and our lives in the future in numerous ways. Firstly, it will significantly reduce traffic accidents. Human errors, such as distractions, fatigue, and speeding, are major causes of accidents. However, with unmanned driving, vehicles are controlled by advanced sensors and algorithms that can react instantly and precisely, minimizing the risk of crashes. For instance, in emergency situations, the unmanned system can make much quicker and more accurate decisions than a human driver.Secondly, unmanned driving will greatly enhance travel efficiency. Autonomous vehicles can communicate with each other and traffic infrastructure in real-time, optimizing routes and avoiding traffic congestion. Imagine a future where commutes are smooth and predictable, and people can use the time spent in the vehicle for productive activities like working or relaxing.In addition, new transportation models will emerge. We might see unmanned shuttles operating in specific areas, providing on-demand transportation services. Or perhaps unmanned delivery vehicles will become common, ensuring packages are delivered promptly and accurately. Moreover, unmanned taxis could offer shared rides, reducing the number of private cars on the road and further easing traffic pressure.In conclusion, unmanned driving holds immense potential to transform our transportation systems and improve our quality of life. While there are challenges to overcome, the benefits it brings are undeniable and exciting.4When it comes to the comparison between driverless cars and traditional ones, there are several notable aspects to consider. Firstly, in terms of comfort, driverless cars have a clear advantage. Imagine sitting in a driverless vehicle, where you can freely adjust your seat to the most relaxing position, and enjoy various entertainment options without thedistraction of the driver's maneuvers. For instance, on a recent journey in a driverless car, I was able to peacefully read a book and listen to my favorite music without any sudden jerks or stops.However, traditional driving also has its merits. The sense of control and the immediate response to road situations can give drivers a certain level of satisfaction. I remember a time when driving a traditional car on a winding mountain road, the thrill of handling the curves and the engine's roar beneath me made the experience quite exciting.In terms of safety, driverless cars are equipped with advanced sensors and algorithms that can potentially avoid human errors. They can react swiftly to unexpected obstacles. But traditional driving relies on the driver's vigilance and experience. Sometimes, a skilled driver can make split-second decisions that might even surpass the capabilities of the pre-programmed systems.To sum up, both driverless and traditional driving have their unique features and drawbacks. The choice between them depends on personal preferences and specific circumstances. As technology progresses, we can expect further improvements in both to enhance our transportation experiences.5The development of driverless technology is a remarkable advancement in the modern era. With the rapid progress of science andtechnology, this field is evolving at an astonishing pace. The integration of 5G technology has brought about revolutionary changes to driverless systems. The high-speed and low-latency characteristics of 5G enable real-time data transmission, allowing vehicles to respond promptly to various road conditions and obstacles.The global market for driverless technology holds immense potential. It is predicted that by a certain year, a significant percentage of new vehicles sold worldwide will incorporate at least some level of autonomous driving features. For instance, major automotive companies and tech giants are investing heavily in research and development. Some have achieved breakthroughs in areas such as sensor accuracy and algorithm optimization, which greatly enhance the safety and reliability of driverless cars.However, despite these promising developments, there are still challenges to overcome. Issues such as legal and ethical considerations, as well as public acceptance, need to be addressed. But with continuous innovation and collaboration among industries, the future of driverless technology looks bright. It has the potential to transform not only the transportation sector but also our daily lives, making travel more efficient, comfortable, and safe.。
神奇的记忆芯片英语作文

神奇的记忆芯片英语作文Incredible Memory Chips: Revolutionizing Data Storage.In the ever-evolving realm of technology, memory chips stand as the cornerstone of data storage. They serve as the repositories of our digital lives, housing the vast amounts of information we create, access, and manipulate daily. However, conventional memory chips have reached a plateau in terms of capacity and performance, prompting the search for innovative solutions to meet the insatiable demand for data storage. This has led to the development of a new generation of memory chips, known as incredible memory chips, that promise to revolutionize the way we store and process data.At the heart of these incredible memory chips lies a groundbreaking technology that breaks free from the limitations of traditional memory designs. Unlike conventional memory chips that store data in binary form (0s and 1s), incredible memory chips employ a novelapproach called multi-level cell (MLC) storage. MLC enables each memory cell to store multiple bits of data,effectively increasing the storage density of the chip. This remarkable innovation has the potential tosignificantly boost the capacity of memory devices, allowing for the storage of massive amounts of data in a compact form.Moreover, incredible memory chips leverage advanced materials and fabrication techniques to achieve unprecedented performance levels. They utilize materials with exceptional electrical and thermal properties, minimizing data loss and energy consumption. Additionally, innovative manufacturing processes ensure the fabrication of memory cells with high precision and reliability, resulting in reduced latency and improved data integrity.The implications of incredible memory chips for various industries are profound. For the consumer electronics sector, these chips will pave the way for the development of compact devices with exceptional data storage capabilities. Smartphones, laptops, and tablets will beable to store vast libraries of photos, videos, and music without compromising on portability and performance.In the field of cloud computing, incredible memory chips will empower data centers with the capacity to handle the ever-growing deluge of data. These chips will enable the efficient storage and processing of massive datasets, facilitating advanced data analytics, machine learning, and artificial intelligence applications.Furthermore, incredible memory chips will play acrucial role in the development of autonomous systems, such as self-driving cars and drones. They will provide these systems with the ability to store and process large amounts of sensory data in real-time, enabling them to navigate complex environments and make informed decisions.The development of incredible memory chips marks a significant milestone in the evolution of data storage technology. These chips promise to redefine the way we store and process data, unlocking new possibilities for innovation across a wide range of industries. As the demandfor data storage continues to surge, incredible memory chips will undoubtedly play a pivotal role in shaping the future of the digital world.。
无线传感器网络的路由算法

AODV协议1. 概述Nokia研究中心开发,自组网路由协议的RFc标准,它是DSR和DSDV的综合,借用了DSR中路由发现和路由维护的基础程序,及DSDV的逐跳(Hop-by-HoP)路由、目的节点序列号和路由维护阶段的周期更新机制,以DSDV为基础,结合DSR中的按需路由思想并加以改进。
它应用于无线自组织网络中进行路由选择的路由协议, 它能够实现单播和多播路由。
该协议是自组织网络中按需生成路由方式的典型协议。
用于特定网络中的可移动节点。
它能在动态变化的点对点网络中确定一条到目的地的路由,并且具有接入速度快,计算量小,内存占用低,网络负荷轻等特点。
它采用目的序列号来确保在任何时候都不会出现回环,避免了传统的距离向量协议中会出现的很多问题。
AODV最初提出的目的是为了建立一个纯粹的按需路由的系统。
网络中的节点完全不依赖活动路径,既不维护任何路由信息,也不参与任何定期的路由表交换。
节点不需要发现和维护到其他节点的路由,除非两个节点需要通讯或者节点是作为中间转发节点提供特定的服务来维护另外两个节点的连接性。
提出:With the goals of minimizing broadcasts and transmission latency when new routes are needed, we designed a protocol to improve up on the performance characteristics of DSDV in the creation and maintenance of ad-hoc networks.2. 特点优点:(1)基本路由算法为距离向量算法,但有所改进,思路简单、易懂。
(2)按需路由协议,而且节点只存储需要的路由,减少了内存的需求和不必要的复制。
(3)采用UDP 封装,属于应用层协议。
(4)支持中间节点应答,能使源节点快速获得路由,有效减少了广播数,但存在过时路由问题。
优化传输方案英文

Optimizing the Transmission SolutionAbstractIn today’s rapidly evolving digital world, efficient and reliable data transmission is of paramount importance. This document aims to present an optimized transmission solution that ensures seamless data transfer while maximizing speed and minimizing errors. By leveraging advanced technologies and adopting best practices, businesses can significantly enhance their data transmission capabilities.IntroductionData transmission plays a crucial role in modern communication systems. It involves the transfer of information from one location to another, either within a local network or over the Internet. However, traditional transmission methods often suffer from issues such as slow speeds, high latency, and increased data loss. This calls for an optimized transmission solution that addresses these challenges and provides a robust and efficient method for data transfer.Challenges in Data TransmissionSeveral factors contribute to the inefficiency of data transmission. Some of the major challenges include:1.Bandwidth Limitations: Insufficient network bandwidth can lead toslow data transfer speeds, especially when dealing with large files or highvolumes of data.2.Packet Loss and Errors: Network congestion and transmissionerrors can result in packet loss, reducing the reliability and integrity of datatransmission.tency: The time delay between data being sent and received canimpact real-time applications, such as audio or video streaming, where delays can lead to a poor user experience.4.Security: Ensuring data security during transmission is essential toprotect sensitive information from being intercepted or tampered with.Optimized Transmission Solution1. Utilize Data CompressionData compression techniques can significantly reduce the size of data files, optimizing transmission by reducing the required bandwidth and speeding up the transfer process. By compressing files before transmission and decompressing them at the receiving end, both the transmission time and bandwidth utilization can be substantially improved.2. Implement Error Correction CodesTo address packet loss and errors during transmission, error correction codes (ECC) can be employed. ECC adds additional redundant information to the transmitted data, allowing the receiving end to identify and correct errors. This technique enhances data integrity and reduces the need for retransmission, thereby improving overall transmission efficiency.3. Prioritize Quality of Service (QoS)By implementing Quality of Service (QoS) mechanisms, network traffic can be prioritized based on the specific requirements of different applications. QoS ensures that real-time applications, such as video conferencing or VoIP, receive sufficient bandwidth and lower latency, enabling smoother and uninterrupted data transmission.4. Utilize Parallel TransmissionParallel transmission involves dividing a large data file into smaller segments and transmitting them simultaneously through multiple channels. This technique can significantly reduce transmission time, especially when dealing with large datasets. However, it requires sufficient bandwidth and network infrastructure capable of supporting parallel transmission.5. Implement Encryption and AuthenticationData transmission security is paramount to protect sensitive information from unauthorized access or tampering. Implementing encryption algorithms such as SSL/TLS can ensure that data is transmitted securely over the network. Additionally, authentication mechanisms should be implemented to verify the identity of the sender and receiver, further enhancing data security.ConclusionAchieving optimized data transmission is crucial for businesses and individuals relying on fast and reliable data transfer. By incorporating data compression, error correction codes, QoS mechanisms, parallel transmission, andencryption/authentication techniques, organizations can significantly enhance their transmission capabilities. It is essential to evaluate the specific requirements and available resources before implementing an optimized transmission solution to maximize its effectiveness. With an optimized transmission solution in place, businesses can improve productivity, enhance customer experiences, and strengthen data security.。
软件工程_东北大学中国大学mooc课后章节答案期末考试题库2023年

软件工程_东北大学中国大学mooc课后章节答案期末考试题库2023年1._______ is a discipline whose aim is the production of fault-free software,delivered on time and within budget, that satisfies the client's needs._______是一个学科,其目标是生产出满足客户的需求的、未超出预算的、按时交付的、没有错误的软件。
答案:2.The relationship between whole-class and part-classes is called ______.整体和部分类之间的关系被称为______。
答案:aggregation3.The relationship between super-class and subclasses is called ______.超类和子类之间的关系称为______。
答案:inheritance4.The strategy of inheritance is to use inheritance wherever _______.继承的策略是在_______的情况下使用继承。
答案:appropriate5._____is to encapsulate the attributes and operations in an object, and hides theinternal details of an object as possible. _____是为了在一个对象中封装属性和操作,并尽可能隐藏对象的内部细节。
Data encapsulation6.Two modules are ________ coupled if they have write access to global data.如果两个模块对全局数据具有写访问权限,则是________耦合。
节点方案英文

节点方案英文Node SchemeIntroductionIn today's rapidly evolving technological landscape, the need for efficient and reliable networks is paramount. One crucial aspect of designing a network is determining the appropriate node scheme. A node scheme refers to the arrangement and configuration of network nodes, which are the essential building blocks of any network infrastructure. This article aims to explore the fundamental principles and considerations involved in devising a node scheme, focusing on key aspects such as scalability, redundancy, and network optimization.ScalabilityScalability is a vital factor when it comes to designing a node scheme. It refers to the network's ability to handle an increasing workload and expand in response to growing demands. To achieve scalability, a node scheme should incorporate modular architectures that allow for easy addition or removal of nodes without disrupting the entire network. Additionally, the use of virtualization technologies, such as cloud computing, can enhance scalability by enabling seamless resource allocation and management.RedundancyEnsuring network reliability is another crucial aspect of a well-designed node scheme. Redundancy, which involves duplicating network components, plays a significant role in achieving this goal. By incorporating redundantnodes, failures or disruptions in one part of the network can be mitigated as traffic is rerouted through alternative paths. Redundancy can be achieved at various levels, including hardware redundancy, where multiple physical devices are deployed, and software redundancy, which involves implementing failover mechanisms and backup systems.Network OptimizationOptimizing network performance is a key objective of any node scheme. This involves fine-tuning various parameters to ensure efficient data transmission and minimize latency. An effective node scheme should consider factors such as bandwidth allocation, routing protocols, and network traffic management. By applying load balancing techniques, network administrators can evenly distribute the workload across nodes, preventing bottlenecks and optimizing overall performance.Security ConsiderationsWhen designing a node scheme, security should be paramount. In an interconnected world, networks are vulnerable to various threats, such as unauthorized access, data breaches, and malware attacks. Implementing robust security measures, including authentication mechanisms, encryption protocols, and intrusion detection systems, is essential to safeguard network integrity. The node scheme should take into account these security considerations and provide a framework for secure data transmission and protection against potential threats.Case Study: Enterprise NetworkTo better understand the practical implementation of a node scheme, let's consider a case study of an enterprise network. In this scenario, the node scheme should cater to the organization's specific requirements, such as seamless communication, data exchange, and resource sharing.The node scheme for an enterprise network might consist of a centralized hub, where critical services and central data repositories are located. From this central hub, various branches or remote locations can be connected through distributed nodes, ensuring efficient communication and data synchronization. The deployment of redundant nodes at critical points within the network provides resilience and fault tolerance, minimizing downtime and ensuring business continuity.ConclusionIn conclusion, a well-designed node scheme is fundamental to building a robust and efficient network infrastructure. By considering scalability, redundancy, network optimization, and security, network architects can develop a node scheme that meets the specific requirements of any organization or application. Understanding the intricacies of node schemes is crucial in today's interconnected world, where networks are the backbone of modern communication and information exchange.。
人工智能与5g时代已悄然来临英语作文

人工智能与5g时代已悄然来临英语作文Artificial Intelligence and the 5G Era: Shaping the FutureAs the world rapidly evolves, the convergence of two groundbreaking technologies – Artificial Intelligence (AI) and 5G –has ushered in a new era of unprecedented possibilities. This dynamic duo is poised to transform every aspect of our lives, from the way we communicate and access information to how we tackle complex challenges and envision the future.The advent of 5G, the fifth-generation wireless network, has ushered in a new era of lightning-fast connectivity, enabling real-time data transmission and seamless integration of various devices. This technological breakthrough has paved the way for a more interconnected world, where the Internet of Things (IoT) can thrive, and the potential for remote collaboration, telemedicine, and autonomous vehicles becomes a tangible reality.Artificial Intelligence, on the other hand, has been making significant strides in recent years, revolutionizing various industries and sectors. From machine learning algorithms that can analyze vast amounts of data to natural language processing that allows for more intuitivehuman-machine interactions, AI has demonstrated its ability to augment and enhance human capabilities in remarkable ways.The synergistic relationship between AI and 5G is where the true magic happens. The high-speed, low-latency connectivity of 5G empowers AI systems to access and process data in real-time, enabling faster decision-making and more responsive applications. This, in turn, unlocks new frontiers in fields such as smart cities, precision agriculture, and personalized healthcare.In the realm of smart cities, the integration of AI and 5G can transform urban landscapes. Intelligent traffic management systems can leverage AI-powered algorithms to optimize traffic flow, reduce congestion, and improve air quality. Predictive maintenance of infrastructure, such as roads and utilities, can be enhanced through AI-driven analytics, ensuring efficient resource allocation and proactive maintenance. Furthermore, the combination of AI and 5G can enable seamless communication between various city systems, facilitating the development of integrated and responsive urban environments.In the agricultural sector, the fusion of AI and 5G is poised to revolutionize precision farming. Drones equipped with AI-powered sensors can collect real-time data on soil conditions, crop health, and weather patterns, enabling farmers to make informed decisions andoptimize their operations. AI-driven irrigation systems can precisely monitor and adjust water usage, minimizing waste and maximizing productivity. Additionally, 5G's low latency and high bandwidth can facilitate the remote monitoring and control of autonomous farming equipment, revolutionizing the way we approach food production.The healthcare industry is another domain where the convergence of AI and 5G is transforming the landscape. Telehealth and remote patient monitoring become more accessible and effective with the high-speed connectivity of 5G. AI-powered diagnostic tools can analyze medical images and patient data with unprecedented accuracy, aiding in early detection and personalized treatment plans. Furthermore, the integration of AI and 5G can enable real-time data sharing between healthcare providers, facilitating collaborative decision-making and improving patient outcomes.Beyond these specific applications, the broader implications of AI and 5G are far-reaching. The ability to process and analyze vast amounts of data in real-time can unlock new frontiers in scientific research, enabling breakthroughs in fields such as climate change mitigation, drug discovery, and materials science. The potential for AI-powered automation and robotics, coupled with the seamless connectivity of 5G, can revolutionize various industries, improving efficiency, productivity, and safety.However, as with any transformative technology, the integration of AI and 5G also raises important ethical and societal considerations. Issues such as data privacy, algorithmic bias, and the impact on employment must be carefully addressed to ensure the responsible and equitable development of these technologies. Policymakers, industry leaders, and the public must work together to establish robust governance frameworks and ethical guidelines that prioritize the well-being of individuals and communities.In conclusion, the convergence of Artificial Intelligence and 5G is ushering in a new era of unprecedented possibilities. From smart cities and precision agriculture to personalized healthcare and scientific breakthroughs, the synergistic relationship between these two technologies holds the power to transform our world in profound and positive ways. As we navigate this exciting and rapidly evolving landscape, it is crucial that we approach it with foresight, responsibility, and a steadfast commitment to shaping a future that benefits all of humanity.。
distilling the knowledge in a neural network

distilling the knowledge in a neural networkKnowledge Distilling Is a method of model compression, which refers to the method of using a more complex Teacher model to guide a lighter Student model training, so as to maintain the accuracy of the original Teacher model as far as possible while reducing the model size and computing resources. This approach was noticed, mainly due to Hinton's paper Distilling the Knowledge in a Neural Network.Knowledge Distill Is a simple way to make up for the insufficient supervision signal of classification problems. In the traditional classification problem, the goal of the model is to map the input features to a point in the output space, for example, in the famous Imagenet competition, which is to map all possible input images to 1000 points in the output space. In doing so, each of the 1,000 points is a one hot-encoded category information. Such a label can provide only the supervision information of log (class) so many bits. In KD, however, we can use teacher model to output a continuous label distribution for each sample, so that the supervised information is much more available than one hot's. From another perspective, you can imagine that if there is only one goal like label, the goal of the model is to force the mapping of each class in the training sample to the same point, so that the intra-class variance and inter-class distance that are very helpful for training will be lost. However, using the output of teacher model can recover this information. The specific example is like the paper, where a cat and a dog are closer than a cat and a table, and if an animal does look like a cat or a dog, it can provide supervision for both categories. To sum up, the core idea of KD is that "dispersing" is compressed to the supervisory information of a point, so that the output of student model can be distributed as much as the output of match teacher model as possible. In fact, to achieve this goal, it is not necessarily teacher model to be used. The uncertain information retained in the data annotation or collection can also help the training of the model.。
华硕WiFiAccess Point产品说明书
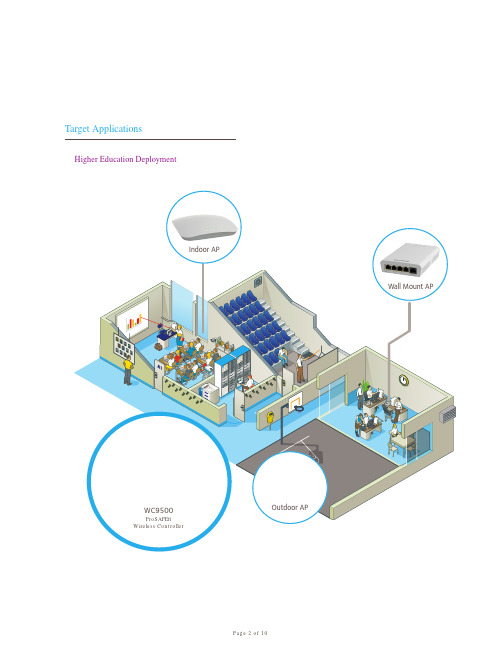
The NETGEAR WC9500 High Capacity Wireless Controller supports rapid mobility across VLANs and subnets including 802.11i preauthentication and fast roaming support (FRS). Seamless L2 and L3 roaming provides support for latency-sensitive applications such as video, audio and voice over wireless. WiFi Multimedia (WMM) advanced prioritization extends WiFi s high-quality end-user experience to voice applications (VoWiFi).
WAC730
Description
Part Numbers
WAC720 WNDAP660
Typical Deployment
Product Image (Front)
Product Image (Back)
WNDAP620
WNDAP360
WNDAP350 WNAP320 WNAP210 WN370 WND930
Page 3 of 10
Features
Scalable Architecture
The NETGEAR WC9500 High Capacity Controller supports up to 200 APs and is upgradable in 10, 50, 100, or 200 APs via so ware licenses. Stackable up to three controllers, a WC9500 High Capacity Controller stack can support up to 600 access points with a single interface. The WC9500 o ers redundancy for always-on reliability.
Minimizing message processing latency in a communi

专利名称:Minimizing message processing latency in a communication network发明人:Pöyhönen, Petteri,Rajahalme, Jarno申请号:EP04396009.5申请日:20040209公开号:EP1463267B1公开日:20080625专利内容由知识产权出版社提供摘要:The present invention concerns a method and a system for minimizing message processing latency in a communication network. A message from a first node is received at a second node which message requires an acknowledgement message, preferably of Boolean type. Functionalities required for processing the message are partitioned into at least a first part and a second part. The first part comprises a minimum set of functionalities required to generate the acknowledgement message. The functionalities of the first part are executed. The acknowledgement message is generated and transmitted to the first node after to finishing the functionalities of the first part. The present invention makes it possible to effectively minimize the perceived message processing latency. It is also possible to dynamically optimize the latency according to available resources.申请人:NOKIA CORP地址:FI国籍:FI代理机构:Simmelvuo, Markku Kalevi更多信息请下载全文后查看。
英语作文-提高互联网游戏服务的用户参与度方法

英语作文-提高互联网游戏服务的用户参与度方法Enhancing User Engagement in Internet Gaming Services。
In the dynamic landscape of online gaming, user engagement is the cornerstone of success for any platform. With the ever-expanding array of gaming options available to players, it has become imperative for service providers to continually innovate and improve upon their offerings to ensure a high level of user participation. In this article, we will explore effective strategies to enhance user engagement in internet gaming services.First and foremost, creating a seamless and immersive gaming experience is paramount. This entails optimizing game performance, ensuring smooth gameplay, and minimizing latency issues. By investing in robust server infrastructure and employing advanced networking technologies, gaming platforms can provide users with a lag-free experience that keeps them coming back for more.Moreover, personalization plays a crucial role in fostering user engagement. By leveraging data analytics and machine learning algorithms, gaming services can tailor the gaming experience to the preferences and behaviors of individual users. This could include recommending personalized game suggestions, offering targeted in-game promotions, or providing customized challenges based on past performance.In addition to personalization, community building is essential for fostering a sense of belonging among users. Introducing features such as chat rooms, forums, and social media integration allows players to connect with like-minded individuals, share experiences, and form meaningful relationships within the gaming community. Furthermore, organizing tournaments, competitions, and events encourages healthy competition and camaraderie among players, driving up engagement levels.Furthermore, regular content updates and expansion packs are instrumental in keeping users engaged over the long term. By introducing new game modes, characters, maps, and quests, gaming services can reignite interest and excitement among existing players while also attracting new ones. Additionally, soliciting feedback from the community and actively incorporating user suggestions into future updates demonstrates a commitment to user satisfaction and engagement.Another effective strategy for enhancing user engagement is gamification. By incorporating elements such as achievements, badges, leaderboards, and rewards systems, gaming services can incentivize desired behaviors and encourage continued participation. This not only adds an element of fun and competition to the gaming experience but also provides users with tangible incentives for investing time and effort into the platform.Moreover, fostering a sense of ownership and creativity among users can significantly enhance engagement levels. Introducing user-generated content tools, such as level editors, character customization options, and modding support, empowers players to express their creativity and contribute to the evolving ecosystem of the game. This not only increases the longevity of the gaming experience but also fosters a deeper sense of attachment and investment among users.Lastly, maintaining open and transparent communication with users is essential for building trust and loyalty. Keeping users informed about upcoming updates, addressing their concerns and grievances in a timely manner, and soliciting their input on important decisions fosters a sense of partnership and mutual respect. By cultivating a strong and engaged community, gaming services can create a virtuous cycle of feedback, innovation, and growth.In conclusion, enhancing user engagement in internet gaming services requires a multifaceted approach that encompasses technical optimization, personalization, community building, content updates, gamification, user empowerment, and transparent communication. By implementing these strategies effectively, gaming platforms can cultivate a vibrant and thriving ecosystem that captivates and retains users in the long run.。
mt5标准接口规范文档

mt5标准接口规范文档The MT5 standard interface specification document is essential for understanding the technical details and requirements for integrating with the MT5 trading platform. MT5标准接口规范文档对于理解与MT5交易平台集成的技术细节和要求至关重要。
This document outlines the necessary guidelines and protocols that must be followed to ensure seamless communication between the trading platform and external systems. 这份文档概述了必须遵循的必要准则和协议,以确保交易平台与外部系统之间的无缝通信。
From a technical standpoint, the MT5 standard interface specification document provides detailed information on the various APIs and protocols supported by the platform. 从技术角度来看,MT5标准接口规范文档提供了有关平台支持的各种API和协议的详细信息。
Developers and system integrators can refer to this document to understand the specific requirements for integrating their systems with MT5. 开发人员和系统集成商可以参考这份文档,了解与MT5集成其系统的具体要求。
preempt patch工作机制

preempt patch工作机制Preempt patch is a mechanism designed to enhance the responsiveness and performance of a system by minimizing the latency caused by long-running tasks or processes. Its working principle revolves around the preemption of low-priority tasks, allowing high-priority tasks to take precedence and execute without delay.Preempt patch工作机制旨在通过最小化由长时间运行的任务或进程引起的延迟,来提高系统的响应性和性能。
其工作原理主要围绕低优先级任务的抢占,允许高优先级任务优先执行,从而避免延迟。
At the core of the preempt patch lies the concept of priority scheduling. The system assigns different priority levels to tasks based on their importance and urgency. When a high-priority task arrives, the preempt patch mechanism intervenes and temporarily halts the execution of any low-priority tasks that are currently running.preempt patch工作机制的核心是优先级调度。
系统根据任务的重要性和紧急性为其分配不同的优先级。
当高优先级任务到达时,preempt patch 机制会介入,并暂时中断当前正在执行的任何低优先级任务。
苹果13的英语作文

苹果13的英语作文Title: The Impact of Apple's iPhone 13: A Revolutionary Device。
The release of Apple's iPhone 13 has undoubtedlystirred a whirlwind of excitement and speculation in the tech world. This latest iteration of the iconic smartphone promises to deliver groundbreaking features and improvements, setting new standards for innovation and user experience. In this essay, we will delve into the various aspects of the iPhone 13 and explore its significance in shaping the future of mobile technology.First and foremost, the iPhone 13 boasts significant advancements in terms of performance and capabilities. Equipped with Apple's latest A15 Bionic chip, it offers unparalleled speed and efficiency, ensuring seamless multitasking and smooth user experience. Whether it's gaming, streaming, or productivity tasks, the iPhone 13 sets a new benchmark for performance in the smartphoneindustry.Moreover, the iPhone 13 introduces several notable enhancements to its camera system, catering to the growing demand for high-quality photography and videography. With improved low-light performance, enhanced image stabilization, and advanced computational photography features, users can capture stunning images and videos in any environment. The addition of Cinematic mode further elevates the storytelling potential of iPhone photography, allowing users to create professional-looking videos with ease.In terms of design, the iPhone 13 retains the sleek and minimalist aesthetic that Apple is renowned for, while also introducing subtle refinements to enhance durability and usability. The Ceramic Shield front cover and aerospace-grade aluminum frame provide added protection against drops and accidents, ensuring that the device remains pristine and functional even in the harshest conditions. Additionally, the introduction of new color options adds a touch of personalization, allowing users to express theirindividuality through their choice of device.One of the most anticipated features of the iPhone 13is its support for 5G connectivity, ushering in a new eraof high-speed mobile internet and network performance. With 5G capabilities, users can experience lightning-fast download and upload speeds, reduced latency, and enhanced reliability, unlocking a world of possibilities for streaming, gaming, and communication on the go. The integration of 5G technology further solidifies Apple's commitment to staying at the forefront of mobile innovation and providing users with the best possible experience.Beyond its technical specifications, the iPhone 13 also embodies Apple's dedication to sustainability and environmental responsibility. The device is made from recycled materials and utilizes energy-efficient components, reducing its carbon footprint and minimizing environmental impact. Furthermore, Apple's commitment to productlongevity and recycling initiatives ensures that the iPhone 13 is not only a cutting-edge device but also a sustainable choice for conscientious consumers.In conclusion, the release of the iPhone 13 marks a significant milestone in the evolution of mobile technology. With its groundbreaking features, unparalleled performance, and commitment to sustainability, the iPhone 13 sets a new standard for excellence in the smartphone industry. As we embrace the possibilities of this revolutionary device, we are reminded once again of Apple's enduring legacy of innovation and its relentless pursuit of excellence.。
Harrier AF-Zoom IP摄像头最低延迟获取指南说明书

TECHNICAL NOTE:OBTAINING THE LOWEST LATENCY FROM YOUR HARRIER AF-ZOOM IP CAMERASummaryThis Technical Note introduces IP cameras and the latency associated with IP video transmission; it also explains how to achieve the lowest latency from a Harrier AF-Zoom IP camera or Harrier IP Camera Interface Board, and what rates can beexpected. With some Harrier cameras, latency can be as low as 140ms, however many factors will affect this, including the network configuration and type of PC used.BackgroundAn IP (Internet Protocol) camera is a digital camera that transmits and receives data over a network or the internet. An IP camera uses its own IP address to connect to a network and doesn’t rely on a connection to a PC or alternative host device. IP cameras capture images, compress them (usually using H.264 or H.265 encoders) and then transmit them over an Ethernet network, commonly in the form of streaming real-time video. They may be used with a wired network (connected via an Ethernet cable to a switch/router/PC), or wirelessly (via a WiFi router/access point).Controlling Harrier AF-Zoom IP cameras is straightforward. As they are ONVIF Profile S compatible, user developed applications, or any Profile S-based third-party software, can easily control the camera. Harrier AF-Zoom IP cameras also offer a wide range of other advanced camera features (e.g. day/night functionality, optical zoom, WDR, etc.) that can all be controlled remotely. In addition, the IP video stream is available in three different profiles, each with different video compression settings.Understanding latencyFor the purpose of this Technical Note, latency is defined as the delay from when an image iscaptured by the camera lens to when it is observable on a video display (glass to glass). Variability in latency is referred to as jitter, so a system with high variation in latency will have high jitter.Image capture and video data transmission will always be subject to latency because of the unavoidable acquisition, transport and processing delays between various system components. Latency in vision systems is typically recorded in milliseconds (ms).The level of acceptable latency within a vision system depends on the application. For example, an ANPR parking system can tolerate high latency as there is no short critical time requirement in theapplication. However, a moving remote-operated robot or vehicle requires the lowest latency Figure 1 – Harrier 10x AF-Zoom IP/HDMI Camera (Tamron MP3010M-EV)possible so that the operator can respond quickly to the changes in the environment with minimal delay; a slow response time can result in inefficient operation and even damage to the vehicle or other nearby objects.Human perception also plays a part in determining if latency levels are acceptable – anything taking longer than 200-300ms tends to feel sluggish and awkward to control, so ideally a real-time user-controlled system will aim for less than this.Sources of latency and optimizationsMany different elements of the vision system add latency to the overall data transmission. The diagram below (Figure 2) shows where latency may be introduced.Figure 2 - Elements that may add latency to vision systemsMost Harrier IP cameras consist of an AF-Zoom block camera module (with LVDS output) connected to a Harrier IP Camera Interface Board that converts the LVDS video to IP format (see Figure 1).AF-Zoom block cameras are sophisticated imaging instruments and they have many image processing features (e.g. auto white balance, auto exposure, lens distortion compensation, noise reduction, image stabilization, text and color overlays, privacy screens, motion alerts, and more). However, the processing required for these features takes time, increasing the latency of the camera video. A typical AF-Zoom camera will have latency of 2-6 frames depending on the camera and the processing operations performed. The latency is also usually related to the video frame rate; e.g. features that require the processing of two image frames can only be applied after two frames have been captured, giving a minimum latency of at least a two frame time period. If the frame rate is faster, this time limitation is smaller - hence there is a direct relationship between frame rate and video output latency. To minimize latency in the block camera you should set a fast frame rate and not use complex image processing features; your camera may have low latency modes that can be enabled using a VISCA command (note: setting these modes usually limits the processing features of the camera).The Harrier IP Camera Interface Board receives the image data from the camera module and can perform additional image processing such as the addition of overlays or image scaling. The images are then H.264 compressed and converted to a data packet format (IP/UDP) that can be sent to the network. Latency is reduced by using hardware to encode the video, and by optimizing/minimizing the video processing required. The latency of the Harrier IP Camera Interface Board is ~80ms.The network receives the IP packets and routes them to the host computer. Receiving and transmitting the data is usually relatively fast and free of jitter. However, a complex and busy network will incur longer delays and more jitter as the packets may get held up and/or routed over different network paths. For low latency the network should be as simple as possible and not carry high amounts of unrelated data. A point-to-point (camera to host PC) connection will deliver the lowest latency and jitter.As shown in Figure 2, the receiving computer/PC will add further latencies; data decompression and (optional) image processing contributing the greatest delays within the PC. Selecting a high-performance computer that can receive, decode, process and display the images quickly and without interruption will help deliver low latency, low jitter video transmission.The video rendering software used to capture and display the video can also make a significant difference to the latency. Some software buffers several frames of data so that it can perform additional image processing to improve the image quality and deliver a smooth video stream. To reduce latency, ensure that the software can be, and is, set up to do minimal buffering and processing of the video stream before it sends the images to the screen. If a TCP/IP packet is lost the networking system will request that the packet be resent – this can cause the software to pause the video while it is waiting for the missing packet, other video data that is arriving is buffered, delaying the video stream. Some video renderers preserve this buffer/delay resulting in a longer latency, so you should check the properties of your video renderer and potentially use UDP packets instead of TCP. Missing UDP packets are not tracked/recovered and are simply lost.Finally comes the latency of the display itself (often called input/display lag by gamers). This delay is caused by the time taken for the monitor electronics to receive and display the image on the LCD screen and can vary between 5ms and 68ms. Note that this is not the same as the pixel response time, which is the time taken for a pixel to change from one color to another. Some televisions and monitors/displays buffer a whole frame before displaying the image, adding a minimum latency of one frame period (~16.7ms @60fps). Others may also perform image processing to scale the image (to match the native display resolution) and/or reduce image artefacts (e.g. HDR, dynamic brightness/contrast, edge sharpening, comb filtering, etc.). These all add latency to the display of the image. For this reason, many modern televisions and displays offer a "game mode" setting that turns off the additional processing and minimizes the latency. Some gaming monitors can run at higher fame rates (e.g.120Hz); this reduces the monitor latency in the same way that setting your camera to the highest frame rate does.For minimum latency, carefully check the features of your display, turn off all processing options that add latency and set the video resolution to be the same as the native monitor resolution (so that no image scaling is required and hence the latency is optimized). Some monitors may even have some input ports that are lower latency than others!For low latency video, keep the system as simple as possible and select your hardware and software carefully and with configuration for low latency in mind. Design the system to perform fewer, more specific tasks and eliminate unnecessary additional image processing where possible. Implement a latency optimized system and use hardware acceleration to minimize/eliminate delays and reduce jitter.IP Ethernet latency measurementThis is how the latency of the Harrier IP camera module was measured:•An application that shows the view of the camera on the PC monitor/display/screen is required e.g. ONVIF Device Manager, GStreamer. For these measurements ONVIF DeviceManager (ODM) was used•The camera was pointed at the PC screen.• A timer with a fast screen refresh should be placed in the view of the camera.In this case the Windows Clock application was run in stopwatch mode and displayed on the screen so that it was in the view of the camera.•The ODM application was opened and the camera video displayed. The ODM window was positioned so that the image of the timer in ODM was also in the view of the camera. Screen shots were made and glass-to-glass latency calculated from the difference in the two timerimages shown on the display. Multiple measurements were made.•As the timer display, camera and output monitor each have their own asynchronous refresh rates the calculated latency varies as these timings go in and out of phase resulting in jitter of approximately 40-50ms.System Setup:Harrier IP Camera:•Profile: balanced_h264 (bitrate=0).•Firmware version: v3.2•Connection: 1000BASE-T (wired)•Type: TCPPC/software:•ThinkPad X1 carbon 6th,Intel(R) Core(TM) i7-8550U CPU @1.80GHz / 1.99 GHz,•Thinkpad USB-C dock, DK1633•Windows 10 Pro 22H2•ODM v2.2.250•Microsoft Windows Clock application•Dell monitor U2412MFigure 3: Set up for recording latency measurementsLatency measurementsCamera Resolution & FPS Encoding Interval* Latency (ms) Harrier 10x AF-Zoom IP Camera1080p60 1 ~140AS-CIB-IP-001-10LHD-AHarrier 10x AF-Zoom IP Camera1080p60 2 ~140AS-CIB-IP-001-10LHD-AHarrier 10x AF-Zoom IP Camera1080p30 1 ~210AS-CIB-IP-001-10LHD-AHarrier 10x AF-Zoom IP/HDMI Camera1080p60 1 ~180 (Tamron MP3010M-EV)AS-CIB-IP-00x-3010-AHarrier 10x AF-Zoom IP/HDMI Camera1080p60 2 ~180 (Tamron MP3010M-EV)AS-CIB-IP-00x-3010-AHarrier 10x AF-Zoom IP/HDMI Camera1080p30 1 ~280 (Tamron MP3010M-EV)AS-CIB-IP-00x-3010-AHarrier 36x AF-Zoom IP Camera1080p30 1 ~230AS-CIB-IP-00x-36LGHD-AHarrier 40x AF-Zoom IP Camera1080p60 1 ~140AS-CIB-IP-00x-40LHD-AHarrier 40x AF-Zoom IP Camera1080p60 2 ~140AS-CIB-IP-00x-40LHD-AHarrier 40x AF-Zoom IP Camera1080p30 1 ~200AS-CIB-IP-00x-40LHD-AHarrier 30x AF-Zoom IP Camera1080p60 1 ~210 (Sony FCB-EV7520A)AS-CIB-IP-00x-7520A-AHarrier 30x AF-Zoom IP Camera1080p60 2 ~220 (Sony FCB-EV7520A)AS-CIB-IP-00x-7520A-AHarrier 30x AF-Zoom IP Camera1080p30 1 ~310 (Sony FCB-EV7520A)AS-CIB-IP-00x-7520A-ANOTE: The Harrier IP Camera Interface Board introduces a latency of circa 80ms depending on the mode used. Most of the remaining latency comes from the AF-Zoom block camera and other parts of the system. The Harrier 23x AF-Zoom IP 4K camera does not require a camera interface board as processing is carried out directly on the camera.* Harrier 1080p30 special low latency modeHarrier IP cameras with a Harrier camera interface board have a special 1080p30 low latency configuration. This mode delivers 1080p30 video with the same camera latency as 1080p60 video by configuring the camera to 1080p60 but setting the IP video encoder to only process every other frame (Encoding Interval (E.I) = 2). Some AF-Zoom block cameras, including Tamron and Sony cameras, also have low latency modes that can be turned on – however these can restrict the ability of the camera to process the video data.The value of the Encoding Interval can be set in ONVIF Device Manager or in the ONVIF element: VideoEncoderConfiguration:: RateControl.Figure 4: Latency measurements in millisecondsSummaryHarrier IP cameras bring extremely low latency to the video system. While each element of a vision system will add to the overall latency, developers can address aspects of each component to reduce this as much as possible. In this note, we have made these recommendations to minimize latency: •Set a high frame rate on the AF-Zoom camera (60Hz)•Do not use processing-intense AF-Zoom camera features•Enable low latency mode if the AF-Zoom camera has one•If the volume of the data at the high frame rate is too high set the Harrier IP Camera Interface board Encoding Interval to 2 to deliver 1080p30 with ~1080p60 latency•Use a hardware accelerated IP processing interface board such as the Harrier IP board•Operate a simple network that doesn’t carry high amounts of unrelated data•Use a point-to-point network connection for the lowest latency and jitter•Select a high-performance computer that can receive, decode, process and display images quickly without interruption•Select software which can be set to perform minimal buffering and video processing•Ensure that the display screen has minimal latency.Depending on the model and mode/image processing features used, the AF-Zoom camera will add between 50-200ms of latency to the video. The Harrier IP Camera Interface Board will add approximately 80ms of additional latency. By configuring the various components of the system, you can obtain the lowest latency results for your vision system without additional complexity or cost. FAQsHow do I set up my Harrier IP camera and interface board?All our Harrier cameras and interface boards come with a Quick Start guide which can be downloaded from the product page on our website:https:///products/cameras/This includes instructions on discovering the camera’s IP address, assigning a fixed IP address, viewing video streams and controlling the camera. You can also view the tutorial video on our website, “How to set up a Harrier IP camera”.Examples of how to implement the text/graphical overlays and VISCA camera control can be found in the Harrier IP Example Software which is also available to download from our website.What are the optimal camera settings?Camera latency is usually related to the frame rate so higher frame rates are usually better. For example the camera latency may be specified as 3 frames, so at 30Hz this is 100ms, at 60Hz this is 50ms.If 60Hz generates too much data for your network or your recordings, the Harrier IP Camera Interface Board can be set into a special low latency mode; the camera is configured as 1080p60 and the Encoding Interval set to 2. In this mode, the camera is set to 60Hz to obtain the lowest latency, butevery other frame is discarded to give a 30Hz IP video output. This reduces the transmission bandwidth and storage requirement but retains the lowest camera latency.Can this be optimized further with less compression?The H.264 compression is done in hardware so changing the compression settings is unlikely to noticeably reduce the latency.What’s available in the Harrier range?The Harrier range of IP video products consists of:•Harrier IP Camera Interface Board – supports Tamron, Sony and other LVDS block cameras (converts LVDS video data to Ethernet IP [H.264 RTP streaming] video). The IP board has an option to support both wired and wireless IP connectivity.•Harrier 10x AF-Zoom IP Camera•Harrier 10x AF-Zoom IP/HDMI Camera (Tamron MP3010M-EV)•Harrier 23x AF-Zoom IP 4K Camera•Harrier 30x AF-Zoom IP Camera (Sony FCB-EV7520)•Harrier 36x AF-Zoom IP Camera with Global Shutter•Harrier 40x AF-Zoom IP CameraHeadquarters:Active Silicon LtdPinewood Mews, Bond Close, Iver, Bucks, SL0 0NA, UK.Tel: +44 (0)1753 650600 Fax: +44 (0)1753 651661 Email ********************** Website: North America:Active Silicon, Inc.479 Jumpers Hole Road, Suite 301, Severna Park, MD 21146, USA. Tel: +1 410-696-7642 Fax: +1 410-696-7643 Email: ********************** Website: 。
Palo Alto Networks PA-7000系列产品说明说明书

The controlling element of the PA-7000 Series is PAN-OS®, the same software that runs all Palo Alto Networks NGFWs. PAN-OS natively classifies all traffic, inclusive of a pplications, threats, and content, and then ties that traffic to the user r egardless of location or device type. The appli c ation, content, and user—in other words, the elements that run your business—then serve as the basis of your security policies, resulting in improved security posture, reduced incident response time, and lower administra-tive overhead associated with keeping s ecurity policies current in a highly dynamic environment.Key Security and Connectivity FeaturesML-Powered Next-Generation Firewall• Embeds machine learning (ML) in the core of the firewall to provide inline signatureless attack prevention for file-based attacks while identifying and immediately stopping never-before-seen phishing attempts.• Leverages cloud-based ML processes to push zero-delay signatures and instructions back to the NGFW.• Uses behavioral analysis to detect Internet of Things (IoT) devices and make policy recommendations; cloud- delivered and natively i ntegrated service on the NGFW.• Automates policy recommendations that save time and r educe the chance of human error.Identifies and categorizes all applications, on all ports, all the time, with full Layer 7 inspection • Identifies the applications traversing your network i rrespective of port, protocol, evasive techniques, or en-cryption (TLS/SSL).• Uses the application, not the port, as the basis for all your safe enablement policy decisions: allow, deny, schedule, inspect, and apply traffic-shaping.• Offers the ability to create custom App-ID™ tags for propri-etary applications or request App-ID development for new applications from Palo Alto Networks.• Identifies all payload data within the application (e.g., files and data patterns) to block malicious files and thwart data exfiltration attempts.• Creates standard and customized application usage re-ports, including software-as-a-service (SaaS) reports that provide insight into all sanctioned and unsanctioned SaaS traffic on your network.• Enables safe migration of legacy Layer 4 rule sets to A pp-ID-based rules with built-in Policy Optimizer, giving you a rule set that is more secure and easier to manage. Enforces security for users at any location,on any device, while adapting policy alls anctioned and unsanctioned SaaS trafficon user activity• Enables visibility, security policies, reporting, and forensics based on users and groups—not just IP addresses.• Easily integrates with a wide range of repositories to lever-age user information: wireless LAN controllers, VPNs, d irectory servers, SIEMs, proxies, and more.• Allows you to define Dynamic User Groups (DUGs) on the firewall to take time-bound security actions without wait-ing for changes to be applied to user directories.• Applies consistent policies irrespective of users’ locations (office, home, travel, etc.) and devices (iOS and Android®mobile devices, macOS®, Windows®, Linux desktops, lap-tops; Citrix and Microsoft VDI and Terminal Servers).• Prevents corporate credentials from leaking to third-par-ty websites and prevents reuse of stolen credentials by en-abling multi-factor authentication (MFA) at the network layer for any application without any application changes.• Provides dynamic security actions based on user behavior to restrict suspicious or malicious users.Prevents malicious activity concealed ine ncrypted traffic• Inspects and applies policy to TLS/SSL-encrypted traffic, both inbound and outbound, including for traffic that uses TLS 1.3 and HTTP/2.• Offers rich visibility into TLS traffic, such as amount of en-crypted traffic, TLS/SSL versions, cipher suites, and more, without decrypting.• Enables control over use of legacy TLS protocols, insecure ciphers, and misconfigured certificates to mitigate risks.• Facilitates easy deployment of decryption and lets you use built-in logs to troubleshoot issues, such as applications with pinned cetificates.• Lets you enable or disable decryption flexibly based on URL category and source and destination zone, address, user, user group, device, and port, for privacy and regulatory compliance purposes.• Allows you to create a copy of decrypted traffic from the firewall (i.e., decryption mirroring) and send it to traffic collection tools for forensics, historical purposes, or dataloss prevention (DLP). PA-7050PA-7080Offers centralized management and visibility • Benefits from centralized management, configuration, and visibility for multiple distributed Palo Alto Networks NGFWs (irrespective of location or scale) through Panorama™ net-work security management, in one unified user interface.• Streamlines configuration sharing through Panorama with templates and device groups, and scales log collection as logging needs increase.• Enables users, through the Application Command Center (ACC), to obtain deep visibility and comprehensive insights into network traffic and threats.Detects and prevents threats with cloud- d elivered security servicesToday’s sophisticated cyberattacks can spawn 45,000 variants in 30 minutes using multiple threat vectors and advanced tech-niques to deliver malicious payloads. Traditional siloed securi-ty causes challenges for organizations by introducing security gaps, increasing overhead for security teams, and hindering business productivity with inconsistent access and visibility. Seamlessly integrated with our industry-leading NGFWs, our Cloud-Delivered Security Services use the network effect of 80,000 customers to instantly coordinate intelligence and pro-tect against all threats across all vectors. Eliminate coverage gaps across your locations and take advantage of best-in-class security delivered consistently in a platform to stay safe from even the most advanced and evasive threats. Services include:• Threat Prevention—goes beyond a traditional intrusion pre-vention system (IPS) to prevent all known threats across all traffic in a single pass without sacrificing performance.• Advanced URL Filtering—provides best-in-class web protection while maximizing operational efficiency with the industry’s first real-time web protection engine and industry-leading phishing protection.• Wildfire®—ensures files are safe with automatic detection and prevention of unknown malware powered by indus-try-leading cloud-based analysis and crowdsourced intelli-gence from more than 42,000 customers.• DNS Security—harnesses the power of ML to detect as well as prevent threats over DNS in real time and e mpowers se-curity personnel with the intelligence and context to craft policies and respond to threats quickly and effectively.• IoT Security—provides the industry’s most comprehensive IoT security solution, delivering ML-powered visibility, pre-vention, and enforcement in a single platform.• Enterprise DLP—offers the industry’s first cloud-deliv-ered enterprise DLP that consistently protects sensitive data across networks, clouds, and users.• SaaS Security—delivers integrated SaaS security that lets you see and secure new SaaS applications, protect data, and prevent zero-day threats at the lowest total cost of ownership (TCO).Delivers a unique approach to packet processing with Single-Pass Architecture• Performs networking, policy lookup, application and decod-ing, and signature matching—for all threats and content—in a single pass. This significantly reduces the amount of pro-cessing overhead required to perform multi p le functions inone security device.Note: Results were measured on PAN-OS 10.1.* Results in this column were derived from an optimum combination of PA-7000-DPC-A and PA-7000-100G-NPC-A cards populated in all available slots.† Throughput is measured with App-ID and logging enabled, with 64 KB HTTP/appmix transactions.§ Threat Prevention throughput measured with App-ID, IPS, antivirus, anti-spyware, WildFire, DNS Security, file blocking, and logging enabled, utilizing 64 KB HTTP/appmix transactions. || IPsec VPN throughput is measured with 64 KB HTTP transactions and logging enabled.** N ew sessions per second is measured with application override, utilizing 1 byte HTTP transactions.†† The base system includes 25 virtual systems at no cost, and up to 200 additional licenses may be purchased. The maximum number of virtual systems supported is 225.• Avoids introducing latency by scanning traffic for all signa-tures in a single pass, using stream-based, uniform signa t ure matching.• Enables consistent and predictable performance when se c urity subscriptions are enabled. (In table 1, “Threat P re v ention throughput” is measured with multiple subscrip-tions enabled.)Enables SD-WAN functionality• Allows you to easily adopt SD-WAN by simply enabling it on your existing firewalls.• Enables you to safely implement SD-WAN, which is natively integrated with our industry-leading security.• Delivers an exceptional end user experience by minimizing latency, jitter, and packet loss.PA-7000 Series ArchitectureThe PA-7000 Series is powered by a scalable architec-ture for the purposes of applying the appropriate type and v olume of processing power to the key functional tasks of networking, security, and management. The PA-7000 S eries is managed as a single, unified system, enabling you to easily direct all available resources to protect your data. The PA-7000 Series chassis intelligently distributes pro-cessing demands across three subsystems, each with mas-sive amounts of computing power and dedicated memory: the processing card(s), the System Management Card, and the Dedicated Logging Card.Processing CardThe PA-7080 offers 10 slots for processing cards while the PA-7050 offers six. Processing cards are available as N etwork P rocessing Cards (NPCs), which support both net-working f unctions and data processing, or Data P rocessing Cards (DPCs), which maximize data processing perfor-mance. For network connectivity, the PA-7000 series r equires at least one NPC.Network Processing CardThe NPC is dedicated to executing all packet-process-ing tasks, including networking, traffic classification, and threat p revention. The 100G-NPC (PA-7000-100G-NPC-A) has 144 processing cores (three 48-core CPUs) with offload processing, all focused on protecting your network at up to 66 Gbps per NPC. The PA-7000-100G-NPC-A offers 100G, 40G, 10G, and 1G c onnectivity options.Data Processing CardThe DPC-A (PA-7000-DPC-A) maximizes security pro-cessing by packing 192 processing cores (four 48-core CPUs) on a s ingle card capable of protecting your network at up to 86 Gbps per DPC-A. The DPC-A leverages the de-sign of the 100G-NPC, adding a fourth compute complex and an additional offload processor in place of Ethernet I/O. Switch Management CardActing as the control center of the PA-7000 Series, the Switch Management Card (PA-7000-SMC-B) intelligently oversees all traffic and executes all management functions, using a combination of three elements: the First Packet Processor (FPP), a high-speed backplane, and the management subsys-tem.First Packet ProcessorThe key to maximizing performance and delivering linear s calability to the PA-7000 Series, the FPP constantly tracks the shared pool of available processing and I/O resources across all NPCs and DPCs, intelligently directing inbound traffic to the appropriate data processor based on the con-figured policy. As processing cards are added to increase performance and capacity, the FPP automatically detects and utilizes new resources added to the system, mean-ing no traffic management c hanges are required, nor is it necessary to re-cable or reconfigure your PA-7000 S eries. Scaling throughput to the maximum 700 Gbps on the PA-7080, or 416 Gbps on the PA-7050, is as easy as a dding a new DPC-A or 100G-NPC and allowing the FPP to d etermine the best use of the new processing power.High-Speed BackplaneEach processing card has access to more than 100 Gbps of non-blocking traffic capacity with a high-speed backplane. Management SubsystemThis subsystem acts as a dedicated point of contact for c ontrolling all aspects of the PA-7000 Series. Dedicated Logging CardThe Log Forwarding Card (PA-7000-LFC-A), an integral part of every system, utilizes a multi-core CPU design, cre-ating a dedicated subsystem to manage the high volume of logs the PA-7000 Series generates. The PA-7000-LFC-A is a high-performance card dedicated to exporting log mes-sages. It enables forwarding of logs to Panorama™ network security management, Cortex®Data Lake, and Syslog for o ffline analysis.* For additional information, refer to our ML-Powered NGFWs for 5G datasheet.3000 Tannery Way Santa Clara, CA 95054Main: +1.408.753.4000Sales: +1.866.320.4788Support: +1.866.898.9087© 2021 Palo Alto Networks, Inc. Palo Alto Networks is a registered t rademark of Palo Alto Networks. A list of our trademarks can be found at https:///company/trademarks.html. All other marks mentioned herein may be trademarks of their respective companies. strata_ds_pa-3200-series_061121To view additional information about the features and associated capacities of the PA-7000 Series, please visit /network-security/next-generation-firewall/pa-7000-series .。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Academic Open Internet Journal Volume 16, 2005A FRAMEWORK FOR MINIMIZING LATENCY IN CDNUSING URL REQUEST ROUTING APPROACHS.Manikandan1, A.Chitra2 , P.Venketesh31 Senior Lecturer, 2Professor, 3LecturerDept of Computer Science and Engg, PSG College of Technology,Coimbatore -641004, India.manigandan_me@yahoo.co.inAbstractIncrease of web data in recent years is a crisis for distributing and managing the content of a websites.Content Distribution Network (CDN) serves to provide some special solution tothese issues. Content Distribution Network maintains large number of replicas to act on behalf oforigin servers. The main issues in designing Content Distribution Network are Request routing,Object replication, replication consistency and Server Distribution. Request routing is a familiartechnique to progress the accessibility of web sites. It normally minimizes the client latency andincreases content availability. This paper presents an exploration on different Request routingapproaches and proposes a framework to minimize client latency using URL based requestrouting method.Keywords:Content Distribution Network, Request Routing, Object replication, Replicationconsistency, Latency time, URL Request Routing.IntroductionA proxy server acts as an intermediary in the Web page loading process,accepting a request from a browser, implementing authentication and filtering policies,and managing the request through, to the Web server. It can also give reports of user’sactivity and also smart caching system i.e. to read documents "unplugged" to the Internet.Proxy servers provide tighter control at network boundaries, because proxy is onlyconnected to the Internet. A proxy server has proven to be an effective solution forcontrolling network access. As the demand for Internet content has increased it leads toseveral problems that are discussed later.CDNs burst onto the scene in 1999 to address the fact that the Internet was not designed to handle large transmissions of Web content over long distances. Networkcongestion and traffic bottlenecks, worsen by growing payloads of Web traffic anddegrade both individual Web site and network performance [1]. CDNs address theproblem by storing and serving the content from many distributed surrogate servers thatare geographically apart rather than from a centralized origin server. Using cachingtechnology, CDNs store replicas of content near users, rather than repeatedly transmitting identical versions of the content from an origin server thus improving the response time. As a result CDN accelerates and improves the quality of content delivered to end users, while lowering network congestion and bandwidth costs for ISPs.CDNs replicate and deliver only content that the owners specify from surrogate servers throughout the Internet. The main issues in designing Content Distribution Network are Request routing, Object replication, replication consistency and Server Distribution.Request routing methods select the appropriate surrogate server for the required clients request and redirect. The selection is based on information about surrogates load and on network metrics collected by various ways such as routing protocol information, RTTs (round trip times) measured by network probes etc. CDNs employ routing intelligence to guide user requests to local servers. Object replication can be used to improve availability in the face of network or server failure, to create numbers of concurrent accesses, and to allow users to access to close copies of objects, thus limiting the effects of network congestion. The replicated objects are to check with its consistency pattern. The consistency pattern is decided with the consideration of consistency models and policies designed by individual companies. Yet another challenge in CDN is to position the surrogate server in the right location. The locating problem includes surrogate server placement and surrogate content placement.The Building blocks for a single CDN consist of several surrogate servers, a distribution system, a request routing system and an accounting system (used for billing). This paper presents a report based on the investigation on different request routing methods and proposed URL request routing method with its performance with DNS based request routing system.The rest of this paper is organized as follows. Section 2 describes various request routing methods that are deployed in CDNs. The proposed URL request routing method with its equations are mentioned in Section 3. Section 4 presents the comparison of different methods. Section 5 concludes the paper with final remarks.Request RoutingA typical CDN contains active components like Request Routing System (RRS), Distribution System (DS) and Accounting System (AS) and Surrogate server as shown in the fig1. A request-routing system [2][3] facilitates the activity of directing a client request to a suitable surrogate server. It consists of a set of network elements called Request routers. A Distribution system consists of a collection of network elements called content-distributor. It supports the activity of moving a publisher’s content from the origin server to one or more Surrogate servers (using either Push or Pull algorithm).The Accounting system supports the measurement and recording of content distribution and delivery activities. Information recorded by the accounting system is used as a basis for the transfer of money, goods, and obligation among the network service providers and the content providers.Fig1: CDN Architecture.C1, C2, C3-Clients, DS-Distribution System,RRS-Request Routing System, AS- Accounting SystemServers in a CDN are located at different locations in the Internet called surrogate servers. Client typically access content from surrogate servers by first contacting a request router. The request router makes a server selection decision and returns a server address to the client. The client then retrieves the content from the specified surrogate servers. A primary issue for a request router is how to direct client requests for an object served by the surrogate servers within the network. From the database, Request routerschoose the best server using static and dynamic information of various surrogate servers. Surrogate servers pass the information such as metrics of the server, network conditions and client proximity to the Request router. This section describes different techniques like DNS based, Transport layer based, Application layer based and content based request routing used in CDN.DNS based Request RoutingDomain Name Server (DNS) based request routing is extensively deployed in the Internet at present. DNS based request routing [4] is also deployed as a directory service in CDNs for resolving the client request to appropriate surrogate server address. Specialized DNS server included in DNS system does the DNS resolution process [5-7]. DNS server is capable of resolving single or multiple surrogate address to handle the domain name of the desired website or content.The client request for a web site or content in the Internet, subsequently the request moves towards the nearest DNS. The DNS resolves the request and returns the apt surrogate server address that can be either single or multiple replies. A single reply CDN server is authoritative for the entire DNS domain or sub domain. Client gets the surrogate address as a reply and contacts the surrogate server for website or content. Then the content is transferred from the surrogate servers to the client. If multiple surrogate server address is reply to the client, Client site DNS server decides to which surrogate server it should select from the reply. RFC 2782 (DNS SRV) provides guidance on the use of DNS for load balancing [8]. The aforesaid methods are single-level DNS server resolution system. Instead of single-level DNS resolution system multi-level DNS server resolution is in practice. This is to fetch the IP address from the next level of DNS server.A hierarchical architecture is deployed for multi-level DNS server resolution approach and in this, the most common mechanism used to insert multiple requests routing DNS server, in a single DNS resolution is by employing Name Server (NS) and Canonical NAME (CNAME).In NS redirection, records are redirecting the authority to next hierarchical level. Here, to implement NS mechanism, Multiple DNS server is implicated in the name resolution. For example, a client site DNS server resolving wouldeventually request a resolution of from the name server, authoritative for . The name server authoritative for this domain might be a Request-Routing NS server. In this case the Request-Routing DNS server can either return a set of A records or can redirect the resolution of the request to the DNS server that is authoritative for using NS records.In CNAME redirection [4], the Request-Routing DNS server returns a CNAME record to direct resolution to an exclusively new domain. In principle, the new domain might use a new set of Request-Routing DNS servers. Multiple physical DNS servers that combine request routing and metric measurement can share an anycast IP address [9]. The packet containing the DNS resolution request will reach one of these DNS servers, which is the closest to the client site DNS server. After receiving the packet, the DNS server knows that it is the closest and can use this information in making routing decision.Transport Layer Request-RoutingIn Transport layer request routing technique closely inputs the first packet of the client’s request to select the appropriate surrogate server for high-level granularity. As shown in the fig2, the first packet of the client request contains data about services, client, IP address, and port information and layer four protocols used in client side. Using these information’s and integrating with user-defined policies, surrogate servers are selected.In practice, the transport layer request routing using DNS server, which chooses forward flow traffic. But reverse flow traffic has larger data than forward flow traffic, so it takes a direct route instead via DNS.Fig2: Transport Layer Request-Routing ArchitectureApplication layer Request RoutingApplication layer based request routing is implemented in DNS as like transport layer request routing approach. In this even more fine-grained request routing method is established for better efficient control. The first packet is imported even more closely than transport layer header, which exposes to the client IP address and with objects enable system for better selection of surrogateApplication layer based request routing is classified into two types1. Header Inspection2. Content ModificationHeader InspectionIn HTTP [10], RTSP [11] and SSL application level protocol’s first portion of the header gives information about how request should be directed towards the surrogate. So it is easy to categorize the different service request and direct to appropriate surrogate server. Basically two different methods are used to inspecting the header Universal Resource Locater (URL) and MIME request header based implementation.Application level protocol such as HTTP and RTSP [11] describe the URL [7] methods, which uses prefix URL for content request in decision-making. The URL based requesting routing uses 302 redirection and in path element method for its routing and directing towards the surrogate server.MIME header helps in identifying the type of client device request, like, voice browser, PDA, Cell phone or wireless nodes, which needs special content delivery. These issues are implemented with the help of cookie languages, user agents for decision-making. In MIME header site-specific identifier method helps to authenticate and identify a session form the client that is used in application level protocol like SSL.Content ModificationContent routing [12] sustain in the central part of the Internet performed by content routers. This technique is used to take routing decisions without any special switching device between the server and the client. The main advantage of this content routing is the client can access the origin server directly. Only gateways, firewalls and Border Gateway Protocol (BGP) level routers have to be content router. Clients instigate content requests by contacting a local content router. Each content router preserves a set of name-to-next-hop mappings in a routing table.In broad-spectrum, the technique takes advantage of content objects that consist of basic structure that consist of references to additional object called embedded objects. Most web pages comprise HTML document (plain text) that contains some embedded objects, like JPEG images. Embedded HTML directives contain embedded objects that are used as a reference in the particular web pages. Hence, only these meticulous objects will be retrieved from the surrogate server. Now, the content provider with respect to the embedded objects that are retrieved from the best origin server will modify HTML web pages. The technique is also referred as URL rewriting. In general two types of URL rewriting are executed, namely A-priori URL Rewriting, On-Demand URL Rewriting.Content server’s authenticity verifies the signature on initial routing update. If a content peer becomes unreachable, then all the contents available through that peer are unreachable as well. Routing advertisement from content servers also includes a measure of the load at that server, specified in terms of the predictable response latency. Contentmodification techniques must not violate the architectural concepts of the Internet [13]. Special deliberation is made to guarantee the task of modifying the content is performed in a consistent manner with RFC 3238, whether it checks operations or modifications on content is done [13].URL Based Request RoutingIn the Default DNS based approach (First approach), If client wants to request for a content from a surrogate server which is located apart, the client will establish a TCP connection with nearest DNS server for resolving the URL to IP address. The DNS server gives the IP address back as a response to the requested client. The client creates HTTP header with the resolved IP address and sent to default gateway. The IP address in the HTTP header is look up in the routing table and if it’s in the routing table, the HTTP header request is then forwarded to the surrogate server via the particular interface as shown in the fig3.Router or GatewayFig3: Default DNS to resolve IP and sending HTTP requests to Router.In the second approach as shown in the fig3 the DNS look up table for resolving the URL to IP address is implemented using Message Digest 5 algorithm [14]. MD5 algorithm use digests to reduce variable length URL string in to fixed length digest value. The Digest value is used as a key in the DNS hash table to map corresponding IP address. But in default DNS server, the entire URL is stored as the key and to retrieve the IP address, linear searching algorithm is implemented.In the new URL routing [15] approach as shown in the fig4, instead of sending the resolved IP address back to the client, the client request is modified and the resolved IP address is included in the HTTP request in URL router itself and the corresponding IP address is looked up in the routing table. The proposed new method reduces the latency time and also reduces the traffic between the clients and the URL router. Using the proposed method, we have reduced the IP resolving time and reduce the latency of theclient by approximately 50%.URL RouterFig4: URL routing where DNS table is Inbuilt in the RouterGeneral EquationDo + DLo + Ro + RLo----- Equation (1)Where,Do - TCP connection Establishing Time (millisecond) from client to DNS server. DLo - DNS table Look-up Time (millisecond) to resolve IP address from URL. Ro - TCP connection Establishing Time (millisecond) from client to Router.RLo – Routing table Look-up Time (millisecond).Co is a constant for all the three above mentioned methods and given by Co= Ro + RLoDefault DNS:Do + DLo + Co----- Equation (2) MD5 Hashing DNS table:Do + Ho + Co----- Equation (3) URL Routing:Ho + Co ----- Equation (4)Here Ho is a MD5 Hashing method for DNS look up table.DiscussionDNS based request routing is easy and simple to implement but some of its limitations are: Domain level resolution is only possible in DNS based request routing. Not all DNS realization is standard. Name server based DNS request routing system supports only with the information of client site server, which has the database of short time-to-live values (TTL). Some time it can cause timeouts and lead to exception handling condition. So, choosing the value of TTL is very critical. DNS server can allow recursive resolution of DNS name. For example, Content Network can resolve , but the request for the resolution might come from as a result of the recursion and might allow additional overheads. DNS based request routing techniques can suffer from serious limitations. The use of such techniques can overburden third party DNS servers, which should not be allowed [16]. RFC 2782 provides warnings on the use of DNS for load balancing [8].The overhead associated with transport-layer Request-Routing [16] is healthier suited for long-lived sessions such as RTSP [11] and FTP [17]. In general, transport-layer Request-Routing can be combined with DNS based techniques. Hence, the DNS based methods could be used as a first step in deciding on an appropriate surrogate with more accurate refinement made by the transport-layer Request-Routing system.An application-layer based request routing system is using application-layer anycasting [18]. The process could be performed in real time at the time of the object request. Object-specific control of server loading is done using URL based application layer request routing. Header based application routing can be used to direct traffic to a language-specific delivery node.Content based approach experience many limitations, such as, the initial request from a client and all the embedded objects of the HTML web pages are to be served from the specific site of the origin server [19]. Non-cacheable pages can be marked to be cacheable only for a relatively short period of time. Rewritten URLs on cached pages can cause problems, because they can get outdated and point to surrogates that are no longer available or no longer good choices. Even though content based routinghas a limitation, the overall goal is to improve scalability and the performance for delivering the modified content, including all embedded objects.Combination of different mechanisms can be beneficial and advantageous over using one of the mechanisms alone. Content modification can be used together with DNS Request-Routing to overcome the resolution granularity problem in DNS Request-Routing. Using DNS Request-Routing, requests for those objects can now dynamically be directed to different surrogates. With content modification, references to different objects on the same origin server can be rewritten to point into different domain name spaces.In the equation (1) the TCP connection Establishing Time from client to Router (Ro) and Routing table Look-up Time (RLo) is constant (Co) for all the three methods. Using default DNS server the equation (2) represents the time to pass HTTP request header from the nearest router to surrogate server. In default DNS the searching time for resolving the IP address depends on number of URL entries in the DNS table i.e. O(n). In equation (3) MD5 hashing method used in DNS server, Ho is the resolving time or computational time of the given URL. By means of hashing, the IP address is resolved in O(1) from the DNS table. Comparing the MD5 hashing method with default DNS server method Do and Co are constant. The difference in searching time for both methods is [O(n) – O(1)]. The latency can be reduced by [O(n) – O(1)] times to the users in the internet. When comparing with URL routing, the DNS hashing is inbuilt in the URL router. So in the equation (4), Do can be ignored and using URL routing the latency is reduced by {Do + [O(n) – O(1)]} times to the internet users.ConclusionThis paper discusses a comparison on different types of request routing methods used in content distribution networks. The importance of DNS based and application based request routing schemes with all the merits and limitations of different approaches are compared. A novel framework for URL routing with MD5 hashing method used in DNS look-up table has been proposed in this paper. It is also identified that URL routing scheme would improve the performance and scalability of request routing in CDN.References[1] -“Internet Bottlenecks”.[2] B. Cain, F. Douglis, M. Green, M. Hofmann, R. Nair, D. Potter, and O.Spatscheck, Known CDN Request-Routing Mechanisms", November 2000.[3] M. Day, B.Cain, and G. Tomlinson, "A Model forCDN Peering", November 2000.[4] Md. Humayun Kabir, Eric G. Manning, Gholamali C. Shoja., “Request-RoutingTrends and Techniques in Content Distribution Network” Parallel, Networking, Distributed Applications (PANDA) Laboratory, University of Victoria , Canada.[5] Eastlake, D. and A, Panitz, "Reserved Top Level DNS Names", BCP32, RFC2606, June 1999.[6] Mockapetris P.,"Domain names - concepts and facilities", STD13, RFC 1034,November 1987.[7] Mockapetris P., "Domain names - concepts and facilities", STD13, RFC 1035,November 1987.[8] Gulbrandsen A., Vixie, P. and L. Esibov, "A DNS RR for specifying the locationof services (DNS SRV)", RFC 2782, February 2002.[9] A.Barbir et al., “Known CN request-routing mechanisms.” Internet Draft (draft-ietf-RFC 3568, July 2003.[10] Fielding, R., Gettys, J., Mogul, J., Frystyk, H., Masinter, L., Leach, P. and T.Berners-Lee, "Hypertext Transfer Protocol -- HTTP/1.1", RFC 2616, June 1999.[11] Schulzrinne, H., Rao, A. and R. Lanphier, "Real Time Streaming Protocol", RFC2326, April 1998.[12] Mark Gritter, David R. Cheriton, "An Architecture for Content Routing Supportin the Internet", /papers/contentrouting/2001[13] Floyd, S. and L. Daigle, "IAB Architectural and Policy Considerations for OpenPluggable Edge Services", RFC 3238, January 2002.[14] R. Rivest, “The MD5 Message Digest Algorithm”, November1992.[15] Zornita Genova , Kenneth, “ Managing routing tables for URL routers in CDN,International Journal of Networking Management, 2004.[16] Shaikh A., "On the effectiveness of DNS-based Server Selection", INFOCOM2001, August 2001.[17] Postel, J. and J. Reynolds, "File Transfer Protocol", STD 9, RFC 959, October1985.[18] Huston, G., "Commentary on Inter-Domain Routing in the Internet", RFC 3221,December 2001.[19] K. Johnson et al., "The measured performance of content distribution networks",Proceedings of the Fifth International Web Caching Workshop and ContentDelivery Workshop 2000, May 2000.Technical College - Bourgas All rights reserved, © March, 2000。
